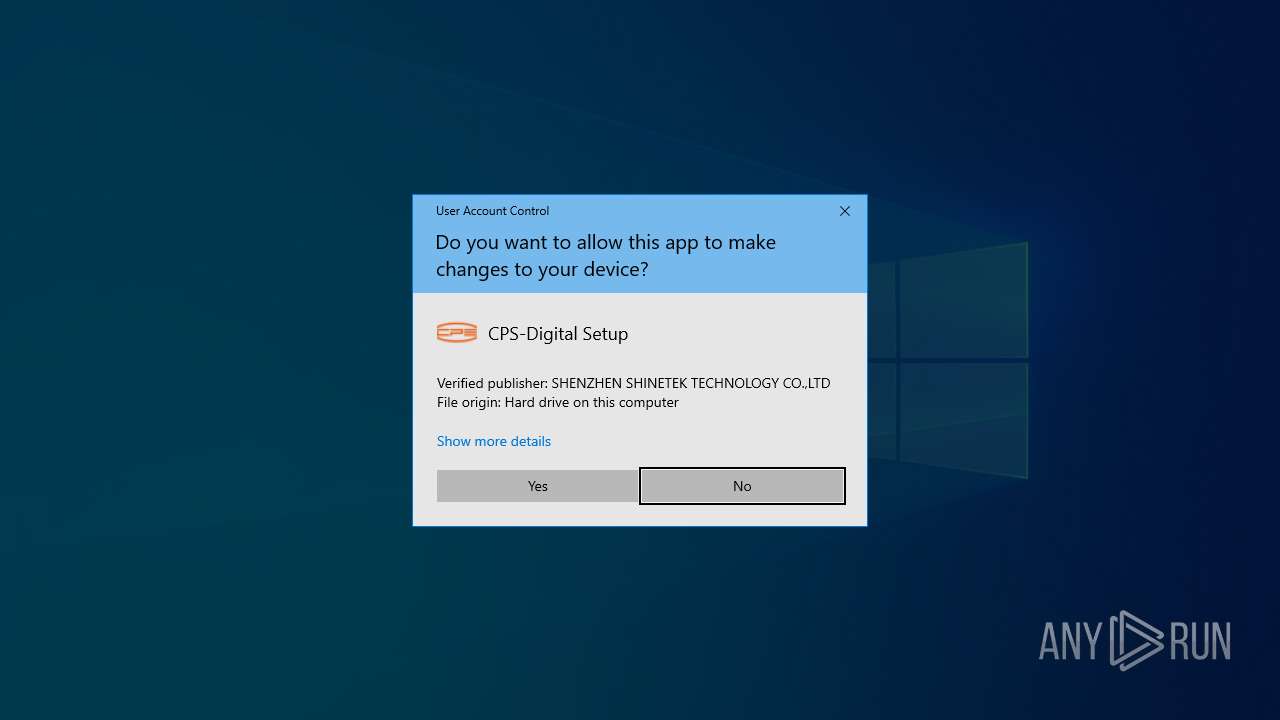
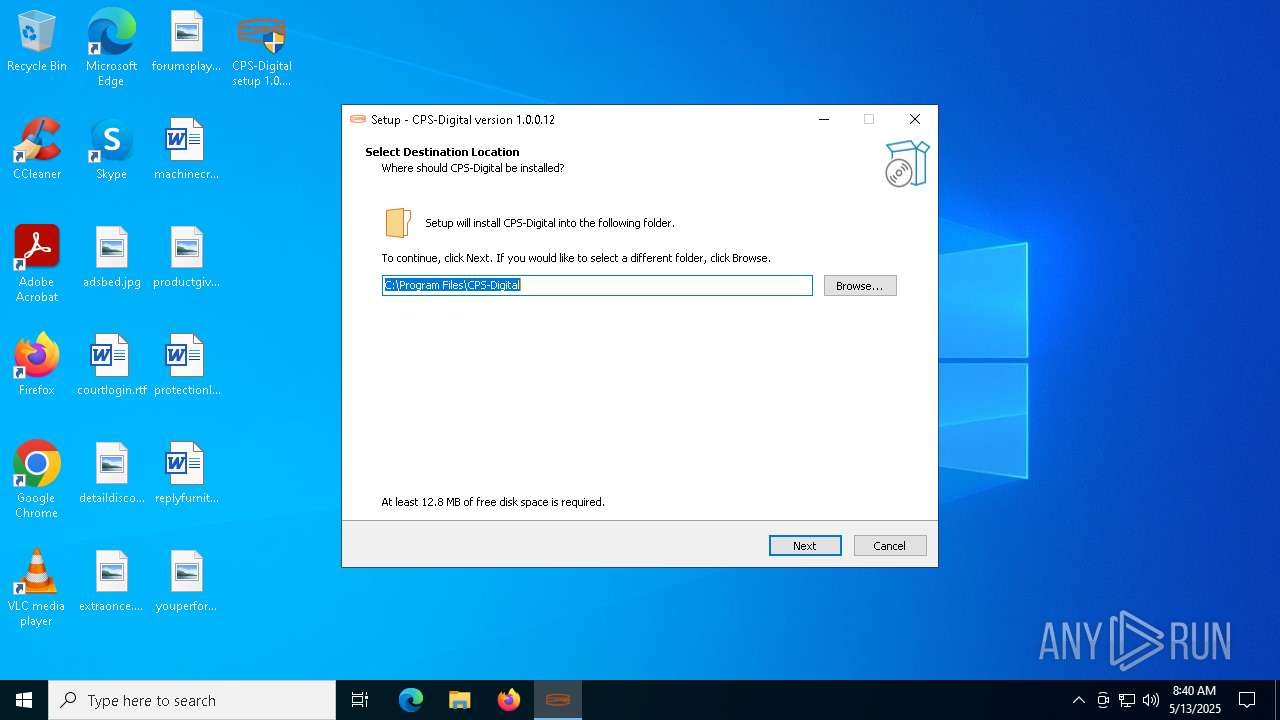
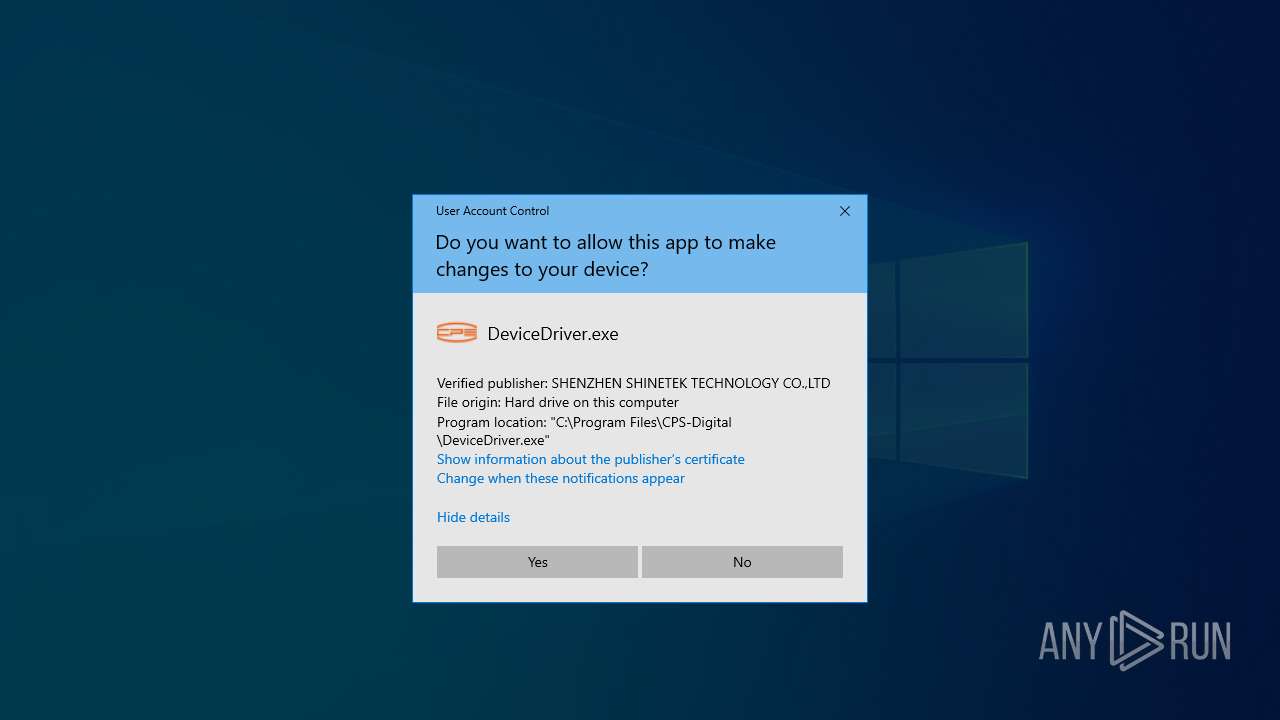
| File name: | CPS-Digital setup 1.0.0.12.exe |
| Full analysis: | https://app.any.run/tasks/ead695da-7ce6-47b6-a516-67766fb47652 |
| Verdict: | Malicious activity |
| Analysis date: | May 13, 2025, 08:40:05 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 11 sections |
| MD5: | BF07EB36FC88F6718239F496182BB573 |
| SHA1: | 7D588E0DBA7448EB331459770B5310CA233EFD1D |
| SHA256: | 039FADB22CD33BE780EE3F98A13E2AF952628FA5244BB1917631FC2D14D3B281 |
| SSDEEP: | 98304:Urq3BdwQCeC/CxdGf272JyJ7Yd8lkyQxqg85LpeGIrtB1ES1gWdJ3pCbD4jYV9j+:8l4CbL |
MALICIOUS
Vulnerable driver has been detected
- OpenHardwareMonitorServer.exe (PID: 7984)
SUSPICIOUS
Reads the Windows owner or organization settings
- CPS-Digital setup 1.0.0.12.tmp (PID: 7240)
Executable content was dropped or overwritten
- CPS-Digital setup 1.0.0.12.exe (PID: 7216)
- CPS-Digital setup 1.0.0.12.tmp (PID: 7240)
- OpenHardwareMonitorServer.exe (PID: 7984)
Reads security settings of Internet Explorer
- CPS-Digital setup 1.0.0.12.tmp (PID: 7240)
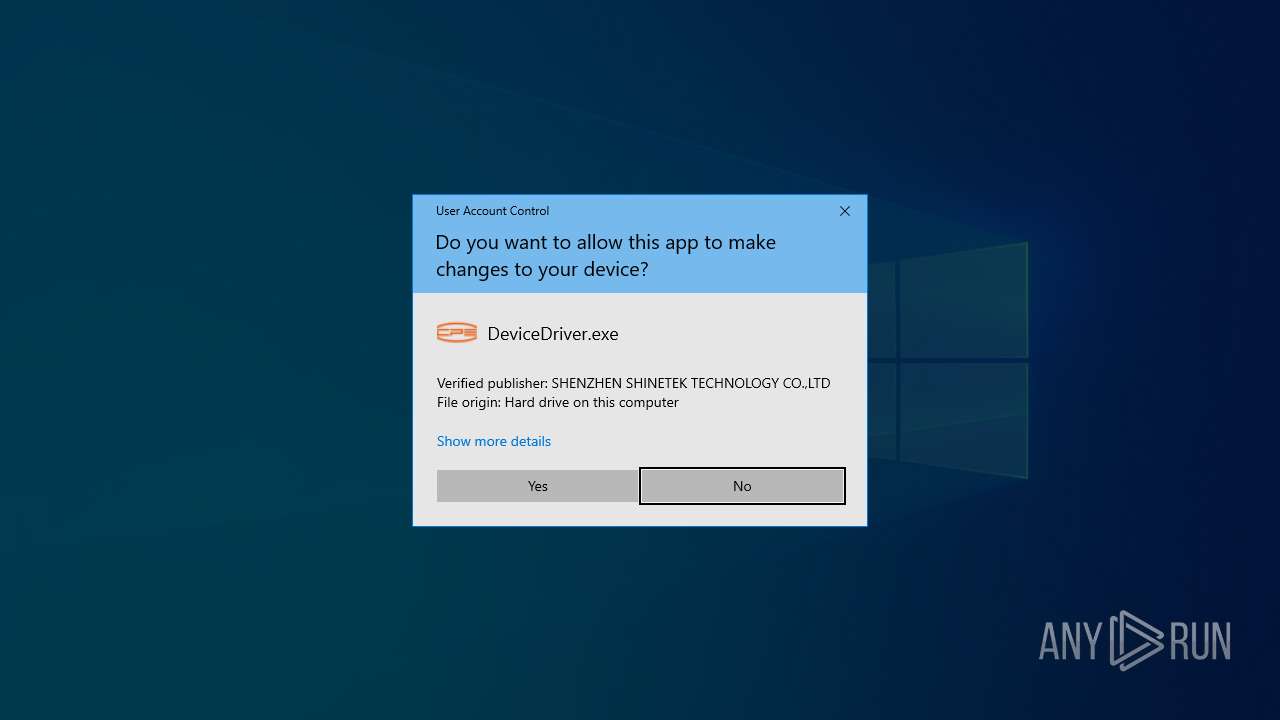
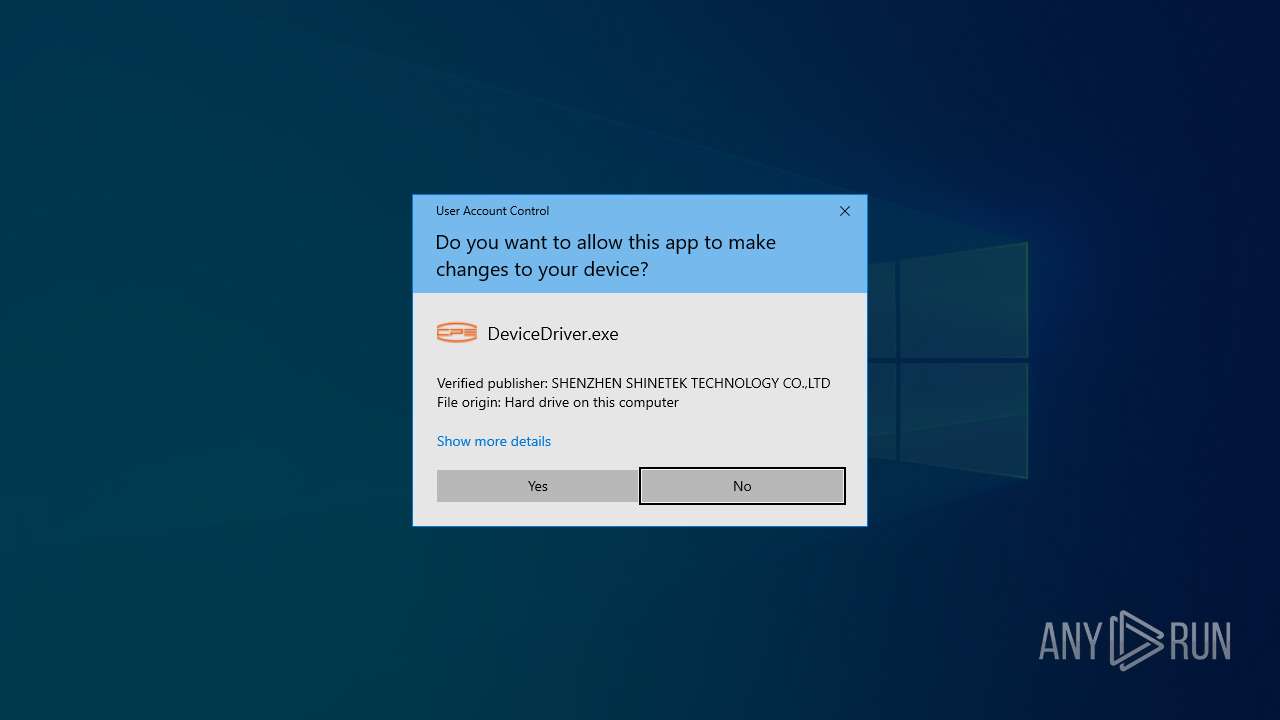
- DeviceDriver.exe (PID: 7940)
Uses TASKKILL.EXE to kill process
- CPS-Digital setup 1.0.0.12.tmp (PID: 7240)
The process drops C-runtime libraries
- CPS-Digital setup 1.0.0.12.tmp (PID: 7240)
Process drops legitimate windows executable
- CPS-Digital setup 1.0.0.12.tmp (PID: 7240)
Drops a system driver (possible attempt to evade defenses)
- OpenHardwareMonitorServer.exe (PID: 7984)
INFO
Checks supported languages
- CPS-Digital setup 1.0.0.12.exe (PID: 7216)
- CPS-Digital setup 1.0.0.12.tmp (PID: 7240)
- OpenHardwareMonitorServer.exe (PID: 7984)
- DeviceDriver.exe (PID: 7940)
- DeviceDriver.exe (PID: 1348)
Create files in a temporary directory
- CPS-Digital setup 1.0.0.12.exe (PID: 7216)
- CPS-Digital setup 1.0.0.12.tmp (PID: 7240)
Reads the computer name
- CPS-Digital setup 1.0.0.12.tmp (PID: 7240)
- CPS-Digital setup 1.0.0.12.exe (PID: 7216)
- DeviceDriver.exe (PID: 7940)
- OpenHardwareMonitorServer.exe (PID: 7984)
Creates files in the program directory
- CPS-Digital setup 1.0.0.12.tmp (PID: 7240)
- OpenHardwareMonitorServer.exe (PID: 7984)
The sample compiled with english language support
- CPS-Digital setup 1.0.0.12.tmp (PID: 7240)
Process checks computer location settings
- CPS-Digital setup 1.0.0.12.tmp (PID: 7240)
Detects InnoSetup installer (YARA)
- CPS-Digital setup 1.0.0.12.exe (PID: 7216)
- CPS-Digital setup 1.0.0.12.tmp (PID: 7240)
Compiled with Borland Delphi (YARA)
- CPS-Digital setup 1.0.0.12.exe (PID: 7216)
- CPS-Digital setup 1.0.0.12.tmp (PID: 7240)
Creates a software uninstall entry
- CPS-Digital setup 1.0.0.12.tmp (PID: 7240)
The sample compiled with japanese language support
- OpenHardwareMonitorServer.exe (PID: 7984)
Reads the software policy settings
- DeviceDriver.exe (PID: 7940)
- slui.exe (PID: 7292)
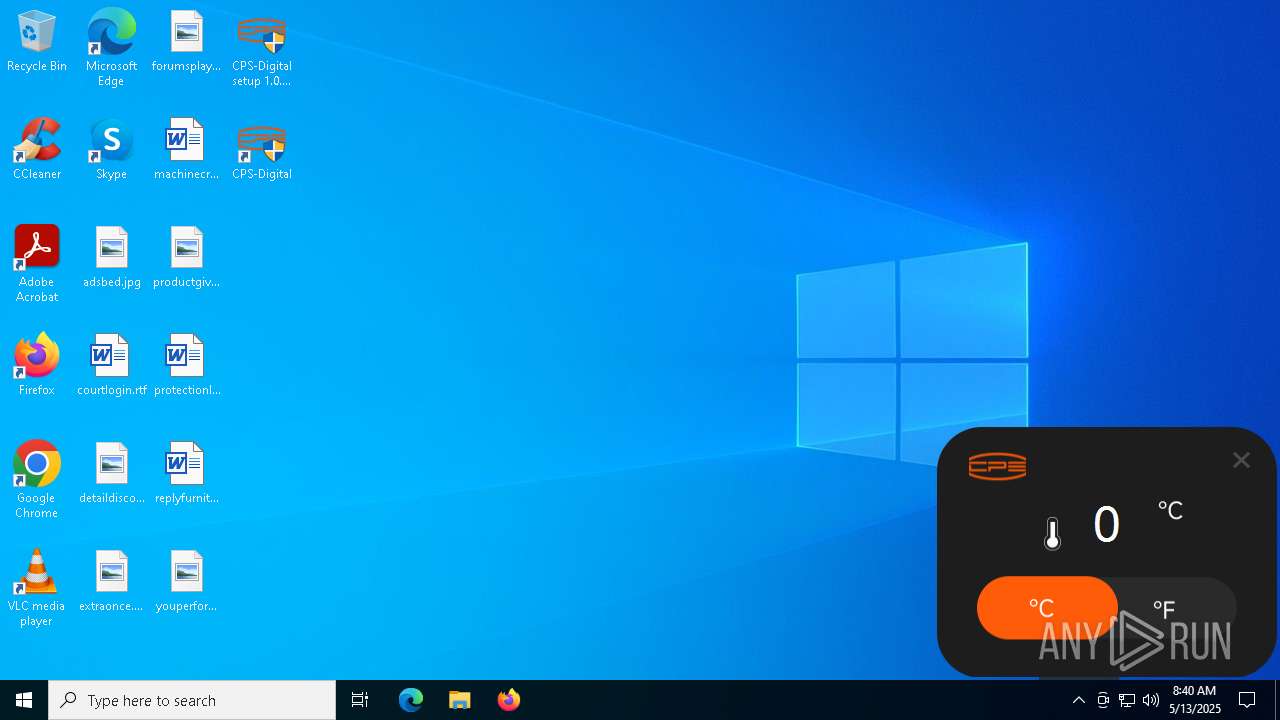
Creates files or folders in the user directory
- DeviceDriver.exe (PID: 7940)
Reads the machine GUID from the registry
- DeviceDriver.exe (PID: 7940)
Checks proxy server information
- DeviceDriver.exe (PID: 7940)
Manual execution by a user
- DeviceDriver.exe (PID: 3096)
- DeviceDriver.exe (PID: 7148)
- DeviceDriver.exe (PID: 7924)
- DeviceDriver.exe (PID: 2420)
- DeviceDriver.exe (PID: 7428)
- DeviceDriver.exe (PID: 1348)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (67.7) |
|---|---|---|
| .exe | | | Win32 EXE PECompact compressed (generic) (25.6) |
| .exe | | | Win32 Executable (generic) (2.7) |
| .exe | | | Win16/32 Executable Delphi generic (1.2) |
| .exe | | | Generic Win/DOS Executable (1.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:07:12 07:26:53+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 685056 |
| InitializedDataSize: | 156160 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xa83bc |
| OSVersion: | 6.1 |
| ImageVersion: | - |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | |
| FileDescription: | CPS-Digital Setup |
| FileVersion: | |
| LegalCopyright: | |
| OriginalFileName: | |
| ProductName: | CPS-Digital |
| ProductVersion: | 1.0.0.12 |
Total processes
154
Monitored processes
17
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1348 | "C:\Program Files\CPS-Digital\DeviceDriver.exe" | C:\Program Files\CPS-Digital\DeviceDriver.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2420 | "C:\Program Files\CPS-Digital\DeviceDriver.exe" | C:\Program Files\CPS-Digital\DeviceDriver.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3096 | "C:\Program Files\CPS-Digital\DeviceDriver.exe" | C:\Program Files\CPS-Digital\DeviceDriver.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 4880 | "C:\Users\admin\Desktop\CPS-Digital setup 1.0.0.12.exe" | C:\Users\admin\Desktop\CPS-Digital setup 1.0.0.12.exe | — | explorer.exe | |||||||||||
User: admin Company: Integrity Level: MEDIUM Description: CPS-Digital Setup Exit code: 3221226540 Version: Modules
| |||||||||||||||
| 7148 | "C:\Program Files\CPS-Digital\DeviceDriver.exe" | C:\Program Files\CPS-Digital\DeviceDriver.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 7216 | "C:\Users\admin\Desktop\CPS-Digital setup 1.0.0.12.exe" | C:\Users\admin\Desktop\CPS-Digital setup 1.0.0.12.exe | explorer.exe | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: CPS-Digital Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 7240 | "C:\Users\admin\AppData\Local\Temp\is-DOG06.tmp\CPS-Digital setup 1.0.0.12.tmp" /SL5="$8028C,3585567,842240,C:\Users\admin\Desktop\CPS-Digital setup 1.0.0.12.exe" | C:\Users\admin\AppData\Local\Temp\is-DOG06.tmp\CPS-Digital setup 1.0.0.12.tmp | CPS-Digital setup 1.0.0.12.exe | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 7260 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7292 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7336 | "C:\Program Files\CPS-Digital\\HardwareMonitor\OpenHardwareMonitorServer.exe" | C:\Program Files\CPS-Digital\HardwareMonitor\OpenHardwareMonitorServer.exe | — | DeviceDriver.exe | |||||||||||
User: admin Integrity Level: HIGH Description: OpenHardwareMonitorServer Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
2 619
Read events
2 586
Write events
33
Delete events
0
Modification events
| (PID) Process: | (7240) CPS-Digital setup 1.0.0.12.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\.myp\OpenWithProgids |
| Operation: | write | Name: | CPS-DigitalFile.myp |
Value: | |||
| (PID) Process: | (7240) CPS-Digital setup 1.0.0.12.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Applications\DeviceDriver.exe\SupportedTypes |
| Operation: | write | Name: | .myp |
Value: | |||
| (PID) Process: | (7240) CPS-Digital setup 1.0.0.12.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\CPS-Digital |
| Operation: | write | Name: | LCID |
Value: 1033 | |||
| (PID) Process: | (7240) CPS-Digital setup 1.0.0.12.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{DFDE92CF-050B-4D44-8580-9C665C255D31}_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 6.3.3 | |||
| (PID) Process: | (7240) CPS-Digital setup 1.0.0.12.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{DFDE92CF-050B-4D44-8580-9C665C255D31}_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\Program Files\CPS-Digital | |||
| (PID) Process: | (7240) CPS-Digital setup 1.0.0.12.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{DFDE92CF-050B-4D44-8580-9C665C255D31}_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files\CPS-Digital\ | |||
| (PID) Process: | (7240) CPS-Digital setup 1.0.0.12.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{DFDE92CF-050B-4D44-8580-9C665C255D31}_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: (Default) | |||
| (PID) Process: | (7240) CPS-Digital setup 1.0.0.12.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{DFDE92CF-050B-4D44-8580-9C665C255D31}_is1 |
| Operation: | write | Name: | Inno Setup: User |
Value: admin | |||
| (PID) Process: | (7240) CPS-Digital setup 1.0.0.12.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{DFDE92CF-050B-4D44-8580-9C665C255D31}_is1 |
| Operation: | write | Name: | Inno Setup: Selected Tasks |
Value: desktopicon | |||
| (PID) Process: | (7240) CPS-Digital setup 1.0.0.12.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{DFDE92CF-050B-4D44-8580-9C665C255D31}_is1 |
| Operation: | write | Name: | Inno Setup: Deselected Tasks |
Value: | |||
Executable files
29
Suspicious files
11
Text files
32
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7240 | CPS-Digital setup 1.0.0.12.tmp | C:\Program Files\CPS-Digital\DeviceDriver.exe | executable | |
MD5:A47528D67392E9D5C2E18A626BF8F0BF | SHA256:501CA13A515200E0F340F59FEB12638E7883C9AC78F9A0AA14C1E2E7560AE431 | |||
| 7240 | CPS-Digital setup 1.0.0.12.tmp | C:\Program Files\CPS-Digital\is-1AS9G.tmp | executable | |
MD5:A47528D67392E9D5C2E18A626BF8F0BF | SHA256:501CA13A515200E0F340F59FEB12638E7883C9AC78F9A0AA14C1E2E7560AE431 | |||
| 7240 | CPS-Digital setup 1.0.0.12.tmp | C:\Users\admin\AppData\Local\Temp\is-F4S3P.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 7240 | CPS-Digital setup 1.0.0.12.tmp | C:\Program Files\CPS-Digital\is-83LOD.tmp | executable | |
MD5:A47528D67392E9D5C2E18A626BF8F0BF | SHA256:501CA13A515200E0F340F59FEB12638E7883C9AC78F9A0AA14C1E2E7560AE431 | |||
| 7216 | CPS-Digital setup 1.0.0.12.exe | C:\Users\admin\AppData\Local\Temp\is-DOG06.tmp\CPS-Digital setup 1.0.0.12.tmp | executable | |
MD5:2A48B00D247C2E4CAF3E250A0AEA5318 | SHA256:A1E2DBAA8FB2DE1F489E5F48712039E4DA95D909EF5F6FC5C3D81038F22E686F | |||
| 7240 | CPS-Digital setup 1.0.0.12.tmp | C:\Program Files\CPS-Digital\vcruntime140.dll | executable | |
MD5:31CE620CB32AC950D31E019E67EFC638 | SHA256:1E0F8F7F13502F5CEE17232E9BEBCA7B44DD6EC29F1842BB61033044C65B2BBF | |||
| 7240 | CPS-Digital setup 1.0.0.12.tmp | C:\Program Files\CPS-Digital\XYUI.dll | executable | |
MD5:8A479E710C6A83C2CA949F625942EF5C | SHA256:A17F55CF3C7D5FA48AE43C8077918F316B515BF7E0949BBA4AA1DD8FA0B5CF9A | |||
| 7240 | CPS-Digital setup 1.0.0.12.tmp | C:\Program Files\CPS-Digital\is-A0FH1.tmp | executable | |
MD5:8A479E710C6A83C2CA949F625942EF5C | SHA256:A17F55CF3C7D5FA48AE43C8077918F316B515BF7E0949BBA4AA1DD8FA0B5CF9A | |||
| 7240 | CPS-Digital setup 1.0.0.12.tmp | C:\Program Files\CPS-Digital\XYUI.lib | binary | |
MD5:CD628EFA95A69BFD475123F6ED1E6BE9 | SHA256:0990D6D5CC2D416E512C30A5E04C340B6DD0D04B17BD47957609D1DAB5FE3E81 | |||
| 7240 | CPS-Digital setup 1.0.0.12.tmp | C:\Program Files\CPS-Digital\HardwareMonitor\is-R7R3P.tmp | executable | |
MD5:9B91700C132B6C09B4602B212FA517F7 | SHA256:EF5BBF11138D57F082073C08CD87A2B9432176193CC060677C847B33A738C865 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
28
DNS requests
22
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7940 | DeviceDriver.exe | GET | 200 | 104.18.21.226:80 | http://ocsp.globalsign.com/rootr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCDQHuXxad%2F5c1K2Rl1mo%3D | unknown | — | — | whitelisted |
7940 | DeviceDriver.exe | GET | 200 | 104.18.21.226:80 | http://ocsp.globalsign.com/gsrsaovsslca2018/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBRrcGT%2BanRD3C1tW3nsrKeuXC7DPwQU%2BO9%2F8s14Z6jeb48kjYjxhwMCs%2BsCDFFE8lCd0P0bqZaxeQ%3D%3D | unknown | — | — | whitelisted |
7940 | DeviceDriver.exe | GET | 200 | 104.18.21.226:80 | http://ocsp2.globalsign.com/rootr3/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBT1nGh%2FJBjWKnkPdZIzB1bqhelHBwQUj%2FBLf6guRSSuTVD6Y5qL3uLdG7wCDQHuXyId%2FGI71DM6hVc%3D | unknown | — | — | whitelisted |
2616 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2616 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.32.74:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2112 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
upgrade-1318931438.cos.ap-beijing.myqcloud.com |
| whitelisted |
ocsp.globalsign.com |
| whitelisted |
ocsp2.globalsign.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Misc activity | ET INFO Tencent Cloud Storage Domain in DNS Lookup (myqcloud .com) |
7940 | DeviceDriver.exe | Misc activity | ET INFO Observed Tencent Cloud Storage Domain (myqcloud .com in TLS SNI) |
2196 | svchost.exe | Misc activity | ET INFO Tencent Cloud Storage Domain in DNS Lookup (myqcloud .com) |
7924 | DeviceDriver.exe | Misc activity | ET INFO Observed Tencent Cloud Storage Domain (myqcloud .com in TLS SNI) |