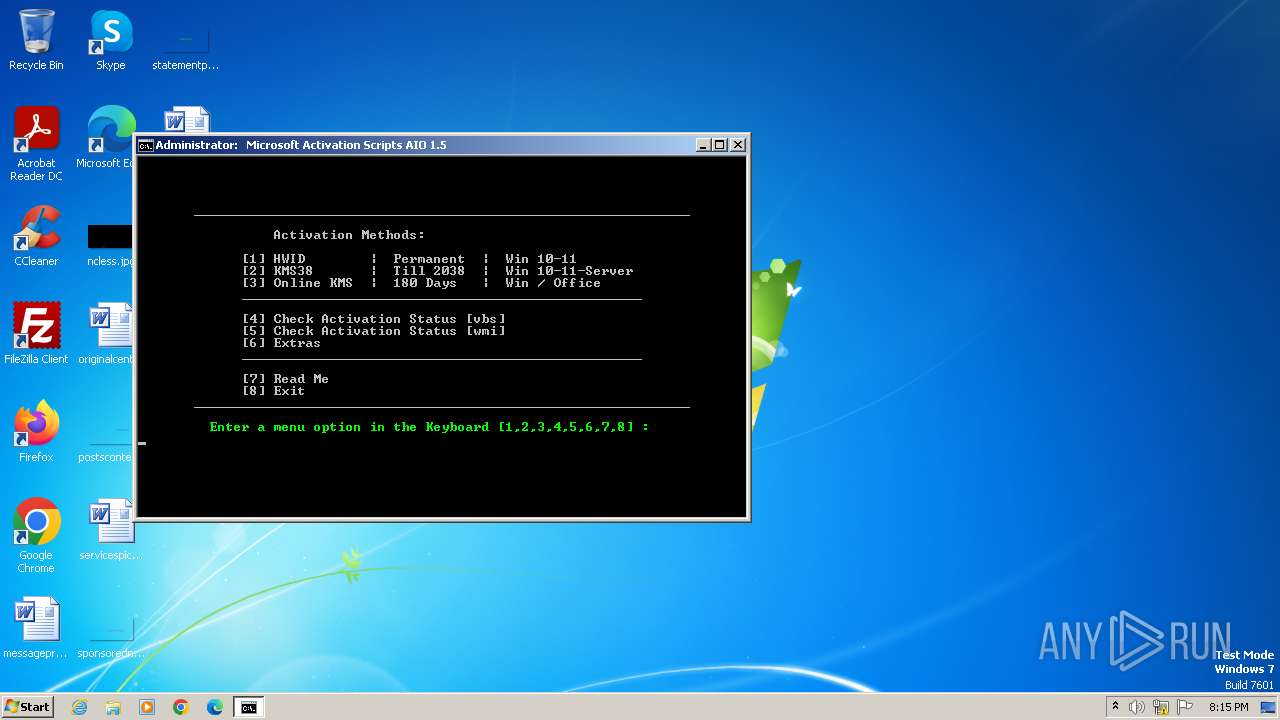
| File name: | MAS_1.5_AIO_CRC32_21D20776.cmd |
| Full analysis: | https://app.any.run/tasks/36fd80b4-9988-4a66-bc84-76008af810e0 |
| Verdict: | Malicious activity |
| Analysis date: | November 24, 2023, 20:15:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines, with CRLF line terminators |
| MD5: | A0F1C3AA3CD2380B669F77F3B8BAC024 |
| SHA1: | 4D11828CAC7728E25F6E2D1E76553D779D4A33FF |
| SHA256: | 0271E8F4113A31D688668D0E3BC7D06C525CF082930A8930273D5D9A69CE981D |
| SSDEEP: | 24576:xI3OiPLyZpRvavXZGkRaOGTOzdutMO+pixuOSOihJv0bXuFH9:SNj6qbGTOXqSfLvH9 |
MALICIOUS
Starts Visual C# compiler
- powershell.exe (PID: 2316)
Drops the executable file immediately after the start
- csc.exe (PID: 2764)
Starts NET.EXE for service management
- net.exe (PID: 1696)
- cmd.exe (PID: 2776)
- net.exe (PID: 3824)
- net.exe (PID: 2416)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 948)
- cmd.exe (PID: 2776)
Executing commands from ".cmd" file
- cmd.exe (PID: 948)
- powershell.exe (PID: 3320)
- cmd.exe (PID: 2776)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 948)
- powershell.exe (PID: 3320)
- cmd.exe (PID: 2776)
Powershell version downgrade attack
- powershell.exe (PID: 3320)
- powershell.exe (PID: 2316)
- powershell.exe (PID: 4080)
- powershell.exe (PID: 1276)
Application launched itself
- cmd.exe (PID: 948)
- cmd.exe (PID: 2776)
Reads the Internet Settings
- powershell.exe (PID: 3320)
- WMIC.exe (PID: 3328)
- WMIC.exe (PID: 2292)
- WMIC.exe (PID: 3940)
- WMIC.exe (PID: 2168)
- WMIC.exe (PID: 3008)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 2776)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 2776)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 2776)
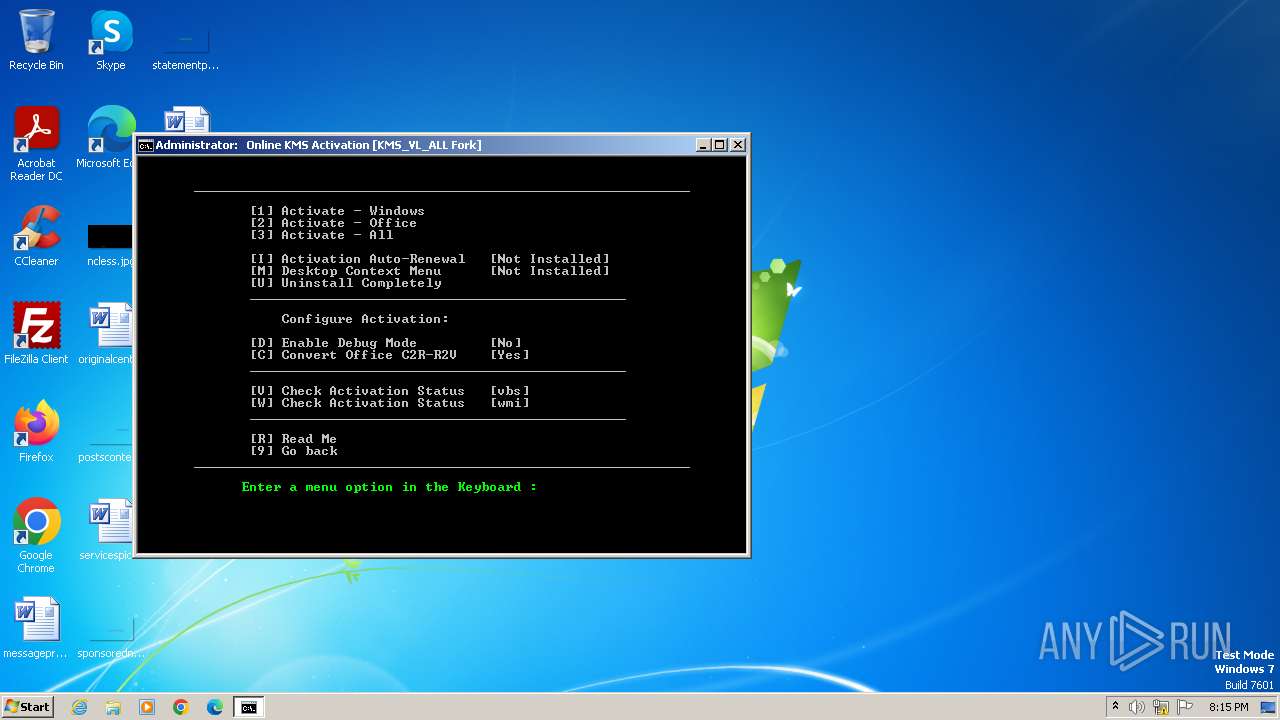
Uses .NET C# to load dll
- powershell.exe (PID: 2316)
Starts SC.EXE for service management
- cmd.exe (PID: 2776)
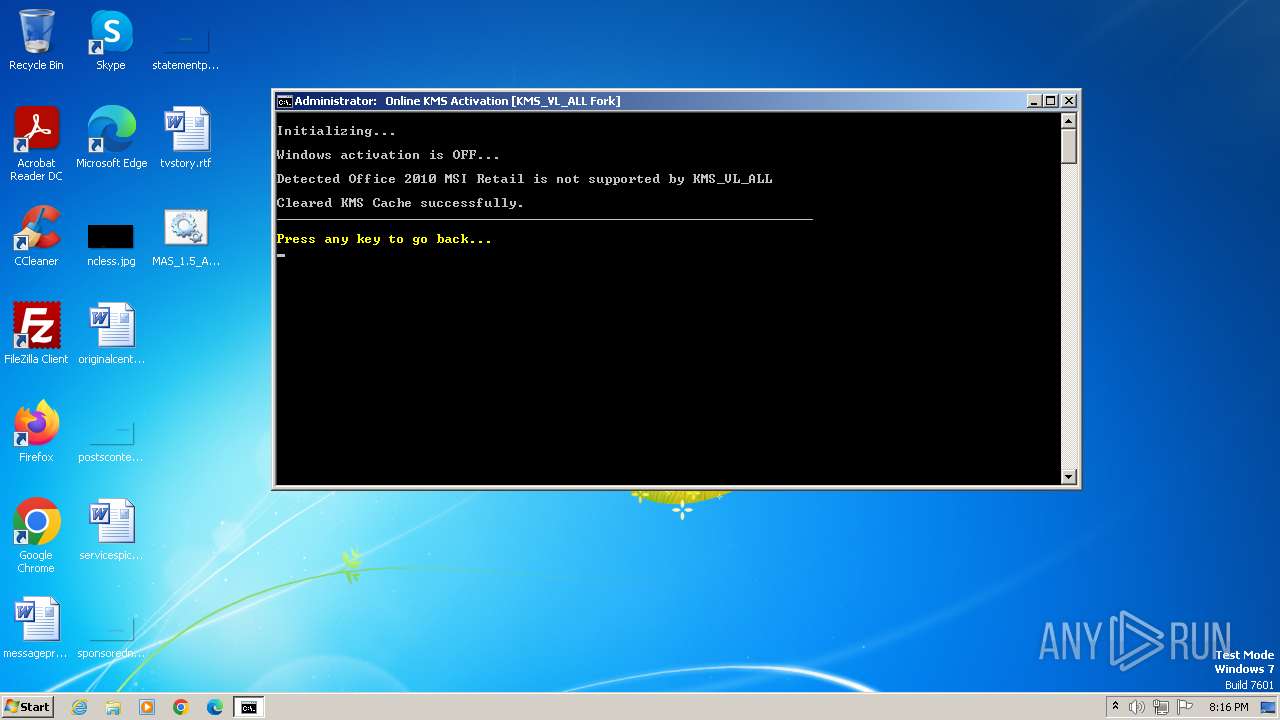
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 2776)
Uses WMIC.EXE to obtain service application data
- cmd.exe (PID: 2004)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 2776)
INFO
Checks operating system version
- cmd.exe (PID: 948)
- cmd.exe (PID: 2776)
Checks supported languages
- csc.exe (PID: 2764)
- cvtres.exe (PID: 3344)
- mode.com (PID: 2332)
- mode.com (PID: 4020)
- wmpnscfg.exe (PID: 3464)
- mode.com (PID: 3448)
Reads the machine GUID from the registry
- csc.exe (PID: 2764)
- cvtres.exe (PID: 3344)
- wmpnscfg.exe (PID: 3464)
Create files in a temporary directory
- csc.exe (PID: 2764)
- cvtres.exe (PID: 3344)
Manual execution by a user
- wmpnscfg.exe (PID: 3464)
Reads Microsoft Office registry keys
- reg.exe (PID: 1752)
Reads the computer name
- wmpnscfg.exe (PID: 3464)
Drops the executable file immediately after the start
- expand.exe (PID: 2444)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
184
Monitored processes
138
Malicious processes
6
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 304 | sc query osppsvc | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 552 | C:\Windows\system32\cmd.exe /c "prompt $H&for %B in (1) do rem" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 824 | sc query ClickToRunSvc | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 1060 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 900 | reg query "HKLM\SOFTWARE\Microsoft\Windows Script Host\Settings" /v Enabled | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 944 | find /i "C:\Users\admin\AppData\Local\Temp" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 948 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\Desktop\MAS_1.5_AIO_CRC32_21D20776.cmd" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 952 | find /i "STOPPED" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1028 | findstr /a:07 /f:`.txt "." | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1276 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe "$f=[io.file]::ReadAllText('C:\Users\admin\Desktop\MAS_1.5_AIO_CRC32_21D20776.cmd') -split \":kacttxt\:.*`r`n\"; [io.file]::WriteAllText('C:\Windows\Temp\__MAS\Activate.cmd',$f[1].Trim(),[System.Text.Encoding]::ASCII);" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1496 | C:\Windows\system32\cmd.exe /c ver | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
7 498
Read events
7 267
Write events
224
Delete events
7
Modification events
| (PID) Process: | (3320) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3320) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3320) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3320) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3320) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2316) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1276) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (4080) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3464) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{7C5CECB3-25C3-4CB9-A096-285AD2187767}\{B308663B-A653-4799-A7ED-37CCA946D59F} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3464) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{7C5CECB3-25C3-4CB9-A096-285AD2187767} |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
5
Suspicious files
18
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2764 | csc.exe | C:\Users\admin\AppData\Local\Temp\jdg9s2tl.pdb | binary | |
MD5:BA5D06355FF99DFAE088FC4E8769FBAD | SHA256:F668036840E5A096692420C3250D23B5112E2CF3E6F4002E1176F2712F86A90D | |||
| 2316 | powershell.exe | C:\Users\admin\AppData\Local\Temp\jdg9s2tl.0.cs | text | |
MD5:047F0CF592670E8FCA358F12E4CD5A89 | SHA256:32E77D9085AD9EA0FD1EB5A9556E29CB42F5D3016CCF9853F3C39D358F479978 | |||
| 3320 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:16F6D260068B85896C0EBB2E1B2A60D1 | SHA256:6E3B1EF1FB4736A9BF18FADF8E42935CC5053478B6F403A38EFBA8500E819984 | |||
| 2316 | powershell.exe | C:\Users\admin\AppData\Local\Temp\jdg9s2tl.cmdline | text | |
MD5:318BCFE1D52D98C9F9D9E9A40A15E9F1 | SHA256:D4E3670945811C62C7AC9C9FA13665BA42F39566C776DAC7C9800F17120BDF21 | |||
| 2776 | cmd.exe | C:\Windows\Temp\' | binary | |
MD5:5058F1AF8388633F609CADB75A75DC9D | SHA256:— | |||
| 2316 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:16F6D260068B85896C0EBB2E1B2A60D1 | SHA256:6E3B1EF1FB4736A9BF18FADF8E42935CC5053478B6F403A38EFBA8500E819984 | |||
| 2776 | cmd.exe | C:\Windows\Temp\`.txt | text | |
MD5:ACBDFFB9A78518ABA6865C2175A4DFAF | SHA256:0DA31B6041199F00BE31703C3A6E180F045E6DD87B52539AC6F19B1EF049B0A5 | |||
| 2316 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF1c01ad.TMP | binary | |
MD5:16F6D260068B85896C0EBB2E1B2A60D1 | SHA256:6E3B1EF1FB4736A9BF18FADF8E42935CC5053478B6F403A38EFBA8500E819984 | |||
| 2764 | csc.exe | C:\Users\admin\AppData\Local\Temp\jdg9s2tl.dll | executable | |
MD5:B2FE277714C0904EDD413F4F0CD49A05 | SHA256:1BBB5468F73EBEC12BF634C478F8E9FAFCCD2A8DA2FD6B98FF8C1FF1F99E3BBB | |||
| 2764 | csc.exe | C:\Users\admin\AppData\Local\Temp\CSC3D0.tmp | binary | |
MD5:1D6A2B8A375E6F262500EEA7EAE8DD94 | SHA256:1305F19A3698424F36CEE0E8C76F8981C467DEFAEF3BF1ECF2EEE2571ECF13F9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
5
DNS requests
3
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1080 | svchost.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?08208ad102fb932b | unknown | compressed | 4.66 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1080 | svchost.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
kms.kuretru.com |
| unknown |
kms.moeyuuko.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
Threats
Process | Message |
|---|---|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|