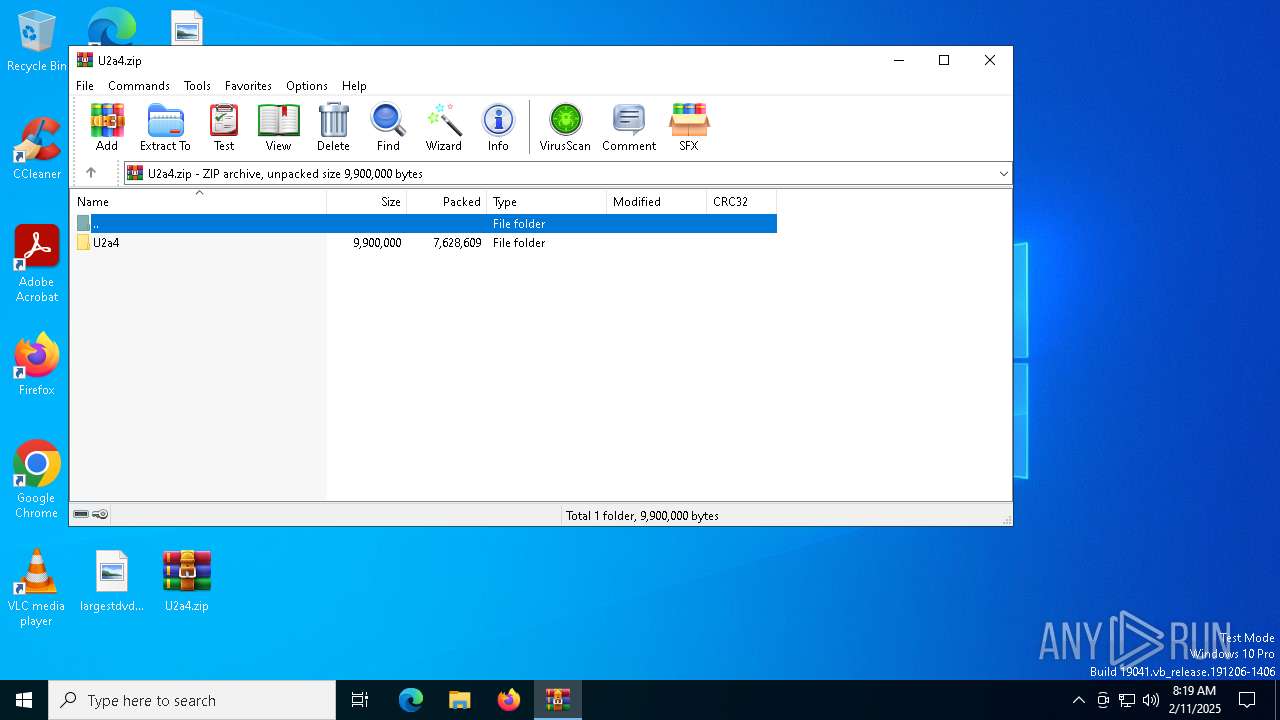
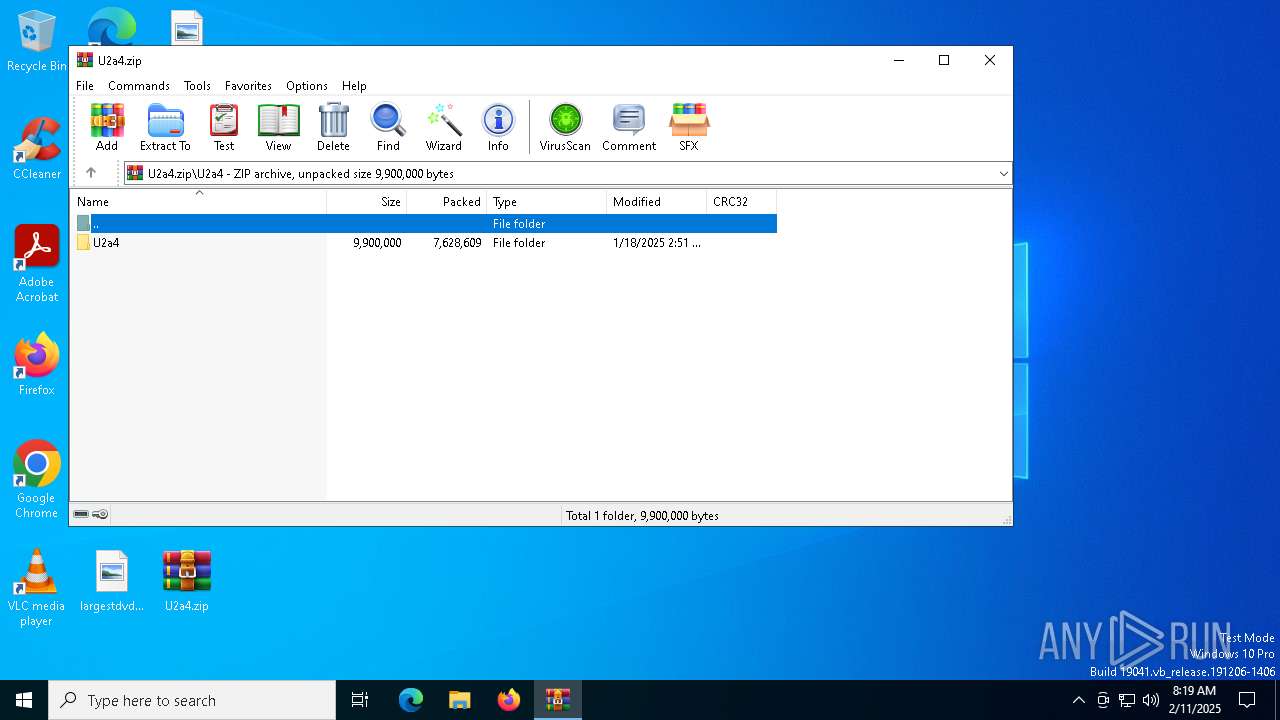
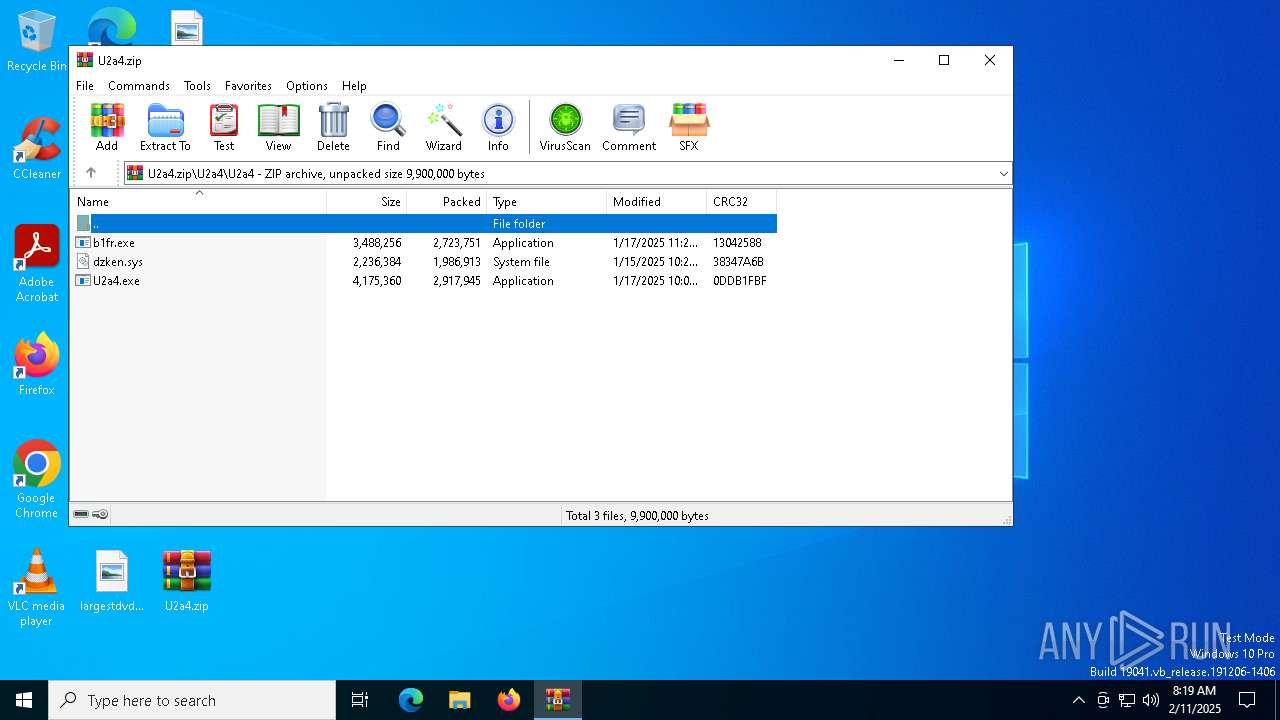
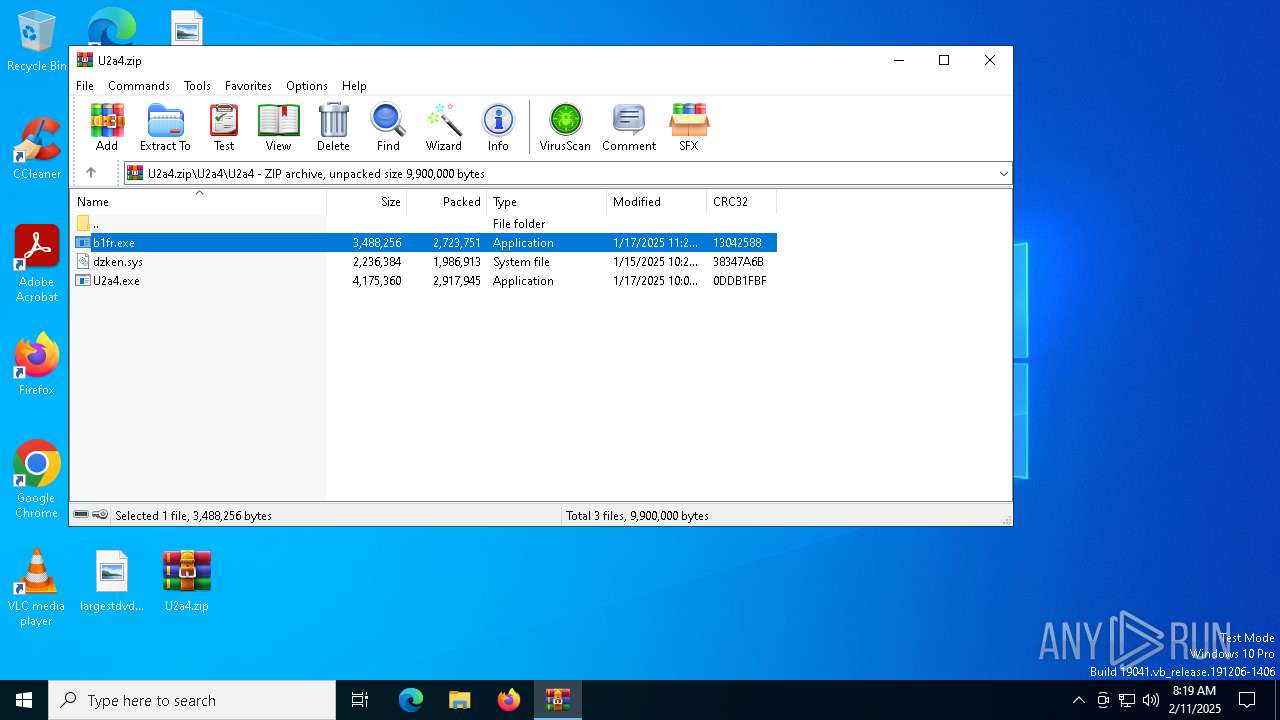
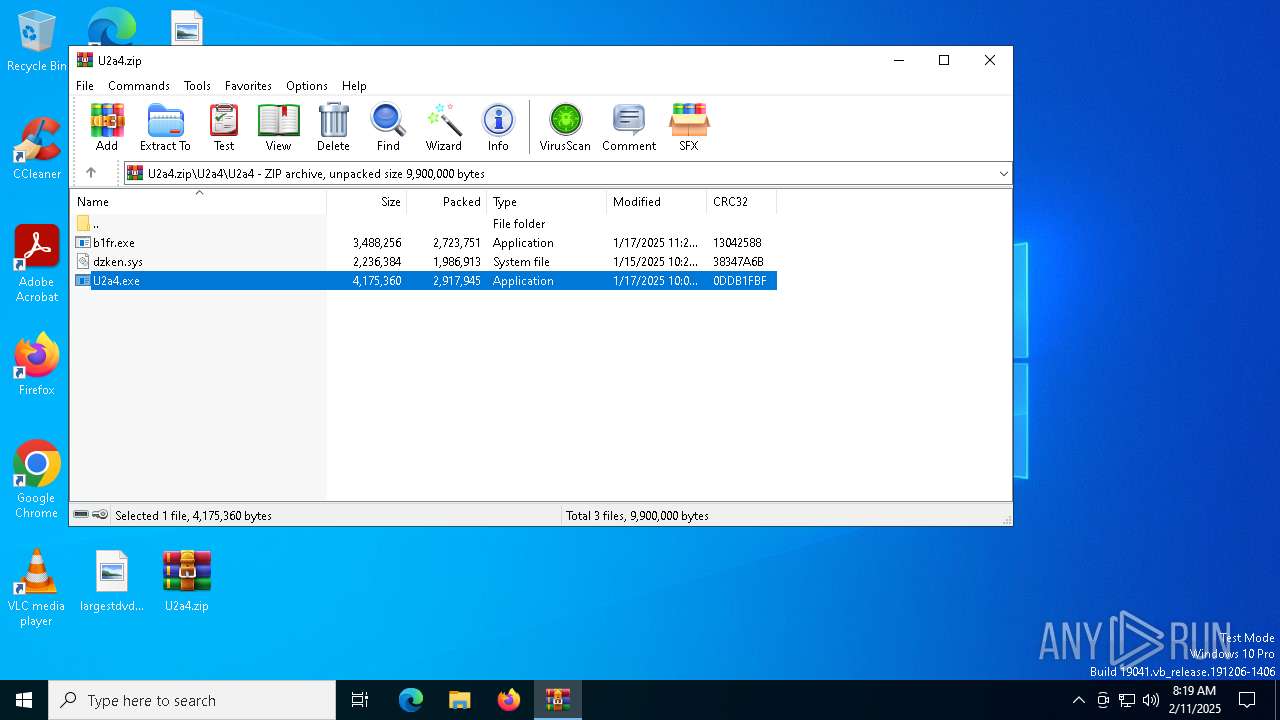
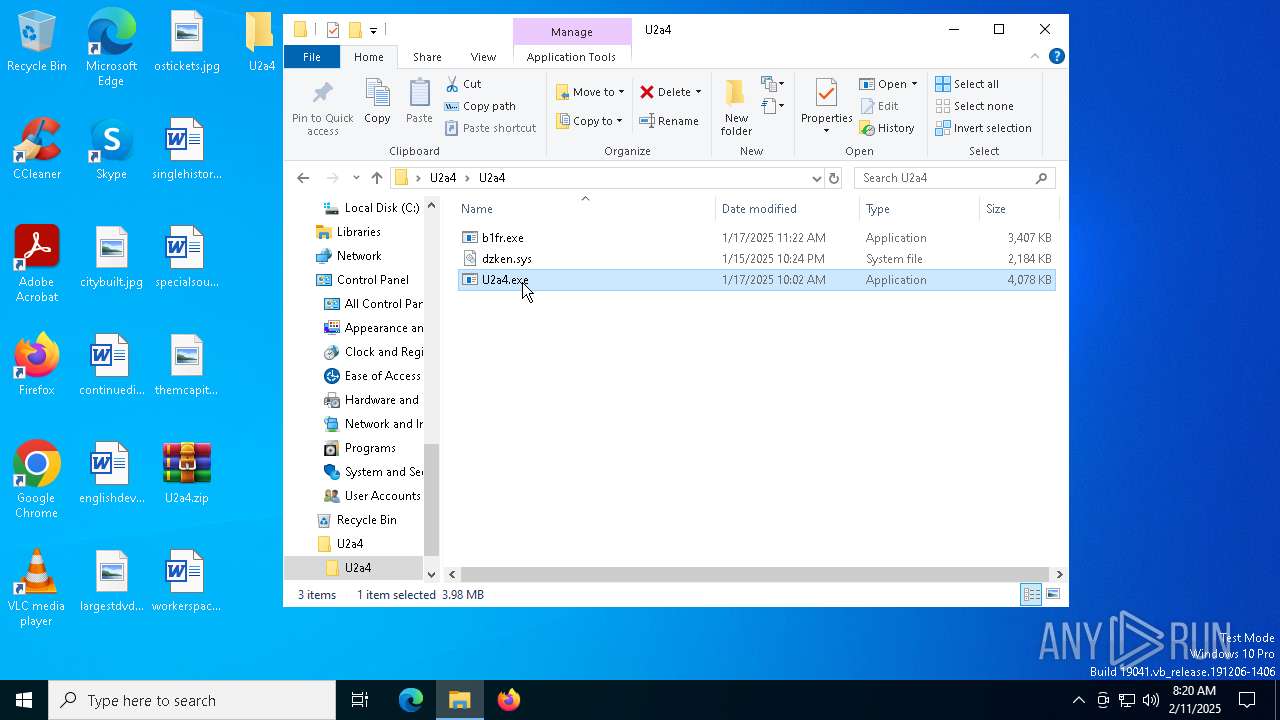
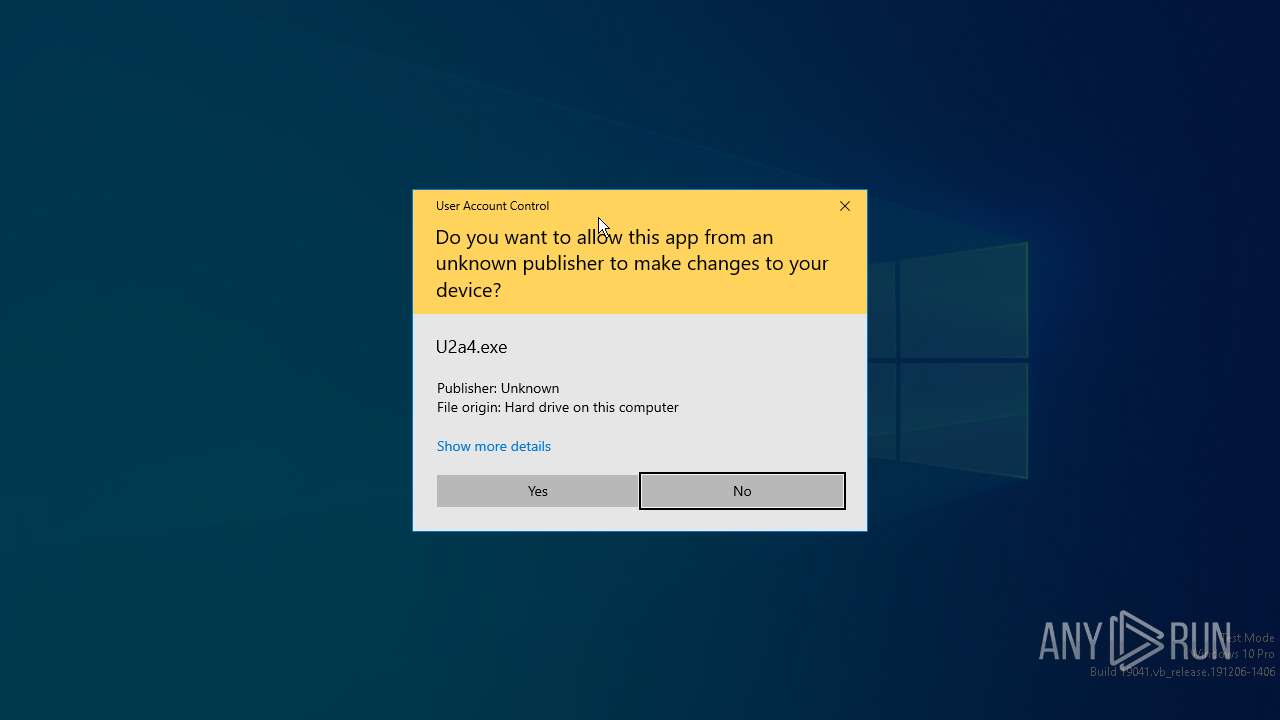
| File name: | U2a4.zip |
| Full analysis: | https://app.any.run/tasks/c4c8cc82-24b4-4fd7-be5f-9e7fc57bdaec |
| Verdict: | Malicious activity |
| Analysis date: | February 11, 2025, 08:18:57 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | E4CE824232CDBCE68C3F841E216DEBE1 |
| SHA1: | 26CF0263B912E625CD1CA8F58BC6511B33F0D98D |
| SHA256: | 03B3728B6C930CBFA54F9D33AABBF02D3F08DE68F69DDA0A27EE483461D0712F |
| SSDEEP: | 98304:TJEkYndxAoI3BlZt+MYlDKLBID+kJOxpTJZfvrlmBaLQ45+8LwpEMWTGzAv9r/xT:rPybAfXJu2K+LiX+ |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6332)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6332)
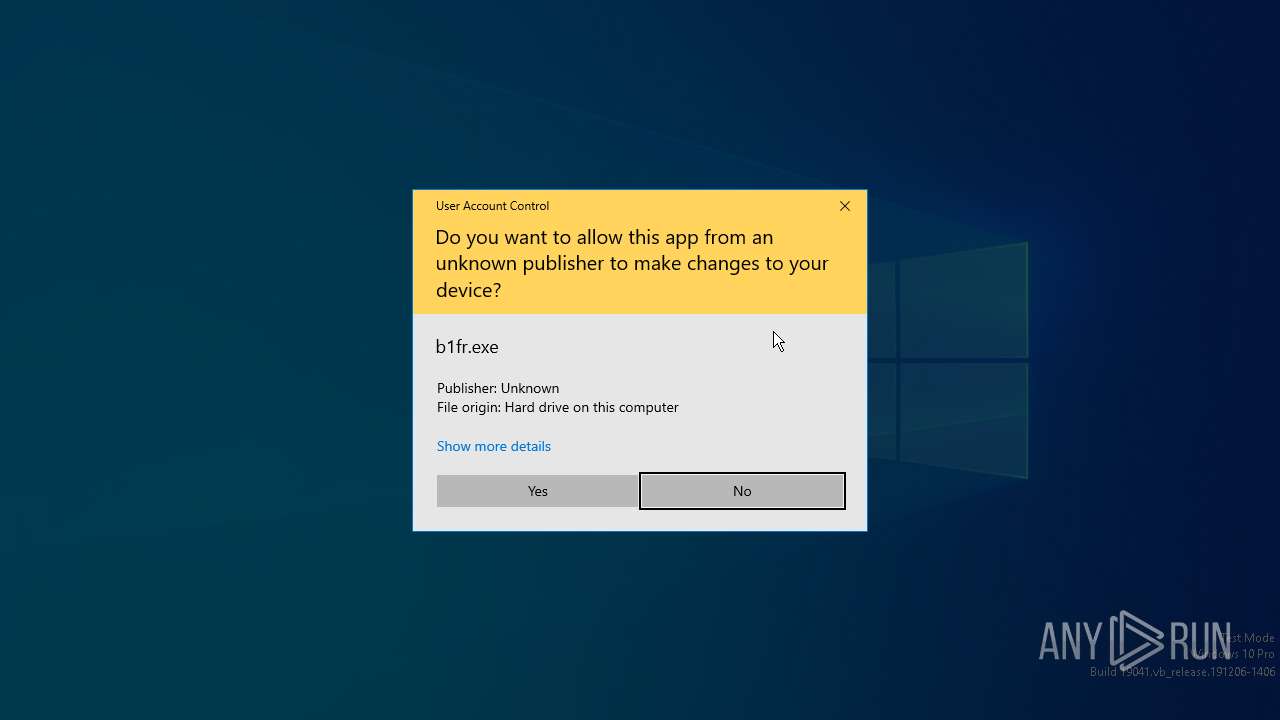
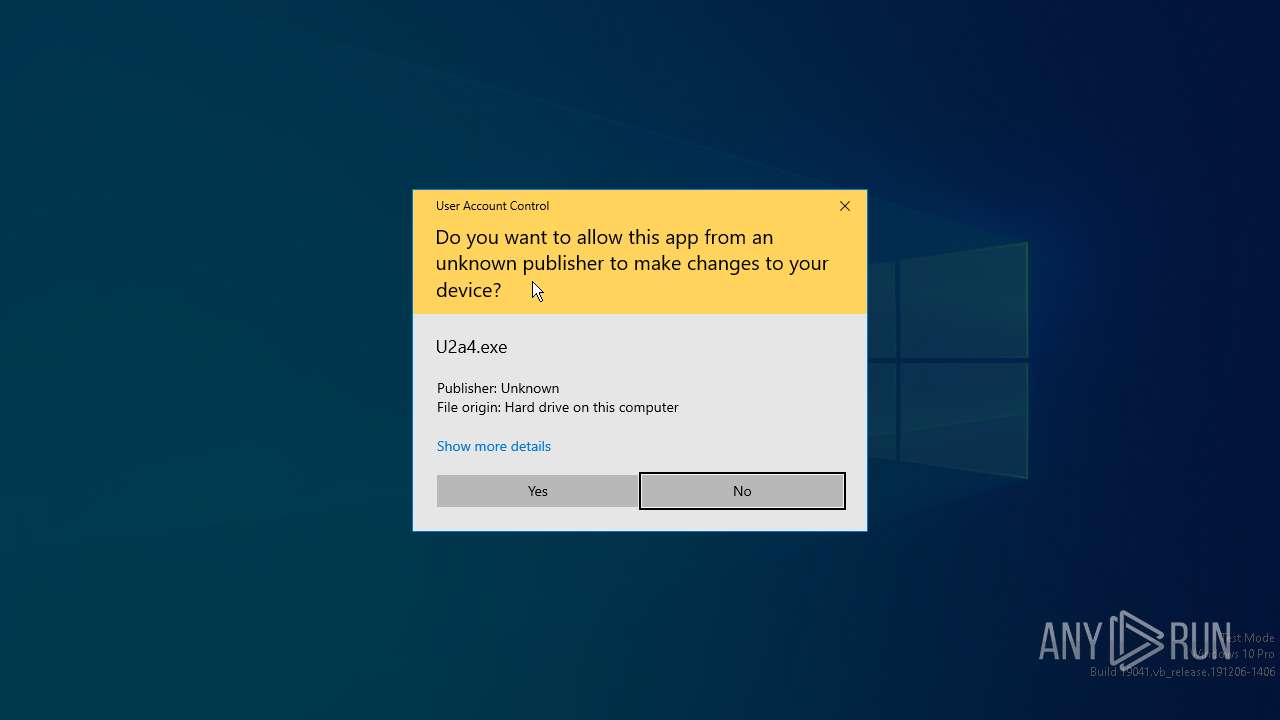
- b1fr.exe (PID: 6952)
- U2a4.exe (PID: 7056)
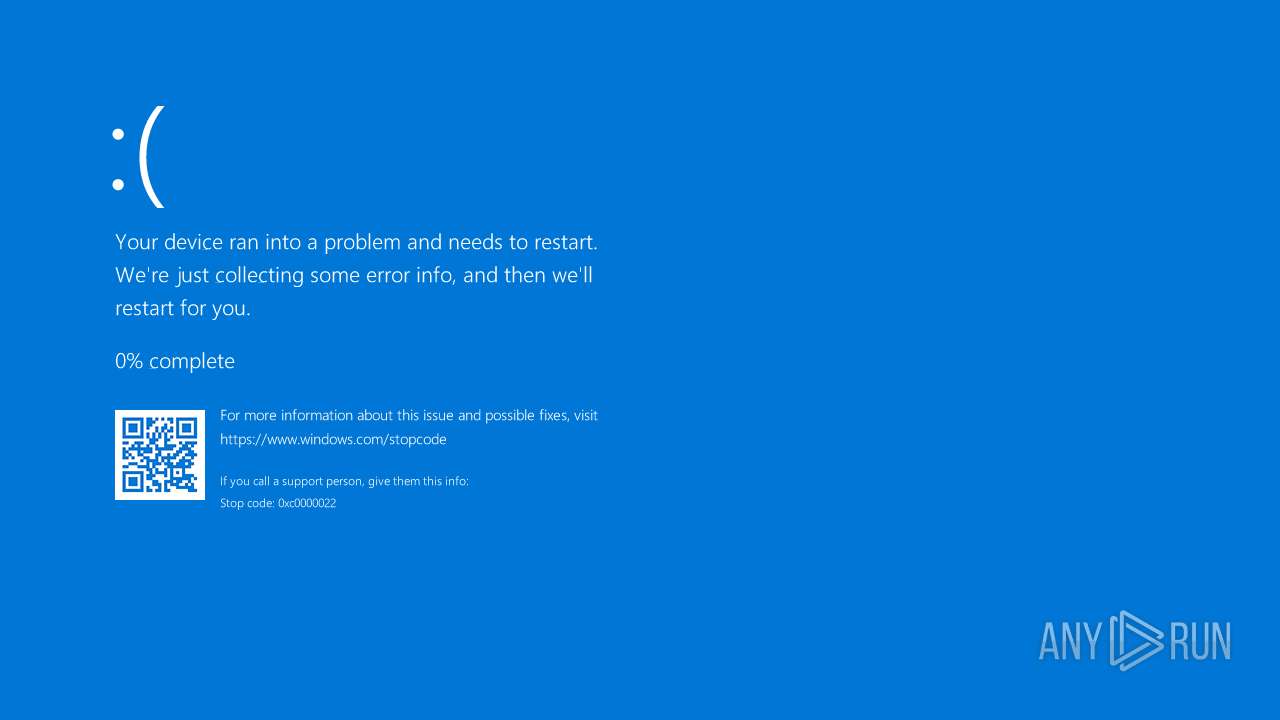
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 6332)
Application launched itself
- b1fr.exe (PID: 6932)
- b1fr.exe (PID: 6952)
- U2a4.exe (PID: 7056)
- b1fr.exe (PID: 7044)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6332)
The sample compiled with english language support
- WinRAR.exe (PID: 6332)
Checks supported languages
- b1fr.exe (PID: 6932)
- b1fr.exe (PID: 6952)
- b1fr.exe (PID: 7044)
- U2a4.exe (PID: 7056)
- U2a4.exe (PID: 6156)
- b1fr.exe (PID: 6276)
Reads the computer name
- b1fr.exe (PID: 6952)
- U2a4.exe (PID: 7056)
- U2a4.exe (PID: 6156)
Process checks computer location settings
- b1fr.exe (PID: 6952)
- U2a4.exe (PID: 7056)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:01:18 02:51:58 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | U2a4/U2a4/ |
Total processes
133
Monitored processes
7
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 6156 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6332.26878\U2a4\U2a4\U2a4.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6332.26878\U2a4\U2a4\U2a4.exe | U2a4.exe | ||||||||||||
User: admin Company: Stormcoast Fortress Integrity Level: HIGH Description: Scmdraft 2 Version: 0, 8, 0, 0 Modules
| |||||||||||||||
| 6276 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6332.26614\U2a4\U2a4\b1fr.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6332.26614\U2a4\U2a4\b1fr.exe | — | b1fr.exe | |||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 6332 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\U2a4.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6932 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6332.26614\U2a4\U2a4\b1fr.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6332.26614\U2a4\U2a4\b1fr.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 6952 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6332.26614\U2a4\U2a4\b1fr.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6332.26614\U2a4\U2a4\b1fr.exe | — | b1fr.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 7044 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6332.26614\U2a4\U2a4\b1fr.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6332.26614\U2a4\U2a4\b1fr.exe | b1fr.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 7056 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6332.26878\U2a4\U2a4\U2a4.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6332.26878\U2a4\U2a4\U2a4.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Stormcoast Fortress Integrity Level: MEDIUM Description: Scmdraft 2 Exit code: 1 Version: 0, 8, 0, 0 Modules
| |||||||||||||||
Total events
2 278
Read events
2 270
Write events
8
Delete events
0
Modification events
| (PID) Process: | (6332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\U2a4.zip | |||
| (PID) Process: | (6332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
6
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6332 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6332.26614\U2a4\U2a4\b1fr.exe | executable | |
MD5:085130C6109DF702E5B72B7752F9B52E | SHA256:DDF23DB6881E42E65440C26A208C9175AD705C708F0A5D8426A2636BAD79777C | |||
| 6332 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6332.26614\U2a4\U2a4\U2a4.exe | executable | |
MD5:ED87E66398DEA00FAD8DB930478D0A4D | SHA256:2E7BEF464ADA3FA6F7B86D385D46A7B6AAB14CF61713516ABBA32ABDE1F54579 | |||
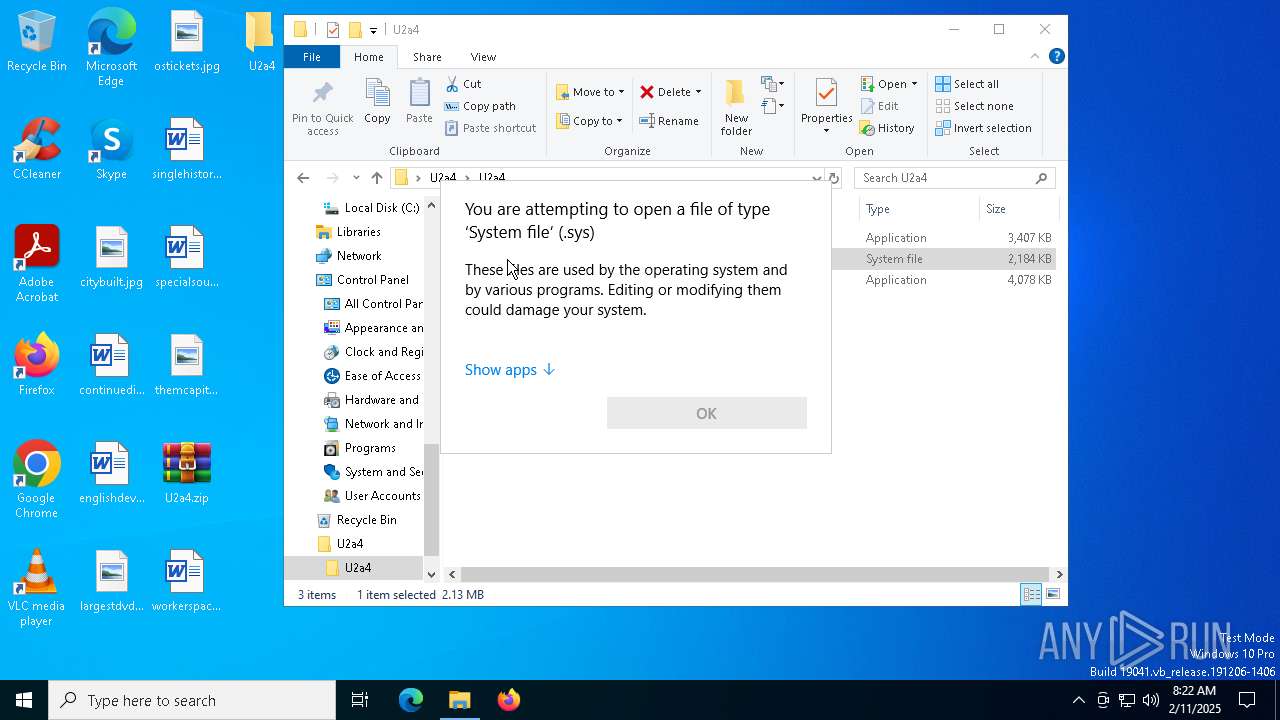
| 6332 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6332.26878\U2a4\U2a4\dzken.sys | executable | |
MD5:84414D0F2AB10D509580DD84D24E6708 | SHA256:B2FF9EF50AE037BB003D7157EA8DA008A48F715A78C644B5F027B070BF5EB049 | |||
| 6332 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6332.26614\U2a4\U2a4\dzken.sys | executable | |
MD5:84414D0F2AB10D509580DD84D24E6708 | SHA256:B2FF9EF50AE037BB003D7157EA8DA008A48F715A78C644B5F027B070BF5EB049 | |||
| 6332 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6332.26878\U2a4\U2a4\U2a4.exe | executable | |
MD5:ED87E66398DEA00FAD8DB930478D0A4D | SHA256:2E7BEF464ADA3FA6F7B86D385D46A7B6AAB14CF61713516ABBA32ABDE1F54579 | |||
| 6332 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6332.26878\U2a4\U2a4\b1fr.exe | executable | |
MD5:085130C6109DF702E5B72B7752F9B52E | SHA256:DDF23DB6881E42E65440C26A208C9175AD705C708F0A5D8426A2636BAD79777C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
24
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
904 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 2.23.227.215:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
— | — | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
1176 | svchost.exe | 20.190.160.64:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1076 | svchost.exe | 2.19.106.8:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
1596 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 224.0.0.251:5353 | — | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |