| File name: | 360mpGui v1.5.0.0.exe |
| Full analysis: | https://app.any.run/tasks/2f52fdab-a99e-478a-9a60-60dbc528f41b |
| Verdict: | Malicious activity |
| Analysis date: | August 04, 2024, 22:59:35 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed |
| MD5: | CE20A4FA9956B21DF844AE9A4B2F0437 |
| SHA1: | E2EA1FB9CF0888B1E5D5D886591FC92A499D936E |
| SHA256: | 030C6ABFF1F3556E96BF8DFC1D3EBAC95F105B64FF7D71D5790E0790E216FCDB |
| SSDEEP: | 98304:n7bF01deMcbXlVZHTOqfM1Bn/GcraLq8Me4KKeEnTAy/bIq2hF7Z3o+wmBhBGZNe:ZpomgbDApvx1LA45/ |
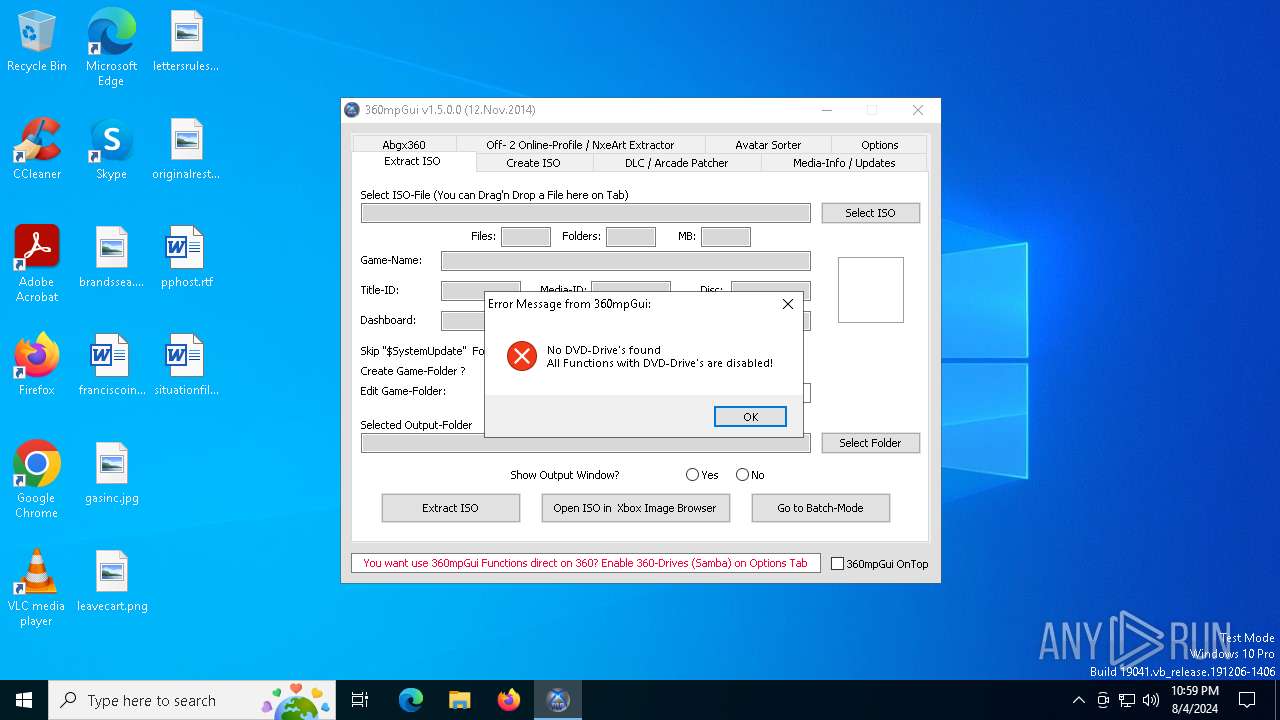
MALICIOUS
Drops the executable file immediately after the start
- 360mpGui v1.5.0.0.exe (PID: 6584)
SUSPICIOUS
Reads security settings of Internet Explorer
- 360mpGui v1.5.0.0.exe (PID: 6584)
Executable content was dropped or overwritten
- 360mpGui v1.5.0.0.exe (PID: 6584)
Process drops legitimate windows executable
- 360mpGui v1.5.0.0.exe (PID: 6584)
Reads Microsoft Outlook installation path
- 360mpGui v1.5.0.0.exe (PID: 6584)
Reads Internet Explorer settings
- 360mpGui v1.5.0.0.exe (PID: 6584)
INFO
Checks supported languages
- 360mpGui v1.5.0.0.exe (PID: 6584)
Reads mouse settings
- 360mpGui v1.5.0.0.exe (PID: 6584)
Reads the computer name
- 360mpGui v1.5.0.0.exe (PID: 6584)
Create files in a temporary directory
- 360mpGui v1.5.0.0.exe (PID: 6584)
UPX packer has been detected
- 360mpGui v1.5.0.0.exe (PID: 6584)
Process checks Internet Explorer phishing filters
- 360mpGui v1.5.0.0.exe (PID: 6584)
Checks proxy server information
- 360mpGui v1.5.0.0.exe (PID: 6584)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (39.3) |
|---|---|---|
| .exe | | | Win32 EXE Yoda's Crypter (38.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (9.5) |
| .exe | | | Win32 Executable (generic) (6.5) |
| .exe | | | Generic Win/DOS Executable (2.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2010:04:16 07:47:33+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 9 |
| CodeSize: | 270336 |
| InitializedDataSize: | 188416 |
| UninitializedDataSize: | 638976 |
| EntryPoint: | 0xdebd0 |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.5.0.0 |
| ProductVersionNumber: | 3.3.6.1 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | English (British) |
| CharacterSet: | Unicode |
| FileVersion: | 1.5.0.0 |
| Comments: | 360mpGui |
| FileDescription: | 360mpGui |
| LegalCopyright: | 360mpGui |
Total processes
127
Monitored processes
1
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 6584 | "C:\Users\admin\Downloads\360mpGui v1.5.0.0.exe" | C:\Users\admin\Downloads\360mpGui v1.5.0.0.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: 360mpGui Exit code: 0 Version: 1.5.0.0 Modules
| |||||||||||||||
Total events
8 500
Read events
8 410
Write events
84
Delete events
6
Modification events
| (PID) Process: | (6584) 360mpGui v1.5.0.0.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6584) 360mpGui v1.5.0.0.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6584) 360mpGui v1.5.0.0.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6584) 360mpGui v1.5.0.0.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6584) 360mpGui v1.5.0.0.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6584) 360mpGui v1.5.0.0.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6584) 360mpGui v1.5.0.0.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6584) 360mpGui v1.5.0.0.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (6584) 360mpGui v1.5.0.0.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 04000000030000000E0000000F000000000000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
| (PID) Process: | (6584) 360mpGui v1.5.0.0.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\4 |
| Operation: | write | Name: | MRUListEx |
Value: 040000000000000005000000020000000100000003000000FFFFFFFF | |||
Executable files
6
Suspicious files
12
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6584 | 360mpGui v1.5.0.0.exe | C:\Users\admin\AppData\Local\Temp\dtpybdr | text | |
MD5:83FD13ADA78C873E10959783BE31CF9B | SHA256:1C7414A35F9A8E718120B7025B9839EE91C0EA2FD0EEB34DE3216C711EF8B2FA | |||
| 6584 | 360mpGui v1.5.0.0.exe | C:\Users\admin\AppData\Local\Temp\aut532E.tmp | binary | |
MD5:6C2331581D5359E2FD9A9107604DA006 | SHA256:53060A6BF58EF04B1E5FA3DDEFE60BC51F2B9ACF11152CDB4B295B5A68EED3AD | |||
| 6584 | 360mpGui v1.5.0.0.exe | C:\Users\admin\AppData\Local\Temp\aut534F.tmp | executable | |
MD5:48B1EAFDFF8DAEC984224041AF5D4388 | SHA256:C496403D68704F5FCE2E2E30033025B3E3C01357452F52E7074DDB2ED94A2496 | |||
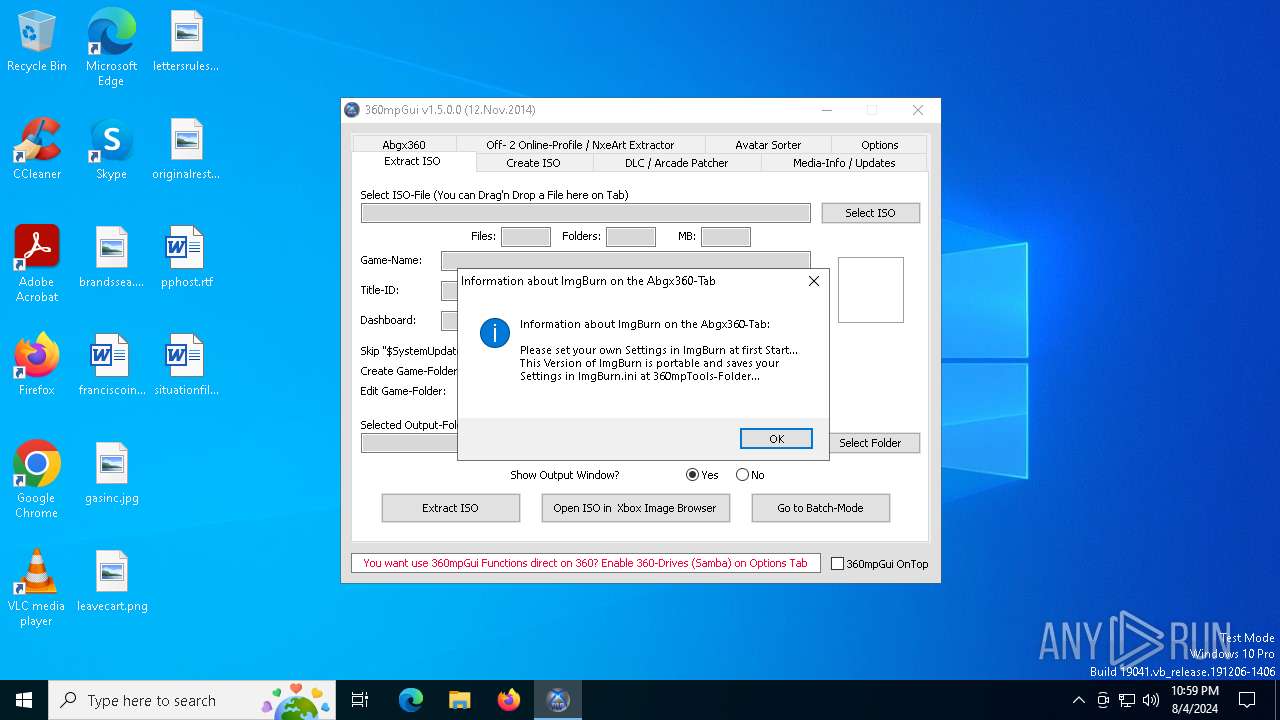
| 6584 | 360mpGui v1.5.0.0.exe | C:\Users\admin\Downloads\360mpTools\ImgBurn.exe | executable | |
MD5:48B1EAFDFF8DAEC984224041AF5D4388 | SHA256:C496403D68704F5FCE2E2E30033025B3E3C01357452F52E7074DDB2ED94A2496 | |||
| 6584 | 360mpGui v1.5.0.0.exe | C:\Users\admin\AppData\Local\Temp\360mpGui\BootLogo.jpg | image | |
MD5:951662223E04D035BD1C1056C4516EDD | SHA256:F7C722BD68277A078AB50E10FB2E99179666821850FBC56673DDBDEB4DBA1C91 | |||
| 6584 | 360mpGui v1.5.0.0.exe | C:\Users\admin\AppData\Local\Temp\360mpGui\360mpGui.ico | image | |
MD5:813BB0894F82DEE01D4BEE35B3A3F121 | SHA256:5792A3805DC36991D66796FAC575208066603D6B5C69EAB45CEE1AFC6FC245AC | |||
| 6584 | 360mpGui v1.5.0.0.exe | C:\Users\admin\AppData\Local\Temp\~DF1C6B06B2D3CBE7C6.TMP | binary | |
MD5:051557F209EAC3BE536FB84D5ED94D28 | SHA256:625153B2E95F7B684CB805E8C4CD65421070FACD4BA56B426C434F0B37135B3E | |||
| 6584 | 360mpGui v1.5.0.0.exe | C:\Users\admin\Downloads\360mpTools\ImgBurnStuff\Sounds\Error.wav | wav | |
MD5:EFAD8C5D6CC6CAE180EBE01CE3A60C88 | SHA256:ACAD74B9BB57809E1B35BC06F357941986EBDC547BA33FC618F07E6E7BDC49BD | |||
| 6584 | 360mpGui v1.5.0.0.exe | C:\Users\admin\AppData\Local\Temp\aut541B.tmp | binary | |
MD5:4952C13A6C2EE32190FCB5CB145B0D4A | SHA256:AF75CDC31EFC365477A6520E65A40E9FD0C5FC553BE5E69608E15DEE005A95F4 | |||
| 6584 | 360mpGui v1.5.0.0.exe | C:\Users\admin\AppData\Local\Temp\aut4E5A.tmp | binary | |
MD5:310CDF21DFB5854617C7FFD3960DFC52 | SHA256:78A7B882FF8E0C30AF5EA489C61EDD5749B67193CD8008AADD836AB04F242DF1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
36
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1928 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1928 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6944 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
7000 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4936 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3140 | RUXIMICS.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4936 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5336 | SearchApp.exe | 95.100.146.8:443 | www.bing.com | Akamai International B.V. | CZ | unknown |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1928 | svchost.exe | 20.190.159.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
th.bing.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |