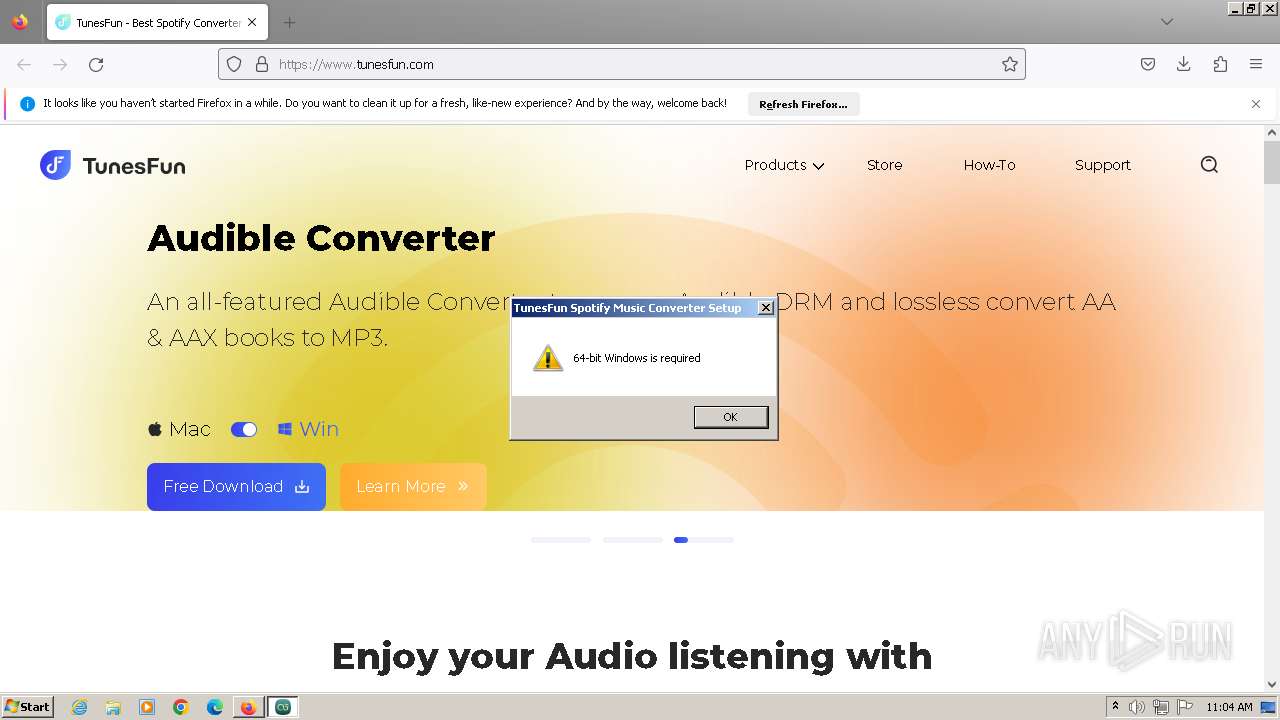
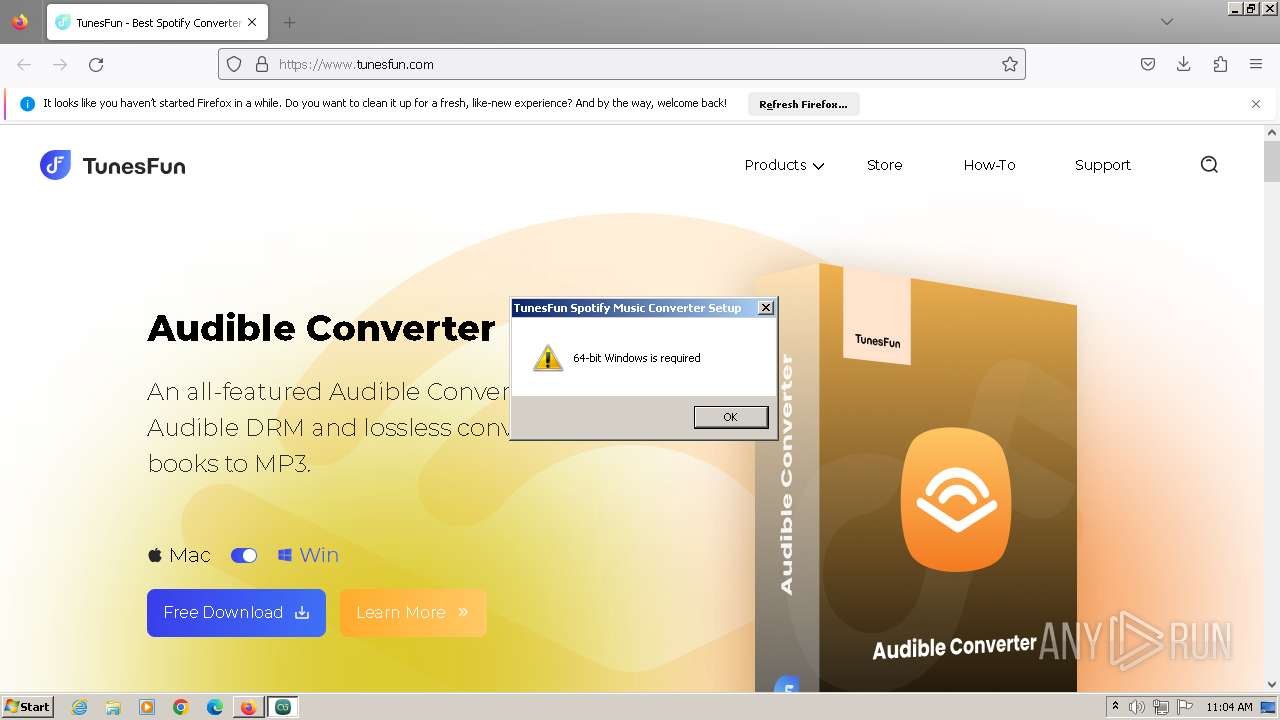
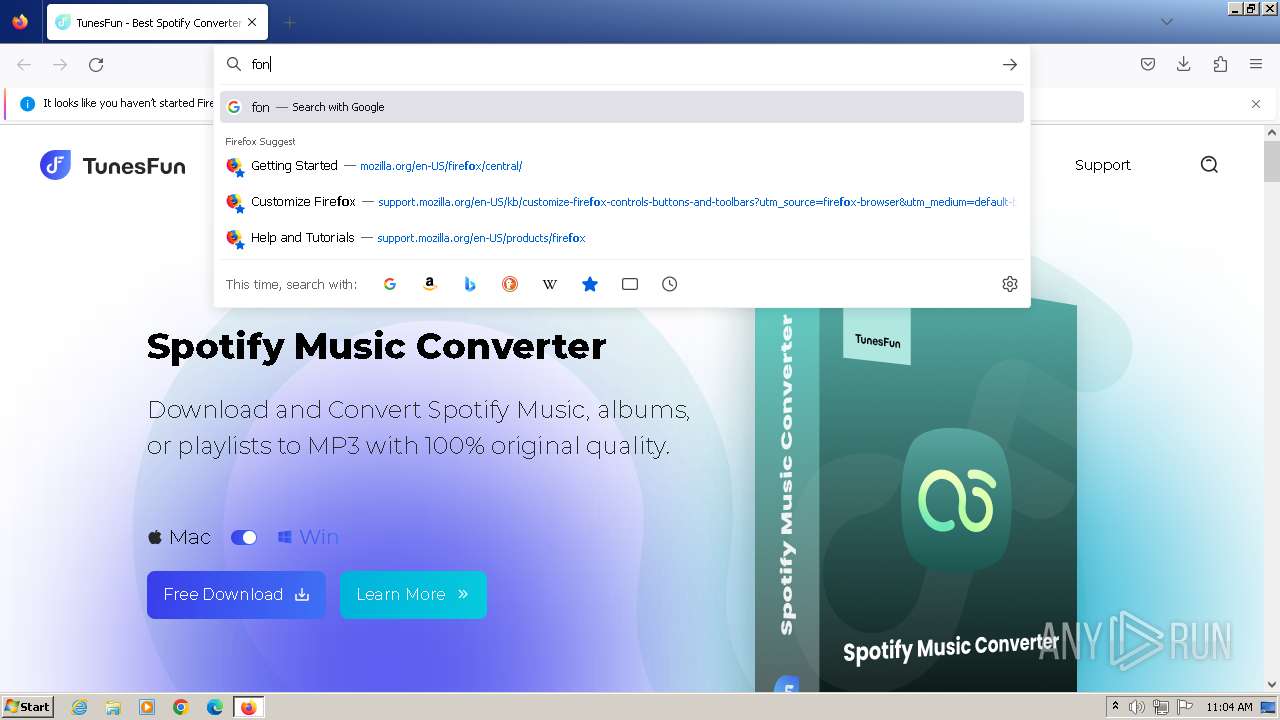
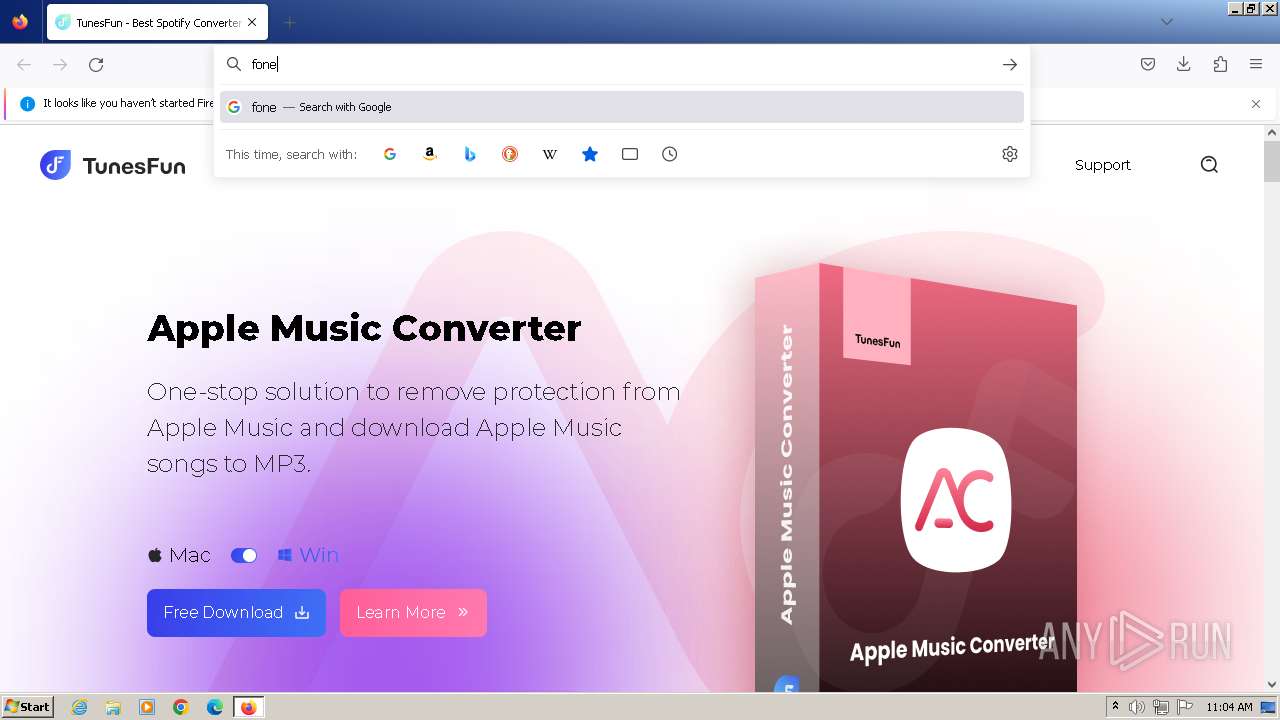
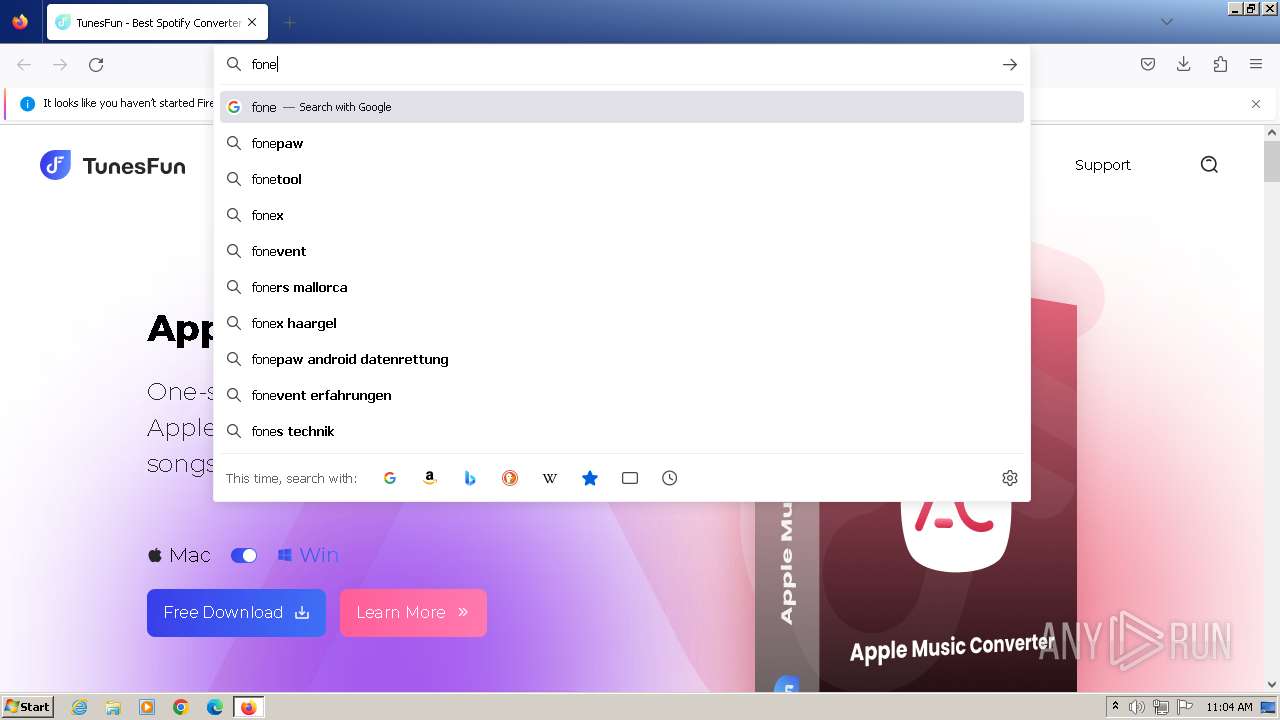
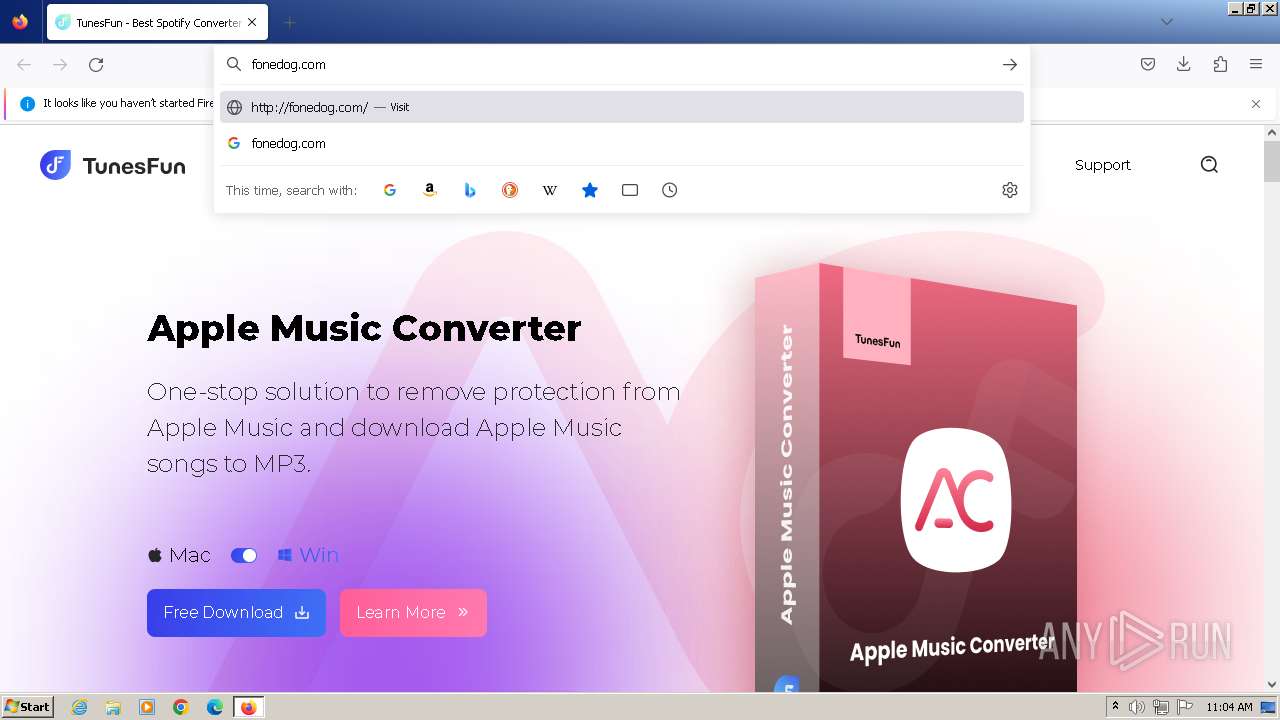
| URL: | tunesfun.com |
| Full analysis: | https://app.any.run/tasks/c6a037e4-2038-454b-b022-d4d4fff49faf |
| Verdict: | Malicious activity |
| Analysis date: | May 07, 2024, 10:03:32 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 9836EB9C0223D034BE2FE58AB2A940DB |
| SHA1: | 18CFF49575CDC020DF42E8EBB240B402473D43EB |
| SHA256: | 029E8FA277297445CDB8D35D07E5DC9801530FD589DC939A1F7C7A8FB8A419FC |
| SSDEEP: | 3:me2:mr |
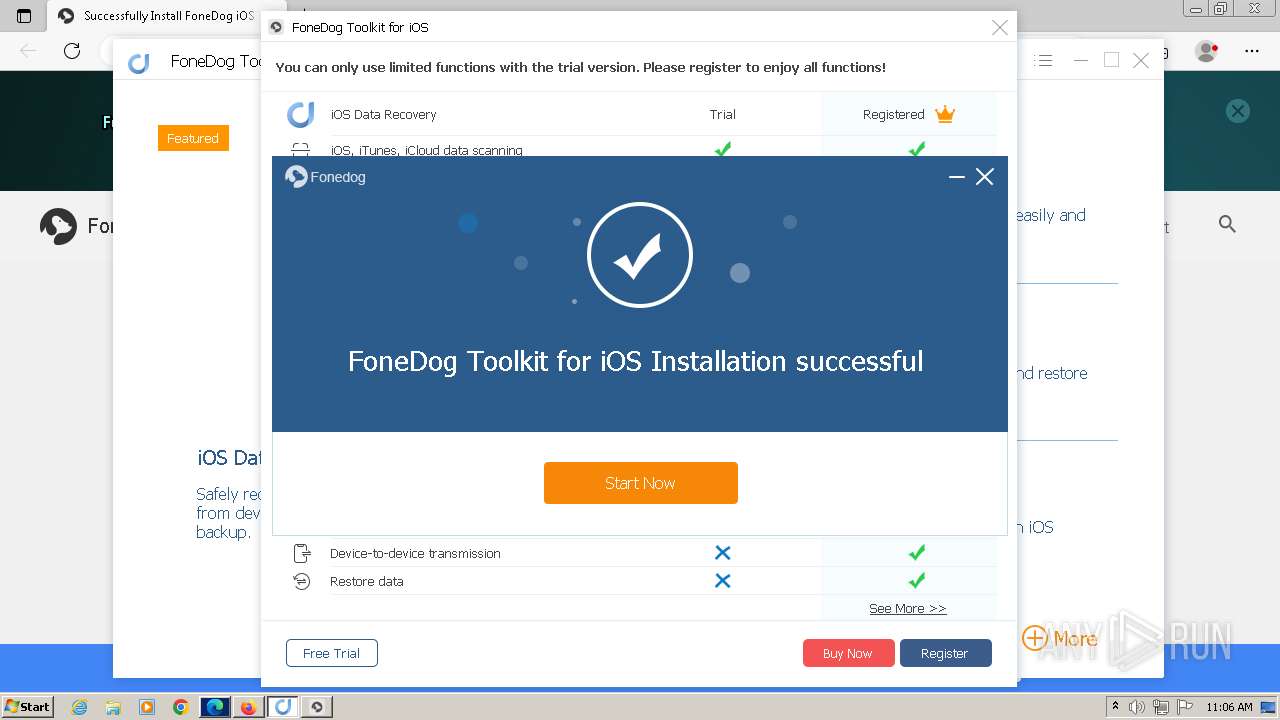
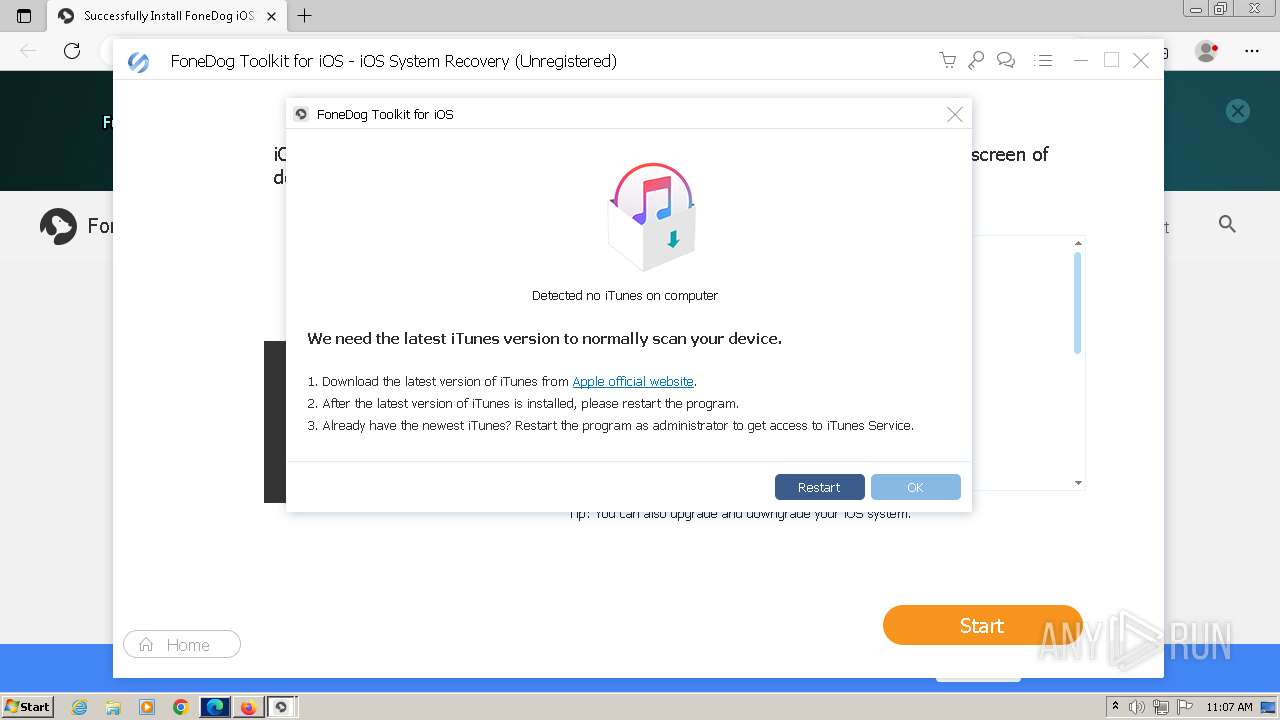
MALICIOUS
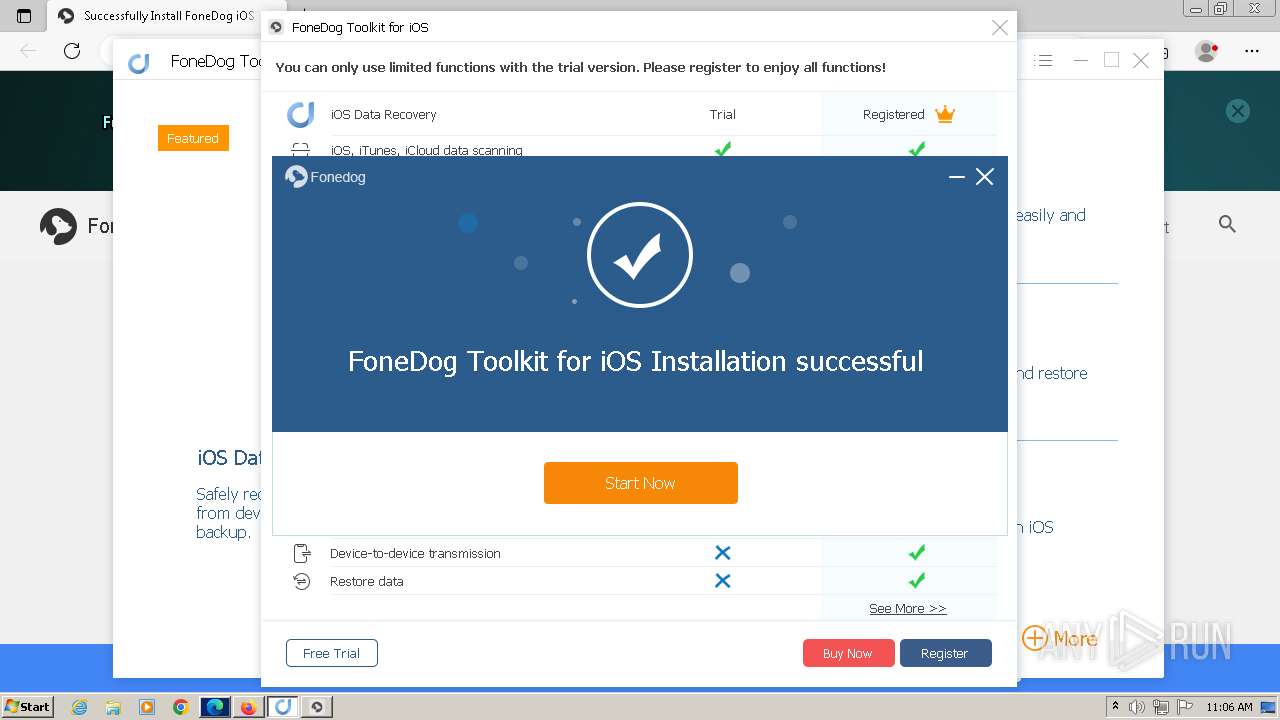
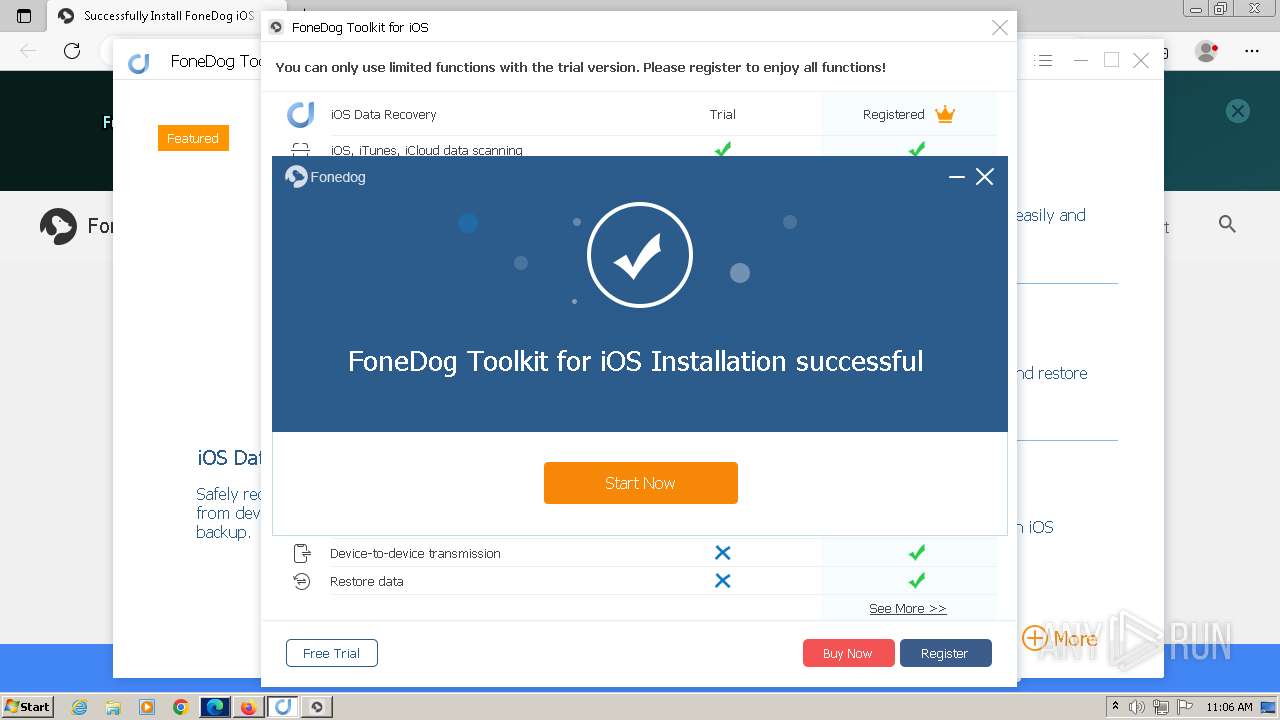
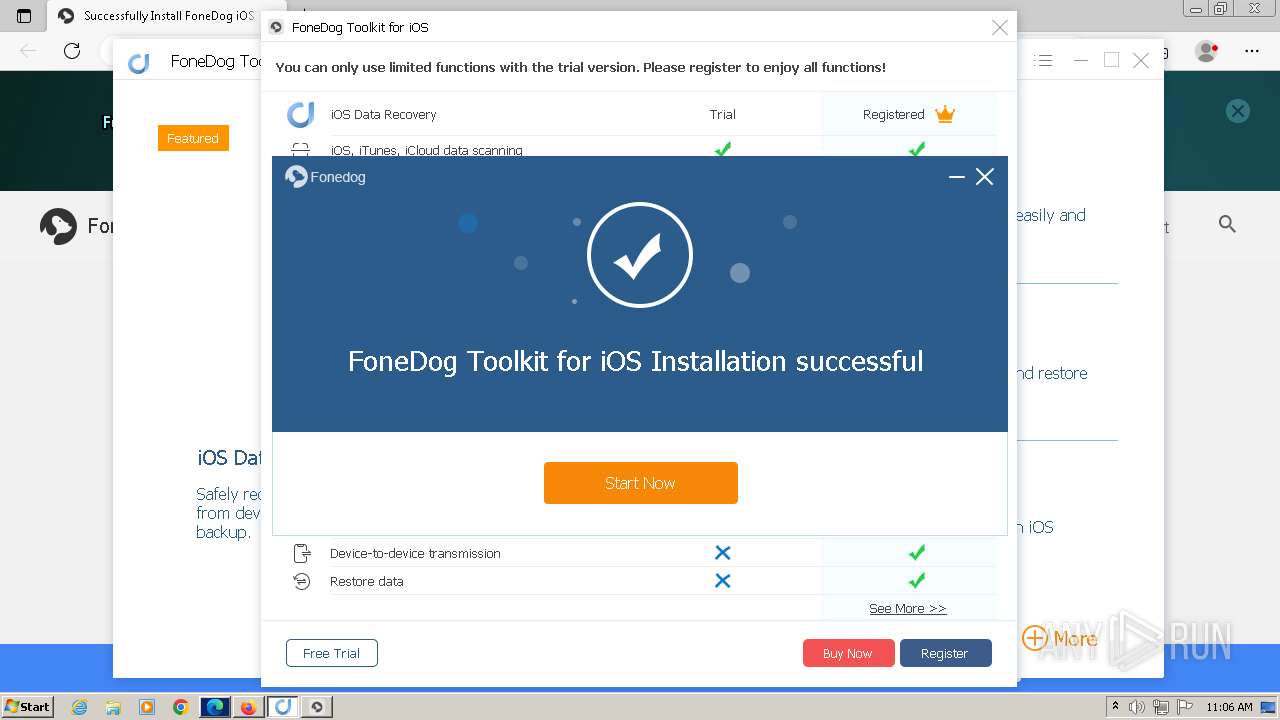
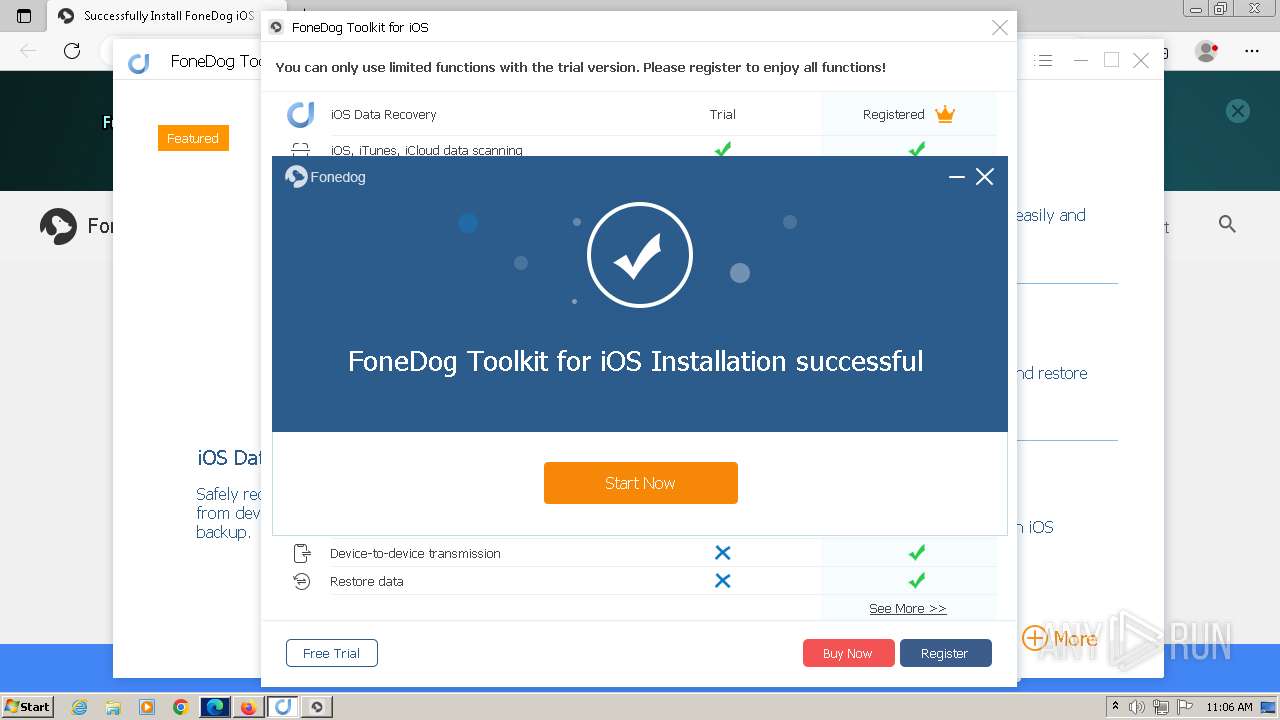
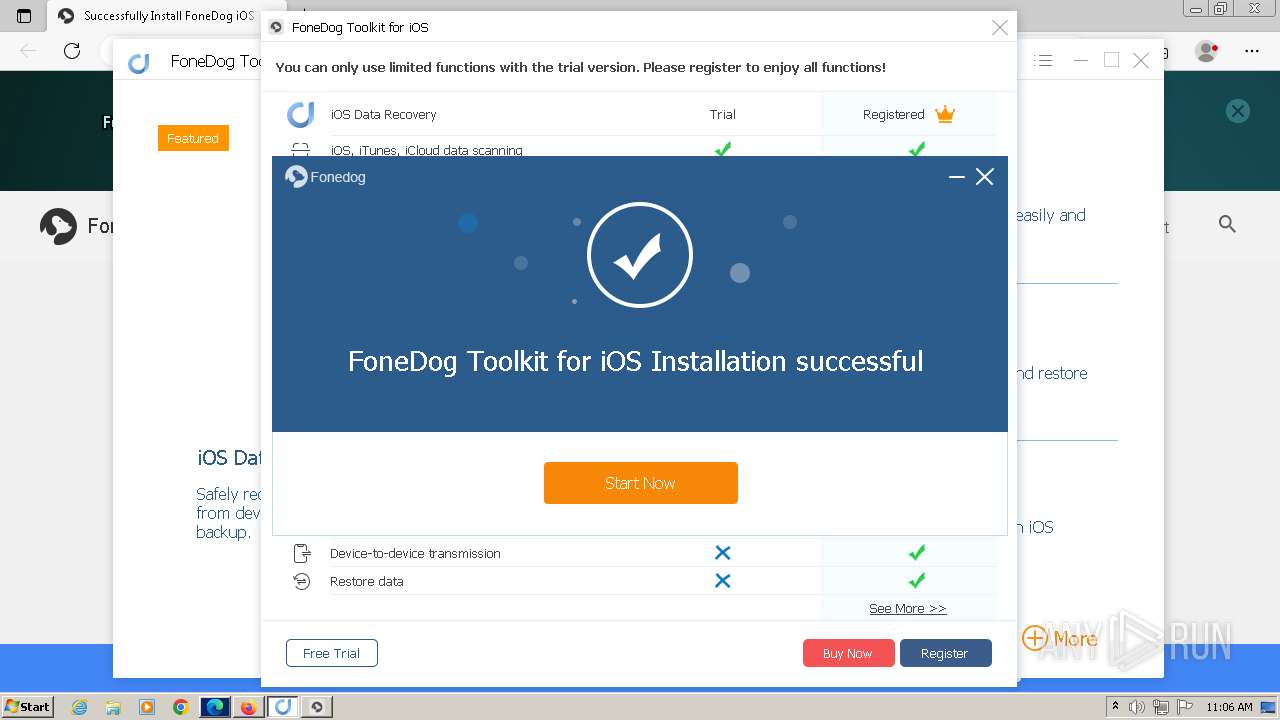
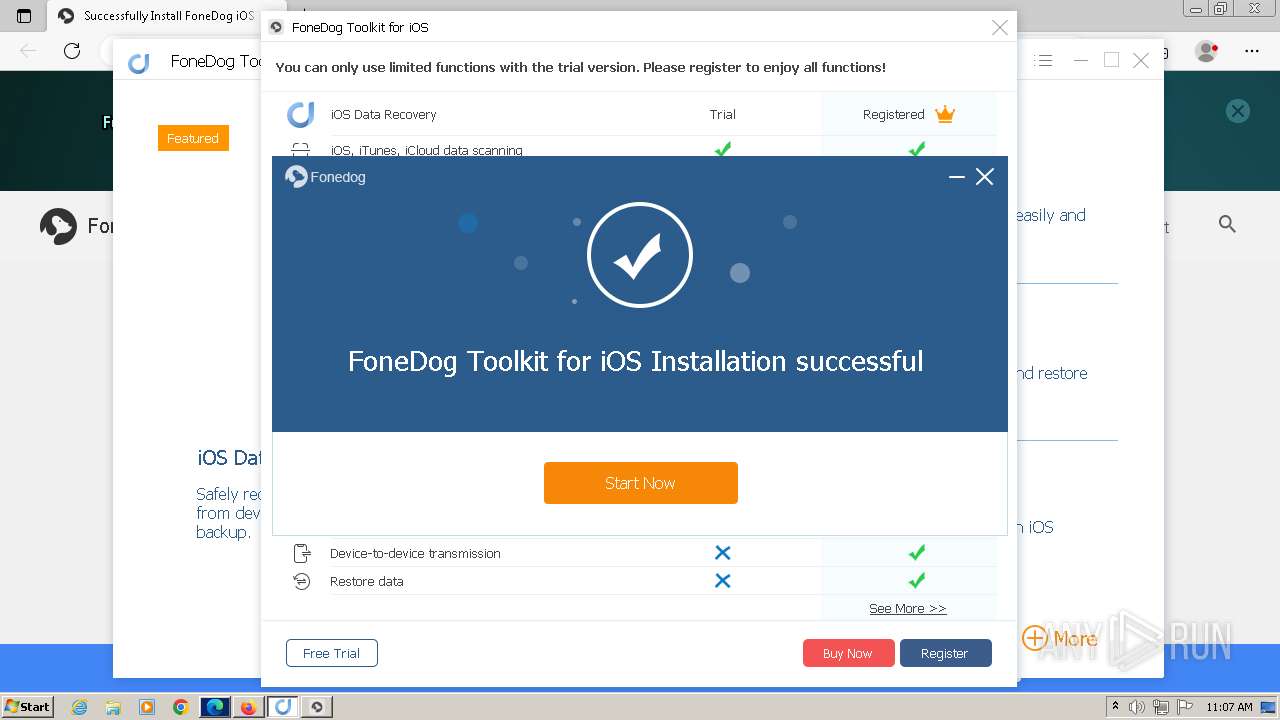
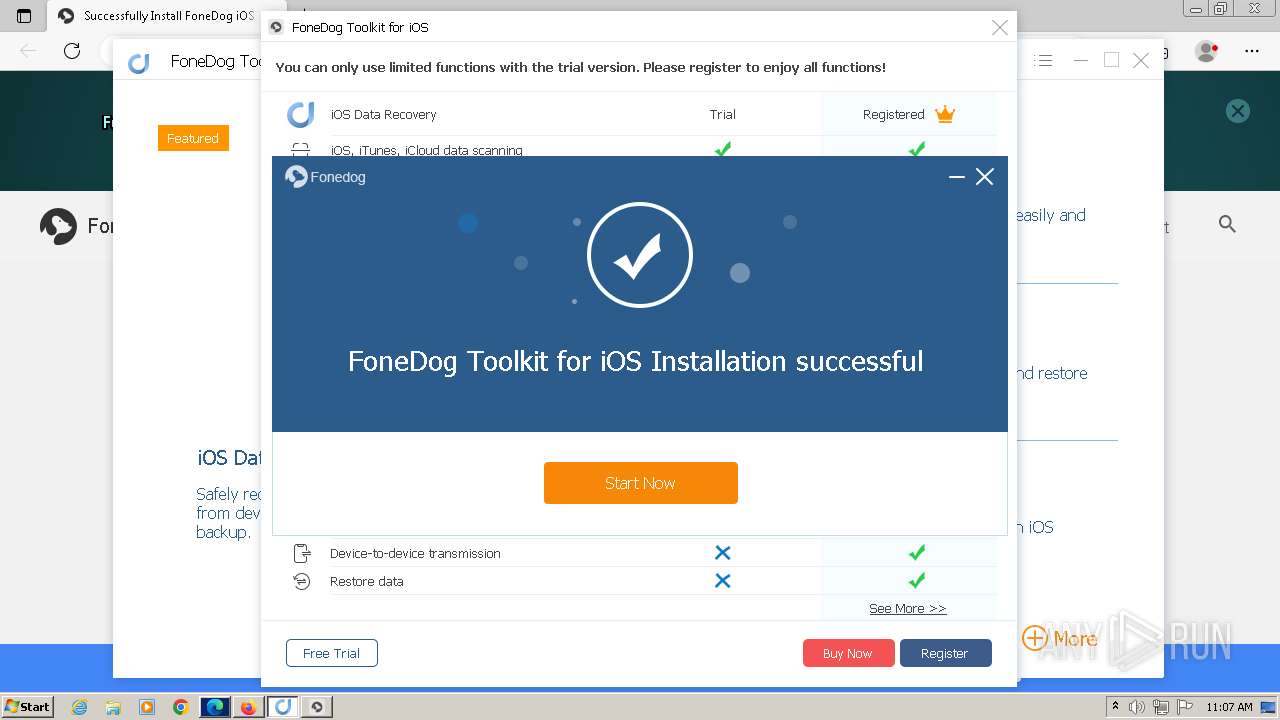
Drops the executable file immediately after the start
- spotify-music-converter.exe (PID: 3104)
- fonedog-ios-toolkit.exe (PID: 3960)
- fonedog-ios-toolkit.tmp (PID: 1756)
- fonedog-ios-toolkit-32.exe (PID: 2824)
- fonedog-ios-toolkit-32.tmp (PID: 2840)
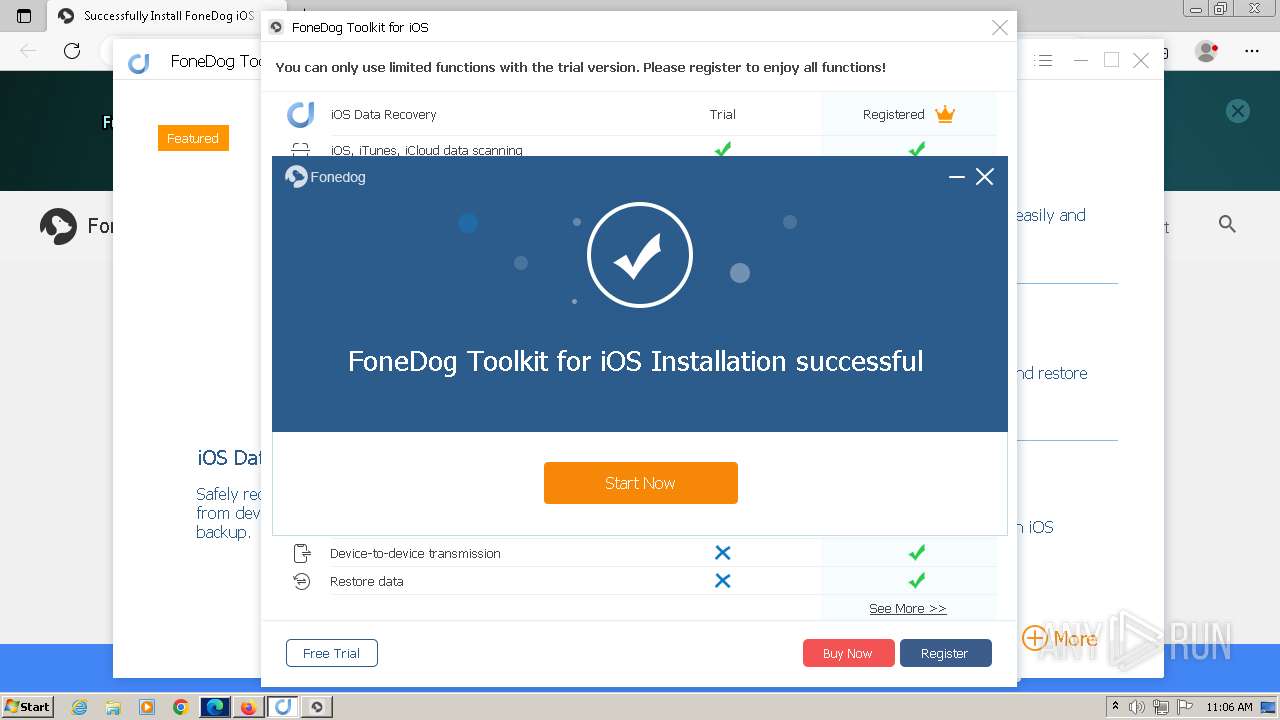
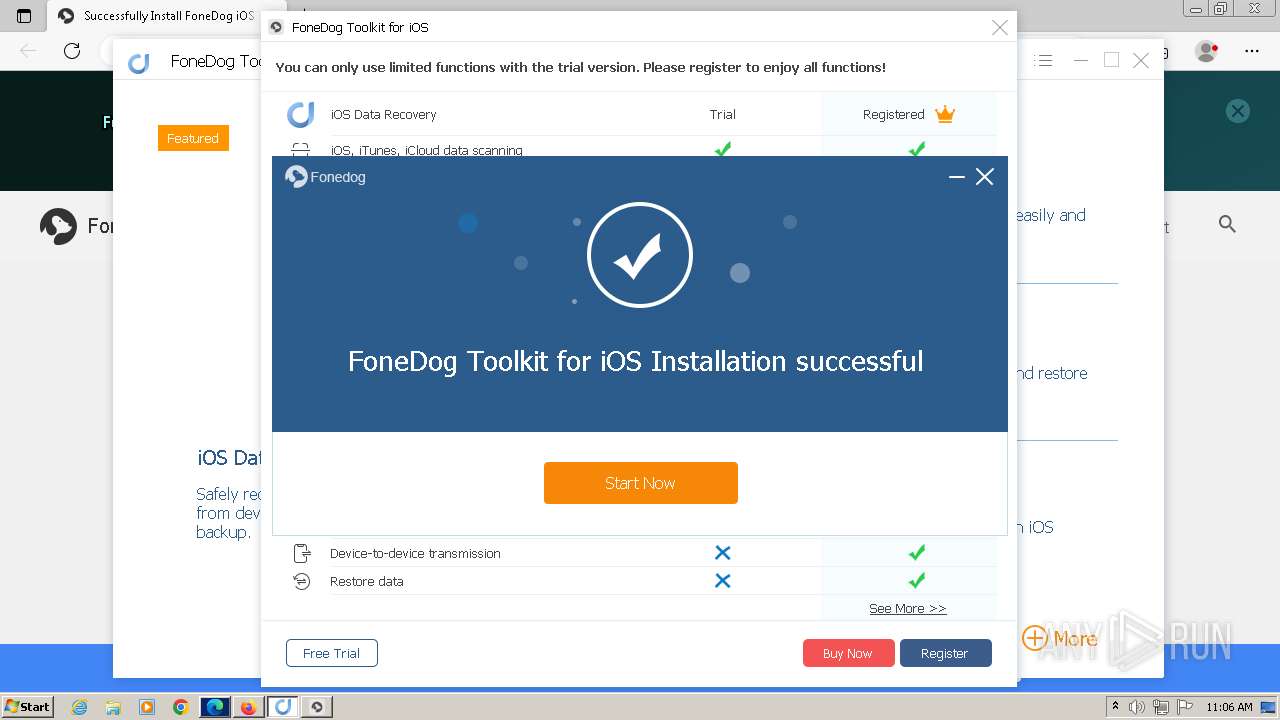
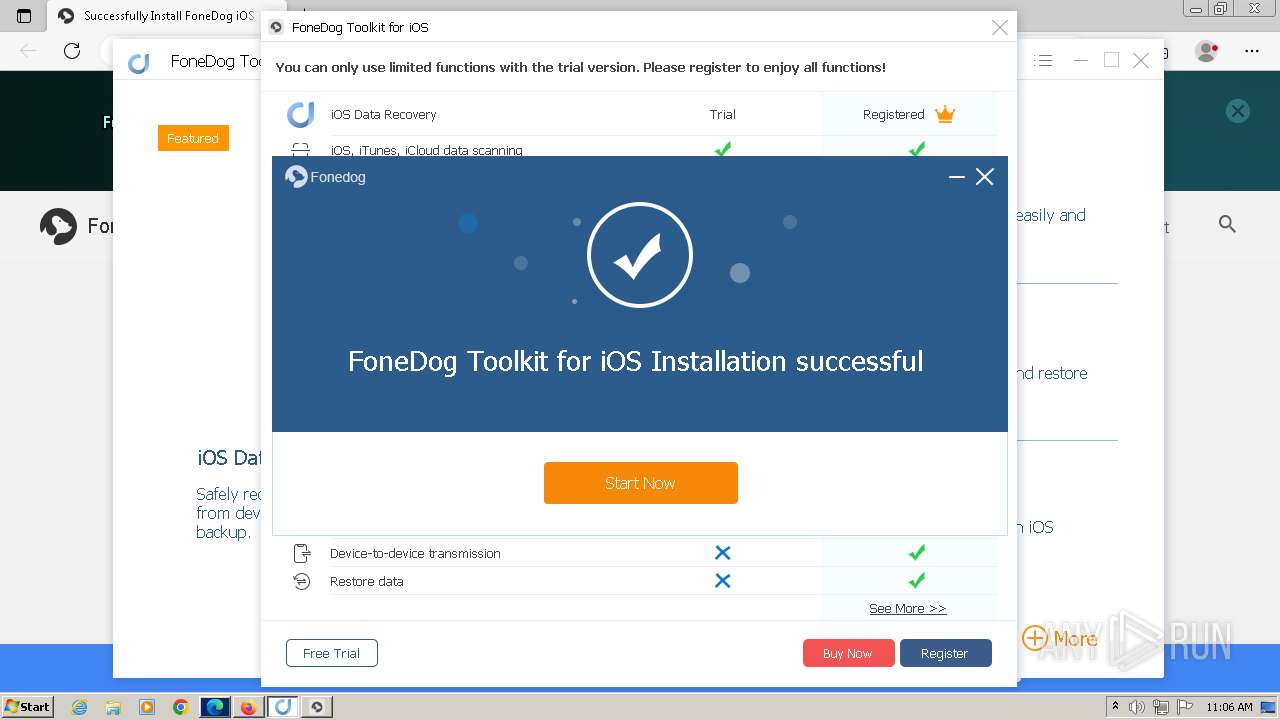
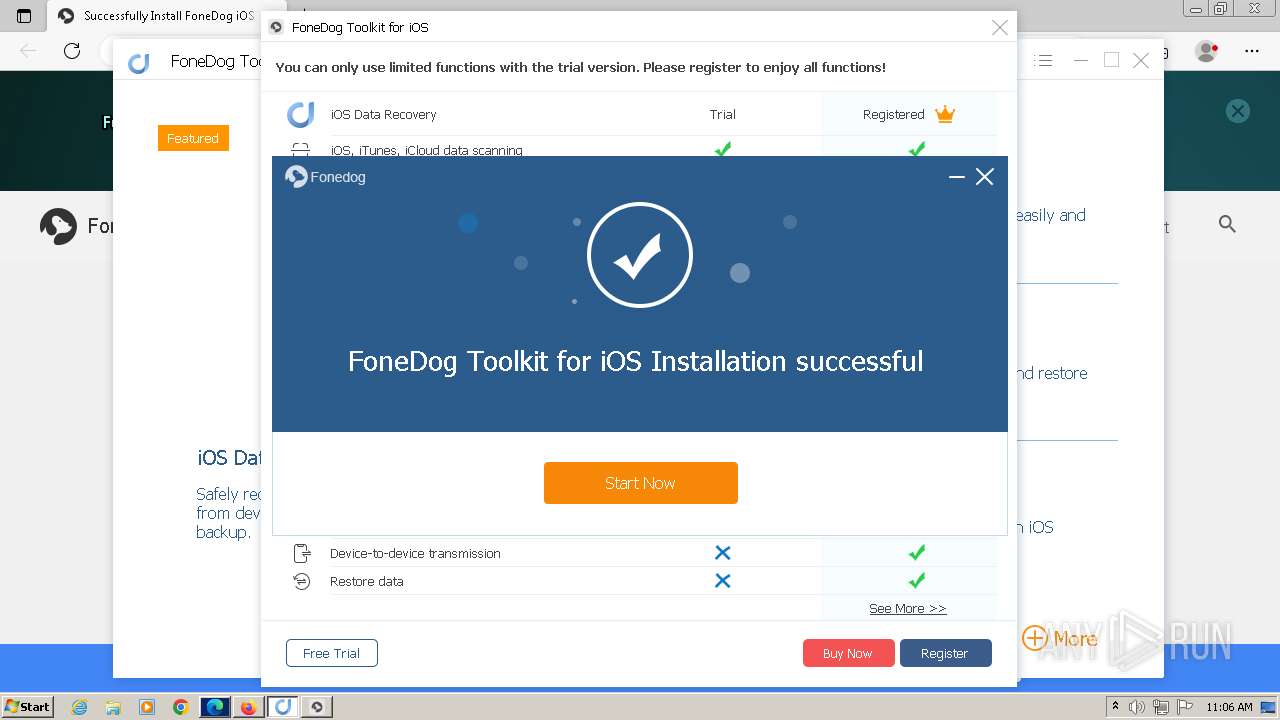
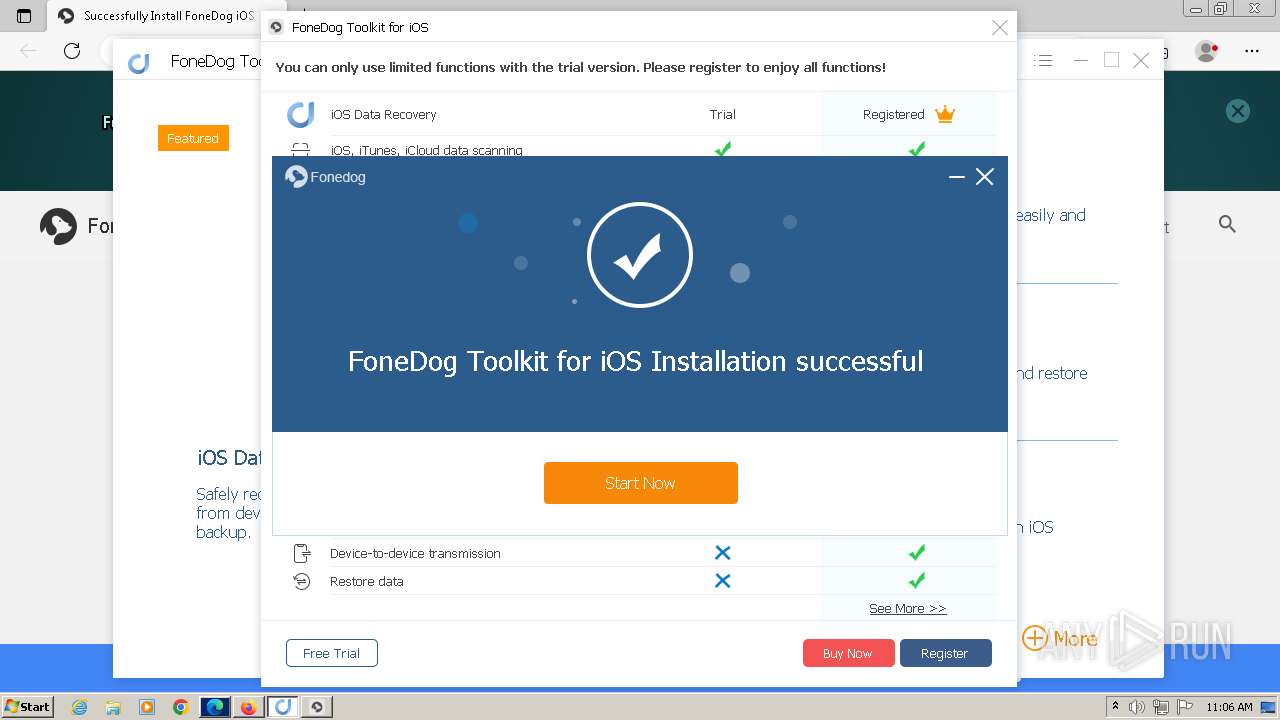
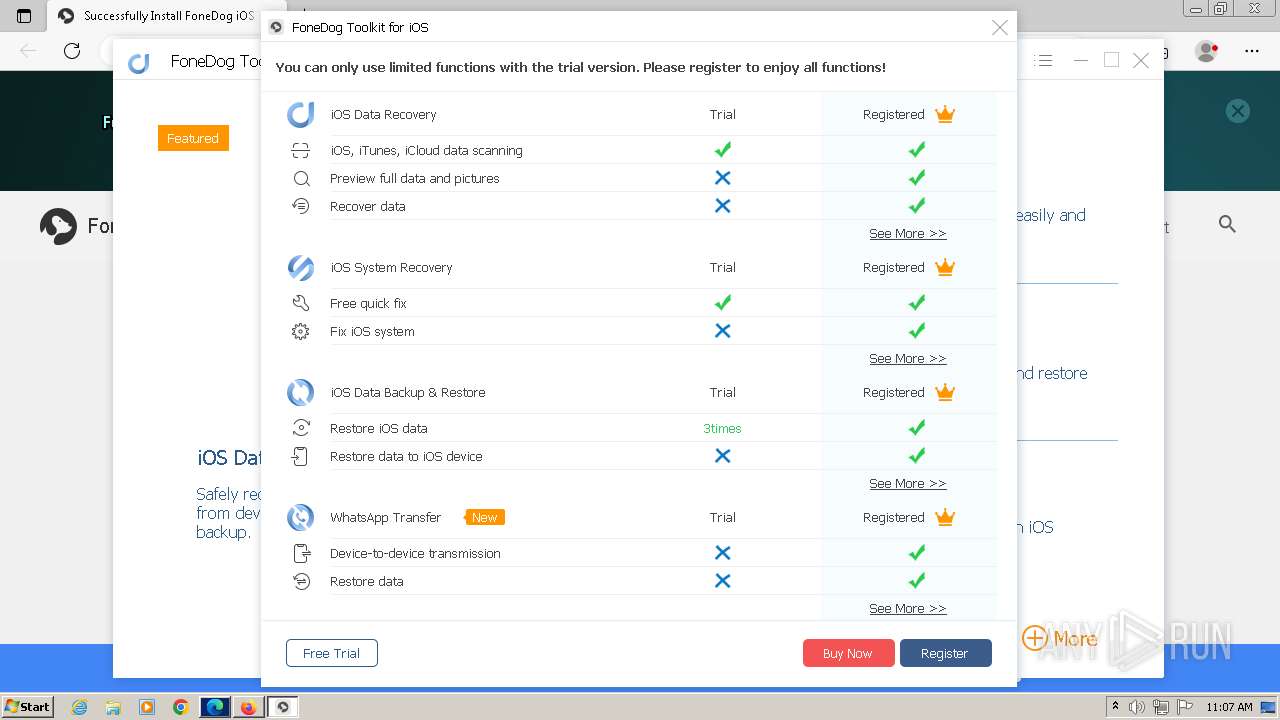
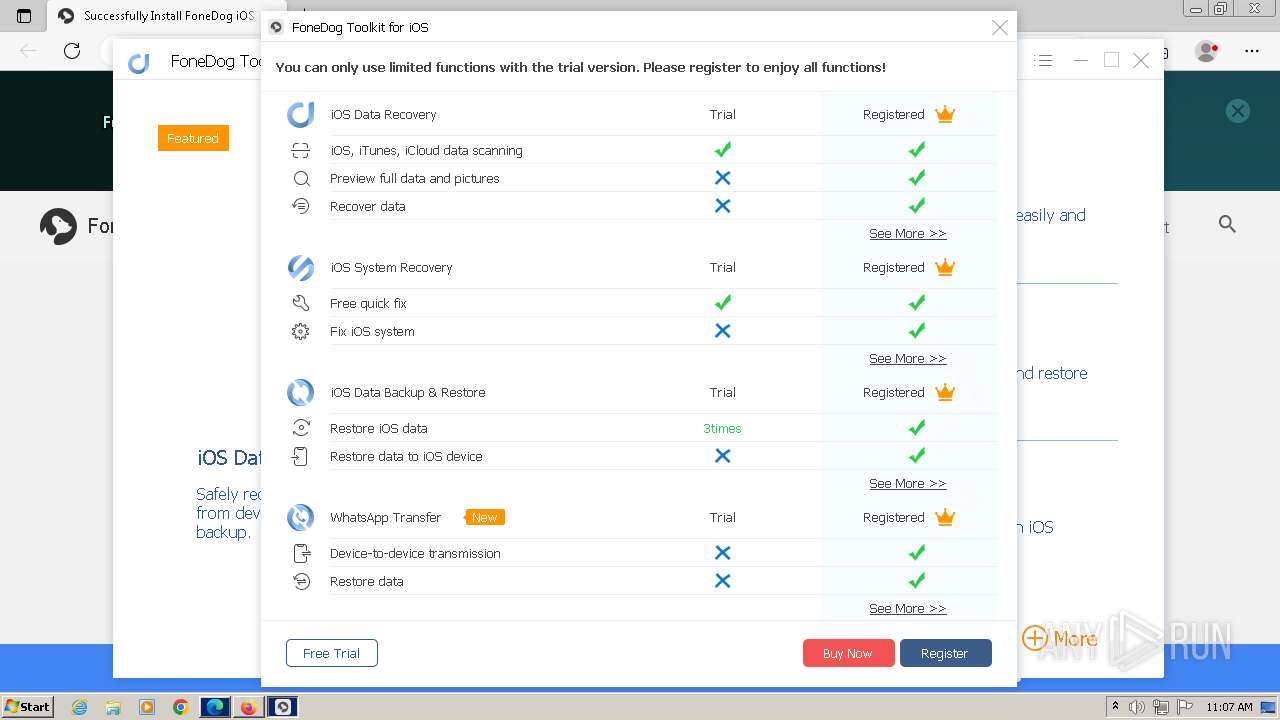
- FoneDog Toolkit - iOS Data Recovery.exe (PID: 3380)
Changes the autorun value in the registry
- fonedog-ios-toolkit-32.tmp (PID: 2840)
SUSPICIOUS
Executable content was dropped or overwritten
- spotify-music-converter.exe (PID: 3104)
- fonedog-ios-toolkit.exe (PID: 3960)
- fonedog-ios-toolkit.tmp (PID: 1756)
- fonedog-ios-toolkit-32.exe (PID: 2824)
- fonedog-ios-toolkit-32.tmp (PID: 2840)
- FoneDog Toolkit - iOS Data Recovery.exe (PID: 3380)
The process creates files with name similar to system file names
- spotify-music-converter.exe (PID: 3104)
Malware-specific behavior (creating "System.dll" in Temp)
- spotify-music-converter.exe (PID: 3104)
Reads the Windows owner or organization settings
- fonedog-ios-toolkit.tmp (PID: 1756)
- fonedog-ios-toolkit-32.tmp (PID: 2840)
Drops 7-zip archiver for unpacking
- fonedog-ios-toolkit-32.tmp (PID: 2840)
Process drops legitimate windows executable
- fonedog-ios-toolkit-32.tmp (PID: 2840)
- FoneDog Toolkit - iOS Data Recovery.exe (PID: 3380)
Reads the Internet Settings
- fonedog-ios-toolkit-32.tmp (PID: 2840)
- FoneDog Toolkit - iOS Data Recovery.exe (PID: 2512)
- fonedog-ios-toolkit.tmp (PID: 1756)
Process drops SQLite DLL files
- fonedog-ios-toolkit-32.tmp (PID: 2840)
Reads security settings of Internet Explorer
- fonedog-ios-toolkit-32.tmp (PID: 2840)
- fonedog-ios-toolkit.tmp (PID: 1756)
The process drops C-runtime libraries
- fonedog-ios-toolkit-32.tmp (PID: 2840)
- FoneDog Toolkit - iOS Data Recovery.exe (PID: 3380)
Reads settings of System Certificates
- AppService.exe (PID: 3072)
- FoneDog Toolkit - iOS Data Recovery.exe (PID: 3028)
- FoneDog Toolkit - iOS Data Recovery.exe (PID: 3380)
- FoneDog Toolkit - iOS Data Recovery.exe (PID: 2160)
Searches for installed software
- FoneDog Toolkit - iOS Data Recovery.exe (PID: 3380)
- FoneDog Toolkit - iOS Data Recovery.exe (PID: 2160)
Application launched itself
- FoneDog Toolkit - iOS Data Recovery.exe (PID: 3380)
INFO
Application launched itself
- firefox.exe (PID: 3956)
- firefox.exe (PID: 3972)
- msedge.exe (PID: 2652)
- msedge.exe (PID: 3656)
Manual execution by a user
- wmpnscfg.exe (PID: 2852)
- msedge.exe (PID: 3656)
Checks supported languages
- wmpnscfg.exe (PID: 2852)
- spotify-music-converter.exe (PID: 3104)
- fonedog-ios-toolkit.exe (PID: 3960)
- fonedog-ios-toolkit.tmp (PID: 1756)
- fonedog-ios-toolkit-32.exe (PID: 2824)
- FoneDog Toolkit - iOS Data Recovery.exe (PID: 3136)
- AppService.exe (PID: 3072)
- fonedog-ios-toolkit-32.tmp (PID: 2840)
- FoneDog Toolkit - iOS Data Recovery.exe (PID: 2512)
- FoneDog Toolkit - iOS Data Recovery.exe (PID: 3028)
- FoneDog Toolkit - iOS Data Recovery.exe (PID: 3380)
- splashScreen.exe (PID: 1612)
- AppService.exe (PID: 1012)
- FoneDog Toolkit - iOS Data Recovery.exe (PID: 3180)
- CEIPPost.exe (PID: 1980)
- FoneDog Toolkit - iOS Data Recovery.exe (PID: 2160)
- splashScreen.exe (PID: 3000)
- AppService.exe (PID: 2756)
- CleanCache.exe (PID: 2920)
Reads the computer name
- wmpnscfg.exe (PID: 2852)
- spotify-music-converter.exe (PID: 3104)
- fonedog-ios-toolkit.tmp (PID: 1756)
- fonedog-ios-toolkit-32.tmp (PID: 2840)
- AppService.exe (PID: 3072)
- FoneDog Toolkit - iOS Data Recovery.exe (PID: 2512)
- FoneDog Toolkit - iOS Data Recovery.exe (PID: 3136)
- FoneDog Toolkit - iOS Data Recovery.exe (PID: 3028)
- FoneDog Toolkit - iOS Data Recovery.exe (PID: 3380)
- AppService.exe (PID: 1012)
- FoneDog Toolkit - iOS Data Recovery.exe (PID: 3180)
- CEIPPost.exe (PID: 1980)
- FoneDog Toolkit - iOS Data Recovery.exe (PID: 2160)
- AppService.exe (PID: 2756)
Create files in a temporary directory
- spotify-music-converter.exe (PID: 3104)
- fonedog-ios-toolkit.exe (PID: 3960)
- fonedog-ios-toolkit.tmp (PID: 1756)
- fonedog-ios-toolkit-32.exe (PID: 2824)
- fonedog-ios-toolkit-32.tmp (PID: 2840)
- FoneDog Toolkit - iOS Data Recovery.exe (PID: 3380)
- FoneDog Toolkit - iOS Data Recovery.exe (PID: 2160)
Executable content was dropped or overwritten
- firefox.exe (PID: 3972)
Drops the executable file immediately after the start
- firefox.exe (PID: 3972)
The process uses the downloaded file
- firefox.exe (PID: 3972)
Creates files in the program directory
- fonedog-ios-toolkit.tmp (PID: 1756)
- fonedog-ios-toolkit-32.tmp (PID: 2840)
- FoneDog Toolkit - iOS Data Recovery.exe (PID: 3380)
- FoneDog Toolkit - iOS Data Recovery.exe (PID: 2160)
Dropped object may contain TOR URL's
- fonedog-ios-toolkit-32.tmp (PID: 2840)
Creates a software uninstall entry
- fonedog-ios-toolkit-32.tmp (PID: 2840)
Creates files or folders in the user directory
- fonedog-ios-toolkit-32.tmp (PID: 2840)
- FoneDog Toolkit - iOS Data Recovery.exe (PID: 2512)
- AppService.exe (PID: 3072)
- FoneDog Toolkit - iOS Data Recovery.exe (PID: 3380)
- FoneDog Toolkit - iOS Data Recovery.exe (PID: 2160)
Reads the machine GUID from the registry
- AppService.exe (PID: 3072)
- FoneDog Toolkit - iOS Data Recovery.exe (PID: 3028)
- FoneDog Toolkit - iOS Data Recovery.exe (PID: 3380)
- FoneDog Toolkit - iOS Data Recovery.exe (PID: 2160)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
99
Monitored processes
57
Malicious processes
8
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1012 | "C:\Program Files\FoneDog\FoneDog Toolkit - iOS Data Recovery\AppService.exe" | C:\Program Files\FoneDog\FoneDog Toolkit - iOS Data Recovery\AppService.exe | — | FoneDog Toolkit - iOS Data Recovery.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1024 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3972.0.1360182851\1384843620" -parentBuildID 20230710165010 -prefsHandle 1120 -prefMapHandle 1112 -prefsLen 28523 -prefMapSize 244195 -appDir "C:\Program Files\Mozilla Firefox\browser" - {c38e6d8a-e749-41f3-9f42-1f978d547002} 3972 "\\.\pipe\gecko-crash-server-pipe.3972" 1192 d7a91a0 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 115.0.2 Modules
| |||||||||||||||
| 1036 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3972.1.655817496\931899231" -parentBuildID 20230710165010 -prefsHandle 1436 -prefMapHandle 1428 -prefsLen 28600 -prefMapSize 244195 -appDir "C:\Program Files\Mozilla Firefox\browser" - {1a9b5859-d1a2-42e9-9365-bd652d51b130} 3972 "\\.\pipe\gecko-crash-server-pipe.3972" 1448 d71b130 socket | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 115.0.2 Modules
| |||||||||||||||
| 1128 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2212 --field-trial-handle=1288,i,8683127995237398539,13598137484147027971,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1132 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3516 --field-trial-handle=1288,i,8683127995237398539,13598137484147027971,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1248 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=3444 --field-trial-handle=1288,i,8683127995237398539,13598137484147027971,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1412 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=109.0.5414.149 "--annotation=exe=C:\Program Files\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win32 "--annotation=prod=Microsoft Edge" --annotation=ver=109.0.1518.115 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd8,0x690af598,0x690af5a8,0x690af5b4 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1612 | "C:\Program Files\FoneDog\FoneDog Toolkit - iOS Data Recovery\splashScreen.exe" -l ZW4= -m1 PGZvbnQgY29sb3IgPSAjZmZmPkxvYWRpbmcgbGFuZ3VhZ2UuLi48L2ZvbnQ+ -c PGZvbnQgY29sb3I9IzY2NjY2Nj5Db3B5cmlnaHQgPHNwYW4gc3R5bGU9ImZvbnQtZmFtaWx5OkFyaWFsOyI+JmNvcHk7PC9zcGFuPiAyMDI0IEZvbmVEb2cuIEFsbCByaWdodHMgcmVzZXJ2ZWQuPC9mb250Pg== -v PGI+PGZvbnQgY29sb3IgPSAjNjY2NjY2PlZlcnNpb246IDIuMS45NjwvZm9udD4= -m2 PGZvbnQgY29sb3IgPSAjZmZmPkZyYW1ld29yayBpbml0aWFsaXppbmcuLi48L2ZvbnQ+ -m3 PGZvbnQgY29sb3IgPSAjZmZmPkxvYWRpbmcgc2tpbi4uLjwvZm9udD4= -m4 PGZvbnQgY29sb3IgPSAjZmZmPlByZXBhcmluZyBtYWluIHdpbmRvdy4uLjwvZm9udD4= -f VGFob21h | C:\Program Files\FoneDog\FoneDog Toolkit - iOS Data Recovery\splashScreen.exe | — | FoneDog Toolkit - iOS Data Recovery.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 62097 Modules
| |||||||||||||||
| 1756 | "C:\Users\admin\AppData\Local\Temp\is-9MCF7.tmp\fonedog-ios-toolkit.tmp" /SL5="$30136,1334348,166912,C:\Users\admin\Downloads\fonedog-ios-toolkit.exe" | C:\Users\admin\AppData\Local\Temp\is-9MCF7.tmp\fonedog-ios-toolkit.tmp | fonedog-ios-toolkit.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 1 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 1856 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3972.2.1145471938\1897661635" -childID 1 -isForBrowser -prefsHandle 2000 -prefMapHandle 2024 -prefsLen 24491 -prefMapSize 244195 -jsInitHandle 896 -jsInitLen 240908 -parentBuildID 20230710165010 -appDir "C:\Program Files\Mozilla Firefox\browser" - {4a075ee8-5a82-4cab-a8bb-ddaf83a82183} 3972 "\\.\pipe\gecko-crash-server-pipe.3972" 2088 12e93280 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 115.0.2 Modules
| |||||||||||||||
Total events
45 338
Read events
44 831
Write events
482
Delete events
25
Modification events
| (PID) Process: | (3956) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Launcher |
Value: D340FBE200000000 | |||
| (PID) Process: | (3972) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Browser |
Value: 63E3FCE200000000 | |||
| (PID) Process: | (3972) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Installer\308046B0AF4A39CB |
| Operation: | delete value | Name: | installer.taskbarpin.win10.enabled |
Value: | |||
| (PID) Process: | (3972) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Telemetry |
Value: 0 | |||
| (PID) Process: | (3972) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (3972) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\PreXULSkeletonUISettings |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Theme |
Value: 1 | |||
| (PID) Process: | (3972) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\PreXULSkeletonUISettings |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Enabled |
Value: 1 | |||
| (PID) Process: | (3972) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableTelemetry |
Value: 1 | |||
| (PID) Process: | (3972) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableDefaultBrowserAgent |
Value: 0 | |||
| (PID) Process: | (3972) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|SetDefaultBrowserUserChoice |
Value: 1 | |||
Executable files
503
Suspicious files
270
Text files
220
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3972 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 3972 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\activity-stream.discovery_stream.json | — | |
MD5:— | SHA256:— | |||
| 3972 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\2918063365piupsah.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 3972 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\urlCache-current.bin | binary | |
MD5:04BADC0A17F546BBD91CC2404D2776D9 | SHA256:54CD83D3031D15EA1F5B1C5D73416C0B2F9151F93E130DD525DDA488A8EB9110 | |||
| 3972 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\targeting.snapshot.json | — | |
MD5:— | SHA256:— | |||
| 3972 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\prefs-1.js | text | |
MD5:A4C0253717519EB0B07D5D8DD14F5D02 | SHA256:115B88AA451EA9D5CD010C60DB4B97759E55ECE806CF6C4EBA737C6290C0D044 | |||
| 3972 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\1657114595AmcateirvtiSty.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 3972 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\prefs.js | text | |
MD5:A4C0253717519EB0B07D5D8DD14F5D02 | SHA256:115B88AA451EA9D5CD010C60DB4B97759E55ECE806CF6C4EBA737C6290C0D044 | |||
| 3972 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 3972 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
45
TCP/UDP connections
225
DNS requests
354
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3972 | firefox.exe | POST | 200 | 142.250.186.35:80 | http://ocsp.pki.goog/gts1c3 | unknown | — | — | unknown |
3972 | firefox.exe | POST | 200 | 18.245.65.219:80 | http://ocsp.r2m02.amazontrust.com/ | unknown | — | — | unknown |
3972 | firefox.exe | POST | 200 | 18.245.65.219:80 | http://ocsp.e2m02.amazontrust.com/ | unknown | — | — | unknown |
3972 | firefox.exe | POST | 200 | 95.100.146.41:80 | http://r3.o.lencr.org/ | unknown | — | — | unknown |
3972 | firefox.exe | POST | 200 | 142.250.186.35:80 | http://ocsp.pki.goog/gts1c3 | unknown | — | — | unknown |
3972 | firefox.exe | POST | 200 | 142.250.186.35:80 | http://ocsp.pki.goog/gts1c3 | unknown | — | — | unknown |
3972 | firefox.exe | GET | 301 | 188.114.96.3:80 | http://tunesfun.com/ | unknown | — | — | unknown |
3972 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | unknown |
3972 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | unknown |
3972 | firefox.exe | POST | 200 | 95.100.146.41:80 | http://r3.o.lencr.org/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3972 | firefox.exe | 188.114.96.3:80 | tunesfun.com | CLOUDFLARENET | NL | unknown |
3972 | firefox.exe | 142.250.186.35:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
3972 | firefox.exe | 142.250.184.202:443 | safebrowsing.googleapis.com | — | — | whitelisted |
3972 | firefox.exe | 188.114.96.3:443 | tunesfun.com | CLOUDFLARENET | NL | unknown |
3972 | firefox.exe | 34.117.188.166:443 | contile.services.mozilla.com | — | — | unknown |
3972 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
3972 | firefox.exe | 34.149.100.209:443 | firefox.settings.services.mozilla.com | GOOGLE | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
tunesfun.com |
| unknown |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
spocs.getpocket.com |
| shared |
prod.ads.prod.webservices.mozgcp.net |
| unknown |
firefox.settings.services.mozilla.com |
| whitelisted |
prod.remote-settings.prod.webservices.mozgcp.net |
| whitelisted |
Threats
2 ETPRO signatures available at the full report
Process | Message |
|---|---|
AppService.exe | ASL checking for logging parameters in environment variable "AppService.exe.log"
|
AppService.exe | ASL checking for logging parameters in environment variable "asl.log"
|
AppService.exe | ASL logging to file "C:\Users\admin\AppData\Roaming\Apple Computer\Logs\asl.110612_07May24.log"
|
AppService.exe | [(unknown facility) AppService.exe] _MobileDeviceLibraryInitRoutine (thread 3272): MobileDevice.framework version: 1533.100.57.100.2
|
AppService.exe | [(unknown facility) AppService.exe] AMDeviceNotificationSubscribeWithOptions (thread 3272): Failed to subscribe for mux notifications: 0xe8000063 (kAMDMuxCreateListenerError)
|
AppService.exe | [(unknown facility) AppService.exe] _SubscribeForMuxNotifications (thread 3272): USBMuxListenerCreate: File exists
|
FoneDog Toolkit - iOS Data Recovery.exe | QCssParser::parseHexColor: Unknown color name '#black'
|
FoneDog Toolkit - iOS Data Recovery.exe | libpng warning: iCCP: known incorrect sRGB profile
|
FoneDog Toolkit - iOS Data Recovery.exe | libpng warning: iCCP: known incorrect sRGB profile
|
FoneDog Toolkit - iOS Data Recovery.exe | libpng warning: iCCP: known incorrect sRGB profile
|