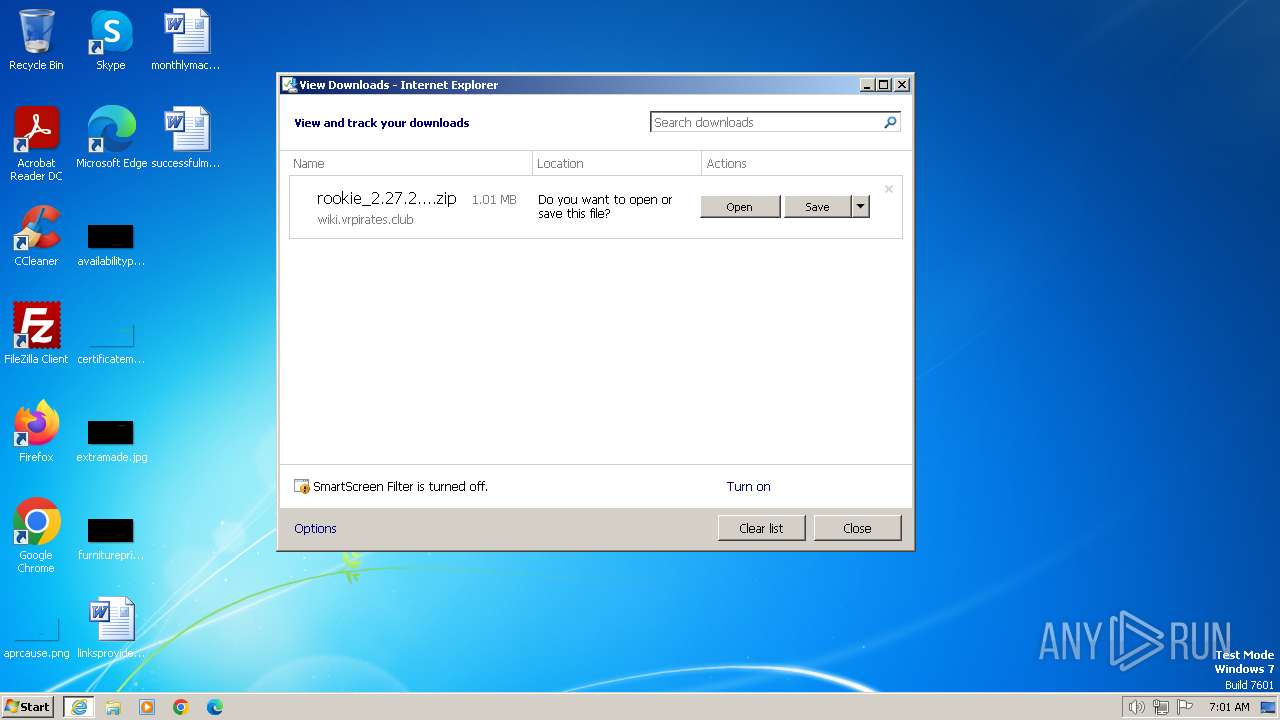
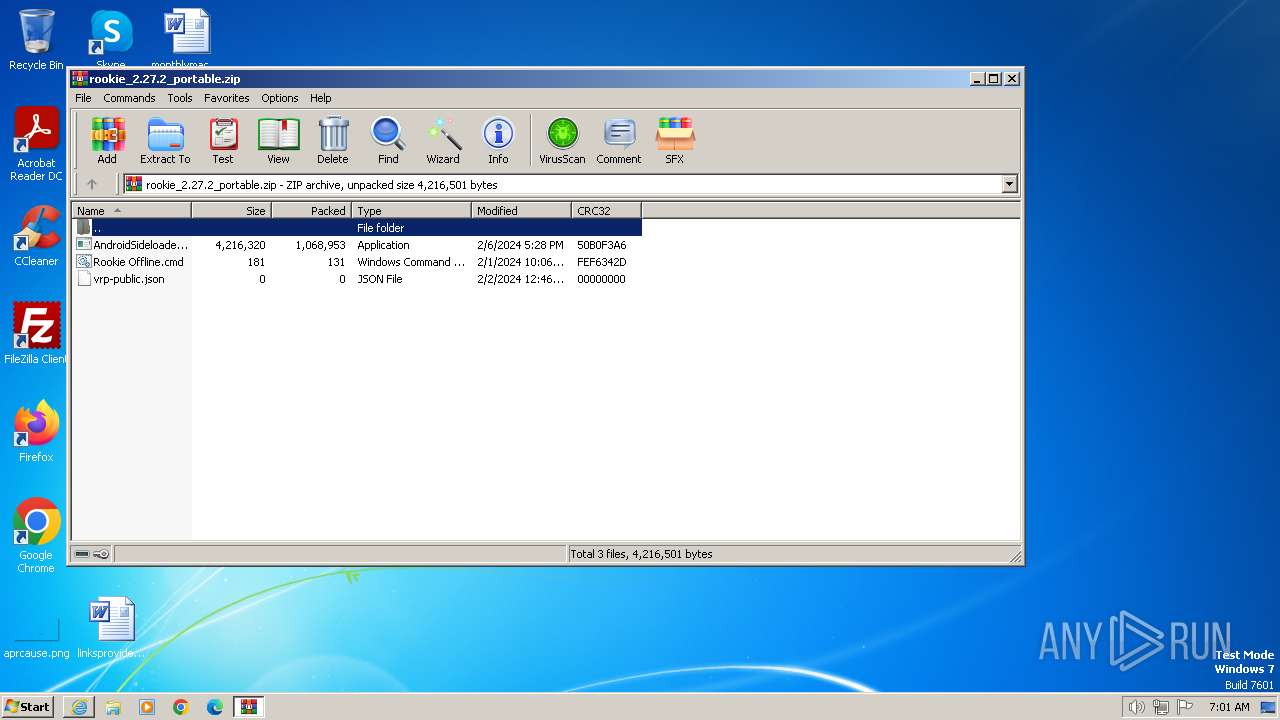
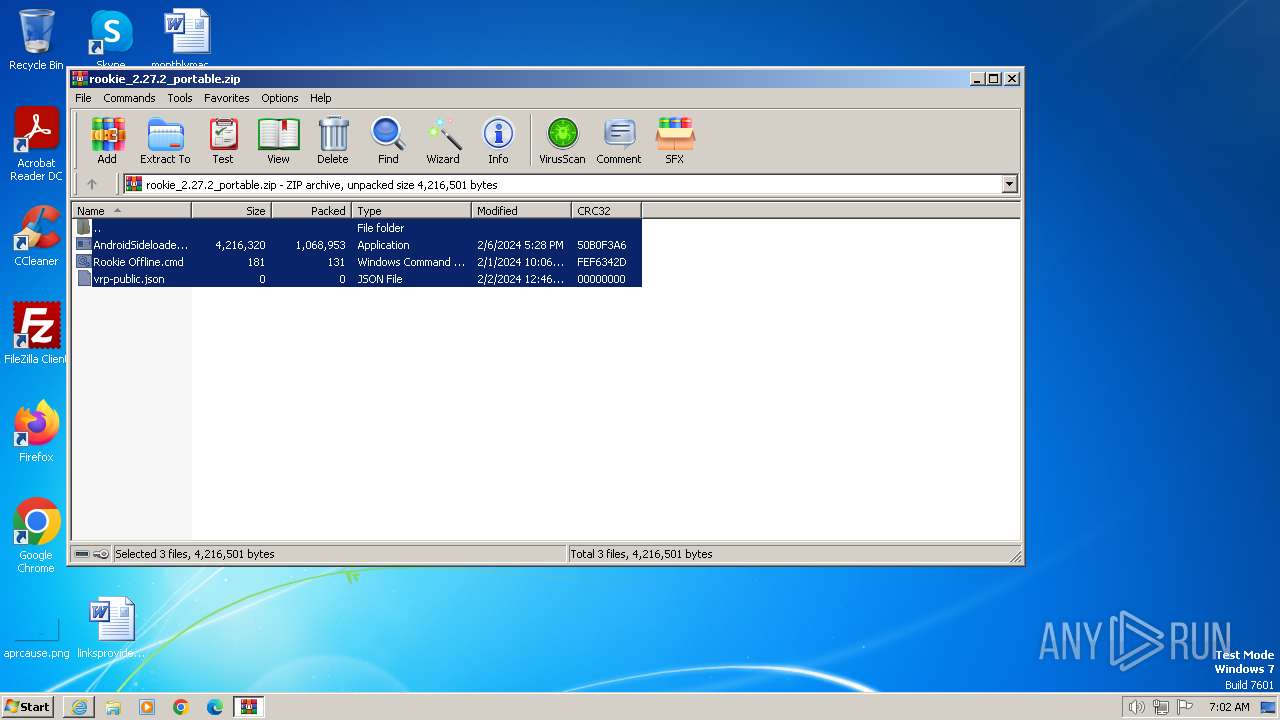
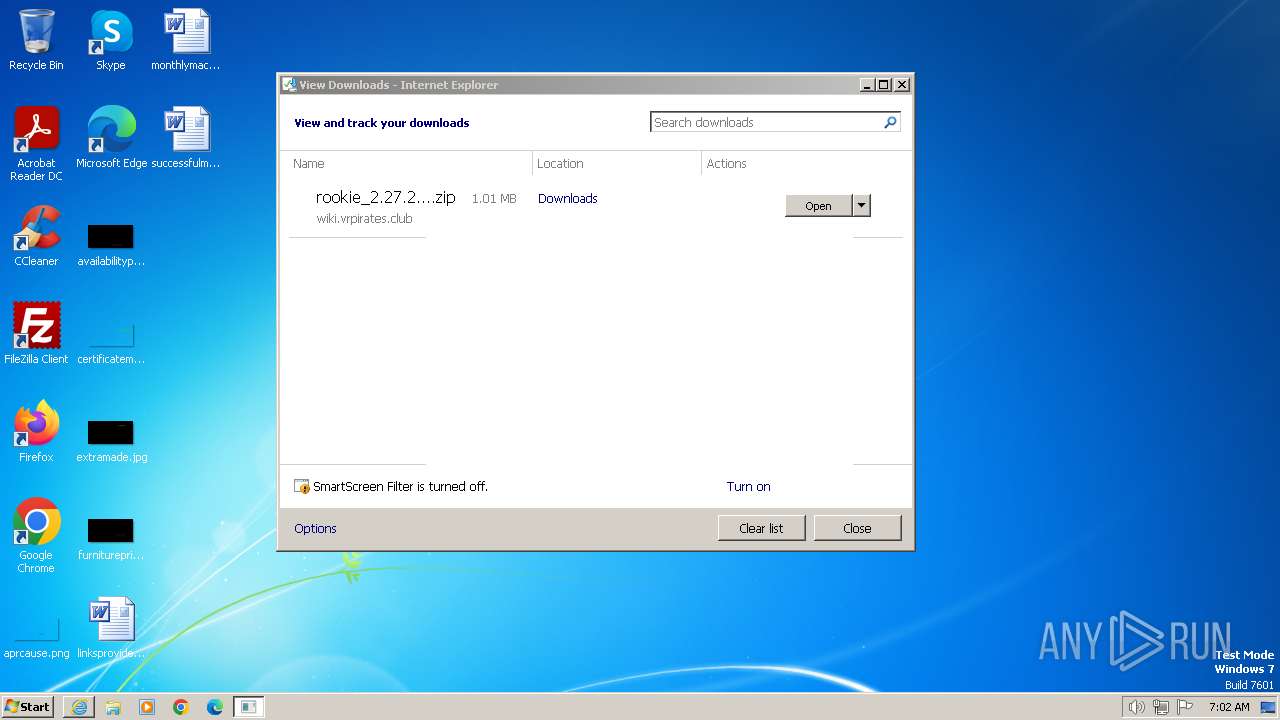
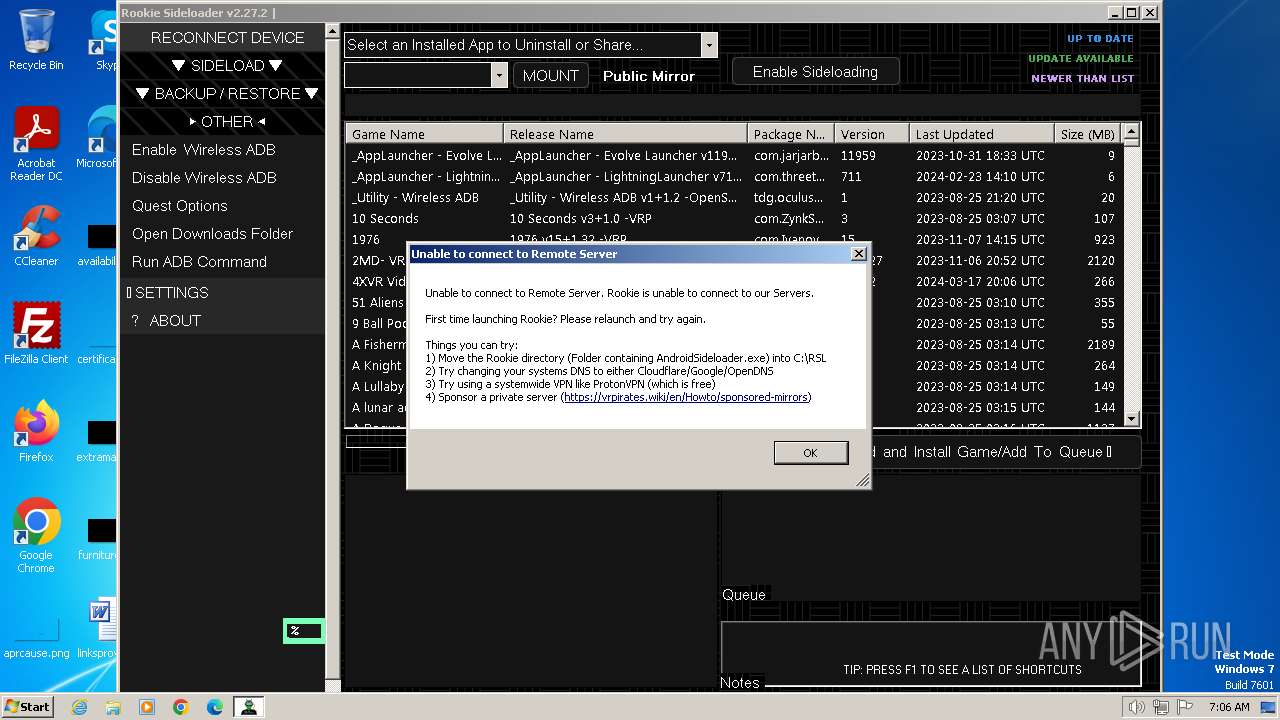
| URL: | https://wiki.vrpirates.club/downloads/rookie/rookie_2.27.2_portable.zip |
| Full analysis: | https://app.any.run/tasks/29f74581-6e3e-4d2a-8fb0-08807245eade |
| Verdict: | Malicious activity |
| Analysis date: | March 29, 2024, 07:01:39 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 5533AEF641D8AFA6641B4A55C2D06D1A |
| SHA1: | FB5D8A2F892B6D44078C0DDB4834CF162A9CCFDA |
| SHA256: | 03274EBA71372CA48CCFD0FAD0DA1B2E827F1E28EFF3B3A912267A262DC96AB9 |
| SSDEEP: | 3:N8dj2UL46K45LqgXkLV:2LL4h40h |
MALICIOUS
Drops the executable file immediately after the start
- AndroidSideloader v2.27.2.exe (PID: 3616)
- 7z.exe (PID: 3172)
SUSPICIOUS
Reads security settings of Internet Explorer
- AndroidSideloader v2.27.2.exe (PID: 3616)
Reads the Internet Settings
- AndroidSideloader v2.27.2.exe (PID: 3616)
Reads settings of System Certificates
- AndroidSideloader v2.27.2.exe (PID: 3616)
- rclone.exe (PID: 3376)
Drops 7-zip archiver for unpacking
- AndroidSideloader v2.27.2.exe (PID: 3616)
Application launched itself
- adb.exe (PID: 3108)
Adds/modifies Windows certificates
- AndroidSideloader v2.27.2.exe (PID: 3616)
- rclone.exe (PID: 3376)
INFO
Application launched itself
- iexplore.exe (PID: 3956)
Modifies the phishing filter of IE
- iexplore.exe (PID: 3956)
Manual execution by a user
- explorer.exe (PID: 2596)
- WinRAR.exe (PID: 2780)
- AndroidSideloader v2.27.2.exe (PID: 3616)
The process uses the downloaded file
- iexplore.exe (PID: 3956)
- WinRAR.exe (PID: 2780)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2780)
Checks supported languages
- AndroidSideloader v2.27.2.exe (PID: 3616)
- 7z.exe (PID: 3172)
- adb.exe (PID: 2880)
- adb.exe (PID: 3108)
- rclone.exe (PID: 1428)
- rclone.exe (PID: 3376)
- 7z.exe (PID: 1264)
- adb.exe (PID: 3808)
- 7z.exe (PID: 2228)
- adb.exe (PID: 864)
- adb.exe (PID: 3464)
- adb.exe (PID: 3536)
- adb.exe (PID: 2912)
Reads the computer name
- AndroidSideloader v2.27.2.exe (PID: 3616)
- 7z.exe (PID: 1264)
- adb.exe (PID: 2880)
- rclone.exe (PID: 1428)
- rclone.exe (PID: 3376)
- 7z.exe (PID: 3172)
- 7z.exe (PID: 2228)
Reads the machine GUID from the registry
- AndroidSideloader v2.27.2.exe (PID: 3616)
- rclone.exe (PID: 3376)
Reads Environment values
- AndroidSideloader v2.27.2.exe (PID: 3616)
Reads the software policy settings
- AndroidSideloader v2.27.2.exe (PID: 3616)
- rclone.exe (PID: 3376)
Creates files or folders in the user directory
- AndroidSideloader v2.27.2.exe (PID: 3616)
Create files in a temporary directory
- adb.exe (PID: 2880)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
72
Monitored processes
18
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 864 | "C:\RSL\platform-tools\adb.exe" shell dumpsys battery | C:\RSL\platform-tools\adb.exe | — | AndroidSideloader v2.27.2.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 1264 | "7z.exe" x "C:\Users\admin\Downloads\rookie_2.27.2_portable\rclone.zip" -y -o"C:\Users\admin\Downloads\rookie_2.27.2_portable" -bsp1 | C:\Users\admin\Downloads\rookie_2.27.2_portable\7z.exe | — | AndroidSideloader v2.27.2.exe | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip Standalone Console Exit code: 0 Version: 23.01 Modules
| |||||||||||||||
| 1428 | "C:\Users\admin\Downloads\rookie_2.27.2_portable\rclone\rclone.exe" listremotes --config vrp.download.config | C:\Users\admin\Downloads\rookie_2.27.2_portable\rclone\rclone.exe | — | AndroidSideloader v2.27.2.exe | |||||||||||
User: admin Company: https://rclone.org Integrity Level: MEDIUM Description: Rsync for cloud storage Exit code: 0 Version: 1.62.2 Modules
| |||||||||||||||
| 2148 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\rookie_2.27.2_portable.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | iexplore.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2228 | "7z.exe" x "C:\Users\admin\Downloads\rookie_2.27.2_portable\meta.7z" -y -o"C:\Users\admin\Downloads\rookie_2.27.2_portable\meta" -p"gL59VfgPxoHR" -bsp1 | C:\Users\admin\Downloads\rookie_2.27.2_portable\7z.exe | — | AndroidSideloader v2.27.2.exe | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip Standalone Console Exit code: 0 Version: 23.01 Modules
| |||||||||||||||
| 2596 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2780 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Downloads\rookie_2.27.2_portable.zip" C:\Users\admin\Downloads\rookie_2.27.2_portable\ | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2880 | adb -L tcp:5037 fork-server server --reply-fd 216 | C:\RSL\platform-tools\adb.exe | — | adb.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 2912 | "C:\RSL\platform-tools\adb.exe" shell svc usb setFunctions mtp true | C:\RSL\platform-tools\adb.exe | — | AndroidSideloader v2.27.2.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 3108 | "C:\RSL\platform-tools\adb.exe" start-server | C:\RSL\platform-tools\adb.exe | — | AndroidSideloader v2.27.2.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
41 246
Read events
40 990
Write events
199
Delete events
57
Modification events
| (PID) Process: | (3956) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3956) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3956) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31097254 | |||
| (PID) Process: | (3956) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 146018770 | |||
| (PID) Process: | (3956) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31097255 | |||
| (PID) Process: | (3956) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3956) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3956) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3956) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3956) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
17
Suspicious files
11
Text files
3 070
Unknown types
90
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3964 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 3964 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\78118620D6B8F6CB2909CD29DD8239E9 | binary | |
MD5:— | SHA256:— | |||
| 3964 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\78118620D6B8F6CB2909CD29DD8239E9 | binary | |
MD5:— | SHA256:— | |||
| 3964 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\D0E1C4B6144E7ECAB3F020E4A19EFC29_03D1B482EE3032A122274428715A4E19 | binary | |
MD5:— | SHA256:— | |||
| 3964 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\D0E1C4B6144E7ECAB3F020E4A19EFC29_03D1B482EE3032A122274428715A4E19 | binary | |
MD5:— | SHA256:— | |||
| 3964 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\9748296F8EC6A1B83B3A993229E7E102 | binary | |
MD5:— | SHA256:— | |||
| 3964 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\9748296F8EC6A1B83B3A993229E7E102 | binary | |
MD5:— | SHA256:— | |||
| 3964 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\rookie_2.27.2_portable[1].zip | compressed | |
MD5:— | SHA256:— | |||
| 3964 | iexplore.exe | C:\Users\admin\Downloads\rookie_2.27.2_portable.zip.vlj8zqn.partial | compressed | |
MD5:— | SHA256:— | |||
| 3956 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF871CDDBA41D8C4DC.TMP | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
28
DNS requests
24
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3964 | iexplore.exe | GET | 304 | 23.32.238.219:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?92967c53a8c0ec29 | unknown | — | — | unknown |
3964 | iexplore.exe | GET | 304 | 23.32.238.219:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?36ca310eb28aaa33 | unknown | — | — | unknown |
3964 | iexplore.exe | GET | 200 | 104.18.38.233:80 | http://zerossl.crt.sectigo.com/ZeroSSLECCDomainSecureSiteCA.crt | unknown | — | — | unknown |
3964 | iexplore.exe | GET | 200 | 104.18.38.233:80 | http://zerossl.crt.sectigo.com/ZeroSSLECCDomainSecureSiteCA.crt | unknown | — | — | unknown |
3964 | iexplore.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSr83eyJy3njhjVpn5bEpfc6MXawQQUOuEJhtTPGcKWdnRJdtzgNcZjY5oCECO3bePBuysaUZYeCOq3ZOg%3D | unknown | — | — | unknown |
3964 | iexplore.exe | GET | 200 | 172.64.149.23:80 | http://zerossl.ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBQzH%2F4%2F%2FQuEFihPlI1WwH4Dktj2TQQUD2vmS845R672fpAeefAwkZLIX6MCEQClHQmP3r10EbiyayR0kuDT | unknown | — | — | unknown |
3956 | iexplore.exe | GET | 304 | 23.32.238.201:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?3ffc3fbc5b315e52 | unknown | — | — | unknown |
3956 | iexplore.exe | GET | 304 | 23.32.238.208:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?31055eca6ea3b32e | unknown | — | — | unknown |
3956 | iexplore.exe | GET | 304 | 23.32.238.169:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?719f0b64dcb4a601 | unknown | — | — | unknown |
1080 | svchost.exe | GET | 200 | 23.32.238.201:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?4f071b604691de88 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3964 | iexplore.exe | 185.247.224.87:443 | wiki.vrpirates.club | Flokinet Ltd | SC | unknown |
3964 | iexplore.exe | 23.32.238.219:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
3964 | iexplore.exe | 104.18.38.233:80 | zerossl.crt.sectigo.com | CLOUDFLARENET | — | shared |
3964 | iexplore.exe | 172.64.149.23:80 | zerossl.crt.sectigo.com | CLOUDFLARENET | US | unknown |
3956 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | EDGECAST | US | whitelisted |
3956 | iexplore.exe | 23.32.238.201:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
wiki.vrpirates.club |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
zerossl.crt.sectigo.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
zerossl.ocsp.sectigo.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3964 | iexplore.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |
3964 | iexplore.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |
— | — | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |