| download: | index.html |
| Full analysis: | https://app.any.run/tasks/0636869d-fa84-446d-83db-42147809549a |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | March 14, 2019, 15:55:04 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, UTF-8 Unicode text, with very long lines |
| MD5: | 135428F63281950347D2FD4C0C362D1E |
| SHA1: | 5CAA4EE7AD2A1965FCBEF5FEA9419A903FBCEB5C |
| SHA256: | 02C717BFB2DB81690329092E4A20EDE6D70575F05119D1E6492490D411DD323E |
| SSDEEP: | 1536:BV6RAfbaDUk0F0ePpxrP9NsYdRiXxsLzfE7:B0RAfbB0ePzrliY+Xxsk |
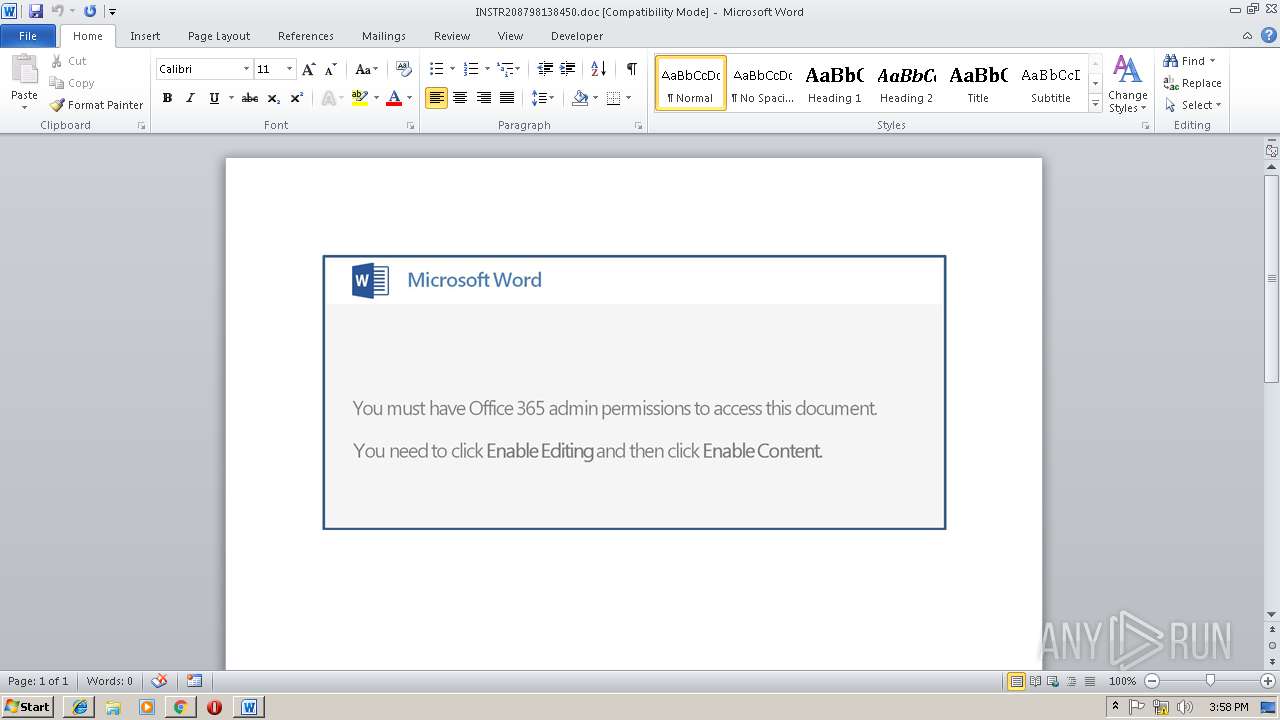
MALICIOUS
Application was dropped or rewritten from another process
- 272.exe (PID: 3536)
- 272.exe (PID: 2284)
- wabmetagen.exe (PID: 1832)
- wabmetagen.exe (PID: 996)
Downloads executable files from the Internet
- powershell.exe (PID: 2864)
Emotet process was detected
- wabmetagen.exe (PID: 996)
Changes the autorun value in the registry
- wabmetagen.exe (PID: 1832)
EMOTET was detected
- wabmetagen.exe (PID: 1832)
Connects to CnC server
- wabmetagen.exe (PID: 1832)
SUSPICIOUS
Application launched itself
- WINWORD.EXE (PID: 3204)
- 272.exe (PID: 2284)
- wabmetagen.exe (PID: 996)
Starts Microsoft Office Application
- chrome.exe (PID: 3116)
- WINWORD.EXE (PID: 3204)
Creates files in the user directory
- powershell.exe (PID: 2864)
Executable content was dropped or overwritten
- powershell.exe (PID: 2864)
- 272.exe (PID: 3536)
Starts itself from another location
- 272.exe (PID: 3536)
INFO
Application launched itself
- iexplore.exe (PID: 3348)
- chrome.exe (PID: 3116)
Changes internet zones settings
- iexplore.exe (PID: 3348)
Reads Internet Cache Settings
- chrome.exe (PID: 3116)
- iexplore.exe (PID: 3916)
Reads internet explorer settings
- iexplore.exe (PID: 3916)
Creates files in the user directory
- iexplore.exe (PID: 3916)
- WINWORD.EXE (PID: 3204)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3204)
- WINWORD.EXE (PID: 1856)
Reads settings of System Certificates
- chrome.exe (PID: 3116)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .html | | | HyperText Markup Language (100) |
|---|
Total processes
60
Monitored processes
23
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 996 | "C:\Users\admin\AppData\Local\wabmetagen\wabmetagen.exe" | C:\Users\admin\AppData\Local\wabmetagen\wabmetagen.exe | 272.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Sticky Notes Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1104 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=988,371649513052297509,664695571885234646,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=4B8ED70175A5A44BB68C1ED34F67A046 --mojo-platform-channel-handle=780 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 1804 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=988,371649513052297509,664695571885234646,131072 --enable-features=PasswordImport --disable-gpu-sandbox --gpu-preferences=KAAAAAAAAACAAwBAAQAAAAAAAAAAAGAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --service-request-channel-token=E6F3BBDD36AF4A59769365C373C2C5C0 --mojo-platform-channel-handle=2024 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 1832 | "C:\Users\admin\AppData\Local\wabmetagen\wabmetagen.exe" | C:\Users\admin\AppData\Local\wabmetagen\wabmetagen.exe | wabmetagen.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Sticky Notes Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1856 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /Embedding | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2284 | "C:\Users\admin\272.exe" | C:\Users\admin\272.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Sticky Notes Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2564 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=988,371649513052297509,664695571885234646,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=9E246AD8007E5DA8CC52C3705A58BA3E --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=9E246AD8007E5DA8CC52C3705A58BA3E --renderer-client-id=8 --mojo-platform-channel-handle=3756 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2656 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=988,371649513052297509,664695571885234646,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=EB0941A4031042CB9F4D132C748A1F34 --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=EB0941A4031042CB9F4D132C748A1F34 --renderer-client-id=6 --mojo-platform-channel-handle=2912 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2704 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=988,371649513052297509,664695571885234646,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAACAAwBAAQAAAAAAAAAAAGAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --service-request-channel-token=21FB5BA95DD0430DD0C881FF2B62B2A0 --mojo-platform-channel-handle=1000 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2828 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=988,371649513052297509,664695571885234646,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=EE70BBAFD45958FB38161ED5051C48B1 --mojo-platform-channel-handle=3764 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
Total events
3 640
Read events
3 063
Write events
560
Delete events
17
Modification events
| (PID) Process: | (3916) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}\iexplore |
| Operation: | write | Name: | Type |
Value: 3 | |||
| (PID) Process: | (3916) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}\iexplore |
| Operation: | write | Name: | Count |
Value: 3 | |||
| (PID) Process: | (3916) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}\iexplore |
| Operation: | write | Name: | Time |
Value: E307030004000E000F0037001A000C00 | |||
| (PID) Process: | (3916) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}\iexplore |
| Operation: | write | Name: | LoadTime |
Value: 11 | |||
| (PID) Process: | (3348) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3348) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3348) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3348) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (3348) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3348) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000069000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
Executable files
2
Suspicious files
66
Text files
108
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3348 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\R9ZEWH8D\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 3348 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3916 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\RB73MZ6Y\logo[1].png | image | |
MD5:— | SHA256:— | |||
| 3916 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\R9ZEWH8D\Arrow-Malcolm-Merlyn-Leather-Black-Jacket-324x413[1].jpg | image | |
MD5:— | SHA256:— | |||
| 3916 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\RB73MZ6Y\The-Drop-Tom-Hardy-Bob-Blue-Cotton-Jacket-324x413[1].jpg | image | |
MD5:— | SHA256:— | |||
| 3916 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\R9ZEWH8D\Battlestar-Galactica-Pilot-Jacket-324x413[1].jpg | image | |
MD5:— | SHA256:— | |||
| 3916 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\D2YPIJ90\Need-For-Speed-Aaron-Paul-White-Leather-Jacket-324x413[1].jpg | image | |
MD5:— | SHA256:— | |||
| 3916 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0UU90R59\24-TV-Series-Jack-Bauer-Jacket-324x413[1].jpg | image | |
MD5:— | SHA256:— | |||
| 3916 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0UU90R59\Elle-Fanning-Cotton-Jacket-324x413[1].jpg | image | |
MD5:— | SHA256:— | |||
| 3916 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\D2YPIJ90\Jared-Leto-Thirty-Seconds-to-Mars-Jacket-324x413[1].jpg | image | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
49
DNS requests
18
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2864 | powershell.exe | GET | 200 | 178.128.41.189:80 | http://turningspeech.com/rm44r5z/usg/ | GR | executable | 355 Kb | suspicious |
1832 | wabmetagen.exe | GET | 200 | 187.233.152.78:443 | http://187.233.152.78:443/ | MX | binary | 132 b | malicious |
3348 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3348 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
4 | System | 216.97.36.50:445 | www.idealjackets.com | CoreSpace, Inc. | US | suspicious |
4 | System | 216.97.36.50:139 | www.idealjackets.com | CoreSpace, Inc. | US | suspicious |
3916 | iexplore.exe | 216.97.36.50:443 | www.idealjackets.com | CoreSpace, Inc. | US | suspicious |
3116 | chrome.exe | 216.58.208.35:443 | www.gstatic.com | Google Inc. | US | whitelisted |
3116 | chrome.exe | 172.217.23.131:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
3116 | chrome.exe | 172.217.23.170:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
3116 | chrome.exe | 216.58.207.35:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
3116 | chrome.exe | 172.217.18.13:443 | accounts.google.com | Google Inc. | US | whitelisted |
3116 | chrome.exe | 216.58.206.3:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.idealjackets.com |
| suspicious |
www.bing.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
www.google.de |
| whitelisted |
safebrowsing.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
ssl.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
www.google.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2864 | powershell.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2864 | powershell.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
2864 | powershell.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
2864 | powershell.exe | Misc activity | ET INFO EXE IsDebuggerPresent (Used in Malware Anti-Debugging) |
1832 | wabmetagen.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo HTTP request |
1 ETPRO signatures available at the full report