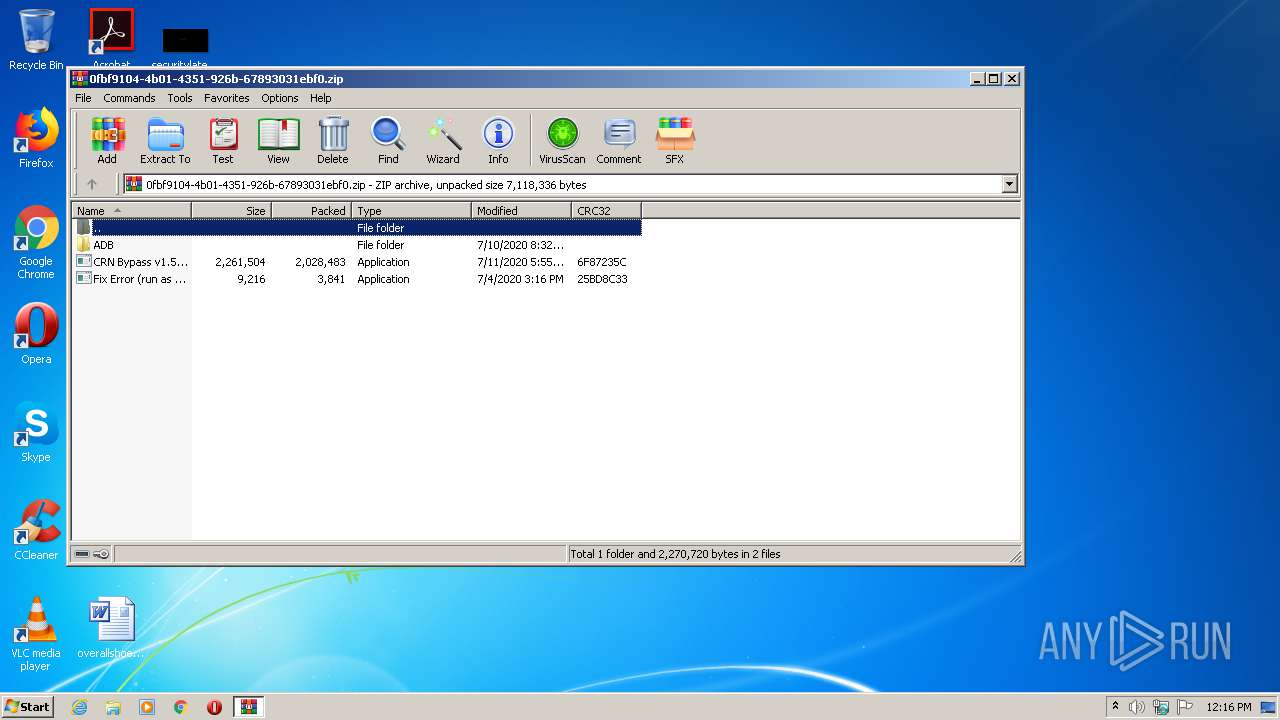
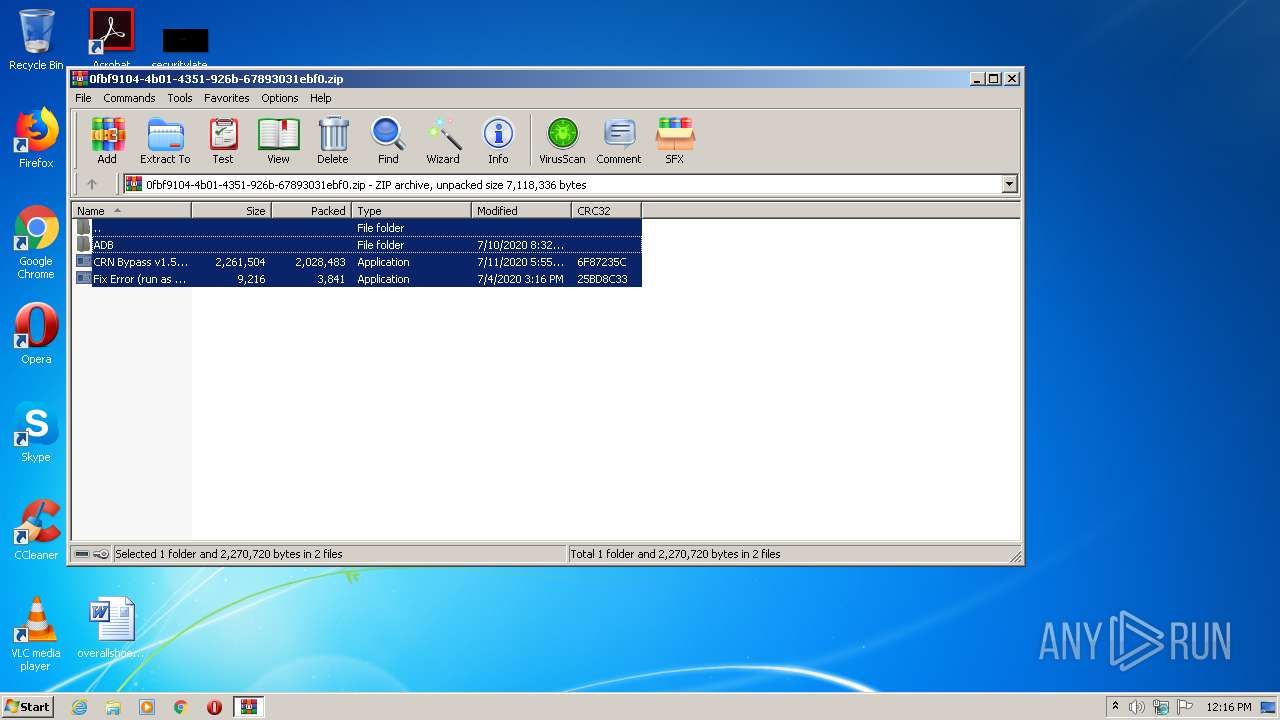
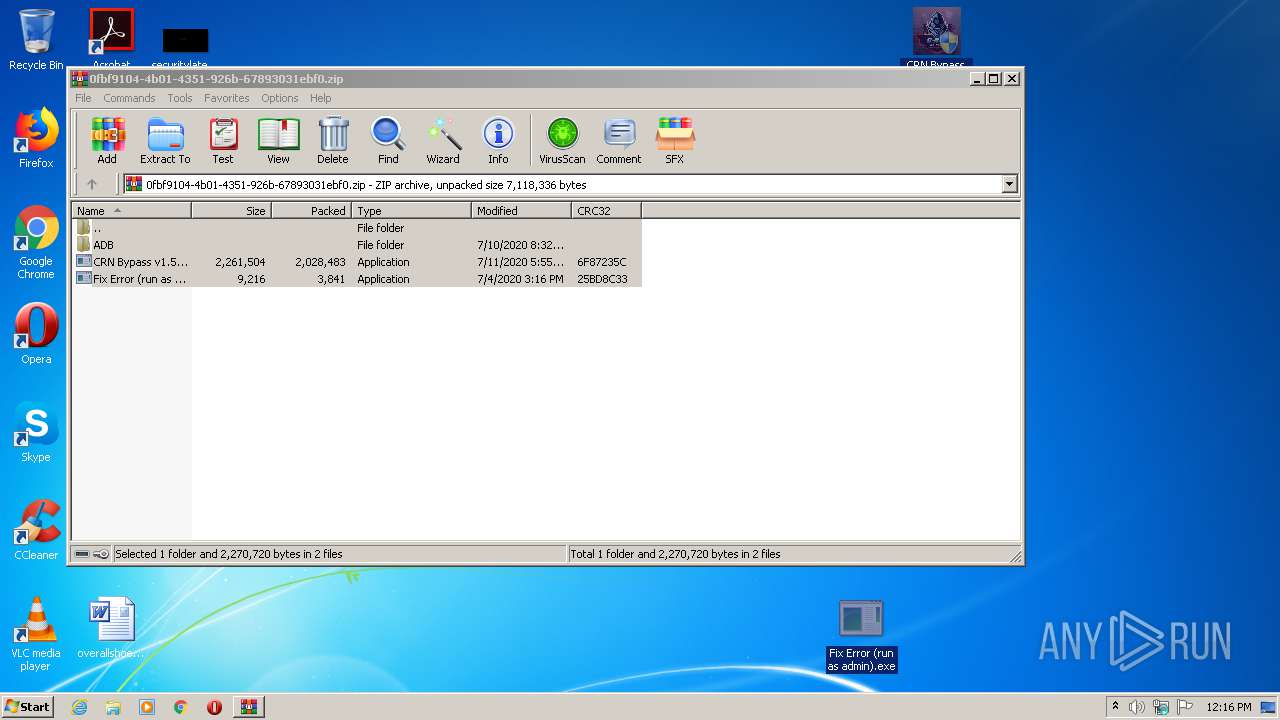
| download: | CRN%20Bypass%20v1.5.1.sp.zip |
| Full analysis: | https://app.any.run/tasks/31bc3757-f1f0-4e17-9b1a-1cda7c8c49ee |
| Verdict: | Malicious activity |
| Analysis date: | July 12, 2020, 11:16:20 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | 01A04429C9956B05999C891BABF16599 |
| SHA1: | F4118336FCD8BDF758D8518D6E24E97E873EE171 |
| SHA256: | 02633F7FA5985E0F05CF4263C5071BF920AEA3926727926073C6C4BBBBB18831 |
| SSDEEP: | 98304:/gE26D/OD9PEDs/CM2KI9rFDQBne+jzXQBA4I8vCvCmuv+8:/g0D/ODVEDsF2lrFDwnhUM5vCms |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3604)
Application was dropped or rewritten from another process
- CRN Bypass v1.5.1.sp.exe (PID: 3800)
- CRN Bypass v1.5.1.sp.exe (PID: 1832)
Changes settings of System certificates
- CRN Bypass v1.5.1.sp.exe (PID: 1832)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 544)
Reads internet explorer settings
- CRN Bypass v1.5.1.sp.exe (PID: 1832)
Reads Internet Cache Settings
- CRN Bypass v1.5.1.sp.exe (PID: 1832)
Adds / modifies Windows certificates
- CRN Bypass v1.5.1.sp.exe (PID: 1832)
INFO
Manual execution by user
- CRN Bypass v1.5.1.sp.exe (PID: 3800)
- CRN Bypass v1.5.1.sp.exe (PID: 1832)
Reads the hosts file
- CRN Bypass v1.5.1.sp.exe (PID: 1832)
Reads settings of System Certificates
- CRN Bypass v1.5.1.sp.exe (PID: 1832)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2020:07:11 02:32:20 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | ADB/ |
Total processes
67
Monitored processes
18
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 544 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\0fbf9104-4b01-4351-926b-67893031ebf0.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 592 | "C:\Windows\System32\arp.exe" -a | C:\Windows\System32\arp.exe | — | CRN Bypass v1.5.1.sp.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Arp Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 788 | "C:\Windows\System32\arp.exe" -a | C:\Windows\System32\arp.exe | — | CRN Bypass v1.5.1.sp.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Arp Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 880 | "C:\Windows\System32\arp.exe" -a | C:\Windows\System32\arp.exe | — | CRN Bypass v1.5.1.sp.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Arp Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 988 | "C:\Windows\System32\arp.exe" -a | C:\Windows\System32\arp.exe | — | CRN Bypass v1.5.1.sp.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Arp Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1508 | "C:\Windows\System32\arp.exe" -a | C:\Windows\System32\arp.exe | — | CRN Bypass v1.5.1.sp.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Arp Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1732 | "C:\Windows\System32\arp.exe" -a | C:\Windows\System32\arp.exe | — | CRN Bypass v1.5.1.sp.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Arp Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
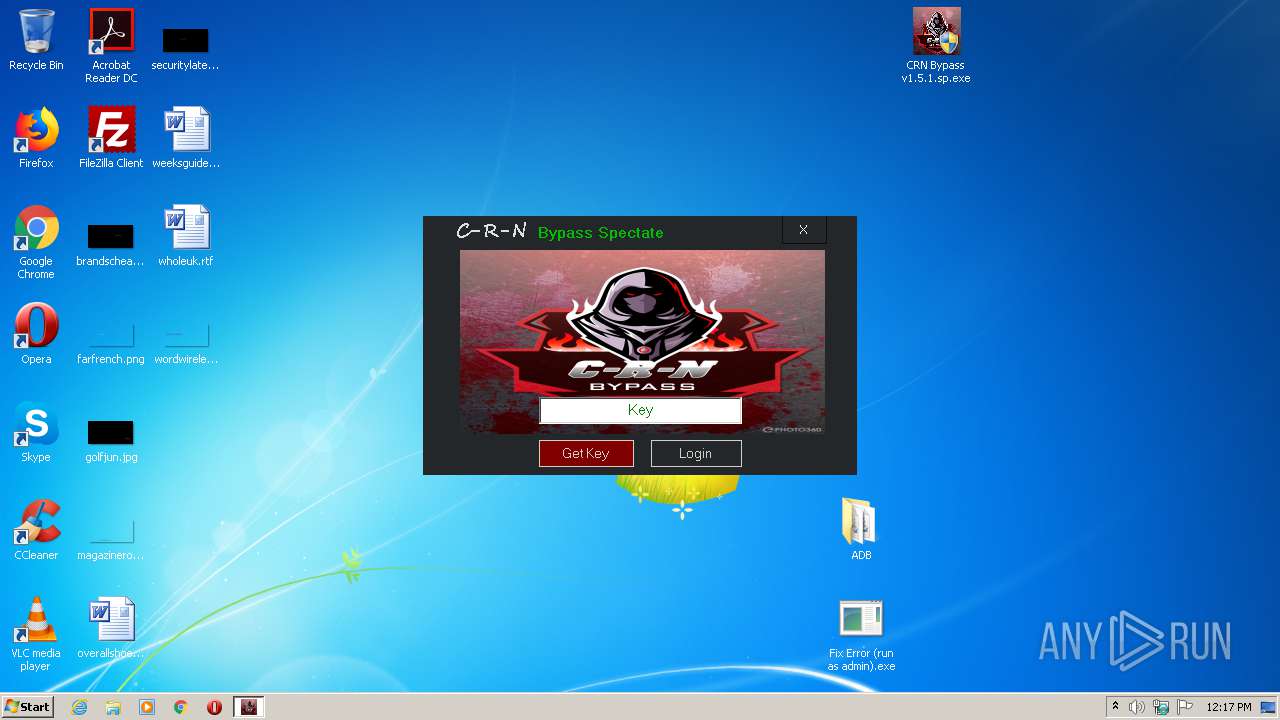
| 1832 | "C:\Users\admin\Desktop\CRN Bypass v1.5.1.sp.exe" | C:\Users\admin\Desktop\CRN Bypass v1.5.1.sp.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: CRN Team Exit code: 0 Version: 1.5.0.0 Modules
| |||||||||||||||
| 1856 | "C:\Windows\System32\arp.exe" -a | C:\Windows\System32\arp.exe | — | CRN Bypass v1.5.1.sp.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Arp Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2488 | "C:\Windows\System32\arp.exe" -a | C:\Windows\System32\arp.exe | — | CRN Bypass v1.5.1.sp.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Arp Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 277
Read events
1 039
Write events
1 238
Delete events
0
Modification events
| (PID) Process: | (544) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (544) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (544) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (544) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\NetworkExplorer.dll,-1 |
Value: Network | |||
| (PID) Process: | (544) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\0fbf9104-4b01-4351-926b-67893031ebf0.zip | |||
| (PID) Process: | (544) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (544) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (544) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (544) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (544) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
Executable files
5
Suspicious files
0
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 544 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa544.44550\CRN Bypass v1.5.1.sp.exe | executable | |
MD5:— | SHA256:— | |||
| 544 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa544.44550\Fix Error (run as admin).exe | executable | |
MD5:— | SHA256:— | |||
| 1832 | CRN Bypass v1.5.1.sp.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\thongbao[1].txt | text | |
MD5:— | SHA256:— | |||
| 544 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa544.44550\ADB\AdbWinUsbApi.dll | executable | |
MD5:0E24119DAF1909E398FA1850B6112077 | SHA256:25207C506D29C4E8DCEB61B4BD50E8669BA26012988A43FBF26A890B1E60FC97 | |||
| 544 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa544.44550\ADB\adb.exe | executable | |
MD5:94226EA671D068461171EC790197ADB9 | SHA256:FBB96C5B47F7166C70B6790ACC01CF19FE9CCF17CAD77615CDFE2BB06BEA2330 | |||
| 544 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa544.44550\ADB\AdbWinApi.dll | executable | |
MD5:ED5A809DC0024D83CBAB4FB9933D598D | SHA256:D60103A5E99BC9888F786EE916F5D6E45493C3247972CB053833803DE7E95CF9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
2
DNS requests
2
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1832 | CRN Bypass v1.5.1.sp.exe | GET | 200 | 153.92.6.135:80 | http://filesgame.xyz/Ldbypass/thongbao.txt | US | text | 181 b | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1832 | CRN Bypass v1.5.1.sp.exe | 104.24.111.151:443 | api.auth.gg | Cloudflare Inc | US | shared |
1832 | CRN Bypass v1.5.1.sp.exe | 153.92.6.135:80 | filesgame.xyz | Hostinger International Limited | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.auth.gg |
| whitelisted |
filesgame.xyz |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1832 | CRN Bypass v1.5.1.sp.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |