| File name: | spybot-search-destroy-3.4.0.0-installer_YucA-21.exe |
| Full analysis: | https://app.any.run/tasks/5d6d59ed-18f9-46cb-a285-84fc828d6cda |
| Verdict: | Malicious activity |
| Analysis date: | November 19, 2024, 19:45:28 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | C1FE2147288DF9F805ADD851B0A250FB |
| SHA1: | BBD4CF561810B2A5F6B57FBC4878CA27B11620B6 |
| SHA256: | 02E032F5112CC1AAAB727F99B059736F0B4C30B4895C66D93CA29B2ACBDAADAF |
| SSDEEP: | 98304:wyRr3UJ1IqsdPDMJoPvpyUwyFgS8S7ce/Unba+O+CB3jD9hl:y |
MALICIOUS
Antivirus name has been found in the command line (generic signature)
- AVGUI.exe (PID: 3716)
- AVGUI.exe (PID: 4328)
- AVGUI.exe (PID: 540)
- AVGUI.exe (PID: 6856)
- AVGUI.exe (PID: 2120)
- AVGUI.exe (PID: 3688)
SUSPICIOUS
Reads security settings of Internet Explorer
- spybot-search-destroy-3.4.0.0-installer_YucA-21.exe (PID: 3816)
- saBSI.exe (PID: 1596)
Executable content was dropped or overwritten
- spybot-search-destroy-3.4.0.0-installer_YucA-21.exe (PID: 3816)
- avg_antivirus_free_setup.exe (PID: 3972)
- icarus.exe (PID: 3428)
- avg_antivirus_free_online_setup.exe (PID: 5160)
- icarus.exe (PID: 2088)
- AvEmUpdate.exe (PID: 4556)
- spybot-search-destroy-3.4.0.0-installer.exe (PID: 1192)
- setup.exe (PID: 5776)
- icarus.exe (PID: 2084)
- engsup.exe (PID: 1512)
- aswOfferTool.exe (PID: 2152)
- AVGSvc.exe (PID: 5096)
Starts itself from another location
- icarus.exe (PID: 3428)
Checks Windows Trust Settings
- saBSI.exe (PID: 1596)
The process verifies whether the antivirus software is installed
- saBSI.exe (PID: 1596)
Process drops legitimate windows executable
- icarus.exe (PID: 2084)
- setup.exe (PID: 5776)
The process drops C-runtime libraries
- icarus.exe (PID: 2084)
- setup.exe (PID: 5776)
Drops a system driver (possible attempt to evade defenses)
- icarus.exe (PID: 2084)
- engsup.exe (PID: 1512)
Executes as Windows Service
- wsc_proxy.exe (PID: 5752)
- AVGSvc.exe (PID: 5096)
- afwServ.exe (PID: 1572)
- avgToolsSvc.exe (PID: 4604)
- aswidsagent.exe (PID: 6564)
Malware-specific behavior (creating "System.dll" in Temp)
- setup.exe (PID: 5776)
Checks for external IP
- AvEmUpdate.exe (PID: 4556)
Application launched itself
- AVGUI.exe (PID: 3688)
INFO
Checks supported languages
- spybot-search-destroy-3.4.0.0-installer_YucA-21.exe (PID: 3816)
- avg_antivirus_free_setup.exe (PID: 3972)
- saBSI.exe (PID: 1596)
- avg_antivirus_free_online_setup.exe (PID: 5160)
- icarus.exe (PID: 3428)
Reads the machine GUID from the registry
- spybot-search-destroy-3.4.0.0-installer_YucA-21.exe (PID: 3816)
- avg_antivirus_free_setup.exe (PID: 3972)
- saBSI.exe (PID: 1596)
- avg_antivirus_free_online_setup.exe (PID: 5160)
- icarus.exe (PID: 3428)
Reads the computer name
- spybot-search-destroy-3.4.0.0-installer_YucA-21.exe (PID: 3816)
- avg_antivirus_free_setup.exe (PID: 3972)
- saBSI.exe (PID: 1596)
- avg_antivirus_free_online_setup.exe (PID: 5160)
- icarus.exe (PID: 3428)
Reads the software policy settings
- spybot-search-destroy-3.4.0.0-installer_YucA-21.exe (PID: 3816)
- avg_antivirus_free_setup.exe (PID: 3972)
- saBSI.exe (PID: 1596)
- avg_antivirus_free_online_setup.exe (PID: 5160)
Sends debugging messages
- spybot-search-destroy-3.4.0.0-installer_YucA-21.exe (PID: 3816)
- saBSI.exe (PID: 1596)
Checks proxy server information
- spybot-search-destroy-3.4.0.0-installer_YucA-21.exe (PID: 3816)
- avg_antivirus_free_online_setup.exe (PID: 5160)
- saBSI.exe (PID: 1596)
Create files in a temporary directory
- spybot-search-destroy-3.4.0.0-installer_YucA-21.exe (PID: 3816)
- avg_antivirus_free_online_setup.exe (PID: 5160)
The process uses the downloaded file
- spybot-search-destroy-3.4.0.0-installer_YucA-21.exe (PID: 3816)
Creates files in the program directory
- saBSI.exe (PID: 1596)
- avg_antivirus_free_online_setup.exe (PID: 5160)
- icarus.exe (PID: 3428)
Reads CPU info
- icarus.exe (PID: 3428)
Manual execution by a user
- AVGUI.exe (PID: 3688)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (18) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (2.9) |
| .exe | | | Generic Win/DOS Executable (1.3) |
| .exe | | | DOS Executable Generic (1.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:10:14 12:00:04+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.39 |
| CodeSize: | 2145792 |
| InitializedDataSize: | 2305536 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1c2253 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.0.9.1 |
| ProductVersionNumber: | 3.0.9.1 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Softonic |
| FileDescription: | Softonic |
| FileVersion: | 3.0.9.1 |
| LegalCopyright: | (c) Softonic. All rights reserved. |
| ProductName: | Softonic |
| ProductVersion: | 3.0.9.1 |
Total processes
182
Monitored processes
48
Malicious processes
8
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 436 | "C:\Program Files (x86)\foobar2000\foobar2000.exe" /install /quiet /exportshelldata "C:\Users\admin\AppData\Local\Temp\fb2kshelldata.tmp" | C:\Program Files (x86)\foobar2000\foobar2000.exe | — | setup.exe | |||||||||||
User: admin Company: Piotr Pawlowski Integrity Level: HIGH Description: foobar2000 Exit code: 0 Version: 2.1.4.0 Modules
| |||||||||||||||
| 540 | "C:\Program Files\AVG\Antivirus\AVGUI.exe" --type=renderer --no-sandbox --autoplay-policy=no-user-gesture-required --log-file="C:\Users\admin\AppData\Roaming\AVG\Antivirus\log\cef_log.txt" --field-trial-handle=5732,4942236942359043718,12553617794642162151,131072 --disable-features=CalculateNativeWinOcclusion,CookiesWithoutSameSiteMustBeSecure,SameSiteByDefaultCookies,SameSiteDefaultChecksMethodRigorously --disable-gpu-compositing --lang=en-US --log-file="C:\Users\admin\AppData\Roaming\AVG\Antivirus\log\cef_log.txt" --log-severity=error --user-agent="Mozilla/5.0 AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.101 Safari/537.36 Avastium (0.0.0) (Windows 10.0)" --disable-webaudio --force-wave-audio --disable-software-rasterizer --no-sandbox --blacklist-accelerated-compositing --disable-accelerated-2d-canvas --disable-accelerated-compositing --disable-accelerated-layers --disable-accelerated-video-decode --blacklist-webgl --disable-bundled-ppapi-flash --disable-flash-3d --enable-aggressive-domstorage-flushing --enable-media-stream --disable-gpu --disable-webgl --disable-gpu-compositing --allow-file-access-from-files=1 --pack_loading_disabled=1 --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=4 --mojo-platform-channel-handle=9372 /prefetch:1 | C:\Program Files\AVG\Antivirus\AVGUI.exe | — | AVGUI.exe | |||||||||||
User: admin Company: Gen Digital Inc. Integrity Level: MEDIUM Description: AVG Antivirus Version: 24.11.9615.0 | |||||||||||||||
| 900 | "C:\Program Files\AVG\Antivirus\RegSvr.exe" "C:\Program Files\AVG\Antivirus\aswAMSI.dll" | C:\Program Files\AVG\Antivirus\RegSvr.exe | — | icarus.exe | |||||||||||
User: admin Company: Gen Digital Inc. Integrity Level: HIGH Description: AVG Antivirus Installer Exit code: 0 Version: 24.11.9615.0 Modules
| |||||||||||||||
| 1192 | "C:\Users\admin\Downloads\spybot-search-destroy-3.4.0.0-installer.exe" | C:\Users\admin\Downloads\spybot-search-destroy-3.4.0.0-installer.exe | spybot-search-destroy-3.4.0.0-installer_YucA-21.exe | ||||||||||||
User: admin Company: Efficacious Approval Applications Integrity Level: HIGH Description: Efficacious Approval Applications Exit code: 0 Version: 2.1.5.0 Modules
| |||||||||||||||
| 1356 | "C:\Program Files\AVG\Antivirus\x86\RegSvr.exe" "C:\Program Files\AVG\Antivirus\x86\aswAMSI.dll" | C:\Program Files\AVG\Antivirus\x86\RegSvr.exe | — | icarus.exe | |||||||||||
User: admin Company: Gen Digital Inc. Integrity Level: HIGH Description: AVG Antivirus Installer Exit code: 0 Version: 24.11.9615.0 Modules
| |||||||||||||||
| 1512 | "C:\Program Files\AVG\Antivirus\defs\24111902\engsup.exe" /prepare_definitions_folder | C:\Program Files\AVG\Antivirus\defs\24111902\engsup.exe | icarus.exe | ||||||||||||
User: admin Company: Gen Digital Inc. Integrity Level: HIGH Description: AVG Antivirus vps tool Exit code: 0 Version: 18.0.2075.0 Modules
| |||||||||||||||
| 1572 | "C:\Program Files\AVG\Antivirus\afwServ.exe" | C:\Program Files\AVG\Antivirus\afwServ.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Gen Digital Inc. Integrity Level: SYSTEM Description: AVG firewall service Version: 24.11.9615.0 Modules
| |||||||||||||||
| 1596 | "C:\Users\admin\AppData\Local\Temp\ISV9566.tmp\saBSI.exe" /affid {aflt} PaidDistribution=true CountryCode=US | C:\Users\admin\AppData\Local\Temp\ISV9566.tmp\saBSI.exe | spybot-search-destroy-3.4.0.0-installer_YucA-21.exe | ||||||||||||
User: admin Company: McAfee, LLC Integrity Level: HIGH Description: McAfee WebAdvisor(bootstrap installer) Exit code: 0 Version: 4,1,1,865 Modules
| |||||||||||||||
| 2084 | C:\WINDOWS\Temp\asw-9a85ddca-4d8f-4338-aa90-9aae5c157869\avg-av\icarus.exe /silent /ws /psh:hIA7qv6y4LnyhZ8uUg5ES7NJSv5xFxjsl6RHqJGR35jKfB2LkrE9eOjWN5xgM0llMoJ1AtB9KgRCtX /cookie:mmm_irs_ppi_902_451_o /edat_dir:C:\WINDOWS\Temp\asw.a0a141e024ffca9c /track-guid:10001d9a-d2bf-4ef9-97cf-100992588996 /er_master:master_ep_bd8016e7-37fb-43e4-aab5-cadbb5854751 /er_ui:ui_ep_68ae9c36-3bab-4c1e-a262-bfddaa6b7184 /er_slave:avg-av_slave_ep_d4dc1762-1c24-4ec5-b796-f4bc89facefd /slave:avg-av | C:\Windows\Temp\asw-9a85ddca-4d8f-4338-aa90-9aae5c157869\avg-av\icarus.exe | icarus.exe | ||||||||||||
User: admin Company: Gen Digital Inc. Integrity Level: HIGH Description: AVG Installer Exit code: 0 Version: 24.11.8270.0 Modules
| |||||||||||||||
| 2088 | C:\WINDOWS\Temp\asw-9a85ddca-4d8f-4338-aa90-9aae5c157869\avg-av-vps\icarus.exe /silent /ws /psh:hIA7qv6y4LnyhZ8uUg5ES7NJSv5xFxjsl6RHqJGR35jKfB2LkrE9eOjWN5xgM0llMoJ1AtB9KgRCtX /cookie:mmm_irs_ppi_902_451_o /edat_dir:C:\WINDOWS\Temp\asw.a0a141e024ffca9c /track-guid:10001d9a-d2bf-4ef9-97cf-100992588996 /er_master:master_ep_bd8016e7-37fb-43e4-aab5-cadbb5854751 /er_ui:ui_ep_68ae9c36-3bab-4c1e-a262-bfddaa6b7184 /er_slave:avg-av-vps_slave_ep_4c0907cb-44d8-4621-a44a-24d2437f8727 /slave:avg-av-vps | C:\Windows\Temp\asw-9a85ddca-4d8f-4338-aa90-9aae5c157869\avg-av-vps\icarus.exe | icarus.exe | ||||||||||||
User: admin Company: Gen Digital Inc. Integrity Level: HIGH Description: AVG Installer Exit code: 0 Version: 24.11.8270.0 Modules
| |||||||||||||||
Total events
8 812
Read events
8 016
Write events
703
Delete events
93
Modification events
| (PID) Process: | (3816) spybot-search-destroy-3.4.0.0-installer_YucA-21.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Discardable\PostSetup\Component Categories\{56FFCC30-D398-11D0-B2AE-00A0C908FA49}\Enum |
| Operation: | write | Name: | Implementing |
Value: 1C00000001000000E8070B000200130013002E002E00CE02010000001E768127E028094199FEB9D127C57AFE | |||
| (PID) Process: | (3816) spybot-search-destroy-3.4.0.0-installer_YucA-21.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 0100000000000000F7EC79C4BB3ADB01 | |||
| (PID) Process: | (1596) saBSI.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\McAfee\WebAdvisor |
| Operation: | write | Name: | UUID |
Value: {A8B906F3-91EB-4BC7-BFDC-16EA556ECAD1} | |||
| (PID) Process: | (1596) saBSI.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\McAfee\WebAdvisor |
| Operation: | write | Name: | InstallerFlags |
Value: 1 | |||
| (PID) Process: | (5160) avg_antivirus_free_online_setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\1D0EC6DE-4A80-4CC3-A335-E6E41C951198 |
| Operation: | write | Name: | 5FD38555-4B16-40AE-9A09-E2C969CB74AF |
Value: F6D4F52220BB5A3D7246A004278BB23F | |||
| (PID) Process: | (5160) avg_antivirus_free_online_setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\C06AEB9D-8774-46E7-8160-8321BCD14D9F |
| Operation: | write | Name: | 7CCD586D-2ABC-42FF-A23B-3731F4F183D9 |
Value: F6D4F52220BB5A3D7246A004278BB23F | |||
| (PID) Process: | (5160) avg_antivirus_free_online_setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\1D0EC6DE-4A80-4CC3-A335-E6E41C951198 |
| Operation: | write | Name: | 8C5CFDF4-AB05-4EB0-8EF6-7B4620DC2CF3 |
Value: AQAAANCMnd8BFdERjHoAwE/Cl+sBAAAAtA46N03Oz0Cz07PubfNy/wQAAAACAAAAAAAQZgAAAAEAACAAAADFj6W4FFonOwZOPf8fuJ5gb9zqaZwQnZt8XfB8M9257QAAAAAOgAAAAAIAACAAAAADjfeed2GUEeUJW9UMAlWhzFUKBus9INzVXWwCtyVqUVAAAAArWzQml1oDYoW5YgJP/ZAe6D9pOXQW1XqCZoojpJV8Gm4Nn33YeOlqMOMfSPFV//a20UEiK7TjPEBVyI4LGs8O3nRPck40xxSYsw2/dIMiQ0AAAABUbpll3mSUsWXbsK/RhSB1NobeXfYKapRzQk5PlPHSPt5Bjv7+NC1F7D8VGf4bQnni8h1zIDmZT4SQ0aZoFi8+ | |||
| (PID) Process: | (5160) avg_antivirus_free_online_setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\C06AEB9D-8774-46E7-8160-8321BCD14D9F |
| Operation: | write | Name: | 5E1D6A55-0134-486E-A166-38C2E4919BB1 |
Value: AQAAANCMnd8BFdERjHoAwE/Cl+sBAAAAtA46N03Oz0Cz07PubfNy/wQAAAACAAAAAAAQZgAAAAEAACAAAADFj6W4FFonOwZOPf8fuJ5gb9zqaZwQnZt8XfB8M9257QAAAAAOgAAAAAIAACAAAAADjfeed2GUEeUJW9UMAlWhzFUKBus9INzVXWwCtyVqUVAAAAArWzQml1oDYoW5YgJP/ZAe6D9pOXQW1XqCZoojpJV8Gm4Nn33YeOlqMOMfSPFV//a20UEiK7TjPEBVyI4LGs8O3nRPck40xxSYsw2/dIMiQ0AAAABUbpll3mSUsWXbsK/RhSB1NobeXfYKapRzQk5PlPHSPt5Bjv7+NC1F7D8VGf4bQnni8h1zIDmZT4SQ0aZoFi8+ | |||
| (PID) Process: | (5160) avg_antivirus_free_online_setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\1D0EC6DE-4A80-4CC3-A335-E6E41C951198 |
| Operation: | write | Name: | 144807F0-DE37-4C62-9C05-EB4CC64A7A2F |
Value: 1a13586a-7cd2-4883-9151-f94c19f6c817 | |||
| (PID) Process: | (5160) avg_antivirus_free_online_setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\C06AEB9D-8774-46E7-8160-8321BCD14D9F |
| Operation: | write | Name: | 56C7A9DA-4B11-406A-8B1A-EFF157C294D6 |
Value: 1a13586a-7cd2-4883-9151-f94c19f6c817 | |||
Executable files
831
Suspicious files
1 653
Text files
323
Unknown types
12
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1596 | saBSI.exe | C:\ProgramData\McAfee\WebAdvisor\saBSI.exe\log_00000057003F001D0006.txt | text | |
MD5:410C78500862933173B3FE7F5D821EB2 | SHA256:F8C945EAA4F690D144129E87AA1CAA6DC2C522371DDA07D323D07C873C11A4BD | |||
| 5160 | avg_antivirus_free_online_setup.exe | C:\Users\admin\AppData\Local\Temp\F07D8C6A-04B6-4025-869C-70A788D7B5C0 | binary | |
MD5:F37796AFCA92FE51B77B5C370BEB509A | SHA256:B2DCE8B93807A5709107BDEA7235D0D5BF28C5D9E580E66C7F3D29B8F5DAC1D7 | |||
| 5160 | avg_antivirus_free_online_setup.exe | C:\Windows\Temp\asw-9a85ddca-4d8f-4338-aa90-9aae5c157869\common\product-info.xml | xml | |
MD5:F703EEDD39374802BFF0E485505F4130 | SHA256:9E1A26F315C40217096F24BE67B2CA9C2FDE60894D99535536E769897BB86D74 | |||
| 5160 | avg_antivirus_free_online_setup.exe | C:\ProgramData\AVG\Icarus\Logs\sfx.log | text | |
MD5:ECAA88F7FA0BF610A5A26CF545DCD3AA | SHA256:F1945CD6C19E56B3C1C78943EF5EC18116907A4CA1EFC40A57D48AB1DB7ADFC5 | |||
| 3972 | avg_antivirus_free_setup.exe | C:\Windows\Temp\asw.a0a141e024ffca9c\avg_antivirus_free_online_setup.exe | executable | |
MD5:FB4D24ABE3AE811025140C5F34D60F81 | SHA256:3B216887612445F58C20FA8F140C404477F33B49A631616C43E26523ED082383 | |||
| 5160 | avg_antivirus_free_online_setup.exe | C:\Windows\Temp\asw-9a85ddca-4d8f-4338-aa90-9aae5c157869\common\icarus.exe | executable | |
MD5:043105E55F5AEA4FC68F51F69B04D6C2 | SHA256:20A4B502D996BBEE3A4CBF4D344190CC42F216119C3711A9120267171E759AEE | |||
| 3816 | spybot-search-destroy-3.4.0.0-installer_YucA-21.exe | C:\Users\admin\AppData\Local\Temp\ISV9566.tmp\saBSI.zip | compressed | |
MD5:F68008B70822BD28C82D13A289DEB418 | SHA256:CC6F4FAF4E8A9F4D2269D1D69A69EA326F789620FB98078CC98597F3CB998589 | |||
| 5160 | avg_antivirus_free_online_setup.exe | C:\Windows\Temp\asw-9a85ddca-4d8f-4338-aa90-9aae5c157869\common\icarus_mod.dll | executable | |
MD5:4F006AA4BC4D037B5A4C939F2CB85FFB | SHA256:7296F7BC71088F1E3F01F95A7004C73F403360F614ABE44F62ED50532FAACFD8 | |||
| 5160 | avg_antivirus_free_online_setup.exe | C:\Users\admin\AppData\Local\Temp\6358C710-B89F-46B9-93F2-F6CAC44F5286 | binary | |
MD5:5013A4A9A3834A074B58CEC3A64E23E6 | SHA256:118D4C35D9C18A163626D4A7E0499964C49F9E0E81B4041FB3FCBF7FF0D9E92D | |||
| 5160 | avg_antivirus_free_online_setup.exe | C:\Windows\Temp\asw-9a85ddca-4d8f-4338-aa90-9aae5c157869\common\7c13e270-fb32-40cc-ba64-20ccd9b00bd7 | compressed | |
MD5:EDA65FABA0BC9A453B95E2F5669776CE | SHA256:41E41987668E0C140FFFDA68FF3F47572D0D6A0C38FED1097740CBC5F141E709 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
49
TCP/UDP connections
215
DNS requests
269
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4932 | svchost.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4932 | svchost.exe | GET | 200 | 2.16.164.89:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1760 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1760 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3972 | avg_antivirus_free_setup.exe | POST | 204 | 34.117.223.223:80 | http://v7event.stats.avast.com/cgi-bin/iavsevents.cgi | unknown | — | — | whitelisted |
1300 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4556 | AvEmUpdate.exe | HEAD | 200 | 2.19.126.157:80 | http://emupdate.avcdn.net/files/emupdate/pong.txt | unknown | — | — | whitelisted |
4556 | AvEmUpdate.exe | GET | 200 | 2.19.11.101:80 | http://emupdate.bav.avcdn.net/files/bav/emupdate/autoupdate.ini | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
544 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4932 | svchost.exe | 2.16.164.89:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4932 | svchost.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4932 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 2.23.209.148:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
1176 | svchost.exe | 40.126.32.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Misc activity | ET INFO External IP Lookup Service in DNS Query (ip-info .ff .avast .com) |
2192 | svchost.exe | Misc activity | ET INFO External IP Lookup Service in DNS Query (ip-info .ff .avast .com) |
4556 | AvEmUpdate.exe | Misc activity | ET INFO Observed External IP Lookup Domain (ip-info .ff .avast .com) in TLS SNI |
— | — | Misc activity | ET INFO External IP Lookup Service in DNS Query (ip-info .ff .avast .com) |
— | — | Misc activity | ET INFO Observed External IP Lookup Domain (ip-info .ff .avast .com) in TLS SNI |
— | — | Misc activity | ET INFO External IP Lookup Service in DNS Query (ip-info .ff .avast .com) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |
— | — | Potential Corporate Privacy Violation | ET POLICY External IP Lookup (avast .com) |
— | — | Misc activity | ET INFO Observed External IP Lookup Domain (ip-info .ff .avast .com) in TLS SNI |
Process | Message |
|---|---|
spybot-search-destroy-3.4.0.0-installer_YucA-21.exe | LoadingPage
|
spybot-search-destroy-3.4.0.0-installer_YucA-21.exe | WelcomePage
|
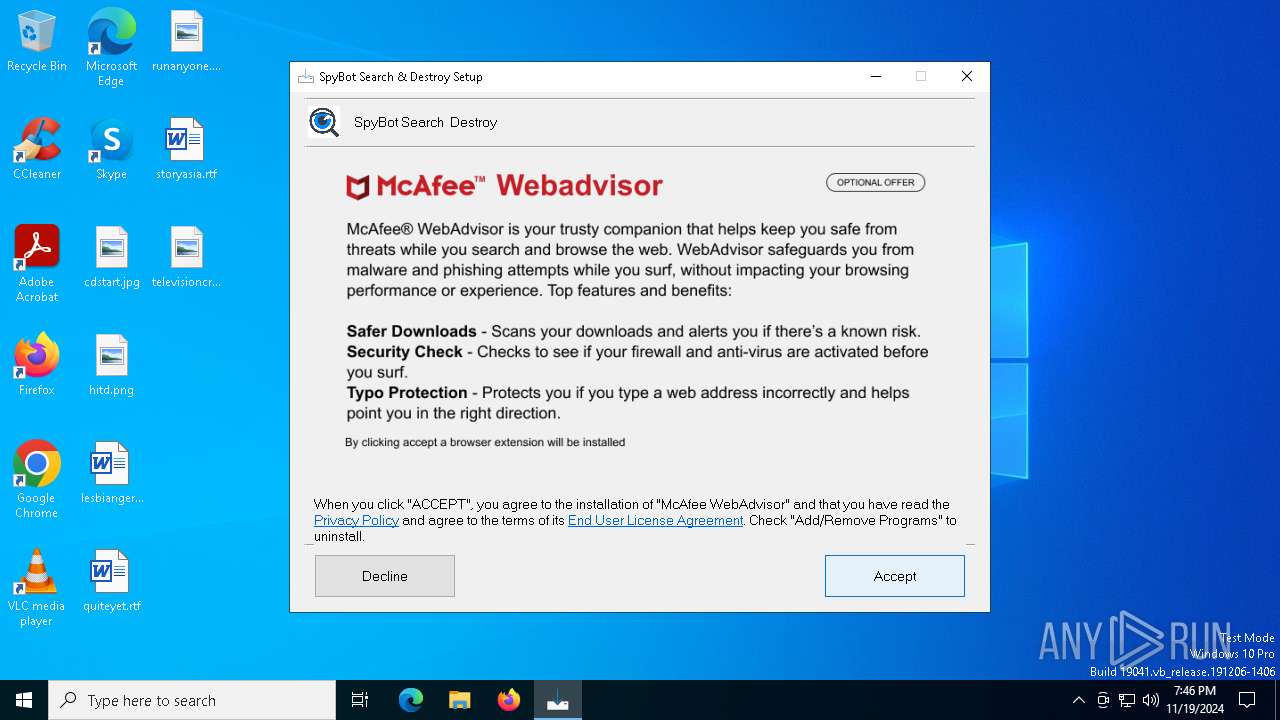
spybot-search-destroy-3.4.0.0-installer_YucA-21.exe | ProductPage
|
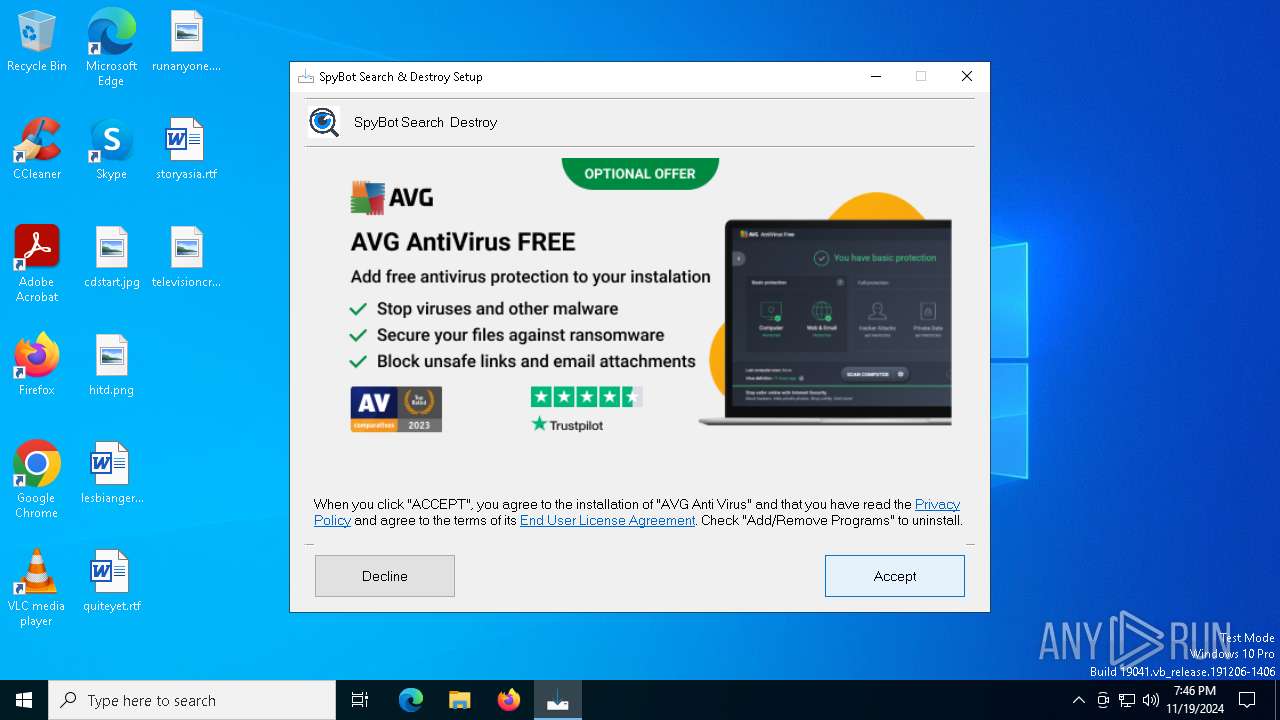
spybot-search-destroy-3.4.0.0-installer_YucA-21.exe | ProductPage
|
spybot-search-destroy-3.4.0.0-installer_YucA-21.exe | DownloadPageDLM
|
spybot-search-destroy-3.4.0.0-installer_YucA-21.exe | FinishPageDLM
|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in current directory
|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in current directory
|
saBSI.exe | NotComDllGetInterface: C:\Users\admin\AppData\Local\Temp\ISV9566.tmp\saBSI.exe loading C:\Users\admin\AppData\Local\Temp\ISV9566.tmp\mfeaaca.dll, WinVerifyTrust failed with 80092003
|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in current directory
|