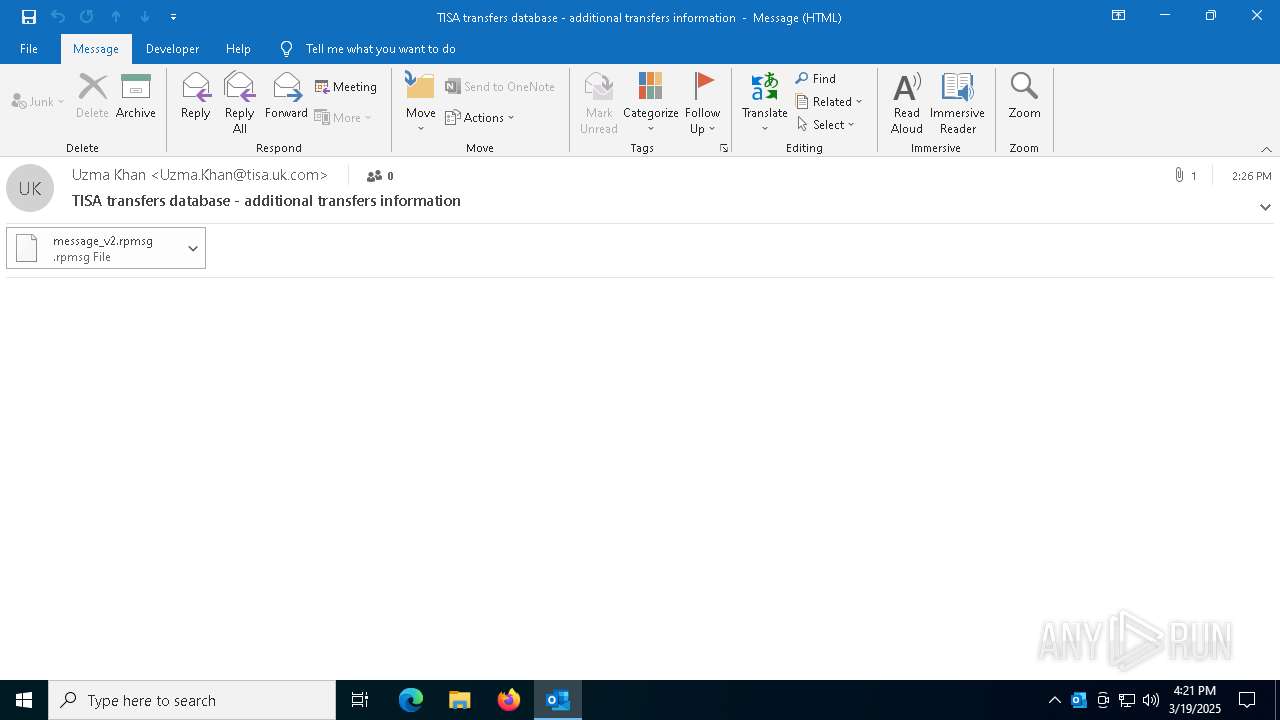
| File name: | TISA transfers database - additional transfers information.msg |
| Full analysis: | https://app.any.run/tasks/2baf439b-b7a8-4f1d-9fdd-159462e1ad48 |
| Verdict: | Malicious activity |
| Analysis date: | March 19, 2025, 16:21:32 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | 1C5007CE7B36D8D9EE42F096FF6160D2 |
| SHA1: | 3827FC9D6404AFC8EC55119332D7CC8E4486E61F |
| SHA256: | 03387A85ADF9DC207C993398E20EB9E871C3D2D8C653D186AC92ACDF432D115D |
| SSDEEP: | 24576:gJm8h9HfmA+kcuJh+c3alnKHiydhVFVTxrpXwfLqoJ7kvD4p5U:gJ/h9HfmA+kcuJh+c3alnKHiyd73TxrF |
MALICIOUS
No malicious indicators.SUSPICIOUS
Email with suspicious attachment
- OUTLOOK.EXE (PID: 1348)
INFO
Email verification fail (SPF, DKIM or DMARC)
- OUTLOOK.EXE (PID: 1348)
Email with attachments
- OUTLOOK.EXE (PID: 1348)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (58.9) |
|---|---|---|
| .oft | | | Outlook Form Template (34.4) |
Total processes
138
Monitored processes
4
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1348 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /f "C:\Users\admin\AppData\Local\Temp\TISA transfers database - additional transfers information.msg" | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 1672 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4000 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7656 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "5F1C942A-23E5-4F2C-9839-8703F2CBD3BD" "196A03CD-BA76-4E6D-9EF9-B4CA2BE74895" "1348" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
Total events
8 643
Read events
8 233
Write events
360
Delete events
50
Modification events
| (PID) Process: | (1348) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 6 |
Value: 01941A000000001000B24E9A3E06000000000000000600000000000000 | |||
| (PID) Process: | (1348) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\OUTLOOK\1348 |
| Operation: | write | Name: | 0 |
Value: 0B0E1027964C9915589C408021BE0BB804111523004698CCD58EB09DE6ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511C40AD2120B6F00750074006C006F006F006B002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (1348) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootCommand |
Value: | |||
| (PID) Process: | (1348) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootFailureCount |
Value: | |||
| (PID) Process: | (1348) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1348) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | CantBootResolution |
Value: BootSuccess | |||
| (PID) Process: | (1348) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | ProfileBeingOpened |
Value: Outlook | |||
| (PID) Process: | (1348) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | SessionId |
Value: C3D8E96E-C1AF-4750-8D52-F4E28119C131 | |||
| (PID) Process: | (1348) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | BootDiagnosticsLogFile |
Value: C:\Users\admin\AppData\Local\Temp\Outlook Logging\OUTLOOK_16_0_16026_20146-20240718T1116060318-1644.etl | |||
| (PID) Process: | (1348) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | ProfileBeingOpened |
Value: | |||
Executable files
0
Suspicious files
16
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1348 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 1348 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\BPWHZ3PU\message_v2.rpmsg:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 1348 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | binary | |
MD5:E89907A694F1B891434CA17EEB569061 | SHA256:4CF1F429737BDA7EFCCBACD581C653552B95A87153F3CADECBED1C74EE4768AE | |||
| 1348 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\MSIPC\keyfile3.drm | binary | |
MD5:D22FCC3560E13FED15B084CD46EC07FB | SHA256:0B02DA1E8D2FAF05BC71B2A01F23F4AA68FCD97C5295D7E5577FE12797414051 | |||
| 1348 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\MSIPC\CERT-Machine-2048.drm | binary | |
MD5:FF80414C6824F73B9C66F422AC6DA30A | SHA256:8F653A9302719D0F34F8F26CD6F063D55E7782CBEE4A140419F9A129A94DCF07 | |||
| 1348 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\MSIPC\CERT-Machine.drm | binary | |
MD5:FEFEFA9AF4B350D50840C2083CC76B66 | SHA256:CF4818C735A9D11AC15931A1F671C8B4BB2CD14E9D317030121730751842582C | |||
| 1348 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:61641259605D25C62FE6FBE85BE43451 | SHA256:6EF4D9380BDA235BA790EC6D884A330A2D37CFB2DBFD38017B2871E691A1C46A | |||
| 1348 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\37C951188967C8EB88D99893D9D191FE | binary | |
MD5:3B5E0BD6640456A749D9155E6C135727 | SHA256:C362A3D2B661C6066A02FC169FAAA1976C2F6160DA5837C7E68B7E0F67B794ED | |||
| 1348 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\21253908F3CB05D51B1C2DA8B681A785 | binary | |
MD5:C1B2B57D6D5B4506A5AE61EF6AB2D79D | SHA256:207DA28E4E0E03D358F2CB880136C0EE06B3C8EE48CB44874DEB0E92128C4ECF | |||
| 1348 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | binary | |
MD5:C346107E724122700B027B09DBBCDC99 | SHA256:41090553208003D9AED6C22056FA8FDD9696F457E9F58B1B6488C1BE01A78260 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
32
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.138:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.138:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1348 | OUTLOOK.EXE | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1348 | OUTLOOK.EXE | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
1348 | OUTLOOK.EXE | GET | 200 | 23.48.23.138:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1348 | OUTLOOK.EXE | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
7900 | SIHClient.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4408 | backgroundTaskHost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7900 | SIHClient.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.138:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.48.23.138:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1348 | OUTLOOK.EXE | 52.123.128.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6544 | svchost.exe | 20.190.159.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 23.54.109.203:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1348 | OUTLOOK.EXE | 52.109.28.47:443 | roaming.officeapps.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
1348 | OUTLOOK.EXE | 23.54.109.203:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
90fe58f5-095f-46a0-acdf-64f9eda82418.rms.eu.aadrm.com |
| unknown |
www.microsoft.com |
| whitelisted |