| File name: | 2022-12-05_05421b33391eca99cd6a4b7ded9fce9b_cryptolocker |
| Full analysis: | https://app.any.run/tasks/f4772cef-e8f8-44c3-9543-d3b6b82f6377 |
| Verdict: | Malicious activity |
| Analysis date: | December 06, 2022, 05:29:10 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | MS-DOS executable PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows, MZ for MS-DOS |
| MD5: | 05421B33391ECA99CD6A4B7DED9FCE9B |
| SHA1: | 9CA698BCCC41F18B20D0FFA180B36F73EA539950 |
| SHA256: | 03975B96388ED79A658664C691B97C32B0EAE7F1441E82780CD8A39BA2BCE982 |
| SSDEEP: | 768:xQz7yVEhs9+4uR1bytOOtEvwDpjWfbZ7uyA36S7MSRb8u:xj+VGMOtEvwDpjubwQEnl |
MALICIOUS
Drops the executable file immediately after the start
- 2022-12-05_05421b33391eca99cd6a4b7ded9fce9b_cryptolocker.exe (PID: 1756)
SUSPICIOUS
Starts itself from another location
- 2022-12-05_05421b33391eca99cd6a4b7ded9fce9b_cryptolocker.exe (PID: 1756)
Executable content was dropped or overwritten
- 2022-12-05_05421b33391eca99cd6a4b7ded9fce9b_cryptolocker.exe (PID: 1756)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 2013-Oct-02 12:54:25 |
| Detected languages: |
|
DOS Header
| e_magic: | MZ |
|---|---|
| e_cblp: | 64 |
| e_cp: | 1 |
| e_crlc: | - |
| e_cparhdr: | 2 |
| e_minalloc: | - |
| e_maxalloc: | 65535 |
| e_ss: | - |
| e_sp: | 184 |
| e_csum: | - |
| e_ip: | - |
| e_cs: | - |
| e_ovno: | - |
| e_oemid: | 46080 |
| e_oeminfo: | 52489 |
| e_lfanew: | 64 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| NumberofSections: | 4 |
| TimeDateStamp: | 2013-Oct-02 12:54:25 |
| PointerToSymbolTable: | - |
| NumberOfSymbols: | - |
| SizeOfOptionalHeader: | 224 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.MPRESS1 | 4096 | 36864 | 17408 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 5.13375 |
.MPRESS2 | 40960 | 4096 | 1024 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 5.88318 |
.rsrc | 45056 | 16384 | 13312 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 5.78499 |
.imports | 61440 | 4096 | 1024 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 2.9983 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 4.96947 | 9832 | Latin 1 / Western European | English - United States | RT_ICON |
3 | 2.01924 | 20 | Latin 1 / Western European | English - United States | RT_GROUP_ICON |
RA03 | 7.88926 | 1837 | Latin 1 / Western European | UNKNOWN | RA03 |
IDR_VERSION1 | 3.13044 | 408 | Latin 1 / Western European | English - United States | RT_VERSION |
1 (#2) | 4.79597 | 346 | Latin 1 / Western European | English - United States | RT_MANIFEST |
Imports
gdi32.dll |
kernel32.dll |
user32.dll |
Total processes
38
Monitored processes
3
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1756 | "C:\Users\admin\Desktop\2022-12-05_05421b33391eca99cd6a4b7ded9fce9b_cryptolocker.exe" | C:\Users\admin\Desktop\2022-12-05_05421b33391eca99cd6a4b7ded9fce9b_cryptolocker.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
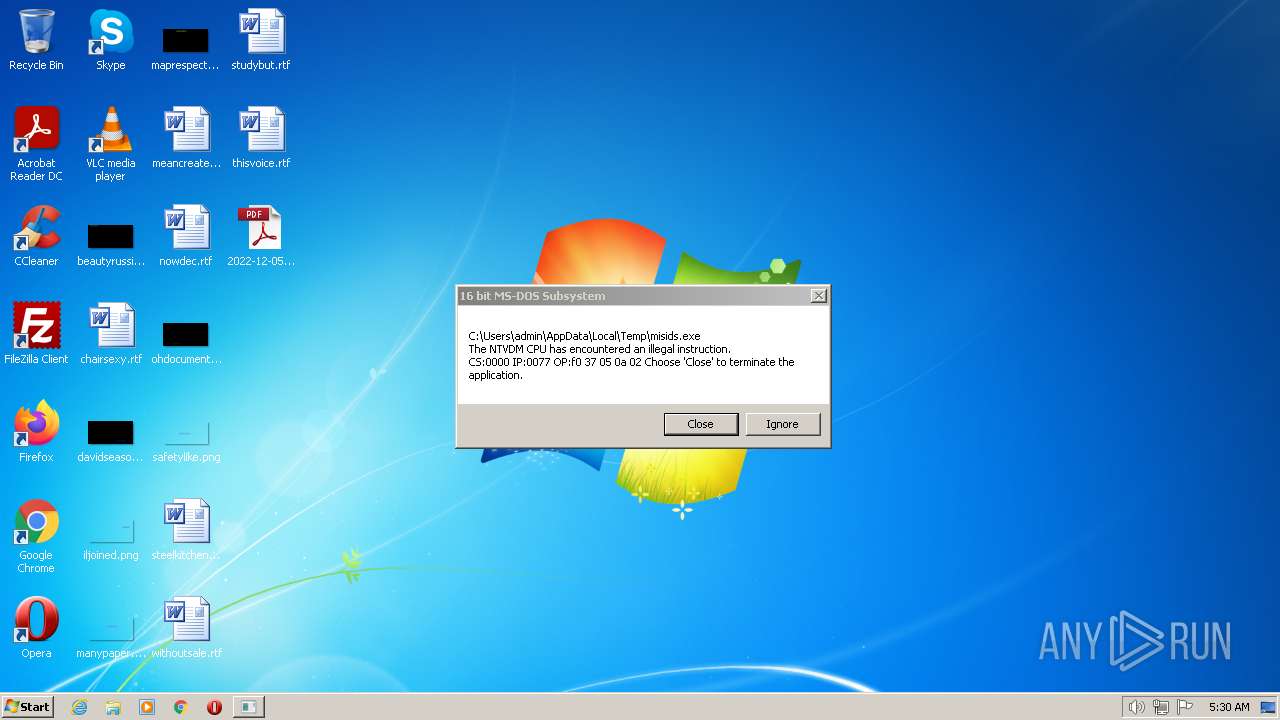
| 2016 | "C:\Users\admin\AppData\Local\Temp\misid.exe" | C:\Users\admin\AppData\Local\Temp\misid.exe | 2022-12-05_05421b33391eca99cd6a4b7ded9fce9b_cryptolocker.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3012 | "C:\Windows\system32\ntvdm.exe" -i1 | C:\Windows\system32\ntvdm.exe | — | misid.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: NTVDM.EXE Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
7 578
Read events
7 536
Write events
42
Delete events
0
Modification events
| (PID) Process: | (1756) 2022-12-05_05421b33391eca99cd6a4b7ded9fce9b_cryptolocker.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1756) 2022-12-05_05421b33391eca99cd6a4b7ded9fce9b_cryptolocker.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1756) 2022-12-05_05421b33391eca99cd6a4b7ded9fce9b_cryptolocker.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1756) 2022-12-05_05421b33391eca99cd6a4b7ded9fce9b_cryptolocker.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2016) misid.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2016) misid.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000003D010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A80164000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2016) misid.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2016) misid.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2016) misid.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2016) misid.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
1
Suspicious files
10
Text files
3
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2016 | misid.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\5080DC7A65DB6A5960ECD874088F3328_862BA1770B2FEE013603D2FF9ABEAFDA | der | |
MD5:— | SHA256:— | |||
| 2016 | misid.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\5080DC7A65DB6A5960ECD874088F3328_862BA1770B2FEE013603D2FF9ABEAFDA | binary | |
MD5:— | SHA256:— | |||
| 2016 | misid.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\0255CEC2C51D081EFF40366512890989_8139DA8AF71D2AC8E295A42D0C1D413B | binary | |
MD5:— | SHA256:— | |||
| 2016 | misid.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\87CD74335D81E59B3AD1335BFD4C2A0E | binary | |
MD5:— | SHA256:— | |||
| 2016 | misid.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\87CD74335D81E59B3AD1335BFD4C2A0E | binary | |
MD5:— | SHA256:— | |||
| 2016 | misid.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 2016 | misid.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:— | SHA256:— | |||
| 1756 | 2022-12-05_05421b33391eca99cd6a4b7ded9fce9b_cryptolocker.exe | C:\Users\admin\AppData\Local\Temp\misid.exe | executable | |
MD5:— | SHA256:— | |||
| 2016 | misid.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\0255CEC2C51D081EFF40366512890989_8139DA8AF71D2AC8E295A42D0C1D413B | binary | |
MD5:5BFA51F3A417B98E7443ECA90FC94703 | SHA256:BEBE2853A3485D1C2E5C5BE4249183E0DDAFF9F87DE71652371700A89D937128 | |||
| 2016 | misid.exe | C:\Users\admin\AppData\Local\Temp\Cab76C7.tmp | compressed | |
MD5:FC4666CBCA561E864E7FDF883A9E6661 | SHA256:10F3DEB6C452D749A7451B5D065F4C0449737E5EE8A44F4D15844B503141E65B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
12
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2016 | misid.exe | GET | 200 | 172.64.155.188:80 | http://ocsp.comodoca.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBReAhtobFzTvhaRmVeJ38QUchY9AwQUu69%2BAj36pvE8hI6t7jiY7NkyMtQCEQDwHUvue3yjezwFZqwFlyRY | US | der | 2.18 Kb | whitelisted |
2016 | misid.exe | GET | 200 | 172.64.155.188:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSTufqHinruS%2FP9Wi1XSjRRzoTLfAQUfgNaZUFrp34K4bidCOodjh1qx2UCEDxnfkAuwwRAeeP5piZS1Hs%3D | US | binary | 5 b | whitelisted |
2016 | misid.exe | GET | 200 | 172.64.155.188:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSTufqHinruS%2FP9Wi1XSjRRzoTLfAQUfgNaZUFrp34K4bidCOodjh1qx2UCEDxnfkAuwwRAeeP5piZS1Hs%3D | US | binary | 5 b | whitelisted |
2016 | misid.exe | GET | 200 | 104.18.32.68:80 | http://crl.comodoca.com/cPanelIncCertificationAuthority.crl | US | binary | 72.3 Kb | whitelisted |
2016 | misid.exe | GET | 200 | 172.64.155.188:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSTufqHinruS%2FP9Wi1XSjRRzoTLfAQUfgNaZUFrp34K4bidCOodjh1qx2UCEDxnfkAuwwRAeeP5piZS1Hs%3D | US | binary | 5 b | whitelisted |
2016 | misid.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?3a5d1a45e7b5df03 | US | compressed | 4.70 Kb | whitelisted |
2016 | misid.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?00dcd94c49904855 | US | compressed | 61.4 Kb | whitelisted |
2016 | misid.exe | GET | 200 | 172.64.155.188:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSTufqHinruS%2FP9Wi1XSjRRzoTLfAQUfgNaZUFrp34K4bidCOodjh1qx2UCEDxnfkAuwwRAeeP5piZS1Hs%3D | US | binary | 5 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2016 | misid.exe | 103.14.121.240:443 | bestccc.com | Good Domain Registry Private Limited | IN | malicious |
2016 | misid.exe | 172.64.155.188:80 | ocsp.comodoca.com | CLOUDFLARENET | US | suspicious |
2016 | misid.exe | 104.18.32.68:80 | ocsp.comodoca.com | CLOUDFLARENET | — | suspicious |
2016 | misid.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
bestccc.com |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
crl.comodoca.com |
| whitelisted |