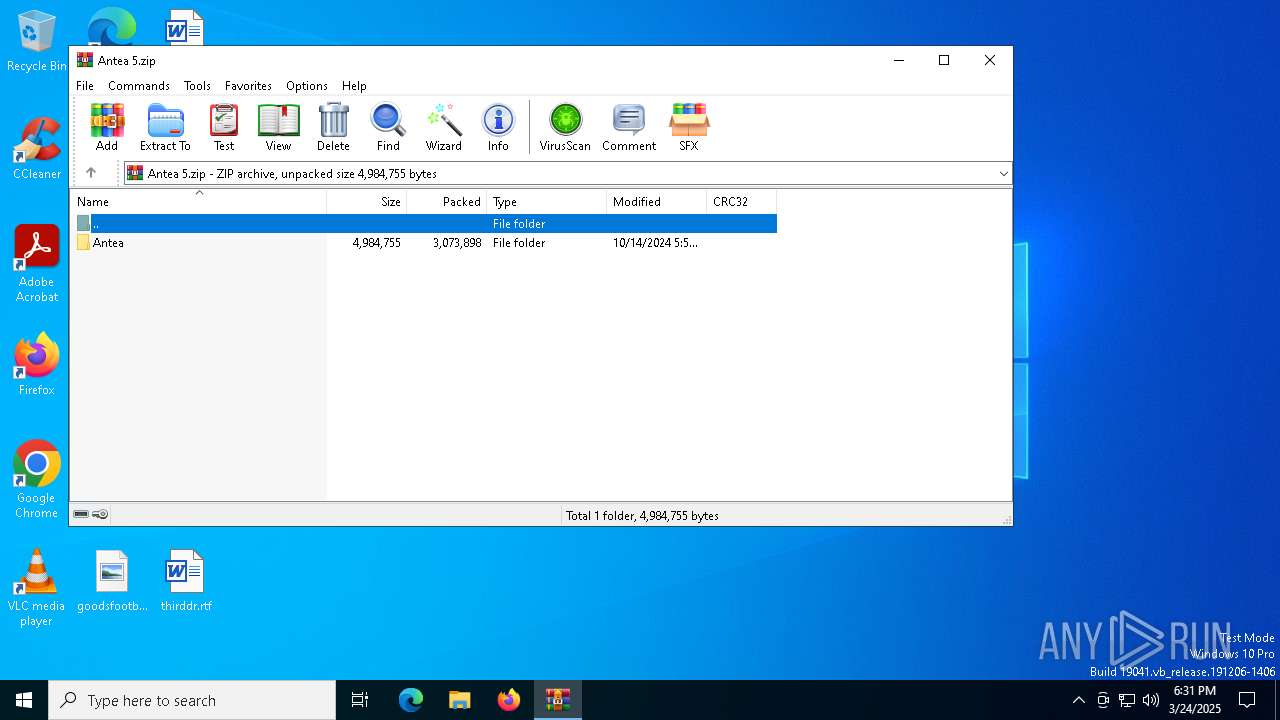
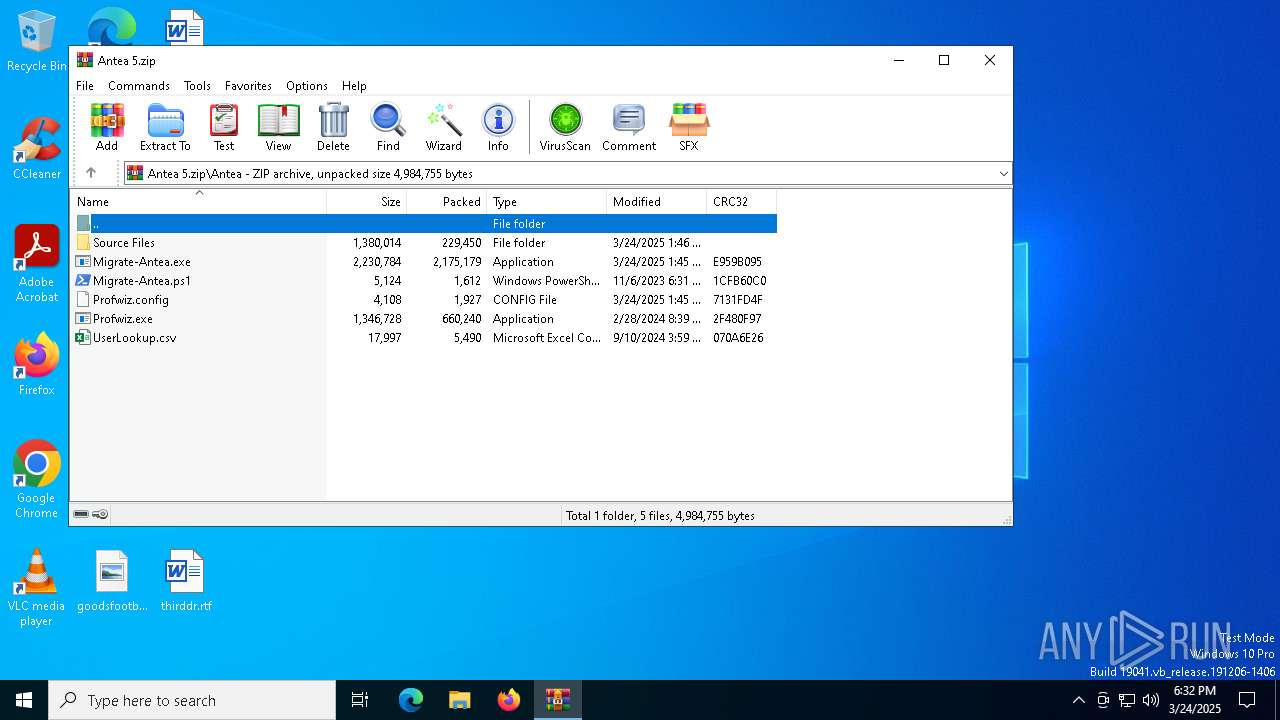
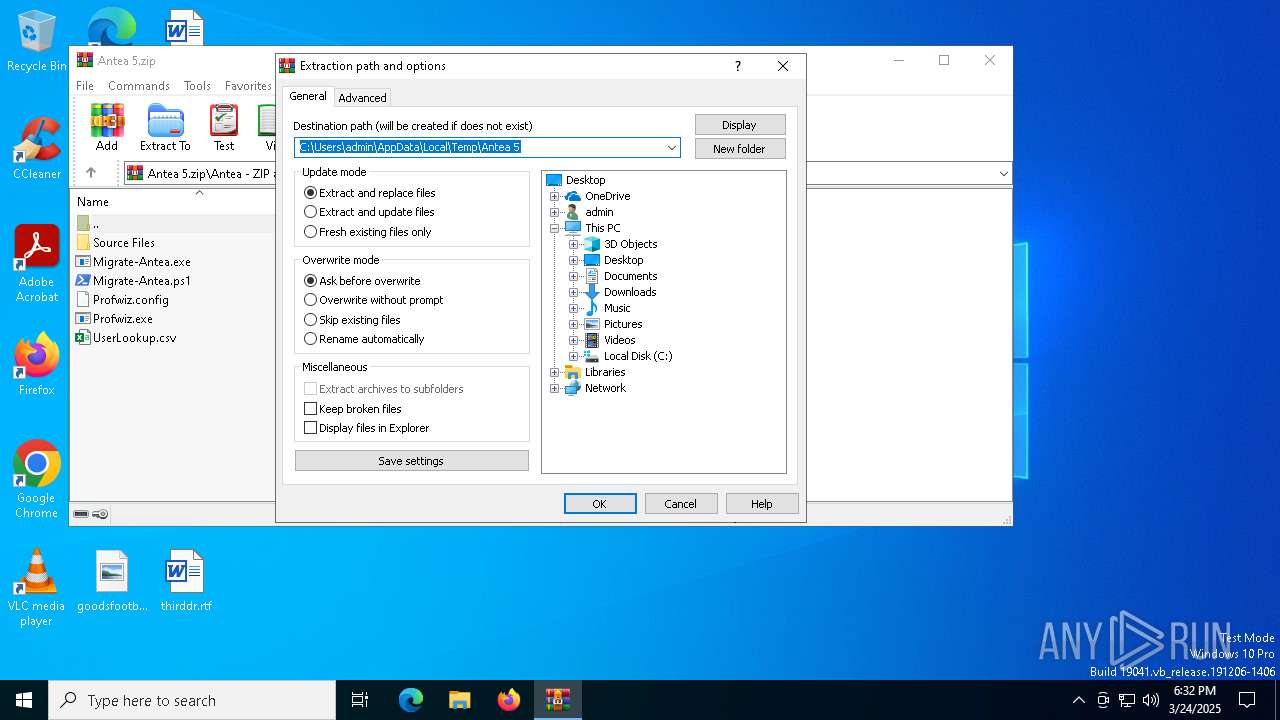
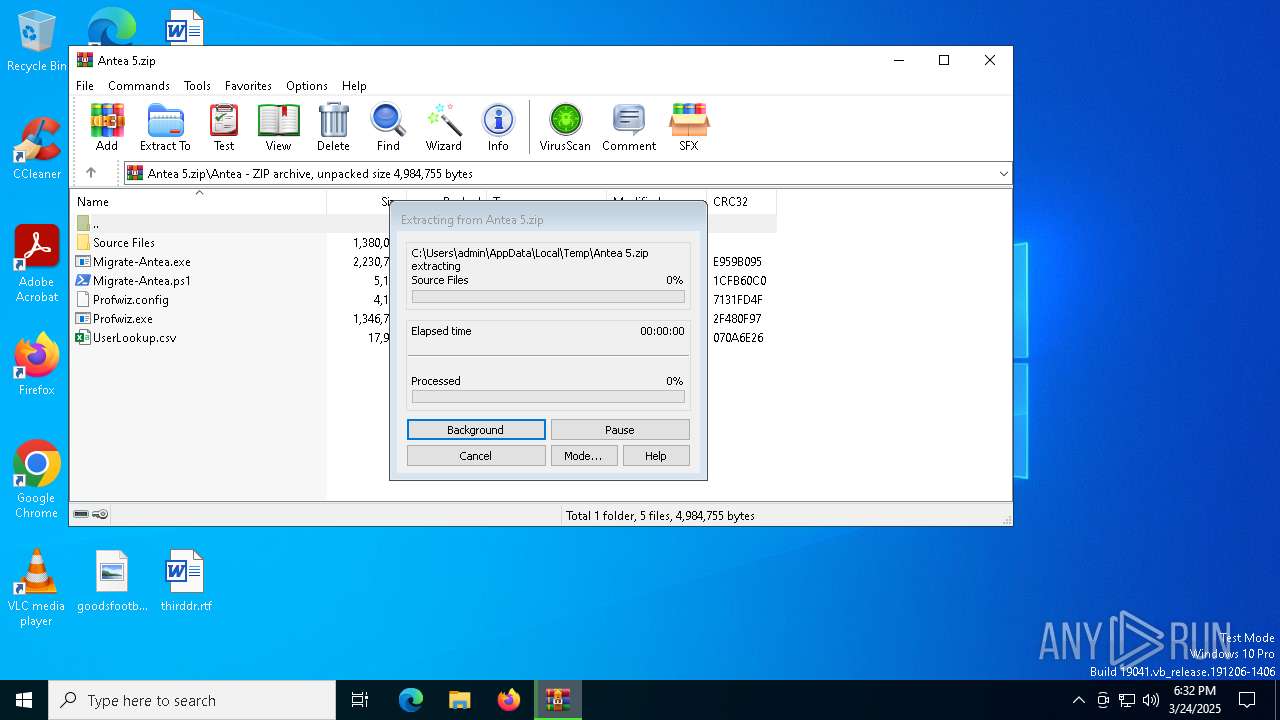
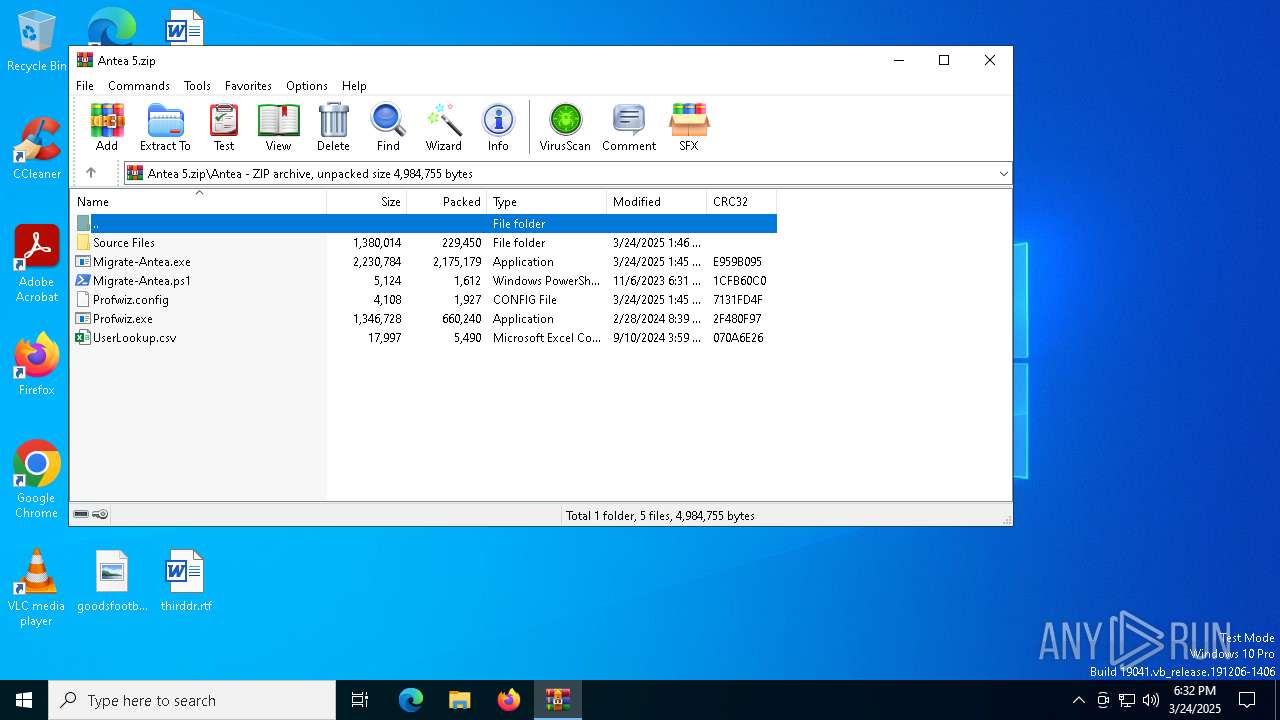
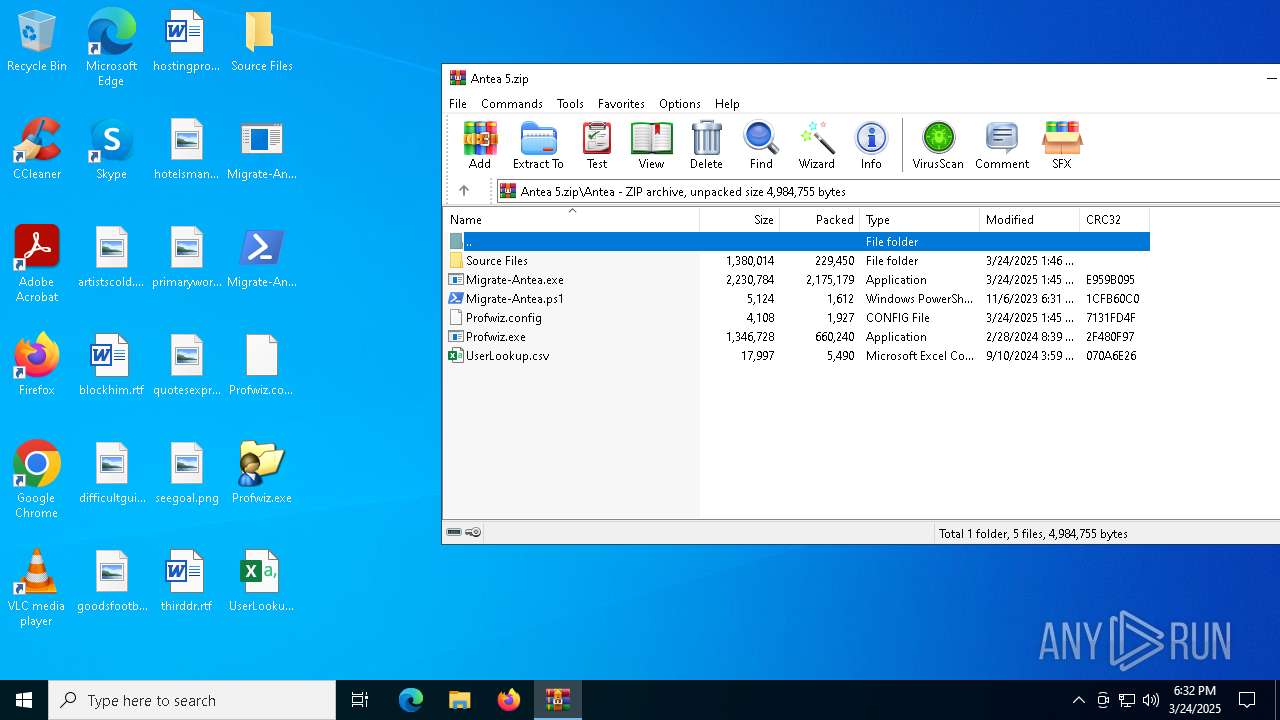
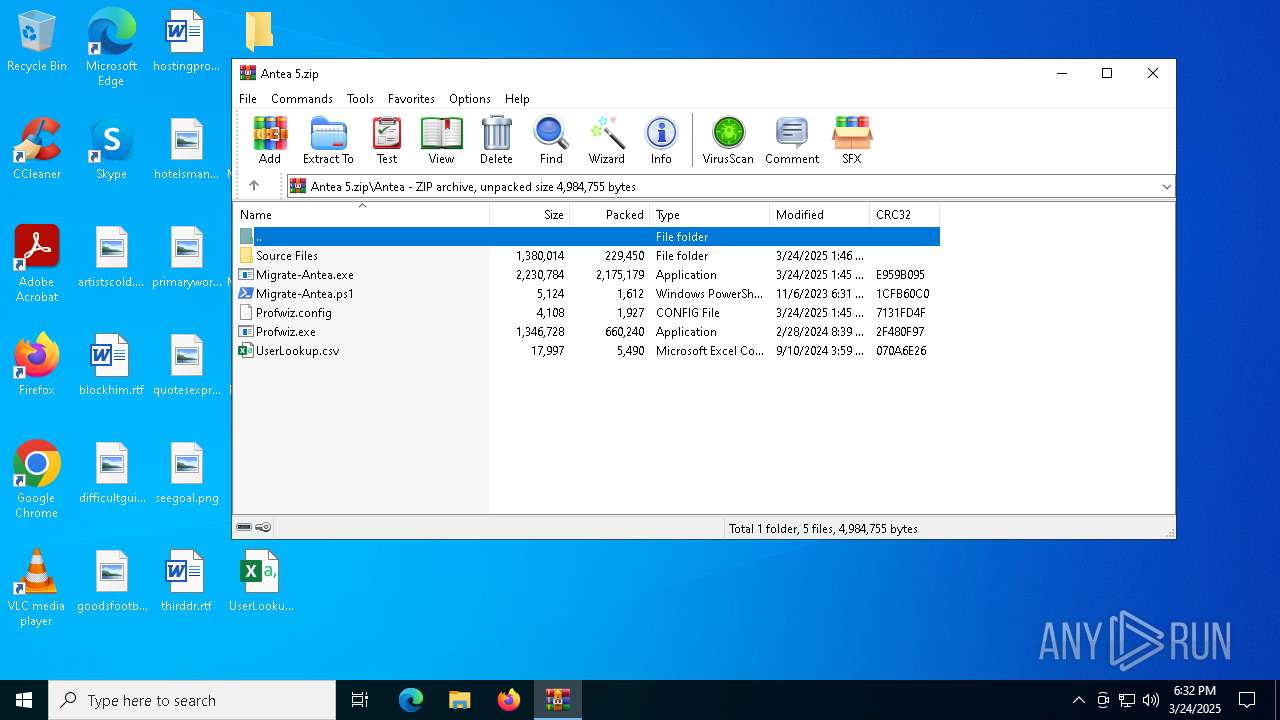
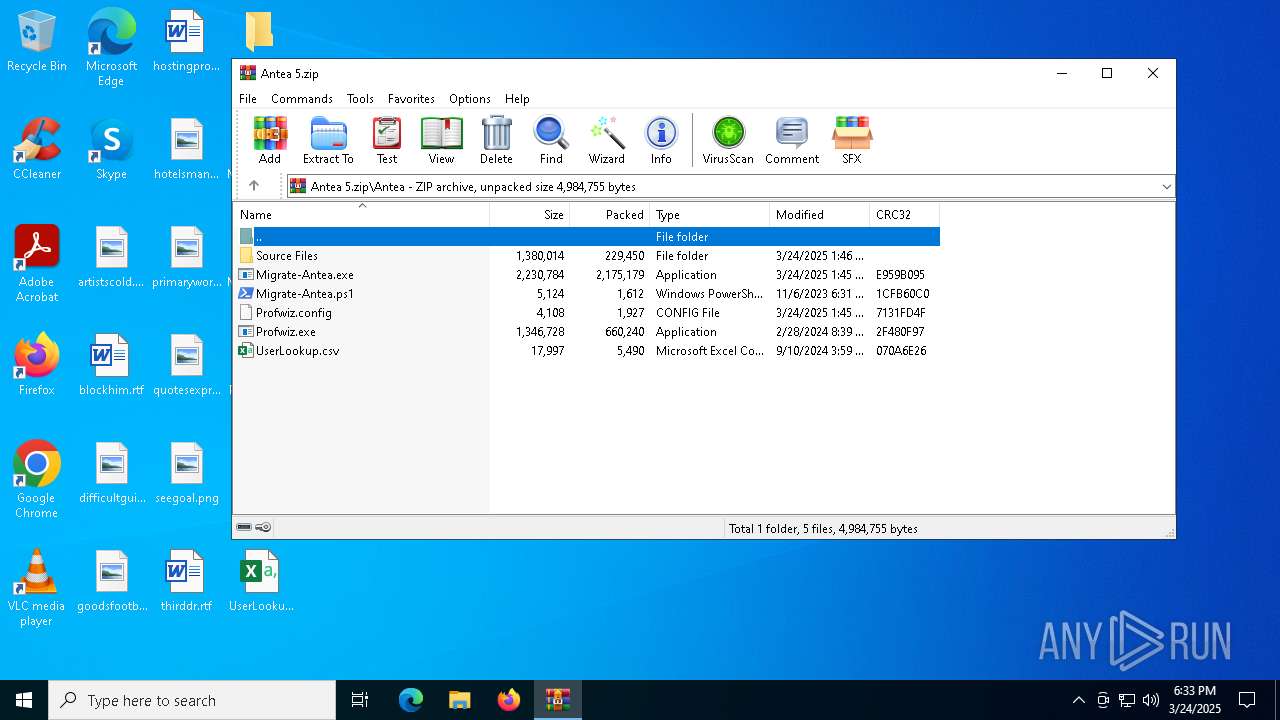
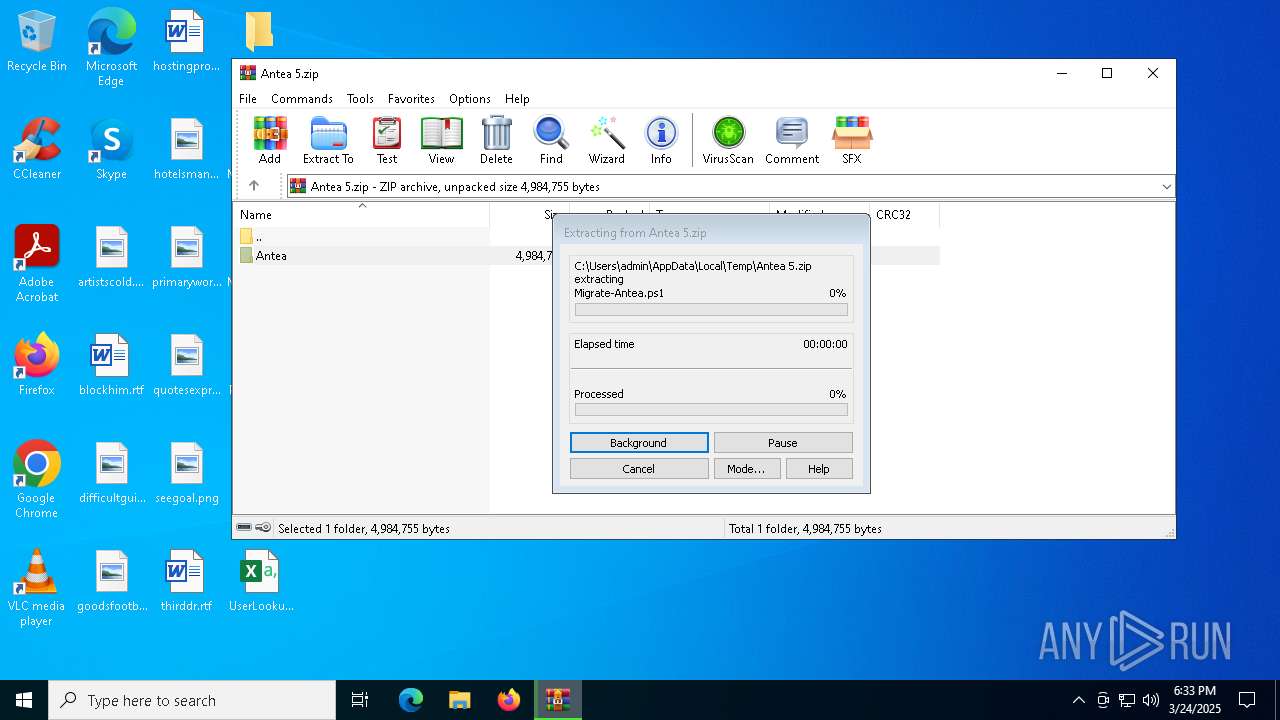
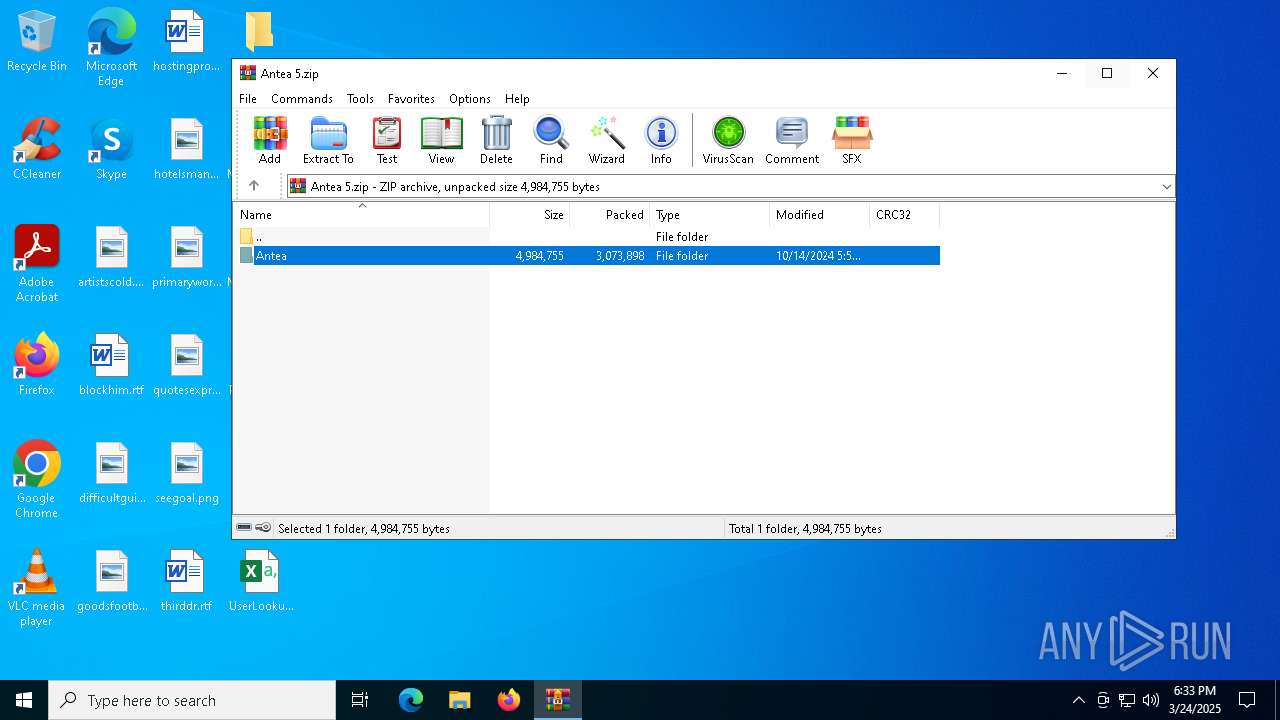
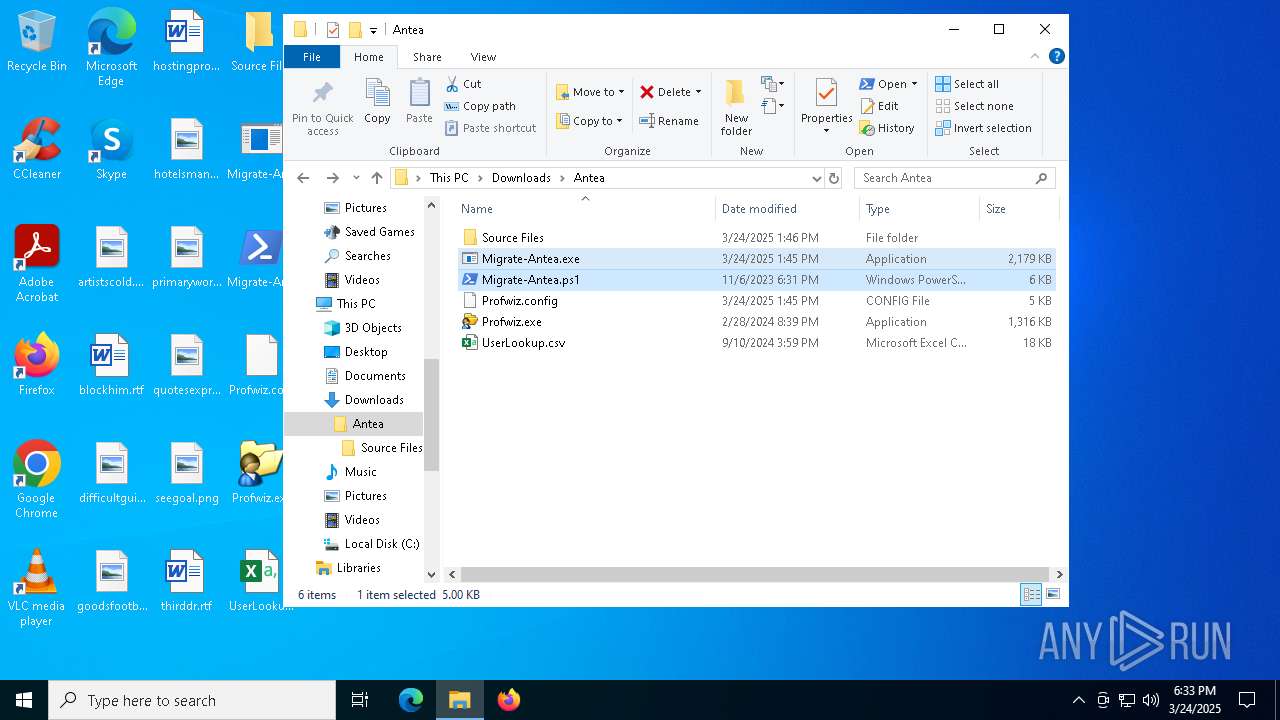
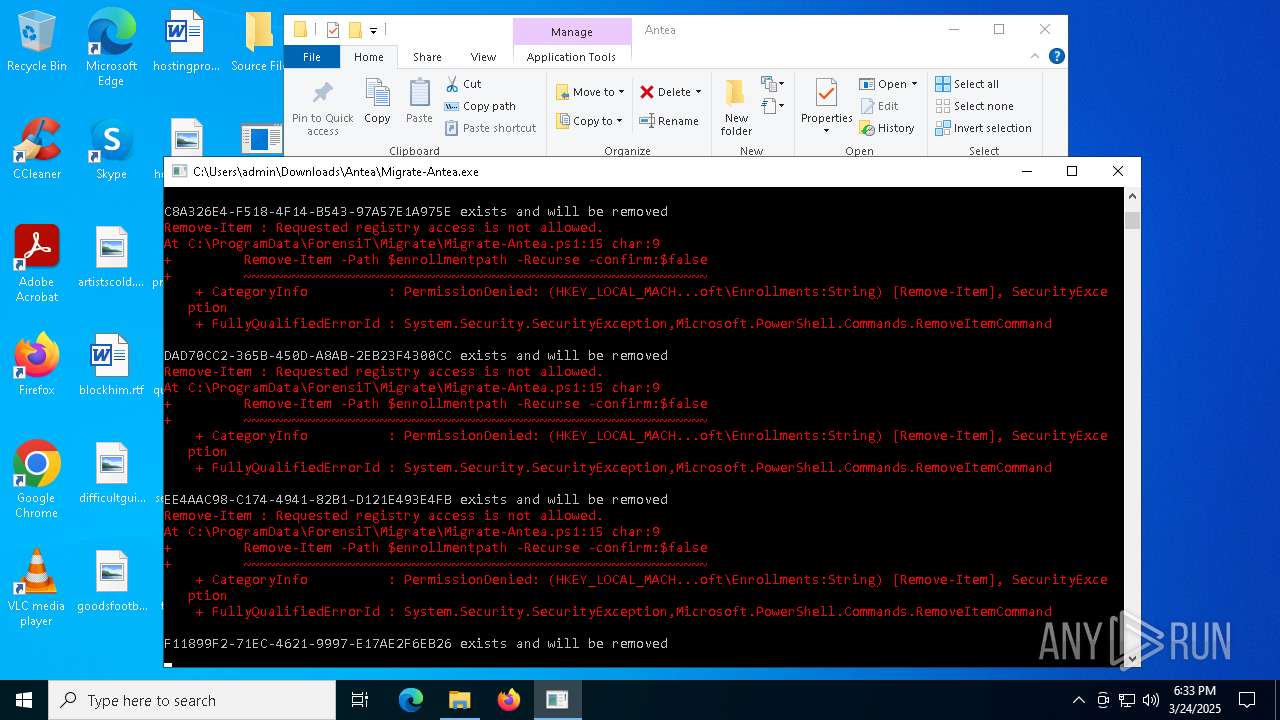
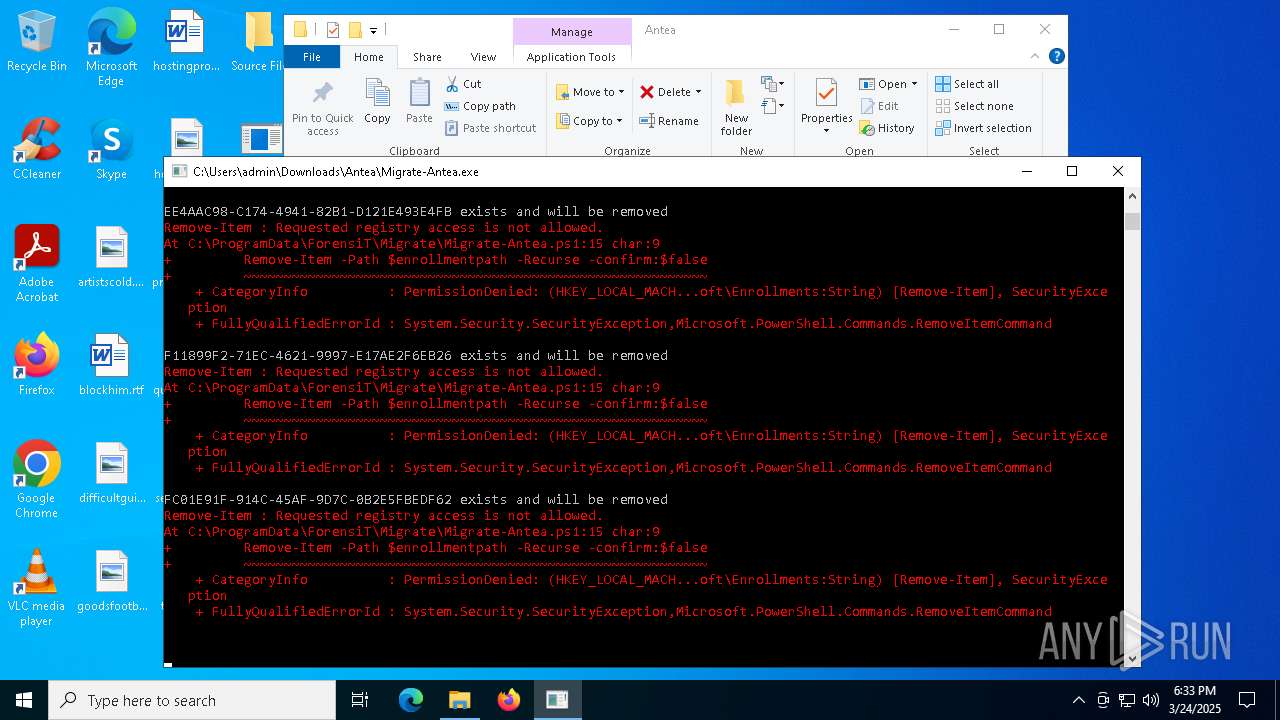
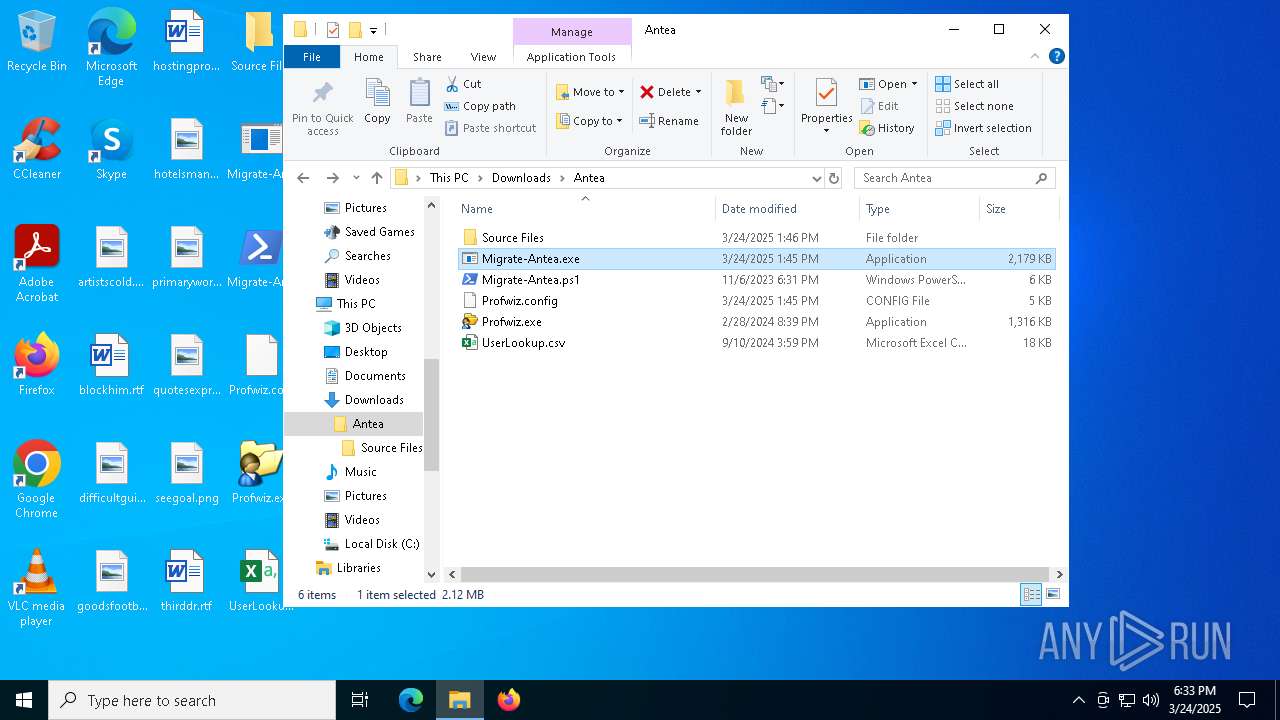
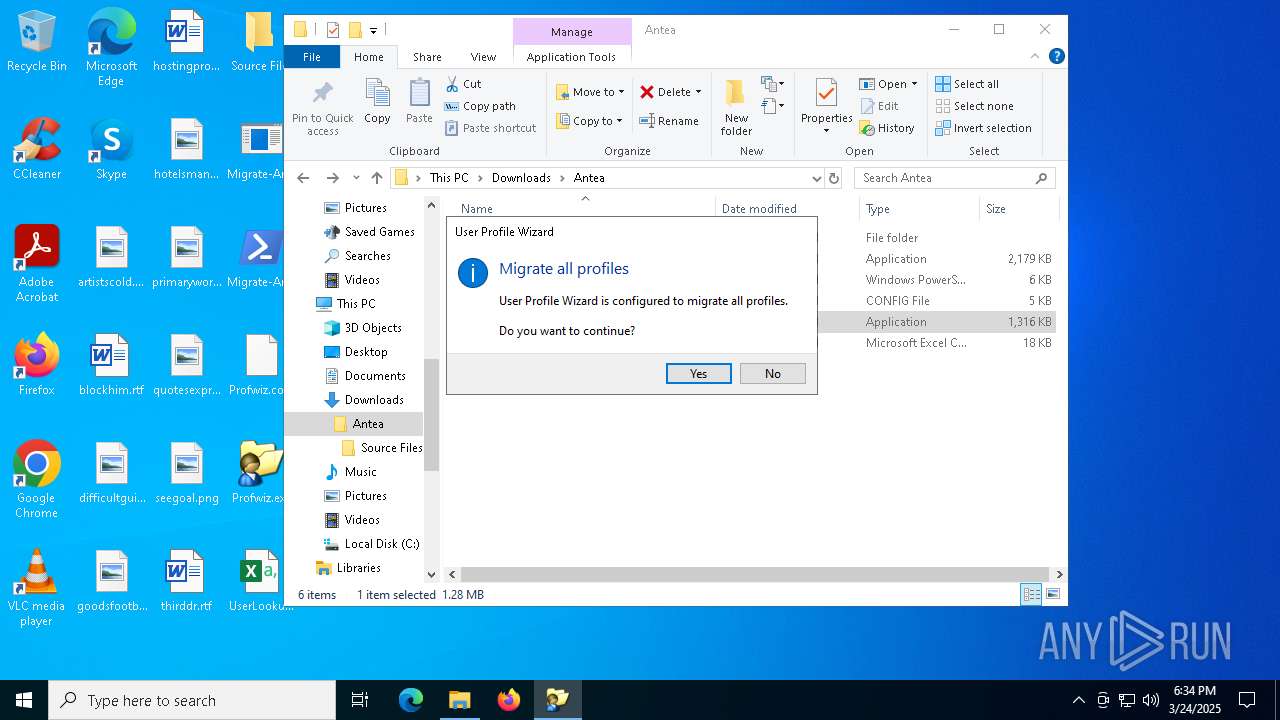
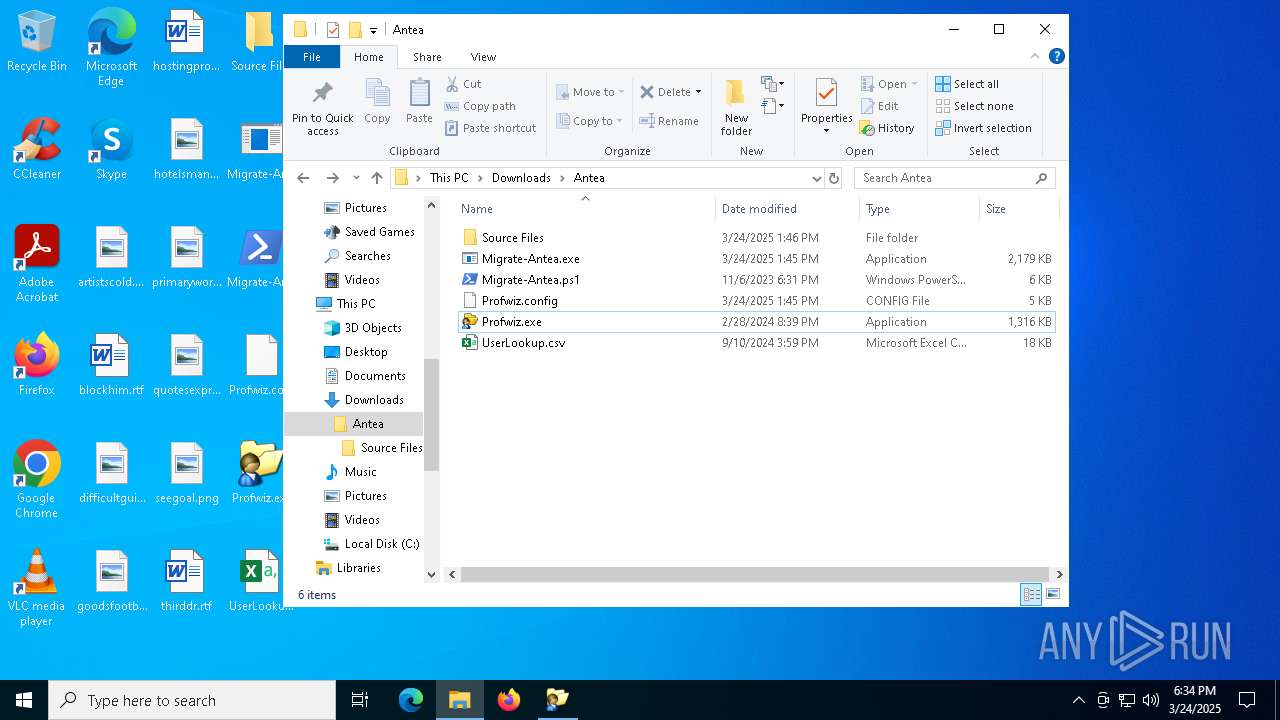
| File name: | Antea 5.zip |
| Full analysis: | https://app.any.run/tasks/a99240c6-3fd6-4291-9ef6-bbe9e99dbc3a |
| Verdict: | Malicious activity |
| Analysis date: | March 24, 2025, 18:31:46 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 88F1F7045C3CCB1ECCB028F8482943E4 |
| SHA1: | 0A7CAA47BF139A4795FDADFE09240E69E7B575B1 |
| SHA256: | 02DA0430D7505F9EF6670E3B03293E3897AC246BF957B986D2D008BD338E4BFE |
| SSDEEP: | 98304:2KHZtXs1Pb6VrCRPpTzw6CO7rJzSjKKecNJ0znTumW41/jx+Ntz7WQPwHqZd2/8U:eNn+6Z |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 7356)
Bypass execution policy to execute commands
- powershell.exe (PID: 7868)
- powershell.exe (PID: 4784)
- powershell.exe (PID: 3332)
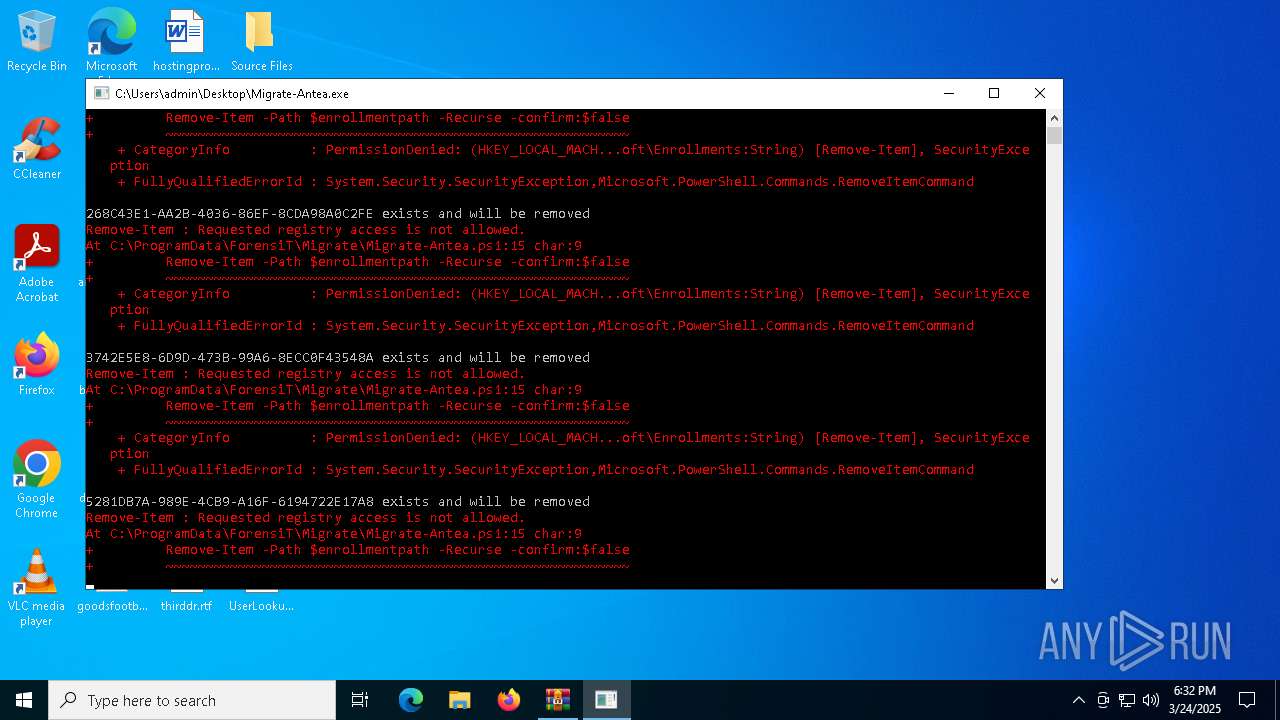
Changes powershell execution policy (Bypass)
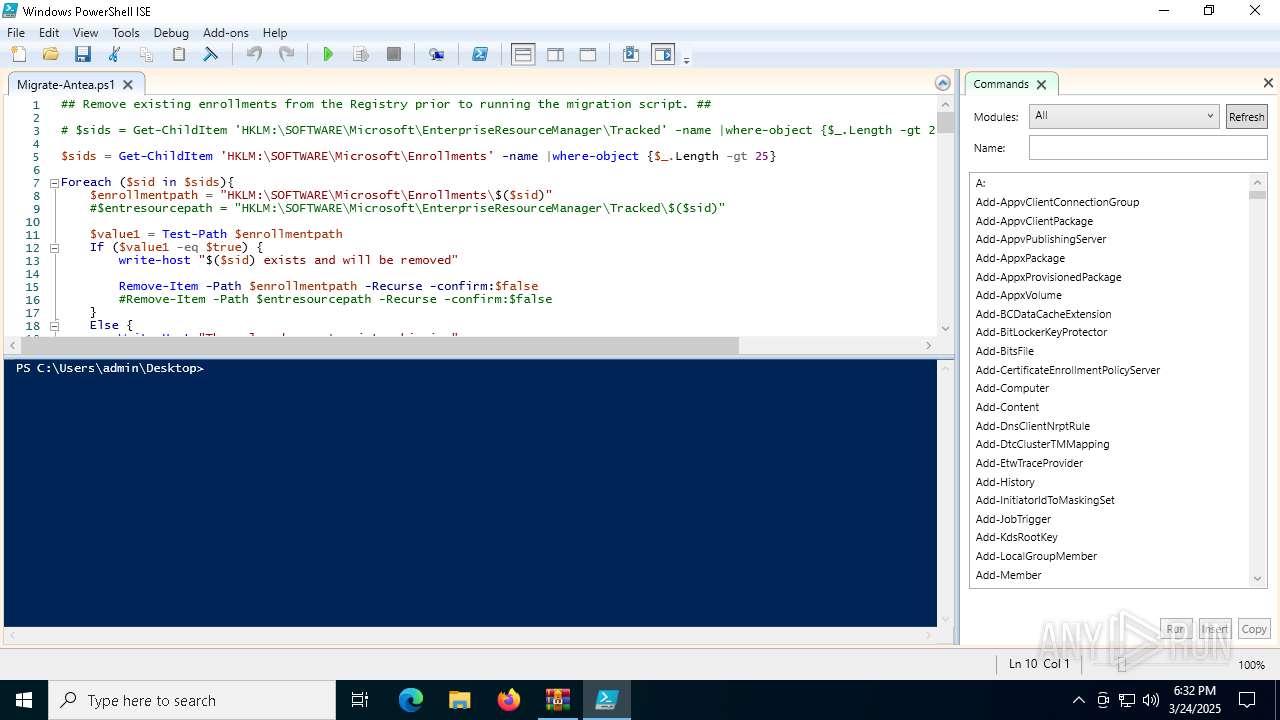
- Migrate-Antea.exe (PID: 7456)
- Migrate-Antea.exe (PID: 1132)
SUSPICIOUS
Gets path to any of the special folders (POWERSHELL)
- powershell.exe (PID: 7868)
- powershell.exe (PID: 3332)
Executable content was dropped or overwritten
- Migrate-Antea.exe (PID: 7456)
- Profwiz.exe (PID: 7824)
- Profwiz.exe (PID: 7528)
Starts POWERSHELL.EXE for commands execution
- Migrate-Antea.exe (PID: 7456)
- Migrate-Antea.exe (PID: 1132)
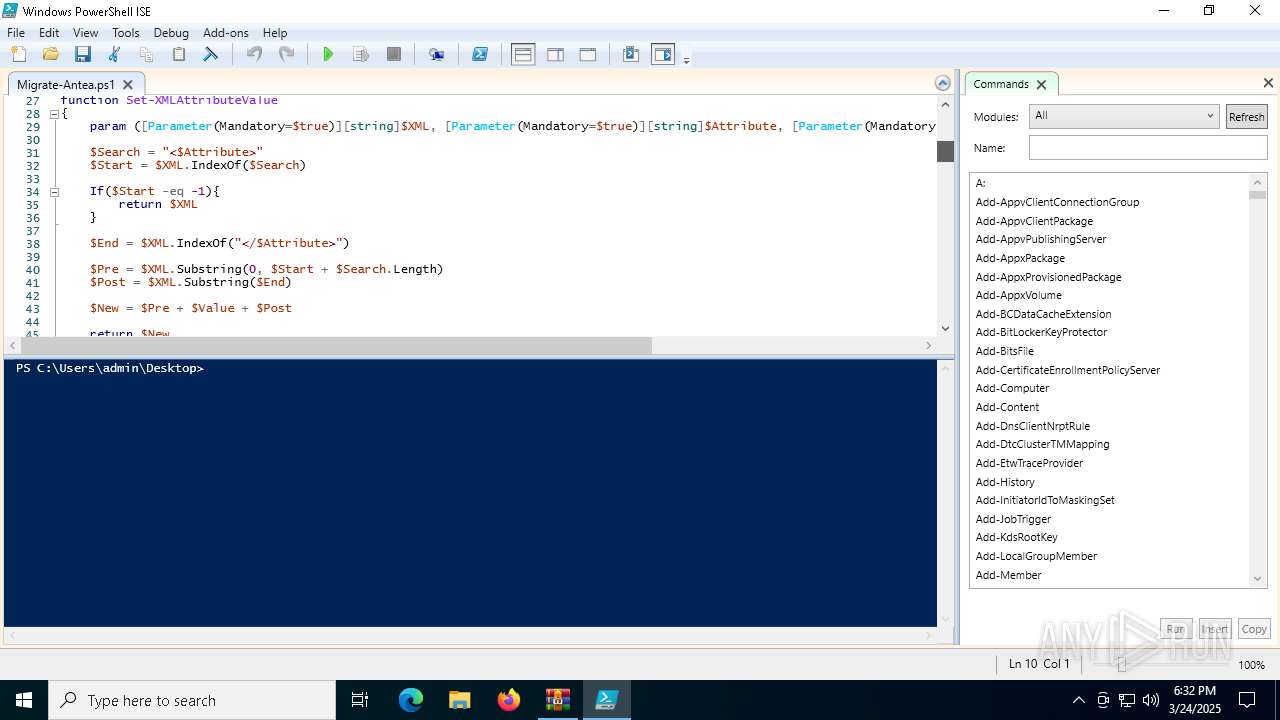
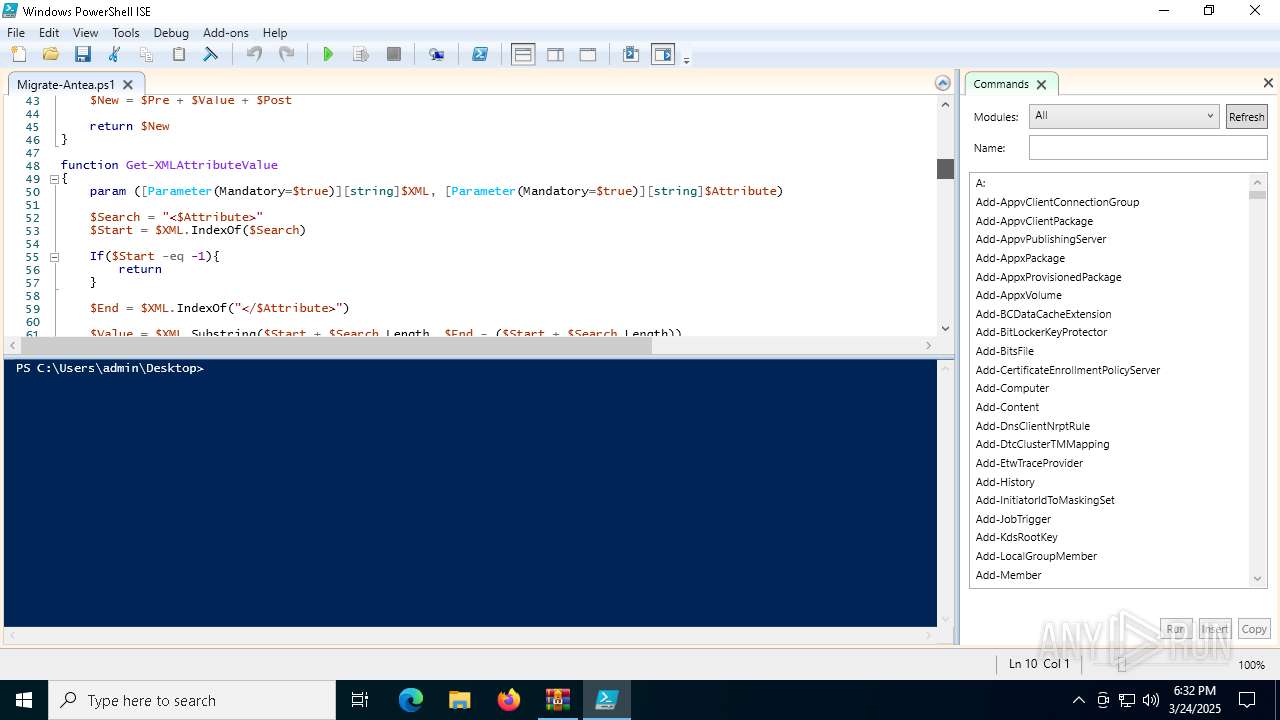
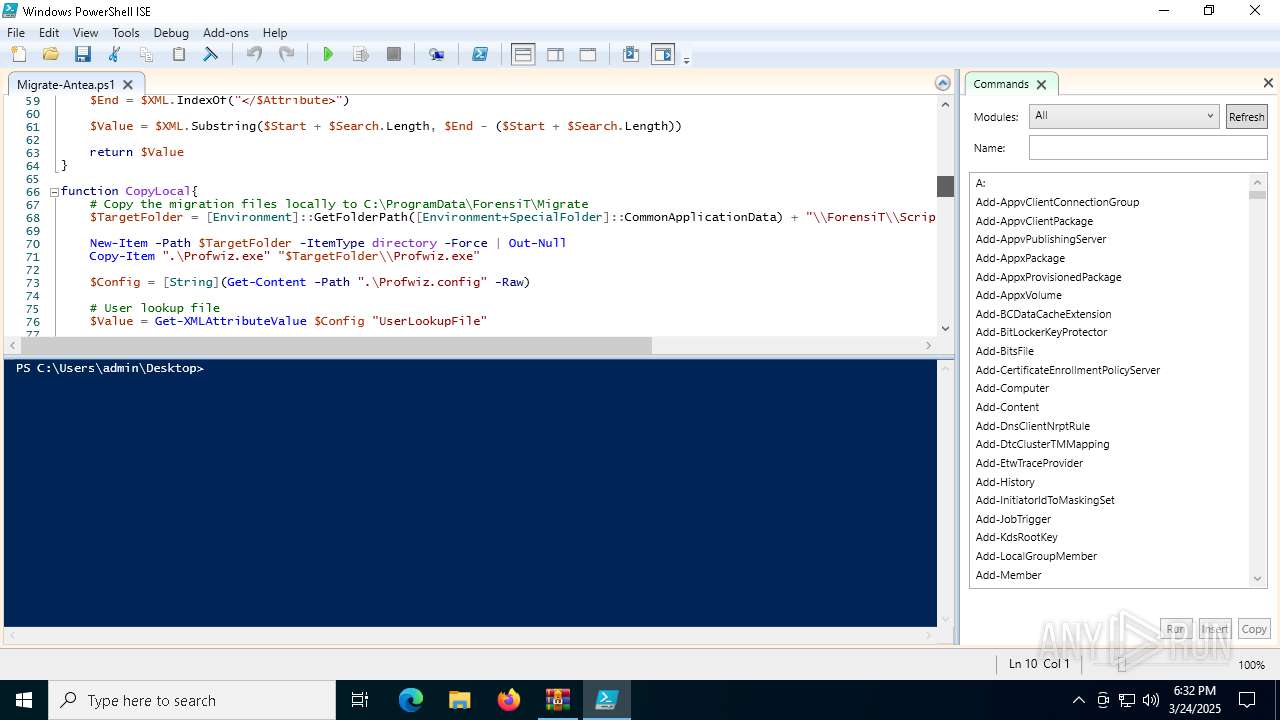
The process executes Powershell scripts
- Migrate-Antea.exe (PID: 7456)
- Migrate-Antea.exe (PID: 1132)
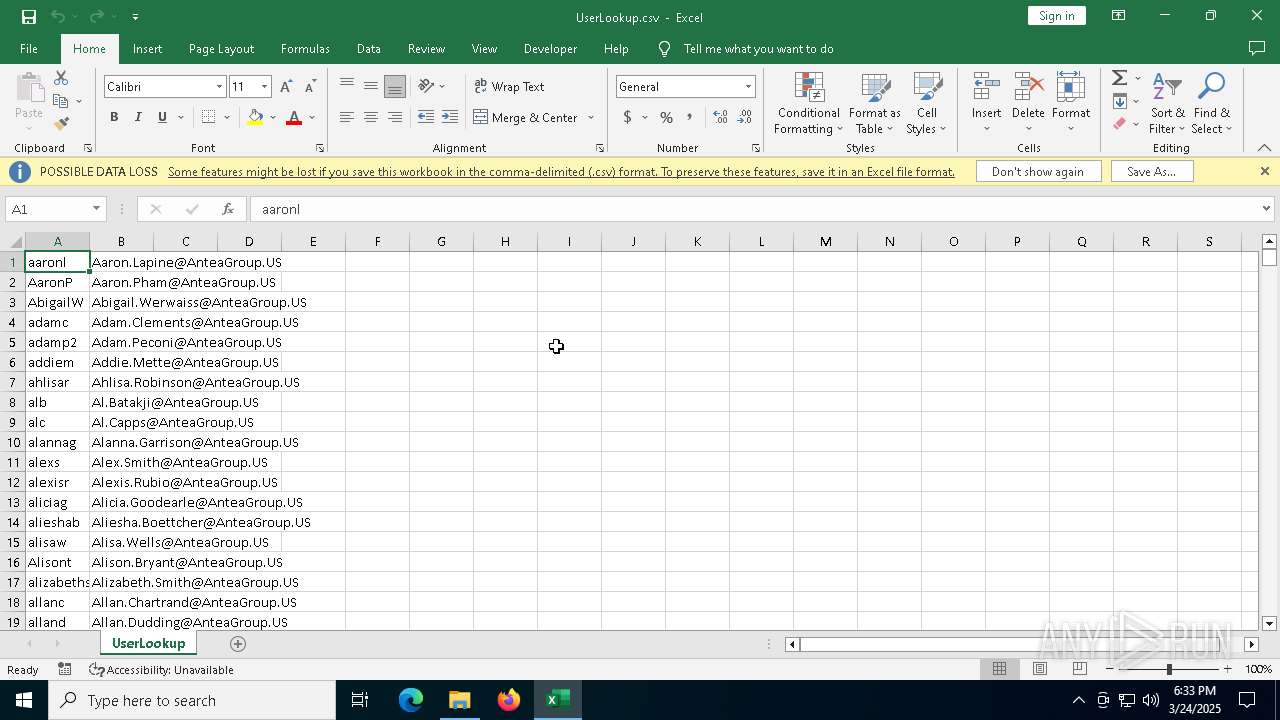
Opens a file (MACROS)
- EXCEL.EXE (PID: 8132)
Reads data from a file (MACROS)
- EXCEL.EXE (PID: 8132)
INFO
Creates files or folders in the user directory
- powershell_ise.exe (PID: 5968)
The sample compiled with english language support
- WinRAR.exe (PID: 7356)
- Migrate-Antea.exe (PID: 7456)
- Profwiz.exe (PID: 7824)
- Profwiz.exe (PID: 7528)
Checks current location (POWERSHELL)
- powershell_ise.exe (PID: 5968)
Manual execution by a user
- powershell_ise.exe (PID: 5968)
- Migrate-Antea.exe (PID: 7456)
- Migrate-Antea.exe (PID: 1132)
- powershell.exe (PID: 4784)
- EXCEL.EXE (PID: 8132)
- Profwiz.exe (PID: 1748)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7356)
Checks proxy server information
- powershell_ise.exe (PID: 5968)
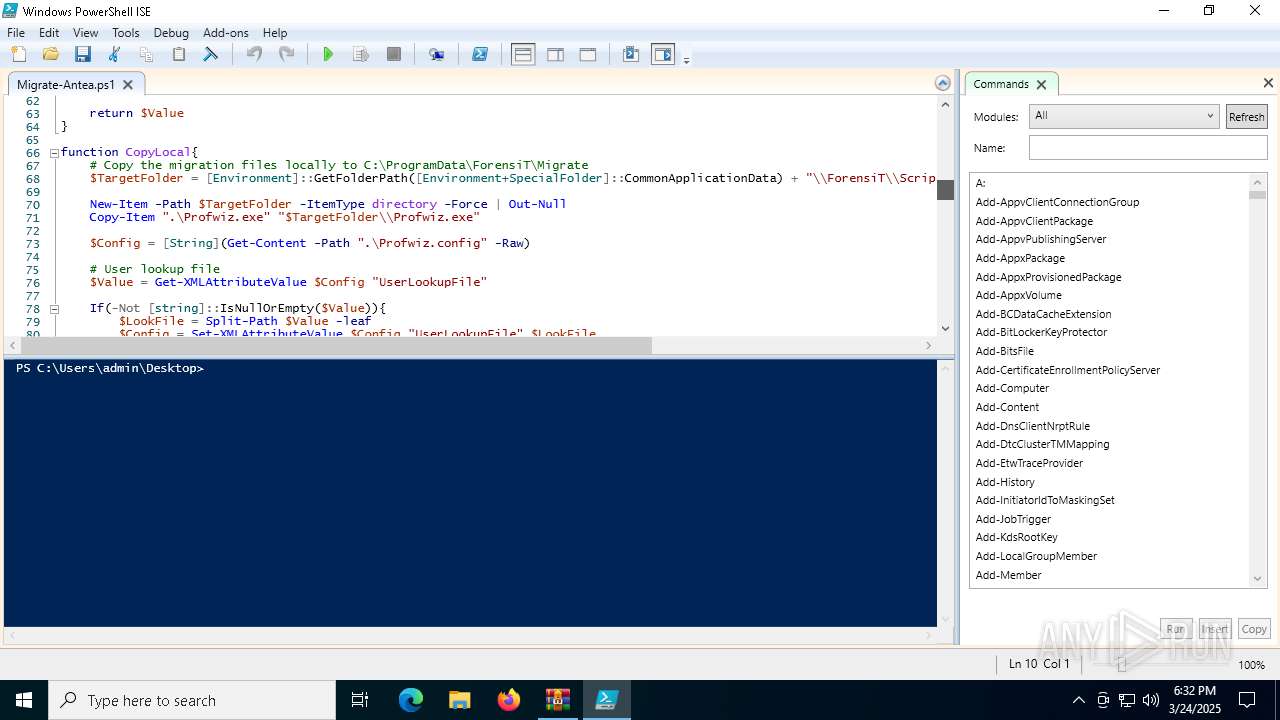
Creates files in the program directory
- Migrate-Antea.exe (PID: 7456)
- Profwiz.exe (PID: 7824)
Reads security settings of Internet Explorer
- powershell_ise.exe (PID: 5968)
Checks supported languages
- Migrate-Antea.exe (PID: 7456)
- Profwiz.exe (PID: 7824)
- Profwiz.exe (PID: 1748)
Create files in a temporary directory
- powershell_ise.exe (PID: 5968)
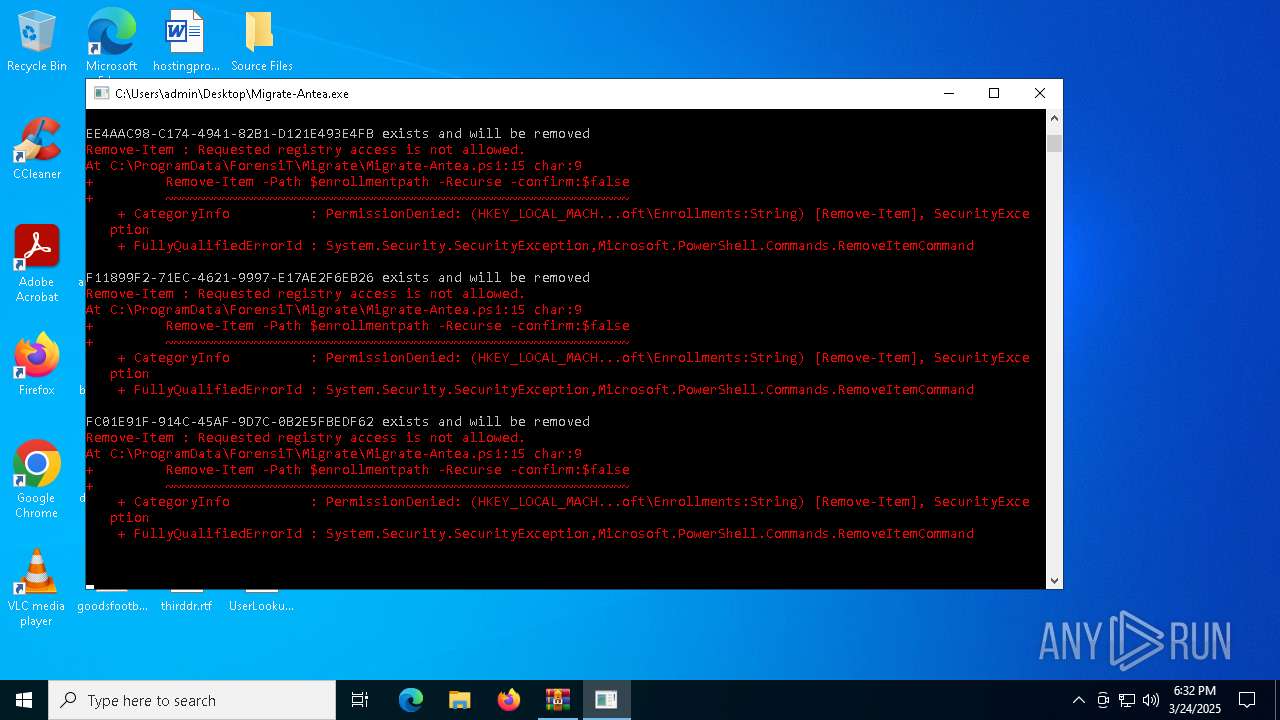
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7868)
- powershell.exe (PID: 4784)
- powershell.exe (PID: 3332)
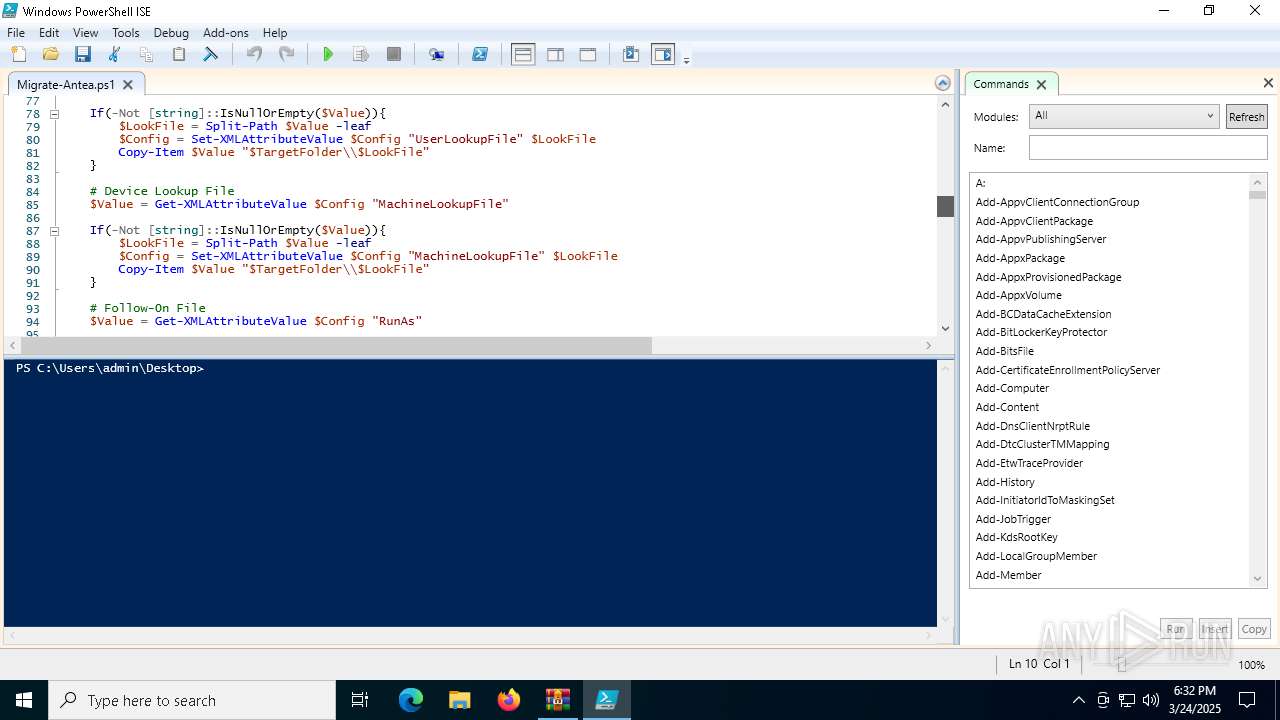
Gets data length (POWERSHELL)
- powershell.exe (PID: 7868)
- powershell.exe (PID: 4784)
- powershell.exe (PID: 3332)
Reads the software policy settings
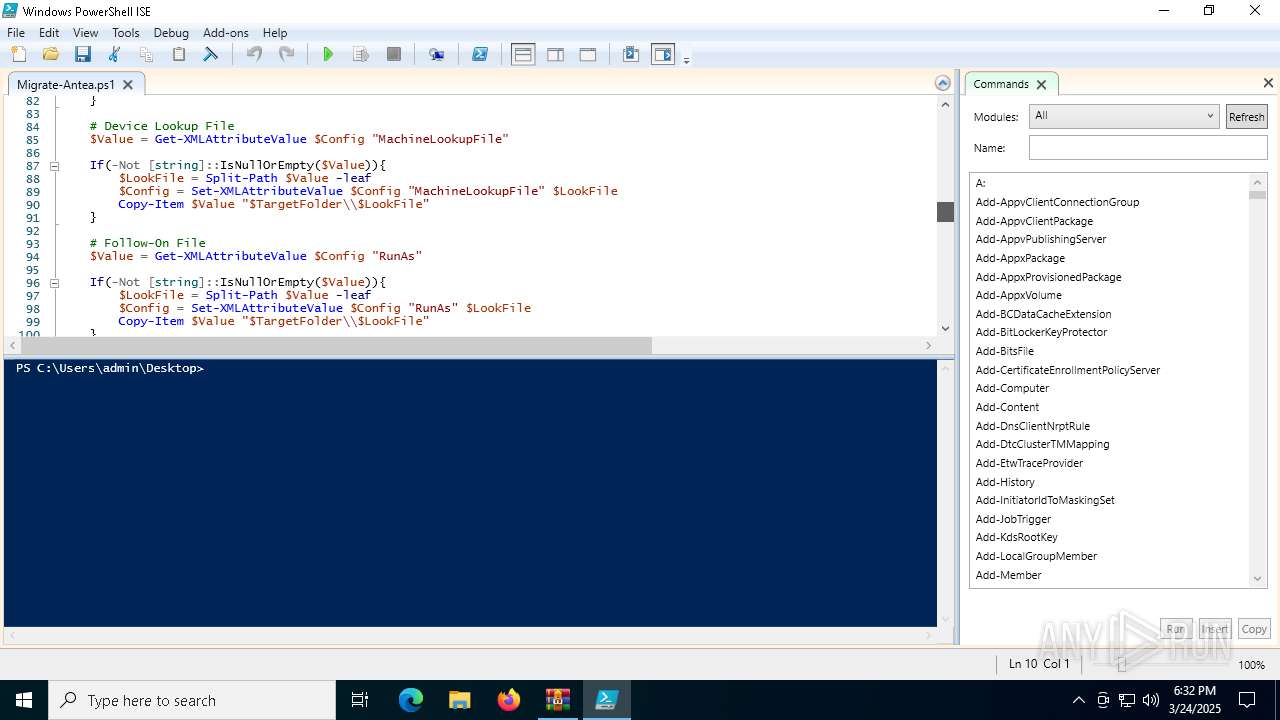
- slui.exe (PID: 7552)
Reads the computer name
- Profwiz.exe (PID: 7824)
- Profwiz.exe (PID: 1748)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
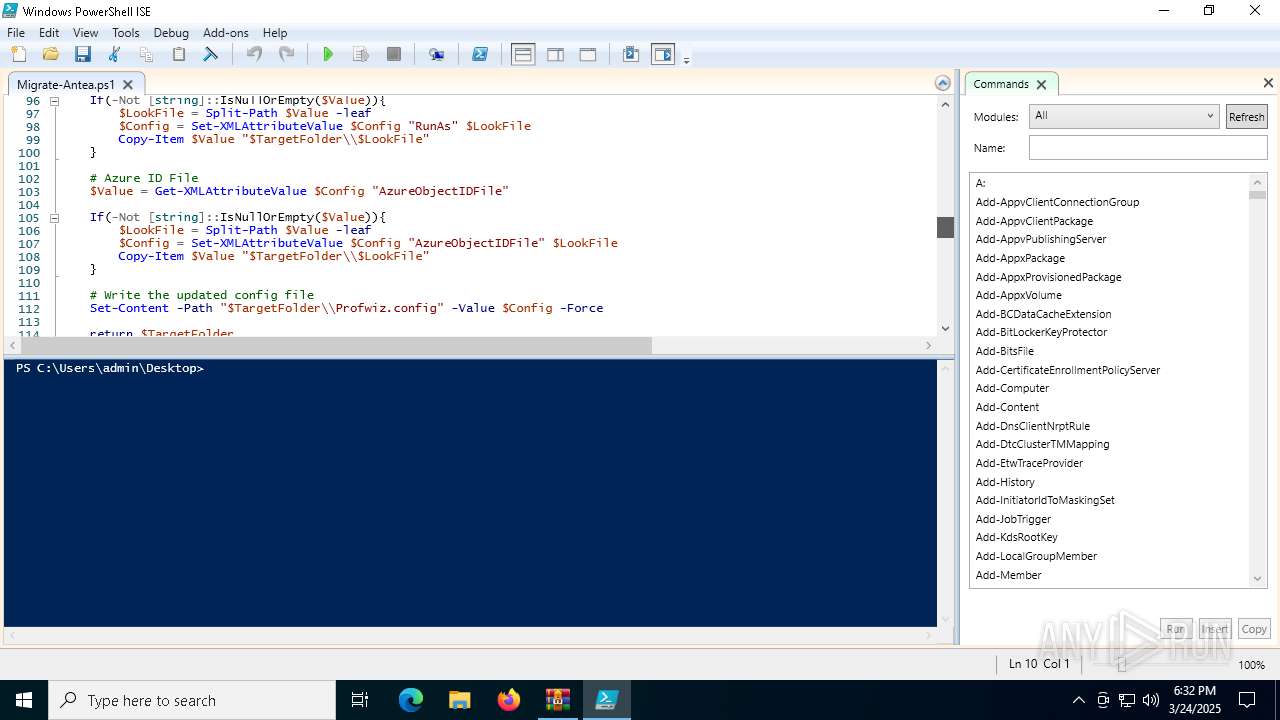
| ZipModifyDate: | 2024:10:14 12:58:30 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Antea/ |
Total processes
157
Monitored processes
18
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
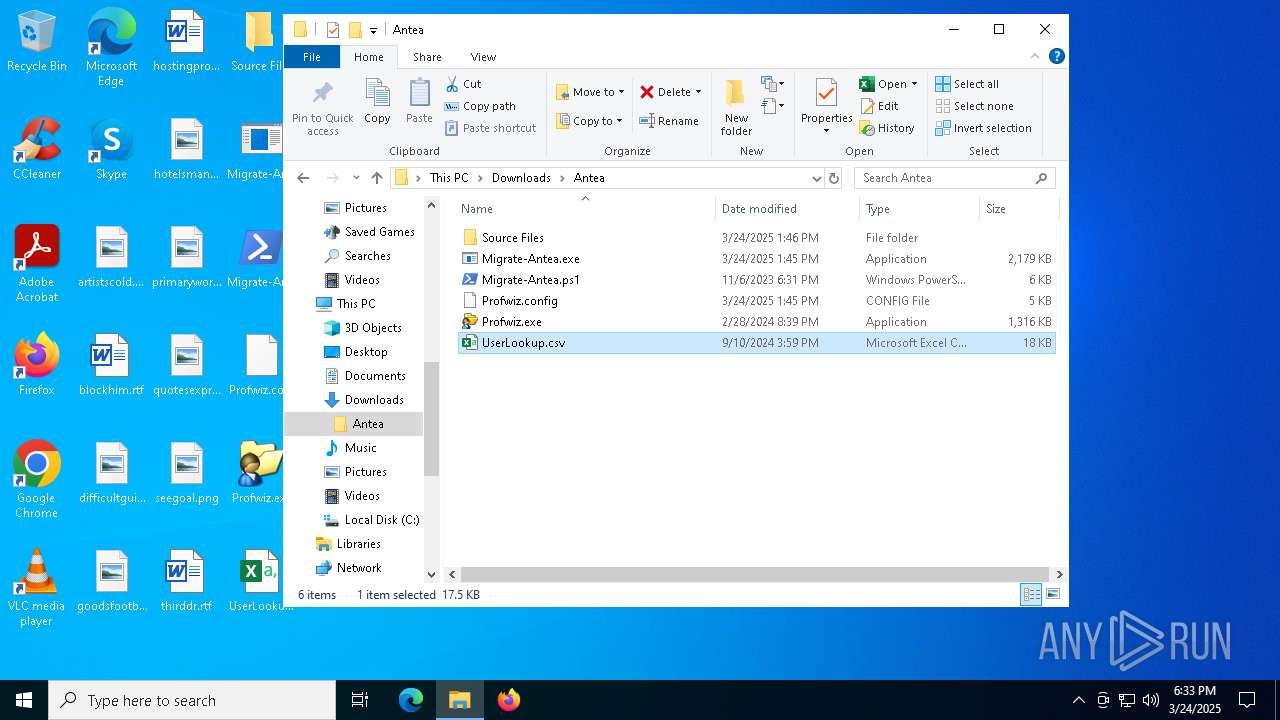
| 1132 | "C:\Users\admin\Downloads\Antea\Migrate-Antea.exe" | C:\Users\admin\Downloads\Antea\Migrate-Antea.exe | — | explorer.exe | |||||||||||
User: admin Company: ForensiT Integrity Level: MEDIUM Description: Create and run a Single Deployment File Exit code: 0 Version: 2.0.0.1 Modules
| |||||||||||||||
| 1300 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Migrate-Antea.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1748 | "C:\Users\admin\Downloads\Antea\Profwiz.exe" | C:\Users\admin\Downloads\Antea\Profwiz.exe | — | explorer.exe | |||||||||||
User: admin Company: ForensiT Software Limited Integrity Level: MEDIUM Description: ForensiT User Profile Wizard Version: 24.6.1293.0 Modules
| |||||||||||||||
| 3332 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe -ExecutionPolicy Bypass -File "C:\ProgramData\ForensiT\Migrate\Migrate-Antea.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | Migrate-Antea.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4208 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4784 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ep bypass "C:\Users\admin\Downloads\Antea\Migrate-Antea.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 3221225786 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
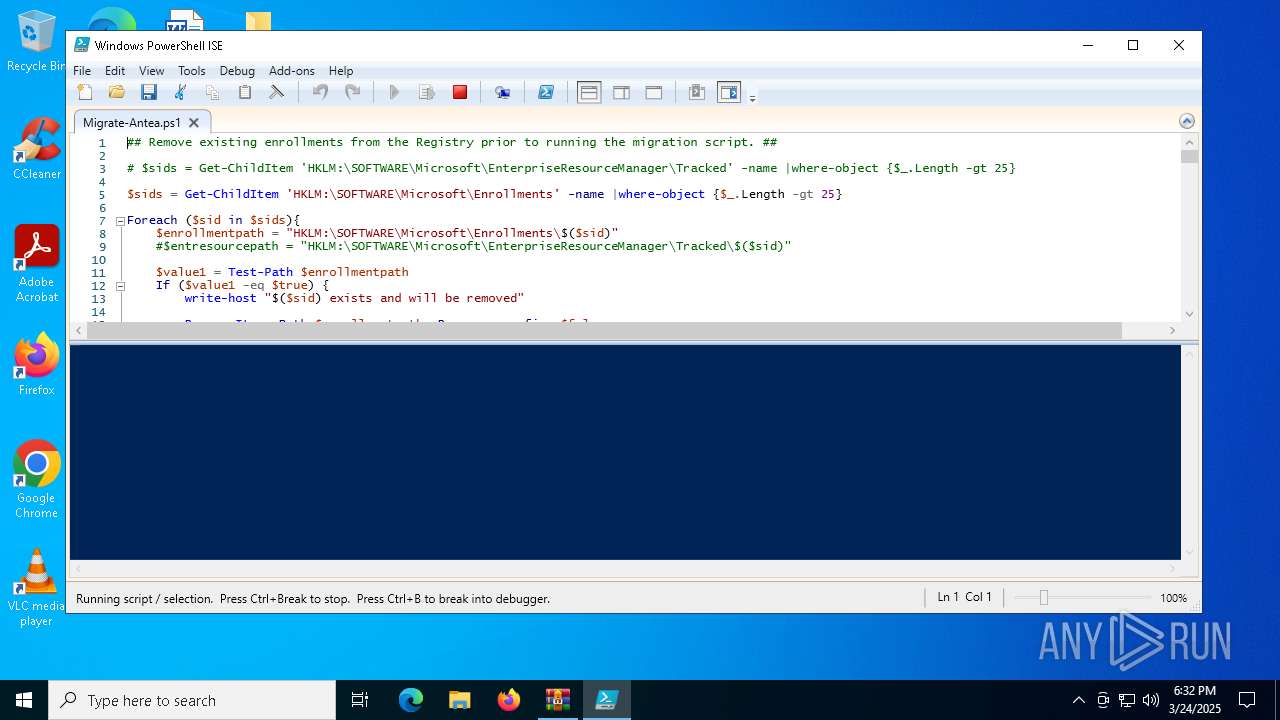
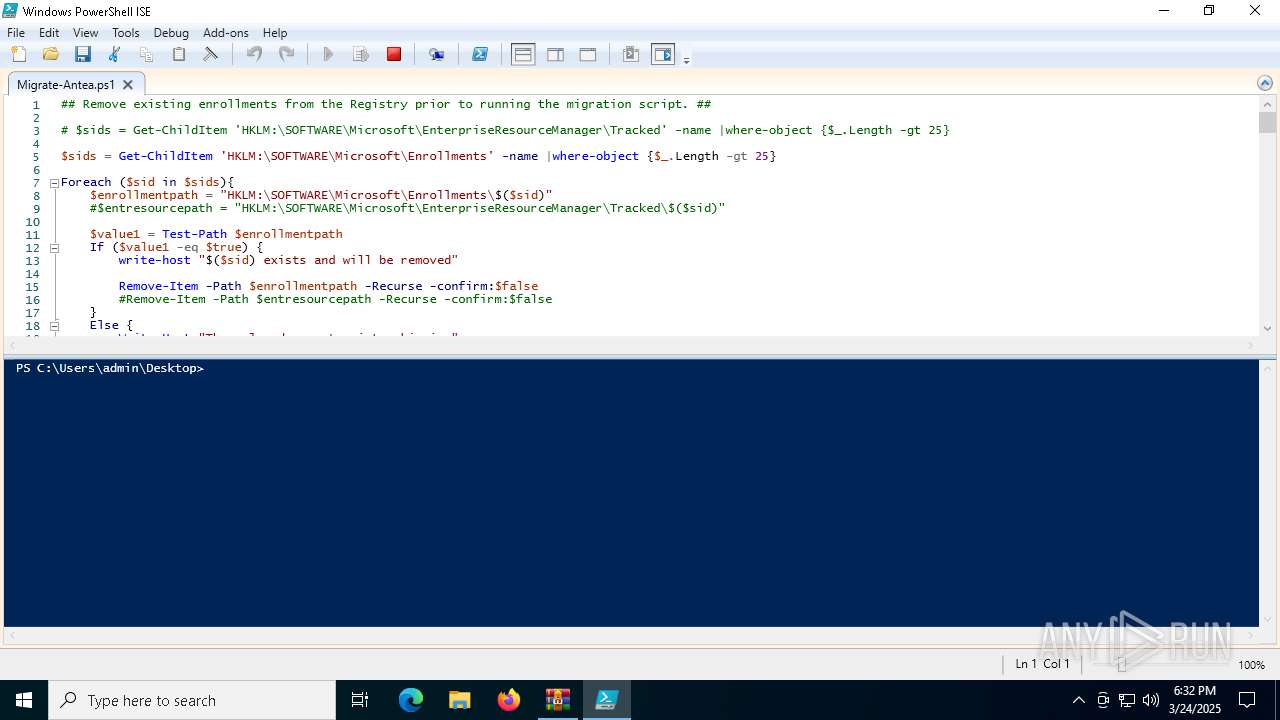
| 5968 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell_ise.exe" "C:\Users\admin\Desktop\Migrate-Antea.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell_ise.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell ISE Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7356 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Antea 5.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 7452 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Migrate-Antea.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7456 | "C:\Users\admin\Desktop\Migrate-Antea.exe" | C:\Users\admin\Desktop\Migrate-Antea.exe | explorer.exe | ||||||||||||
User: admin Company: ForensiT Integrity Level: MEDIUM Description: Create and run a Single Deployment File Exit code: 0 Version: 2.0.0.1 Modules
| |||||||||||||||
Total events
32 176
Read events
31 858
Write events
260
Delete events
58
Modification events
| (PID) Process: | (7356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Antea 5.zip | |||
| (PID) Process: | (7356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (7356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
8
Suspicious files
43
Text files
44
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7356 | WinRAR.exe | C:\Users\admin\Desktop\Migrate-Antea.exe | executable | |
MD5:B371D4AA6F7E7414D524B2AAC3D9A067 | SHA256:FA68B256BCE4F9A3931E730A7CD9E4B318EBC06974BE257DBC6EA44CB7C99CEA | |||
| 7356 | WinRAR.exe | C:\Users\admin\Desktop\Source Files\ICD.log | text | |
MD5:4BDE2C4BFD83541CD8BAB18FB74F0DE6 | SHA256:BF25484A1C8AED3742164637F8470C685D2CEEA0A22784C980E45C917EEA1137 | |||
| 7356 | WinRAR.exe | C:\Users\admin\Desktop\Source Files\ICDCommon.log | text | |
MD5:1AEDB701816A70CE27A23087C2A2BD9C | SHA256:BBDE309442DC3EFE01EFDA69C4FB12CEEB4FCB95D9709B298AB5F5397CCF4AA7 | |||
| 7356 | WinRAR.exe | C:\Users\admin\Desktop\Profwiz.exe | executable | |
MD5:13EF7688CEE502CC4E6C3142D06583FB | SHA256:D1E42E2380B541D56DDB6B143B575042BA125B3038C1FF7D24E5613DCD971115 | |||
| 7356 | WinRAR.exe | C:\Users\admin\Desktop\Profwiz.config | xml | |
MD5:00D82635F4A4A2F2C3EA121486E3C65F | SHA256:78F8237AA3BC7645809601F67FC187BADD9B0940961A0062922B25859D79BB3B | |||
| 7356 | WinRAR.exe | C:\Users\admin\Desktop\Source Files\customizations.xml | xml | |
MD5:9C1D0552FBAE6D42E4D7033FAC8FF203 | SHA256:49B646A15CBD39072B4FBF6BE0D960C308BB47B97ABBC57F64C96CE388F22B3F | |||
| 7356 | WinRAR.exe | C:\Users\admin\Desktop\Source Files\AG2.ppkg | binary | |
MD5:0384927EFE6CB559D85BD4622014AC26 | SHA256:140F9422FCC2DDBA90E928CC9B0C6F253C628104D5CFC4DD1FE92C4C5EA2C99A | |||
| 7356 | WinRAR.exe | C:\Users\admin\Desktop\Source Files\AG2.cat | binary | |
MD5:48F1C44617EABE4477EC7BEFD0F66564 | SHA256:9A93937003D90F3E124A93495568476B2D1B992A837990972B885AD4FB83A0B6 | |||
| 7356 | WinRAR.exe | C:\Users\admin\Desktop\Source Files\AG2.icdproj.xml | xml | |
MD5:44DEBBB47B86332483352A2E5356958C | SHA256:A73E3A48C3AB68598DD0579C73D7D77CB26DF42F20AD4E70AD5FDE8A178AA8EE | |||
| 7356 | WinRAR.exe | C:\Users\admin\Desktop\Source Files\ForensiTAzureID.xml | xml | |
MD5:59223C8C793D03587B5A406095240A1C | SHA256:399ED0174F26E8AE1447E5C73AA8793CD06627CA468741BB107A5F12910566E5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
36
DNS requests
23
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6036 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7732 | backgroundTaskHost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6036 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5968 | powershell_ise.exe | GET | 200 | 23.48.23.162:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5968 | powershell_ise.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | — | — | whitelisted |
8132 | EXCEL.EXE | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
8132 | EXCEL.EXE | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4996 | RUXIMICS.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 20.190.160.131:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 23.54.109.203:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
7732 | backgroundTaskHost.exe | 20.199.58.43:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |