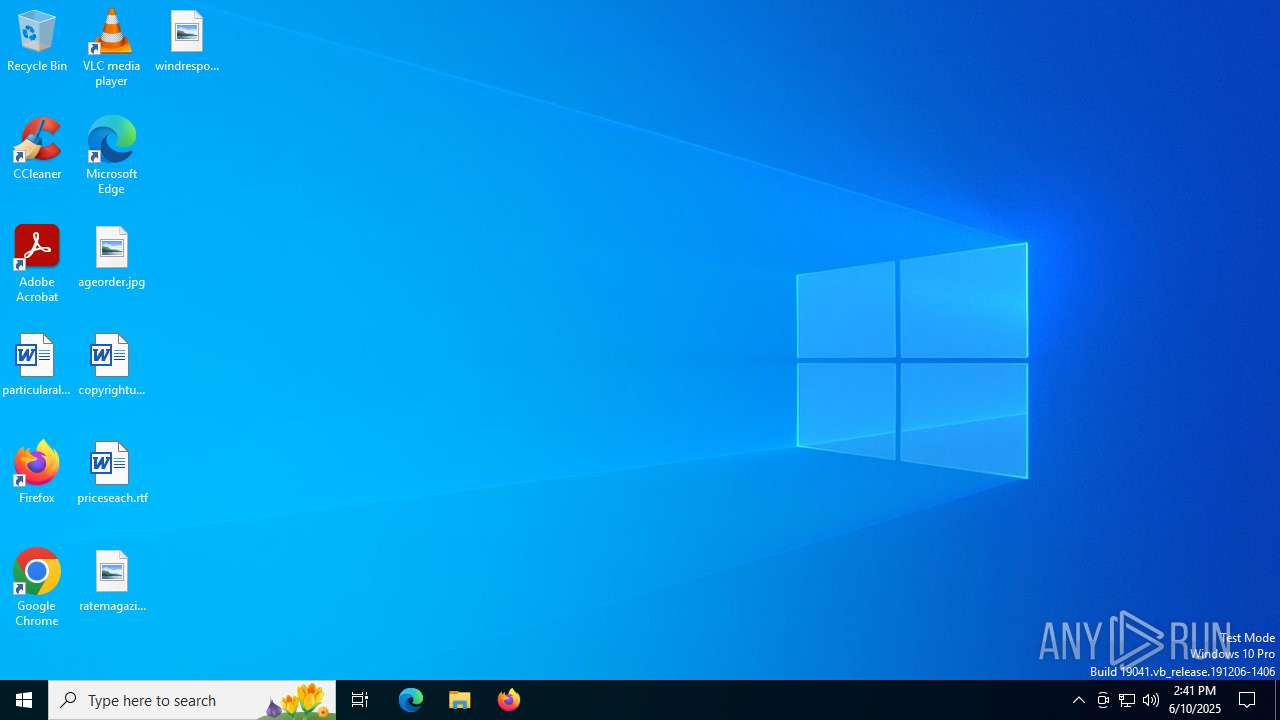
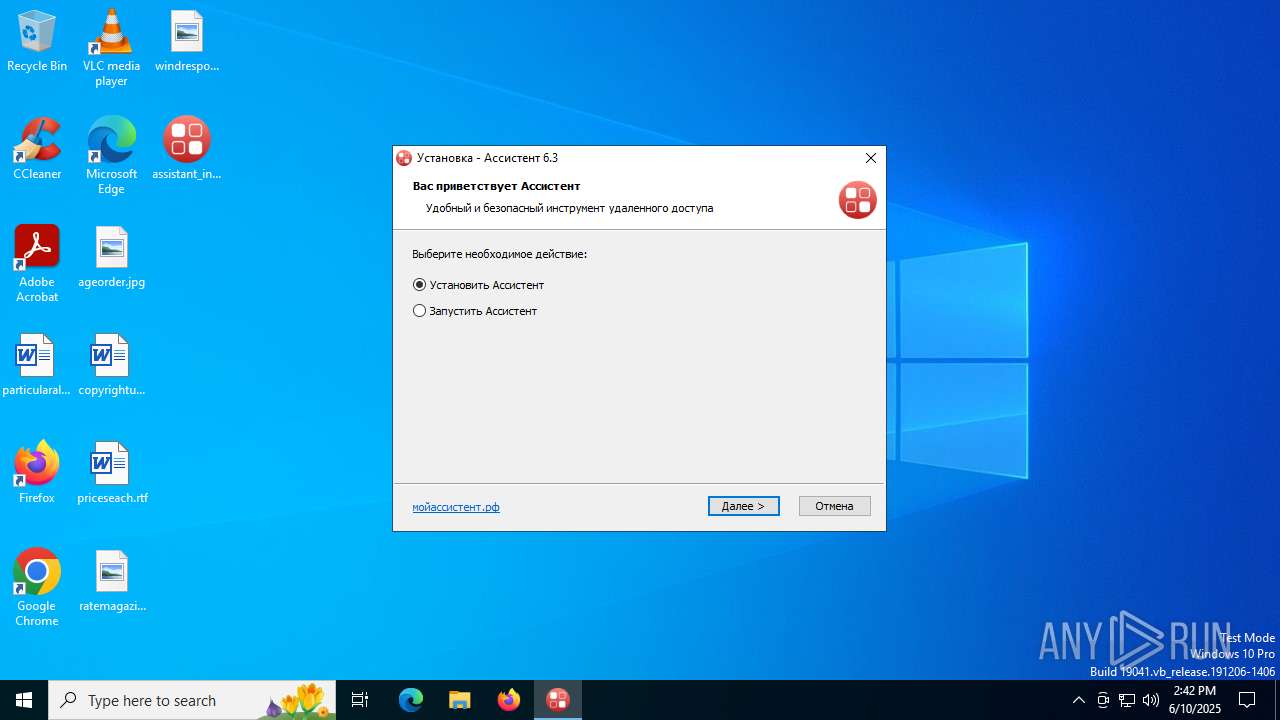
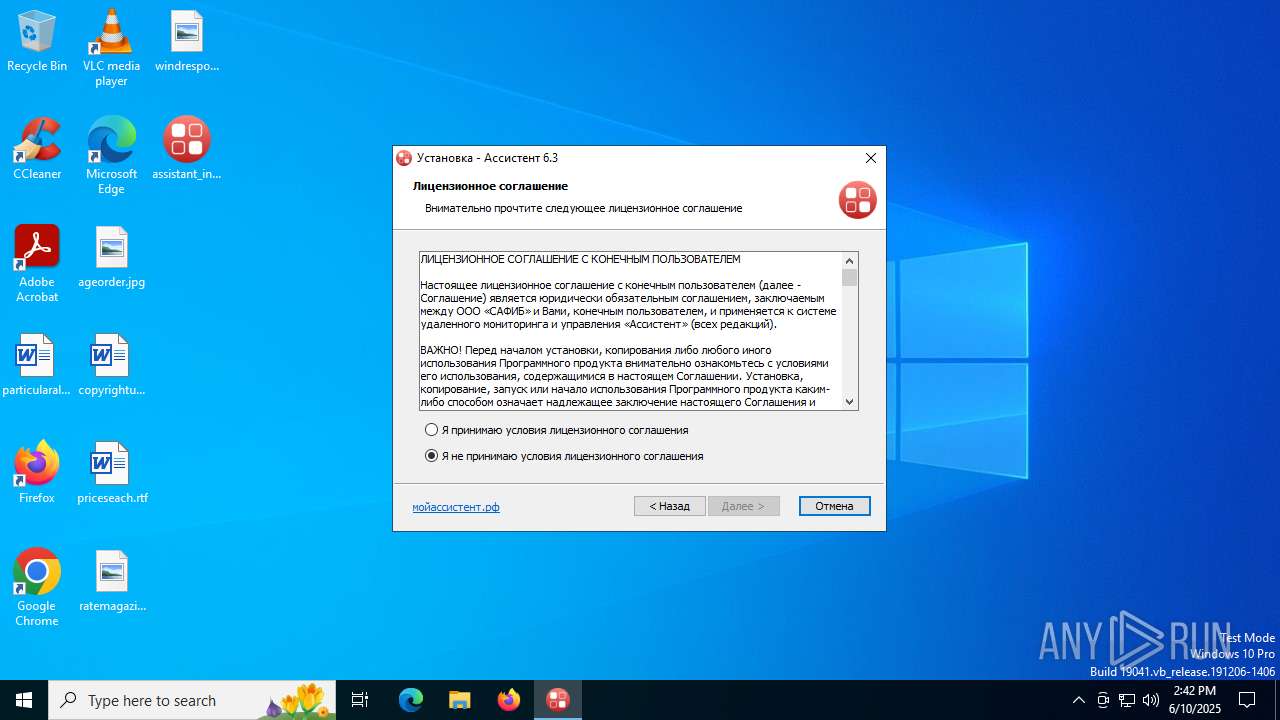
| File name: | assistant_install_6.exe |
| Full analysis: | https://app.any.run/tasks/a069db7a-436d-4751-ab88-6c938a98989f |
| Verdict: | Malicious activity |
| Analysis date: | June 10, 2025, 14:41:46 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | B514FEF229F12B3A364B9152497FE6FE |
| SHA1: | 2F212E6DAA612C19F2560E352BA1372D602DAD86 |
| SHA256: | 0180E9A8FCD9AB30692138F3D7D6434ECC984944C277ADB6DFAAD77D6A105B5E |
| SSDEEP: | 196608:Z+SgJdzV2+SZgYSflTbY9BgPfOaZI3vhQWJvBtmJ+STXpA3BOyn:uJdzdzflMBgOaK3vhQEvzV3BOg |
MALICIOUS
No malicious indicators.SUSPICIOUS
ADVANCEDINSTALLER mutex has been found
- assistant_install_6.exe (PID: 1944)
Reads security settings of Internet Explorer
- assistant_install_6.exe (PID: 1944)
Executable content was dropped or overwritten
- assistant_install_6.exe (PID: 1944)
Process drops legitimate windows executable
- assistant_install_6.exe (PID: 1944)
Reads the Windows owner or organization settings
- assistant_install_6.exe (PID: 1944)
Reads Internet Explorer settings
- assistant_install_6.exe (PID: 1944)
Detects AdvancedInstaller (YARA)
- assistant_install_6.exe (PID: 1944)
There is functionality for taking screenshot (YARA)
- assistant_install_6.exe (PID: 1944)
INFO
The sample compiled with russian language support
- assistant_install_6.exe (PID: 1944)
Checks supported languages
- assistant_install_6.exe (PID: 1944)
- msiexec.exe (PID: 6688)
- msiexec.exe (PID: 2520)
Reads the computer name
- assistant_install_6.exe (PID: 1944)
- msiexec.exe (PID: 6688)
- msiexec.exe (PID: 2520)
Reads the machine GUID from the registry
- assistant_install_6.exe (PID: 1944)
Reads Environment values
- assistant_install_6.exe (PID: 1944)
- msiexec.exe (PID: 2520)
Creates files or folders in the user directory
- assistant_install_6.exe (PID: 1944)
Checks proxy server information
- assistant_install_6.exe (PID: 1944)
- slui.exe (PID: 3720)
Reads the software policy settings
- assistant_install_6.exe (PID: 1944)
- slui.exe (PID: 3720)
The sample compiled with english language support
- assistant_install_6.exe (PID: 1944)
Create files in a temporary directory
- assistant_install_6.exe (PID: 1944)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:07:23 10:22:26+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.14 |
| CodeSize: | 1201664 |
| InitializedDataSize: | 625152 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xdb6d9 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 6.3.2503.1806 |
| ProductVersionNumber: | 6.3.2503.1806 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Debug |
| FileOS: | Win32 |
| ObjectFileType: | Dynamic link library |
| FileSubtype: | - |
| LanguageCode: | Russian |
| CharacterSet: | Unicode |
| CompanyName: | САФИБ |
| FileDescription: | Ассистент 6.3 Installer |
| FileVersion: | 6.3.2503.1806 |
| InternalName: | assistant_install_6 |
| LegalCopyright: | Copyright (C) 2025 САФИБ |
| OriginalFileName: | assistant_install_6.exe |
| ProductName: | Ассистент 6.3 |
| ProductVersion: | 6.3.2503.1806 |
Total processes
135
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1944 | "C:\Users\admin\Desktop\assistant_install_6.exe" | C:\Users\admin\Desktop\assistant_install_6.exe | explorer.exe | ||||||||||||
User: admin Company: САФИБ Integrity Level: MEDIUM Description: Ассистент 6.3 Installer Version: 6.3.2503.1806 Modules
| |||||||||||||||
| 2520 | C:\Windows\syswow64\MsiExec.exe -Embedding 95EE737891A30703AA9745229102620C C | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3720 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6688 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
7 152
Read events
7 151
Write events
1
Delete events
0
Modification events
| (PID) Process: | (2520) msiexec.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Script\Settings |
| Operation: | write | Name: | JITDebug |
Value: 0 | |||
Executable files
16
Suspicious files
2
Text files
16
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1944 | assistant_install_6.exe | C:\Users\admin\AppData\Roaming\САФИБ\Ассистент 6.3 6.3.2503.1806\install\2095095\__4_ast_install.msi | executable | |
MD5:B106AA1F9D43DD7CF604BD0404C9F38D | SHA256:A0F58A2C7A7FD7D0ACF62292D26FBDDE18B44E55283FDD16AC1DE2AFE7EF86F2 | |||
| 1944 | assistant_install_6.exe | C:\Users\admin\AppData\Roaming\САФИБ\Ассистент 6.3 6.3.2503.1806\install\decoder.dll | executable | |
MD5:0D219A13EA4DB9FC7A9DED2E646EF6DC | SHA256:08E5EFFA4E03563DF4B418E859E5A05B8EDEE1D037E4A0E8947663667F8D9C03 | |||
| 1944 | assistant_install_6.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\9CB4373A4252DE8D2212929836304EC5_6C354C532D063DF5607A63BA827F5164 | binary | |
MD5:274FF3B33AE0C10A43677C3C6C0AB39E | SHA256:CAC64A129A5E5826236D4E3B06E3CEA2E292227A0836124CD6AA141FE5EC2DB7 | |||
| 1944 | assistant_install_6.exe | C:\Users\admin\AppData\Local\Temp\shi785C.tmp | executable | |
MD5:84A34BF3486F7B9B7035DB78D78BDD1E | SHA256:F85911C910B660E528D2CF291BAA40A92D09961996D6D84E7A53A7095C7CD96E | |||
| 1944 | assistant_install_6.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\A1D627669EFC8CD4F21BCF387D97F9B5_4BBFCAC9D91CE3A3AB439593958CD41C | binary | |
MD5:6549783DF84C4D8DA8ABA0001DD13008 | SHA256:51048F0695CA943A0019881DEBF84E968F1526F7EA7AB45DF71B7212073B2142 | |||
| 1944 | assistant_install_6.exe | C:\Users\admin\AppData\Local\Temp\MSI78EB.tmp | executable | |
MD5:6B2590DF5E5C28C0765161EA334108A5 | SHA256:6DD214389728CA6D66E2A2DAF23A700060C0389447EABCBA8BE3157D2BDBFDB7 | |||
| 1944 | assistant_install_6.exe | C:\Users\admin\AppData\Local\Temp\MSI7969.tmp | executable | |
MD5:6B2590DF5E5C28C0765161EA334108A5 | SHA256:6DD214389728CA6D66E2A2DAF23A700060C0389447EABCBA8BE3157D2BDBFDB7 | |||
| 1944 | assistant_install_6.exe | C:\Users\admin\AppData\Local\Temp\MSI799B.tmp | executable | |
MD5:6B2590DF5E5C28C0765161EA334108A5 | SHA256:6DD214389728CA6D66E2A2DAF23A700060C0389447EABCBA8BE3157D2BDBFDB7 | |||
| 1944 | assistant_install_6.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\A1D627669EFC8CD4F21BCF387D97F9B5_4BBFCAC9D91CE3A3AB439593958CD41C | der | |
MD5:25A6EC690E1243B72B5343BF72FDD120 | SHA256:3926CC2955E3607DE87D7F5F22EFC4E3A454D98575183A116CA0AB8A8CB2FC6A | |||
| 1944 | assistant_install_6.exe | C:\Users\admin\AppData\Local\Temp\MSI7979.tmp | executable | |
MD5:6B2590DF5E5C28C0765161EA334108A5 | SHA256:6DD214389728CA6D66E2A2DAF23A700060C0389447EABCBA8BE3157D2BDBFDB7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
24
DNS requests
9
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
888 | RUXIMICS.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
888 | RUXIMICS.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1944 | assistant_install_6.exe | GET | 200 | 104.18.21.226:80 | http://ocsp.globalsign.com/gsgccr45codesignca2020/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBTLuA3ygnKW%2F7xuSx%2F09F%2BhHVuEUQQU2rONwCSQo2t30wygWd0hZ2R2C3gCDCoQw2QHz77gdbW5tA%3D%3D | unknown | — | — | whitelisted |
1944 | assistant_install_6.exe | GET | 200 | 104.18.21.226:80 | http://ocsp.globalsign.com/codesigningrootr45/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQVFZP5vqhCrtRN5SWf40Rn6NM1IAQUHwC%2FRoAK%2FHg5t6W0Q9lWULvOljsCEHe9DgOhtwj4VKsGchDZBEc%3D | unknown | — | — | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
2940 | svchost.exe | GET | 200 | 23.209.209.135:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
888 | RUXIMICS.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
888 | RUXIMICS.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
888 | RUXIMICS.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ocsp.globalsign.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |