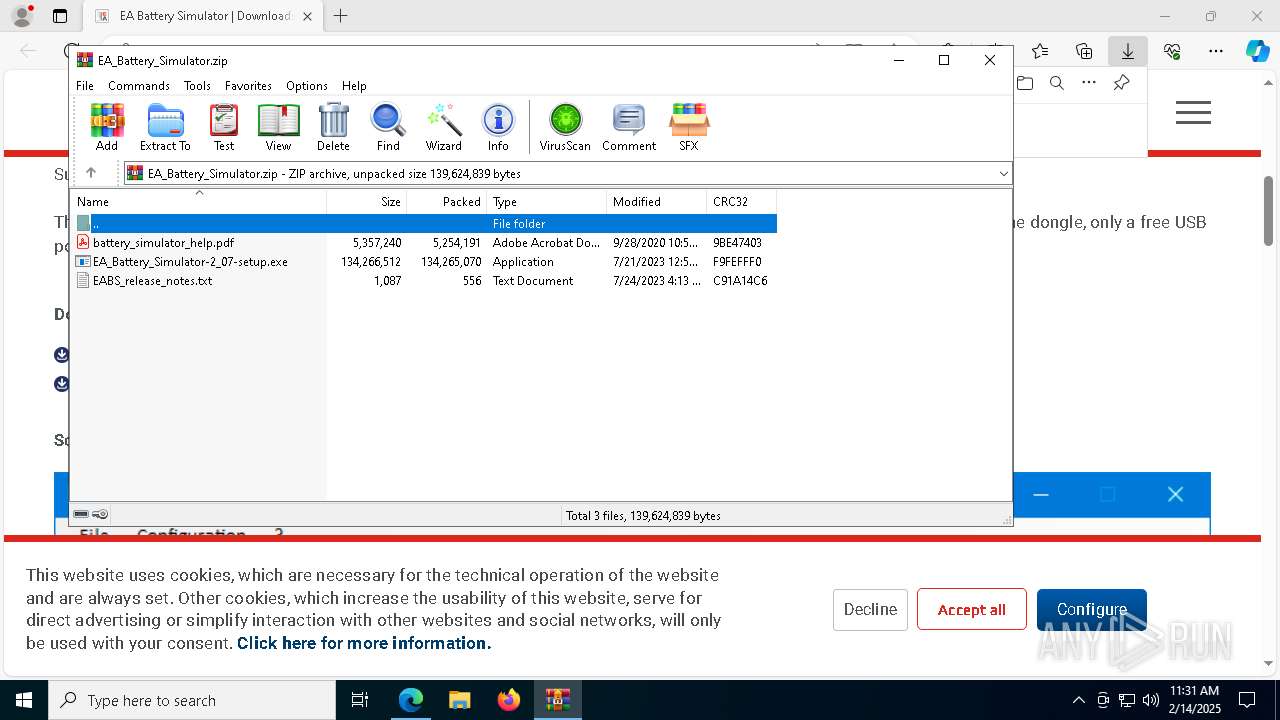
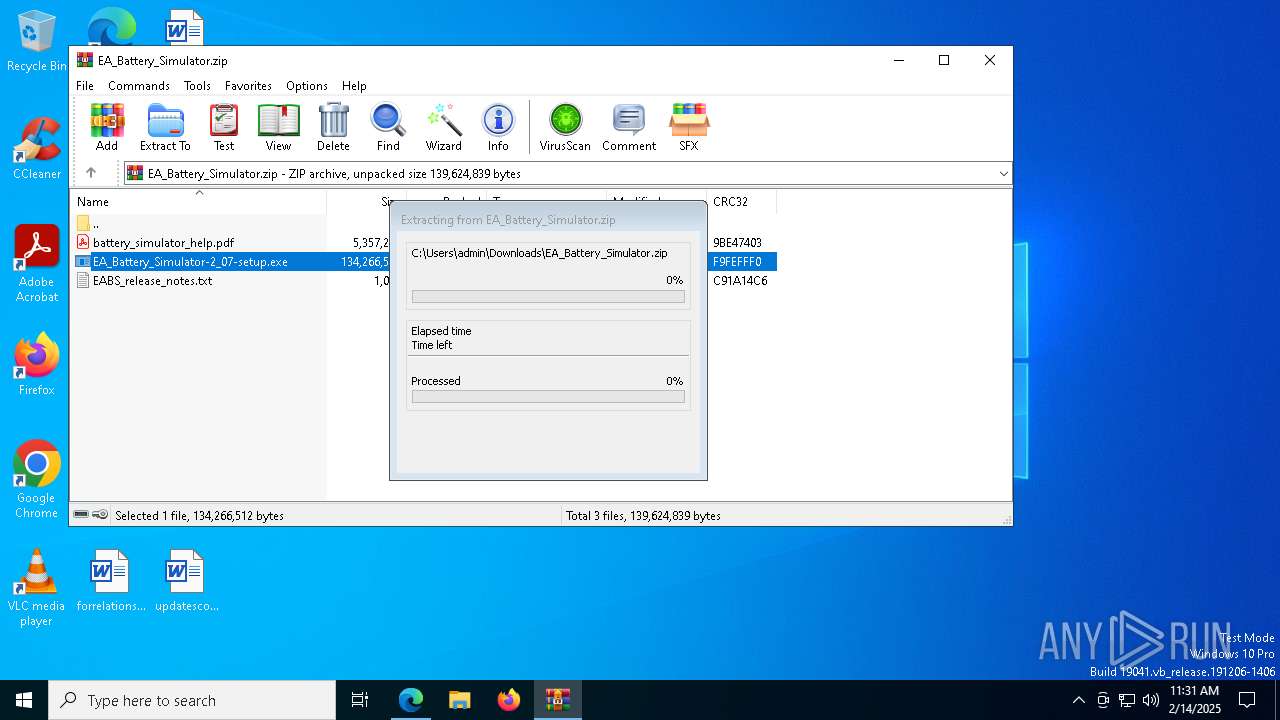
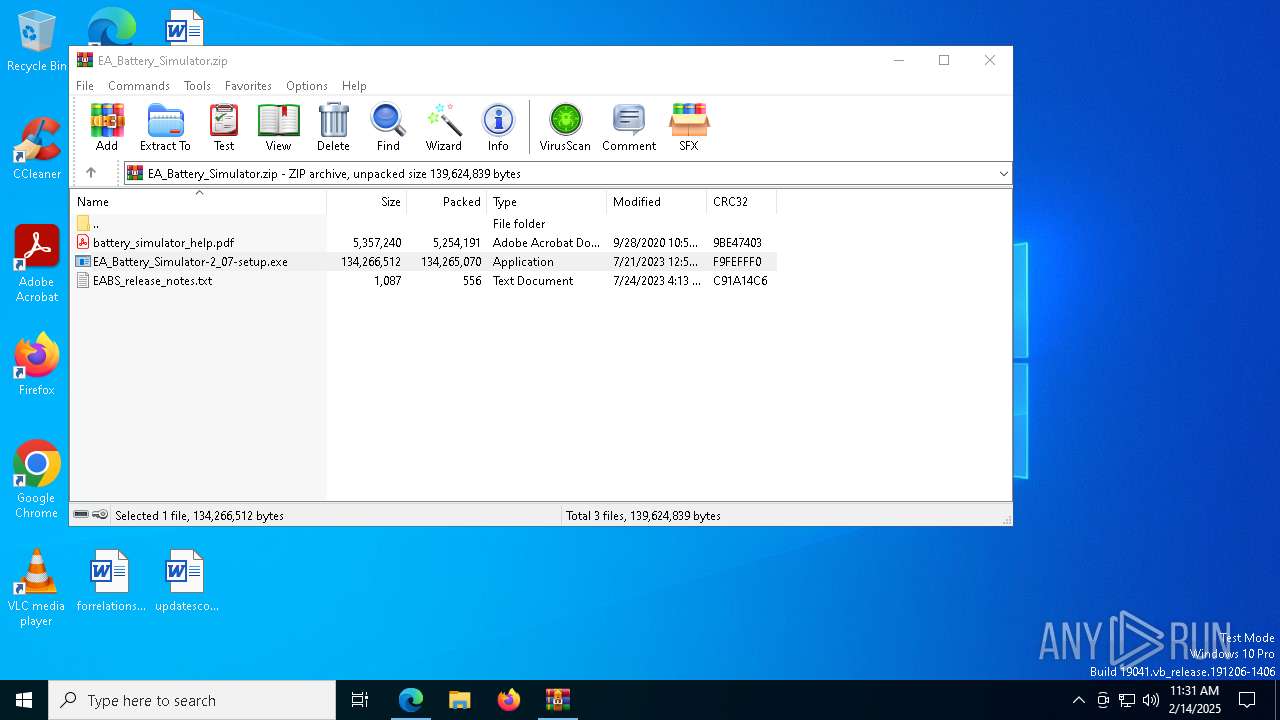
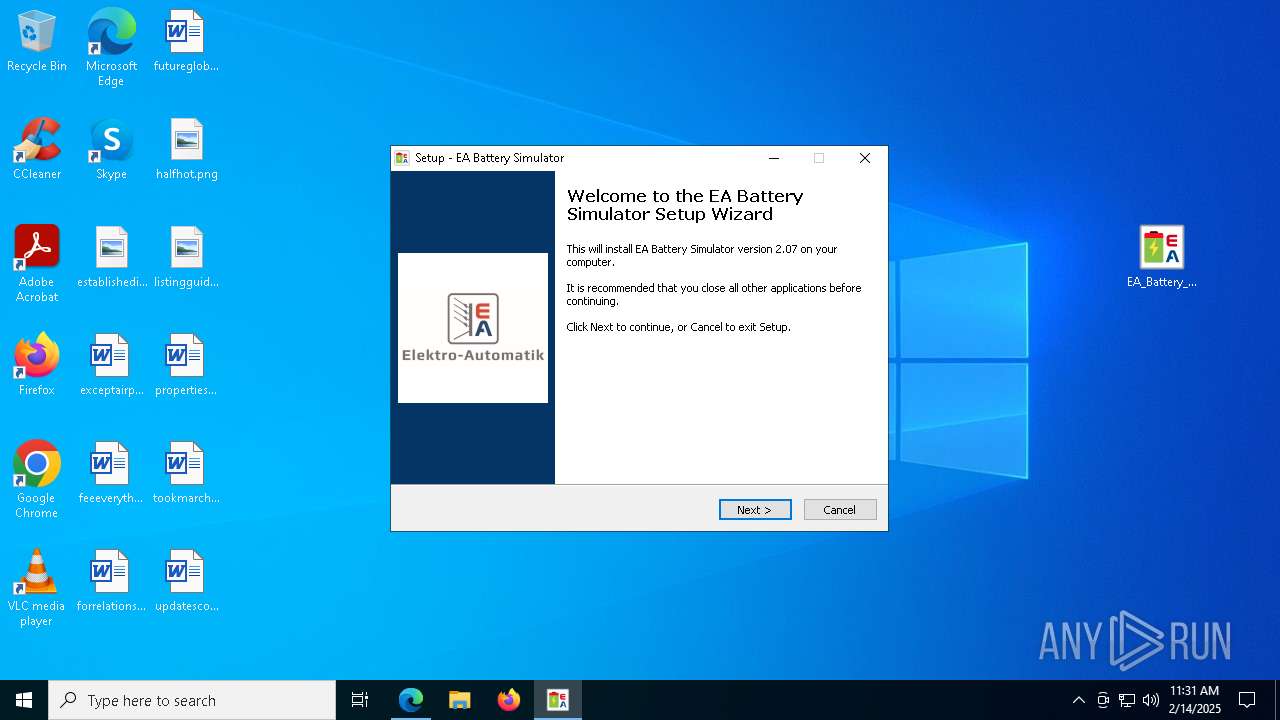
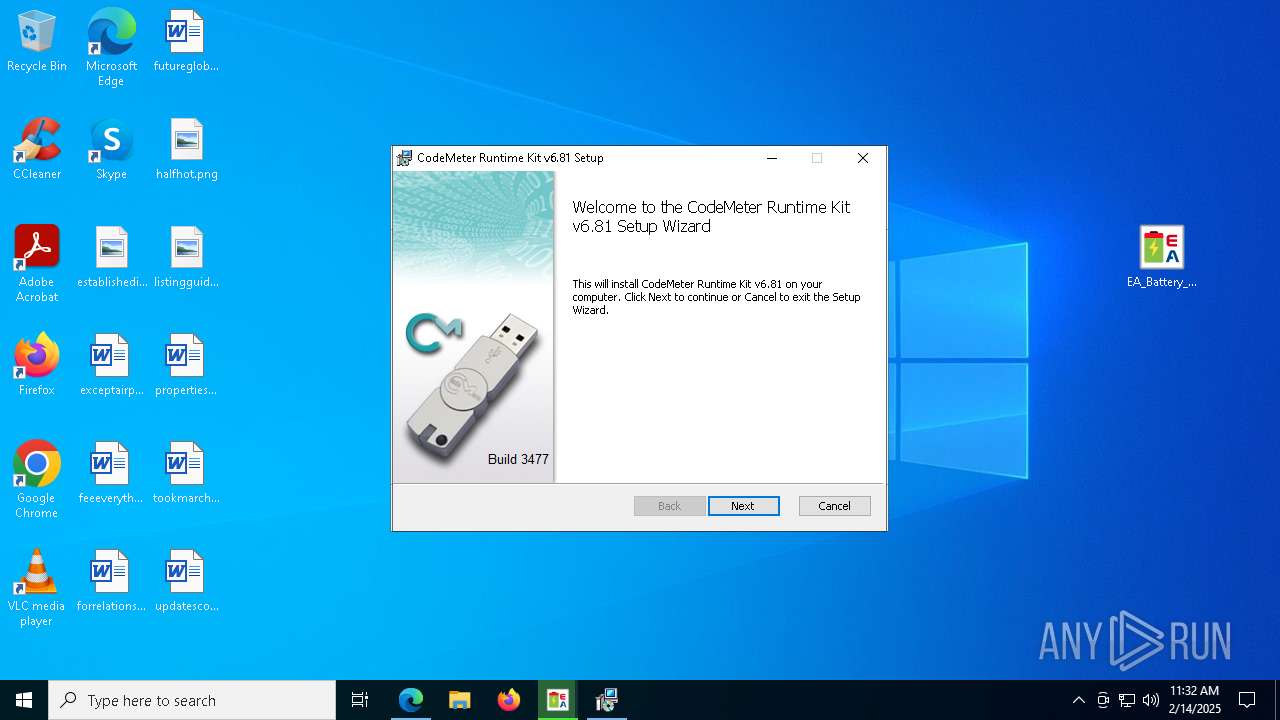
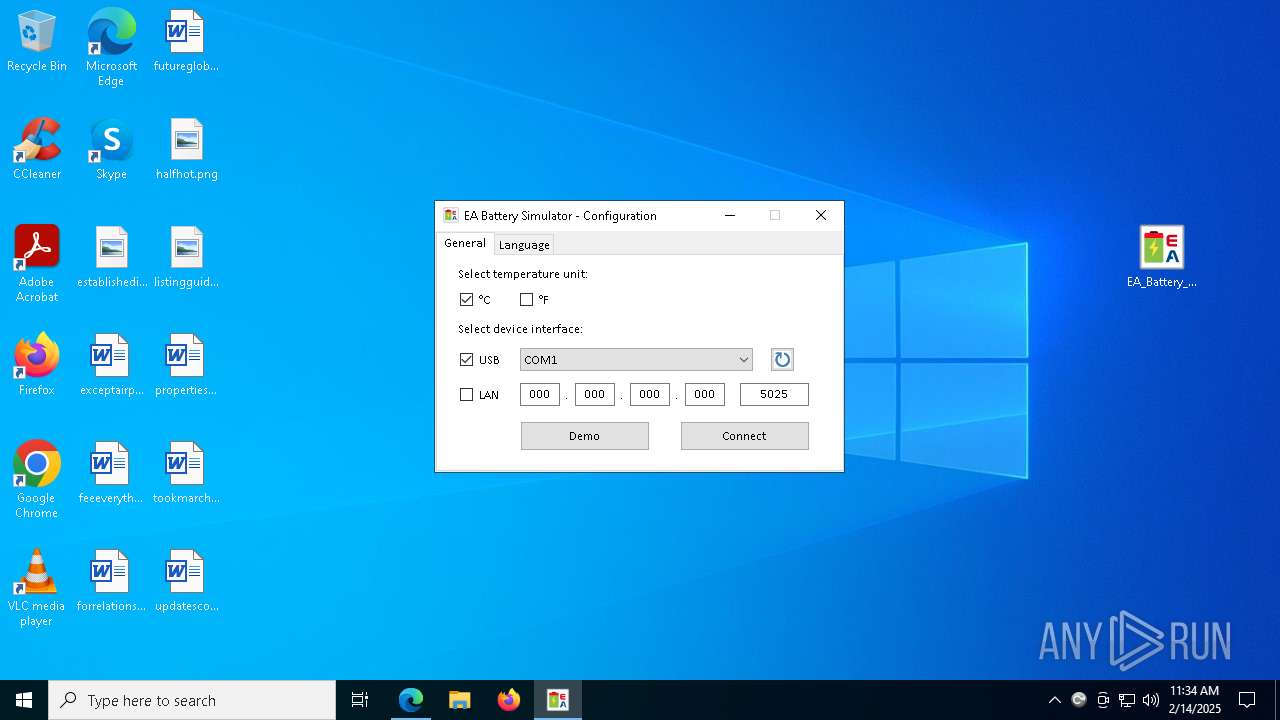
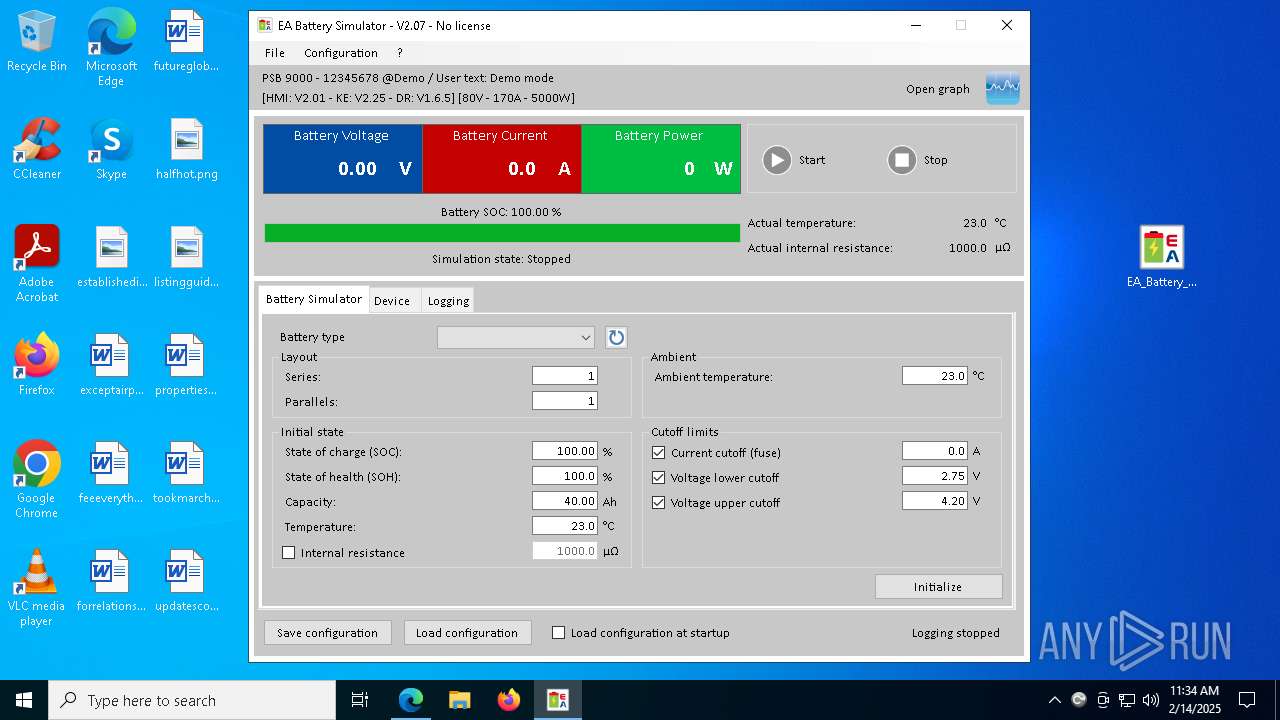
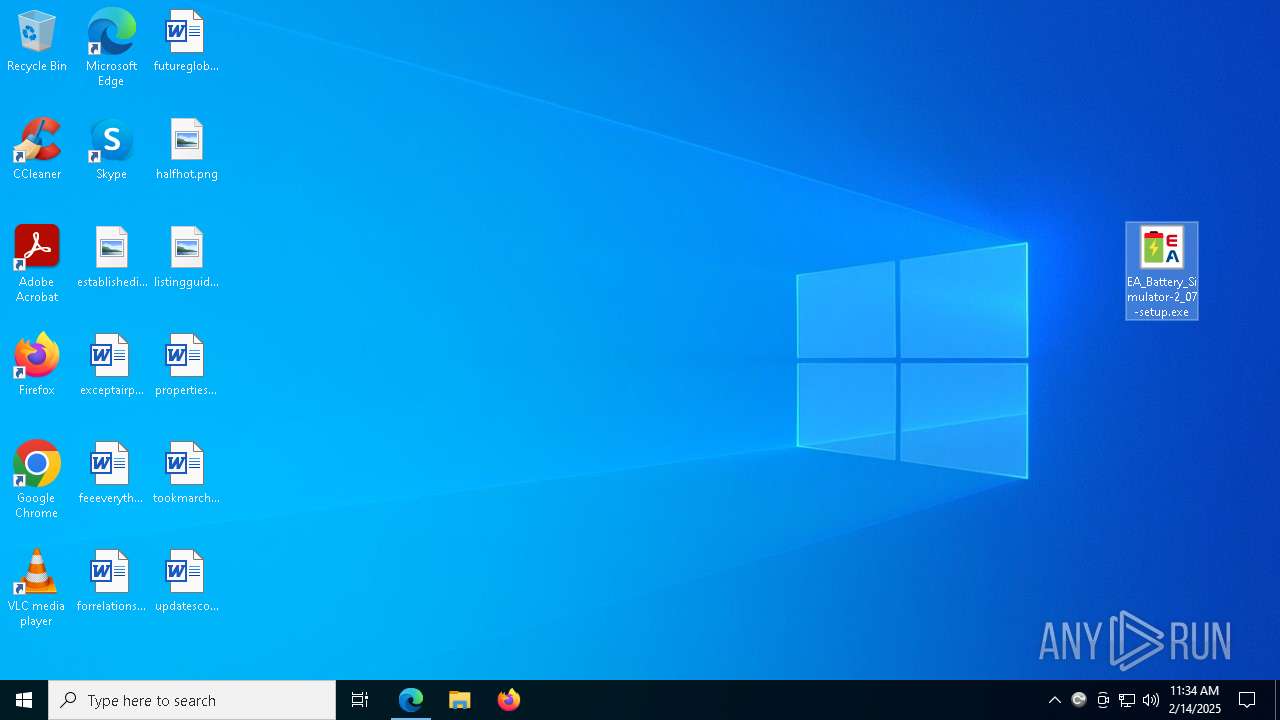
| URL: | https://elektroautomatik.com/shop/en/service/downloads/ea-battery-simulator/ |
| Full analysis: | https://app.any.run/tasks/e4bfe6f4-49bb-452e-850a-cae3a816d8f5 |
| Verdict: | Malicious activity |
| Analysis date: | February 14, 2025, 11:30:19 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 55A574BF71ACD2FFF3032A4D055BDBC4 |
| SHA1: | 5513E3B4471BCD420BEFE1D05E4369068BE80FE6 |
| SHA256: | 02B3F8621C0A6F5AC567A17789AE237BC73F1B9BEA0C33EECE9E6D1EF8CE84F9 |
| SSDEEP: | 3:N8eRPQRT4MOtKObLKzZK46KpwJ/4MK:2kQqMOvKz0apwJ/4MK |
MALICIOUS
Starts NET.EXE for service management
- net.exe (PID: 3736)
- msiexec.exe (PID: 7284)
- net.exe (PID: 7220)
SUSPICIOUS
Executable content was dropped or overwritten
- EA_Battery_Simulator-2_07-setup.exe (PID: 7304)
- EA_Battery_Simulator-2_07-setup.exe (PID: 2076)
- EA_Battery_Simulator-2_07-setup.tmp (PID: 7520)
- CodeMeterRuntime.exe (PID: 7784)
- ea_device_driver_v2_0_2_7.exe (PID: 4012)
- ea_device_driver_v2_0_2_7.exe (PID: 2356)
- ea_device_driver_v2_0_2_7.tmp (PID: 6532)
- UserFiles.exe (PID: 3900)
- UserFiles.exe (PID: 7972)
- dpinst.exe (PID: 5988)
- UserFiles.tmp (PID: 880)
Reads security settings of Internet Explorer
- EA_Battery_Simulator-2_07-setup.tmp (PID: 7356)
- msiexec.exe (PID: 7188)
- msiexec.exe (PID: 7284)
- ea_device_driver_v2_0_2_7.tmp (PID: 1016)
- UserFiles.tmp (PID: 8040)
Reads the Windows owner or organization settings
- EA_Battery_Simulator-2_07-setup.tmp (PID: 7520)
- msiexec.exe (PID: 5964)
- ea_device_driver_v2_0_2_7.tmp (PID: 6532)
- UserFiles.tmp (PID: 880)
Process drops legitimate windows executable
- EA_Battery_Simulator-2_07-setup.tmp (PID: 7520)
- ea_device_driver_v2_0_2_7.tmp (PID: 6532)
- dpinst.exe (PID: 5988)
Likely accesses (executes) a file from the Public directory
- CodeMeterRuntime.exe (PID: 7784)
- ea_device_driver_v2_0_2_7.exe (PID: 4012)
- ea_device_driver_v2_0_2_7.tmp (PID: 1016)
- ea_device_driver_v2_0_2_7.exe (PID: 2356)
- ea_device_driver_v2_0_2_7.tmp (PID: 6532)
There is functionality for taking screenshot (YARA)
- CodeMeterRuntime.exe (PID: 7784)
Executes as Windows Service
- VSSVC.exe (PID: 1228)
- CmWebAdmin.exe (PID: 7900)
- CodeMeter.exe (PID: 7608)
Checks Windows Trust Settings
- msiexec.exe (PID: 5964)
- drvinst.exe (PID: 8176)
Disables SEHOP
- msiexec.exe (PID: 5964)
Creates/Modifies COM task schedule object
- msiexec.exe (PID: 8056)
- msiexec.exe (PID: 6520)
- msiexec.exe (PID: 8052)
Creates a software uninstall entry
- dpinst.exe (PID: 5988)
INFO
Application launched itself
- msedge.exe (PID: 6340)
- msiexec.exe (PID: 5964)
Checks supported languages
- identity_helper.exe (PID: 5880)
- EA_Battery_Simulator-2_07-setup.exe (PID: 7304)
- EA_Battery_Simulator-2_07-setup.tmp (PID: 7356)
- EA_Battery_Simulator-2_07-setup.exe (PID: 2076)
- EA_Battery_Simulator-2_07-setup.tmp (PID: 7520)
- CodeMeterRuntime.exe (PID: 7784)
- msiexec.exe (PID: 5964)
- MSIE50A.tmp (PID: 1292)
- MSIE54A.tmp (PID: 5392)
- msiexec.exe (PID: 7284)
- msiexec.exe (PID: 7188)
- msiexec.exe (PID: 7928)
- msiexec.exe (PID: 6388)
- CmWebAdmin.exe (PID: 7900)
- CodeMeter.exe (PID: 7608)
- CodeMeterCC.exe (PID: 7464)
- msiexec.exe (PID: 5536)
- ea_device_driver_v2_0_2_7.exe (PID: 4012)
- ea_device_driver_v2_0_2_7.tmp (PID: 1016)
- ea_device_driver_v2_0_2_7.exe (PID: 2356)
- ea_device_driver_v2_0_2_7.tmp (PID: 6532)
- dpinst.exe (PID: 7836)
- dpinst.exe (PID: 7796)
- dpinst.exe (PID: 6512)
- dpinst.exe (PID: 6184)
- dpinst.exe (PID: 1888)
- dpinst.exe (PID: 8016)
- dpinst.exe (PID: 4520)
- dpinst.exe (PID: 5208)
- dpinst.exe (PID: 7000)
- dpinst.exe (PID: 6740)
- dpinst.exe (PID: 3828)
- dpinst.exe (PID: 6760)
- dpinst.exe (PID: 1796)
- dpinst.exe (PID: 6976)
- dpinst.exe (PID: 6888)
- dpinst.exe (PID: 68)
- dpinst.exe (PID: 5988)
- drvinst.exe (PID: 8176)
- dpinst.exe (PID: 2956)
- UserFiles.tmp (PID: 880)
- UserFiles.exe (PID: 3900)
- UserFiles.tmp (PID: 8040)
- UserFiles.exe (PID: 7972)
- EA Battery Simulator.exe (PID: 7244)
- dpinst.exe (PID: 6096)
Reads Environment values
- identity_helper.exe (PID: 5880)
- CodeMeter.exe (PID: 7608)
Reads the computer name
- identity_helper.exe (PID: 5880)
- EA_Battery_Simulator-2_07-setup.tmp (PID: 7356)
- EA_Battery_Simulator-2_07-setup.tmp (PID: 7520)
- msiexec.exe (PID: 5964)
- msiexec.exe (PID: 7188)
- msiexec.exe (PID: 7284)
- msiexec.exe (PID: 7928)
- msiexec.exe (PID: 6388)
- CmWebAdmin.exe (PID: 7900)
- CodeMeter.exe (PID: 7608)
- CodeMeterCC.exe (PID: 7464)
- ea_device_driver_v2_0_2_7.tmp (PID: 6532)
- msiexec.exe (PID: 5536)
- ea_device_driver_v2_0_2_7.tmp (PID: 1016)
- dpinst.exe (PID: 5988)
- drvinst.exe (PID: 8176)
- UserFiles.tmp (PID: 8040)
- UserFiles.tmp (PID: 880)
- EA Battery Simulator.exe (PID: 7244)
Reads Microsoft Office registry keys
- msedge.exe (PID: 6340)
Manual execution by a user
- EA_Battery_Simulator-2_07-setup.exe (PID: 7304)
- CodeMeterCC.exe (PID: 7464)
Create files in a temporary directory
- EA_Battery_Simulator-2_07-setup.exe (PID: 7304)
- EA_Battery_Simulator-2_07-setup.exe (PID: 2076)
- EA_Battery_Simulator-2_07-setup.tmp (PID: 7520)
- CodeMeterRuntime.exe (PID: 7784)
- msiexec.exe (PID: 5040)
- ea_device_driver_v2_0_2_7.tmp (PID: 6532)
- dpinst.exe (PID: 5988)
- UserFiles.exe (PID: 7972)
Process checks computer location settings
- EA_Battery_Simulator-2_07-setup.tmp (PID: 7356)
- msiexec.exe (PID: 7284)
- ea_device_driver_v2_0_2_7.tmp (PID: 1016)
- UserFiles.tmp (PID: 8040)
Detects InnoSetup installer (YARA)
- EA_Battery_Simulator-2_07-setup.exe (PID: 7304)
- EA_Battery_Simulator-2_07-setup.tmp (PID: 7356)
- EA_Battery_Simulator-2_07-setup.tmp (PID: 7520)
- EA_Battery_Simulator-2_07-setup.exe (PID: 2076)
Compiled with Borland Delphi (YARA)
- EA_Battery_Simulator-2_07-setup.tmp (PID: 7520)
- EA_Battery_Simulator-2_07-setup.tmp (PID: 7356)
Creates files in the program directory
- EA_Battery_Simulator-2_07-setup.tmp (PID: 7520)
The sample compiled with english language support
- CodeMeterRuntime.exe (PID: 7784)
- EA_Battery_Simulator-2_07-setup.tmp (PID: 7520)
- msedge.exe (PID: 7240)
- msiexec.exe (PID: 5964)
- msiexec.exe (PID: 5040)
The sample compiled with french language support
- CodeMeterRuntime.exe (PID: 7784)
- msiexec.exe (PID: 5964)
The sample compiled with german language support
- CodeMeterRuntime.exe (PID: 7784)
- msiexec.exe (PID: 5964)
The sample compiled with Italian language support
- CodeMeterRuntime.exe (PID: 7784)
- msiexec.exe (PID: 5964)
The sample compiled with japanese language support
- CodeMeterRuntime.exe (PID: 7784)
- msiexec.exe (PID: 5964)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 5040)
- rundll32.exe (PID: 4336)
Creates files or folders in the user directory
- msiexec.exe (PID: 5040)
- ea_device_driver_v2_0_2_7.tmp (PID: 6532)
The sample compiled with chinese language support
- CodeMeterRuntime.exe (PID: 7784)
- msiexec.exe (PID: 5964)
The sample compiled with russian language support
- CodeMeterRuntime.exe (PID: 7784)
- msiexec.exe (PID: 5964)
Checks proxy server information
- msiexec.exe (PID: 5040)
- msiexec.exe (PID: 7188)
Reads the software policy settings
- msiexec.exe (PID: 5040)
- msiexec.exe (PID: 5964)
- dpinst.exe (PID: 7836)
- dpinst.exe (PID: 7796)
- dpinst.exe (PID: 6512)
- dpinst.exe (PID: 6184)
- dpinst.exe (PID: 7000)
- dpinst.exe (PID: 1888)
- dpinst.exe (PID: 8016)
- dpinst.exe (PID: 4520)
- dpinst.exe (PID: 5208)
- dpinst.exe (PID: 6888)
- dpinst.exe (PID: 6096)
- dpinst.exe (PID: 6740)
- dpinst.exe (PID: 6760)
- dpinst.exe (PID: 3828)
- dpinst.exe (PID: 1796)
- dpinst.exe (PID: 6976)
- dpinst.exe (PID: 2956)
- dpinst.exe (PID: 68)
- drvinst.exe (PID: 8176)
- rundll32.exe (PID: 4336)
- dpinst.exe (PID: 5988)
Executable content was dropped or overwritten
- msedge.exe (PID: 7240)
- msiexec.exe (PID: 5964)
- msiexec.exe (PID: 5040)
Manages system restore points
- SrTasks.exe (PID: 3076)
Reads the machine GUID from the registry
- msiexec.exe (PID: 5964)
- CmWebAdmin.exe (PID: 7900)
- CodeMeter.exe (PID: 7608)
- dpinst.exe (PID: 7836)
- dpinst.exe (PID: 7796)
- dpinst.exe (PID: 7000)
- dpinst.exe (PID: 1888)
- dpinst.exe (PID: 8016)
- dpinst.exe (PID: 4520)
- dpinst.exe (PID: 5208)
- dpinst.exe (PID: 6512)
- dpinst.exe (PID: 6184)
- dpinst.exe (PID: 6888)
- dpinst.exe (PID: 6096)
- dpinst.exe (PID: 3828)
- dpinst.exe (PID: 6740)
- dpinst.exe (PID: 6760)
- dpinst.exe (PID: 1796)
- dpinst.exe (PID: 6976)
- dpinst.exe (PID: 2956)
- dpinst.exe (PID: 68)
- drvinst.exe (PID: 8176)
- dpinst.exe (PID: 5988)
- EA Battery Simulator.exe (PID: 7244)
Starts application with an unusual extension
- msiexec.exe (PID: 5964)
Creates a software uninstall entry
- msiexec.exe (PID: 5964)
- EA_Battery_Simulator-2_07-setup.tmp (PID: 7520)
Reads product name
- CodeMeter.exe (PID: 7608)
The sample compiled with arabic language support
- ea_device_driver_v2_0_2_7.tmp (PID: 6532)
- dpinst.exe (PID: 5988)
Adds/modifies Windows certificates
- drvinst.exe (PID: 8176)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
260
Monitored processes
119
Malicious processes
4
Suspicious processes
7
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 68 | "C:\Users\admin\AppData\Local\ea_driver\dpinst.exe" /sw /u V2026\CDC_ACM_WIN.inf | C:\Users\admin\AppData\Local\ea_driver\dpinst.exe | — | ea_device_driver_v2_0_2_7.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Driver Package Installer Exit code: 2147483648 Version: 2.1 Modules
| |||||||||||||||
| 440 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4644 --field-trial-handle=2204,i,17404709538129653207,17944768680420505076,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 444 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6304 --field-trial-handle=2204,i,17404709538129653207,17944768680420505076,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 644 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6268 --field-trial-handle=2204,i,17404709538129653207,17944768680420505076,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 776 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5508 --field-trial-handle=2204,i,17404709538129653207,17944768680420505076,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 880 | "C:\Users\admin\AppData\Local\Temp\is-GLJBF.tmp\UserFiles.tmp" /SL5="$60232,9191135,58368,C:\Program Files (x86)\EABatterySimulator\UserFiles.exe" /SPAWNWND=$40234 /NOTIFYWND=$40222 /VERYSILENT /SUPPRESSMSGBOXES | C:\Users\admin\AppData\Local\Temp\is-GLJBF.tmp\UserFiles.tmp | UserFiles.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 1016 | "C:\Users\admin\AppData\Local\Temp\is-ON83V.tmp\ea_device_driver_v2_0_2_7.tmp" /SL5="$30222,5493016,58368,C:\Users\Public\Documents\EABatterySimulator\dot_net_driver\ea_device_driver_v2_0_2_7.exe" /VERYSILENT /SUPPRESSMSGBOXES | C:\Users\admin\AppData\Local\Temp\is-ON83V.tmp\ea_device_driver_v2_0_2_7.tmp | — | ea_device_driver_v2_0_2_7.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 1020 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=asset_store.mojom.AssetStoreService --lang=en-US --service-sandbox-type=asset_store_service --no-appcompat-clear --mojo-platform-channel-handle=6220 --field-trial-handle=2204,i,17404709538129653207,17944768680420505076,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1228 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1292 | "C:\WINDOWS\Installer\MSIE50A.tmp" /t | C:\Windows\Installer\MSIE50A.tmp | — | msiexec.exe | |||||||||||
User: admin Company: WIBU-SYSTEMS AG Integrity Level: HIGH Description: CleanUp Exit code: 0 Version: Version 6.81 of 2019-Apr-02 (Build 3477) Modules
| |||||||||||||||
Total events
113 761
Read events
112 017
Write events
1 662
Delete events
82
Modification events
| (PID) Process: | (6340) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6340) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6340) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6340) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6340) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 26B994C8AE8C2F00 | |||
| (PID) Process: | (6340) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: AF16A4C8AE8C2F00 | |||
| (PID) Process: | (6340) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\393900 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {CAB31C6A-BC1A-4BBD-8DBA-593CDDD2C2FF} | |||
| (PID) Process: | (6340) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\393900 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {3EAA84CE-D351-49C2-BC57-38307F10DC09} | |||
| (PID) Process: | (6340) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\393900 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {CFA96C19-624E-42F2-8E0D-4BCA9A6FAA0C} | |||
| (PID) Process: | (6340) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\393900 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {3A8E9582-CEB2-420E-834F-4866745A8808} | |||
Executable files
371
Suspicious files
748
Text files
2 251
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6340 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF134d87.TMP | — | |
MD5:— | SHA256:— | |||
| 6340 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6340 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF134d96.TMP | — | |
MD5:— | SHA256:— | |||
| 6340 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6340 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF134d96.TMP | — | |
MD5:— | SHA256:— | |||
| 6340 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6340 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF134db6.TMP | — | |
MD5:— | SHA256:— | |||
| 6340 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6340 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF134db6.TMP | — | |
MD5:— | SHA256:— | |||
| 6340 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
58
TCP/UDP connections
98
DNS requests
90
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.51:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2728 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5728 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/68591036-2289-4858-9f7f-9149e89c8a08?P1=1739801495&P2=404&P3=2&P4=SONmYbuD0J5jE3h5b2TdhZ5PujwPPBkNR8kk7jCvmHx8dKL8TwDcX23OhhOs1UJ9q6yGcO0mnoE%2bqA2%2f9dNpRw%3d%3d | unknown | — | — | whitelisted |
7872 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5728 | svchost.exe | HEAD | 200 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/68591036-2289-4858-9f7f-9149e89c8a08?P1=1739801495&P2=404&P3=2&P4=SONmYbuD0J5jE3h5b2TdhZ5PujwPPBkNR8kk7jCvmHx8dKL8TwDcX23OhhOs1UJ9q6yGcO0mnoE%2bqA2%2f9dNpRw%3d%3d | unknown | — | — | whitelisted |
7872 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5728 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/68591036-2289-4858-9f7f-9149e89c8a08?P1=1739801495&P2=404&P3=2&P4=SONmYbuD0J5jE3h5b2TdhZ5PujwPPBkNR8kk7jCvmHx8dKL8TwDcX23OhhOs1UJ9q6yGcO0mnoE%2bqA2%2f9dNpRw%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 2.16.164.51:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1380 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1016 | RUXIMICS.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5064 | SearchApp.exe | 2.23.227.208:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
3976 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6628 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6340 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
elektroautomatik.com |
| unknown |
business.bing.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
Threats
Process | Message |
|---|---|
CodeMeterCC.exe | Qt: Untested Windows version 10.0 detected!
|
CodeMeterCC.exe | QSystemTrayIcon::setVisible: No Icon set
|
EA Battery Simulator.exe | ### Bat Simu ### First: battery_simu_license_ok = False
|
EA Battery Simulator.exe | ### Bat Simu ### Second: battery_simu_license_ok = False
|