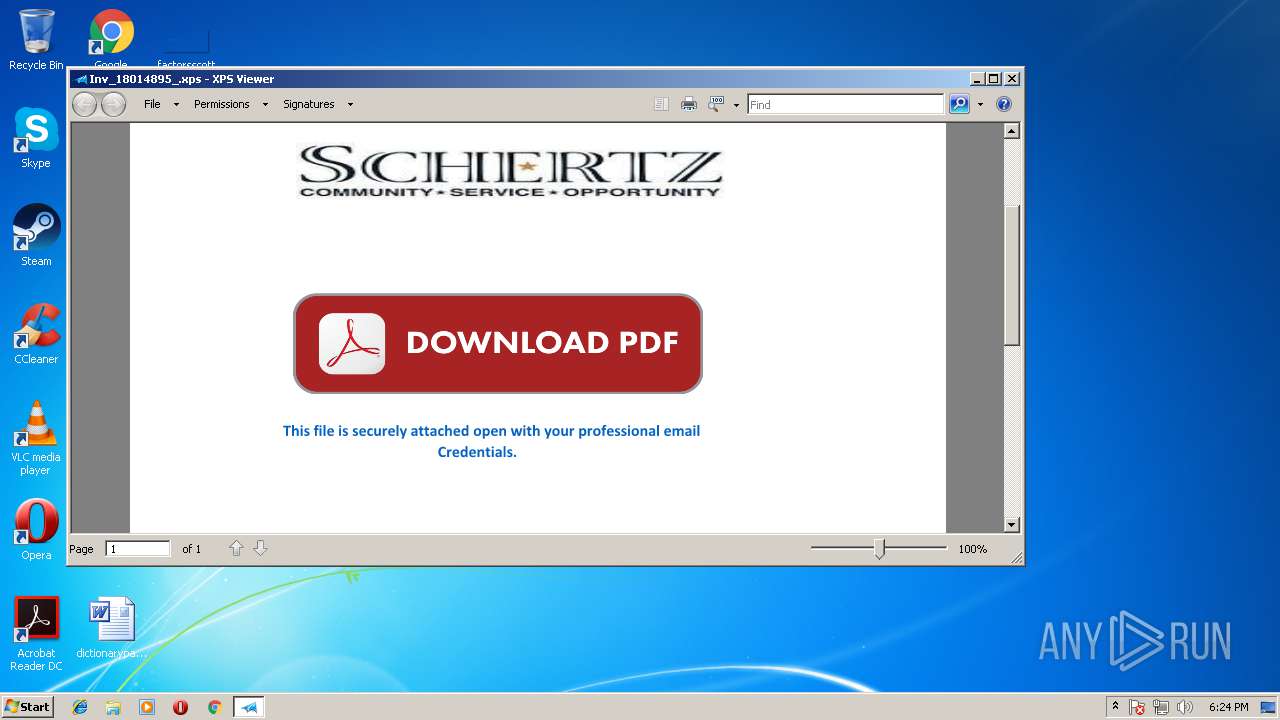
| File name: | Inv_18014895_.xps |
| Full analysis: | https://app.any.run/tasks/7c10547d-63aa-462b-a2e1-b2ac9cbe18d8 |
| Verdict: | Suspicious activity |
| Analysis date: | July 17, 2018, 17:24:23 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/octet-stream |
| File info: | Microsoft OOXML |
| MD5: | 036BEA9206F2F16925B5A5E8EB816514 |
| SHA1: | 5CC62D9CD98FA6B66080C66E7BEFDC96CDB66521 |
| SHA256: | 034EF3C1AF249FFF62D167914F962726B8F598D783EFA83B16C7EECCD0A8EA66 |
| SSDEEP: | 6144:yRSfjtaQBor5OW4Mt3yhzkA+1j7aQ2lObTRP1wSGxNZd5sHrpkRCloqKN28aTWf:qetBoZt3ynExPB0N92rORHRaTWf |
MALICIOUS
No malicious indicators.SUSPICIOUS
Starts Internet Explorer
- xpsrchvw.exe (PID: 2228)
INFO
Changes internet zones settings
- iexplore.exe (PID: 2944)
Reads Internet Cache Settings
- iexplore.exe (PID: 4048)
- iexplore.exe (PID: 2384)
Dropped object may contain URL's
- xpsrchvw.exe (PID: 2228)
- iexplore.exe (PID: 4048)
- iexplore.exe (PID: 2384)
Reads internet explorer settings
- iexplore.exe (PID: 4048)
- iexplore.exe (PID: 2384)
Application launched itself
- iexplore.exe (PID: 2944)
Creates files in the user directory
- iexplore.exe (PID: 2944)
- FlashUtil32_27_0_0_187_ActiveX.exe (PID: 3328)
- iexplore.exe (PID: 2384)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2944)
Changes settings of System certificates
- iexplore.exe (PID: 2944)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .oxps/xps | | | Open XML Paper Specification (57) |
|---|---|---|
| .zip | | | Open Packaging Conventions container (35) |
| .zip | | | ZIP compressed archive (8) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0006 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCRC: | 0x69806908 |
| ZipCompressedSize: | 369 |
| ZipUncompressedSize: | 1114 |
| ZipFileName: | [Content_Types].xml |
XMP
| Creator: | PC |
|---|
XML
| CreateDate: | 2018:07:16 14:32:15Z |
|---|---|
| ModifyDate: | 2018:07:16 14:32:15Z |
Total processes
36
Monitored processes
5
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2228 | "C:\Windows\System32\xpsrchvw.exe" "C:\Users\admin\AppData\Local\Temp\Inv_18014895_.xps" | C:\Windows\System32\xpsrchvw.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: XPS Viewer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2384 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2944 CREDAT:6403 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2944 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | xpsrchvw.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3328 | C:\Windows\system32\Macromed\Flash\FlashUtil32_27_0_0_187_ActiveX.exe -Embedding | C:\Windows\system32\Macromed\Flash\FlashUtil32_27_0_0_187_ActiveX.exe | — | svchost.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe® Flash® Player Installer/Uninstaller 27.0 r0 Exit code: 0 Version: 27,0,0,187 Modules
| |||||||||||||||
| 4048 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2944 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
702
Read events
600
Write events
100
Delete events
2
Modification events
| (PID) Process: | (2228) xpsrchvw.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\XPSViewer\View |
| Operation: | write | Name: | PrevPagesToCache |
Value: 2 | |||
| (PID) Process: | (2228) xpsrchvw.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\XPSViewer\View |
| Operation: | write | Name: | NextPagesToCache |
Value: 10 | |||
| (PID) Process: | (2228) xpsrchvw.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\XPSViewer\View |
| Operation: | write | Name: | HoldAllMaxPagesToCache |
Value: 20 | |||
| (PID) Process: | (2228) xpsrchvw.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: xpsrchvw.exe | |||
| (PID) Process: | (2228) xpsrchvw.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\XPSViewer |
| Operation: | write | Name: | FindOptions |
Value: 16 | |||
| (PID) Process: | (2944) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2944) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2944) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2944) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (2944) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
Executable files
0
Suspicious files
1
Text files
150
Unknown types
30
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2944 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\XB3OCR2W\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2944 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2228 | xpsrchvw.exe | C:\Users\admin\AppData\LocalLow\Temp\Microsoft\OPC\DDT.w0mchhxez211wrje919q8e4fh.tmp | odttf | |
MD5:— | SHA256:— | |||
| 2228 | xpsrchvw.exe | C:\Users\admin\AppData\LocalLow\Temp\Microsoft\OPC\DDT.ntheig4jh22ib8g0c9fffg03f.tmp | image | |
MD5:— | SHA256:— | |||
| 2228 | xpsrchvw.exe | C:\Users\admin\AppData\LocalLow\Temp\Microsoft\OPC\DDT.9zfaw8blaebbruetyp5i_m3hf.tmp | image | |
MD5:— | SHA256:— | |||
| 2228 | xpsrchvw.exe | C:\Users\admin\AppData\LocalLow\Temp\Microsoft\OPC\DDT.34mnuck58k_4eiwr183bk4mbh.tmp | text | |
MD5:— | SHA256:— | |||
| 2228 | xpsrchvw.exe | C:\Users\admin\AppData\LocalLow\Temp\Microsoft\OPC\DDT.ykloouw8fi8l493khtnmcwq_f.tmp | odttf | |
MD5:— | SHA256:— | |||
| 2228 | xpsrchvw.exe | C:\Users\admin\AppData\LocalLow\Temp\Microsoft\OPC\DDT.tr6oqrr06co4znl81ed2ycmpe.tmp | text | |
MD5:— | SHA256:— | |||
| 2228 | xpsrchvw.exe | C:\Users\admin\AppData\LocalLow\Temp\Microsoft\OPC\DDT.wb3fwdzpx4a7ng016jaejhf4e.tmp | text | |
MD5:0A9EBBCA867FF233708008B056DE61B1 | SHA256:A00CA37E3C02C36C3DD6B5DA4A326278FFC20CA27AAA93D4B08A1251FD708D32 | |||
| 4048 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DSILEDM7\ErrorPageTemplate[1] | text | |
MD5:F4FE1CB77E758E1BA56B8A8EC20417C5 | SHA256:8D018639281B33DA8EB3CE0B21D11E1D414E59024C3689F92BE8904EB5779B5F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
42
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2944 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2384 | iexplore.exe | 192.0.78.17:443 | wordpress.com | Automattic, Inc | US | unknown |
2384 | iexplore.exe | 192.0.77.2:443 | i2.wp.com | Automattic, Inc | US | suspicious |
2384 | iexplore.exe | 192.0.77.32:443 | s0.wp.com | Automattic, Inc | US | suspicious |
2384 | iexplore.exe | 192.0.76.3:443 | stats.wp.com | Automattic, Inc | US | suspicious |
2384 | iexplore.exe | 216.58.215.238:443 | www.youtube.com | Google Inc. | US | whitelisted |
2384 | iexplore.exe | 104.17.104.89:443 | embed.tawk.to | Cloudflare Inc | US | shared |
2384 | iexplore.exe | 148.251.235.172:443 | static.whatshelp.io | Hetzner Online GmbH | DE | unknown |
2384 | iexplore.exe | 151.101.2.109:443 | cdn.jsdelivr.net | Fastly | US | suspicious |
2384 | iexplore.exe | 173.255.118.158:443 | va.tawk.to | Google Inc. | US | whitelisted |
2384 | iexplore.exe | 104.17.103.89:443 | embed.tawk.to | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
trungdan.press |
| suspicious |
1hostingmurah.com |
| suspicious |
wordpress.com |
| whitelisted |
i2.wp.com |
| whitelisted |
i1.wp.com |
| whitelisted |
i0.wp.com |
| whitelisted |
platform.twitter.com |
| whitelisted |
stats.wp.com |
| whitelisted |
s0.wp.com |
| whitelisted |