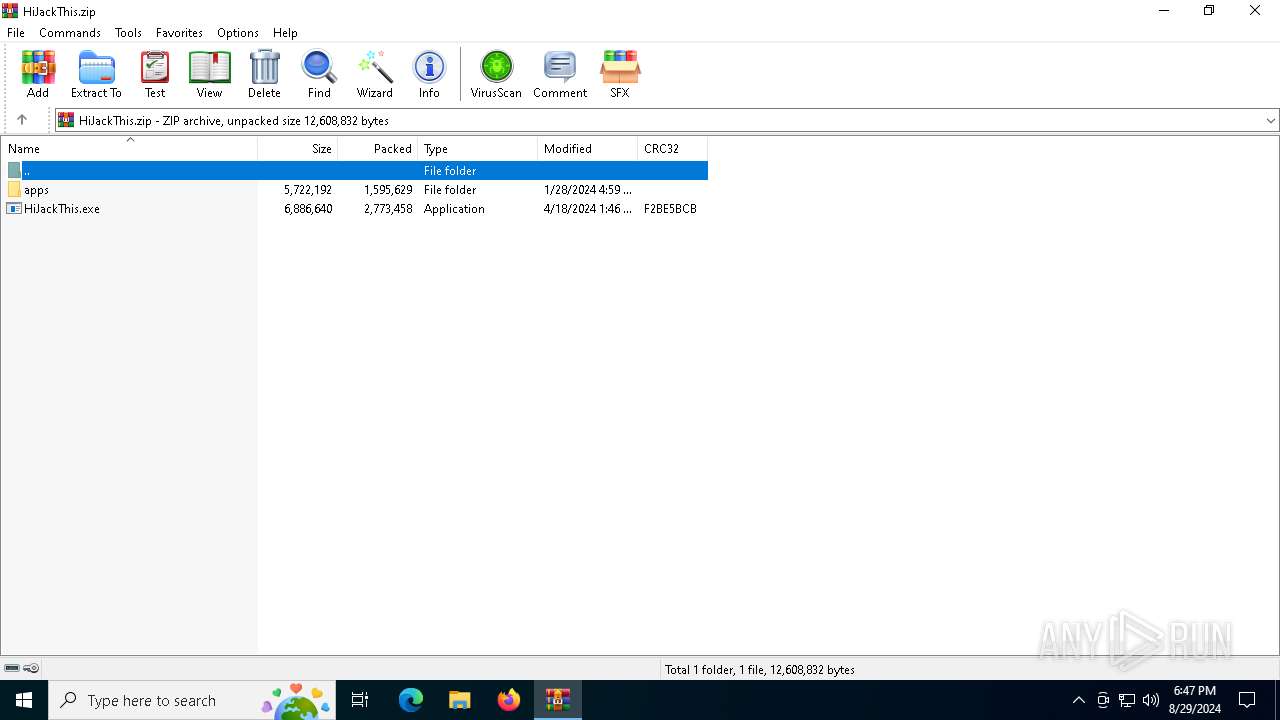
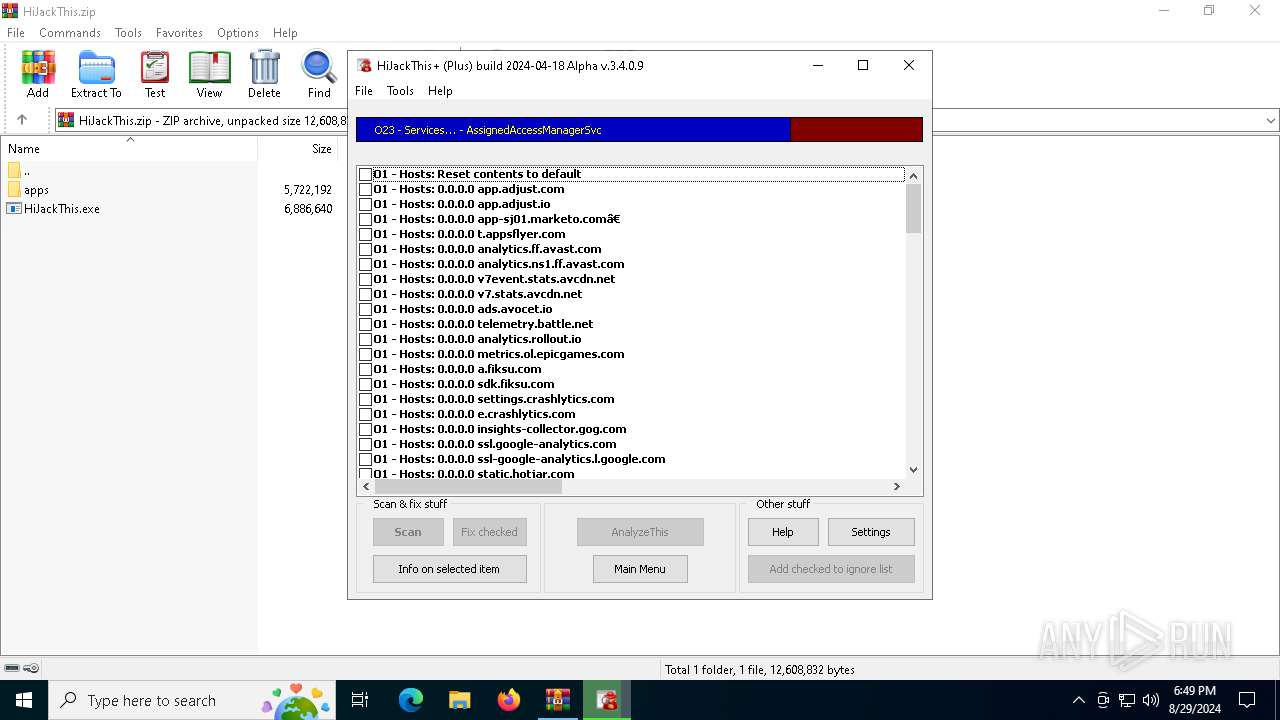
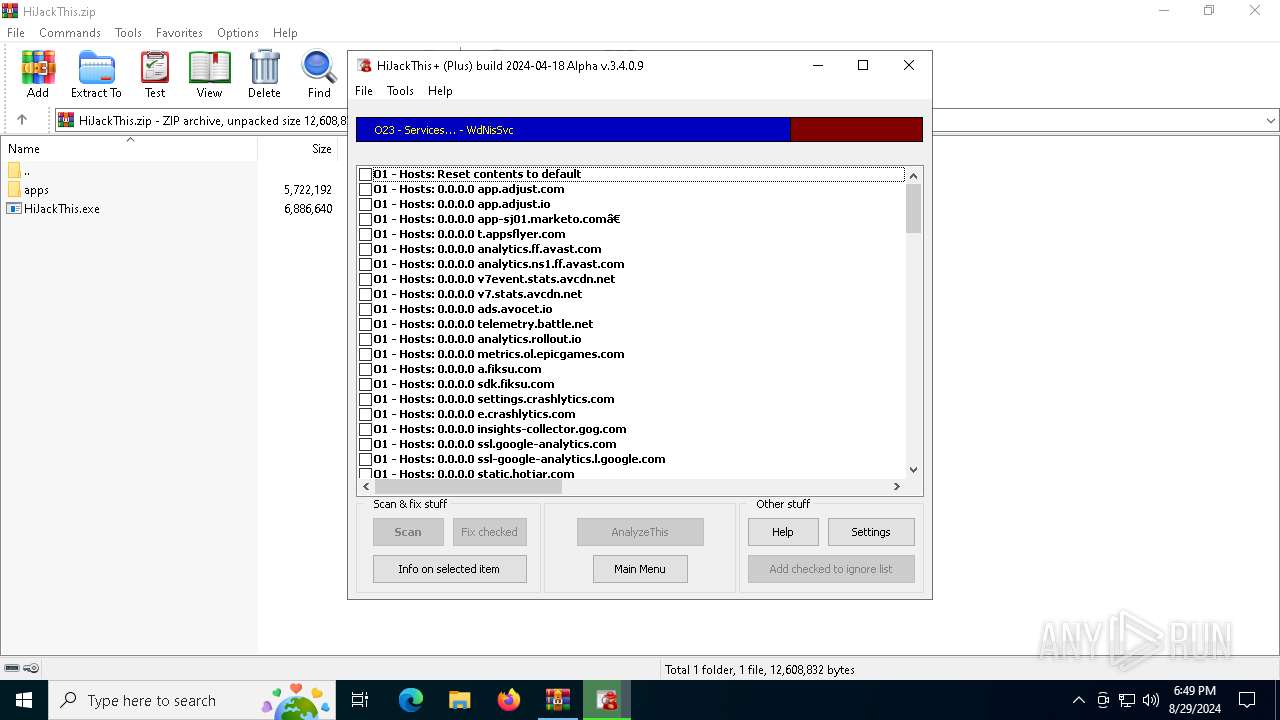
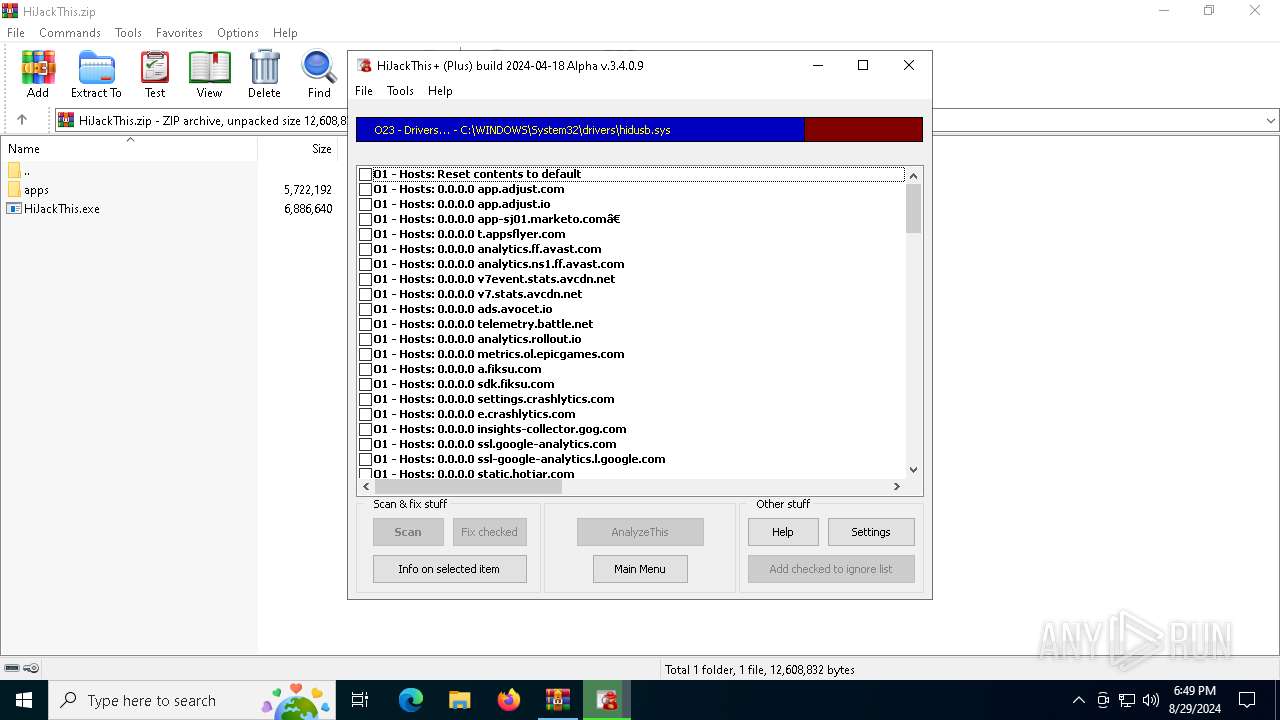
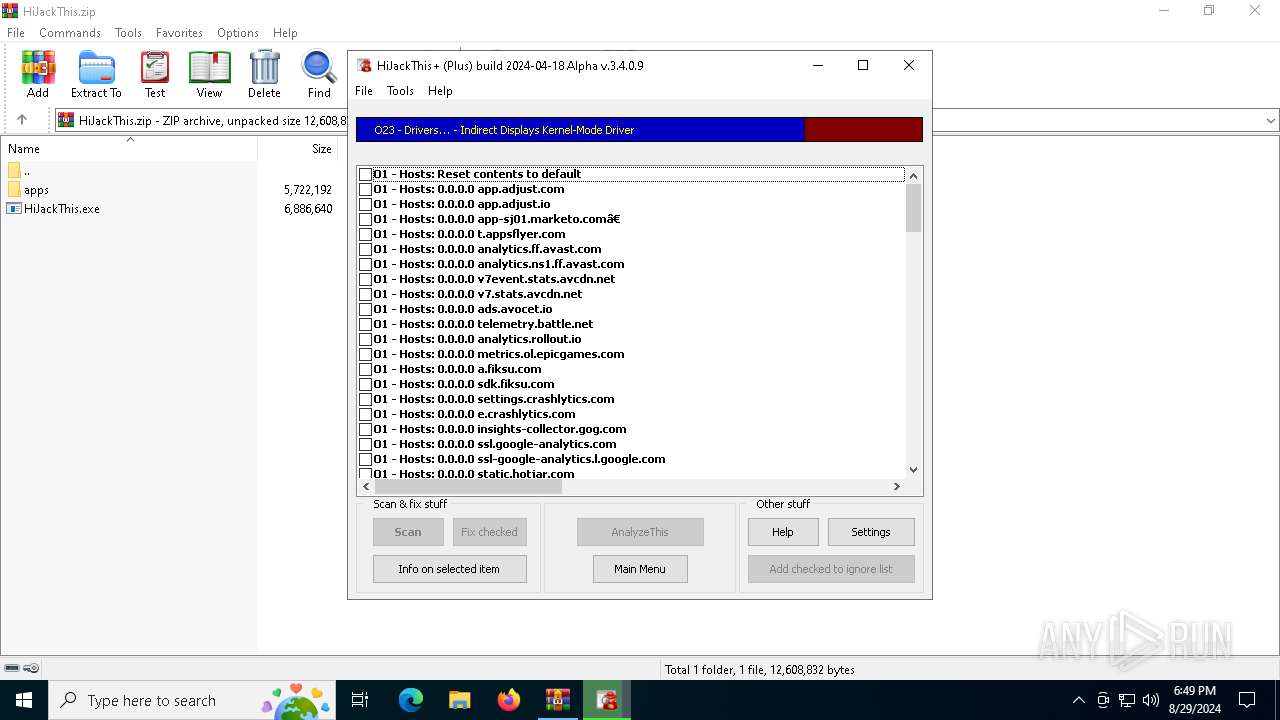
| File name: | HiJackThis.zip |
| Full analysis: | https://app.any.run/tasks/2d63c73e-6750-47f5-8380-1ae32d4129b3 |
| Verdict: | Malicious activity |
| Analysis date: | August 29, 2024, 18:46:53 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 7D8A47BF90052864F9FD3254757D95BE |
| SHA1: | DCB16B42E007AAC863FE8853A6A567DCA40CFC7B |
| SHA256: | 029E2860904A7D443E57DAADBC06C1E539D638BDF15C16EBFE1DA0068CBAED06 |
| SSDEEP: | 98304:7DQKWHXs7y+MLu3wYlVQxKuJ7jKXAbcag//+F7uPsFISZixdaPY4xT5Tq3Tsy3u7:dIgqk80hp2 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2456)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 2456)
- HiJackThis.exe (PID: 2032)
Reads the date of Windows installation
- HiJackThis.exe (PID: 2032)
The process checks if it is being run in the virtual environment
- HiJackThis.exe (PID: 2032)
Read startup parameters
- HiJackThis.exe (PID: 2032)
Adds/modifies Windows certificates
- HiJackThis.exe (PID: 2032)
Checks Windows Trust Settings
- HiJackThis.exe (PID: 2032)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 2456)
Reads product name
- HiJackThis.exe (PID: 2032)
Reads Environment values
- HiJackThis.exe (PID: 2032)
Checks supported languages
- HiJackThis.exe (PID: 2032)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2456)
Reads the machine GUID from the registry
- HiJackThis.exe (PID: 2032)
Create files in a temporary directory
- HiJackThis.exe (PID: 2032)
Reads the computer name
- HiJackThis.exe (PID: 2032)
Reads Microsoft Office registry keys
- HiJackThis.exe (PID: 2032)
Uses BITSADMIN.EXE
- HiJackThis.exe (PID: 2032)
Checks proxy server information
- HiJackThis.exe (PID: 2032)
Process checks whether UAC notifications are on
- HiJackThis.exe (PID: 2032)
Reads the software policy settings
- HiJackThis.exe (PID: 2032)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:01:28 19:59:38 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | apps/ |
Total processes
127
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2032 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2456.11719\HiJackThis.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2456.11719\HiJackThis.exe | WinRAR.exe | ||||||||||||
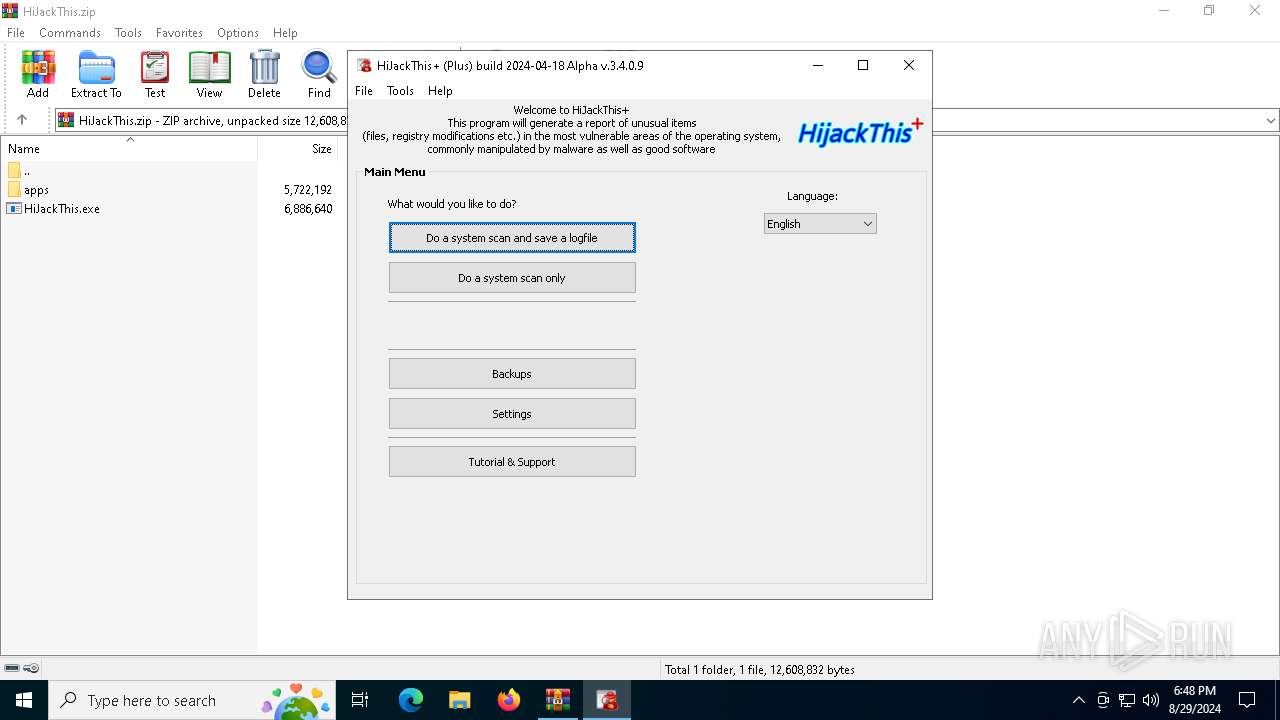
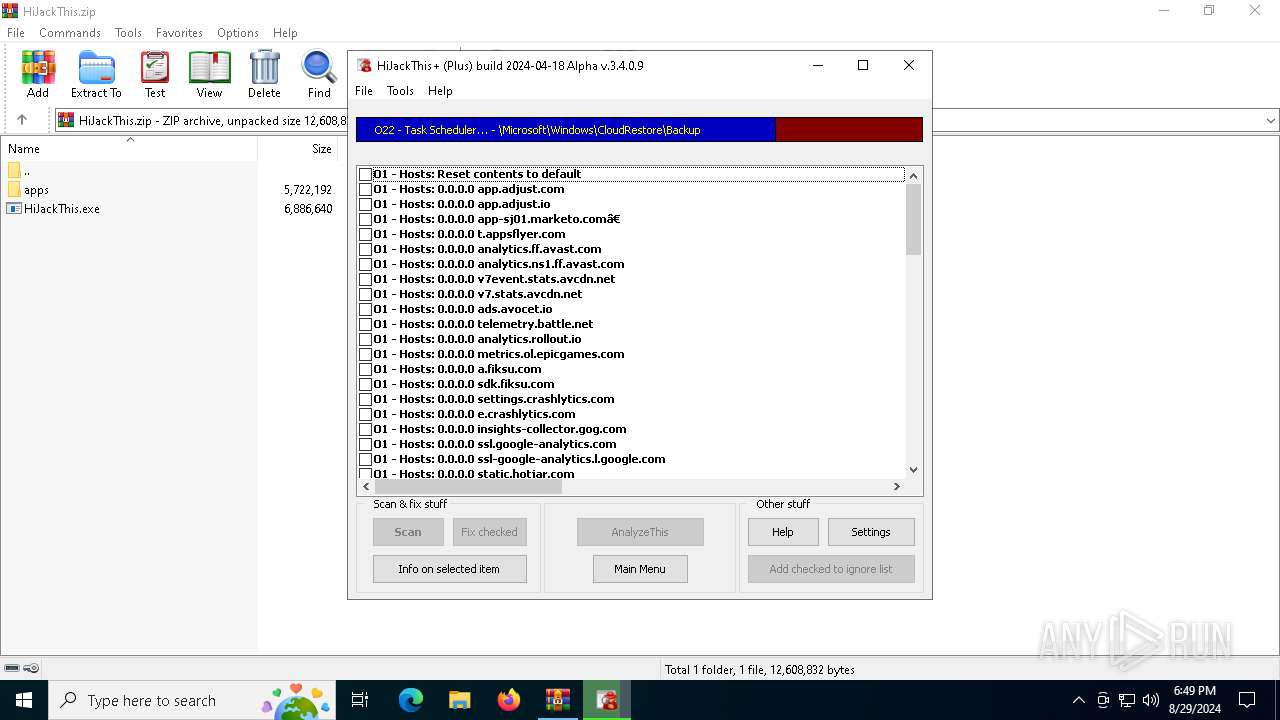
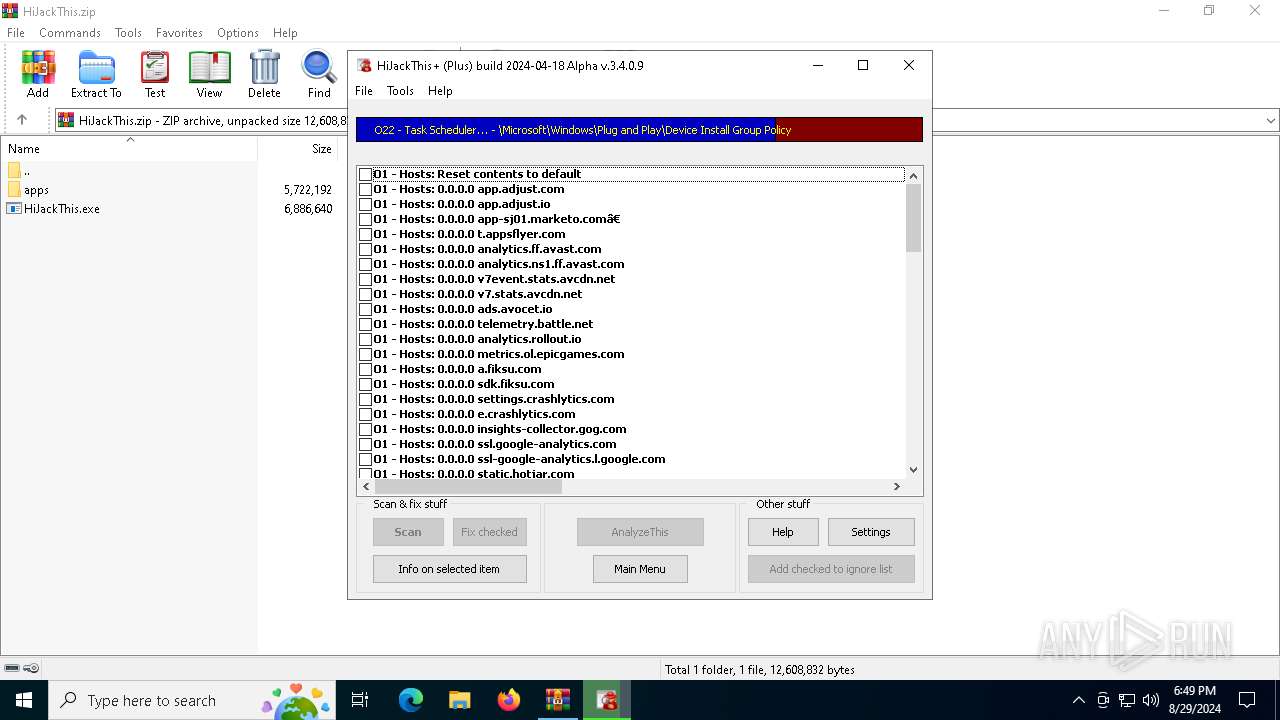
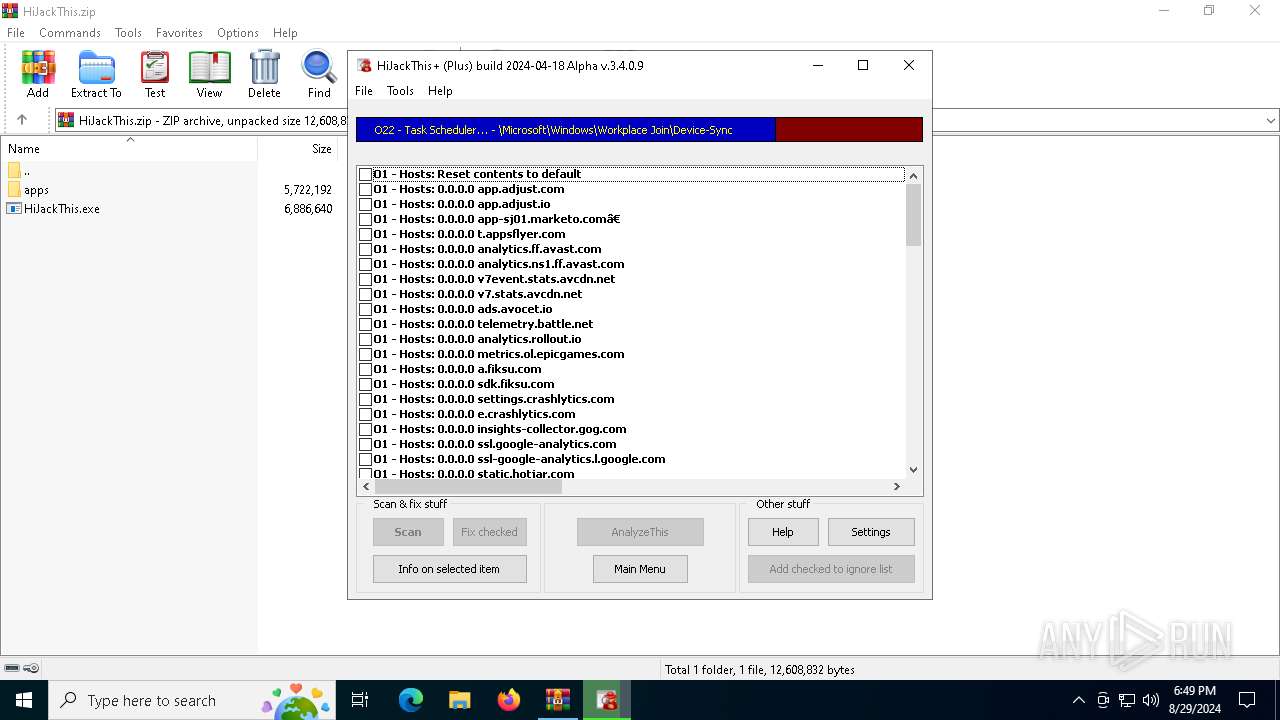
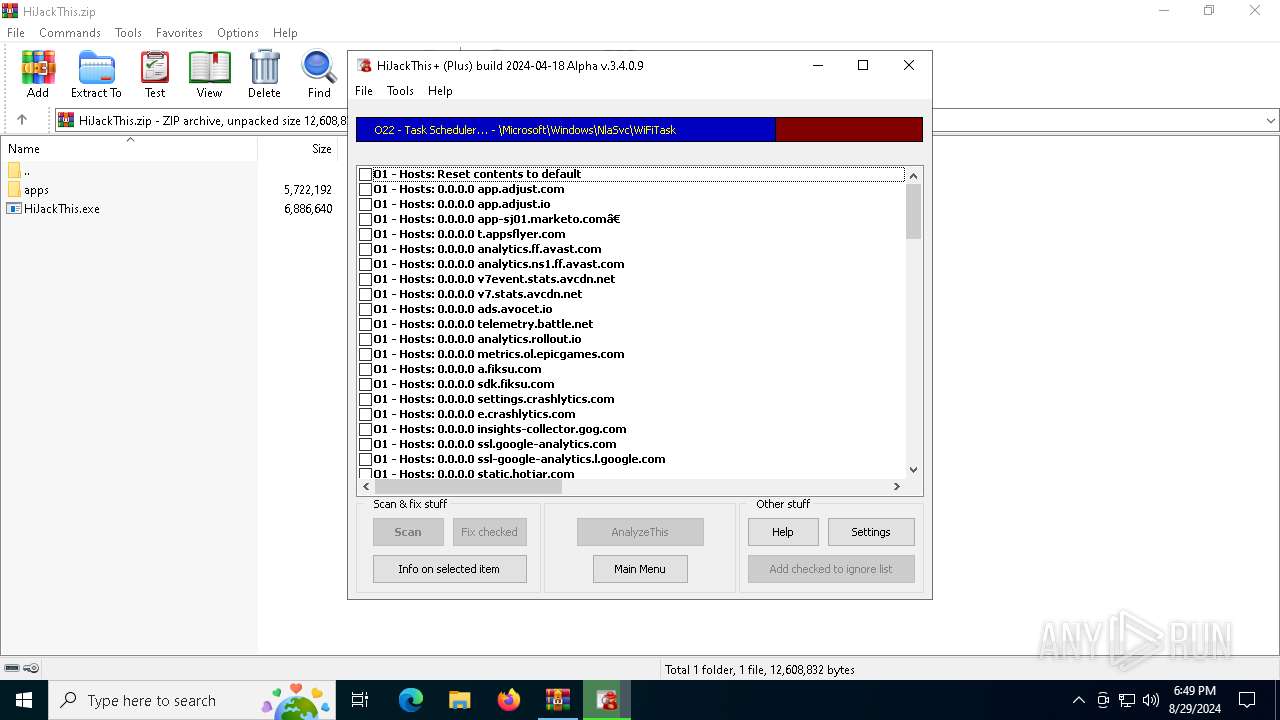
User: admin Company: Alex Dragokas & Trend Micro Inc. Integrity Level: HIGH Description: Creates a report of non-standard parameters of registry and file system for selectively removal of items related to the activities of malware and security risks Version: 3.04.0009 Modules
| |||||||||||||||
| 2456 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\HiJackThis.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6628 | "C:\WINDOWS\SysNative\bitsadmin.exe" /list /allusers /verbose | C:\Windows\System32\bitsadmin.exe | — | HiJackThis.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: BITS administration utility Exit code: 0 Version: 7.8.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6640 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | bitsadmin.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6916 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2456.11719\HiJackThis.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2456.11719\HiJackThis.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Alex Dragokas & Trend Micro Inc. Integrity Level: MEDIUM Description: Creates a report of non-standard parameters of registry and file system for selectively removal of items related to the activities of malware and security risks Exit code: 3221226540 Version: 3.04.0009 Modules
| |||||||||||||||
Total events
57 465
Read events
57 410
Write events
46
Delete events
9
Modification events
| (PID) Process: | (2456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (2456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\HiJackThis.zip | |||
| (PID) Process: | (2456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
3
Suspicious files
2
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2456 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2456.11719\HiJackThis.exe | executable | |
MD5:AA5B7F5C37EBB746D0D510D1B3182930 | SHA256:EB756CF774B337E71D4FC4642054F6AA08FFACBC97607A1EABC7089CEE3FB412 | |||
| 2032 | HiJackThis.exe | C:\Users\admin\AppData\Local\Temp\~DFB505CD23097951A2.TMP | binary | |
MD5:3211AD7257325337881B949D2F5CA163 | SHA256:80A94E357A8828BA0DC55E37C9C125C04AE99F06422A5C2514BA332FE356699C | |||
| 2032 | HiJackThis.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\37C951188967C8EB88D99893D9D191FE | binary | |
MD5:FB64A9EBEDF48D3895381D5B7D80743D | SHA256:EA21D495930AD76F267A33A0F593DBF0C7EA75E457FCAE49A29DAAD8BD920F42 | |||
| 2456 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2456.11719\apps\VBCCR17.OCX | executable | |
MD5:E7AAA82F0A491FE4CF7603038758AF41 | SHA256:B8D73BC915D8C617204979588F788F5DCD90D30DF026AFE9BDE5FE3C39E36DCC | |||
| 2456 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2456.11719\apps\abr.exe | executable | |
MD5:769F78E61DA897AEB15F3378818B97FF | SHA256:FE0B4C38E7B1CA7FFCE3D4F99D6F6E021FCC121E2BA12D4669DF1FB72B15FC13 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
15
DNS requests
6
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6124 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1356 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6124 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4324 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |