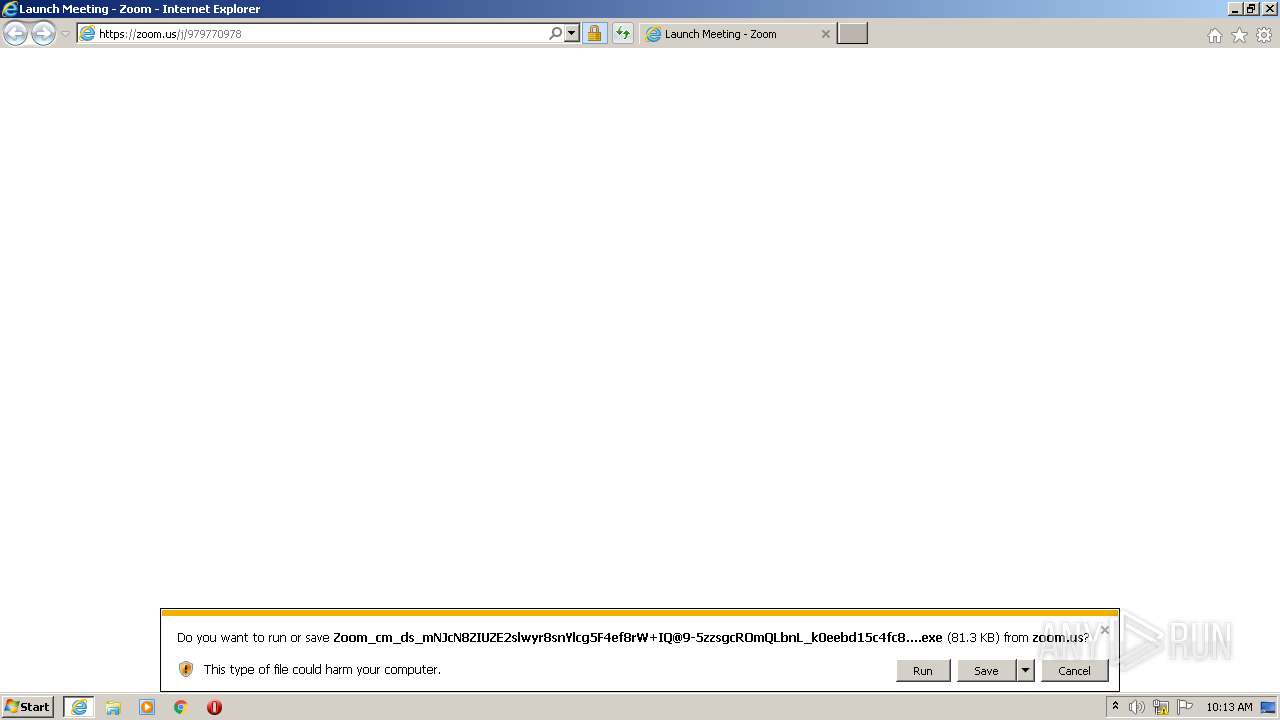
| URL: | https://zoom.us/j/979770978 |
| Full analysis: | https://app.any.run/tasks/c527fd27-ee97-41d3-8557-7d8937234929 |
| Verdict: | Malicious activity |
| Analysis date: | August 08, 2020, 09:13:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 0E128B4F6E103E3EE7419C6E8BA2111A |
| SHA1: | D72968A6B04B76A853F74CFA988ACFDEC2898A33 |
| SHA256: | 0304737BDAF2F27924B36737B73049E86F32E99170B15C206515D0A7BA37F50D |
| SSDEEP: | 3:N88LWSSX:28LWSK |
MALICIOUS
Application was dropped or rewritten from another process
- Zoom_cm_ds_mNJcN8ZIUZE2slwyr8snYlcg5F4ef8rW+IQ@9-5zzsgcROmQLbnL_k0eebd15c4fc89a4c_.exe (PID: 3016)
- Installer.exe (PID: 3968)
- Installer.exe (PID: 2852)
- zm3BCC.tmp (PID: 1984)
- Zoom.exe (PID: 2968)
- Zoom.exe (PID: 280)
Changes settings of System certificates
- Zoom_cm_ds_mNJcN8ZIUZE2slwyr8snYlcg5F4ef8rW+IQ@9-5zzsgcROmQLbnL_k0eebd15c4fc89a4c_.exe (PID: 3016)
Loads dropped or rewritten executable
- Zoom.exe (PID: 280)
- Installer.exe (PID: 3968)
- Zoom.exe (PID: 2968)
SUSPICIOUS
Reads Internet Cache Settings
- Zoom_cm_ds_mNJcN8ZIUZE2slwyr8snYlcg5F4ef8rW+IQ@9-5zzsgcROmQLbnL_k0eebd15c4fc89a4c_.exe (PID: 3016)
Executable content was dropped or overwritten
- iexplore.exe (PID: 2240)
- Zoom_cm_ds_mNJcN8ZIUZE2slwyr8snYlcg5F4ef8rW+IQ@9-5zzsgcROmQLbnL_k0eebd15c4fc89a4c_.exe (PID: 3016)
- Installer.exe (PID: 3968)
- iexplore.exe (PID: 2108)
Creates files in the user directory
- Zoom_cm_ds_mNJcN8ZIUZE2slwyr8snYlcg5F4ef8rW+IQ@9-5zzsgcROmQLbnL_k0eebd15c4fc89a4c_.exe (PID: 3016)
- Zoom.exe (PID: 280)
- Zoom.exe (PID: 2968)
- Installer.exe (PID: 3968)
Application launched itself
- Installer.exe (PID: 3968)
- Zoom.exe (PID: 280)
Changes IE settings (feature browser emulation)
- Installer.exe (PID: 3968)
Creates a software uninstall entry
- Installer.exe (PID: 3968)
Modifies the open verb of a shell class
- Installer.exe (PID: 3968)
Starts application with an unusual extension
- Zoom_cm_ds_mNJcN8ZIUZE2slwyr8snYlcg5F4ef8rW+IQ@9-5zzsgcROmQLbnL_k0eebd15c4fc89a4c_.exe (PID: 3016)
Starts itself from another location
- Zoom_cm_ds_mNJcN8ZIUZE2slwyr8snYlcg5F4ef8rW+IQ@9-5zzsgcROmQLbnL_k0eebd15c4fc89a4c_.exe (PID: 3016)
Adds / modifies Windows certificates
- Zoom_cm_ds_mNJcN8ZIUZE2slwyr8snYlcg5F4ef8rW+IQ@9-5zzsgcROmQLbnL_k0eebd15c4fc89a4c_.exe (PID: 3016)
INFO
Reads internet explorer settings
- iexplore.exe (PID: 2108)
Modifies the phishing filter of IE
- iexplore.exe (PID: 2240)
Changes settings of System certificates
- iexplore.exe (PID: 2240)
Application launched itself
- iexplore.exe (PID: 2240)
Creates files in the user directory
- iexplore.exe (PID: 2108)
Reads settings of System Certificates
- iexplore.exe (PID: 2240)
Reads Internet Cache Settings
- iexplore.exe (PID: 2240)
- iexplore.exe (PID: 2108)
Changes internet zones settings
- iexplore.exe (PID: 2240)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2240)
Dropped object may contain Bitcoin addresses
- Installer.exe (PID: 3968)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
47
Monitored processes
8
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 280 | "C:\Users\admin\AppData\Roaming\Zoom\bin\Zoom.exe" "--url=zoommtg://win.launch?h.domain=zoom.us&h.path=join&confid=dXNzPTdJWk5LMFJkYmtxQ1gyeHhfTTViWEpzZWd4Z0tMNG5pNWtNSHBwSmU2Y2N4SEczM0F3VWFWQk5wSjlzbkpGUU5XM3hDYmhFOE5jbU0uenFfenlMN01Qc01fRXRGVSZ0aWQ9NzBiYzgxMTJjZWZmNDRjN2E0MzlhYzgxMWFmNTQ0ZDE%3D&mcv=0.92.11227.0929&stype=0&zc=64&browser=msie&action=join&confno=979770978" | C:\Users\admin\AppData\Roaming\Zoom\bin\Zoom.exe | Zoom_cm_ds_mNJcN8ZIUZE2slwyr8snYlcg5F4ef8rW+IQ@9-5zzsgcROmQLbnL_k0eebd15c4fc89a4c_.exe | ||||||||||||
User: admin Company: Zoom Video Communications, Inc. Integrity Level: MEDIUM Description: Zoom Meetings Exit code: 0 Version: 5,2,42619,0804 Modules
| |||||||||||||||
| 1984 | "C:\Users\admin\AppData\Local\Temp\zm3BCC.tmp" -DAF8C715436E44649F1312698287E6A5=C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\Zoom_cm_ds_mNJcN8ZIUZE2slwyr8snYlcg5F4ef8rW+IQ@9-5zzsgcROmQLbnL_k0eebd15c4fc89a4c_.exe | C:\Users\admin\AppData\Local\Temp\zm3BCC.tmp | — | Zoom_cm_ds_mNJcN8ZIUZE2slwyr8snYlcg5F4ef8rW+IQ@9-5zzsgcROmQLbnL_k0eebd15c4fc89a4c_.exe | |||||||||||
User: admin Company: Zoom Video Communications, Inc. Integrity Level: MEDIUM Description: Zoom Opener Exit code: 0 Version: 5,0,26188,0601 Modules
| |||||||||||||||
| 2108 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2240 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2240 | "C:\Program Files\Internet Explorer\iexplore.exe" https://zoom.us/j/979770978 | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2852 | "C:\Users\admin\AppData\Roaming\Zoom\ZoomDownload\Installer.exe" /addfwexception --bin_home="C:\Users\admin\AppData\Roaming\Zoom\bin" | C:\Users\admin\AppData\Roaming\Zoom\ZoomDownload\Installer.exe | Installer.exe | ||||||||||||
User: admin Company: Zoom Video Communications, Inc. Integrity Level: HIGH Description: Zoom Installer Exit code: 0 Version: 5,2,42619,0804 Modules
| |||||||||||||||
| 2968 | C:\Users\admin\AppData\Roaming\Zoom\bin\Zoom.exe --action=join --runaszvideo=TRUE | C:\Users\admin\AppData\Roaming\Zoom\bin\Zoom.exe | — | Zoom.exe | |||||||||||
User: admin Company: Zoom Video Communications, Inc. Integrity Level: MEDIUM Description: Zoom Meetings Exit code: 0 Version: 5,2,42619,0804 Modules
| |||||||||||||||
| 3016 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\Zoom_cm_ds_mNJcN8ZIUZE2slwyr8snYlcg5F4ef8rW+IQ@9-5zzsgcROmQLbnL_k0eebd15c4fc89a4c_.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\Zoom_cm_ds_mNJcN8ZIUZE2slwyr8snYlcg5F4ef8rW+IQ@9-5zzsgcROmQLbnL_k0eebd15c4fc89a4c_.exe | iexplore.exe | ||||||||||||
User: admin Company: Zoom Video Communications, Inc. Integrity Level: MEDIUM Description: Zoom Opener Exit code: 0 Version: 5,0,26188,0601 Modules
| |||||||||||||||
| 3968 | "C:\Users\admin\AppData\Roaming\Zoom\ZoomDownload\Installer.exe" ZInstaller --conf.mode=silent --ipc_wnd=66012 | C:\Users\admin\AppData\Roaming\Zoom\ZoomDownload\Installer.exe | Zoom_cm_ds_mNJcN8ZIUZE2slwyr8snYlcg5F4ef8rW+IQ@9-5zzsgcROmQLbnL_k0eebd15c4fc89a4c_.exe | ||||||||||||
User: admin Company: Zoom Video Communications, Inc. Integrity Level: MEDIUM Description: Zoom Installer Exit code: 0 Version: 5,2,42619,0804 Modules
| |||||||||||||||
Total events
1 986
Read events
1 801
Write events
178
Delete events
7
Modification events
| (PID) Process: | (2240) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 1268114496 | |||
| (PID) Process: | (2240) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30829924 | |||
| (PID) Process: | (2240) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2240) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2240) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2240) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2240) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2240) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A3000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2240) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2240) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
147
Suspicious files
67
Text files
26
Unknown types
18
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2108 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabE80D.tmp | — | |
MD5:— | SHA256:— | |||
| 2108 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\TarE80E.tmp | — | |
MD5:— | SHA256:— | |||
| 2108 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\TFN6XOL5.txt | — | |
MD5:— | SHA256:— | |||
| 2108 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\P8UOZUEH.txt | — | |
MD5:— | SHA256:— | |||
| 2108 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\4UOSPMDU.txt | — | |
MD5:— | SHA256:— | |||
| 2108 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\G5G7B4FS.txt | — | |
MD5:— | SHA256:— | |||
| 2108 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\8HEWV6YI.txt | — | |
MD5:— | SHA256:— | |||
| 2240 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2108 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\Zoom_cm_ds_mNJcN8ZIUZE2slwyr8snYlcg5F4ef8rW+IQ@9-5zzsgcROmQLbnL_k0eebd15c4fc89a4c_.exe.1ep0sq9.partial | — | |
MD5:— | SHA256:— | |||
| 2240 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\Zoom_cm_ds_mNJcN8ZIUZE2slwyr8snYlcg5F4ef8rW+IQ@9-5zzsgcROmQLbnL_k0eebd15c4fc89a4c_.exe.1ep0sq9.partial:Zone.Identifier | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
19
TCP/UDP connections
33
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2108 | iexplore.exe | GET | 200 | 23.37.43.27:80 | http://s.symcd.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS56bKHAoUD%2BOyl%2B0LhPg9JxyQm4gQUf9Nlp8Ld7LvwMAnzQzn6Aq8zMTMCEGMYDTj7gJd4qdA1oxYY%2BEA%3D | NL | der | 1.71 Kb | shared |
2108 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAH9o%2BtuynXIiEOLckvPvJE%3D | US | der | 471 b | whitelisted |
2108 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://crl.comodoca.com/AAACertificateServices.crl | US | der | 506 b | whitelisted |
2108 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAyO4MkNaokViAQGHuJB%2Ba8%3D | US | der | 471 b | whitelisted |
2108 | iexplore.exe | GET | 200 | 23.37.43.27:80 | http://s.symcd.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS56bKHAoUD%2BOyl%2B0LhPg9JxyQm4gQUf9Nlp8Ld7LvwMAnzQzn6Aq8zMTMCEGMYDTj7gJd4qdA1oxYY%2BEA%3D | NL | der | 1.71 Kb | shared |
2108 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca4.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrJdiQ%2Ficg9B19asFe73bPYs%2BreAQUdXGnGUgZvJ2d6kFH35TESHeZ03kCEFslzmkHxCZVZtM5DJmpVK0%3D | US | der | 314 b | whitelisted |
2108 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQQX6Z6gAidtSefNc6DC0OInqPHDQQUD4BhHIIxYdUvKOeNRji0LOHG2eICEAiD6oCkBJ7Dc0p019Hmj9U%3D | US | der | 471 b | whitelisted |
2108 | iexplore.exe | GET | 200 | 13.35.253.5:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | US | der | 1.51 Kb | whitelisted |
2108 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca4.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTOpjOEf6LG1z52jqAxwDlTxoaOCgQUQAlhZ%2FC8g3FP3hIILG%2FU1Ct2PZYCEQCqFSHgSXaTfCgEVqEiXGzF | US | der | 280 b | whitelisted |
2108 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAyO4MkNaokViAQGHuJB%2Ba8%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2108 | iexplore.exe | 23.37.43.27:80 | s.symcd.com | Akamai Technologies, Inc. | NL | whitelisted |
2108 | iexplore.exe | 18.205.93.255:443 | zoom.us | — | US | unknown |
2108 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2108 | iexplore.exe | 13.35.253.153:443 | d24cgw3uvb9a9h.cloudfront.net | — | US | unknown |
— | — | 143.204.201.16:443 | static.ada.support | — | US | shared |
2108 | iexplore.exe | 143.204.208.165:80 | o.ss2.us | — | US | malicious |
2108 | iexplore.exe | 13.35.253.198:80 | ocsp.rootg2.amazontrust.com | — | US | whitelisted |
280 | Zoom.exe | 173.231.81.230:3478 | — | Affiniti, LLC | US | unknown |
2108 | iexplore.exe | 3.80.20.234:443 | nws.zoom.us | — | US | unknown |
3016 | Zoom_cm_ds_mNJcN8ZIUZE2slwyr8snYlcg5F4ef8rW+IQ@9-5zzsgcROmQLbnL_k0eebd15c4fc89a4c_.exe | 18.205.93.255:443 | zoom.us | — | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
zoom.us |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
static.ada.support |
| whitelisted |
static.zdassets.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
d24cgw3uvb9a9h.cloudfront.net |
| shared |
s.symcd.com |
| shared |
nws.zoom.us |
| whitelisted |
www.bing.com |
| whitelisted |
api.bing.com |
| whitelisted |
Threats
Process | Message |
|---|---|
Installer.exe | |
Installer.exe | C:\Users\admin\AppData\Roaming\Zoom\zoom_install_src |
Installer.exe | C:\Users\admin\AppData\Roaming\Zoom\zoom_install_src |
Installer.exe | |
Installer.exe | C:\Users\admin\AppData\Roaming\Zoom\uninstall |
Installer.exe | [ProductPathHelper::RecursiveRemoveDirA] Path is: |
Installer.exe | [ProductPathHelper::RecursiveRemoveDirA] Path is: |
Installer.exe | |
Installer.exe | C:\Users\admin\AppData\Roaming\Zoom\bin |
Installer.exe | [CZoomProductPathHelper::RecursiveRemoveDirA] Path is: |