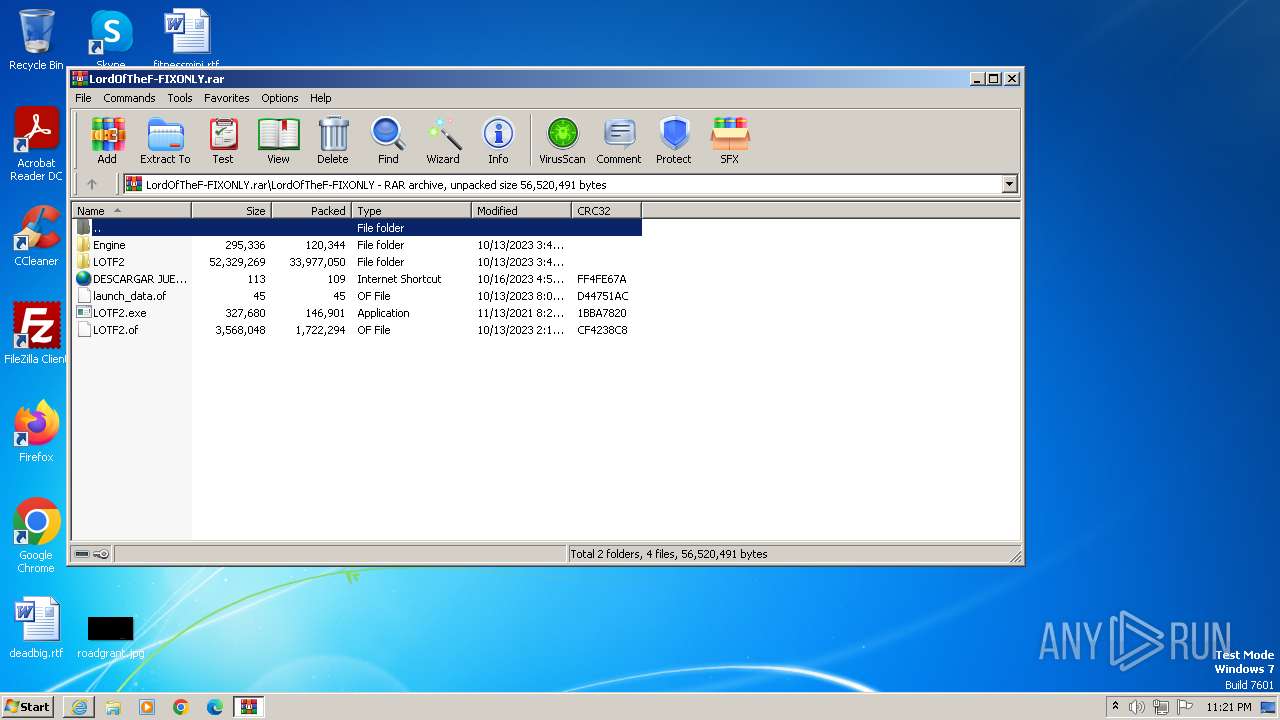
| URL: | https://pixeldrain.com/api/file/x3E2QvYB?download |
| Full analysis: | https://app.any.run/tasks/0721535c-3fa4-4c1a-9a28-762025aa0087 |
| Verdict: | Malicious activity |
| Analysis date: | October 21, 2023, 22:21:09 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| SHA1: | F01FD1E715DD4B729E4D59108D713D07AF544FA9 |
| SHA256: | 02E3AAA2503EC7E72B27B1DC98419AD8895EFB67B9889C72195A86A76DAB13AC |
| SSDEEP: | 3:N8Icl/GK09Sq1oo:2IG/d0v |
MALICIOUS
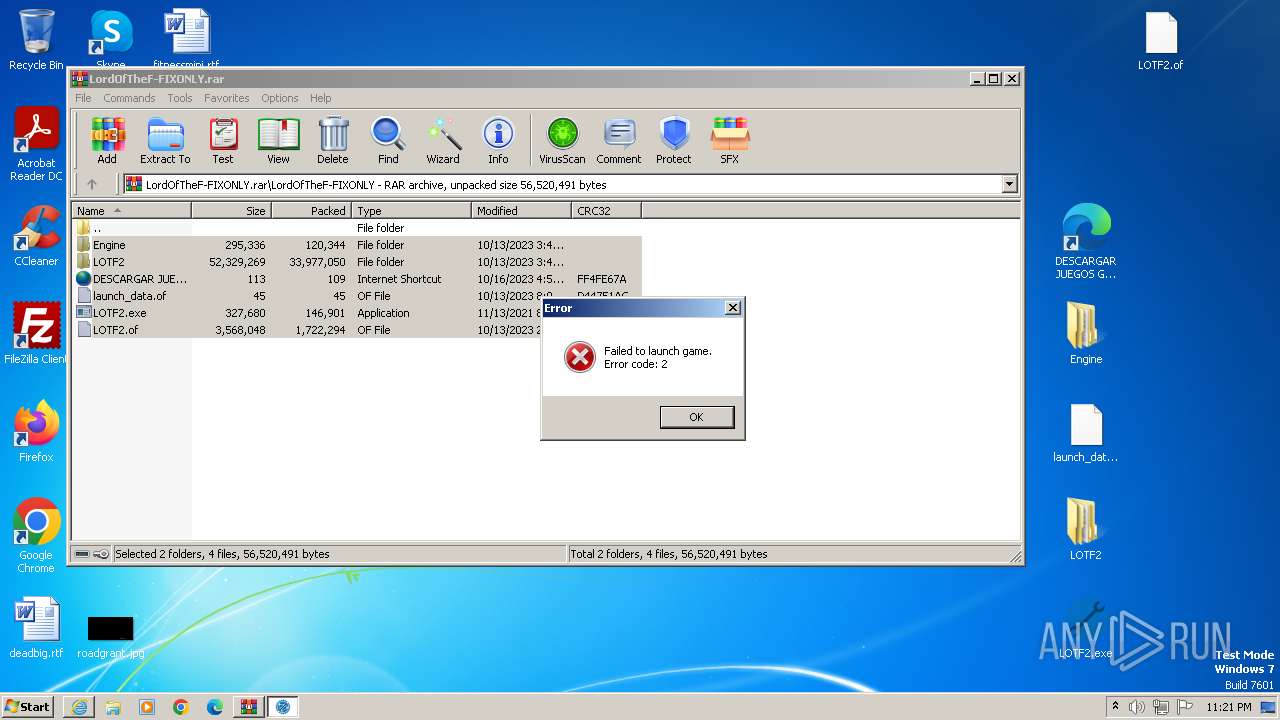
Application was dropped or rewritten from another process
- LOTF2.exe (PID: 2900)
SUSPICIOUS
The process creates files with name similar to system file names
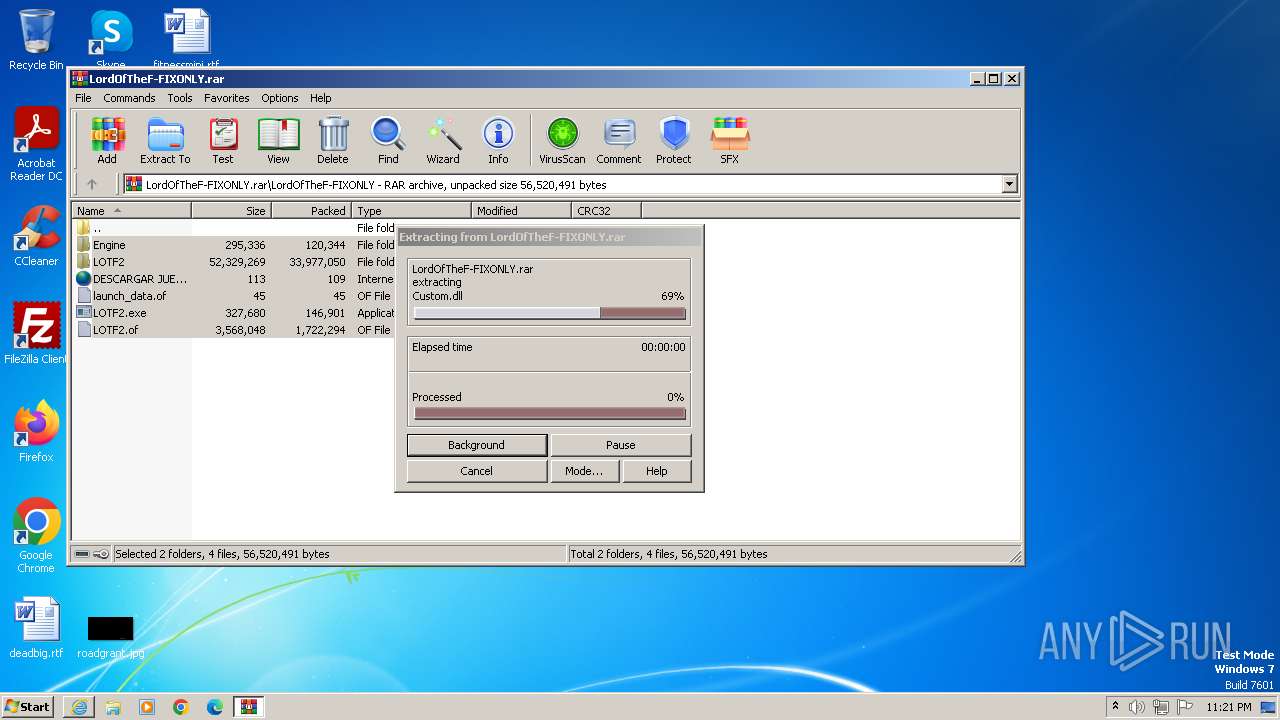
- WinRAR.exe (PID: 2556)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 2556)
- iexplore.exe (PID: 3852)
Application launched itself
- iexplore.exe (PID: 3852)
Checks supported languages
- LOTF2.exe (PID: 2900)
Manual execution by a user
- LOTF2.exe (PID: 2900)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2556)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
41
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
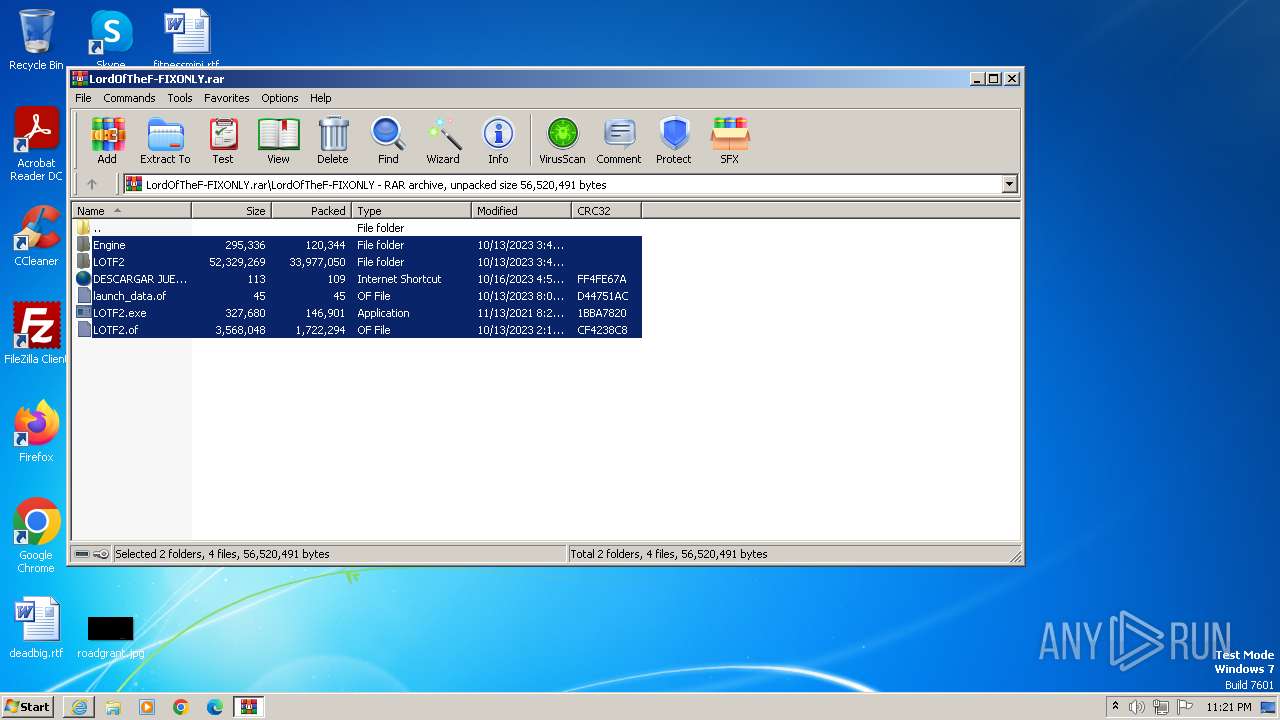
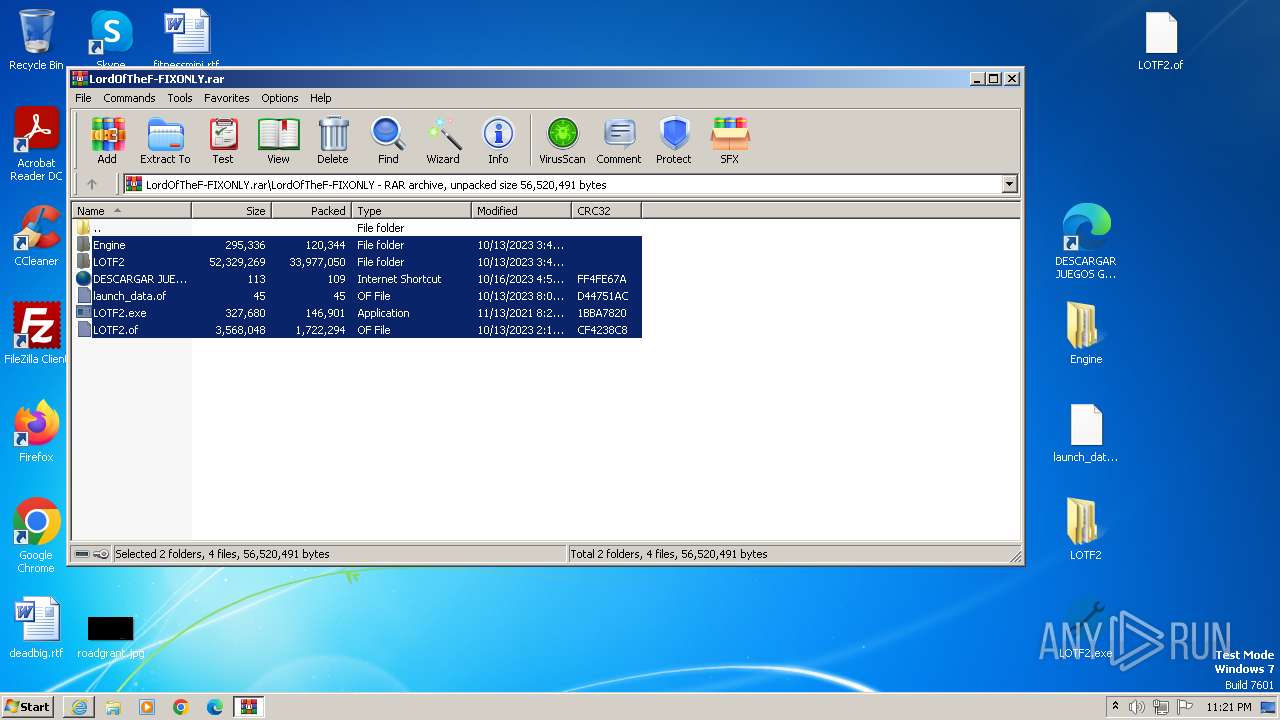
| 2556 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\LordOfTheF-FIXONLY.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | iexplore.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2900 | "C:\Users\admin\Desktop\LOTF2.exe" | C:\Users\admin\Desktop\LOTF2.exe | — | explorer.exe | |||||||||||
User: admin Company: Online-Fix.Me Integrity Level: MEDIUM Description: Generic Launcher Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3248 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3852 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3852 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://pixeldrain.com/api/file/x3E2QvYB?download" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
19 590
Read events
19 513
Write events
76
Delete events
1
Modification events
| (PID) Process: | (3852) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (3852) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (3852) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (3852) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3852) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3852) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3852) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3852) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000056010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3852) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3852) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
10
Suspicious files
21
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3248 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\LordOfTheF-FIXONLY.rar.ny0gmw8.partial | — | |
MD5:— | SHA256:— | |||
| 3852 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\LordOfTheF-FIXONLY.rar | — | |
MD5:— | SHA256:— | |||
| 3248 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:F3441B8572AAE8801C04F3060B550443 | SHA256:6720349E7D82EE0A8E73920D3C2B7CB2912D9FCF2EDB6FD98F2F12820158B0BF | |||
| 3248 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:2B3B3620430FFA0BAD622974F25F292B | SHA256:D4524C94BAA09710771D51BCA295AA0B6D7B8F1BB3A5792192C5165D80B1584E | |||
| 3248 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabBBCE.tmp | compressed | |
MD5:F3441B8572AAE8801C04F3060B550443 | SHA256:6720349E7D82EE0A8E73920D3C2B7CB2912D9FCF2EDB6FD98F2F12820158B0BF | |||
| 3248 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\TarBBCF.tmp | binary | |
MD5:9441737383D21192400ECA82FDA910EC | SHA256:BC3A6E84E41FAEB57E7C21AA3B60C2A64777107009727C5B7C0ED8FE658909E5 | |||
| 3248 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabBBBC.tmp | compressed | |
MD5:F3441B8572AAE8801C04F3060B550443 | SHA256:6720349E7D82EE0A8E73920D3C2B7CB2912D9FCF2EDB6FD98F2F12820158B0BF | |||
| 3248 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 3248 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\LordOfTheF-FIXONLY[1].rar | compressed | |
MD5:984DC6BB73F6D5EEEF74DDA104C379E1 | SHA256:9800C897765DD60F279809C4C1617FDE6E92EC8A89A450208E8BFCB82E7A8214 | |||
| 3852 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\LordOfTheF-FIXONLY.rar.ny0gmw8.partial:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
11
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3248 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?44b7f016ec3320f4 | unknown | compressed | 4.66 Kb | unknown |
3248 | iexplore.exe | GET | 200 | 184.24.77.58:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgPjMsQQze9ODq8%2B5unmG2le%2Fw%3D%3D | unknown | binary | 503 b | unknown |
3248 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?49bc7857dc93f557 | unknown | compressed | 61.6 Kb | unknown |
3248 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?f96a15a63697bdc6 | unknown | compressed | 4.66 Kb | unknown |
3248 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?103191fdc138d83f | unknown | compressed | 61.6 Kb | unknown |
3248 | iexplore.exe | GET | 200 | 23.212.210.158:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
3248 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?1945ababd14fd794 | unknown | compressed | 61.6 Kb | unknown |
3852 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3248 | iexplore.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | STACKPATH-CDN | US | whitelisted |
3248 | iexplore.exe | 23.212.210.158:80 | x1.c.lencr.org | AKAMAI-AS | AU | unknown |
3248 | iexplore.exe | 184.24.77.58:80 | r3.o.lencr.org | Akamai International B.V. | DE | unknown |
2656 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3852 | iexplore.exe | 152.199.19.161:443 | r20swj13mr.microsoft.com | EDGECAST | US | whitelisted |
3852 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r3.o.lencr.org |
| shared |
r20swj13mr.microsoft.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |