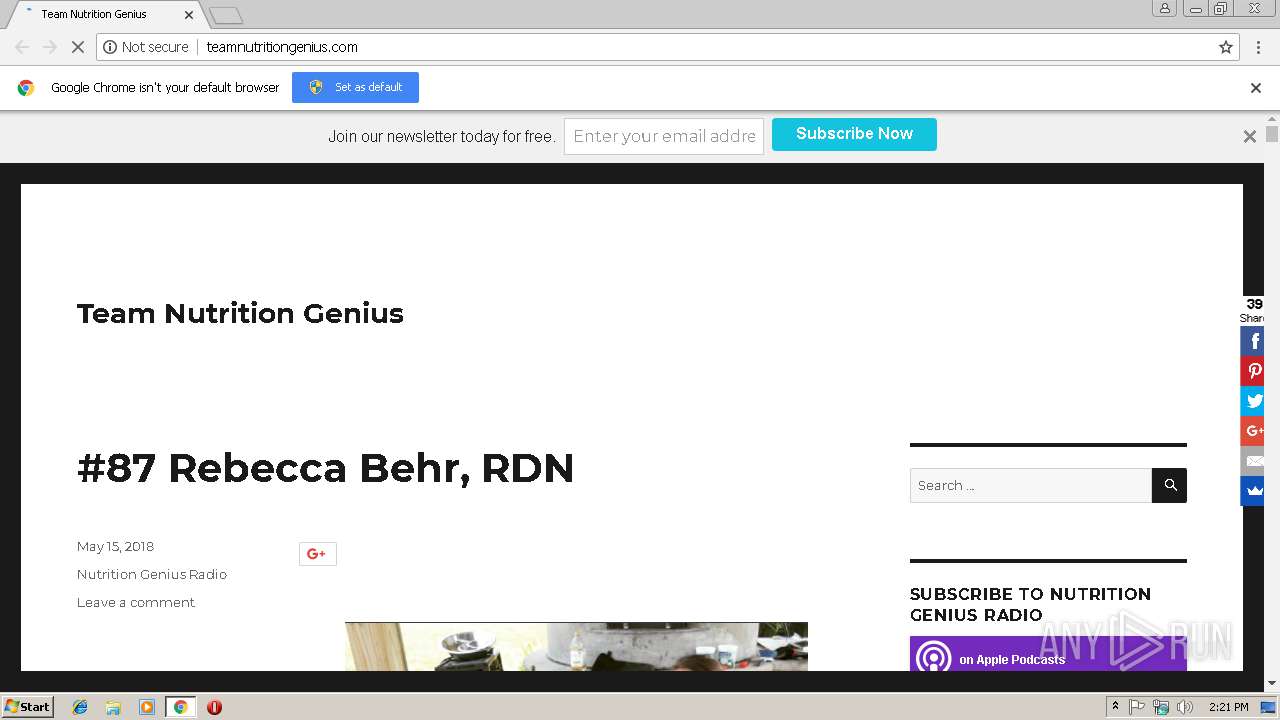
| URL: | http://teamnutritiongenius.com |
| Full analysis: | https://app.any.run/tasks/cb0cbe68-a2bc-4603-af6f-b88fe94b5c99 |
| Verdict: | Malicious activity |
| Analysis date: | February 10, 2019, 14:20:57 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | CD24BC0BC3742A6E55DE48FD0E34D036 |
| SHA1: | D2AE1BB59DA1F544099782F6B36E6CCD25520D1F |
| SHA256: | 025629DE064929D497000F1B3FE52398DF160C7AFA018C2C01A1F820F8EB0217 |
| SSDEEP: | 3:N1KKA00ndHKI:CK/0ndz |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Reads settings of System Certificates
- chrome.exe (PID: 2708)
Application launched itself
- chrome.exe (PID: 2708)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
37
Monitored processes
9
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2296 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=956,1112433181398300262,13346142530850764726,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=82FA702C3F347F8C50A6AB29EEDB37BE --mojo-platform-channel-handle=2420 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2572 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=956,1112433181398300262,13346142530850764726,131072 --enable-features=PasswordImport --disable-gpu-sandbox --gpu-preferences=KAAAAAAAAACAAwBAAQAAAAAAAAAAAGAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --service-request-channel-token=A2660C6CBBD6E67A8CE1B1D5B0384B73 --mojo-platform-channel-handle=4280 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2708 | "C:\Program Files\Google\Chrome\Application\chrome.exe" http://teamnutritiongenius.com | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2756 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=956,1112433181398300262,13346142530850764726,131072 --enable-features=PasswordImport --service-pipe-token=9FA4BEFECCF0649080EA9ECA35DF4D97 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=9FA4BEFECCF0649080EA9ECA35DF4D97 --renderer-client-id=4 --mojo-platform-channel-handle=1908 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2820 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=2712 --on-initialized-event-handle=304 --parent-handle=308 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 3100 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=956,1112433181398300262,13346142530850764726,131072 --enable-features=PasswordImport --service-pipe-token=8FC767577AF1E7C24CB24E9688133455 --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=8FC767577AF1E7C24CB24E9688133455 --renderer-client-id=3 --mojo-platform-channel-handle=1536 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 3272 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=956,1112433181398300262,13346142530850764726,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=702CA2326CF2B3F79178EB13238ADAAB --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=702CA2326CF2B3F79178EB13238ADAAB --renderer-client-id=5 --mojo-platform-channel-handle=3828 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 3468 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=68.0.3440.106 --initial-client-data=0x78,0x7c,0x80,0x74,0x84,0x6f7700b0,0x6f7700c0,0x6f7700cc | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 4012 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=956,1112433181398300262,13346142530850764726,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAACAAwBAAQAAAAAAAAAAAGAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --service-request-channel-token=33FF2C0AC3CCF2B4F5A9F9DE1C426F58 --mojo-platform-channel-handle=992 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
Total events
495
Read events
450
Write events
42
Delete events
3
Modification events
| (PID) Process: | (2708) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2708) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2708) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2820) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 2708-13194282083363125 |
Value: 259 | |||
| (PID) Process: | (2708) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2708) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (2708) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3516-13180984670829101 |
Value: 0 | |||
| (PID) Process: | (2708) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (2708) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 2708-13194282083363125 |
Value: 259 | |||
| (PID) Process: | (2708) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
Executable files
0
Suspicious files
27
Text files
68
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2708 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\17bc742d-4b1a-414b-b45e-bd4121cf4493.tmp | — | |
MD5:— | SHA256:— | |||
| 2708 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Download Service\EntryDB\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2708 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2708 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\6432cc13-7b73-4ae4-a390-659182497f03.tmp | — | |
MD5:— | SHA256:— | |||
| 2708 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Last Version | text | |
MD5:— | SHA256:— | |||
| 2708 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2708 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Service Worker\Database\LOG.old~RF199205.TMP | text | |
MD5:— | SHA256:— | |||
| 2708 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF199205.TMP | text | |
MD5:— | SHA256:— | |||
| 2708 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Service Worker\Database\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2708 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Thumbnails\LOG.old~RF1992d0.TMP | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
109
TCP/UDP connections
57
DNS requests
40
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2708 | chrome.exe | GET | 200 | 166.62.115.254:80 | http://teamnutritiongenius.com/wp-content/plugins/jquery-pin-it-button-for-images/css/client.css?ver=2.3.3 | US | text | 1.13 Kb | malicious |
2708 | chrome.exe | GET | 200 | 2.23.75.124:80 | http://platform-api.sharethis.com/js/sharethis.js | unknown | text | 27.2 Kb | whitelisted |
2708 | chrome.exe | GET | 200 | 166.62.115.254:80 | http://teamnutritiongenius.com/ | US | html | 22.2 Kb | malicious |
2708 | chrome.exe | GET | 200 | 172.217.22.42:80 | http://fonts.googleapis.com/css?family=Shadows+Into+Light%3Aregular&subset=latin%2Call&ver=5.0.3 | US | text | 309 b | whitelisted |
2708 | chrome.exe | GET | 200 | 166.62.115.254:80 | http://teamnutritiongenius.com/wp-content/plugins/jetpack/modules/theme-tools/compat/twentysixteen.css?ver=5.3 | US | text | 2.87 Kb | malicious |
2708 | chrome.exe | GET | 200 | 166.62.115.254:80 | http://teamnutritiongenius.com/wp-content/themes/twentysixteen/css/blocks.css?ver=20181230 | US | text | 1.78 Kb | malicious |
2708 | chrome.exe | GET | 200 | 166.62.115.254:80 | http://teamnutritiongenius.com/wp-content/plugins/click-to-tweet-by-todaymade/assets/css/styles.css?ver=5.0.3 | US | text | 751 b | malicious |
2708 | chrome.exe | GET | 200 | 166.62.115.254:80 | http://teamnutritiongenius.com/wp-content/plugins/jetpack/_inc/social-logos/social-logos.min.css?ver=1 | US | text | 18.5 Kb | malicious |
2708 | chrome.exe | GET | 200 | 166.62.115.254:80 | http://teamnutritiongenius.com/wp-content/plugins/advanced-wp-columns/assets/css/awp-columns.css?ver=5.0.3 | US | text | 167 b | malicious |
2708 | chrome.exe | GET | 200 | 166.62.115.254:80 | http://teamnutritiongenius.com/wp-includes/css/dist/block-library/theme.min.css?ver=5.0.3 | US | text | 452 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2708 | chrome.exe | 216.58.208.35:443 | www.gstatic.com | Google Inc. | US | whitelisted |
2708 | chrome.exe | 216.58.206.3:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2708 | chrome.exe | 172.217.22.42:80 | fonts.googleapis.com | Google Inc. | US | whitelisted |
2708 | chrome.exe | 216.58.205.237:443 | accounts.google.com | Google Inc. | US | whitelisted |
2708 | chrome.exe | 172.217.22.42:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
2708 | chrome.exe | 64.233.167.139:443 | apis.google.com | Google Inc. | US | whitelisted |
2708 | chrome.exe | 35.165.225.32:80 | load.sumome.com | Amazon.com, Inc. | US | unknown |
2708 | chrome.exe | 2.23.75.124:80 | platform-api.sharethis.com | Akamai Technologies, Inc. | — | whitelisted |
2708 | chrome.exe | 172.217.22.3:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
2708 | chrome.exe | 192.0.77.32:443 | s0.wp.com | Automattic, Inc | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
teamnutritiongenius.com |
| malicious |
www.gstatic.com |
| whitelisted |
accounts.google.com |
| shared |
apis.google.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
platform-api.sharethis.com |
| whitelisted |
load.sumome.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
s.gravatar.com |
| whitelisted |