| File name: | Windows-KB890830-V1.34.exe |
| Full analysis: | https://app.any.run/tasks/0b8ab3f8-76f4-441e-a3b6-57dc34f742a5 |
| Verdict: | Malicious activity |
| Analysis date: | February 19, 2025, 16:44:14 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 3 sections |
| MD5: | BA830EEE565B252C0D9441B0017C11BC |
| SHA1: | A827A00A099CA0B9286FC147E49D2A4F95F983B6 |
| SHA256: | 038D19B8B26C685C7C7531932C7F3EC20D86569CAB7FADF4C438EC4E73D96872 |
| SSDEEP: | 98304:FCrWtUp9qva1t4+2H042i24ibO/1OTJ/TYYM0zL+MPf/ufNYCraoBU70yoTfoHLW:o12FVKOKiCCUz5x+c8h |
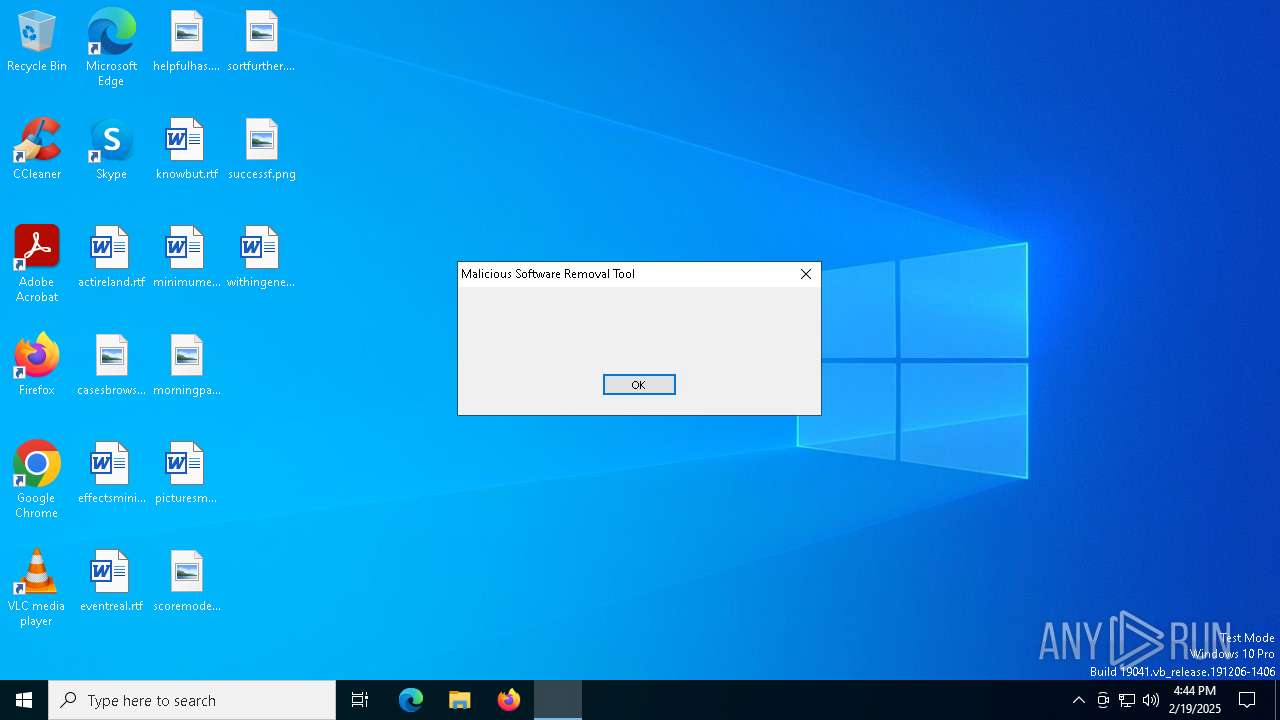
MALICIOUS
Executing a file with an untrusted certificate
- mrtstub.exe (PID: 6688)
- MRT.exe (PID: 6744)
- mrtstub.exe (PID: 6540)
SUSPICIOUS
Starts a Microsoft application from unusual location
- Windows-KB890830-V1.34.exe (PID: 6372)
Process drops legitimate windows executable
- Windows-KB890830-V1.34.exe (PID: 6372)
- mrtstub.exe (PID: 6688)
Executable content was dropped or overwritten
- Windows-KB890830-V1.34.exe (PID: 6372)
- mrtstub.exe (PID: 6688)
- MRT.exe (PID: 6744)
Searches for installed software
- MRT.exe (PID: 6744)
INFO
Checks supported languages
- Windows-KB890830-V1.34.exe (PID: 6372)
- mrtstub.exe (PID: 6688)
Reads the computer name
- Windows-KB890830-V1.34.exe (PID: 6372)
Reads the machine GUID from the registry
- Windows-KB890830-V1.34.exe (PID: 6372)
The sample compiled with english language support
- Windows-KB890830-V1.34.exe (PID: 6372)
- MRT.exe (PID: 6744)
The sample compiled with arabic language support
- Windows-KB890830-V1.34.exe (PID: 6372)
- mrtstub.exe (PID: 6688)
Create files in a temporary directory
- MRT.exe (PID: 6744)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | MS generic-sfx Cabinet File Unpacker (32/64bit MSCFU) (82.5) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (7.3) |
| .exe | | | Win64 Executable (generic) (6.5) |
| .dll | | | Win32 Dynamic Link Library (generic) (1.5) |
| .exe | | | Win32 Executable (generic) (1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2005:02:24 19:44:38+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit, Removable run from swap, Net run from swap |
| PEType: | PE32 |
| LinkerVersion: | 7.1 |
| CodeSize: | 31232 |
| InitializedDataSize: | 72704 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x5972 |
| OSVersion: | 5.2 |
| ImageVersion: | 5.2 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 6.1.22.4 |
| ProductVersionNumber: | 6.1.22.4 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Microsoft Corporation |
| FileDescription: | Self-Extracting Cabinet |
| FileVersion: | 6.1.0022.4 (SRV03_QFE.031113-0918) |
| InternalName: | SFXCAB.EXE |
| LegalCopyright: | © Microsoft Corporation. All rights reserved. |
| OriginalFileName: | SFXCAB.EXE |
| ProductName: | Microsoft® Windows® Operating System |
| ProductVersion: | 6.1.0022.4 |
Total processes
132
Monitored processes
4
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 6372 | "C:\Users\admin\AppData\Local\Temp\Windows-KB890830-V1.34.exe" | C:\Users\admin\AppData\Local\Temp\Windows-KB890830-V1.34.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Self-Extracting Cabinet Version: 6.1.0022.4 (SRV03_QFE.031113-0918) Modules
| |||||||||||||||
| 6540 | c:\0feca2bbf60626d4fed714874a790897\mrtstub.exe | C:\0feca2bbf60626d4fed714874a790897\mrtstub.exe | — | Windows-KB890830-V1.34.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Malicious Software Removal Tool Update Stub Exit code: 3221226540 Version: 1.34.2288.0 Modules
| |||||||||||||||
| 6688 | c:\0feca2bbf60626d4fed714874a790897\mrtstub.exe | C:\0feca2bbf60626d4fed714874a790897\mrtstub.exe | Windows-KB890830-V1.34.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Malicious Software Removal Tool Update Stub Version: 1.34.2288.0 Modules
| |||||||||||||||
| 6744 | "C:\WINDOWS\system32\MRT.exe" | C:\Windows\SysWOW64\MRT.exe | mrtstub.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Windows Malicious Software Removal Tool Version: 1.34.2288.0 Modules
| |||||||||||||||
Total events
3 591
Read events
3 589
Write events
2
Delete events
0
Modification events
| (PID) Process: | (6744) MRT.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\RemovalTools\MRT |
| Operation: | write | Name: | EULA |
Value: 1 | |||
| (PID) Process: | (6744) MRT.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\RemovalTools\MRT |
| Operation: | write | Name: | Version |
Value: 52168AD3-127E-416C-B7F6-068D1254C3A4 | |||
Executable files
4
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6744 | MRT.exe | C:\Users\admin\AppData\Local\Temp\TMP000000066DDC5B3985B279DD | — | |
MD5:— | SHA256:— | |||
| 6372 | Windows-KB890830-V1.34.exe | C:\0feca2bbf60626d4fed714874a790897\mrt.exe | executable | |
MD5:17A08C8124CD99EFCB1D677FBF7CBF86 | SHA256:A476ED3D6309F376C6A6F716F0536E265D88739CABCE6BF42FC30D35FFC54380 | |||
| 6372 | Windows-KB890830-V1.34.exe | C:\0feca2bbf60626d4fed714874a790897\mrtstub.exe | executable | |
MD5:D6FDD814EC24E3FD576E154590BE7759 | SHA256:BB883F087533FB4BF520D2ED4B055E6A86C39A415C220862395D9BE1FEC4BECA | |||
| 6688 | mrtstub.exe | C:\Windows\SysWOW64\MRT.exe | executable | |
MD5:17A08C8124CD99EFCB1D677FBF7CBF86 | SHA256:A476ED3D6309F376C6A6F716F0536E265D88739CABCE6BF42FC30D35FFC54380 | |||
| 6744 | MRT.exe | C:\Users\admin\AppData\Local\Temp\mpengine.dll | executable | |
MD5:927553366341AA701F3CE795BA6D3CD6 | SHA256:F2B0C63F24963159F84D8C8E5C0D01E2E3B65D84C191A1367935A41BF1CCFCED | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
32
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.149:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.149:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6648 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6648 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6448 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5064 | SearchApp.exe | 104.126.37.154:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.149:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
— | — | 23.48.23.149:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 20.190.159.128:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |