| File name: | test.exe |
| Full analysis: | https://app.any.run/tasks/98295894-34b0-4c07-a94c-f59267893c68 |
| Verdict: | Malicious activity |
| Analysis date: | April 07, 2024, 15:18:32 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines (11489) |
| MD5: | 76FDC6165DED95DCA66D8B50D121D167 |
| SHA1: | 3092278AEF2A3662CE1C76CCB43E5BB064864923 |
| SHA256: | 028A41BCE28028D7EC5BEC25CFD2BED18B81420A4E7B44E7AD529EEE65647C52 |
| SSDEEP: | 6144:9yhhFu11P4b6CyD0o0jgAN1azwwttFjbAB:9yhq11P4bS0M+1ak/ |
MALICIOUS
Drops the executable file immediately after the start
- csc.exe (PID: 1976)
- csc.exe (PID: 3508)
- csc.exe (PID: 3912)
Starts Visual C# compiler
- sdiagnhost.exe (PID: 3164)
SUSPICIOUS
Creates file in the systems drive root
- ntvdm.exe (PID: 3092)
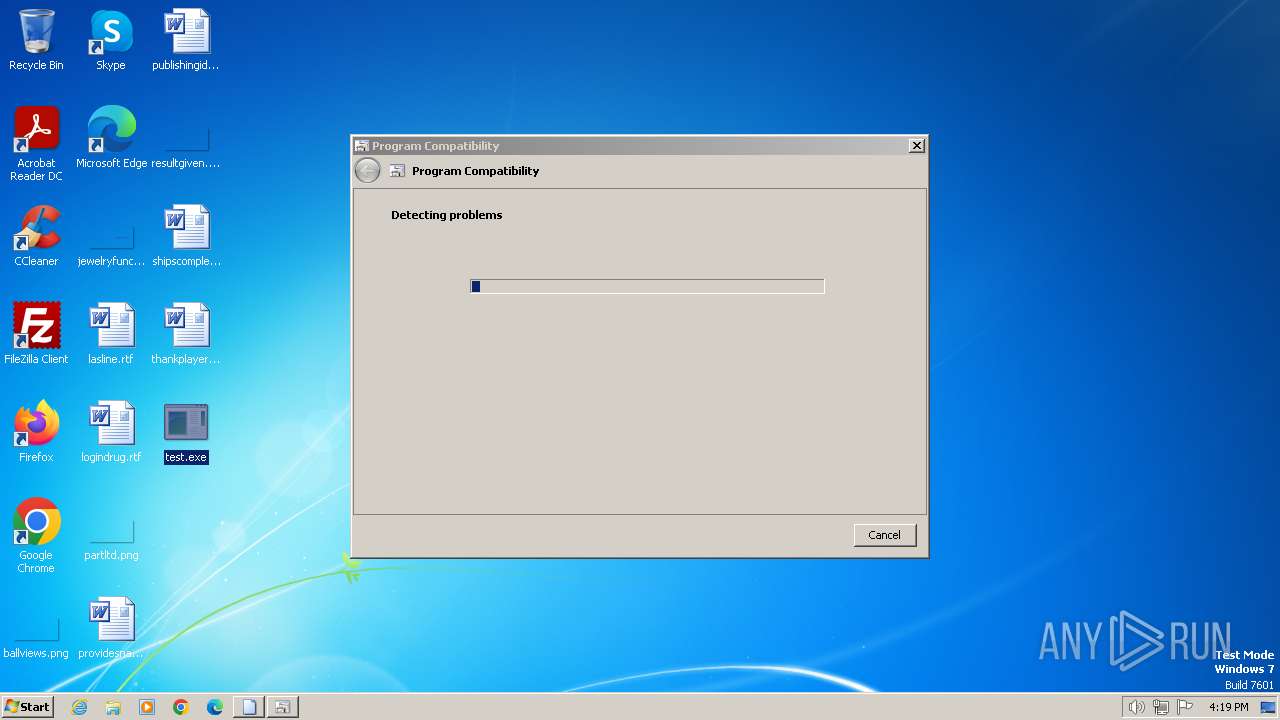
Probably uses Microsoft diagnostics tool to execute malicious payload
- pcwrun.exe (PID: 2756)
Reads the Internet Settings
- sdiagnhost.exe (PID: 3164)
Uses .NET C# to load dll
- sdiagnhost.exe (PID: 3164)
INFO
Manual execution by a user
- pcwrun.exe (PID: 2756)
- ntvdm.exe (PID: 3092)
- notepad++.exe (PID: 3400)
Create files in a temporary directory
- pcwrun.exe (PID: 2756)
- cvtres.exe (PID: 2156)
- sdiagnhost.exe (PID: 3164)
- csc.exe (PID: 1976)
- csc.exe (PID: 3508)
- cvtres.exe (PID: 3308)
- csc.exe (PID: 3912)
- cvtres.exe (PID: 3776)
- msdt.exe (PID: 3488)
Drops the executable file immediately after the start
- msdt.exe (PID: 3488)
Reads the machine GUID from the registry
- csc.exe (PID: 1976)
- csc.exe (PID: 3508)
- cvtres.exe (PID: 2156)
- cvtres.exe (PID: 3308)
- csc.exe (PID: 3912)
- cvtres.exe (PID: 3776)
Reads security settings of Internet Explorer
- sdiagnhost.exe (PID: 3164)
- msdt.exe (PID: 3488)
Checks supported languages
- cvtres.exe (PID: 2156)
- cvtres.exe (PID: 3776)
- csc.exe (PID: 3508)
- cvtres.exe (PID: 3308)
- csc.exe (PID: 3912)
- csc.exe (PID: 1976)
Reads the software policy settings
- msdt.exe (PID: 3488)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .bs/bin | | | PrintFox (C64) bitmap (100) |
|---|
Total processes
50
Monitored processes
12
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1976 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\eqejupnu.cmdline" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe | sdiagnhost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 8.0.50727.5483 (Win7SP1GDR.050727-5400) Modules
| |||||||||||||||
| 2120 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL "C:\Users\admin\AppData\Local\Temp\test.exe.bs/bin" | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2156 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES8122.tmp" "c:\Users\admin\AppData\Local\Temp\CSC8121.tmp" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 8.00.50727.5003 (Win7SP1GDR.050727-5400) Modules
| |||||||||||||||
| 2756 | C:\Windows\system32\pcwrun.exe "C:\Users\admin\Desktop\test.exe" | C:\Windows\System32\pcwrun.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Program Compatibility Troubleshooter Invoker Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3092 | "C:\Windows\system32\ntvdm.exe" -i1 | C:\Windows\System32\ntvdm.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: NTVDM.EXE Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3164 | C:\Windows\System32\sdiagnhost.exe -Embedding | C:\Windows\System32\sdiagnhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Scripted Diagnostics Native Host Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3308 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES824B.tmp" "c:\Users\admin\AppData\Local\Temp\CSC823B.tmp" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 8.00.50727.5003 (Win7SP1GDR.050727-5400) Modules
| |||||||||||||||
| 3400 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Desktop\test.exe" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Version: 7.91 Modules
| |||||||||||||||
| 3488 | C:\Windows\System32\msdt.exe -path C:\Windows\diagnostics\index\PCWDiagnostic.xml -af C:\Users\admin\AppData\Local\Temp\PCW7D0B.xml /skip TRUE | C:\Windows\System32\msdt.exe | — | pcwrun.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Diagnostics Troubleshooting Wizard Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3508 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\oouc0hit.cmdline" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe | sdiagnhost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 8.0.50727.5483 (Win7SP1GDR.050727-5400) Modules
| |||||||||||||||
Total events
6 383
Read events
6 347
Write events
36
Delete events
0
Modification events
| (PID) Process: | (3488) msdt.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3164) sdiagnhost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3164) sdiagnhost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3164) sdiagnhost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3164) sdiagnhost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3400) notepad++.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
5
Suspicious files
9
Text files
18
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3092 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scs6491.tmp | text | |
MD5:— | SHA256:— | |||
| 3092 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scs64A2.tmp | text | |
MD5:— | SHA256:— | |||
| 2756 | pcwrun.exe | C:\Users\admin\AppData\Local\Temp\PCW7D0B.xml | xml | |
MD5:— | SHA256:— | |||
| 3488 | msdt.exe | C:\Users\admin\AppData\Local\Temp\SDIAG_eac35e95-0b83-48d3-9e83-0a830e032552\DiagPackage.diagpkg | html | |
MD5:— | SHA256:— | |||
| 3488 | msdt.exe | C:\Users\admin\AppData\Local\Temp\SDIAG_eac35e95-0b83-48d3-9e83-0a830e032552\DiagPackage.dll | executable | |
MD5:— | SHA256:— | |||
| 3488 | msdt.exe | C:\Users\admin\AppData\Local\Temp\SDIAG_eac35e95-0b83-48d3-9e83-0a830e032552\RS_ProgramCompatibilityWizard.ps1 | text | |
MD5:— | SHA256:— | |||
| 3488 | msdt.exe | C:\Users\admin\AppData\Local\Temp\SDIAG_eac35e95-0b83-48d3-9e83-0a830e032552\TS_ProgramCompatibilityWizard.ps1 | text | |
MD5:— | SHA256:— | |||
| 3488 | msdt.exe | C:\Users\admin\AppData\Local\Temp\SDIAG_eac35e95-0b83-48d3-9e83-0a830e032552\VF_ProgramCompatibilityWizard.ps1 | text | |
MD5:— | SHA256:— | |||
| 3488 | msdt.exe | C:\Users\admin\AppData\Local\Temp\SDIAG_eac35e95-0b83-48d3-9e83-0a830e032552\en-US\CL_LocalizationData.psd1 | text | |
MD5:— | SHA256:— | |||
| 3488 | msdt.exe | C:\Users\admin\AppData\Local\Temp\SDIAG_eac35e95-0b83-48d3-9e83-0a830e032552\en-US\DiagPackage.dll.mui | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
DNS requests
Threats
Process | Message |
|---|---|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|