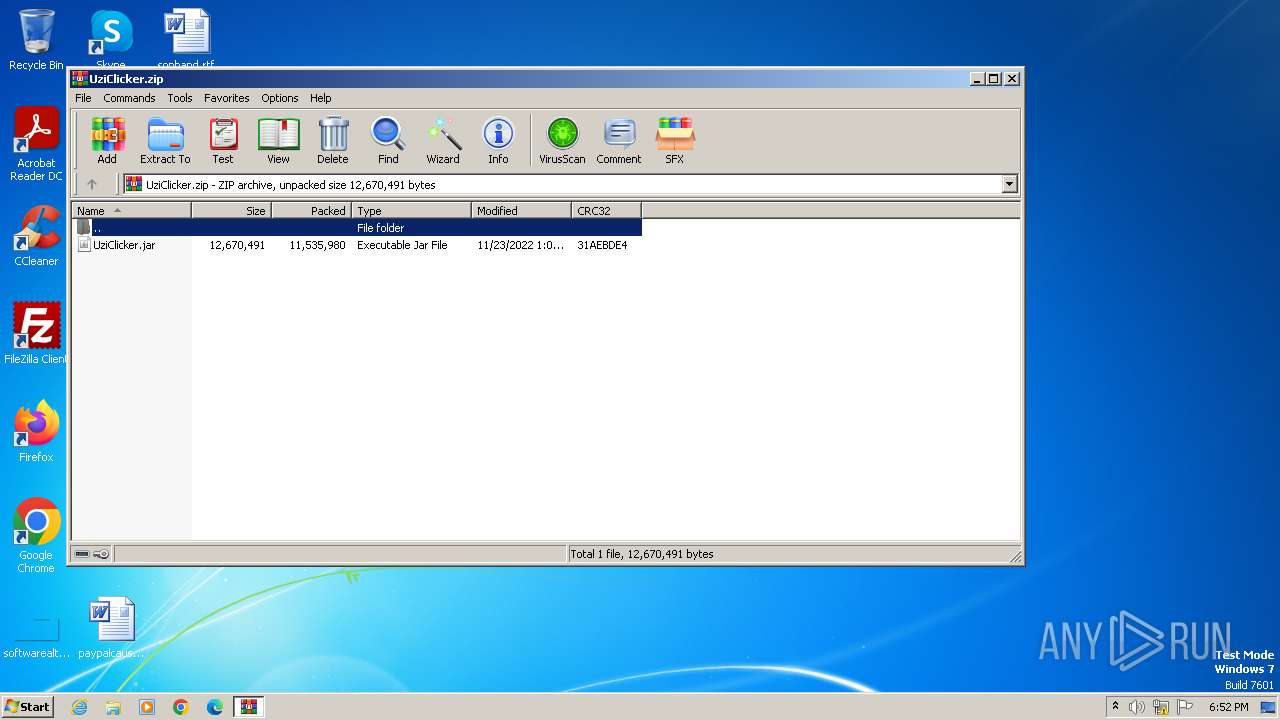
| File name: | UziClicker.zip |
| Full analysis: | https://app.any.run/tasks/7c347191-52cd-4c9d-a4f3-32903ebdd0bc |
| Verdict: | Malicious activity |
| Analysis date: | November 06, 2023, 18:52:44 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 3D81B041743D352A513DCE0530DB3F16 |
| SHA1: | 9B8116E2211C76AFCE9F4A6BC31057897EADB874 |
| SHA256: | 030469BA7CF25957784E2E1D66DE2BF39961704BA8B6B6B60E5E7B8F96905C6B |
| SSDEEP: | 98304:JZrLYoh3O6ubNfdDSESmTUSOT5T7H+enXLRacGtYzKv0L/+G8valMqRO/b3zTtYQ:iJ2xNPJ9AuX4L5MCDreqlD9mw |
MALICIOUS
Drops the executable file immediately after the start
- javaw.exe (PID: 3860)
- javaw.exe (PID: 3988)
SUSPICIOUS
Drops a system driver (possible attempt to evade defenses)
- javaw.exe (PID: 3860)
INFO
Checks supported languages
- javaw.exe (PID: 3124)
- java.exe (PID: 3400)
- javaw.exe (PID: 3860)
- javaw.exe (PID: 3988)
Create files in a temporary directory
- javaw.exe (PID: 3124)
- java.exe (PID: 3400)
- javaw.exe (PID: 3860)
- javaw.exe (PID: 3988)
Manual execution by a user
- javaw.exe (PID: 3124)
- javaw.exe (PID: 3860)
- javaw.exe (PID: 3988)
Reads the computer name
- javaw.exe (PID: 3124)
- java.exe (PID: 3400)
- javaw.exe (PID: 3860)
- javaw.exe (PID: 3988)
Creates files or folders in the user directory
- javaw.exe (PID: 3124)
- java.exe (PID: 3400)
- javaw.exe (PID: 3860)
Creates files in the program directory
- javaw.exe (PID: 3124)
Reads the machine GUID from the registry
- javaw.exe (PID: 3860)
- javaw.exe (PID: 3988)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2022:11:23 01:06:10 |
| ZipCRC: | 0x31aebde4 |
| ZipCompressedSize: | 11535980 |
| ZipUncompressedSize: | 12670491 |
| ZipFileName: | UziClicker.jar |
Total processes
43
Monitored processes
6
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3124 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -jar "C:\Users\admin\Desktop\UziClicker.jar" | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | — | explorer.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 3400 | java -jar C:\Users\admin\AppData\Roaming\uziclicker\UziClicker.jar -create C:\Users\admin\Desktop\UziClicker.jar | C:\Program Files\Java\jre1.8.0_271\bin\java.exe | — | javaw.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 3460 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\UziClicker.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3512 | C:\Windows\system32\icacls.exe C:\ProgramData\Oracle\Java\.oracle_jre_usage /grant "everyone":(OI)(CI)M | C:\Windows\System32\icacls.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3860 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -jar "C:\Users\admin\AppData\Roaming\uziclicker\UziClicker.jar" | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | — | explorer.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 3988 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -jar "C:\Users\admin\AppData\Roaming\uziclicker\UziClicker.jar" | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | explorer.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.2710.9 Modules
| |||||||||||||||
Total events
2 739
Read events
2 729
Write events
10
Delete events
0
Modification events
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3860) javaw.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: Explorer.EXE | |||
| (PID) Process: | (3988) javaw.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: javaw.exe | |||
Executable files
10
Suspicious files
8
Text files
18
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3460 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3460.26616\UziClicker.jar | compressed | |
MD5:03B9133BB7AB3E465B8DE753BF5FEFB4 | SHA256:EA6A8907D64B735E2848CE2CD5BCF8CE5D73FA681CBD8486CA7E7D2A2E15FB5A | |||
| 3124 | javaw.exe | C:\ProgramData\Oracle\Java\.oracle_jre_usage\17dfc292991c8061.timestamp | text | |
MD5:C2A018322C4FA20BF62A482E5747972E | SHA256:A8FA8AE972755C3BF82F6A7658B38D49EEE0779AE6E2265A2DEBF7B10D1FC2BC | |||
| 3400 | java.exe | C:\Users\admin\Desktop\UziClicker.lnk | binary | |
MD5:76A85AE5EFB30CEE18978D08CCF35C50 | SHA256:6FFEF19A052C64F5819DE53E504A4D23DB2648241DFA559DA233D99DAC830CFD | |||
| 3860 | javaw.exe | C:\Users\admin\AppData\Roaming\uziclicker\uzilib.zip | compressed | |
MD5:87C2B93723F1EF09E004425466B7BF50 | SHA256:D68DE08D09449A148516F4FD4D3BA55B038D59E9DB2F2ED26C96FB6284EB7010 | |||
| 3124 | javaw.exe | C:\Users\admin\AppData\Roaming\uziclicker\UziClicker.jar | compressed | |
MD5:03B9133BB7AB3E465B8DE753BF5FEFB4 | SHA256:EA6A8907D64B735E2848CE2CD5BCF8CE5D73FA681CBD8486CA7E7D2A2E15FB5A | |||
| 3860 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio2634303723408405113.tmp | image | |
MD5:116370D071269A27C9DCDB5F943FD25E | SHA256:5787EA5A88C919D70926E3F79E5179B227D2F346AB700A9A3EF0C3D857B2EA5B | |||
| 3400 | java.exe | C:\Users\admin\AppData\Roaming\uziclicker\favicon.ico | image | |
MD5:5B3E8FD207D3AD0A0DBA312845DB53BD | SHA256:7A777537B2AEC669E1A896C6565CEEB200A092F2222DE06E14FF929EEDFB38EF | |||
| 3860 | javaw.exe | C:\Users\admin\AppData\Local\Temp\+~JF8441009812055181866.tmp | binary | |
MD5:F61A4EB27371B7453BF5B12AB3648B9E | SHA256:E554DB189B5D944EF0E6F98EE0E4E8C75F69E95315DC9F4AE0C616A8756A2BA4 | |||
| 3860 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio5408711859515339777.tmp | image | |
MD5:048D79A74397B902F13AC77FF1BC90BC | SHA256:E6698CA7B43645215B88E2BEB3DACC008F53359EF71A0B15543092EEBE4C735E | |||
| 3860 | javaw.exe | C:\Users\admin\AppData\Local\Temp\+~JF3834333069500014516.tmp | binary | |
MD5:8B6AF8E5E8324EDFD77AF8B3B35D7F9C | SHA256:78F127277756AE464F4EB665CE214CB6315746F6F4193E95B31F18F4B3E97527 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
3
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
868 | svchost.exe | 95.101.148.135:80 | — | Akamai International B.V. | NL | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
868 | svchost.exe | 88.221.124.138:80 | armmf.adobe.com | AKAMAI-AS | DE | unknown |
3988 | javaw.exe | 188.114.97.3:443 | uziclicker.pl | CLOUDFLARENET | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
armmf.adobe.com |
| whitelisted |
uziclicker.pl |
| whitelisted |