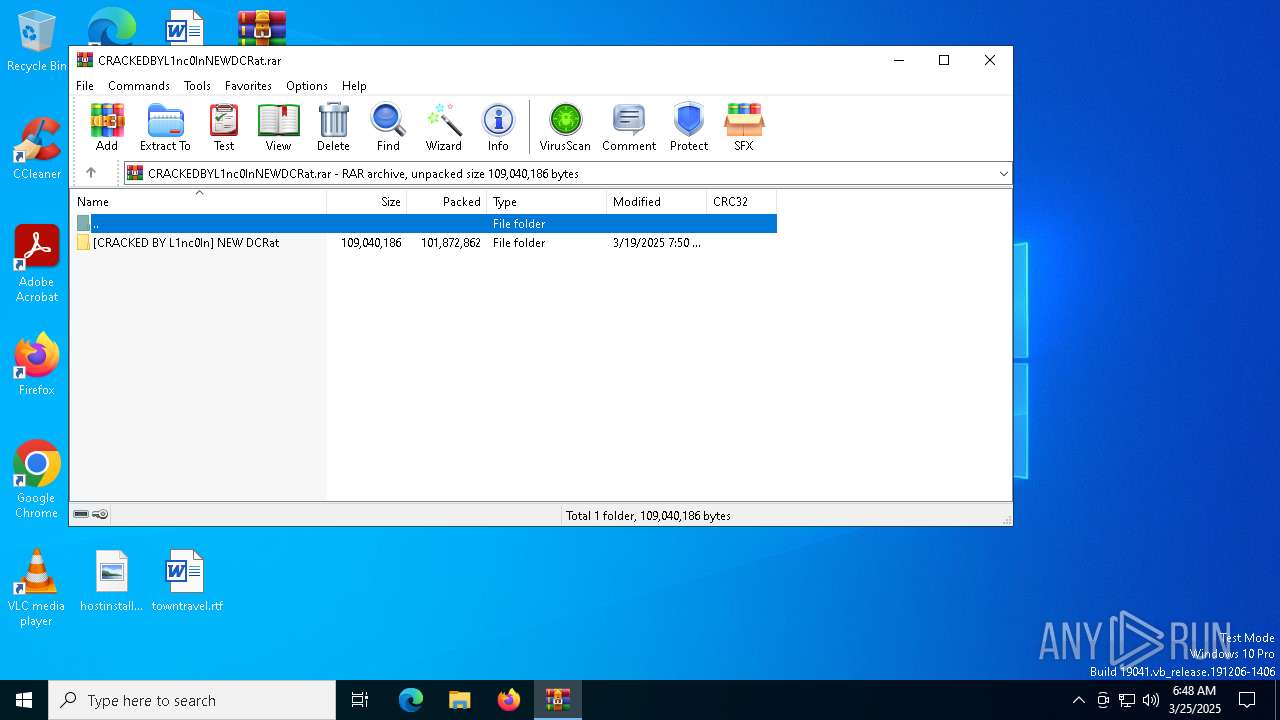
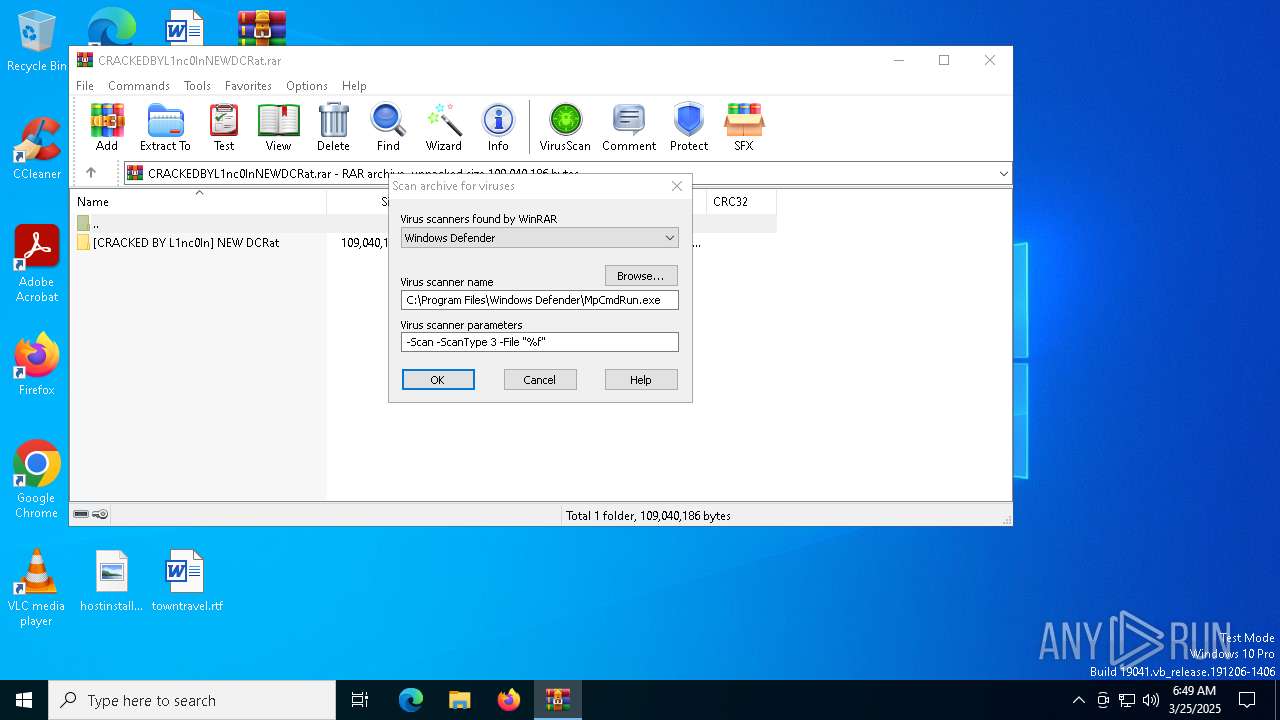
| File name: | CRACKEDBYL1nc0InNEWDCRat.rar |
| Full analysis: | https://app.any.run/tasks/cbd0356d-4a8a-4cee-bf1c-a5adb0258662 |
| Verdict: | Malicious activity |
| Threats: | DCrat, also known as Dark Crystal RAT, is a remote access trojan (RAT), which was first introduced in 2018. It is a modular malware that can be customized to perform different tasks. For instance, it can steal passwords, crypto wallet information, hijack Telegram and Steam accounts, and more. Attackers may use a variety of methods to distribute DCrat, but phishing email campaigns are the most common. |
| Analysis date: | March 25, 2025, 06:47:29 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 7E51293BC2161CB1DAF677E7C95F4811 |
| SHA1: | A228A7C2E2EFD5ABD891B8CFC0D33F3B536A36F3 |
| SHA256: | 01CC2B1BCA4A1A99BB6AE311FF222B788700913CB0BA765DBDEE7F25160BF91A |
| SSDEEP: | 786432:AKT6ft2WVltBlgXPW3kuDKoh814Y9Ir/0yGR7wYYKfd4Q6N:AKel2CtBlgXPW3DCqY9Ir/bGR7wfuz6N |
MALICIOUS
DCRAT has been detected (YARA)
- slui.exe (PID: 7984)
- conhost.exe (PID: 8064)
SUSPICIOUS
Drops 7-zip archiver for unpacking
- WinRAR.exe (PID: 7836)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 7836)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 7836)
There is functionality for taking screenshot (YARA)
- conhost.exe (PID: 8064)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7836)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7836)
The sample compiled with english language support
- WinRAR.exe (PID: 7836)
Drops encrypted VBS script (Microsoft Script Encoder)
- WinRAR.exe (PID: 7836)
Reads the computer name
- MpCmdRun.exe (PID: 8116)
Checks supported languages
- MpCmdRun.exe (PID: 8116)
Create files in a temporary directory
- MpCmdRun.exe (PID: 8116)
Checks proxy server information
- slui.exe (PID: 7984)
Reads the software policy settings
- slui.exe (PID: 7984)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 31988444 |
| UncompressedSize: | 32177408 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | [CRACKED BY L1nc0In] NEW DCRat/DCRat/background.cache |
Total processes
121
Monitored processes
5
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 7836 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\CRACKEDBYL1nc0InNEWDCRat.rar | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 7984 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 8056 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR7836.16277\Rar$Scan40748.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 8064 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 8116 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR7836.16277" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
4 955
Read events
4 946
Write events
9
Delete events
0
Modification events
| (PID) Process: | (7836) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7836) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7836) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7836) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\CRACKEDBYL1nc0InNEWDCRat.rar | |||
| (PID) Process: | (7836) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7836) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7836) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7836) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
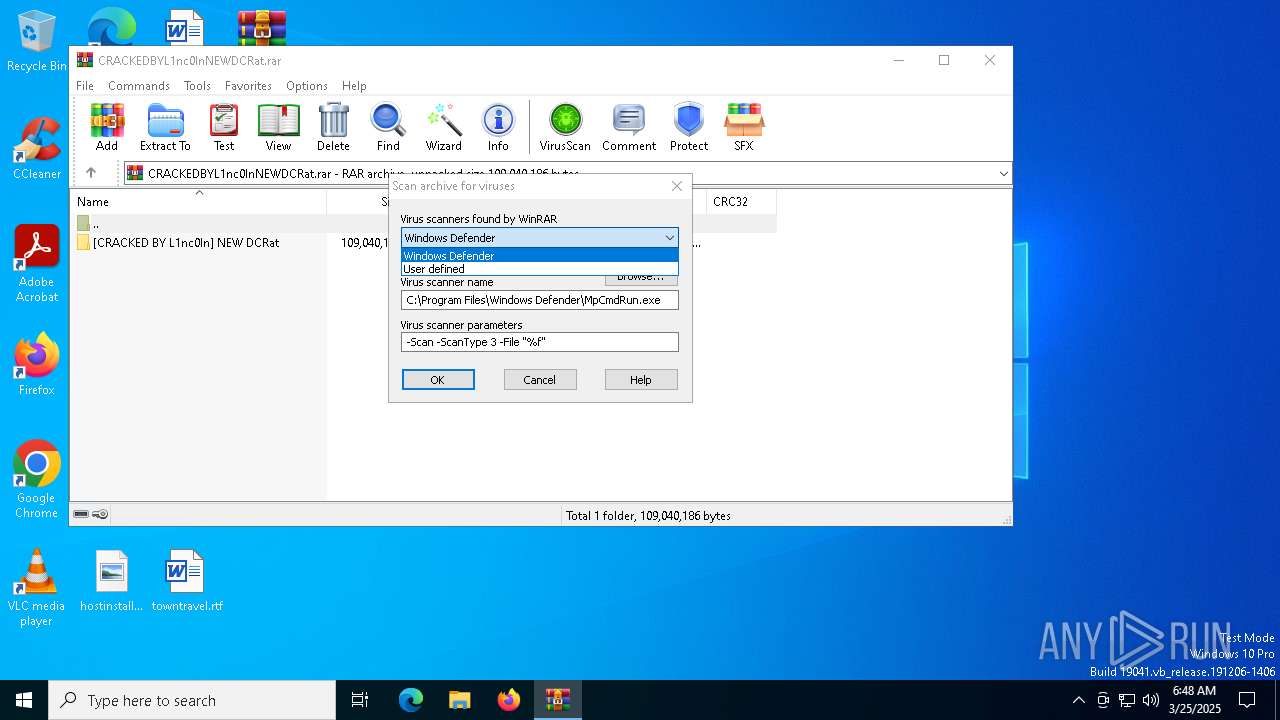
| (PID) Process: | (7836) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\VirusScan |
| Operation: | write | Name: | DefScanner |
Value: Windows Defender | |||
Executable files
24
Suspicious files
87
Text files
63
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7836 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7836.16277\CRACKEDBYL1nc0InNEWDCRat.rar\[CRACKED BY L1nc0In] NEW DCRat\DCRat\background.cache | — | |
MD5:— | SHA256:— | |||
| 7836 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7836.16277\CRACKEDBYL1nc0InNEWDCRat.rar\[CRACKED BY L1nc0In] NEW DCRat\DCRat\data\rar.exe | executable | |
MD5:300D43860DC6961BBECE819912C930BC | SHA256:792708CE3FEC9DA37408CE4179B118D79B4804878D233C602B490C3BD0EAF02A | |||
| 7836 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7836.16277\CRACKEDBYL1nc0InNEWDCRat.rar\[CRACKED BY L1nc0In] NEW DCRat\DCRat\data\dotNET_Reactor.exe | executable | |
MD5:BD73DF4CF427511993075F7A16E037A5 | SHA256:FA0A32D408A8DF70EC44F3D2374B058F57B86FF49B8068B8C68F8505D3463970 | |||
| 7836 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7836.16277\CRACKEDBYL1nc0InNEWDCRat.rar\[CRACKED BY L1nc0In] NEW DCRat\DCRat\data\NCC3.dll | executable | |
MD5:AA84F91EDD922E7B3BB979E663C94F1A | SHA256:38274608D5A4B53EC22F8099F798BA46CE0ED41DB65A33DFB3853F0DBF849F6F | |||
| 7836 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7836.16277\CRACKEDBYL1nc0InNEWDCRat.rar\[CRACKED BY L1nc0In] NEW DCRat\DCRat\data\DCRBT.exe | executable | |
MD5:32E2BC4F79C776B542F6775895BEAF21 | SHA256:98EC5492A2F0AEBA5B39A9F41498D98C73643BF6D8D177E5831FB0AD6E6F8521 | |||
| 7836 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7836.16277\CRACKEDBYL1nc0InNEWDCRat.rar\[CRACKED BY L1nc0In] NEW DCRat\DCRat\data\DCRBC.exe | executable | |
MD5:14A56E4B7BD40512B49D6F72086E8FC1 | SHA256:86C45FB7473E5C1DF78B8CBB2003033C37B4CB01A677C1EF30CA1573E84EC692 | |||
| 7836 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7836.16277\CRACKEDBYL1nc0InNEWDCRat.rar\[CRACKED BY L1nc0In] NEW DCRat\DCRat\data\dotNET_Reactor.Console.exe | executable | |
MD5:69D18A3245F3C2FD02C82304C494E977 | SHA256:B55B0A652538836ED681C2AFD985310FD39AD2F31AC159847FC46A6065F3232E | |||
| 7836 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7836.16277\CRACKEDBYL1nc0InNEWDCRat.rar\[CRACKED BY L1nc0In] NEW DCRat\DCRat\data\enc.vbe | binary | |
MD5:F88125F6EAFC7F4805913CF4077B2525 | SHA256:5981E508E89C65C445FCA892E91B8EC39B1D8563804D0999D963D640AA592444 | |||
| 7836 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7836.16277\CRACKEDBYL1nc0InNEWDCRat.rar\[CRACKED BY L1nc0In] NEW DCRat\DCRat\data\RarExt.dll | executable | |
MD5:1F3BB0F89E7CD67A76220EA2E3E7D8C6 | SHA256:68ECB747F523D122C1C2094B3FB6035F7F76FBD948A97E3D42EE526824546FEC | |||
| 7836 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7836.16277\CRACKEDBYL1nc0InNEWDCRat.rar\[CRACKED BY L1nc0In] NEW DCRat\DCRat\data\WinCon.SFX | executable | |
MD5:AEC7145167E9C207DB5A932E615FBF87 | SHA256:88D0E8B4958660C5D4C57C81A7C198F5E52C1505104C0A4D57DC5EA02504564A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
22
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2104 | svchost.exe | GET | 200 | 23.216.77.42:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 23.216.77.42:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
7492 | slui.exe | 20.83.72.98:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7984 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |