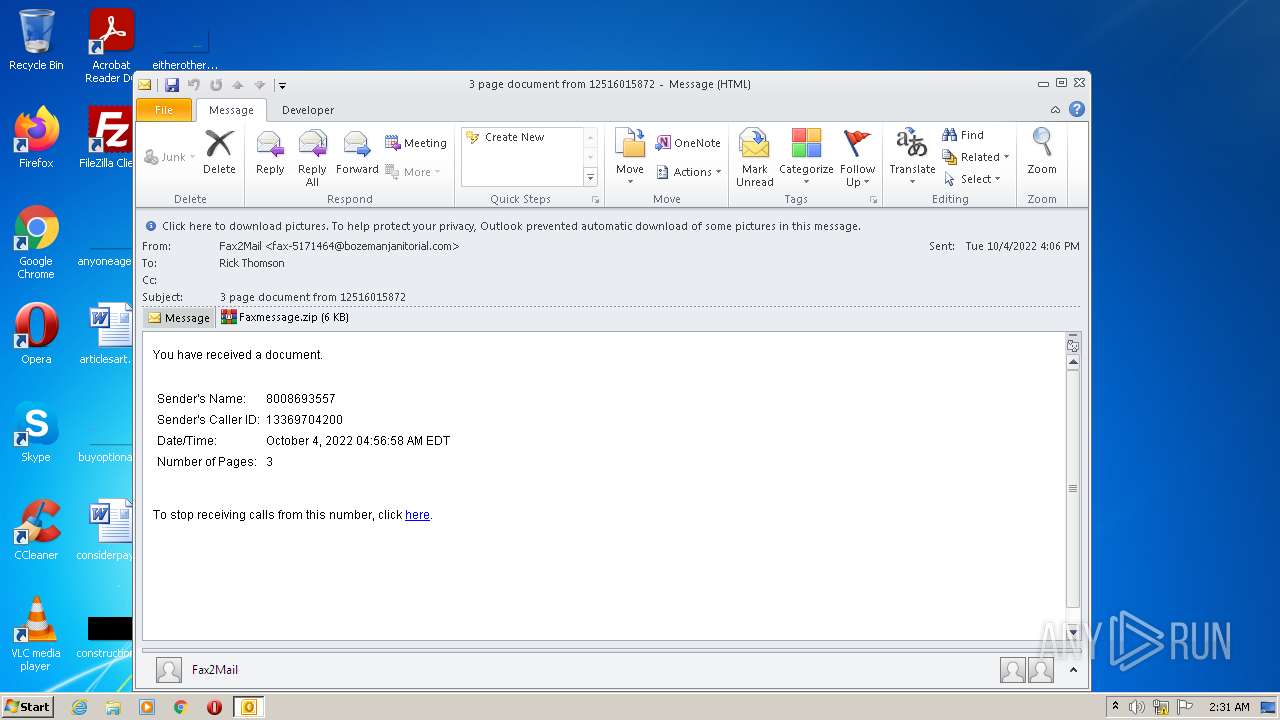
| File name: | noname (3).eml |
| Full analysis: | https://app.any.run/tasks/91104898-64c7-41b3-8a78-3a7402041e6f |
| Verdict: | Malicious activity |
| Analysis date: | October 05, 2022, 01:30:53 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | RFC 822 mail, ASCII text, with CRLF line terminators |
| MD5: | 02A75E3B6F640882C5F97231EDDE4FB4 |
| SHA1: | 66B1AF03E407770FADF15482E8F18099326FADD0 |
| SHA256: | 031140B85B198CDFA7357F61514AA4CD2F716E771FD570FCF810B3AF4845147B |
| SSDEEP: | 384:5n+LRiDMHjf1VbjjFGfVbjJe0qSeZ0q2ZH9krXTSkp4id19DIK:Z+LR7Hb1VbjGVbjHWC1pkOi7N |
MALICIOUS
No malicious indicators.SUSPICIOUS
Checks supported languages
- OUTLOOK.EXE (PID: 1388)
Reads the computer name
- OUTLOOK.EXE (PID: 1388)
Executed as Windows Service
- SearchIndexer.exe (PID: 3548)
Creates files in the user directory
- OUTLOOK.EXE (PID: 1388)
Creates files in the program directory
- SearchIndexer.exe (PID: 3548)
Searches for installed software
- OUTLOOK.EXE (PID: 1388)
Reads default file associations for system extensions
- SearchIndexer.exe (PID: 3548)
INFO
Checks supported languages
- SearchIndexer.exe (PID: 3548)
- SearchProtocolHost.exe (PID: 2072)
- SearchFilterHost.exe (PID: 2224)
- SearchProtocolHost.exe (PID: 2516)
Reads the computer name
- SearchIndexer.exe (PID: 3548)
- SearchProtocolHost.exe (PID: 2072)
- SearchFilterHost.exe (PID: 2224)
- SearchProtocolHost.exe (PID: 2516)
Reads Microsoft Office registry keys
- SearchProtocolHost.exe (PID: 2072)
- OUTLOOK.EXE (PID: 1388)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 5) (100) |
|---|
Total processes
40
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1388 | "C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE" /eml "C:\Users\admin\AppData\Local\Temp\noname (3).eml" | C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 2072 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe_S-1-5-21-1302019708-1500728564-335382590-10001_ Global\UsGthrCtrlFltPipeMssGthrPipe_S-1-5-21-1302019708-1500728564-335382590-10001 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" "1" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
| 2224 | "C:\Windows\system32\SearchFilterHost.exe" 0 520 524 532 65536 528 | C:\Windows\system32\SearchFilterHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Windows Search Filter Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
| 2516 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe2_ Global\UsGthrCtrlFltPipeMssGthrPipe2 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
| 3548 | C:\Windows\system32\SearchIndexer.exe /Embedding | C:\Windows\system32\SearchIndexer.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Indexer Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
9 088
Read events
8 327
Write events
738
Delete events
23
Modification events
| (PID) Process: | (1388) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (1388) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (1388) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (1388) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (1388) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (1388) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (1388) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (1388) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (1388) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
| (PID) Process: | (1388) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: Off | |||
Executable files
0
Suspicious files
8
Text files
10
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1388 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVRABE0.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1388 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook Data File - NoMail.pst | — | |
MD5:— | SHA256:— | |||
| 1388 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 1388 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\outlook logging\firstrun.log | text | |
MD5:— | SHA256:— | |||
| 3548 | SearchIndexer.exe | C:\programdata\microsoft\search\data\applications\windows\projects\systemindex\indexer\cifiles\CiMG0012.000 | binary | |
MD5:— | SHA256:— | |||
| 3548 | SearchIndexer.exe | C:\programdata\microsoft\search\data\applications\windows\projects\systemindex\indexer\cifiles\00010011.dir | binary | |
MD5:— | SHA256:— | |||
| 3548 | SearchIndexer.exe | C:\ProgramData\Microsoft\Search\Data\Applications\Windows\tmp.edb | — | |
MD5:— | SHA256:— | |||
| 3548 | SearchIndexer.exe | C:\ProgramData\Microsoft\Search\Data\Applications\Windows\MSS.log | binary | |
MD5:— | SHA256:— | |||
| 3548 | SearchIndexer.exe | C:\programdata\microsoft\search\data\applications\windows\projects\systemindex\indexer\cifiles\CiMG0012.002 | ppn | |
MD5:— | SHA256:— | |||
| 1388 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\{25ABE177-288B-4B0E-BB86-6F020C3C7F61}\{1C306CB1-771E-4B4B-A902-86E897877F5B}.png | image | |
MD5:4C61C12EDBC453D7AE184976E95258E1 | SHA256:296526F9A716C1AA91BA5D6F69F0EB92FDF79C2CB2CFCF0CEB22B7CCBC27035F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1388 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |