| download: | 65099.html |
| Full analysis: | https://app.any.run/tasks/3a8fbf2a-b85f-4d70-97d3-9e10ee38504d |
| Verdict: | Malicious activity |
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | August 30, 2019, 15:14:44 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, ISO-8859 text, with very long lines, with CRLF, LF line terminators |
| MD5: | E9658BF73B08DD2860268072CF7E657B |
| SHA1: | 755B037740B6EE89436C3E595ADFAFE675CDEBCD |
| SHA256: | 01C2B8C2391AB86D555C2998E2A733CD8E3B1EC0EBD83433B5D2B508556BBC77 |
| SSDEEP: | 1536:yLwfO44a4CH295WXSlgJGmXp5G5V8k937VFttlKJfQ/rs8bueQpQwfD6qrnZzYEf:WW9XSlgJZXuTrVFeYFbueQpQwfD6qrn5 |
MALICIOUS
Downloads executable files from the Internet
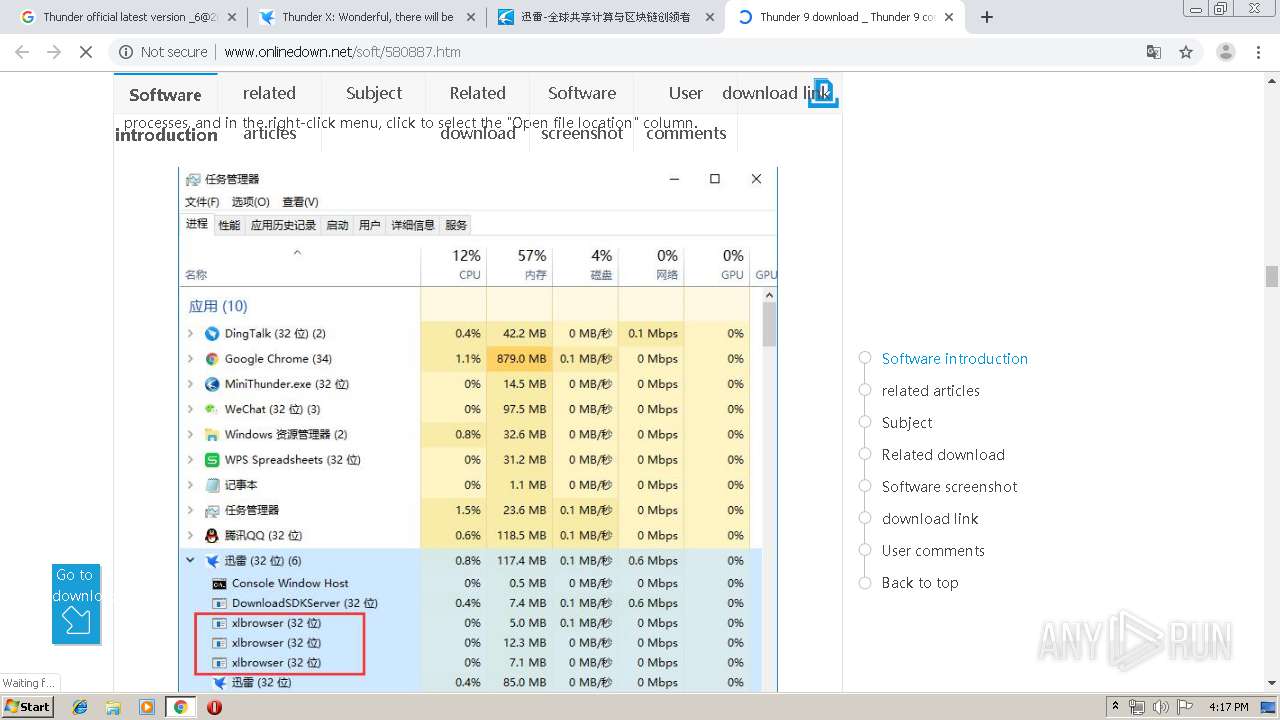
- chrome.exe (PID: 3600)
Application was dropped or rewritten from another process
- XunLeiWebSetup10.1.18.500gw.exe (PID: 4092)
- XunLeiWebSetup10.1.18.500gw.exe (PID: 2596)
- DownloadSDKServer.exe (PID: 2948)
- XLServicePlatform.exe (PID: 3020)
- XLServicePlatform.exe (PID: 3016)
- XLWFPSetup.exe (PID: 1468)
- InstallXLWFP.exe (PID: 4068)
- InstallXLWFP.exe (PID: 1636)
- XLServicePlatform.exe (PID: 3456)
- Win7AppId.exe (PID: 1932)
- Win7AppId.exe (PID: 2396)
- Win7AppId.exe (PID: 3792)
- Win7AppId.exe (PID: 2596)
- Win7AppId.exe (PID: 2764)
- InstallXLGuard.exe (PID: 2192)
- InstallXLGuard.exe (PID: 1420)
- ThunderBHOPlatform.exe (PID: 2844)
- BHOInstall.exe (PID: 3368)
- Thunder.exe (PID: 2656)
- Thunder.exe (PID: 2376)
- Win7AppId.exe (PID: 1156)
Loads dropped or rewritten executable
- XunLeiWebSetup10.1.18.500gw.exe (PID: 4092)
- XunLeiSetup10.1.18.500.exe (PID: 184)
- DownloadSDKServer.exe (PID: 2948)
- XLWFPSetup.exe (PID: 1468)
- svchost.exe (PID: 1008)
- regsvr32.exe (PID: 3176)
- regsvr32.exe (PID: 1804)
- BHOInstall.exe (PID: 3368)
- regsvr32.exe (PID: 3576)
- ThunderBHOPlatform.exe (PID: 2844)
- Thunder.exe (PID: 2656)
- Thunder.exe (PID: 2376)
Creates or modifies windows services
- XLServicePlatform.exe (PID: 3456)
Registers / Runs the DLL via REGSVR32.EXE
- ThunderBHOPlatform.exe (PID: 2844)
- XunLeiSetup10.1.18.500.exe (PID: 184)
Changes the autorun value in the registry
- XunLeiSetup10.1.18.500.exe (PID: 184)
SUSPICIOUS
Modifies files in Chrome extension folder
- chrome.exe (PID: 3660)
Executable content was dropped or overwritten
- XunLeiWebSetup10.1.18.500gw.exe (PID: 4092)
- chrome.exe (PID: 3660)
- chrome.exe (PID: 3600)
- XLWFPSetup.exe (PID: 1468)
- XunLeiSetup10.1.18.500.exe (PID: 184)
- XLServicePlatform.exe (PID: 3456)
- regsvr32.exe (PID: 3576)
- ThunderBHOPlatform.exe (PID: 2844)
Low-level read access rights to disk partition
- XunLeiWebSetup10.1.18.500gw.exe (PID: 4092)
- DownloadSDKServer.exe (PID: 2948)
- XunLeiSetup10.1.18.500.exe (PID: 184)
- XLServicePlatform.exe (PID: 3016)
- InstallXLWFP.exe (PID: 1636)
- InstallXLWFP.exe (PID: 4068)
- InstallXLGuard.exe (PID: 1420)
- InstallXLGuard.exe (PID: 2192)
- XLServicePlatform.exe (PID: 3456)
- svchost.exe (PID: 1008)
- BHOInstall.exe (PID: 3368)
- Thunder.exe (PID: 2656)
- Thunder.exe (PID: 2376)
Connects to unusual port
- XunLeiWebSetup10.1.18.500gw.exe (PID: 4092)
- XunLeiSetup10.1.18.500.exe (PID: 184)
- XLServicePlatform.exe (PID: 3016)
- InstallXLWFP.exe (PID: 4068)
- InstallXLGuard.exe (PID: 2192)
- InstallXLGuard.exe (PID: 1420)
- XLServicePlatform.exe (PID: 3456)
- svchost.exe (PID: 1008)
Creates files in the program directory
- XunLeiWebSetup10.1.18.500gw.exe (PID: 4092)
- XLWFPSetup.exe (PID: 1468)
- XunLeiSetup10.1.18.500.exe (PID: 184)
- XLServicePlatform.exe (PID: 3456)
- regsvr32.exe (PID: 3176)
- regsvr32.exe (PID: 3576)
- ThunderBHOPlatform.exe (PID: 2844)
Uses NETSH.EXE for network configuration
- XunLeiWebSetup10.1.18.500gw.exe (PID: 4092)
- XunLeiSetup10.1.18.500.exe (PID: 184)
Reads CPU info
- DownloadSDKServer.exe (PID: 2948)
Creates a software uninstall entry
- XunLeiSetup10.1.18.500.exe (PID: 184)
Creates files in the user directory
- XunLeiSetup10.1.18.500.exe (PID: 184)
Creates files in the driver directory
- XLWFPSetup.exe (PID: 1468)
Creates files in the Windows directory
- XLWFPSetup.exe (PID: 1468)
- svchost.exe (PID: 1008)
Creates COM task schedule object
- regsvr32.exe (PID: 3176)
- regsvr32.exe (PID: 3576)
- regsvr32.exe (PID: 1804)
Removes files from Windows directory
- svchost.exe (PID: 1008)
Modifies the open verb of a shell class
- XunLeiSetup10.1.18.500.exe (PID: 184)
Application launched itself
- Thunder.exe (PID: 2656)
INFO
Reads internet explorer settings
- iexplore.exe (PID: 3336)
Application launched itself
- chrome.exe (PID: 3660)
- iexplore.exe (PID: 2868)
Creates files in the user directory
- iexplore.exe (PID: 3336)
Changes internet zones settings
- iexplore.exe (PID: 2868)
Manual execution by user
- chrome.exe (PID: 3660)
Reads Internet Cache Settings
- chrome.exe (PID: 3660)
Dropped object may contain Bitcoin addresses
- XunLeiSetup10.1.18.500.exe (PID: 184)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
EXIF
HTML
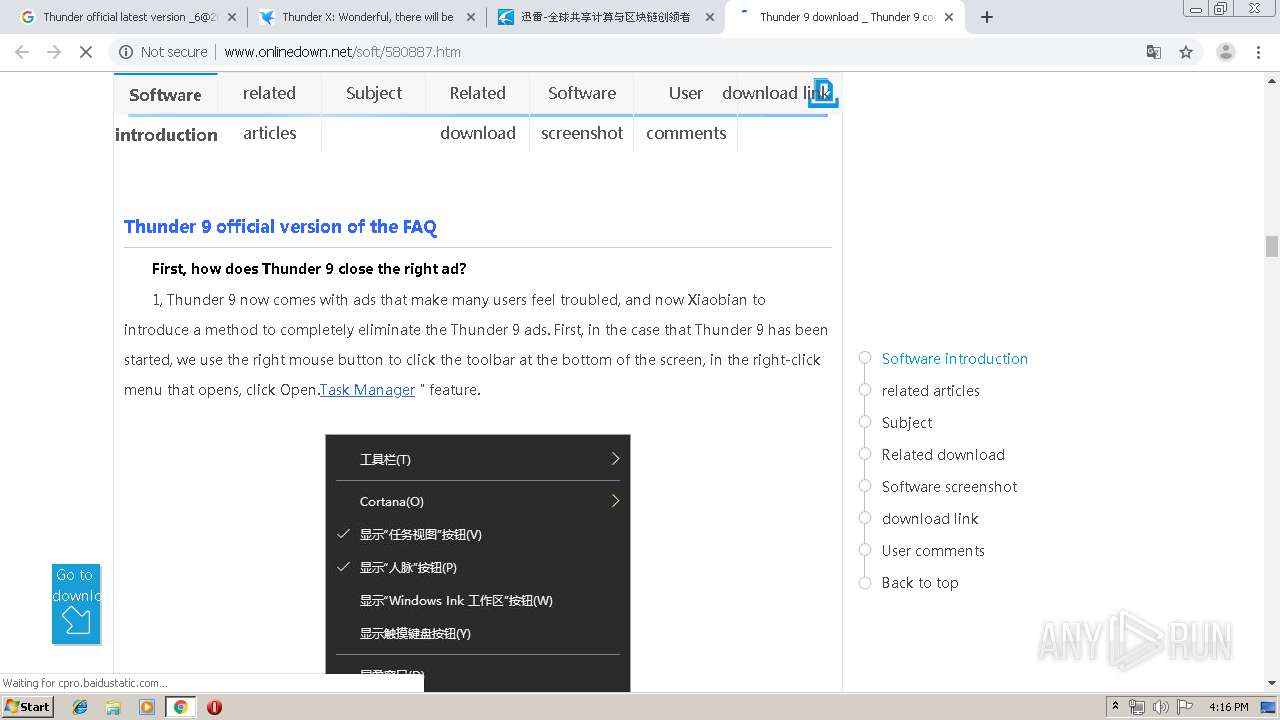
| Title: | Ѹ???????ٷ?????_Ѹ???????ٷ????ء?32λ|64λ??-̫ƽ?????????? |
|---|---|
| referrer: | always |
| Keywords: | Ѹ??????,Ѹ???????ٷ?????,Ѹ??????32λ,Ѹ??????64λ????,Ѹ??????win10 |
| Description: | Ѹ????????Ѹ?ٷ???ʽ????????32λ??64λ??Ѹ??????????Ѹ??ǿ????P2P??Դ?????Ͷ??ص????ؼ??����???ȫ???????????????棬˿??????ʧ???????ٶȡ?????????win10ϵͳ???ܡ?Ѹ????????????ô??????????ǿ????̫ƽ??????????Ϊ???ṩѸ???????ٷ????ء? |
| Author: | author_gz designer_gz |
| renderer: | webkit|ie-comp|ie-stand |
| HTTPEquivMobileAgent: | format=html5; url=//g.pconline.com.cn/dl/pc/65099.html |
| applicableDevice: | pc |
Total processes
120
Monitored processes
72
Malicious processes
11
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 184 | "C:\Users\admin\AppData\Local\Temp\OnlineInstall\10.1.18.500\XunLeiSetup10.1.18.500.exe" /Silent /InstallPath:"C:\Program Files\Thunder Network\Thunder" /ChannelId:100022 /AutoRun | C:\Users\admin\AppData\Local\Temp\OnlineInstall\10.1.18.500\XunLeiSetup10.1.18.500.exe | XunLeiWebSetup10.1.18.500gw.exe | ||||||||||||
User: admin Company: ShenZhen Xunlei Networking Technologies,LTD Integrity Level: HIGH Description: XunLeiSetup10.1.18.500xl Exit code: 0 Version: 10.1.18.500 Modules
| |||||||||||||||
| 272 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1016,2430744627480384416,18124235806640207566,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=13112473740932227434 --renderer-client-id=33 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3144 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 296 | regsvr32 /s "C:\Program Files\Thunder Network\Thunder\BHO\ThunderAgent64.dll" | C:\Windows\system32\regsvr32.exe | — | XunLeiSetup10.1.18.500.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 3 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 812 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=3656 --on-initialized-event-handle=312 --parent-handle=316 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1008 | C:\Windows\system32\svchost -k XLServicePlatform | C:\Windows\system32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1156 | "C:\Program Files\Thunder Network\Thunder\Program\Win7AppId.exe" "C:\Users\admin\AppData\Roaming\Microsoft\Internet Explorer\Quick Launch\User Pinned\TaskBar\迅雷.lnk" "C:\Program Files\Thunder Network\Thunder\Program\Thunder.exe" | C:\Program Files\Thunder Network\Thunder\Program\Win7AppId.exe | — | XunLeiSetup10.1.18.500.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1420 | "C:\Program Files\Thunder Network\Thunder\Program\InstallXLGuard.exe" -i | C:\Program Files\Thunder Network\Thunder\Program\InstallXLGuard.exe | XLWFPSetup.exe | ||||||||||||
User: admin Company: 深圳市迅雷网络技术有限公司 Integrity Level: HIGH Description: XLGUARD驱动安装程序 Exit code: 0 Version: 1, 0, 0, 3 Modules
| |||||||||||||||
| 1468 | "C:\Program Files\Thunder Network\Thunder\Program\XLWFPSetup.exe" /S /PeerID= | C:\Program Files\Thunder Network\Thunder\Program\XLWFPSetup.exe | XunLeiSetup10.1.18.500.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1636 | "C:\Program Files\Thunder Network\Thunder\Program\InstallXLWFP.exe" -i | C:\Program Files\Thunder Network\Thunder\Program\InstallXLWFP.exe | XLWFPSetup.exe | ||||||||||||
User: admin Company: 深圳市迅雷网络技术有限公司 Integrity Level: HIGH Description: XLWFP驱动安装程序 Exit code: 0 Version: 1, 0, 0, 6 Modules
| |||||||||||||||
| 1684 | C:\Windows\system32\netsh.exe advfirewall firewall delete rule name="XLLiveUD" dir=in action=allow program="C:\Users\admin\AppData\Local\Temp\XLLiveUD\Thunder8_10.1.18.500\XLLiveUD.exe" | C:\Windows\system32\netsh.exe | — | XunLeiSetup10.1.18.500.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
3 987
Read events
2 583
Write events
1 385
Delete events
19
Modification events
| (PID) Process: | (2868) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2868) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2868) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2868) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (2868) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2868) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000092000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3336) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}\iexplore |
| Operation: | write | Name: | Type |
Value: 3 | |||
| (PID) Process: | (3336) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}\iexplore |
| Operation: | write | Name: | Count |
Value: 2 | |||
| (PID) Process: | (3336) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}\iexplore |
| Operation: | write | Name: | Time |
Value: E307080005001E000F000E003900E102 | |||
| (PID) Process: | (3336) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}\iexplore |
| Operation: | write | Name: | LoadTime |
Value: 8 | |||
Executable files
232
Suspicious files
239
Text files
893
Unknown types
19
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2868 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2868 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2868 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF2EA08360AE431670.TMP | — | |
MD5:— | SHA256:— | |||
| 2868 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF6548F8E02B2A8D8E.TMP | — | |
MD5:— | SHA256:— | |||
| 2868 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF4F149E5ED2823C0B.TMP | — | |
MD5:— | SHA256:— | |||
| 2868 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFC090105BEB8AB463.TMP | — | |
MD5:— | SHA256:— | |||
| 2868 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\RecoveryStore.{ECBF10A7-CB38-11E9-B86F-5254004A04AF}.dat | — | |
MD5:— | SHA256:— | |||
| 3660 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\63631f8f-ee7e-4431-a343-bcb76fc3372d.tmp | — | |
MD5:— | SHA256:— | |||
| 2868 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Last Active\RecoveryStore.{F7701C3C-CB38-11E9-B86F-5254004A04AF}.dat | binary | |
MD5:— | SHA256:— | |||
| 3660 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000020.dbtmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
264
TCP/UDP connections
196
DNS requests
173
Threats
74
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3600 | chrome.exe | GET | 200 | 171.8.242.178:80 | http://x.xunlei.com/ | CN | html | 2.63 Kb | suspicious |
3600 | chrome.exe | GET | 200 | 171.8.242.178:80 | http://x.xunlei.com/css/reset-min-1.3.css?v=7316509d27358f310534b0084ff56d51 | CN | text | 1.09 Kb | suspicious |
3600 | chrome.exe | GET | 200 | 171.8.242.178:80 | http://x.xunlei.com/images/skin/star.png?v=9fea25c42354ae6fca7d3e2cb1555de3 | CN | image | 161 Kb | suspicious |
3600 | chrome.exe | GET | 200 | 171.8.242.178:80 | http://x.xunlei.com/images/skin/black.png?v=df630b54658aea5da21f1f22c7b89913 | CN | image | 19.9 Kb | suspicious |
3600 | chrome.exe | GET | 200 | 171.8.242.178:80 | http://x.xunlei.com/css/index.css?v=b29a2d7d2ed5547ddddc59aa2c4e7df8 | CN | text | 4.50 Kb | suspicious |
3600 | chrome.exe | GET | 200 | 171.8.242.178:80 | http://x.xunlei.com/img/banner/bg.png?v=9a2870f8d46396a2524ade437c84885a | CN | image | 355 Kb | suspicious |
3600 | chrome.exe | GET | 200 | 171.8.242.178:80 | http://x.xunlei.com/images/skin/blue.png?v=fbc9a292d484e19647f2845d3c539ae1 | CN | image | 27.0 Kb | suspicious |
3600 | chrome.exe | GET | 200 | 171.8.242.178:80 | http://x.xunlei.com/js/vendors.js?v=652291880aaf2f378c0c10fea8394ab1 | CN | text | 170 Kb | suspicious |
3600 | chrome.exe | GET | 200 | 171.8.242.178:80 | http://x.xunlei.com/img/banner/star.png?v=b087ad4b73b714b1e73d081e59cbcee6 | CN | image | 247 Kb | suspicious |
3600 | chrome.exe | GET | 200 | 171.8.242.178:80 | http://x.xunlei.com/img/banner/bird.png?v=bd8e14d42ed081993dffbb139c330bc0 | CN | image | 314 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3600 | chrome.exe | 216.58.207.68:443 | www.google.com | Google Inc. | US | whitelisted |
3600 | chrome.exe | 172.217.21.238:443 | clients2.google.com | Google Inc. | US | whitelisted |
3600 | chrome.exe | 172.217.18.3:443 | www.google.co.uk | Google Inc. | US | whitelisted |
3600 | chrome.exe | 172.217.22.1:443 | clients2.googleusercontent.com | Google Inc. | US | whitelisted |
3600 | chrome.exe | 172.217.22.110:80 | redirector.gvt1.com | Google Inc. | US | whitelisted |
4 | System | 163.171.132.220:445 | www.pconline.com.cn | — | US | malicious |
2868 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
4 | System | 163.171.140.176:445 | js.3conline.com | — | US | unknown |
4 | System | 163.171.132.220:139 | www.pconline.com.cn | — | US | malicious |
4 | System | 163.171.138.119:445 | js.3conline.com | — | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.pconline.com.cn |
| suspicious |
www.bing.com |
| whitelisted |
js.3conline.com |
| suspicious |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com.ua |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3600 | chrome.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
— | — | Potential Corporate Privacy Violation | ET P2P BitTorrent DHT ping request |
2948 | DownloadSDKServer.exe | Unknown Traffic | ET INFO Suspicious User-Agent (1 space) |
2948 | DownloadSDKServer.exe | Unknown Traffic | ET INFO Suspicious User-Agent (1 space) |
2948 | DownloadSDKServer.exe | Unknown Traffic | ET INFO Suspicious User-Agent (1 space) |
2948 | DownloadSDKServer.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2948 | DownloadSDKServer.exe | Unknown Traffic | ET INFO Suspicious User-Agent (1 space) |
2948 | DownloadSDKServer.exe | Unknown Traffic | ET INFO Suspicious User-Agent (1 space) |
2948 | DownloadSDKServer.exe | Unknown Traffic | ET INFO Suspicious User-Agent (1 space) |
2948 | DownloadSDKServer.exe | Unknown Traffic | ET INFO Suspicious User-Agent (1 space) |
34 ETPRO signatures available at the full report
Process | Message |
|---|---|
XLWFPSetup.exe | LJ GetOptionValueFromParamters CodePage = 437, CodePageName = 437 (OEM - United States)
|
XLWFPSetup.exe | LJ CPInfoEx.CodePage = 936 pOptionValue after Unicode to GBK ArgValue = |
XLWFPSetup.exe | 1.0.0.11 |
regsvr32.exe | [1804:2324] [16:19 41] Debug <np_tdieplat.dll> [osshell.cpp:270 Xunlei::Platform::OSShell::GetAppDatalowPath] using SHGetKnownFolderPath with FOLDERID_LocalAppDataLow
|
regsvr32.exe | [1804:2324] [16:19 41] Message <np_tdieplat.dll> [osshell.cpp:39 Xunlei::Platform::OSShell::InstallRuntime] Initializing running environment ...
|
regsvr32.exe | [1804:2324] [16:19 41] Debug <np_tdieplat.dll> [osshell.cpp:49 Xunlei::Platform::OSShell::InstallRuntime] Current environment directories C:\ProgramData\Oracle\Java\javapath;C:\Windows\system32;C:\Windows;C:\Windows\System32\Wbem;C:\Windows\System32\WindowsPowerShell\v1.0\
|
regsvr32.exe | [1804:2324] [16:19 41] Debug <np_tdieplat.dll> [osshell.cpp:56 Xunlei::Platform::OSShell::InstallRuntime] Adding local module directory C:\Program Files\Thunder Network\Thunder\Thunder BHO Platform to work environment
|
regsvr32.exe | [1804:2324] [16:19 41] Debug <np_tdieplat.dll> [osshell.cpp:75 Xunlei::Platform::OSShell::InstallRuntime] Adding C:\Program Files\Thunder Network\Thunder\Thunder BHO Platform to environment
|
regsvr32.exe | [1804:2324] [16:19 41] Debug <np_tdieplat.dll> [osshell.cpp:103 Xunlei::Platform::OSShell::InstallRuntime] --------------- Current Environment --------------
|
regsvr32.exe | [1804:2324] [16:19 41] Debug <np_tdieplat.dll> [osshell.cpp:270 Xunlei::Platform::OSShell::GetAppDatalowPath] using SHGetKnownFolderPath with FOLDERID_LocalAppDataLow
|