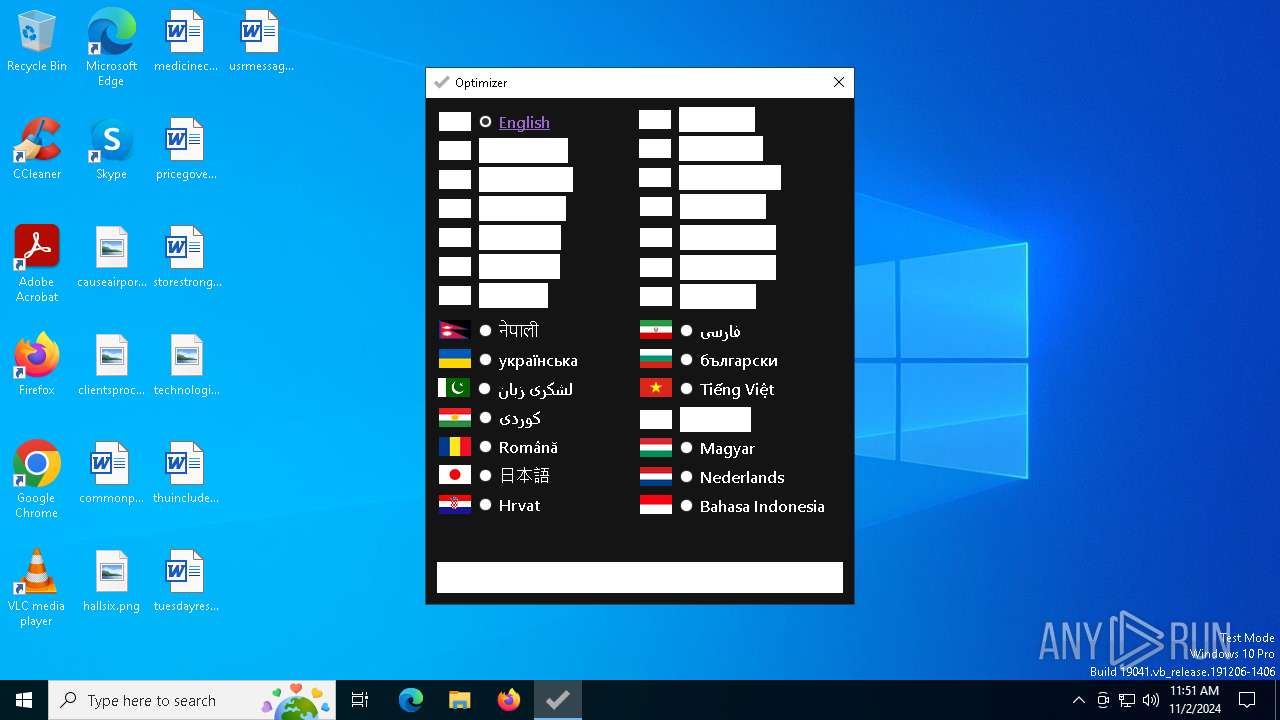
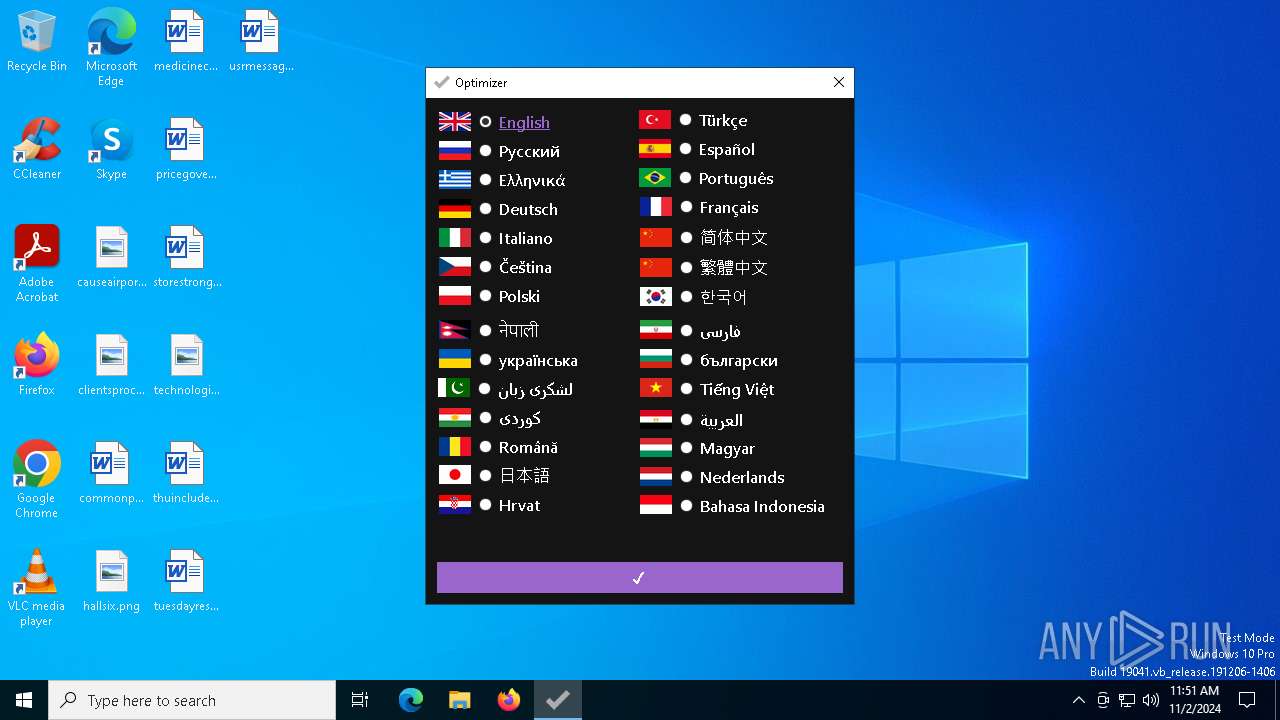
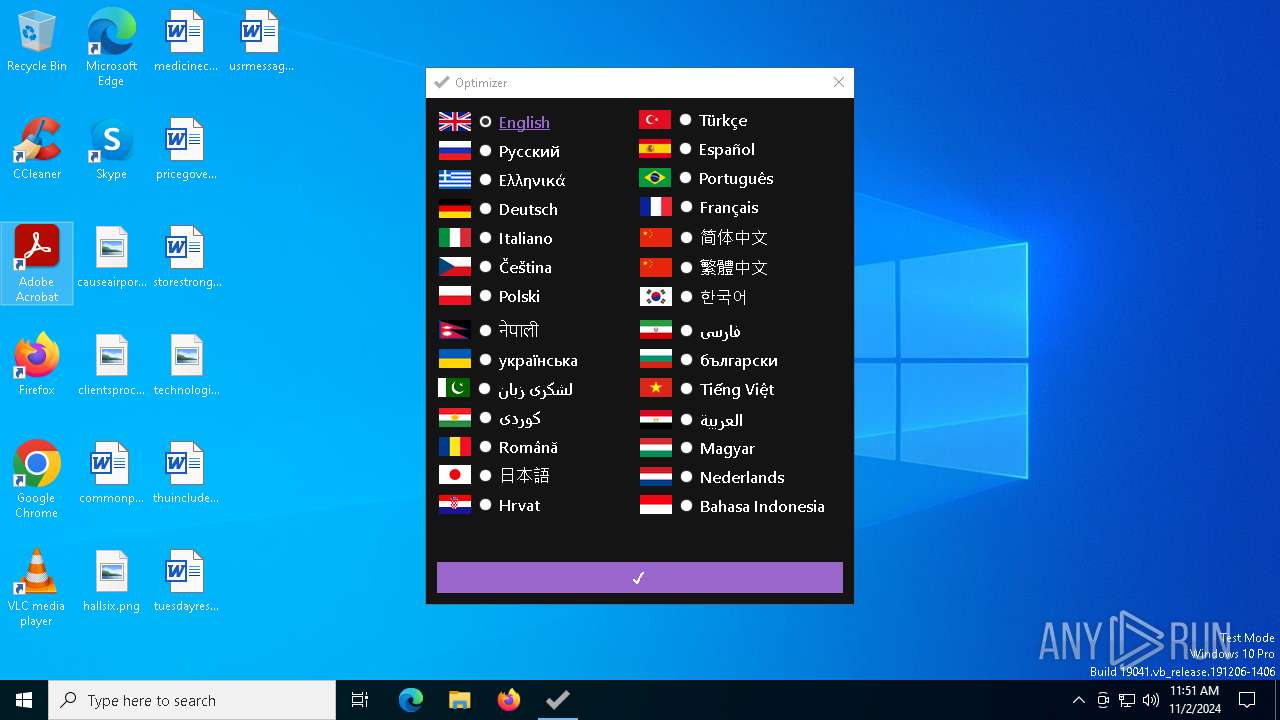
| File name: | Optimizer-16.7.exe |
| Full analysis: | https://app.any.run/tasks/0e3c645a-9103-4534-a23d-670a03843df8 |
| Verdict: | Malicious activity |
| Analysis date: | November 02, 2024, 11:51:08 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 7F57207F221DB2B08E27D64BC9121B28 |
| SHA1: | 3BFC4B12A533EE1CE62E5D348027D4AC90AB49DB |
| SHA256: | 03A234060541B686AC4265754AFF43DF9325C21383F90E17F831E67965D717F8 |
| SSDEEP: | 49152:SVAvLOg3LmfS1MW/EC8mNMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMX:Q2NMMMMMMMMMMMMMMMMMMMMMMMMMMMMx |
MALICIOUS
Starts NET.EXE for service management
- cmd.exe (PID: 6868)
- net.exe (PID: 1768)
SUSPICIOUS
Reads security settings of Internet Explorer
- Optimizer-16.7.exe (PID: 5944)
Reads the date of Windows installation
- Optimizer-16.7.exe (PID: 5944)
Application launched itself
- Optimizer-16.7.exe (PID: 5944)
Starts CMD.EXE for commands execution
- Optimizer-16.7.exe (PID: 5940)
Modifies existing scheduled task
- schtasks.exe (PID: 8056)
- schtasks.exe (PID: 8104)
- schtasks.exe (PID: 8152)
- schtasks.exe (PID: 7212)
- schtasks.exe (PID: 6356)
- schtasks.exe (PID: 4816)
- schtasks.exe (PID: 7644)
- schtasks.exe (PID: 7228)
- schtasks.exe (PID: 7516)
Executing commands from a ".bat" file
- Optimizer-16.7.exe (PID: 5940)
Starts SC.EXE for service management
- cmd.exe (PID: 7768)
- cmd.exe (PID: 7732)
- cmd.exe (PID: 7804)
Uses REG/REGEDIT.EXE to modify registry
- Optimizer-16.7.exe (PID: 5940)
- cmd.exe (PID: 7976)
INFO
Checks supported languages
- Optimizer-16.7.exe (PID: 5944)
- Optimizer-16.7.exe (PID: 5940)
Reads the computer name
- Optimizer-16.7.exe (PID: 5944)
- Optimizer-16.7.exe (PID: 5940)
Process checks computer location settings
- Optimizer-16.7.exe (PID: 5944)
The process uses the downloaded file
- Optimizer-16.7.exe (PID: 5944)
Reads the machine GUID from the registry
- Optimizer-16.7.exe (PID: 5944)
- Optimizer-16.7.exe (PID: 5940)
Reads Environment values
- Optimizer-16.7.exe (PID: 5940)
Reads product name
- Optimizer-16.7.exe (PID: 5940)
Creates files in the program directory
- Optimizer-16.7.exe (PID: 5940)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (56.7) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (21.3) |
| .scr | | | Windows screen saver (10.1) |
| .dll | | | Win32 Dynamic Link Library (generic) (5) |
| .exe | | | Win32 Executable (generic) (3.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:08:18 13:30:29+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 2538496 |
| InitializedDataSize: | 34816 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x26dae2 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | The Finest Windows Optimizer |
| CompanyName: | deadmoon © ∞ |
| FileDescription: | Optimizer |
| FileVersion: | 0.0.0.0 |
| InternalName: | Optimizer.exe |
| LegalCopyright: | deadmoon © ∞ |
| LegalTrademarks: | - |
| OriginalFileName: | Optimizer.exe |
| ProductName: | Optimizer |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
188
Monitored processes
59
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 864 | reg add "HKCU\SOFTWARE\Microsoft\Office\15.0\Common\Feedback" /v "Enabled" /t REG_DWORD /d 0 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1112 | reg add "HKCU\SOFTWARE\Microsoft\Office\Common\ClientTelemetry" /v "VerboseLogging" /t REG_DWORD /d 0 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1568 | reg add "HKCU\SOFTWARE\Microsoft\Office\16.0\Common\ClientTelemetry" /v "DisableTelemetry" /t REG_DWORD /d 1 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1588 | "C:\Windows\System32\cmd.exe" /C schtasks.exe /change /tn NvTmRep_{B2FE1952-0186-46C3-BAEC-A80AA35AC5B8} /disable | C:\Windows\System32\cmd.exe | — | Optimizer-16.7.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1768 | net.exe stop NvTelemetryContainer | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1952 | reg add "HKCU\SOFTWARE\Microsoft\Office\16.0\Common\Feedback" /v "Enabled" /t REG_DWORD /d 0 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2132 | sc.exe stop NvTelemetryContainer | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 1060 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2236 | reg add "HKCU\SOFTWARE\Policies\Microsoft\Office\15.0\OSM" /v "EnableLogging" /t REG_DWORD /d 0 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3832 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3952 | reg add "HKCU\SOFTWARE\Microsoft\Office\16.0\Common\ClientTelemetry" /v "VerboseLogging" /t REG_DWORD /d 0 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
10 140
Read events
10 051
Write events
89
Delete events
0
Modification events
| (PID) Process: | (5940) Optimizer-16.7.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Optimizer-16_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (5940) Optimizer-16.7.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Optimizer-16_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (5940) Optimizer-16.7.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Optimizer-16_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (5940) Optimizer-16.7.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Optimizer-16_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (5940) Optimizer-16.7.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Optimizer-16_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (5940) Optimizer-16.7.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Optimizer-16_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (5940) Optimizer-16.7.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Optimizer-16_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (5940) Optimizer-16.7.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Optimizer-16_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (5940) Optimizer-16.7.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Optimizer-16_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (5940) Optimizer-16.7.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Optimizer-16_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
0
Suspicious files
1
Text files
23
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5940 | Optimizer-16.7.exe | C:\ProgramData\Optimizer\ReadyMadeMenus\SystemShortcuts.reg | text | |
MD5:3B894F19CDEF342C0704E7774BB20AFA | SHA256:02C4C6610F2BAA98CEF5005A2155A76DD5D52B9B2C8BB49CB31E1A1EF5B74B9A | |||
| 5940 | Optimizer-16.7.exe | C:\ProgramData\Optimizer\ReadyMadeMenus\SystemTools.reg | text | |
MD5:13B285768D5140BC337089840E1A9A3B | SHA256:0DC2F4E580BF09632E0961F857556D5F9378A9EBDE76F4D89F302E02DD829C21 | |||
| 5940 | Optimizer-16.7.exe | C:\ProgramData\Optimizer\Required\DisableTelemetryTasks.bat | text | |
MD5:CB03C3144AAFF8FB1C3497C403C2B60F | SHA256:ABD9B7C86E9186C4AF174C2A630629588EC89A716D3FF04D357D2610E490C8D3 | |||
| 5940 | Optimizer-16.7.exe | C:\ProgramData\Optimizer\Required\EnableOfficeTelemetryTasks.bat | text | |
MD5:8E83AAC7A144BB7460A3D7235442B802 | SHA256:275F9E1A0701F097C4CB9505D42E1EF3D5DD0AE9ABA2CBB399F7EBB23E3E8773 | |||
| 5940 | Optimizer-16.7.exe | C:\ProgramData\Optimizer\ReadyMadeMenus\RemoveTakeOwnership.reg | text | |
MD5:01AE3E08513E213ECF621F92B9F0B47C | SHA256:177FB8F30D10E50115500D1B2AF488A9D885FBA42C2FB22E6FBBEE337806AF19 | |||
| 5940 | Optimizer-16.7.exe | C:\ProgramData\Optimizer\ReadyMadeMenus\WindowsApps.reg | text | |
MD5:A1714039AB00D6275EF7EF2559346D71 | SHA256:21223E33A52A85EC5EA797457DDF8458A5040760BABC5E5367646C312D74D5D4 | |||
| 5940 | Optimizer-16.7.exe | C:\ProgramData\Optimizer\Required\DisableOfficeTelemetryTasks.bat | text | |
MD5:FED75B5CB9D9F4EC5EE22B8FD304CCF7 | SHA256:D884C0D04BA09B113D9439D2F8C0B7ED322111AE2E3ED802F6A95278FF8E0AC2 | |||
| 5940 | Optimizer-16.7.exe | C:\ProgramData\Optimizer\ReadyMadeMenus\InstallTakeOwnership.reg | text | |
MD5:29896F795D3E250540AE33EB84D0AF71 | SHA256:61FD9430AAC2D0813451326B5CAEB7F463442CEEC46A9D1D52ED34541768C931 | |||
| 5940 | Optimizer-16.7.exe | C:\ProgramData\Optimizer\Required\EnableXboxTasks.bat | text | |
MD5:FABECE235B2BEE26CAFD321A676F85F5 | SHA256:DDD6EDECA0D2ABFF7DD9FAB08CB8C736D60B37648E7DFC2E8158798D7DDDF7F7 | |||
| 5940 | Optimizer-16.7.exe | C:\ProgramData\Optimizer\Required\GPEditEnablerInHome.bat | text | |
MD5:3D4A492D32B47905461AD2AD3313B589 | SHA256:10A85A8F7E9B6E118ED1AD73BE6C15777F53E88542D301088A8D6CF81BFDCCAD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
38
DNS requests
20
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.32.185.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
3948 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3788 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
7692 | SIHClient.exe | GET | 200 | 95.101.197.132:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7692 | SIHClient.exe | GET | 200 | 95.101.197.132:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6944 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4360 | SearchApp.exe | 23.212.110.176:443 | www.bing.com | Akamai International B.V. | CZ | whitelisted |
1252 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 2.19.11.120:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
5488 | MoUsoCoreWorker.exe | 23.32.185.131:80 | www.microsoft.com | AKAMAI-AS | BR | whitelisted |
4020 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4360 | SearchApp.exe | 23.212.110.184:443 | www.bing.com | Akamai International B.V. | CZ | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2172 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |