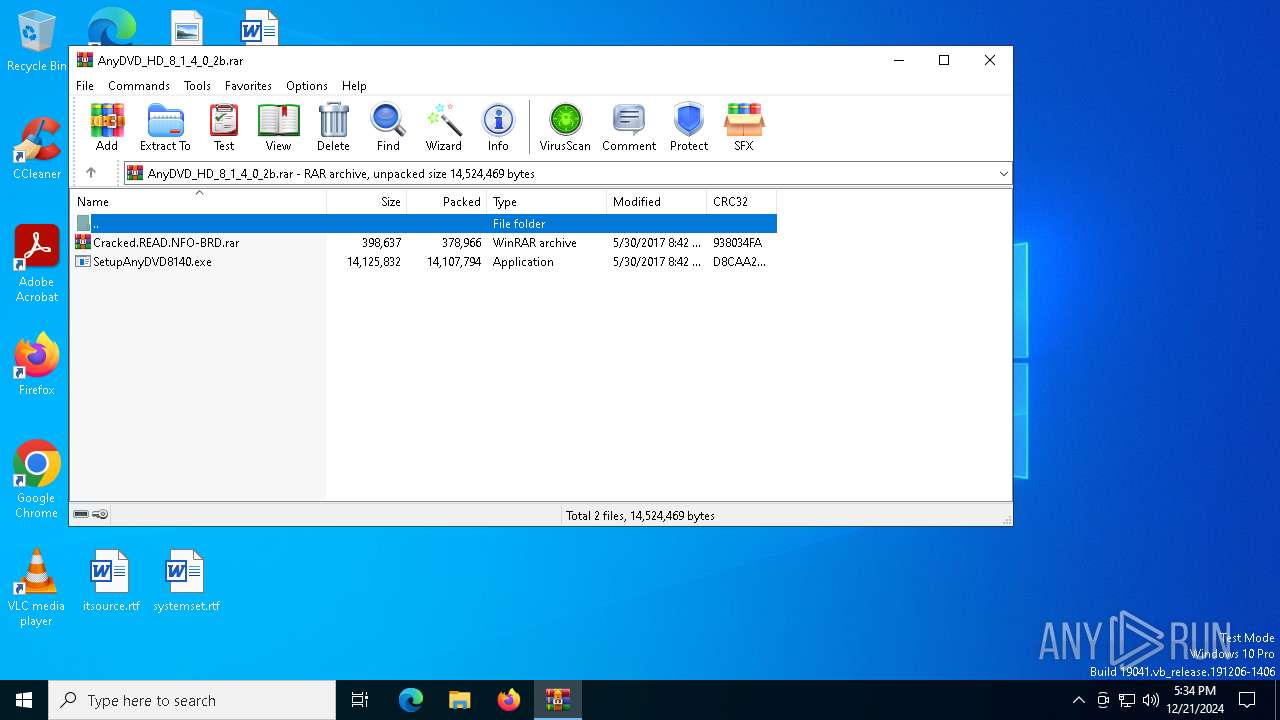
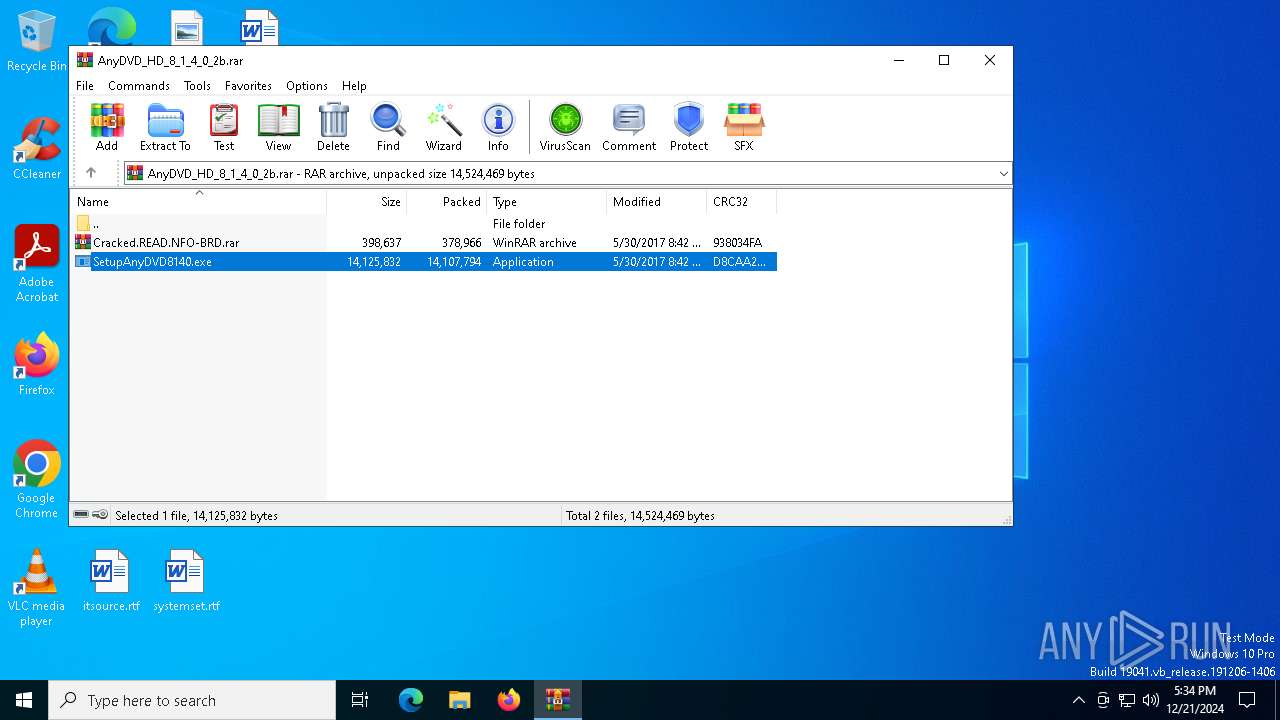
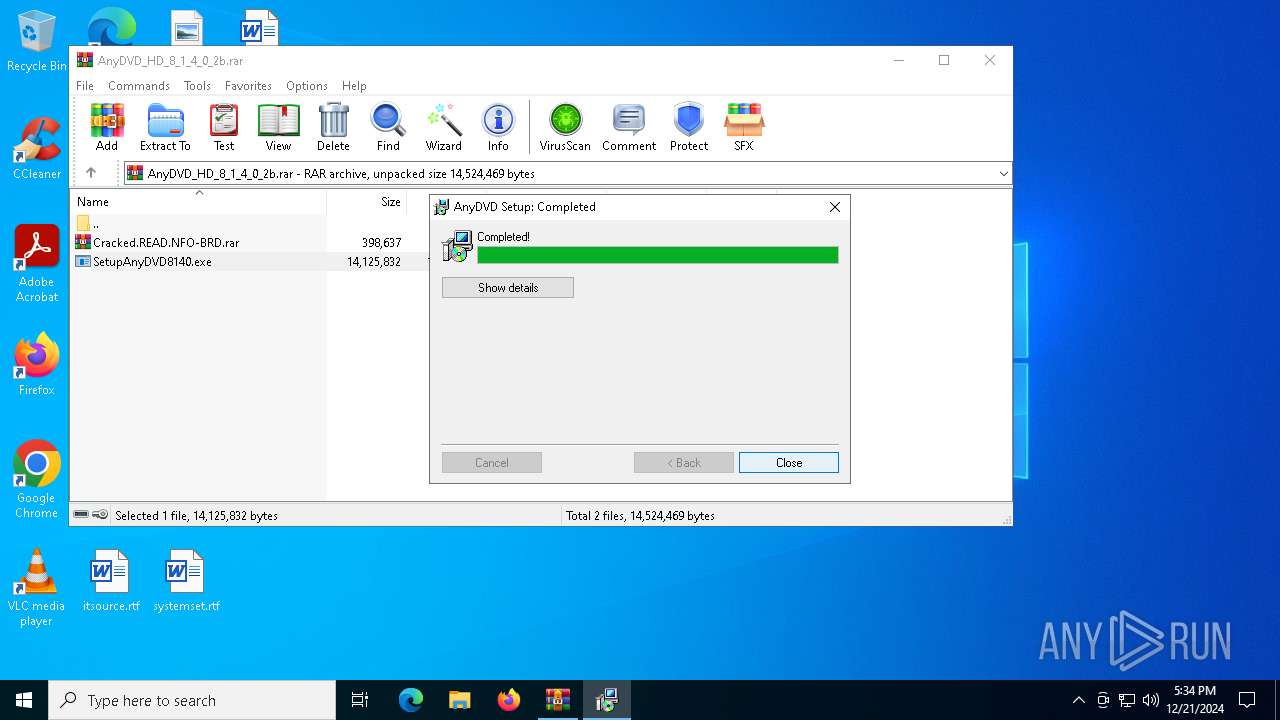
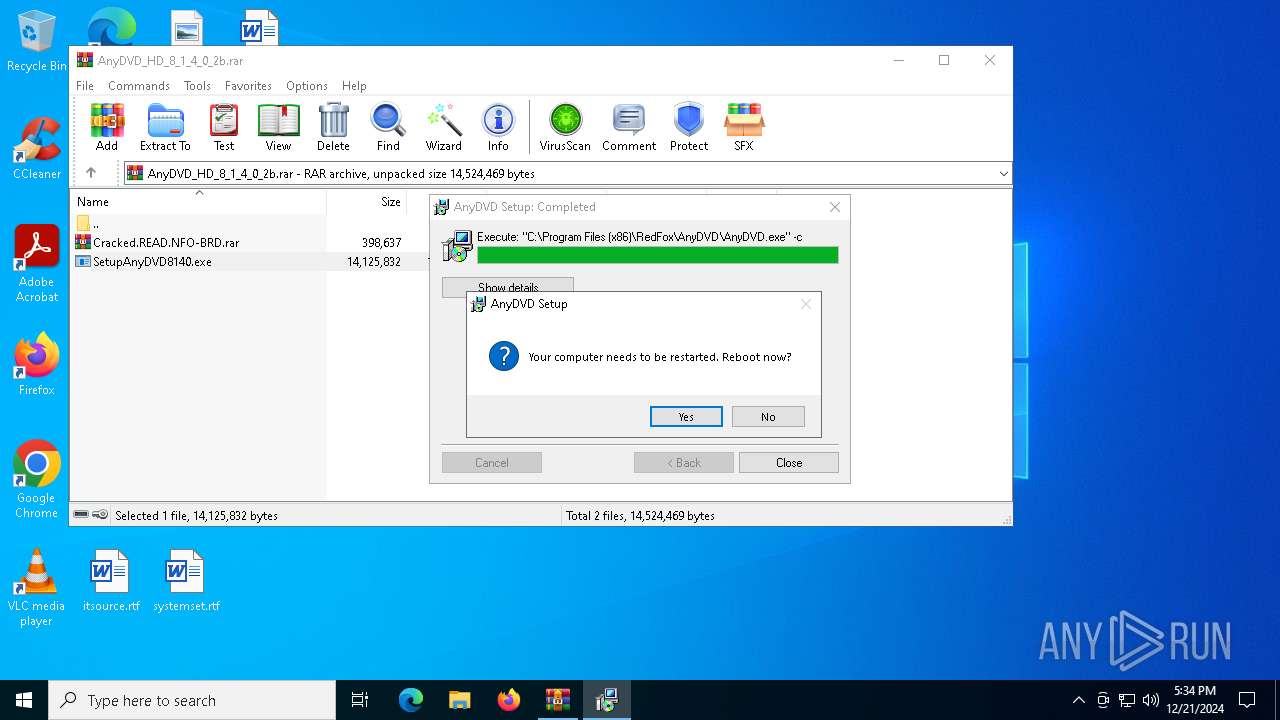
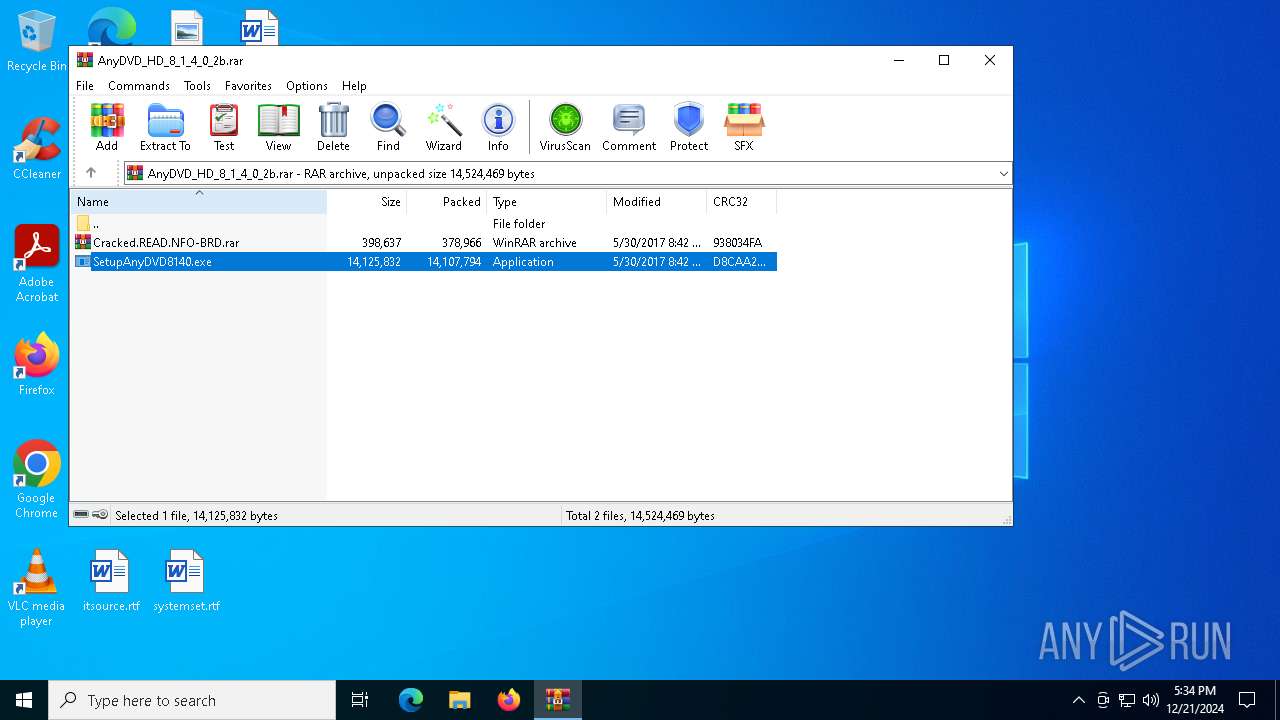
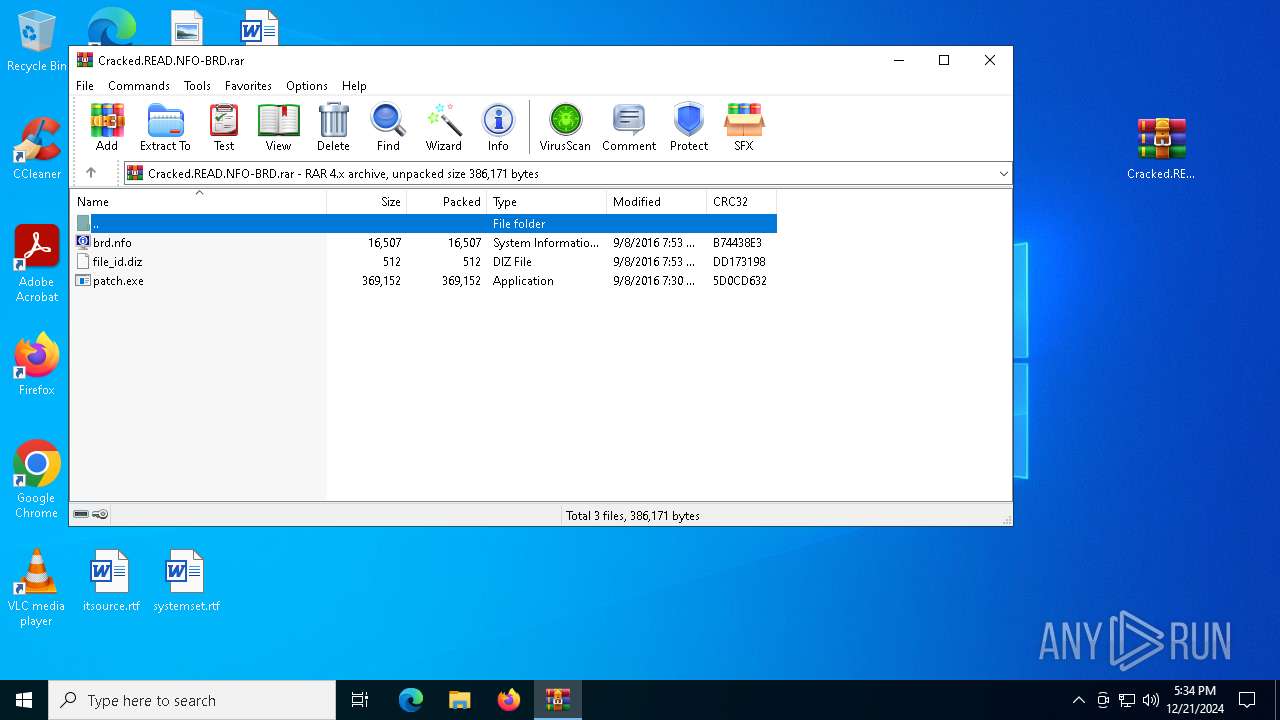
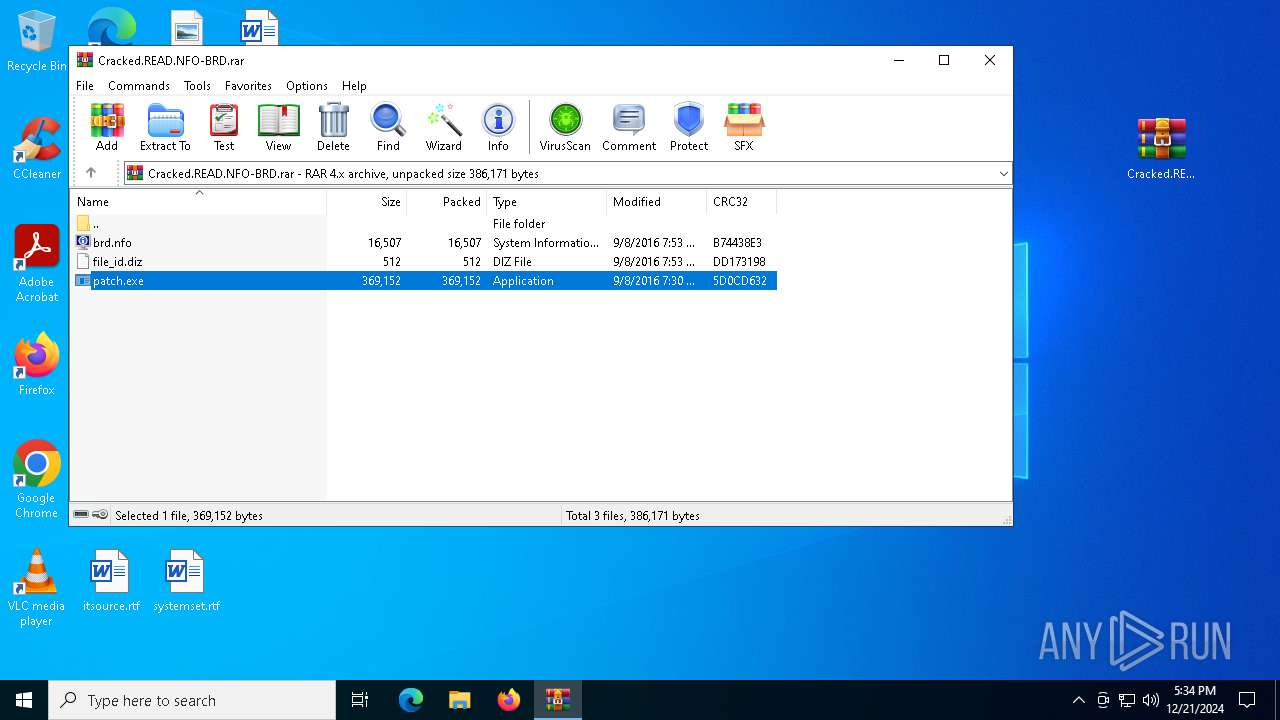
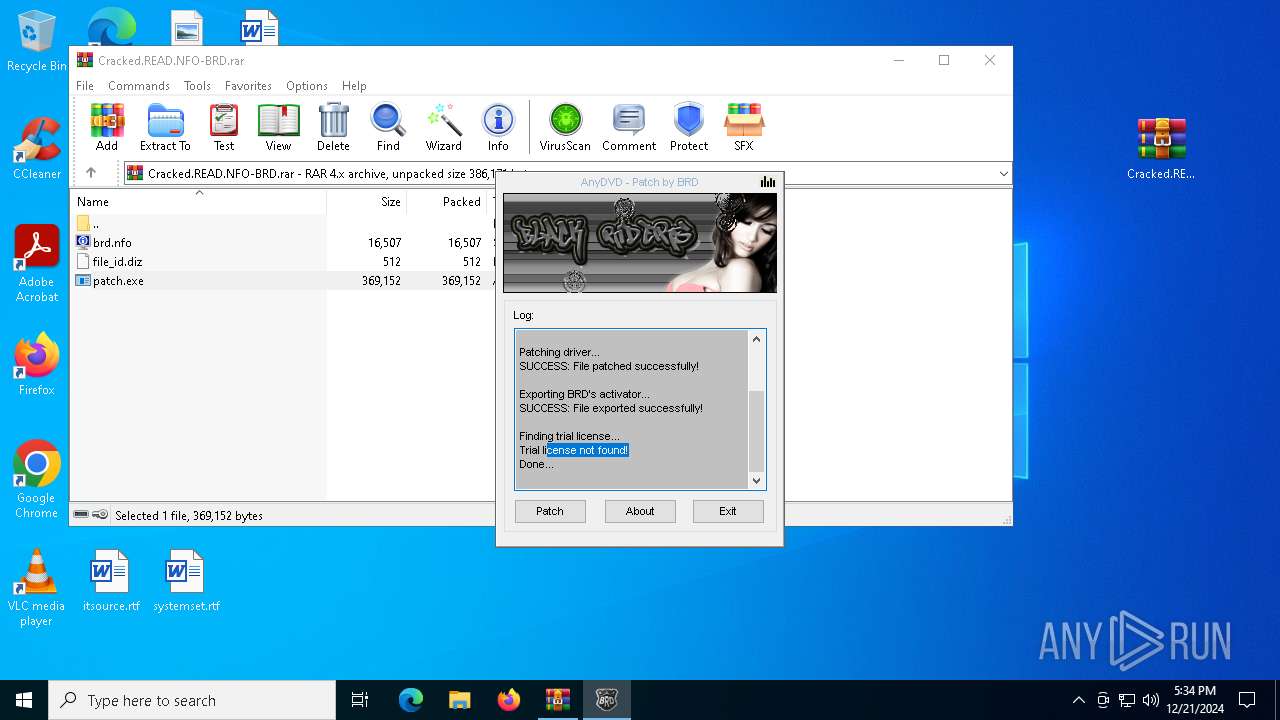
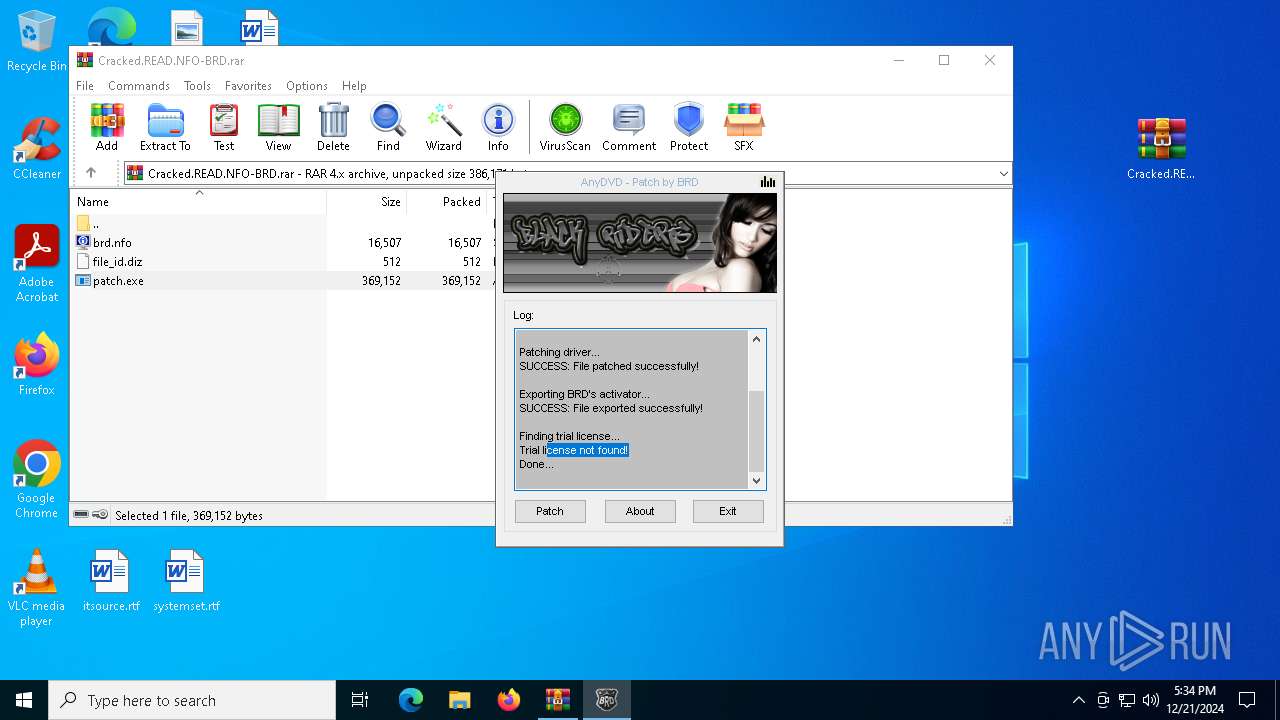
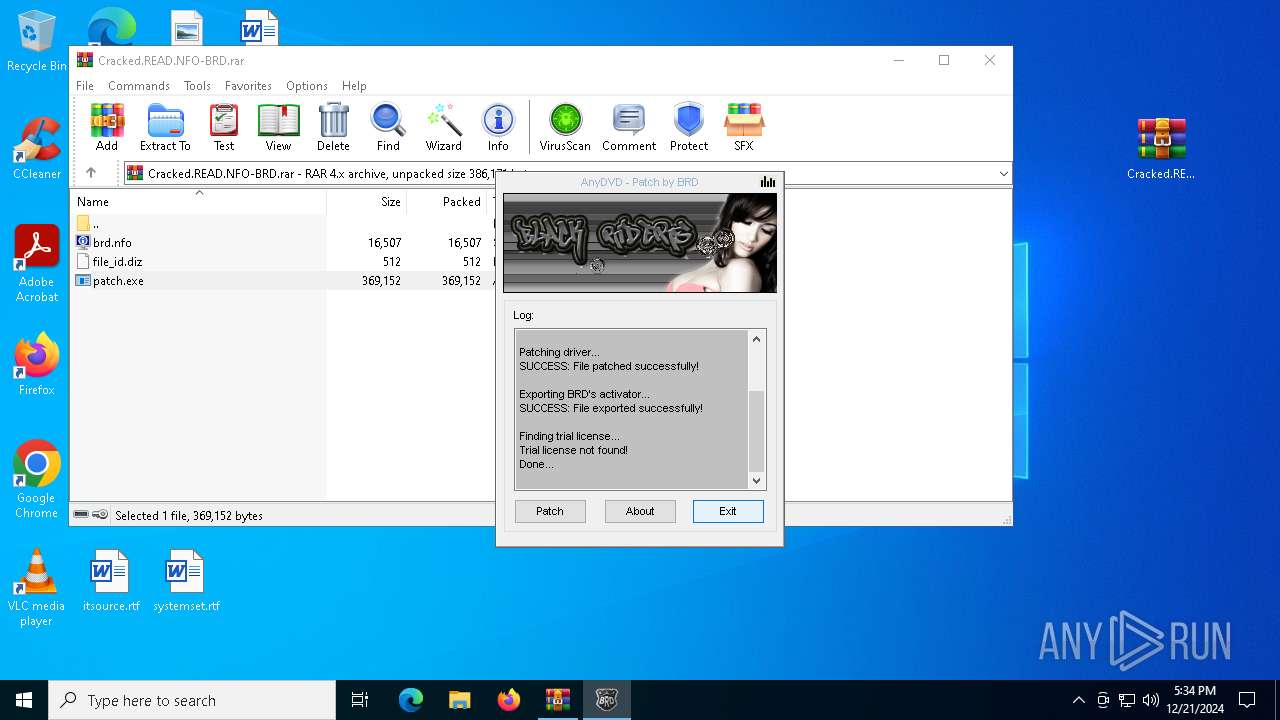
| File name: | AnyDVD_HD_8_1_4_0_2b.rar |
| Full analysis: | https://app.any.run/tasks/22ebcb5c-3166-4087-af73-9f77c1227eb6 |
| Verdict: | Malicious activity |
| Analysis date: | December 21, 2024, 17:33:55 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 42D768429FEC6F1D3264DB4BBEBCE9E1 |
| SHA1: | 36A2ABBEABE96F30AE67033DC7FFADA9A95892EA |
| SHA256: | 02BDA9AAEBFB0F992E5AB6029DDE24204BC2754981997E46C01175C72C96B770 |
| SSDEEP: | 98304:l7pvFumQJrhfX8o6bsLueb6vgEFTpuyvvBv91S90uTwAwEKaC4nxbp9lYupeNe/C:1g/skZ4IrvFO6nK73WYeW |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 7100)
Changes the autorun value in the registry
- nst68A1.tmp (PID: 6388)
- AnyDVDtray.exe (PID: 3052)
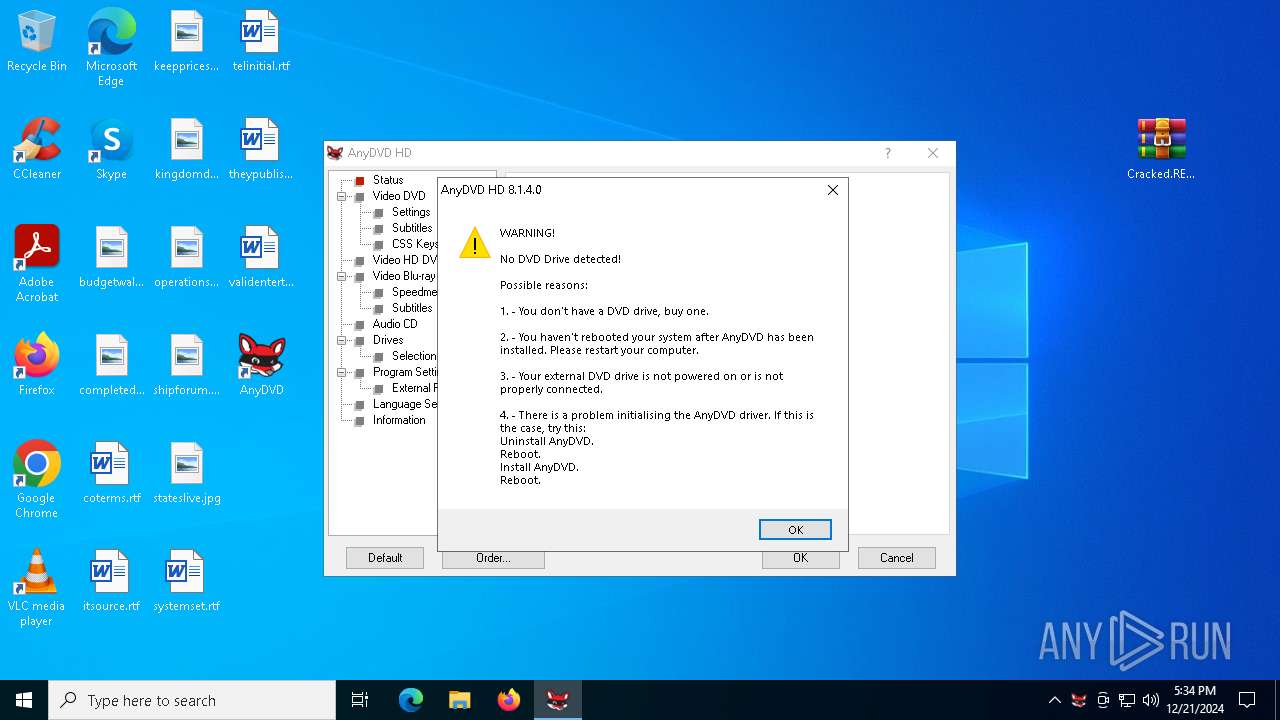
Executing a file with an untrusted certificate
- ADvdDiscHlp64.exe (PID: 6812)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7100)
- WinRAR.exe (PID: 1804)
- WinRAR.exe (PID: 6884)
Executable content was dropped or overwritten
- SetupAnyDVD8140.exe (PID: 3952)
- nst68A1.tmp (PID: 6388)
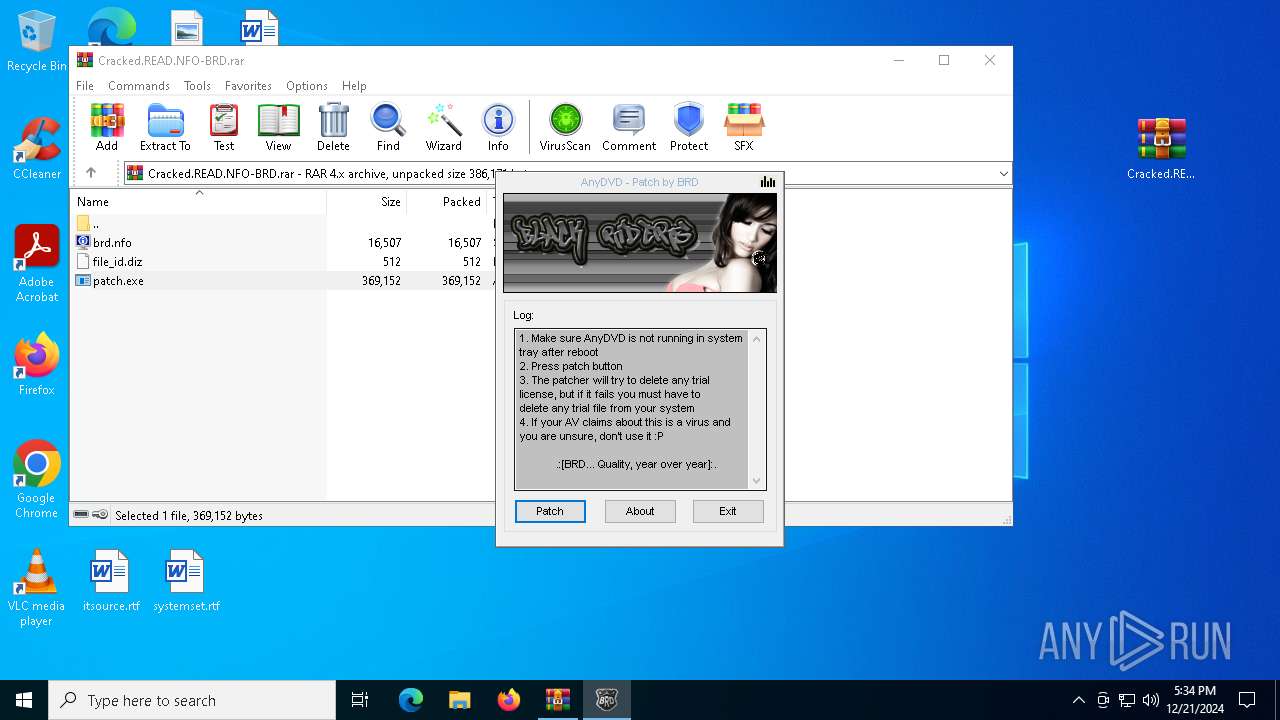
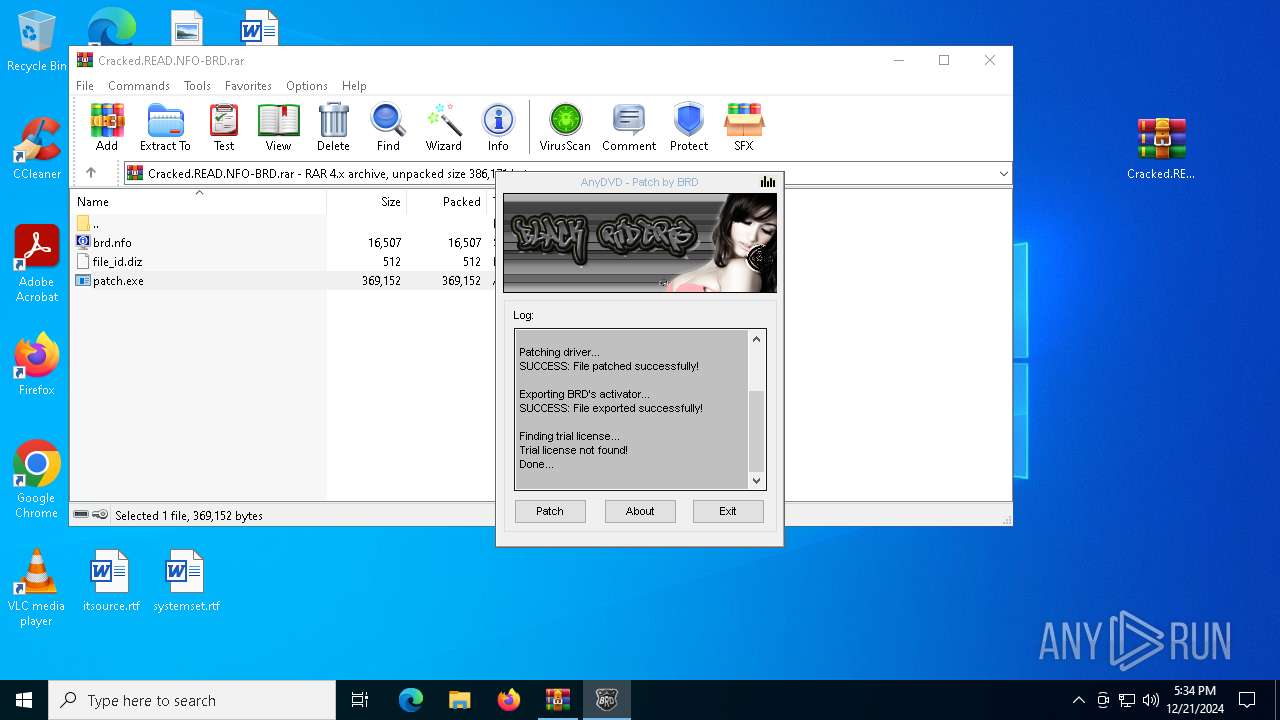
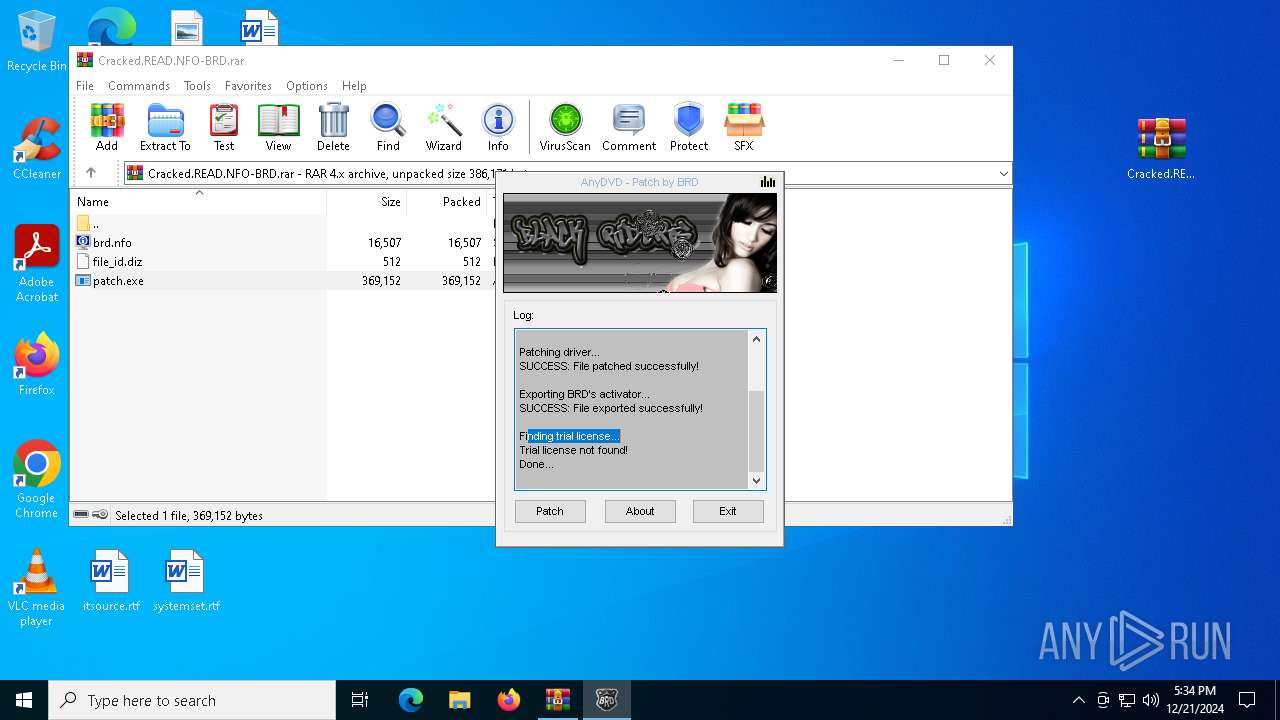
- patch.exe (PID: 6304)
- patch.exe (PID: 5528)
Starts itself from another location
- SetupAnyDVD8140.exe (PID: 3952)
Starts application with an unusual extension
- SetupAnyDVD8140.exe (PID: 3952)
Drops a system driver (possible attempt to evade defenses)
- nst68A1.tmp (PID: 6388)
Creates files in the driver directory
- nst68A1.tmp (PID: 6388)
Creates or modifies Windows services
- nst68A1.tmp (PID: 6388)
Creates a software uninstall entry
- nst68A1.tmp (PID: 6388)
Detected use of alternative data streams (AltDS)
- AnyDVDtray.exe (PID: 3052)
INFO
Create files in a temporary directory
- SetupAnyDVD8140.exe (PID: 3952)
- nst68A1.tmp (PID: 6388)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7100)
- WinRAR.exe (PID: 6884)
- WinRAR.exe (PID: 1804)
The process uses the downloaded file
- WinRAR.exe (PID: 7100)
- WinRAR.exe (PID: 6884)
- WinRAR.exe (PID: 1804)
Checks supported languages
- SetupAnyDVD8140.exe (PID: 3952)
- nst68A1.tmp (PID: 6388)
- AnyDVDtray.exe (PID: 3612)
- setacl.exe (PID: 6484)
- setacl.exe (PID: 3076)
- DevCon.exe (PID: 4444)
- DevCon.exe (PID: 3988)
- AnyDVDtray.exe (PID: 5236)
- AnyDVD.exe (PID: 4996)
- AnyDVD.exe (PID: 5920)
- AnyDVDtray.exe (PID: 5200)
- SetRegACL.exe (PID: 3208)
- AnyDVD.exe (PID: 6440)
- AnyDVDtray.exe (PID: 3052)
- ADvdDiscHlp64.exe (PID: 6812)
- ADvdDiscHlp64.exe (PID: 3076)
- patch.exe (PID: 6304)
- patch.exe (PID: 5528)
The sample compiled with german language support
- nst68A1.tmp (PID: 6388)
Reads the computer name
- nst68A1.tmp (PID: 6388)
- AnyDVDtray.exe (PID: 3612)
- AnyDVDtray.exe (PID: 5236)
- AnyDVDtray.exe (PID: 5200)
- patch.exe (PID: 6304)
- AnyDVDtray.exe (PID: 3052)
- ADvdDiscHlp64.exe (PID: 6812)
- patch.exe (PID: 5528)
Creates files in the program directory
- AnyDVDtray.exe (PID: 3612)
- nst68A1.tmp (PID: 6388)
- patch.exe (PID: 6304)
- patch.exe (PID: 5528)
The sample compiled with english language support
- nst68A1.tmp (PID: 6388)
Manual execution by a user
- AnyDVD.exe (PID: 5920)
- WinRAR.exe (PID: 6884)
- AnyDVD.exe (PID: 6440)
- WinRAR.exe (PID: 1804)
Reads the machine GUID from the registry
- AnyDVDtray.exe (PID: 3052)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 14107794 |
| UncompressedSize: | 14125832 |
| OperatingSystem: | Win32 |
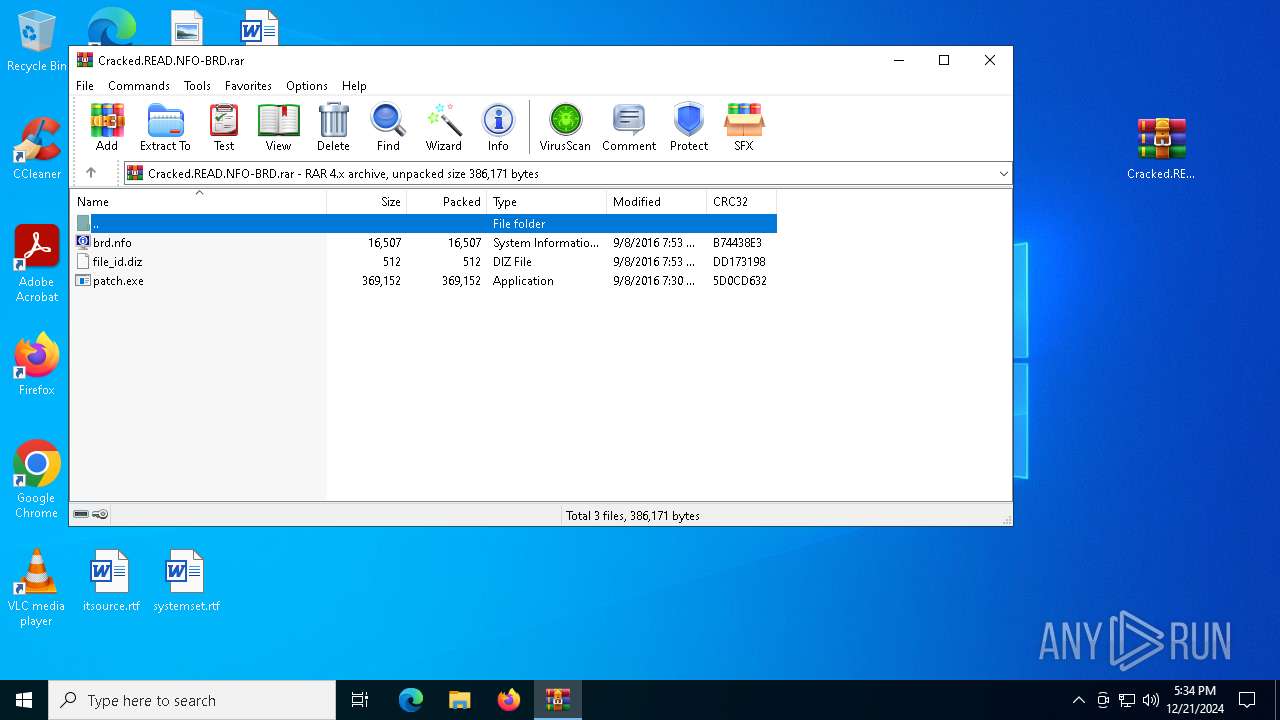
| ArchivedFileName: | SetupAnyDVD8140.exe |
Total processes
152
Monitored processes
31
Malicious processes
4
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1804 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Cracked.READ.NFO-BRD.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 3032 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | ADvdDiscHlp64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3052 | "C:\Program Files (x86)\RedFox\AnyDVD\AnyDVDtray.exe" | C:\Program Files (x86)\RedFox\AnyDVD\AnyDVDtray.exe | AnyDVD.exe | ||||||||||||
User: admin Company: RedFox Integrity Level: MEDIUM Description: AnyDVD Application Exit code: 3221225477 Version: 8.1.4.0 Modules
| |||||||||||||||
| 3076 | "C:\Users\admin\AppData\Local\Temp\nst6A56.tmp\SetACL.exe" "MACHINE\SOFTWARE\SlySoft\AnyDVD\Status" /registry /grant S-1-5-32-545 /full /sid /silent | C:\Users\admin\AppData\Local\Temp\nst6A56.tmp\setacl.exe | — | nst68A1.tmp | |||||||||||
User: admin Company: Helge Klein Integrity Level: HIGH Description: SetACL Exit code: 0 Version: 0, 9, 0, 4 Modules
| |||||||||||||||
| 3076 | ADvdDiscHlp64.exe /u | C:\Program Files (x86)\RedFox\AnyDVD\ADvdDiscHlp64.exe | — | AnyDVDtray.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: AnyDVD 64bit helper Exit code: 0 Version: 3, 0, 0, 1 Modules
| |||||||||||||||
| 3188 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | DevCon.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3208 | "C:\Program Files (x86)\RedFox\AnyDVD\SetRegACL.exe" Software\Microsoft\Windows\CurrentVersion\Explorer\DriveIcons 64 | C:\Program Files (x86)\RedFox\AnyDVD\SetRegACL.exe | — | nst68A1.tmp | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3612 | "C:\Users\admin\AppData\Local\Temp\nst6A56.tmp\AnyDVDTray.exe" -c | C:\Users\admin\AppData\Local\Temp\nst6A56.tmp\AnyDVDtray.exe | — | nst68A1.tmp | |||||||||||
User: admin Company: RedFox Integrity Level: HIGH Description: AnyDVD Application Exit code: 10 Version: 8.1.4.0 Modules
| |||||||||||||||
| 3732 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1804.30957\patch.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1804.30957\patch.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 3952 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa7100.25794\SetupAnyDVD8140.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa7100.25794\SetupAnyDVD8140.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
6 669
Read events
6 301
Write events
365
Delete events
3
Modification events
| (PID) Process: | (7100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\AnyDVD_HD_8_1_4_0_2b.rar | |||
| (PID) Process: | (7100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6388) nst68A1.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\SlySoft\AnyDVD |
| Operation: | write | Name: | Affiliate |
Value: 0 | |||
| (PID) Process: | (6388) nst68A1.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\SlySoft\AnyDVD |
| Operation: | write | Name: | ADvdDiscHlp |
Value: C:\Program Files (x86)\RedFox\AnyDVD\ADvdDiscHlp.dll | |||
Executable files
36
Suspicious files
86
Text files
27
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6388 | nst68A1.tmp | C:\Users\admin\AppData\Local\Temp\nst6A56.tmp\InstallHelp.dll | executable | |
MD5:83B07F94937A933CC1CD4AA07210BAB0 | SHA256:BC68FEF64641E6C17430A956664464ECD0E58439789B685051F41E7FE4D31098 | |||
| 7100 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7100.25794\Cracked.READ.NFO-BRD.rar | compressed | |
MD5:91EEEEAFD9B03B8F245574EB6B647799 | SHA256:A37A969111EA939C20F4957B966B088598A64E81D246FA1CFB3007370DDDF922 | |||
| 6388 | nst68A1.tmp | C:\Users\admin\AppData\Local\Temp\nst6A56.tmp\Language\AnyDVDcs.lng | binary | |
MD5:D63B3335739ECC6DA9B2DD0C1D995E39 | SHA256:0B48612615CAE09EF56559C9584476B8AF88B2AD500A937BA7756F55E80FB7AE | |||
| 6388 | nst68A1.tmp | C:\Users\admin\AppData\Local\Temp\nst6A56.tmp\Language\AnyDVDar.lng | binary | |
MD5:3CE96C4952E3596984ABB7CB73E4247F | SHA256:E2BBA6938976CFA071B20B626D017AA61C0EDB064005D51BC1993AC7BAD19157 | |||
| 6388 | nst68A1.tmp | C:\Users\admin\AppData\Local\Temp\nst6A56.tmp\Language\AnyDVDca.lng | binary | |
MD5:EC2215A5307B916046CB802D46F9C2AC | SHA256:01E7DAC6DC3E1DD72E21AB799AAC0B08F1CCD3846F2E55B27BEB6D03AAEFDF0E | |||
| 6388 | nst68A1.tmp | C:\Users\admin\AppData\Local\Temp\nst6A56.tmp\Language\AnyDVDes.lng | binary | |
MD5:DF13149BA8B5429171BD9A0D2DB44663 | SHA256:A5C67F171A51EB1469F2D85F5C4E8A2D315CFA3B5ECFF59D3E803DED91ED05FA | |||
| 6388 | nst68A1.tmp | C:\Users\admin\AppData\Local\Temp\nst6A56.tmp\Language\AnyDVDfr.lng | binary | |
MD5:4643212F16B78807E66A806FB4C1ABC0 | SHA256:38C5B9563D15EABE9A7BC59BBB2BD3B6BB981F978AA295DB6E893C0DDF48438D | |||
| 6388 | nst68A1.tmp | C:\Users\admin\AppData\Local\Temp\nst6A56.tmp\Language\AnyDVDhe.lng | binary | |
MD5:3D57821D1C2EADB86D69DAD046DABAD2 | SHA256:36F13A9612ADE2C4DD7FE1607F01A4F09D346760319F9C00C9485B1C95029114 | |||
| 6388 | nst68A1.tmp | C:\Users\admin\AppData\Local\Temp\nst6A56.tmp\Language\AnyDVDde.lng | binary | |
MD5:D9B9B58A3457D9DAC2FD9EC13CD241C6 | SHA256:5506A32096DBCEFA362E816D887AC704CBCBE81E1C29D719A3C4A3F06B7437A5 | |||
| 6388 | nst68A1.tmp | C:\Users\admin\AppData\Local\Temp\nst6A56.tmp\Language\AnyDVDen.lng | binary | |
MD5:437F14F068ADED34770FE6495C939484 | SHA256:A719B16D3D562D3E05883298730795192D690F76C9B5C2FCE6461696A49CD747 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
34
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6612 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6904 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4712 | MoUsoCoreWorker.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 104.126.37.123:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1176 | svchost.exe | 40.126.31.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |