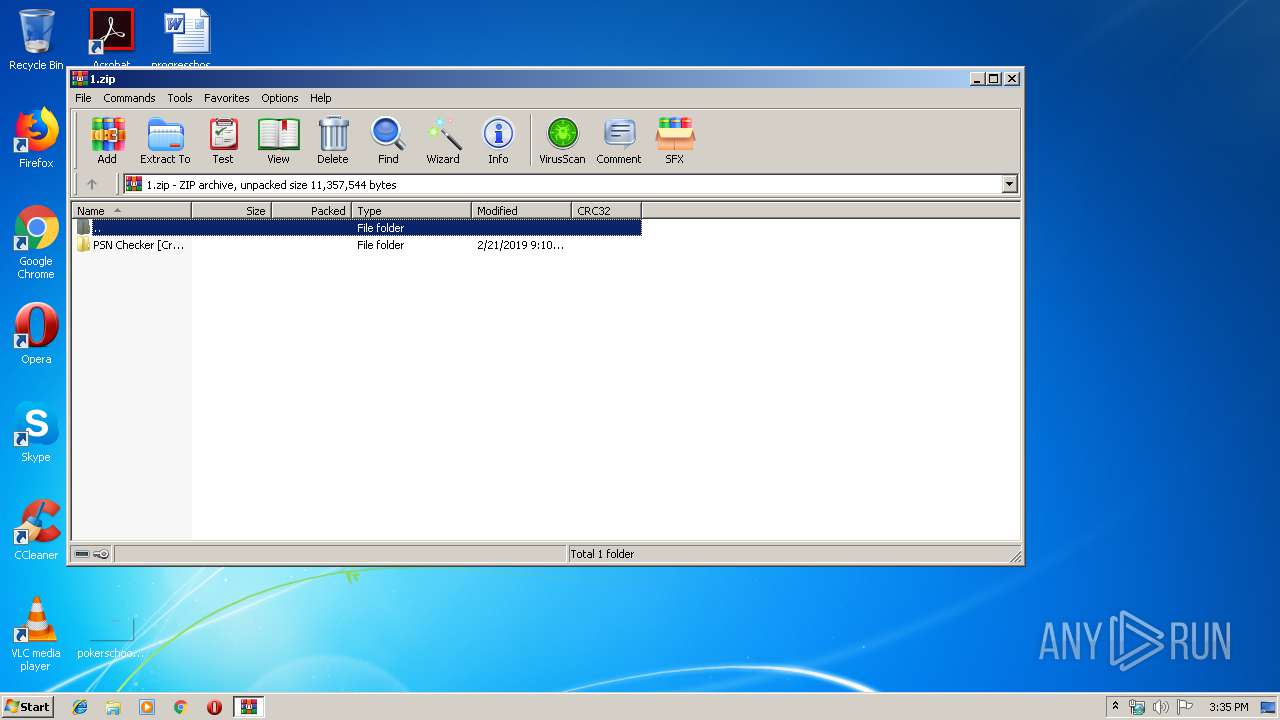
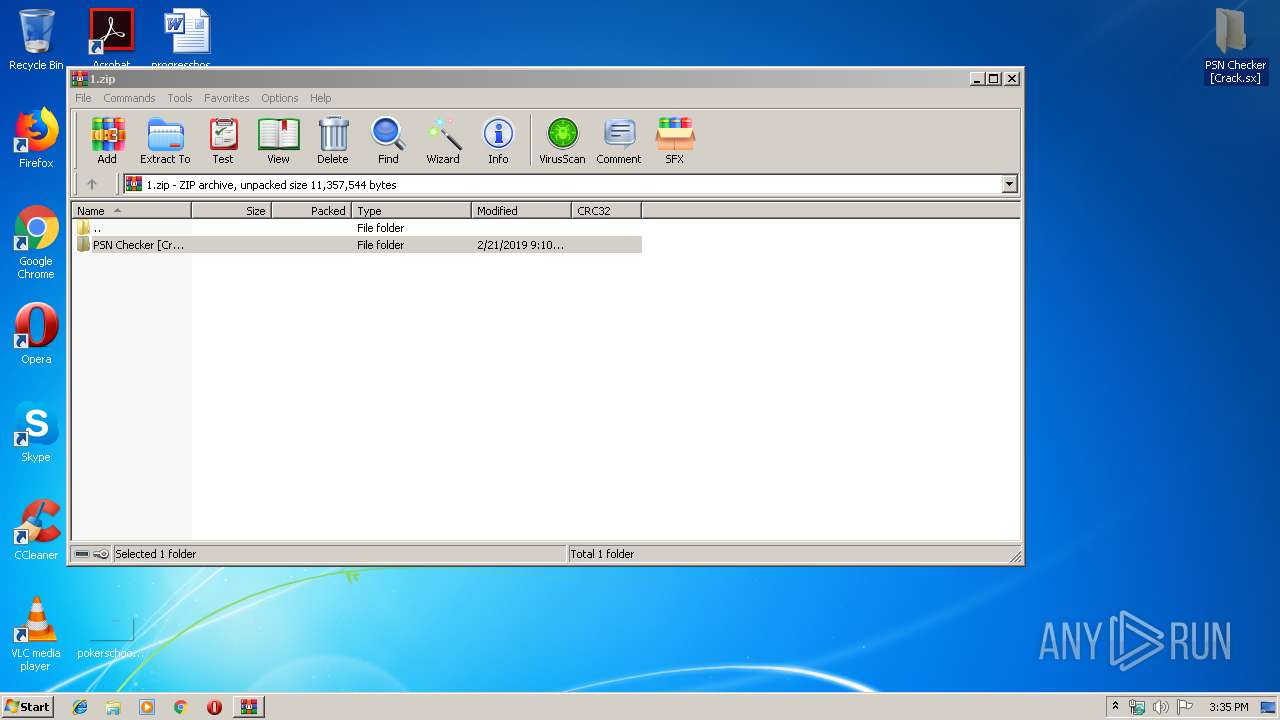
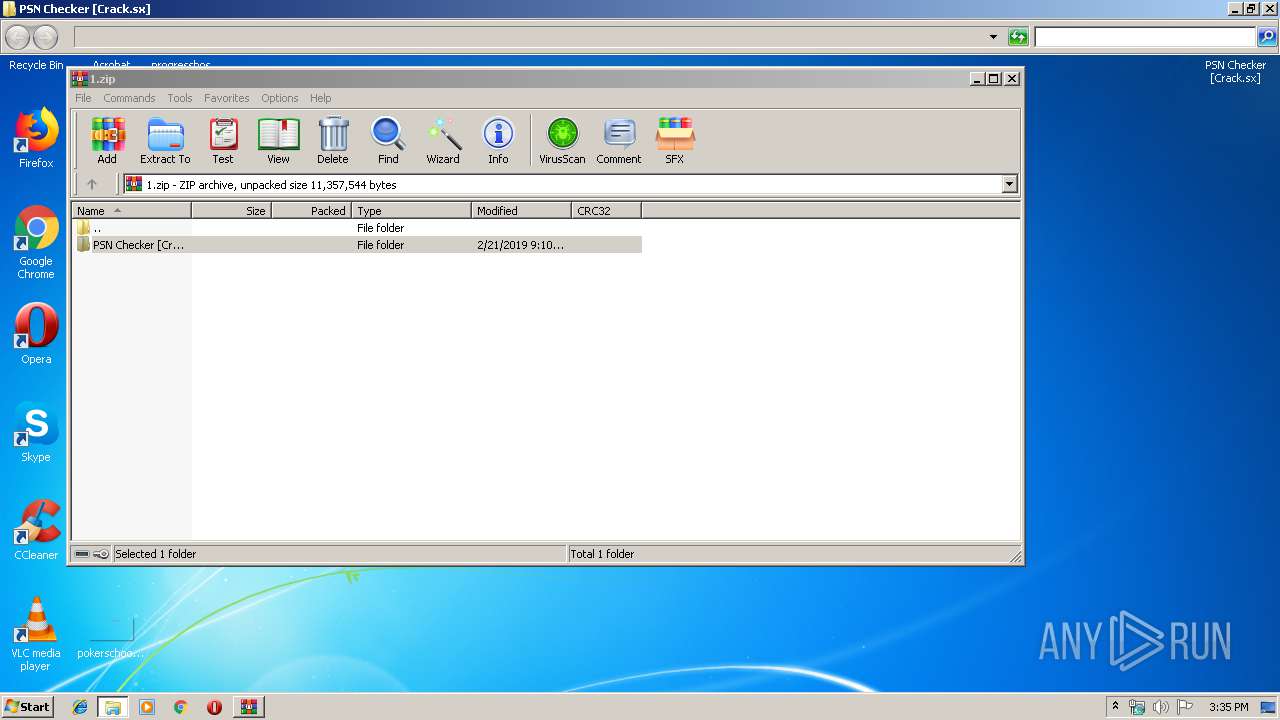
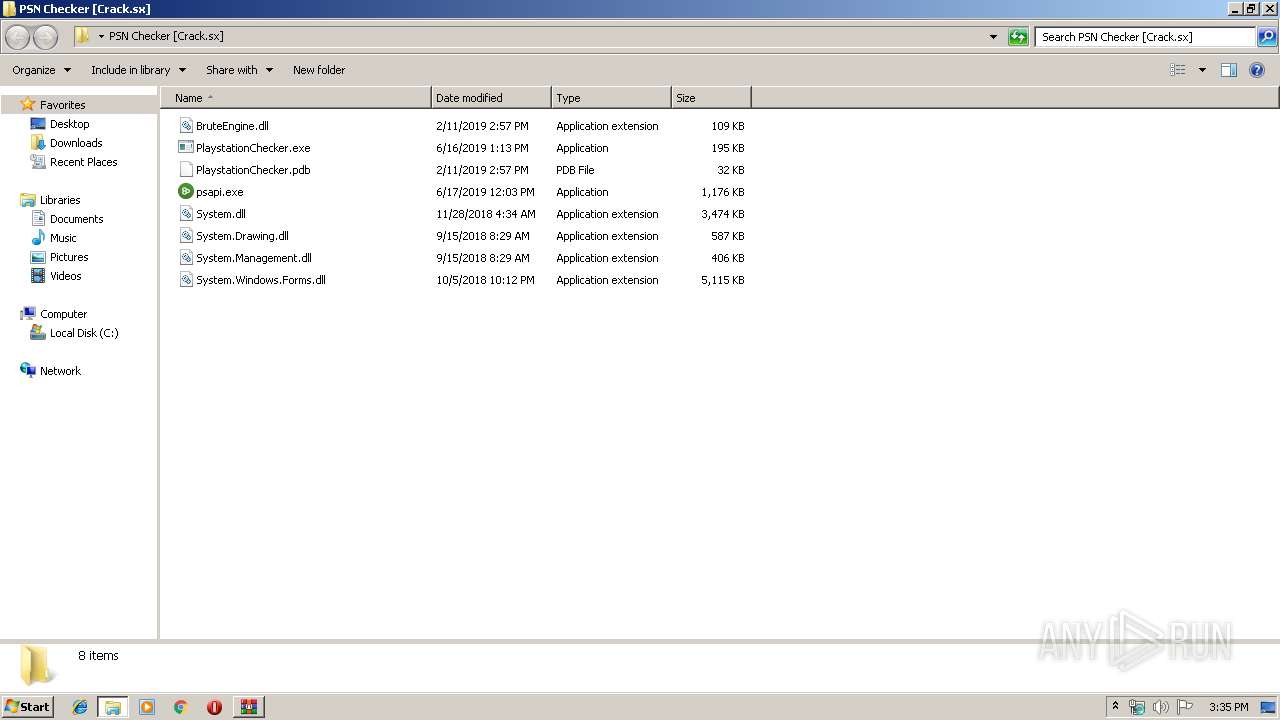
| File name: | 1.zip |
| Full analysis: | https://app.any.run/tasks/fb0f35c6-93c1-4448-ac40-d41e4f1d96ca |
| Verdict: | Malicious activity |
| Analysis date: | July 11, 2019, 14:34:33 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | 80F644C89E7F51A2F946ACFB6B0B98BC |
| SHA1: | 3B7ADF85519EB21294DD155ECA285939303D9D85 |
| SHA256: | 030252E31AB244710DB8CB6E7F1E33A5B36D1B3DE94189770001B00D85772967 |
| SSDEEP: | 98304:ZrTNT+9pShnPgbcfbQ3d5aJJzt6vIDOay9Yphe:RpT+ShnP8cfbwdm/oaMYphe |
MALICIOUS
Writes to a start menu file
- psapi.exe (PID: 2236)
- psapi.exe (PID: 3696)
Application was dropped or rewritten from another process
- NETcore.exe (PID: 3624)
- NETcore.exe (PID: 3172)
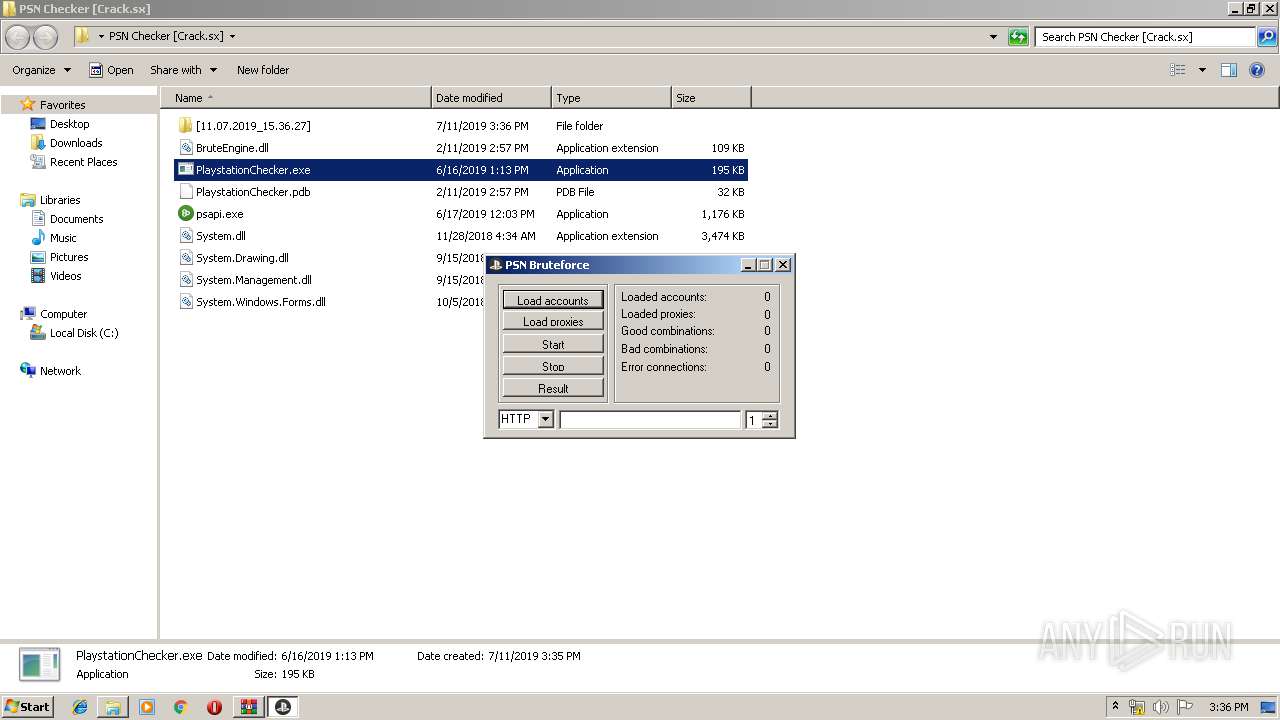
- PlaystationChecker.exe (PID: 1448)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 2436)
- PlaystationChecker.exe (PID: 1448)
Changes settings of System certificates
- psapi.exe (PID: 2236)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 300)
- psapi.exe (PID: 2236)
Creates files in the user directory
- psapi.exe (PID: 2236)
Adds / modifies Windows certificates
- psapi.exe (PID: 2236)
INFO
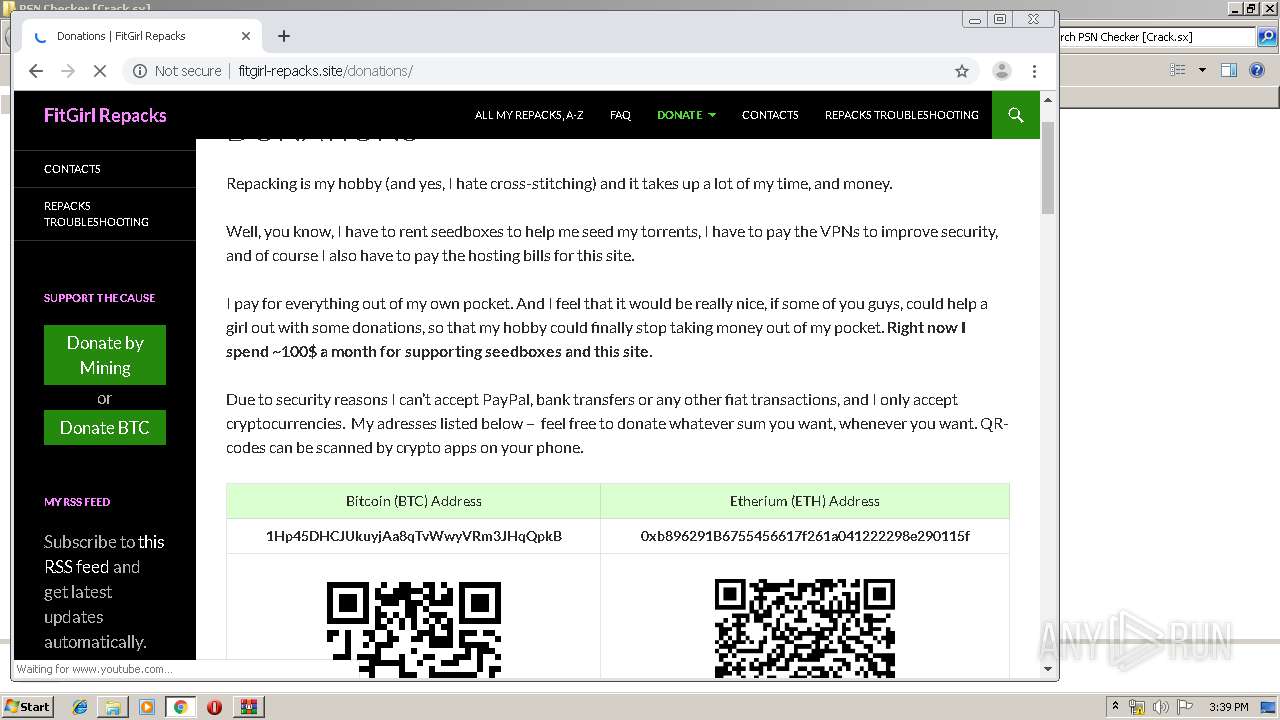
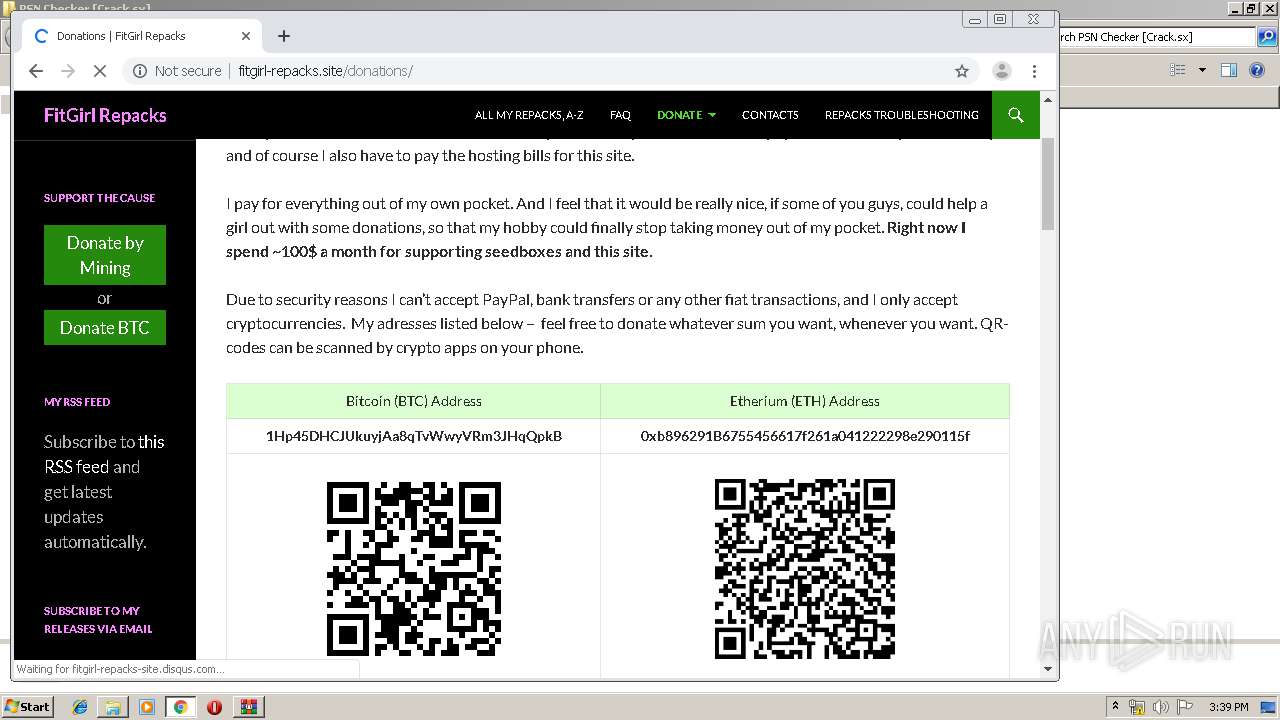
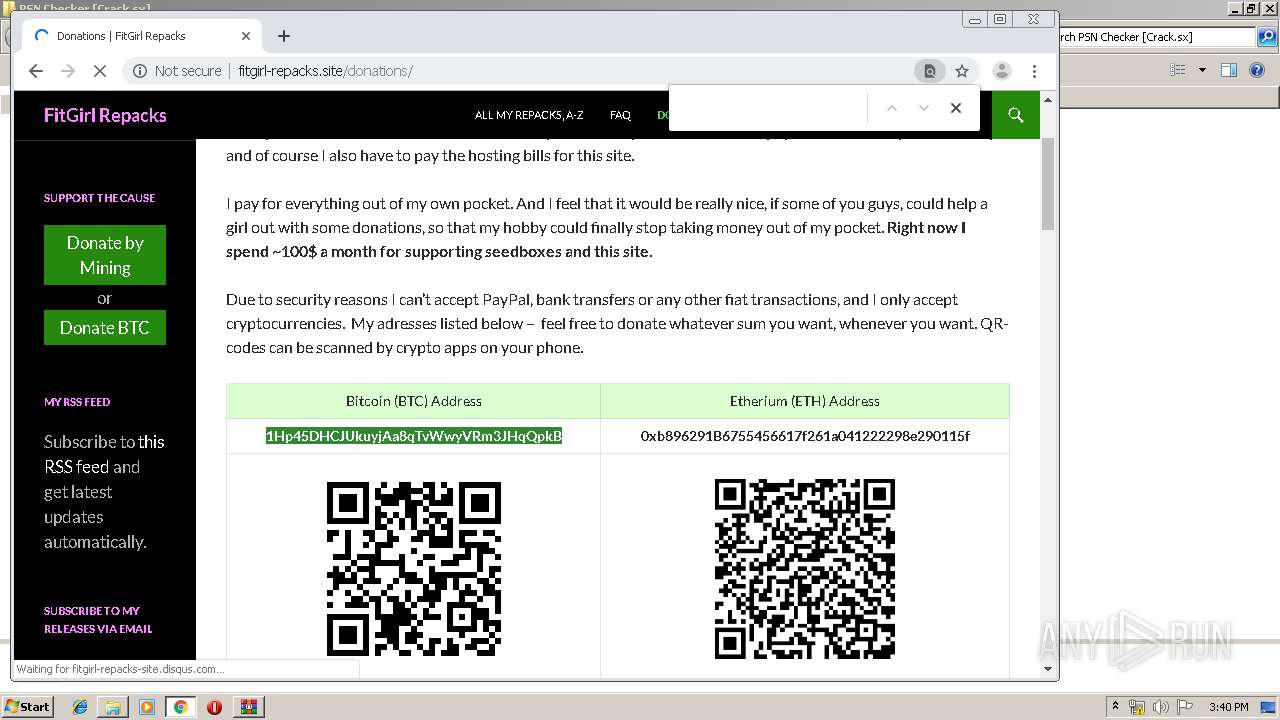
Dropped object may contain Bitcoin addresses
- psapi.exe (PID: 2236)
Manual execution by user
- psapi.exe (PID: 2236)
- PlaystationChecker.exe (PID: 1448)
- chrome.exe (PID: 2252)
Application launched itself
- chrome.exe (PID: 2252)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .kmz | | | Google Earth saved working session (60) |
|---|---|---|
| .zip | | | ZIP compressed archive (40) |
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2019:02:21 21:10:19 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | PSN Checker [Crack.sx]/ |
Total processes
74
Monitored processes
36
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 300 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\1.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 648 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1008,444346848477461496,9227732460517696668,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=17327633991682611906 --renderer-client-id=8 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3332 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 912 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1008,444346848477461496,9227732460517696668,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=4674070842931196061 --renderer-client-id=26 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4304 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1144 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=2836 --on-initialized-event-handle=312 --parent-handle=316 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1160 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1008,444346848477461496,9227732460517696668,131072 --enable-features=PasswordImport --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=8107517643422782565 --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2228 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1216 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1008,444346848477461496,9227732460517696668,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=15475907202354397143 --mojo-platform-channel-handle=988 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
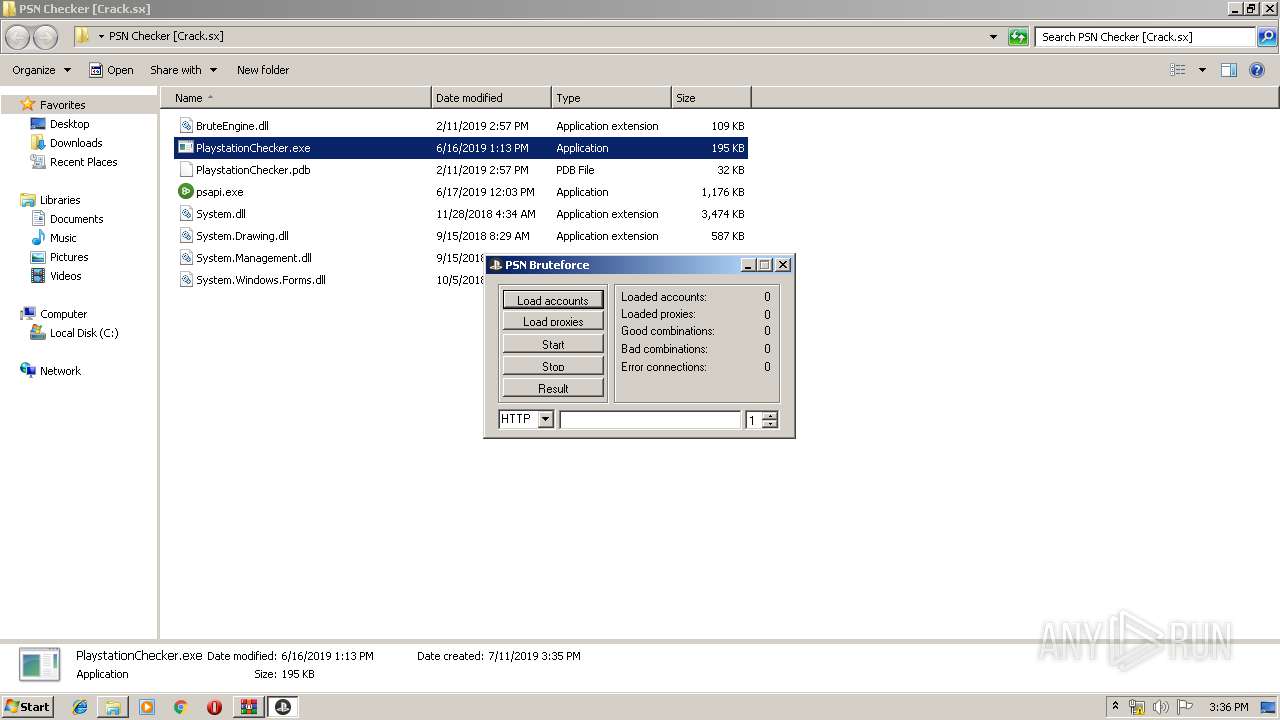
| 1448 | "C:\Users\admin\Desktop\PSN Checker [Crack.sx]\PlaystationChecker.exe" | C:\Users\admin\Desktop\PSN Checker [Crack.sx]\PlaystationChecker.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: PlaystationChecker Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1484 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1008,444346848477461496,9227732460517696668,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=4418173835605805675 --mojo-platform-channel-handle=4000 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1844 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1008,444346848477461496,9227732460517696668,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=10206229154753039088 --mojo-platform-channel-handle=3844 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2060 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1008,444346848477461496,9227732460517696668,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=15071612885314048709 --mojo-platform-channel-handle=4196 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
1 892
Read events
1 772
Write events
115
Delete events
5
Modification events
| (PID) Process: | (300) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (300) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (300) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\70\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (300) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\1.zip | |||
| (PID) Process: | (300) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (300) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (300) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (300) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2236) psapi.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\psapi_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2236) psapi.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\psapi_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
6
Suspicious files
68
Text files
210
Unknown types
11
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 300 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa300.22389\PSN Checker [Crack.sx]\System.Windows.Forms.dll | — | |
MD5:— | SHA256:— | |||
| 300 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa300.22389\PSN Checker [Crack.sx]\psapi.exe | — | |
MD5:— | SHA256:— | |||
| 2236 | psapi.exe | C:\Users\admin\AppData\Roaming\DOTNET\Icon.ico | image | |
MD5:— | SHA256:— | |||
| 300 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa300.22389\PSN Checker [Crack.sx]\System.Management.dll | executable | |
MD5:— | SHA256:— | |||
| 300 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa300.22389\PSN Checker [Crack.sx]\PlaystationChecker.exe | executable | |
MD5:— | SHA256:— | |||
| 2236 | psapi.exe | C:\Users\admin\AppData\Roaming\DOTNET\data.dat | text | |
MD5:— | SHA256:— | |||
| 2236 | psapi.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Discord.lnk | lnk | |
MD5:— | SHA256:— | |||
| 2236 | psapi.exe | C:\Users\admin\AppData\Roaming\DOTNET\NETcore.exe | executable | |
MD5:— | SHA256:— | |||
| 2252 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\2923461f-0f1e-47b6-9fe9-636cc4e01cd5.tmp | — | |
MD5:— | SHA256:— | |||
| 300 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa300.22389\PSN Checker [Crack.sx]\PlaystationChecker.pdb | pdb | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
82
TCP/UDP connections
58
DNS requests
67
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2324 | chrome.exe | GET | 302 | 216.58.206.14:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOWVmQUFXS041NV9ZVXlJVWwxbGc5TUM4dw/7519.422.0.3_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx | US | html | 516 b | whitelisted |
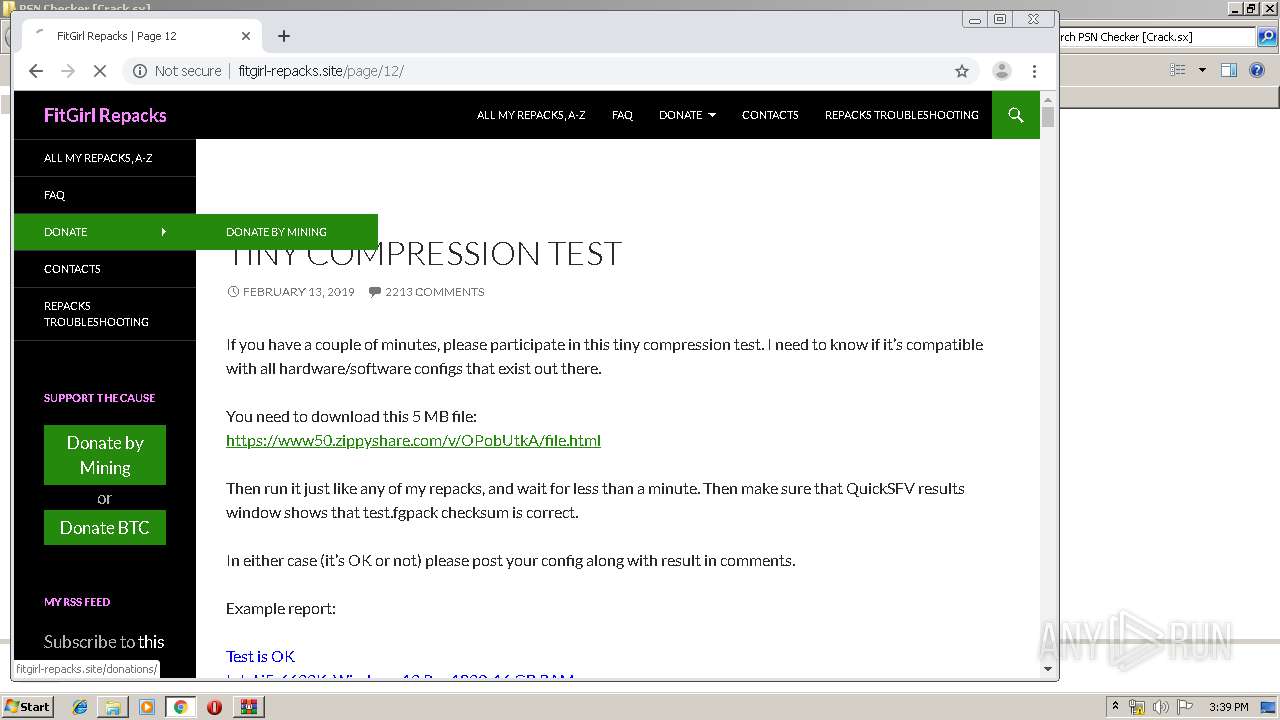
2324 | chrome.exe | GET | 200 | 104.24.126.50:80 | http://fitgirl-repacks.site/page/12/ | US | html | 23.6 Kb | suspicious |
2324 | chrome.exe | GET | 200 | 104.24.126.50:80 | http://fitgirl-repacks.site/wp-content/themes/twentyfourteen/style.css?ver=5.0.2 | US | text | 14.4 Kb | suspicious |
2324 | chrome.exe | GET | 200 | 104.27.179.224:80 | http://s01.riotpixels.net/data/21/5b/215bfd5a-d7b3-4b61-86d6-5d5bcc69bc07.jpg.240p.jpg | US | image | 6.20 Kb | suspicious |
2324 | chrome.exe | GET | 200 | 104.24.126.50:80 | http://fitgirl-repacks.site/wp-content/uploads/2019/02/error.png | US | image | 20.5 Kb | suspicious |
2324 | chrome.exe | GET | 200 | 104.24.126.50:80 | http://fitgirl-repacks.site/wp-includes/js/jquery/jquery.js?ver=1.12.4 | US | text | 33.2 Kb | suspicious |
2324 | chrome.exe | GET | 200 | 104.24.126.50:80 | http://fitgirl-repacks.site/wp-content/plugins/jetpack/modules/theme-tools/compat/twentyfourteen.css?ver=5.5.1 | US | text | 1.62 Kb | suspicious |
2324 | chrome.exe | GET | 200 | 104.24.126.50:80 | http://fitgirl-repacks.site/wp-content/plugins/jetpack/css/jetpack.css?ver=5.5.1 | US | text | 11.7 Kb | suspicious |
2324 | chrome.exe | GET | 200 | 104.24.126.50:80 | http://fitgirl-repacks.site/wp-includes/js/jquery/jquery-migrate.min.js?ver=1.4.1 | US | text | 3.92 Kb | suspicious |
2324 | chrome.exe | GET | 200 | 173.194.188.102:80 | http://r1---sn-4g5ednss.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOWVmQUFXS041NV9ZVXlJVWwxbGc5TUM4dw/7519.422.0.3_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx?cms_redirect=yes&mip=185.183.107.227&mm=28&mn=sn-4g5ednss&ms=nvh&mt=1562855902&mv=m&mvi=0&pl=24&shardbypass=yes | US | crx | 862 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2324 | chrome.exe | 172.217.21.206:443 | consent.google.com | Google Inc. | US | whitelisted |
2324 | chrome.exe | 172.217.16.138:443 | translate.googleapis.com | Google Inc. | US | whitelisted |
— | — | 216.58.206.2:443 | adservice.google.at | Google Inc. | US | whitelisted |
2236 | psapi.exe | 151.101.0.133:443 | raw.githubusercontent.com | Fastly | US | malicious |
2236 | psapi.exe | 196.40.24.242:443 | www.bvs.sa.cr | RADIOGRAFICA COSTARRICENSE | CR | unknown |
3696 | psapi.exe | 151.101.0.133:443 | raw.githubusercontent.com | Fastly | US | malicious |
2324 | chrome.exe | 216.58.205.227:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2324 | chrome.exe | 216.58.208.45:443 | accounts.google.com | Google Inc. | US | whitelisted |
2324 | chrome.exe | 216.58.208.35:443 | www.google.com.ua | Google Inc. | US | whitelisted |
2324 | chrome.exe | 172.217.16.142:443 | clients2.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
raw.githubusercontent.com |
| shared |
www.bvs.sa.cr |
| unknown |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com.ua |
| whitelisted |
clients2.google.com |
| whitelisted |
www.google.com |
| malicious |
www.google.at |
| whitelisted |
clients2.googleusercontent.com |
| whitelisted |
redirector.gvt1.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1064 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .su TLD (Soviet Union) Often Malware Related |