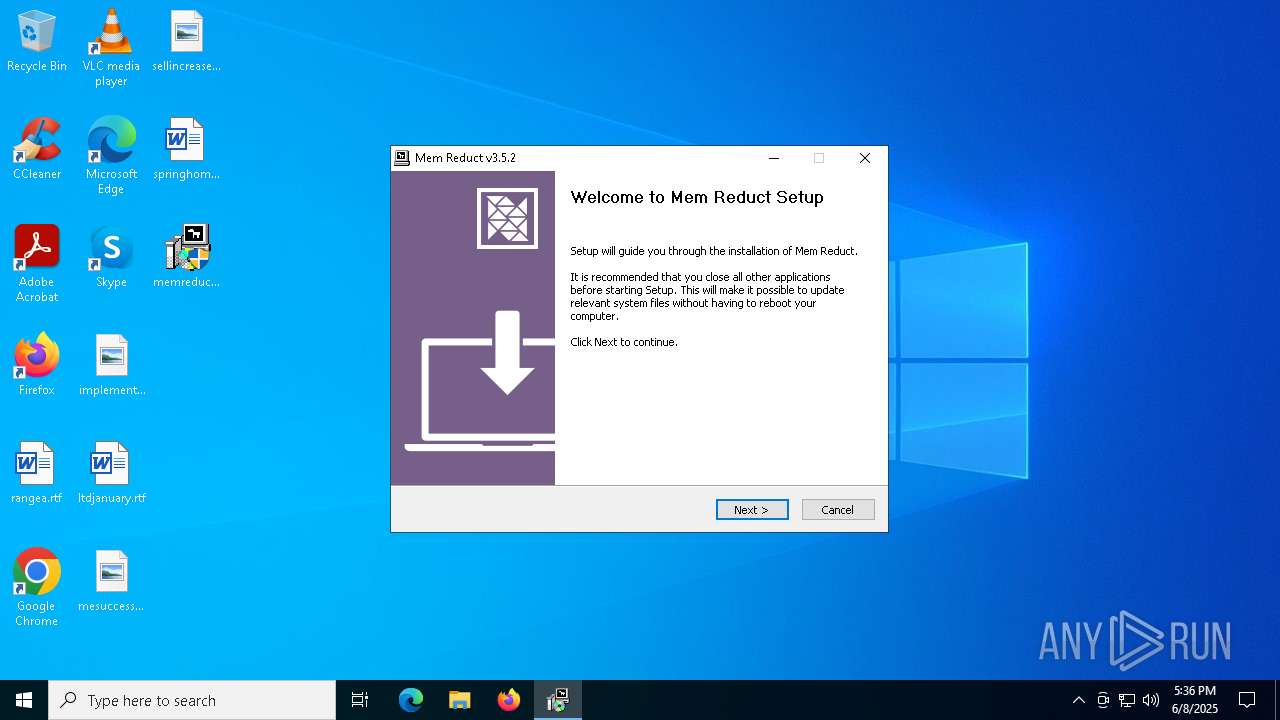
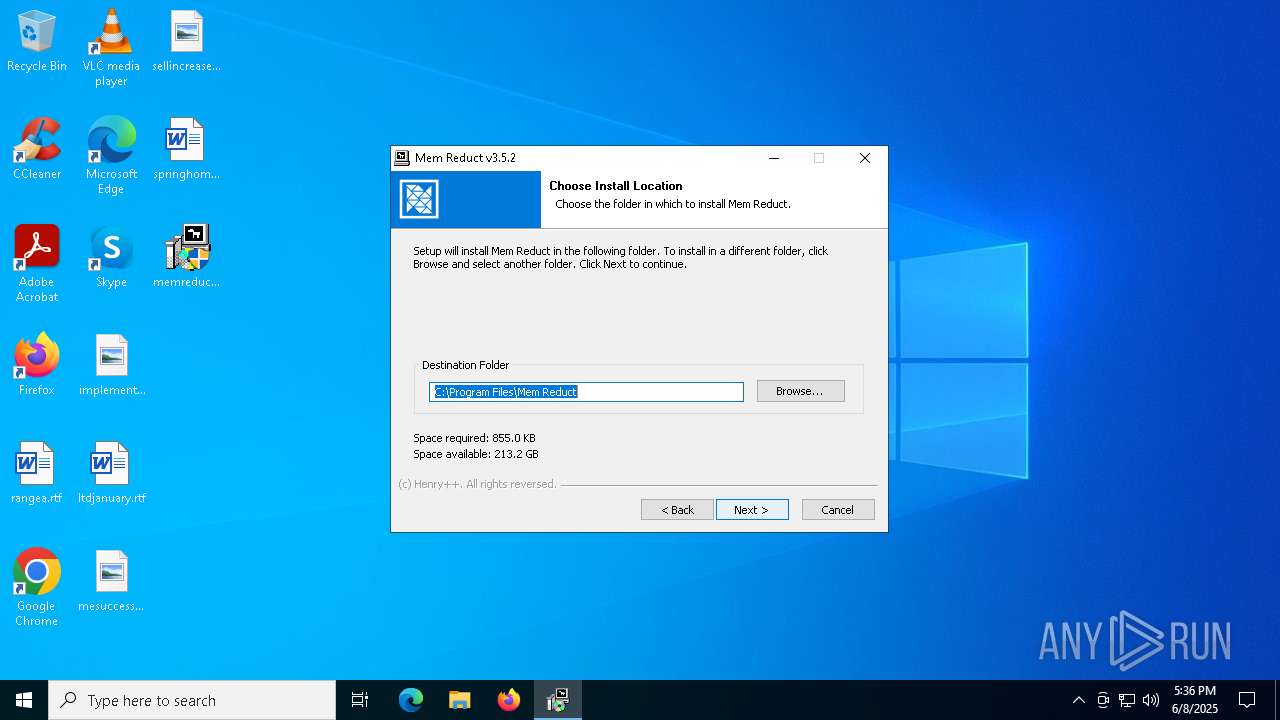
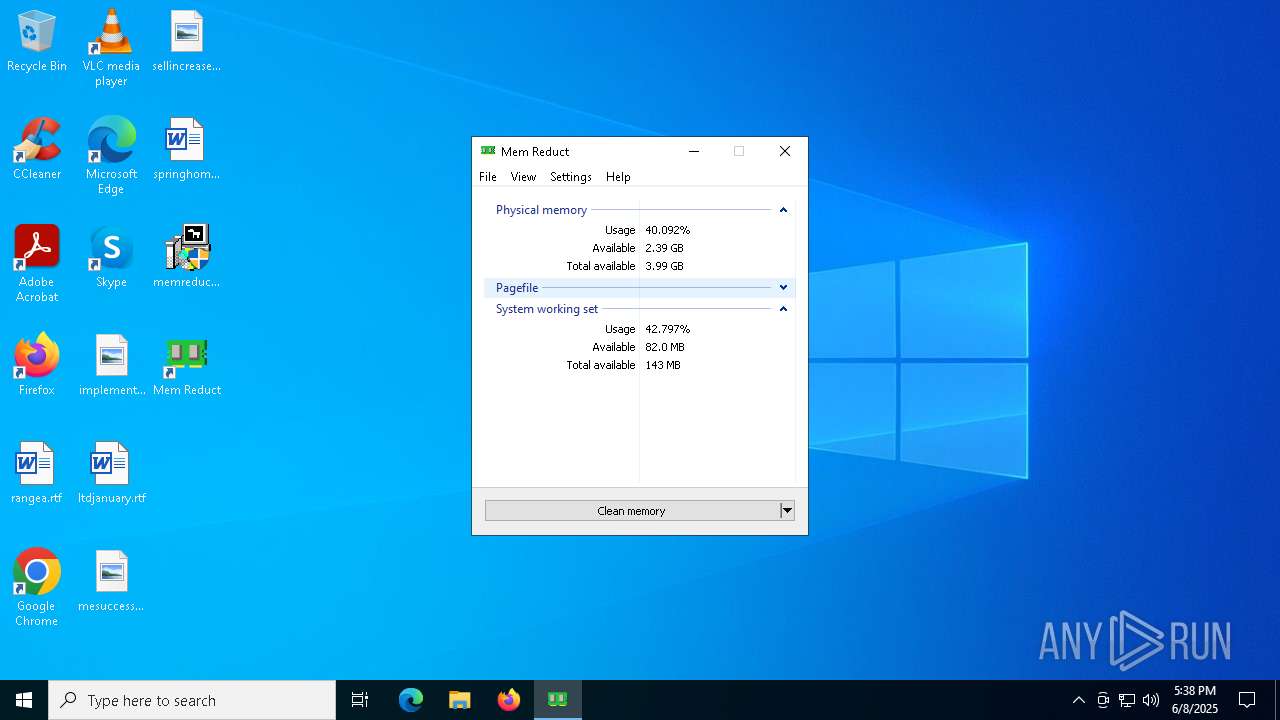
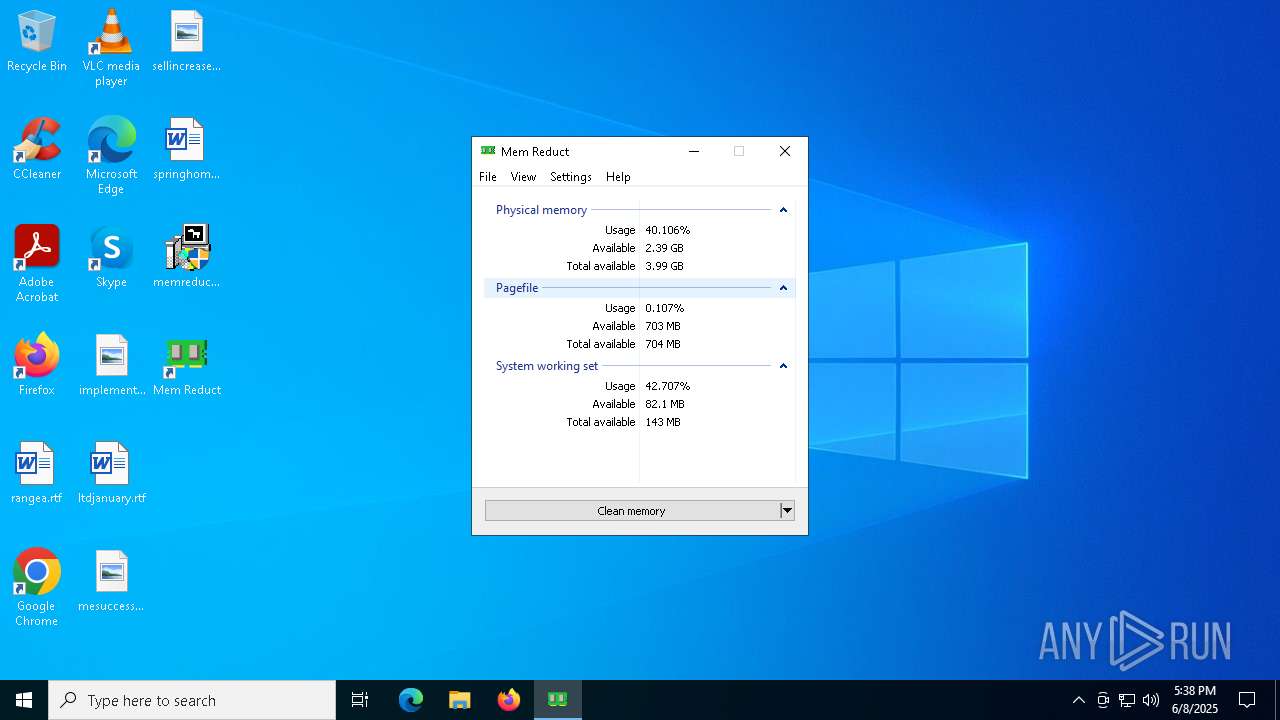
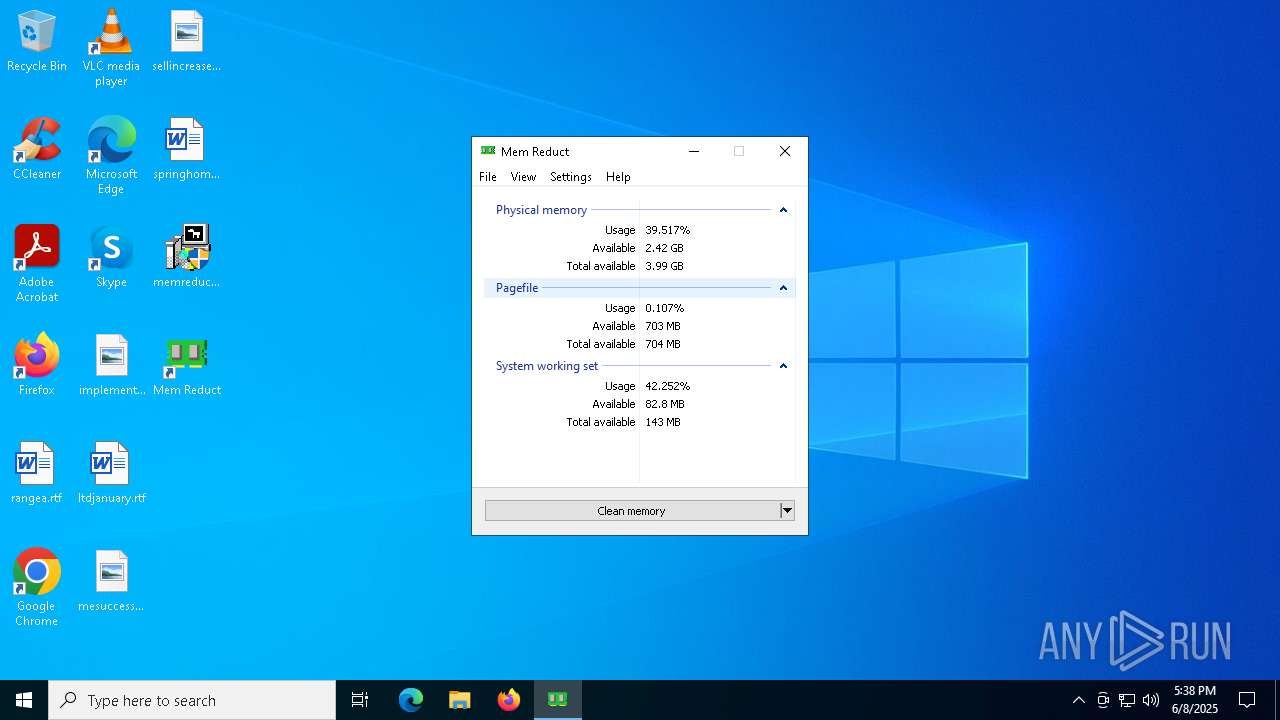
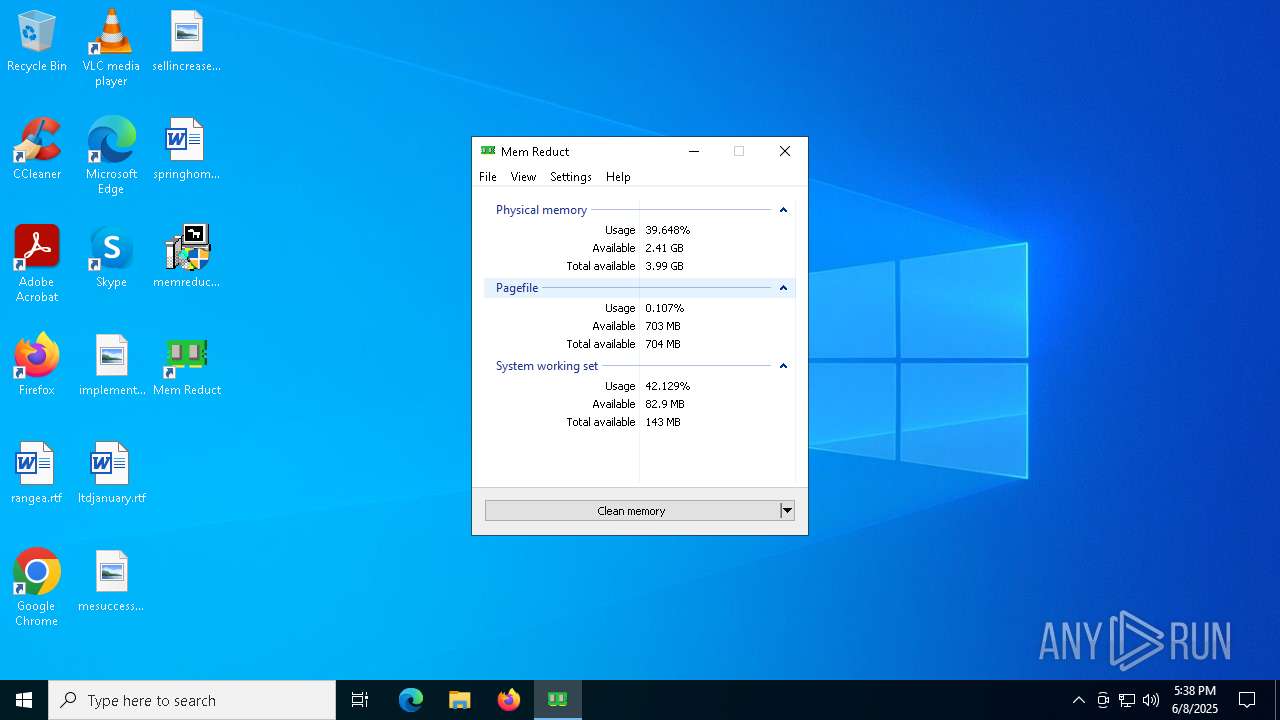
| File name: | memreduct-3.5.2-setup.exe |
| Full analysis: | https://app.any.run/tasks/0b661de6-fec7-4af0-a521-f6fb0da2fe6f |
| Verdict: | Malicious activity |
| Analysis date: | June 08, 2025, 17:36:23 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | 11D30B4D55441D05D85B3B511FFFEEC9 |
| SHA1: | 2CF64758610E031A8157157BCAE0B1383E3A1BF2 |
| SHA256: | 025E5C06F7BECCF5C85CBE931BC058F53A4642CA83A00855A475026A5E6334C4 |
| SSDEEP: | 12288:sioEQO1/yC1VX0j2Mu0BOnVewbmE93Wb/3k+v:3oEQC/yC1p0jbu0BOnVlbl93Wbvk+v |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- memreduct-3.5.2-setup.exe (PID: 5772)
The process creates files with name similar to system file names
- memreduct-3.5.2-setup.exe (PID: 5772)
Malware-specific behavior (creating "System.dll" in Temp)
- memreduct-3.5.2-setup.exe (PID: 5772)
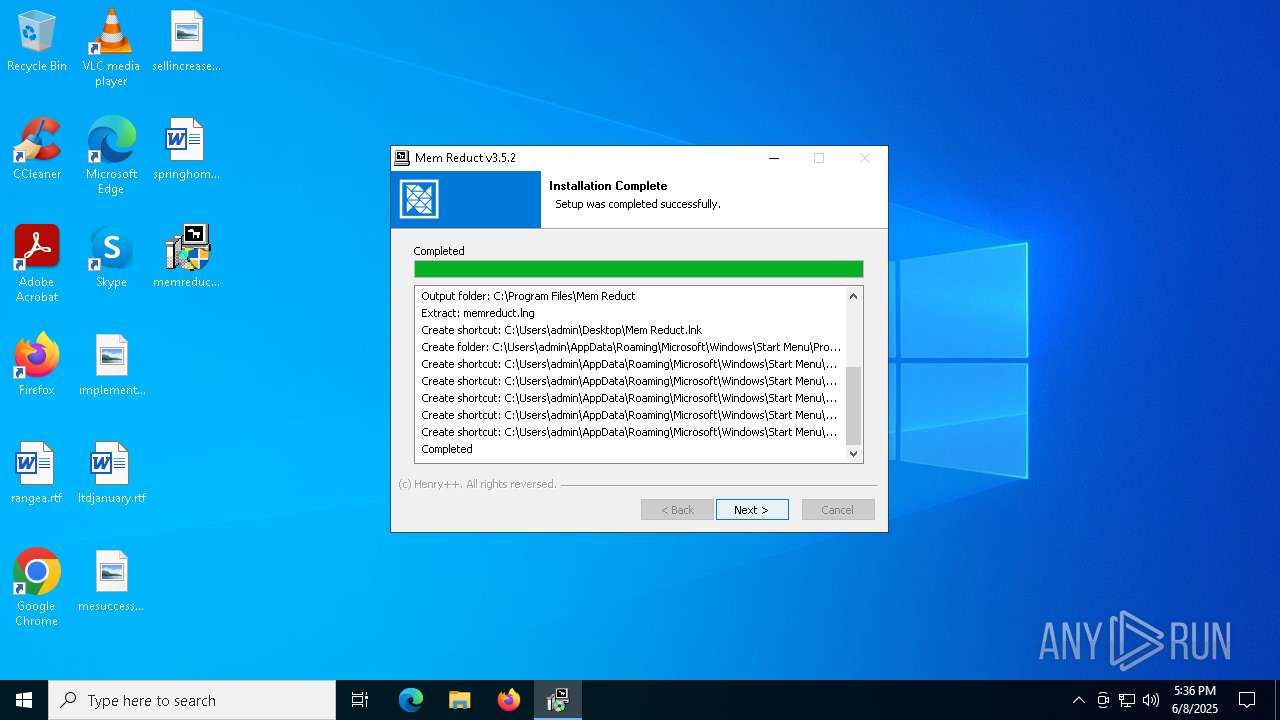
Creates a software uninstall entry
- memreduct-3.5.2-setup.exe (PID: 5772)
There is functionality for taking screenshot (YARA)
- memreduct-3.5.2-setup.exe (PID: 5772)
- memreduct.exe (PID: 6840)
INFO
Checks supported languages
- memreduct-3.5.2-setup.exe (PID: 5772)
- memreduct.exe (PID: 6840)
The sample compiled with english language support
- memreduct-3.5.2-setup.exe (PID: 5772)
Create files in a temporary directory
- memreduct-3.5.2-setup.exe (PID: 5772)
Reads the computer name
- memreduct-3.5.2-setup.exe (PID: 5772)
- memreduct.exe (PID: 6840)
Creates files in the program directory
- memreduct-3.5.2-setup.exe (PID: 5772)
Creates files or folders in the user directory
- memreduct-3.5.2-setup.exe (PID: 5772)
- memreduct.exe (PID: 6840)
Reads the software policy settings
- memreduct.exe (PID: 6840)
- slui.exe (PID: 2660)
Reads the machine GUID from the registry
- memreduct.exe (PID: 6840)
Checks proxy server information
- memreduct.exe (PID: 6840)
- slui.exe (PID: 2660)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:03:08 23:05:20+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 26624 |
| InitializedDataSize: | 139776 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x369f |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.5.2.0 |
| ProductVersionNumber: | 3.5.2.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| Comments: | https://github.com/henrypp |
| CompanyName: | Henry++ |
| FileDescription: | Mem Reduct |
| FileVersion: | 3.5.2 |
| InternalName: | memreduct |
| LegalCopyright: | (c) Henry++. All rights reversed. |
| OriginalFileName: | memreduct-3.5.2-setup.exe |
| ProductName: | Mem Reduct |
| ProductVersion: | 3.5.2 |
Total processes
131
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2660 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5772 | "C:\Users\admin\Desktop\memreduct-3.5.2-setup.exe" | C:\Users\admin\Desktop\memreduct-3.5.2-setup.exe | explorer.exe | ||||||||||||
User: admin Company: Henry++ Integrity Level: HIGH Description: Mem Reduct Exit code: 0 Version: 3.5.2 Modules
| |||||||||||||||
| 6840 | "C:\Program Files\Mem Reduct\memreduct.exe" | C:\Program Files\Mem Reduct\memreduct.exe | memreduct-3.5.2-setup.exe | ||||||||||||
User: admin Company: Henry++ Integrity Level: HIGH Description: Mem Reduct Version: 3.5.2 Modules
| |||||||||||||||
| 6940 | "C:\Users\admin\Desktop\memreduct-3.5.2-setup.exe" | C:\Users\admin\Desktop\memreduct-3.5.2-setup.exe | — | explorer.exe | |||||||||||
User: admin Company: Henry++ Integrity Level: MEDIUM Description: Mem Reduct Exit code: 3221226540 Version: 3.5.2 Modules
| |||||||||||||||
Total events
18 966
Read events
18 956
Write events
10
Delete events
0
Modification events
| (PID) Process: | (5772) memreduct-3.5.2-setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\memreduct |
| Operation: | write | Name: | UninstallString |
Value: "C:\Program Files\Mem Reduct\uninstall.exe" | |||
| (PID) Process: | (5772) memreduct-3.5.2-setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\memreduct |
| Operation: | write | Name: | DisplayName |
Value: Mem Reduct | |||
| (PID) Process: | (5772) memreduct-3.5.2-setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\memreduct |
| Operation: | write | Name: | DisplayIcon |
Value: "C:\Program Files\Mem Reduct\memreduct.exe" | |||
| (PID) Process: | (5772) memreduct-3.5.2-setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\memreduct |
| Operation: | write | Name: | DisplayVersion |
Value: 3.5.2 | |||
| (PID) Process: | (5772) memreduct-3.5.2-setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\memreduct |
| Operation: | write | Name: | Publisher |
Value: Henry++ | |||
| (PID) Process: | (5772) memreduct-3.5.2-setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\memreduct |
| Operation: | write | Name: | InstallLocation |
Value: "C:\Program Files\Mem Reduct" | |||
| (PID) Process: | (5772) memreduct-3.5.2-setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\memreduct |
| Operation: | write | Name: | URLInfoAbout |
Value: https://github.com/henrypp | |||
| (PID) Process: | (5772) memreduct-3.5.2-setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\memreduct |
| Operation: | write | Name: | Installed |
Value: 1 | |||
| (PID) Process: | (5772) memreduct-3.5.2-setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\memreduct |
| Operation: | write | Name: | NoModify |
Value: 1 | |||
| (PID) Process: | (5772) memreduct-3.5.2-setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\memreduct |
| Operation: | write | Name: | NoRepair |
Value: 1 | |||
Executable files
4
Suspicious files
7
Text files
8
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5772 | memreduct-3.5.2-setup.exe | C:\Users\admin\AppData\Local\Temp\nsl401.tmp\System.dll | executable | |
MD5:9B38A1B07A0EBC5C7E59E63346ECC2DB | SHA256:C881253DAFCF1322A771139B1A429EC1E78C507CA81A218A20DC1A4B25ABBFE7 | |||
| 5772 | memreduct-3.5.2-setup.exe | C:\Users\admin\AppData\Local\Temp\nsl401.tmp\modern-header.bmp | image | |
MD5:D98F2159025CCD128B59B6BA715CEE46 | SHA256:B74ED1397C5A50C22DDD4DA1C01CF1A36484FA38623051B4959BB6E01D657547 | |||
| 5772 | memreduct-3.5.2-setup.exe | C:\Program Files\Mem Reduct\memreduct.exe.sig | binary | |
MD5:561870CD86DB34A61AF8C34B15FC7DC5 | SHA256:649FBE7C4576C85903A654663AA1E64701887E32796A91CF211117CDC3BCAE08 | |||
| 5772 | memreduct-3.5.2-setup.exe | C:\Users\admin\AppData\Local\Temp\nsl401.tmp\modern-wizard.bmp | image | |
MD5:48992D90BF2B3360D2301802A0C25900 | SHA256:411961864A8EDB7CC2BA384E702BBB787040EA47488D2CEFC2EF2C6F0A55A832 | |||
| 5772 | memreduct-3.5.2-setup.exe | C:\Program Files\Mem Reduct\memreduct.exe | executable | |
MD5:66F5C7EBE24ABC9405E688C1597E1BE9 | SHA256:2F6E097D5C1B55BB5115910B2736D47F4B2D1955FE9E8DA48E15F165B7DE674B | |||
| 5772 | memreduct-3.5.2-setup.exe | C:\Program Files\Mem Reduct\History.txt | text | |
MD5:03578467A8ECFA11E371A8772B9868D7 | SHA256:ACD05334090B4267600F6C9CB3AE11F5C99ADC1BFF3071C04D7BC8B42660CC32 | |||
| 5772 | memreduct-3.5.2-setup.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Mem Reduct\Uninstall.lnk | binary | |
MD5:F4FB9EF062AE834B81753DC13B7C8C17 | SHA256:660562C560B8C37D0A4C33128EBEDF9E5A79E1D2BC96E0C54DEC65D558B85C3E | |||
| 5772 | memreduct-3.5.2-setup.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Mem Reduct\License.lnk | binary | |
MD5:214CF986CAA587CF62D3C7E7B2E668E8 | SHA256:6F91EECD6C636B8D7F58F2D787C736E0900D9A652C59BCE70DE59BD02D3E6C92 | |||
| 5772 | memreduct-3.5.2-setup.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Mem Reduct\Readme.lnk | binary | |
MD5:EC05139C0BD528A5D90F95ED99CB86BA | SHA256:A803C76EBB12FAC6BB1827FDD017B94917CC45E28625FC43C98B8E3F66420116 | |||
| 5772 | memreduct-3.5.2-setup.exe | C:\Users\admin\AppData\Local\Temp\nsl401.tmp\nsDialogs.dll | executable | |
MD5:8F0E7415F33843431DF308BB8E06AF81 | SHA256:BB49F15FA83452370047A7801E39FC7F64E70C7545B8999BB85AA4749EAA048B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
24
DNS requests
10
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
472 | svchost.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
8008 | RUXIMICS.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
472 | svchost.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
8008 | RUXIMICS.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 140.82.121.3:443 | https://raw.githubusercontent.com/henrypp/memreduct/master/VERSION | unknown | text | 203 b | whitelisted |
— | — | GET | 200 | 140.82.121.3:443 | https://raw.githubusercontent.com/henrypp/memreduct/master/bin/memreduct.lng | unknown | text | 117 Kb | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
472 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
8008 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
472 | svchost.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
8008 | RUXIMICS.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
472 | svchost.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
8008 | RUXIMICS.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
472 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
raw.githubusercontent.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |