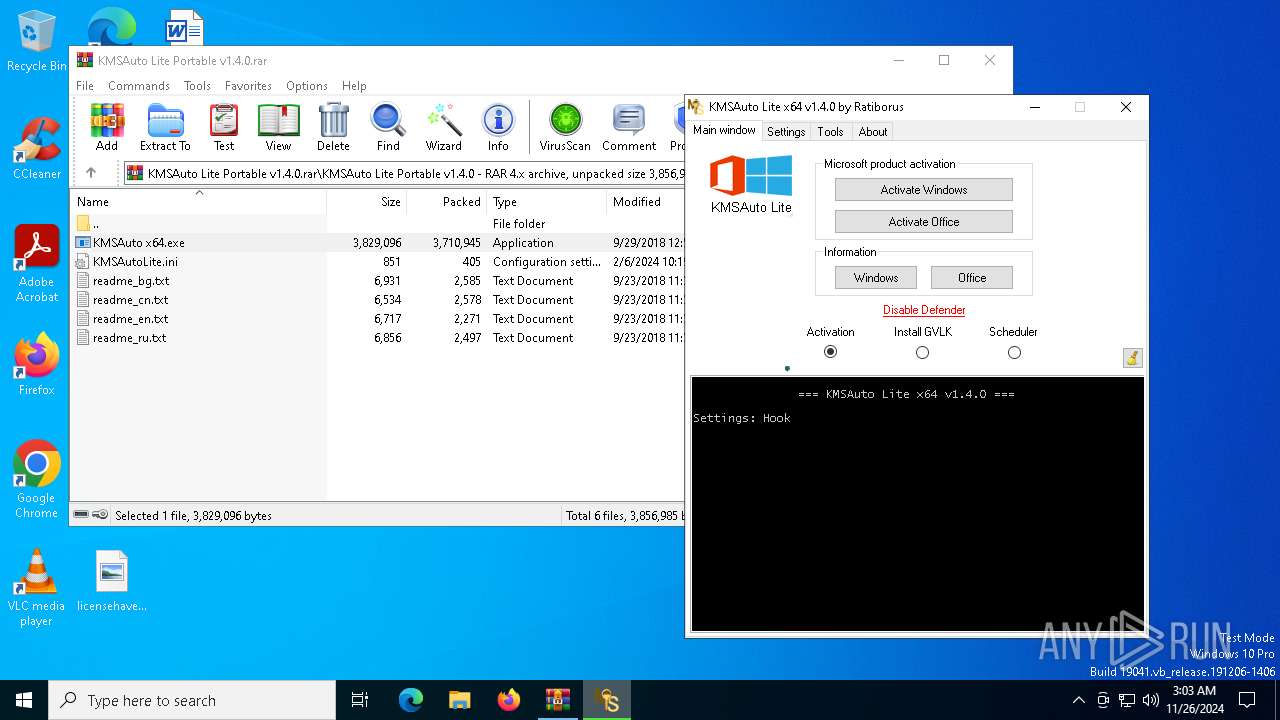
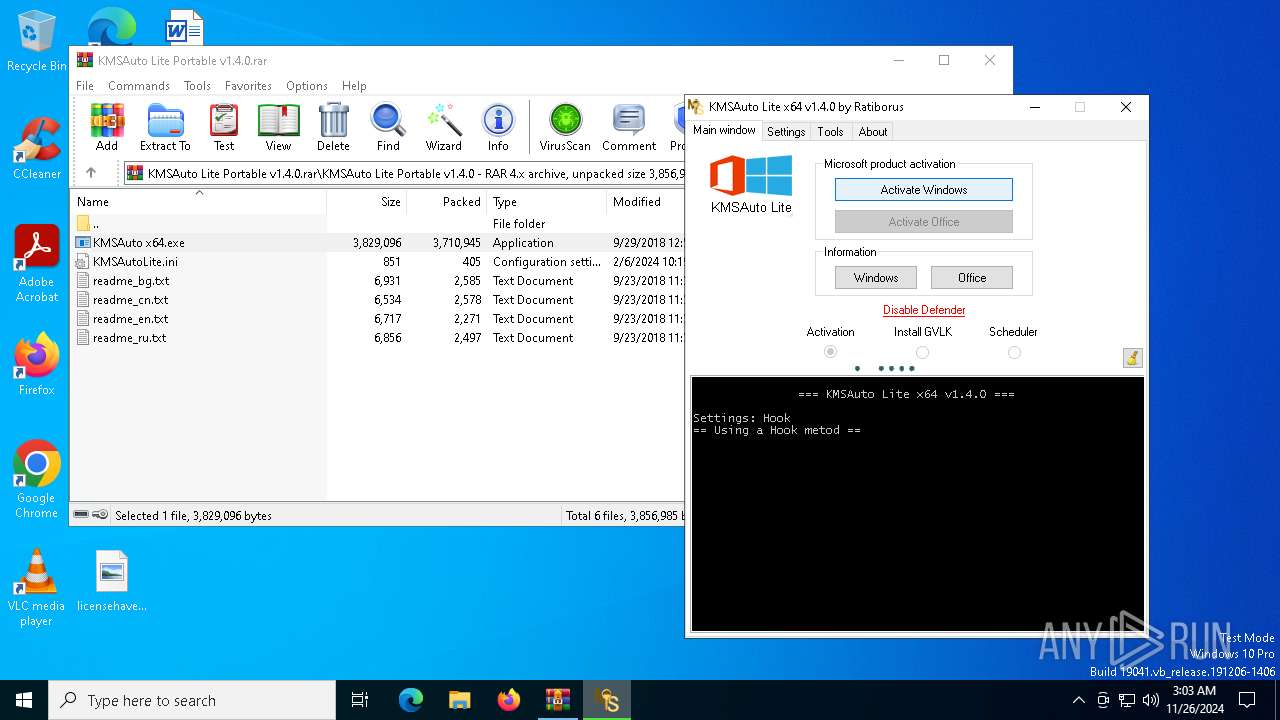
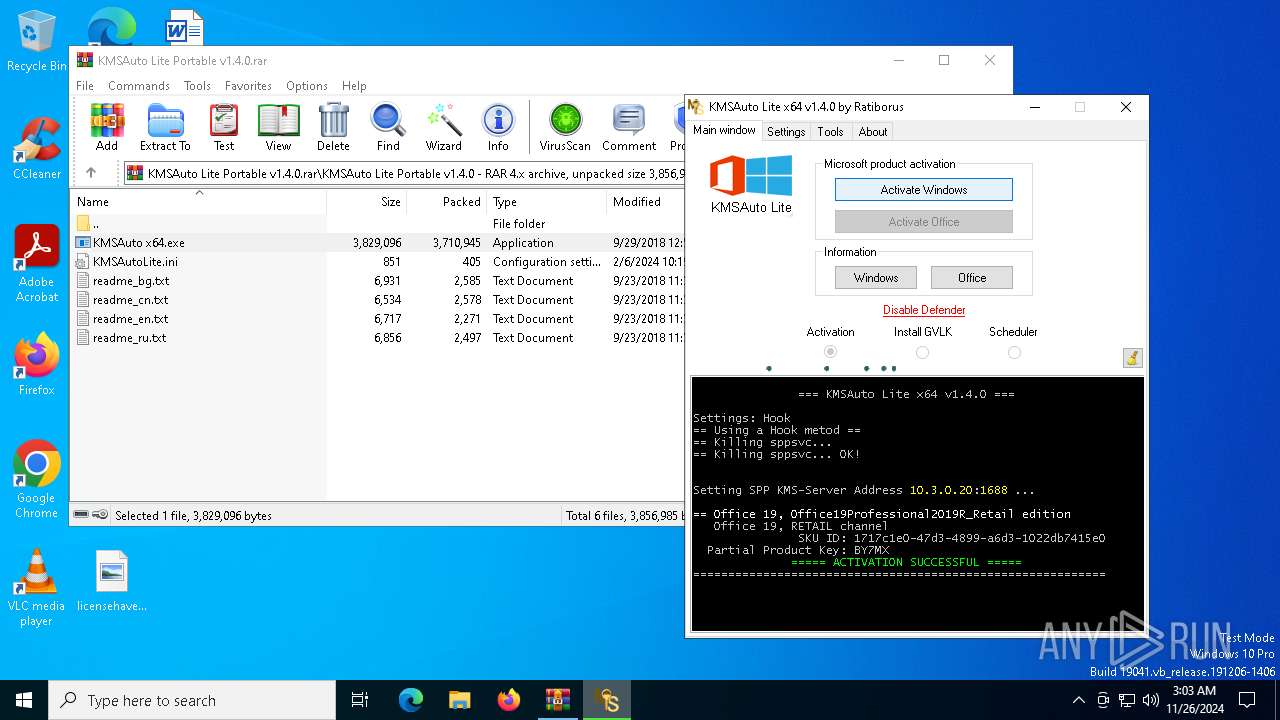
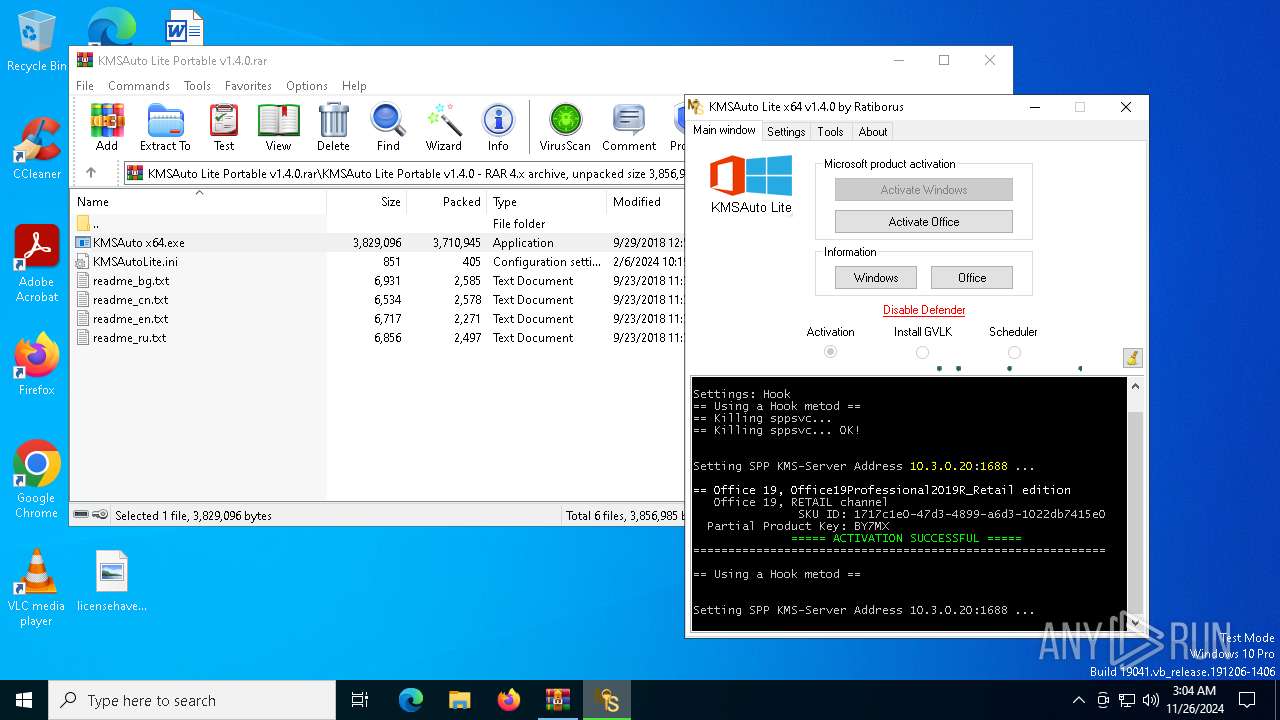
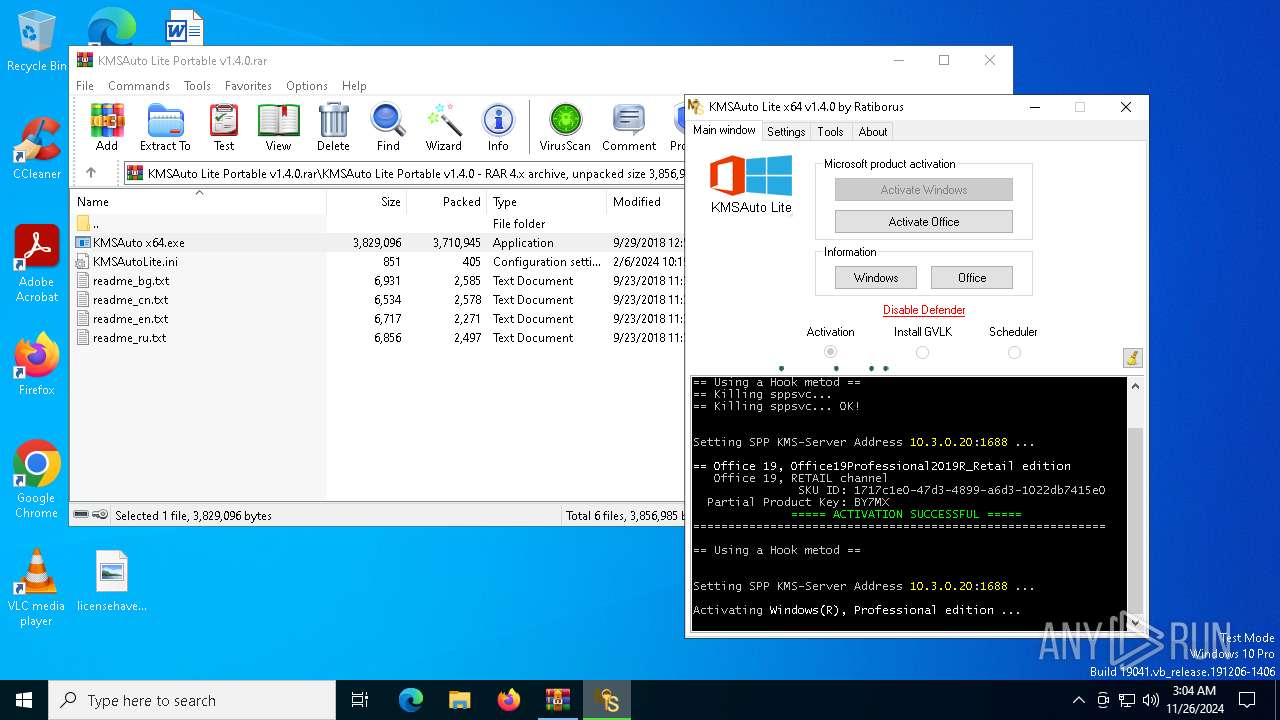
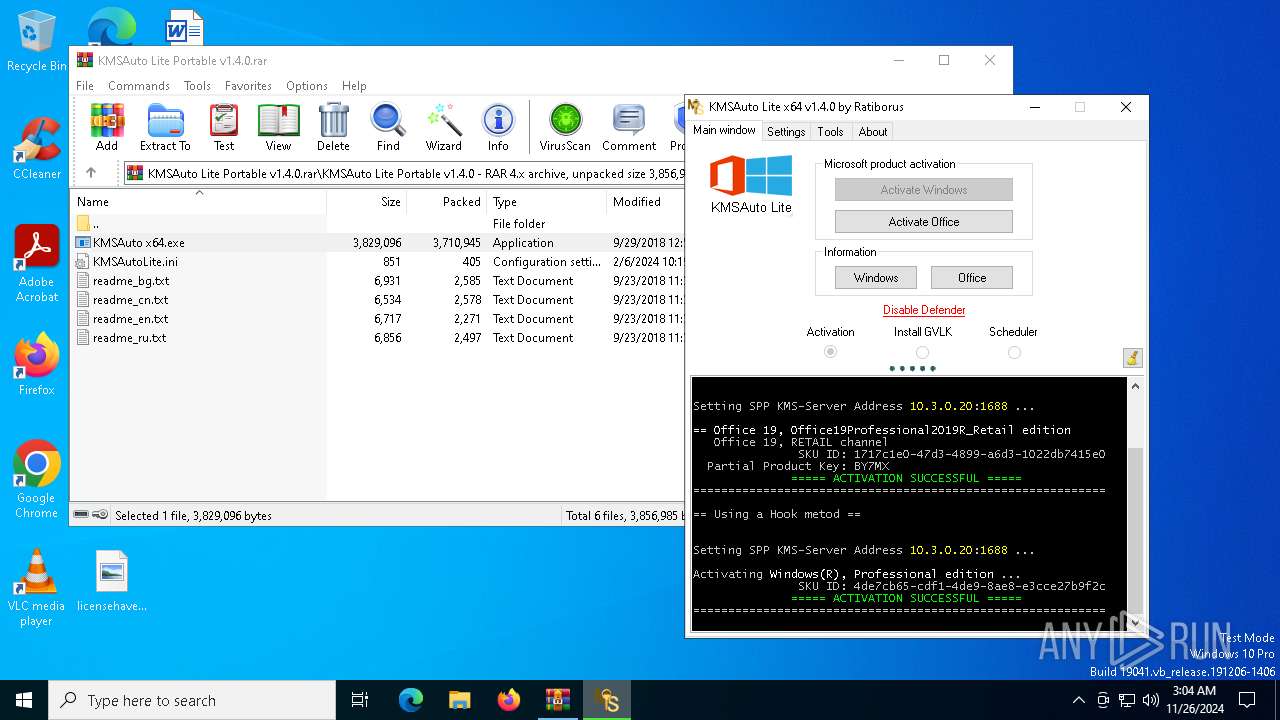
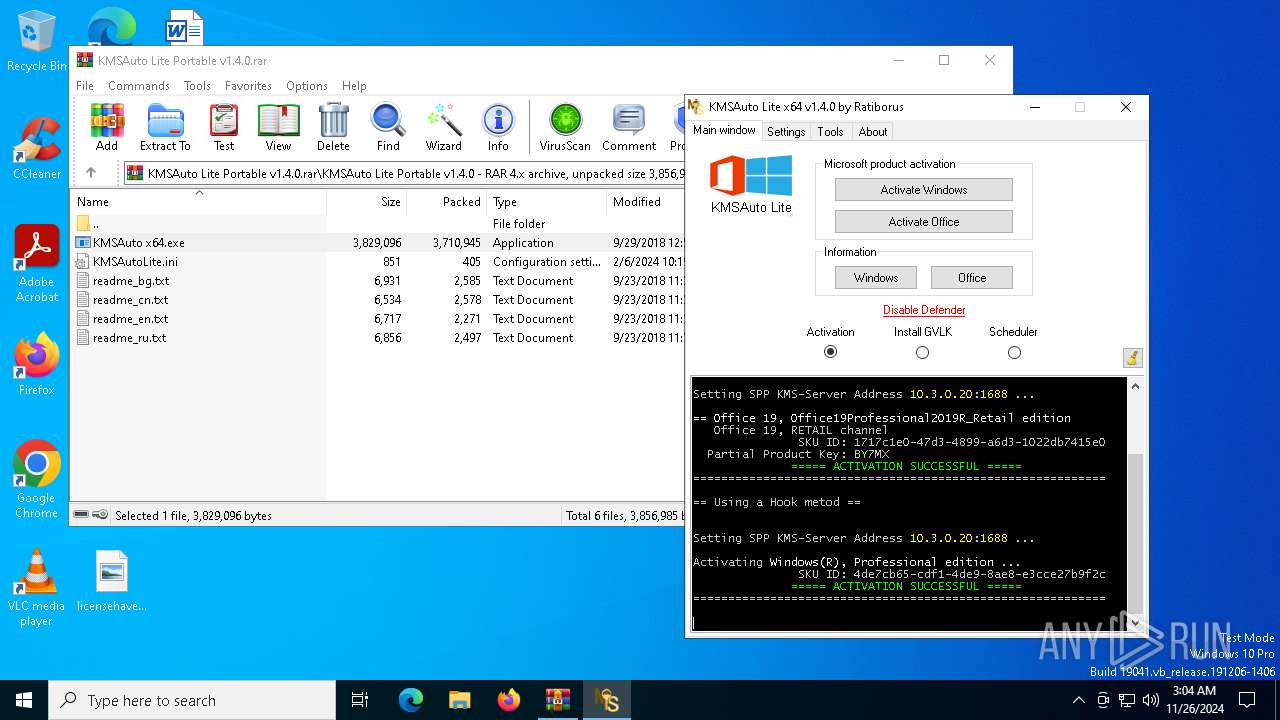
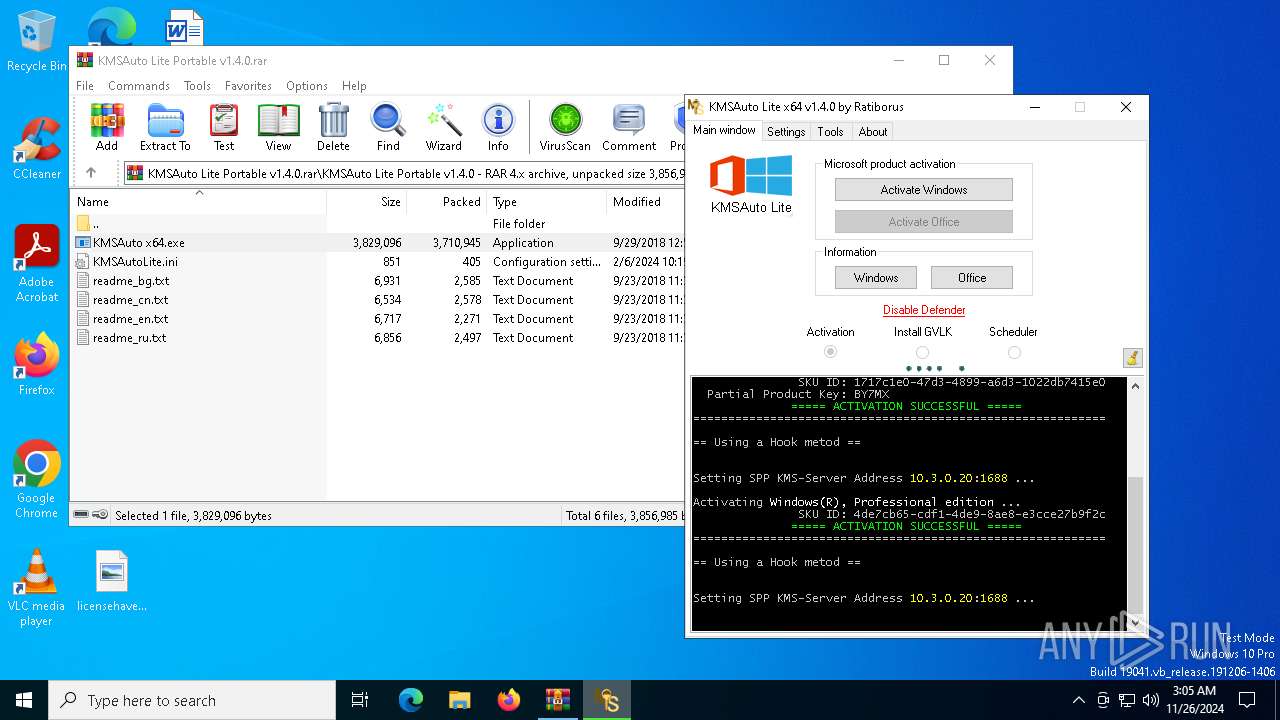
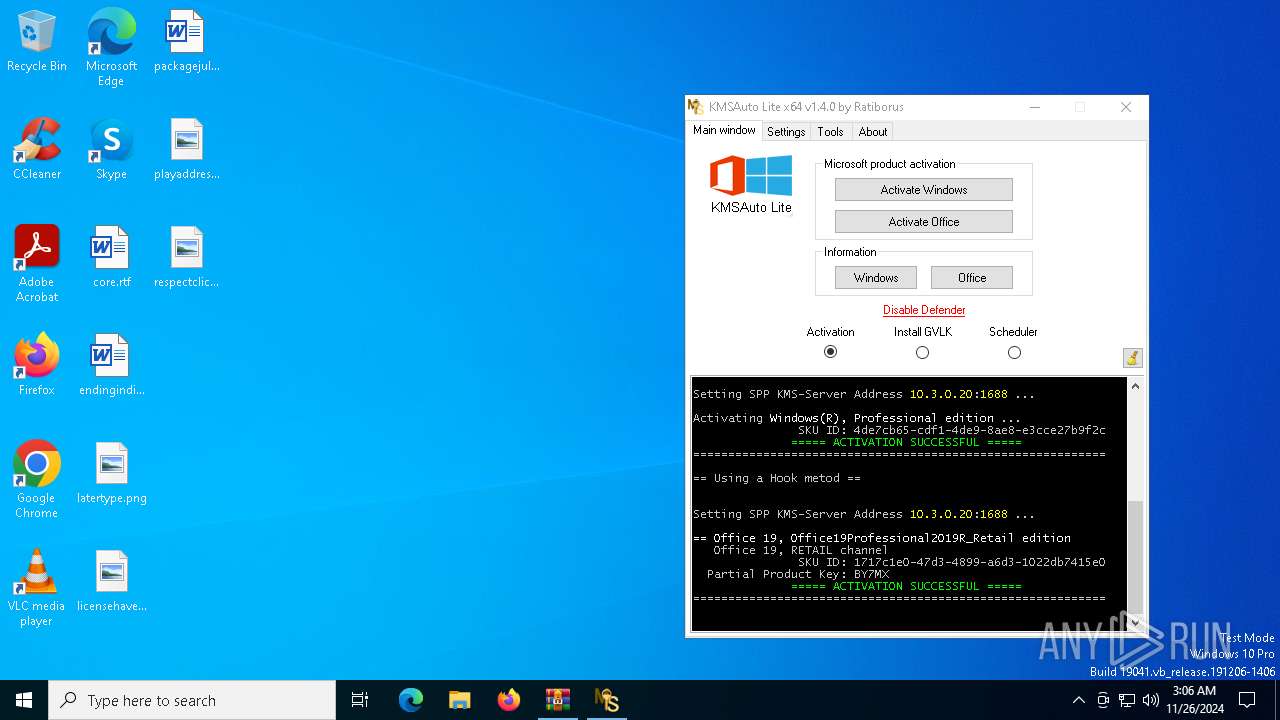
| File name: | KMSAuto Lite Portable v1.4.0.rar |
| Full analysis: | https://app.any.run/tasks/168172b7-1c90-4ca5-8b45-c0f220247e16 |
| Verdict: | Malicious activity |
| Analysis date: | November 26, 2024, 03:03:07 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | 400F46C55DB091D59451D0B9AB4B1EB9 |
| SHA1: | A345304C7463A9196B86F965940B7CE7A53682C3 |
| SHA256: | 03DFFF609A9A39FABB4339273618CB8C2F78D6B98B5E141D288B102B1EA20D70 |
| SSDEEP: | 98304:lZkEXavlwOYxwOd5rrXmiOqQ7UkhiAmlxsF0RCO2x4XWkUBkx6KfQ6ZVGZtD89y4:r0yC0XPbP |
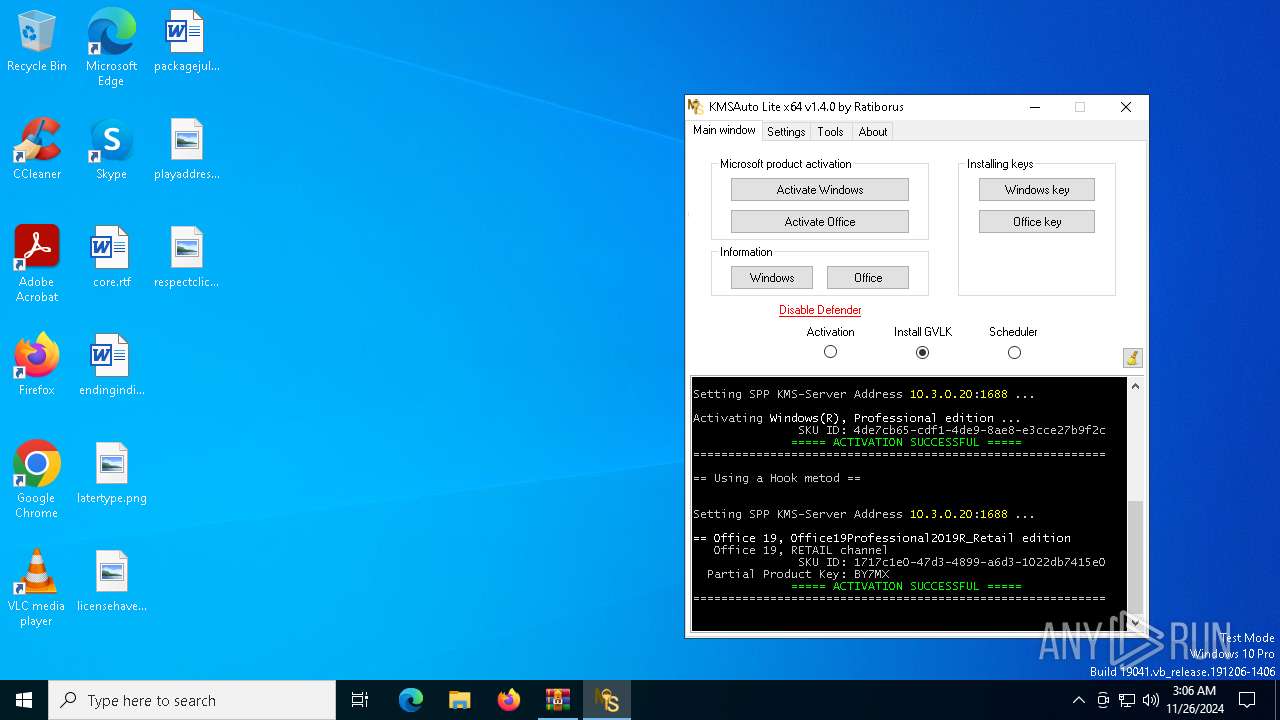
MALICIOUS
Executing a file with an untrusted certificate
- KMSAuto x64.exe (PID: 748)
- KMSAuto x64.exe (PID: 3576)
Generic archive extractor
- WinRAR.exe (PID: 4724)
Uses WMIC.EXE to add exclusions to the Windows Defender
- cmd.exe (PID: 6388)
- cmd.exe (PID: 6504)
- cmd.exe (PID: 6212)
- cmd.exe (PID: 5008)
Starts NET.EXE for service management
- net.exe (PID: 6904)
- cmd.exe (PID: 6856)
SUSPICIOUS
Found strings related to reading or modifying Windows Defender settings
- KMSAuto x64.exe (PID: 3576)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 6688)
- cmd.exe (PID: 6392)
- cmd.exe (PID: 6552)
- cmd.exe (PID: 5268)
- cmd.exe (PID: 6204)
- cmd.exe (PID: 6488)
- cmd.exe (PID: 1796)
- cmd.exe (PID: 4120)
- cmd.exe (PID: 6388)
- cmd.exe (PID: 7000)
- KMSAuto x64.exe (PID: 3576)
- cmd.exe (PID: 3608)
- cmd.exe (PID: 6376)
- cmd.exe (PID: 1416)
- cmd.exe (PID: 432)
- cmd.exe (PID: 6868)
- cmd.exe (PID: 7048)
- cmd.exe (PID: 6244)
- cmd.exe (PID: 640)
- cmd.exe (PID: 6628)
- cmd.exe (PID: 1412)
Hides command output
- cmd.exe (PID: 6772)
Starts SC.EXE for service management
- cmd.exe (PID: 6772)
- cmd.exe (PID: 6884)
- cmd.exe (PID: 6696)
- cmd.exe (PID: 7080)
- cmd.exe (PID: 6672)
- cmd.exe (PID: 2612)
- cmd.exe (PID: 5720)
- cmd.exe (PID: 3808)
- cmd.exe (PID: 3488)
- cmd.exe (PID: 6276)
- cmd.exe (PID: 556)
- cmd.exe (PID: 6584)
- cmd.exe (PID: 4504)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 7012)
- cmd.exe (PID: 7136)
- cmd.exe (PID: 6900)
- cmd.exe (PID: 6708)
- cmd.exe (PID: 7136)
- cmd.exe (PID: 5320)
- cmd.exe (PID: 4244)
Executable content was dropped or overwritten
- KMSAuto x64.exe (PID: 3576)
- cmd.exe (PID: 772)
- cmd.exe (PID: 6224)
- cmd.exe (PID: 6936)
- cmd.exe (PID: 6804)
- cmd.exe (PID: 3900)
- cmd.exe (PID: 6748)
Starts CMD.EXE for commands execution
- KMSAuto x64.exe (PID: 3576)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- cmd.exe (PID: 6512)
- cmd.exe (PID: 6784)
- cmd.exe (PID: 6516)
- cmd.exe (PID: 6160)
- cmd.exe (PID: 6476)
- cmd.exe (PID: 6560)
- cmd.exe (PID: 5876)
- cmd.exe (PID: 3992)
- cmd.exe (PID: 4708)
- cmd.exe (PID: 6568)
- cmd.exe (PID: 6208)
- cmd.exe (PID: 5200)
KMS tool has been detected
- cmd.exe (PID: 6472)
- cmd.exe (PID: 6512)
- KMSAuto x64.exe (PID: 3576)
- cmd.exe (PID: 6516)
- cmd.exe (PID: 5836)
- cmd.exe (PID: 6476)
- cmd.exe (PID: 3992)
- cmd.exe (PID: 4708)
- cmd.exe (PID: 3296)
- cmd.exe (PID: 6208)
The process executes VB scripts
- cmd.exe (PID: 6584)
- cmd.exe (PID: 4428)
- cmd.exe (PID: 6416)
- cmd.exe (PID: 7108)
- cmd.exe (PID: 3896)
- cmd.exe (PID: 1856)
- cmd.exe (PID: 7008)
- cmd.exe (PID: 4628)
Uses NETSH.EXE to add a firewall rule or allowed programs
- cmd.exe (PID: 6772)
- cmd.exe (PID: 6472)
- cmd.exe (PID: 5836)
- cmd.exe (PID: 4648)
- cmd.exe (PID: 3296)
- cmd.exe (PID: 772)
Executes as Windows Service
- KMSSS.exe (PID: 6068)
- KMSSS.exe (PID: 3920)
- KMSSS.exe (PID: 3632)
Uses ROUTE.EXE to obtain the routing table information
- cmd.exe (PID: 1520)
- cmd.exe (PID: 7144)
- cmd.exe (PID: 2084)
The process downloads a VBScript from the remote host
- cmd.exe (PID: 4428)
- cmd.exe (PID: 3896)
- cmd.exe (PID: 1856)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 1380)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4724)
UPX packer has been detected
- KMSAuto x64.exe (PID: 3576)
Deletes a route via ROUTE.EXE
- ROUTE.EXE (PID: 6920)
- ROUTE.EXE (PID: 6436)
- ROUTE.EXE (PID: 3864)
Manual execution by a user
- WINWORD.EXE (PID: 1200)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| FileVersion: | RAR v4 |
|---|---|
| CompressedSize: | 3711010 |
| UncompressedSize: | 3829096 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2018:09:29 00:57:30 |
| PackingMethod: | Normal |
| ArchivedFileName: | KMSAuto Lite Portable v1.4.0\KMSAuto x64.exe |
Total processes
415
Monitored processes
274
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 432 | "C:\WINDOWS\System32\cmd.exe" /c reg.exe delete "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SppExtComObj.Exe" /f | C:\Windows\System32\cmd.exe | — | KMSAuto x64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 440 | cscript //nologo "C:\Program Files\Microsoft Office\Office16\ospp.vbs" /sethst:10.3.0.20 | C:\Windows\System32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 540 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 556 | "C:\WINDOWS\System32\cmd.exe" /c sc.exe stop KMSEmulator | C:\Windows\System32\cmd.exe | — | KMSAuto x64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 640 | "C:\WINDOWS\System32\cmd.exe" /c reg.exe delete "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SppExtComObj.Exe" /f /v "KMS_Emulation" | C:\Windows\System32\cmd.exe | — | KMSAuto x64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 648 | sc.exe delete KMSEmulator | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 748 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa4724.2051\KMSAuto Lite Portable v1.4.0\KMSAuto x64.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa4724.2051\KMSAuto Lite Portable v1.4.0\KMSAuto x64.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 772 | "C:\WINDOWS\System32\cmd.exe" /c copy "C:\WINDOWS\Temp\KMSAuto_Files\bin\SppExtComObjPatcher.exe" "C:\WINDOWS\system32\SppExtComObjPatcher.exe" /Y | C:\Windows\System32\cmd.exe | KMSAuto x64.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 772 | "C:\WINDOWS\System32\cmd.exe" /c Netsh.exe Advfirewall Firewall add rule name=0pen_Port_KMS2 dir=out action=allow protocol=TCP localport=1688 | C:\Windows\System32\cmd.exe | — | KMSAuto x64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 776 | cscript //nologo "C:\Users\admin\AppData\Local\Temp\slmgr.vbs" /skms 10.3.0.20:1688 | C:\Windows\System32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
Total events
55 942
Read events
54 464
Write events
1 368
Delete events
110
Modification events
| (PID) Process: | (4724) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (4724) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (4724) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4724) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4724) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4724) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\KMSAuto Lite Portable v1.4.0.rar | |||
| (PID) Process: | (4724) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4724) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4724) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4724) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
18
Suspicious files
142
Text files
121
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4724 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4724.2051\KMSAuto Lite Portable v1.4.0\KMSAuto x64.exe | executable | |
MD5:F582CAAC417AFACD7EE7D2C2C3233E18 | SHA256:7F4F467A8A5274CF7AE5D3565149E0EEA55E0E794649D2482A297B6A37F8791D | |||
| 6224 | cmd.exe | C:\Windows\System32\SppExtComObjHook.dll | executable | |
MD5:E3281CD3A5293B962683B5AB4AD49309 | SHA256:26AE72400087F417ACCEDB8F68F1E7DF88A7B0B5904A17AC6FCB1D54E9B29980 | |||
| 4724 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4724.2051\KMSAuto Lite Portable v1.4.0\readme_en.txt | text | |
MD5:746BCDA047FF3FDD3B71FB73942252CA | SHA256:02AA25D5E5D7F28C7D01AF3A19E9361EE1BE2CC5D8E99FFA42580D39D6C331CA | |||
| 3576 | KMSAuto x64.exe | C:\Windows\Temp\KMSAuto_Files\bin\SppExtComObjHook.dll | executable | |
MD5:E3281CD3A5293B962683B5AB4AD49309 | SHA256:26AE72400087F417ACCEDB8F68F1E7DF88A7B0B5904A17AC6FCB1D54E9B29980 | |||
| 4724 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4724.2051\KMSAuto Lite Portable v1.4.0\KMSAutoLite.ini | text | |
MD5:936A914AA058549CC67B333C47B73542 | SHA256:4B06E014FE3CE230075B09C92D9F1D7236775104CF6BC1C86BD522612EF4BDE8 | |||
| 4724 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4724.2051\KMSAuto Lite Portable v1.4.0\readme_cn.txt | text | |
MD5:0ED59376D9489FF768982479B0D9CD70 | SHA256:4A6A89357A82760D0D2E6869D76BEA57012F8F3430205C21D212C33F3D2B42EA | |||
| 3920 | KMSSS.exe | C:\Windows\Temp\KMSAuto_Files\bin\KMSSS.log | text | |
MD5:81051BCC2CF1BEDF378224B0A93E2877 | SHA256:7EB70257593DA06F682A3DDDA54A9D260D4FC514F645237F5CA74B08F8DA61A6 | |||
| 6804 | cmd.exe | C:\Windows\System32\SppExtComObjPatcher.exe | executable | |
MD5:3D062A5923050F0885AA5E4882096744 | SHA256:68B536FB2A6A8C9A2B36E17EAD46343D156020C75C559ED068483ECF5BC3F060 | |||
| 6936 | cmd.exe | C:\Windows\System32\SppExtComObjHook.dll | executable | |
MD5:E3281CD3A5293B962683B5AB4AD49309 | SHA256:26AE72400087F417ACCEDB8F68F1E7DF88A7B0B5904A17AC6FCB1D54E9B29980 | |||
| 5200 | cscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\A583E2A51BFBDC1E492A57B7C8325850 | binary | |
MD5:4FC0FFE5395D770EC1116A2D4FE39B1F | SHA256:AF3108BB2E8138CB6BE65BA7E0F4B8304E44E80ACB141CFA1205E10899A5AF9C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
19
TCP/UDP connections
133
DNS requests
47
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5732 | svchost.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5732 | svchost.exe | GET | 200 | 173.223.117.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5400 | SIHClient.exe | GET | 200 | 88.221.125.143:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5400 | SIHClient.exe | GET | 200 | 88.221.125.143:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5200 | cscript.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicCodSigPCA_2010-07-06.crl | unknown | — | — | whitelisted |
5200 | cscript.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
5888 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5732 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4872 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5732 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5732 | svchost.exe | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5732 | svchost.exe | 173.223.117.131:80 | www.microsoft.com | AKAMAI-AS | US | whitelisted |
5732 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5064 | SearchApp.exe | 2.16.110.171:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|