| download: | /DREV1H/FiveM-External-Cheat-KeyAuth-System/main/Loader.exe |
| Full analysis: | https://app.any.run/tasks/1345550c-71bd-478e-9aa0-f383a53299a1 |
| Verdict: | Malicious activity |
| Analysis date: | March 24, 2025, 13:12:49 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | F6E195D0B763235A06093D8013B1D5DC |
| SHA1: | 014EE46292E7A949A21AA29BA11318E099EC1D50 |
| SHA256: | 03D95D9AE7B1908F95FEC4C2932A36C9E662530CC09B91C870886DDA3DEEAB9B |
| SSDEEP: | 768:KqeJWZdFE2ECEL8JRLg23zX/PLXos9punqfaSYxnoXbOfC11kFp5e2h:Rg2ECELcLBzXbXos9puBfabO/FpH |
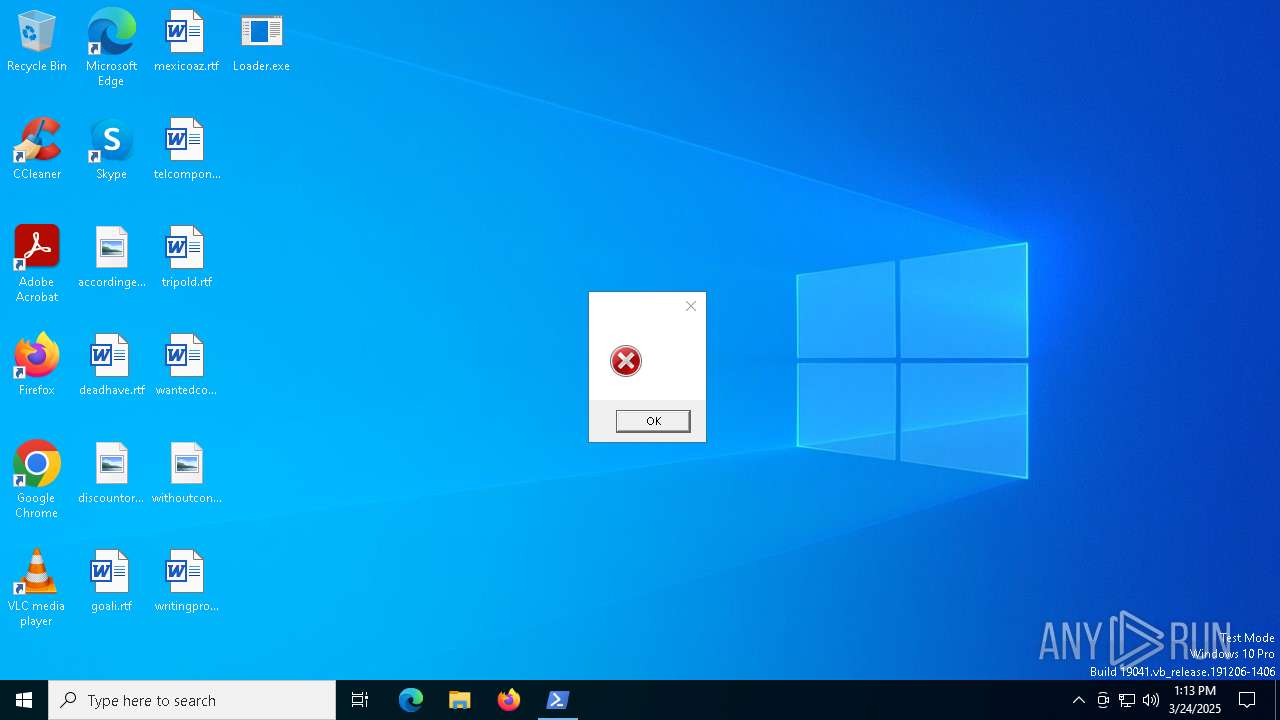
MALICIOUS
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 7568)
Script downloads file (POWERSHELL)
- powershell.exe (PID: 7568)
SUSPICIOUS
Base64-obfuscated command line is found
- Loader.exe (PID: 7360)
Starts POWERSHELL.EXE for commands execution
- Loader.exe (PID: 7360)
- powershell.exe (PID: 7568)
Reads security settings of Internet Explorer
- Loader.exe (PID: 7360)
BASE64 encoded PowerShell command has been detected
- Loader.exe (PID: 7360)
Executable content was dropped or overwritten
- powershell.exe (PID: 7568)
Executes application which crashes
- asprioig.ppf0.exe (PID: 644)
Application launched itself
- powershell.exe (PID: 7568)
INFO
Found Base64 encoded reflection usage via PowerShell (YARA)
- Loader.exe (PID: 7360)
Checks supported languages
- Loader.exe (PID: 7360)
- asprioig.ppf0.exe (PID: 644)
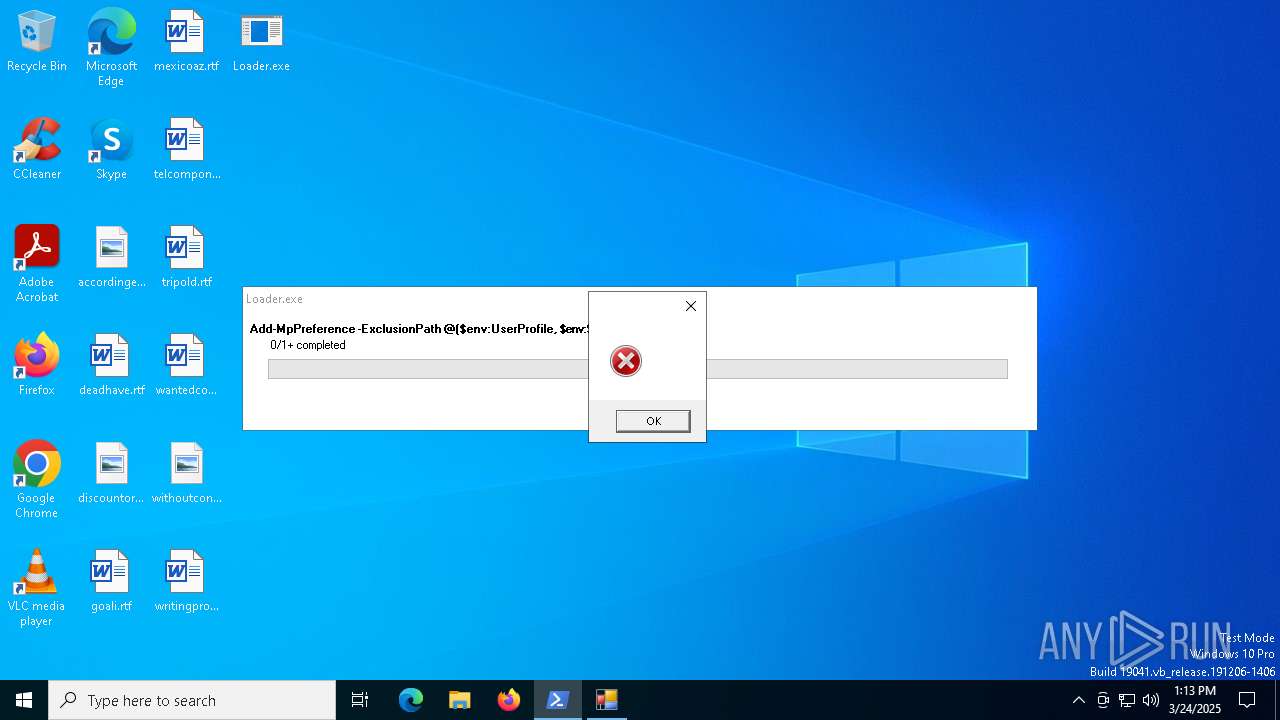
Found Base64 encoded access to Windows Defender via PowerShell (YARA)
- Loader.exe (PID: 7360)
Reads Environment values
- Loader.exe (PID: 7360)
Reads the machine GUID from the registry
- Loader.exe (PID: 7360)
Reads the computer name
- Loader.exe (PID: 7360)
Create files in a temporary directory
- Loader.exe (PID: 7360)
- powershell.exe (PID: 7980)
Checks proxy server information
- powershell.exe (PID: 7568)
Gets data length (POWERSHELL)
- powershell.exe (PID: 7568)
The executable file from the user directory is run by the Powershell process
- asprioig.ppf0.exe (PID: 644)
Creates files or folders in the user directory
- WerFault.exe (PID: 4628)
Reads the software policy settings
- slui.exe (PID: 7772)
- slui.exe (PID: 5400)
- powershell.exe (PID: 7980)
Found Base64 encoded file access via PowerShell (YARA)
- Loader.exe (PID: 7360)
Disables trace logs
- powershell.exe (PID: 7568)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7568)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 7568)
Reads security settings of Internet Explorer
- powershell.exe (PID: 7980)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (55.8) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (21) |
| .scr | | | Windows screen saver (9.9) |
| .dll | | | Win32 Dynamic Link Library (generic) (5) |
| .exe | | | Win32 Executable (generic) (3.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:03:20 14:43:11+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 33792 |
| InitializedDataSize: | 2048 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xa36e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | script.exe |
| LegalCopyright: | |
| OriginalFileName: | script.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
166
Monitored processes
16
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 644 | "C:\Users\admin\AppData\Roaming\asprioig.ppf0.exe" | C:\Users\admin\AppData\Roaming\asprioig.ppf0.exe | powershell.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226505 Modules
| |||||||||||||||
| 680 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | asprioig.ppf0.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1812 | "C:\WINDOWS\system32\UCPDMgr.exe" | C:\Windows\System32\UCPDMgr.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: User Choice Protection Manager Exit code: 0 Version: 1.0.0.414301 Modules
| |||||||||||||||
| 3192 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | — | asprioig.ppf0.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MSBuild.exe Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 4628 | C:\WINDOWS\system32\WerFault.exe -u -p 644 -s 260 | C:\Windows\System32\WerFault.exe | — | asprioig.ppf0.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5400 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5984 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | UCPDMgr.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6736 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | UCPDMgr.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7360 | "C:\Users\admin\Desktop\Loader.exe" | C:\Users\admin\Desktop\Loader.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Version: 0.0.0.0 Modules
| |||||||||||||||
| 7404 | "C:\WINDOWS\system32\UCPDMgr.exe" | C:\Windows\System32\UCPDMgr.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: User Choice Protection Manager Exit code: 0 Version: 1.0.0.414301 Modules
| |||||||||||||||
Total events
14 475
Read events
14 475
Write events
0
Delete events
0
Modification events
Executable files
1
Suspicious files
4
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4628 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_asprioig.ppf0.ex_7117fc3876dfaf3bce43a92445f49cda57e49da_fad6c99d_febac685-d495-4e3a-9b5d-03dbb38d1074\Report.wer | — | |
MD5:— | SHA256:— | |||
| 7360 | Loader.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_aujxczbe.y2g.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7360 | Loader.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_bpb0pu3p.vdn.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7568 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_wgm2hhj0.j4w.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7568 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_1rbtznbh.xmb.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7980 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_iwo24pc2.wa4.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7568 | powershell.exe | C:\Users\admin\AppData\Roaming\asprioig.ppf0.exe | executable | |
MD5:96F6AEBD19DDD7C4E9EF7DB2F1261E29 | SHA256:D6BF681BC2F404B590BDC8E720D2AA7E34AE11EDF82CE9F89B4C986AC3D9C4A2 | |||
| 7980 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_zkzniy54.ixu.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7568 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:2FE70C8557DF52131D80064E881A0E21 | SHA256:3C860966001B512FF5B3FD8617FC594056B9302A238632E904422CF679C30DAB | |||
| 4628 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER682F.tmp.xml | xml | |
MD5:4CD9EA9B42B7A4953C9730FF434F6168 | SHA256:97B2BA6FF1811368E63A64EB40BCCB2F2782CAC0F3B43E72E8749F579E418CAB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
50
DNS requests
29
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2104 | svchost.exe | GET | 200 | 2.16.164.32:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7428 | SIHClient.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7428 | SIHClient.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4988 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
2516 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
2516 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 2.16.164.32:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
6544 | svchost.exe | 20.190.159.129:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 20.190.159.129:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
3216 | svchost.exe | 20.197.71.89:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | SG | whitelisted |
5496 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5544 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4988 | backgroundTaskHost.exe | 20.223.35.26:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |