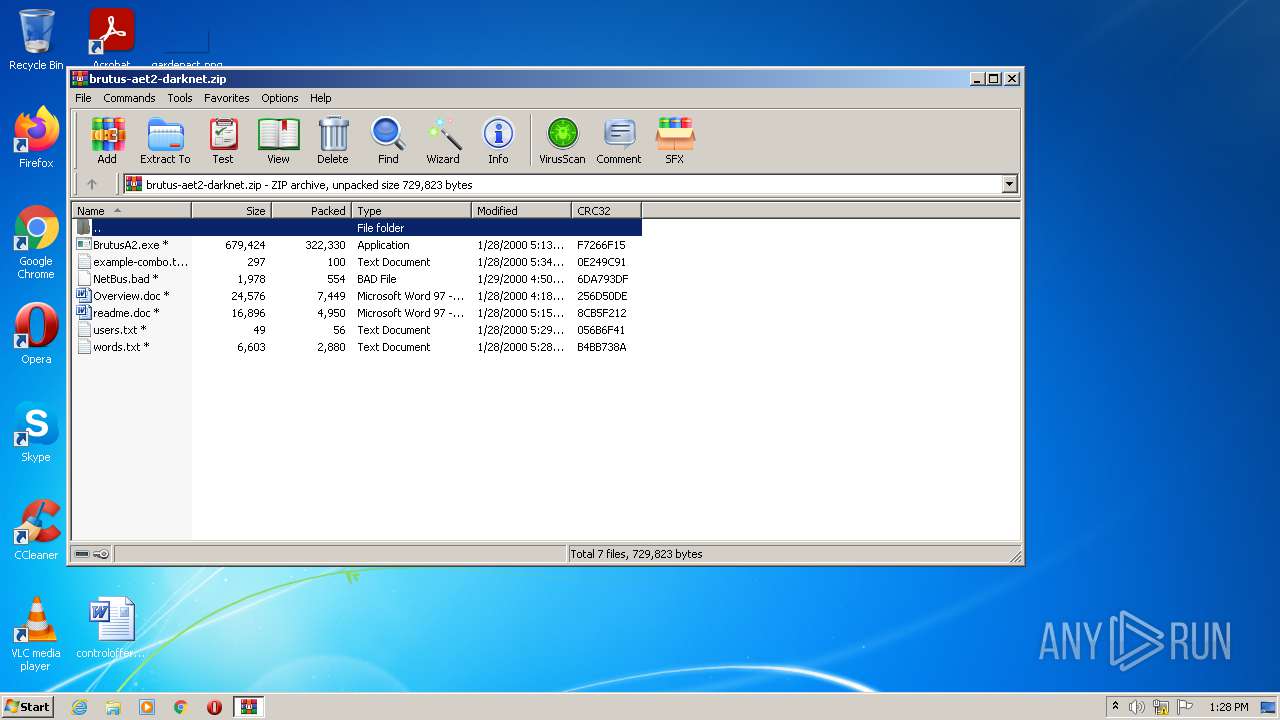
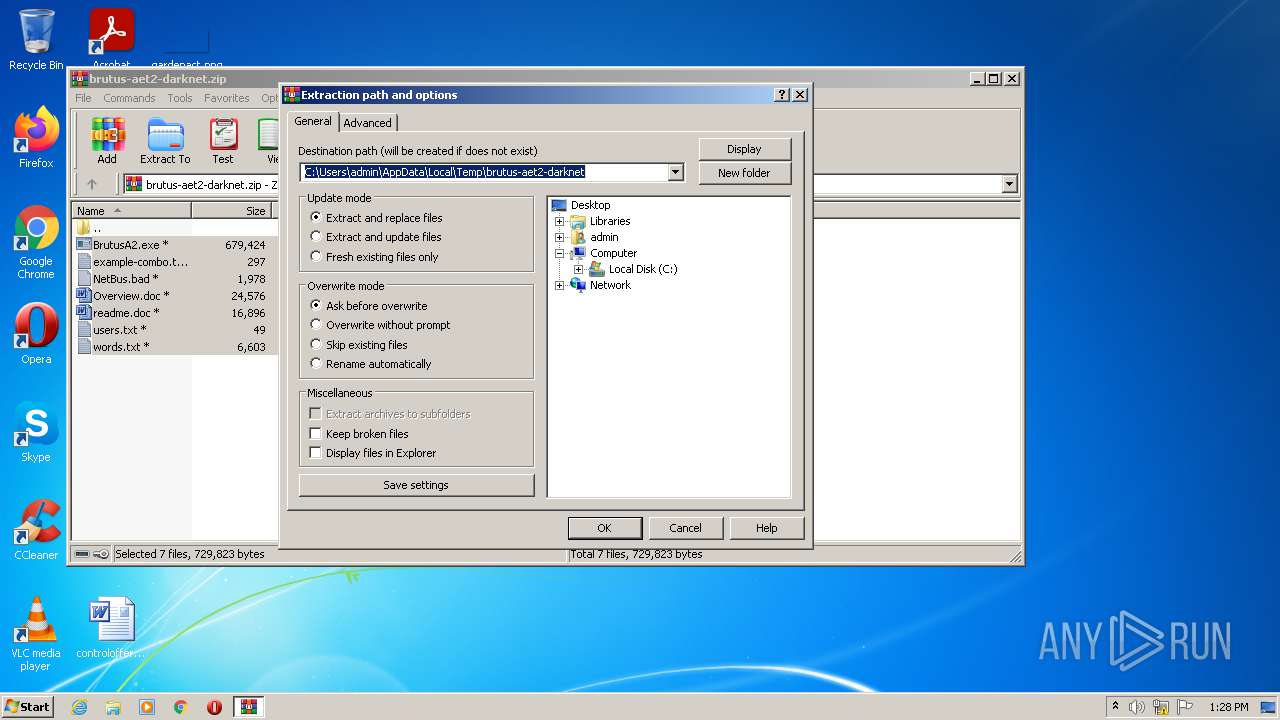
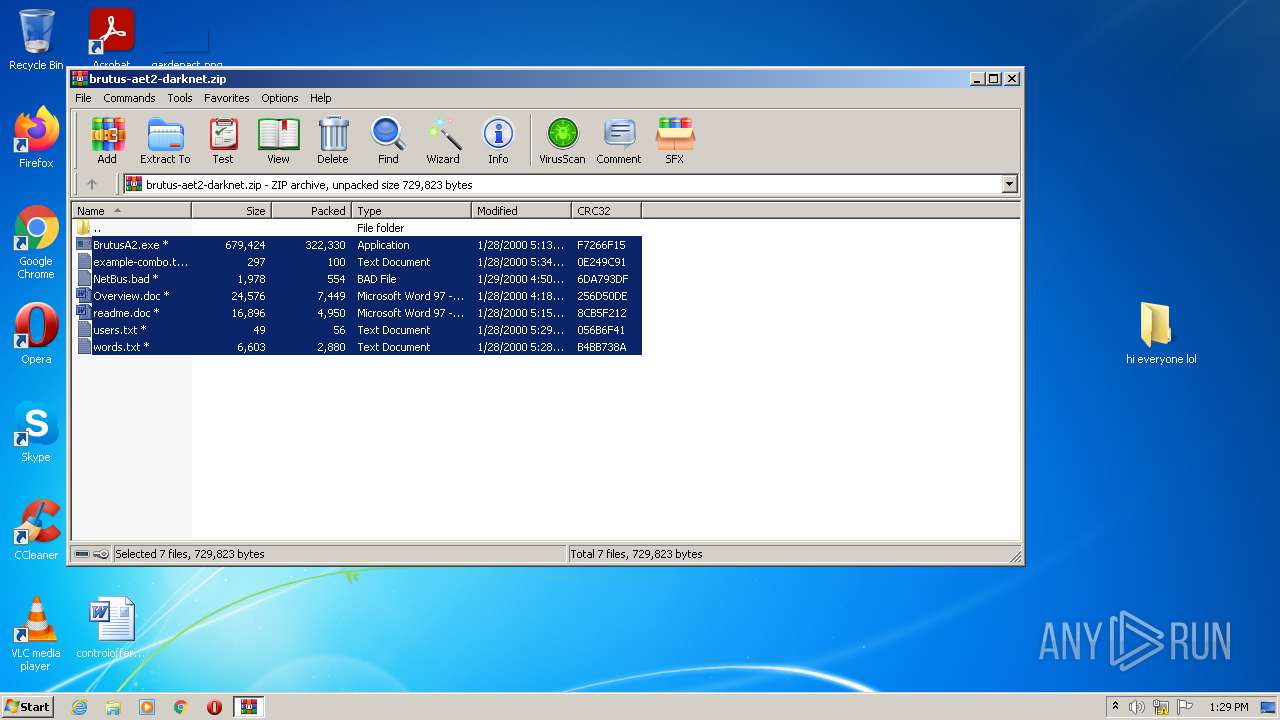
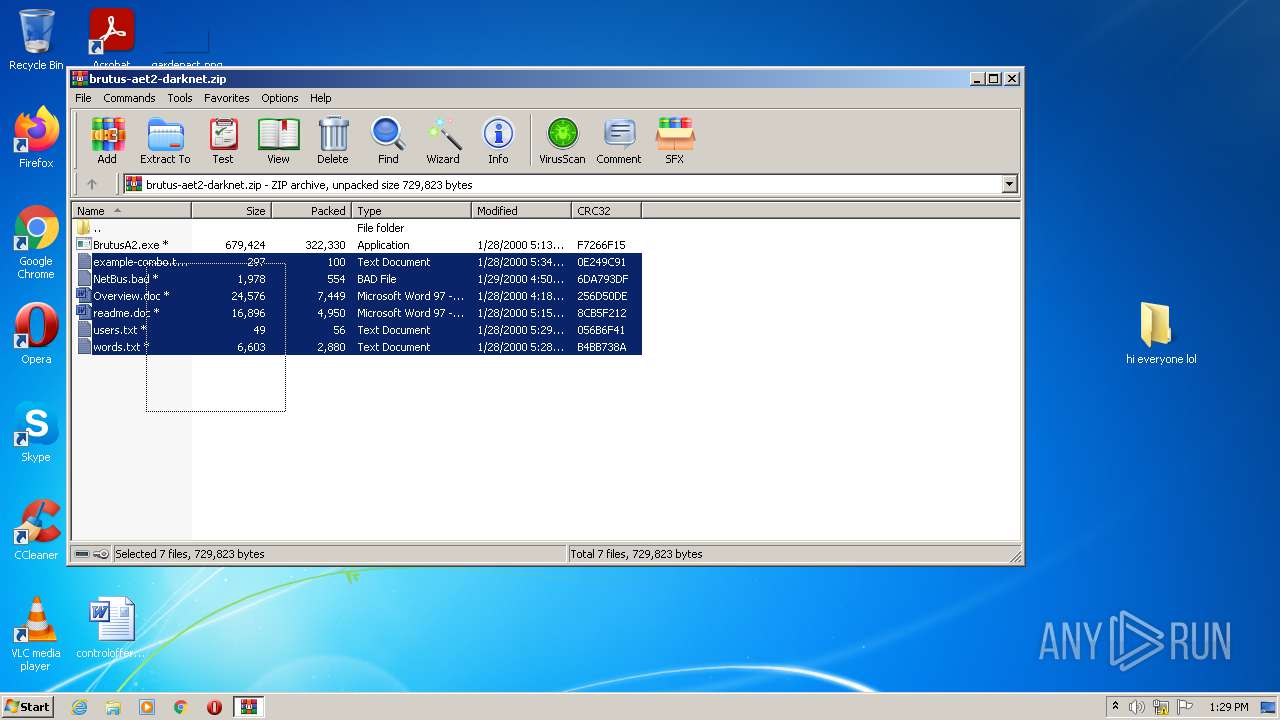
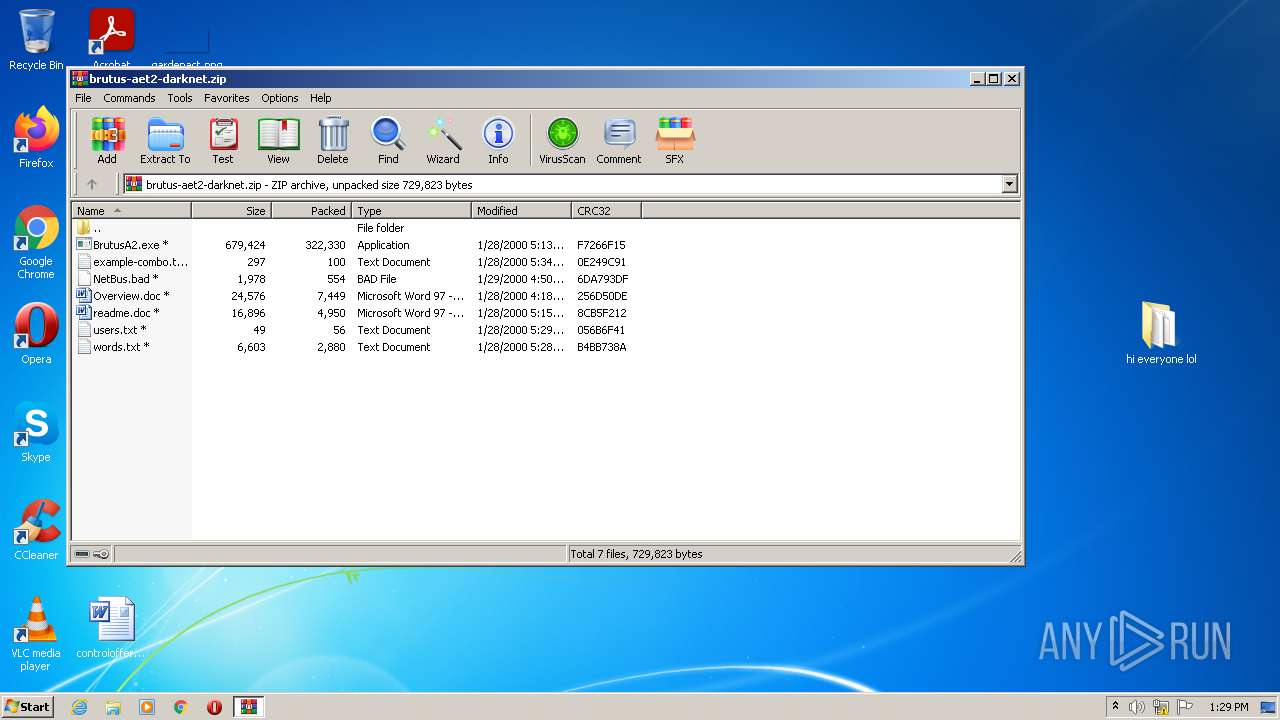
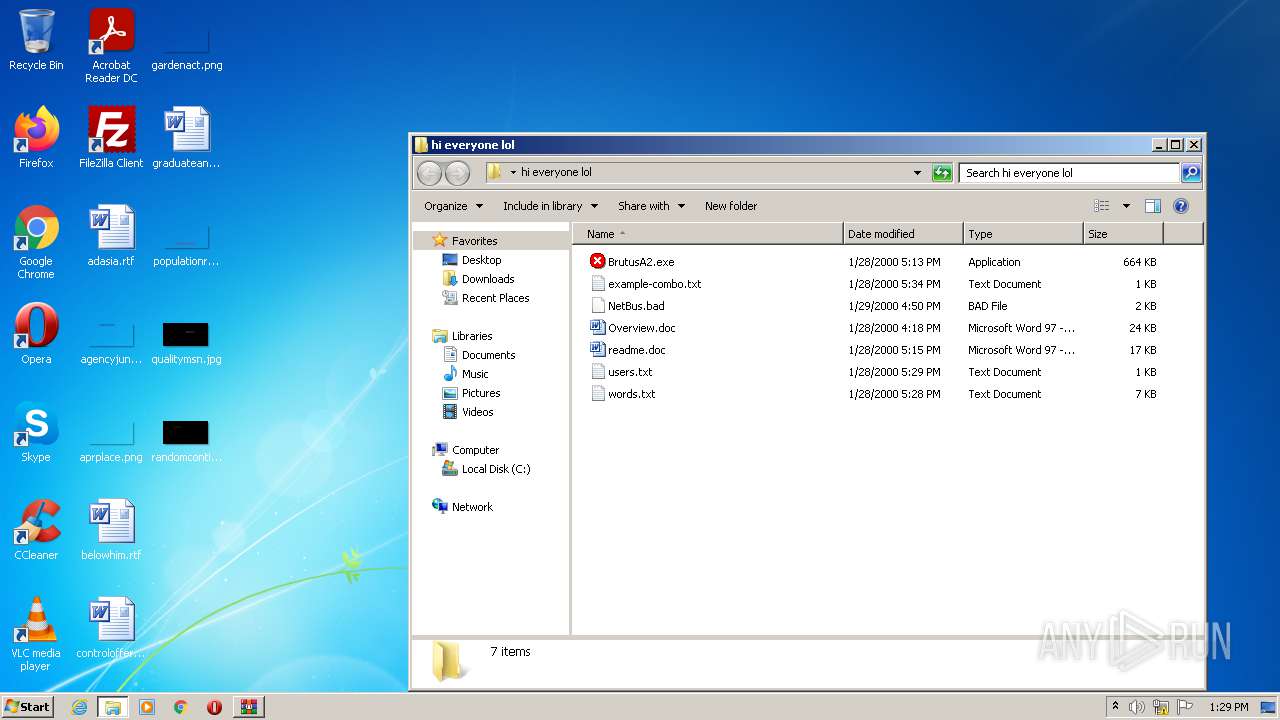
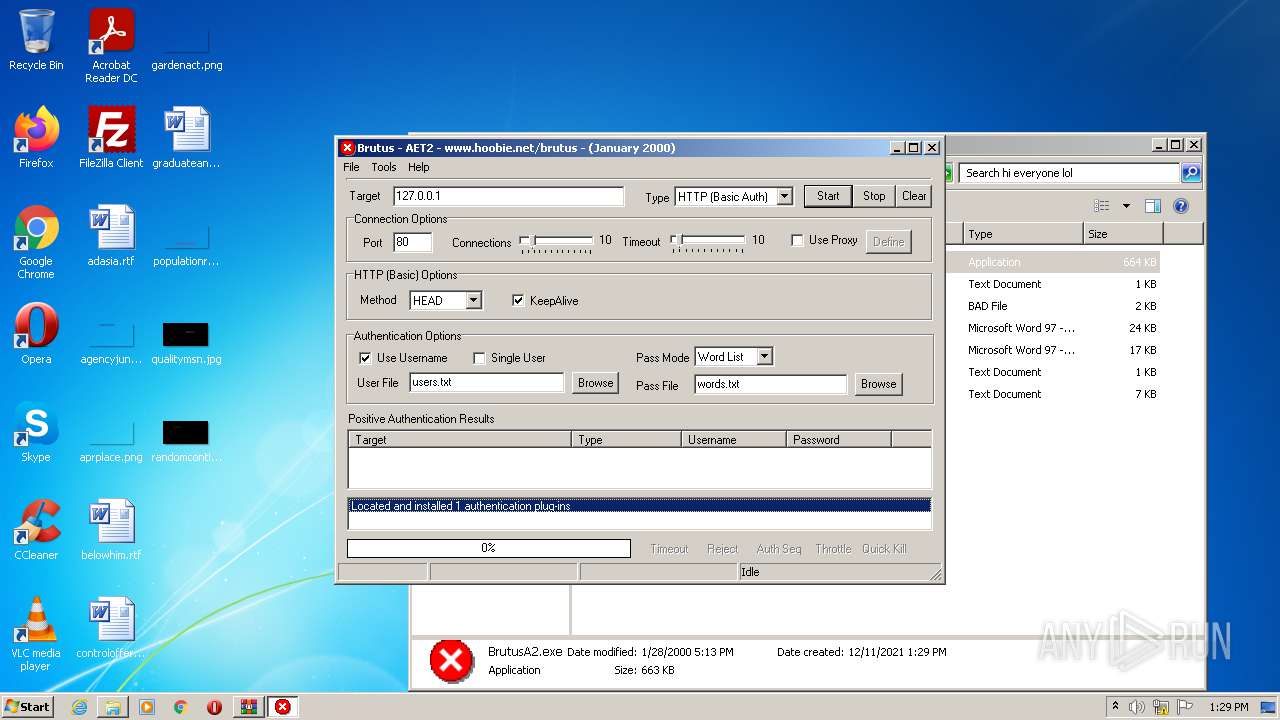
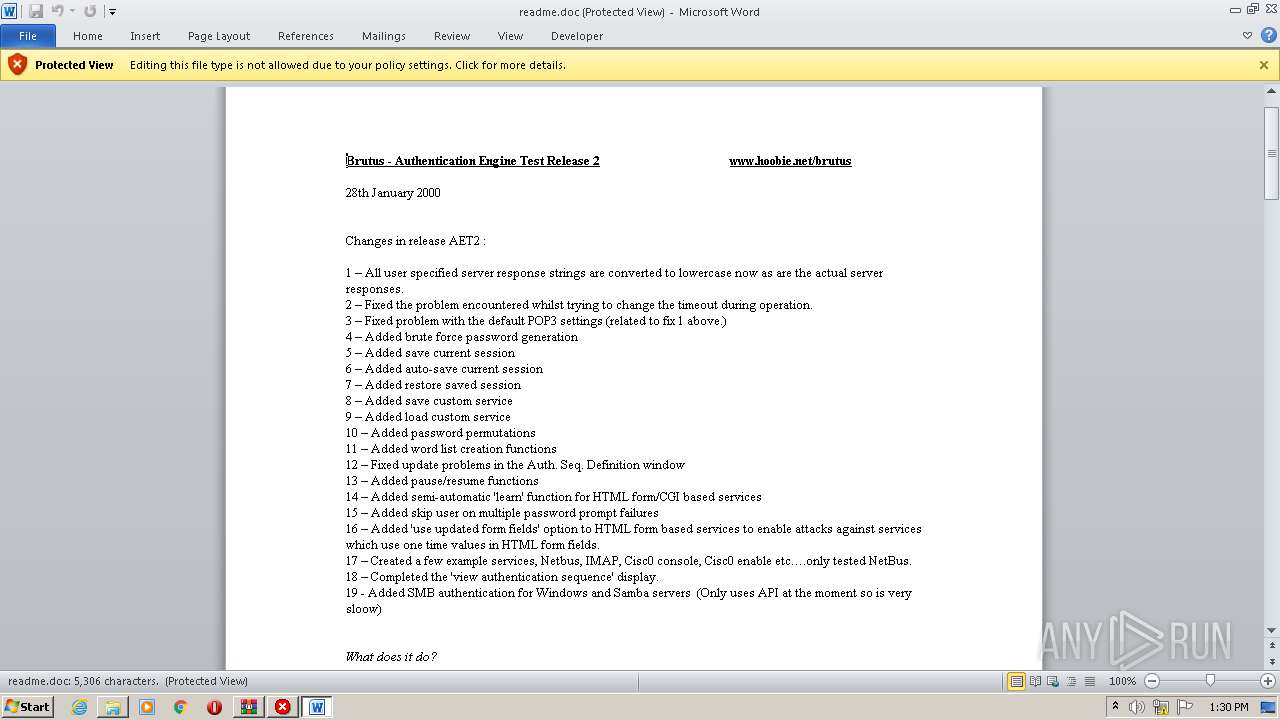
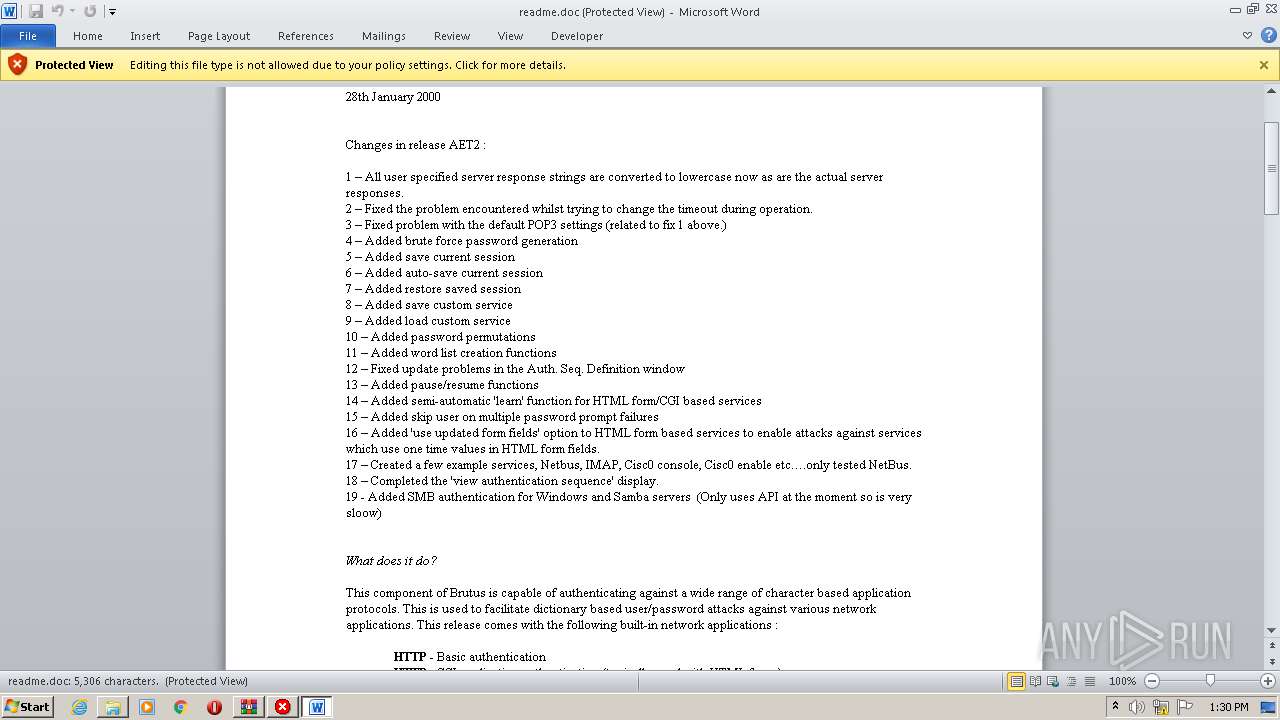
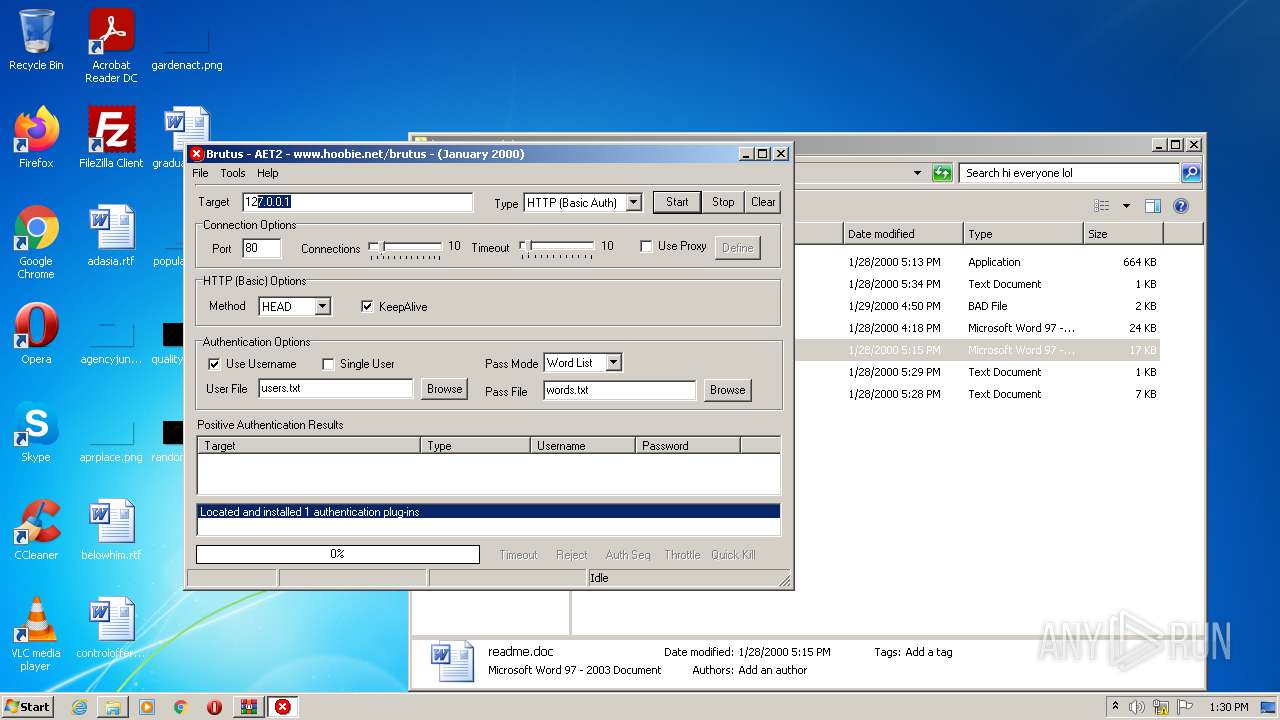
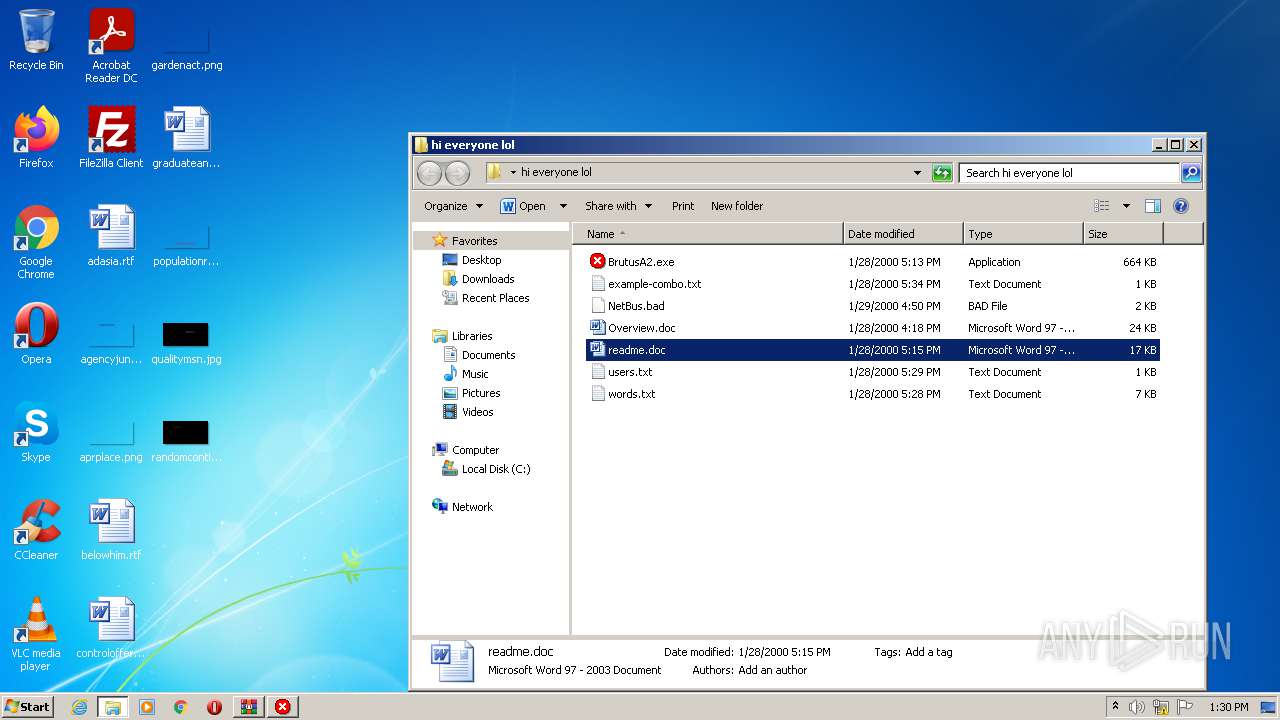
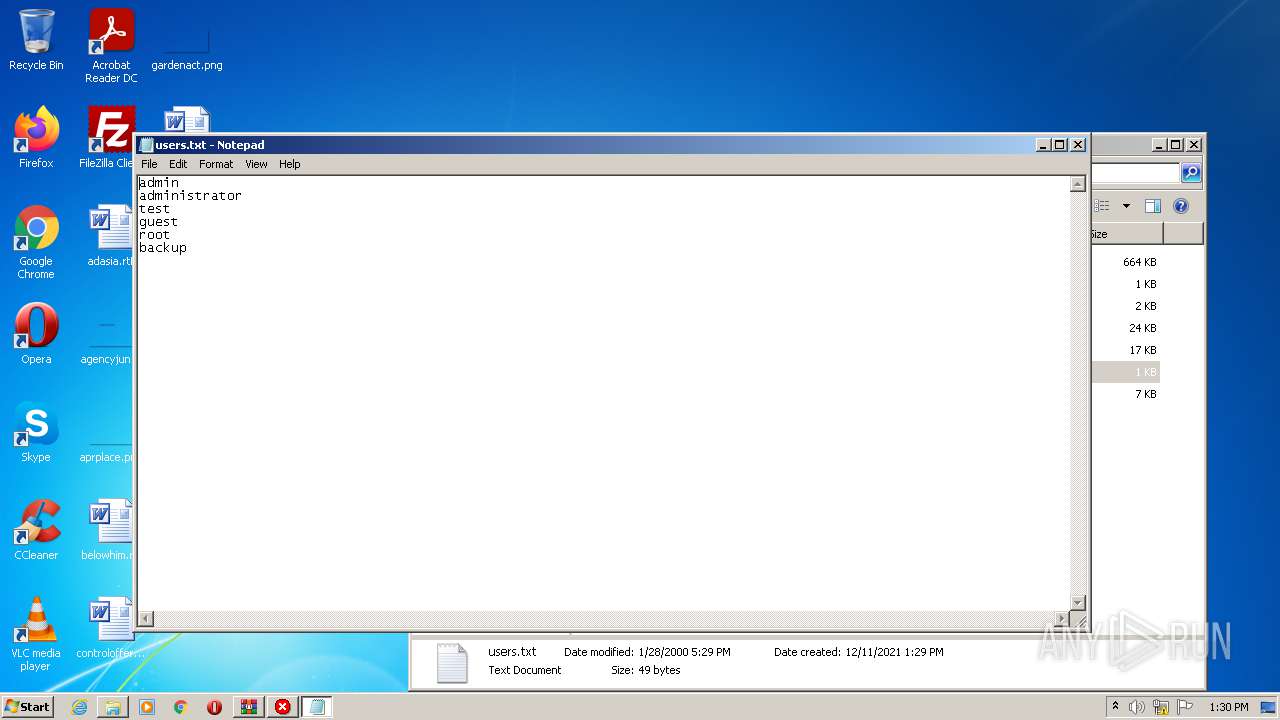
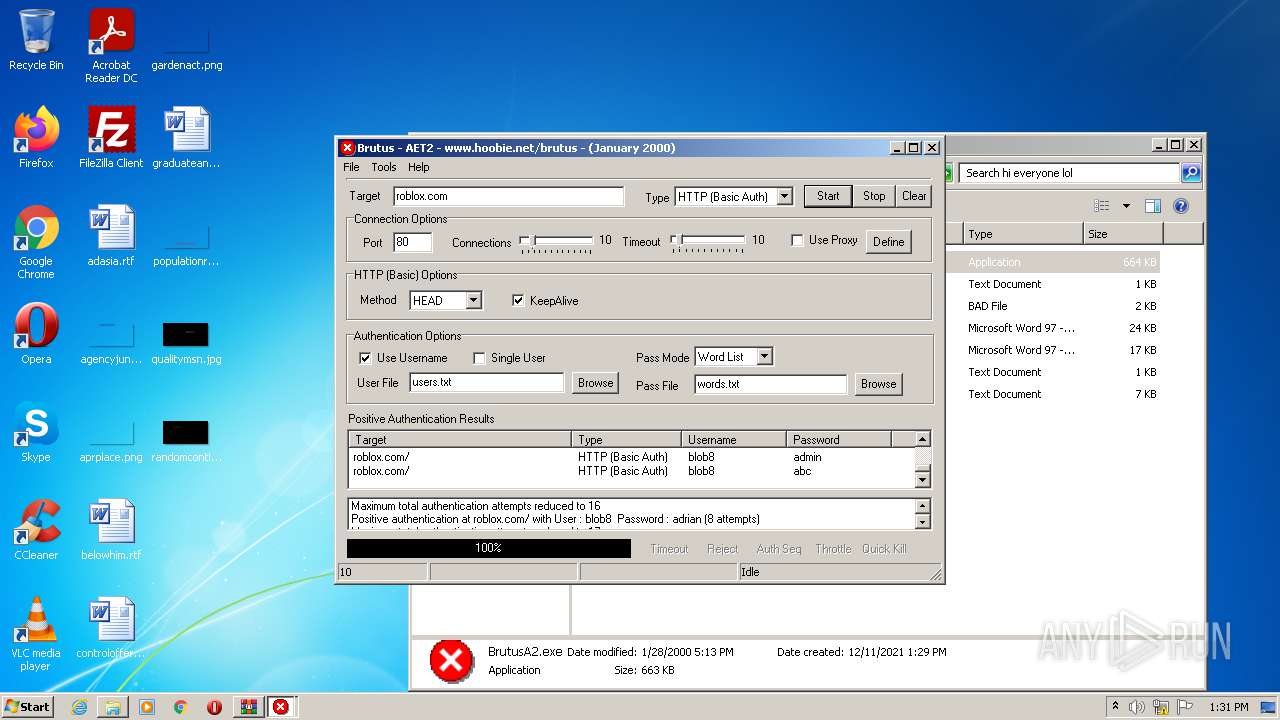
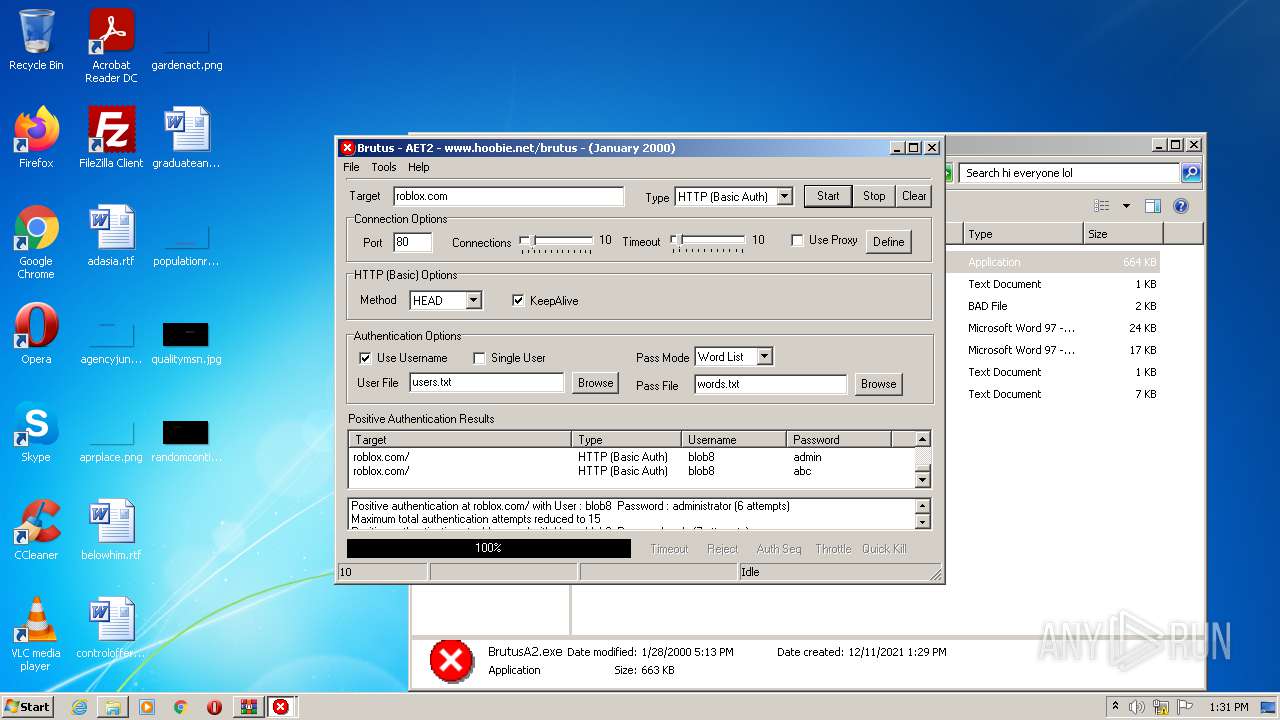
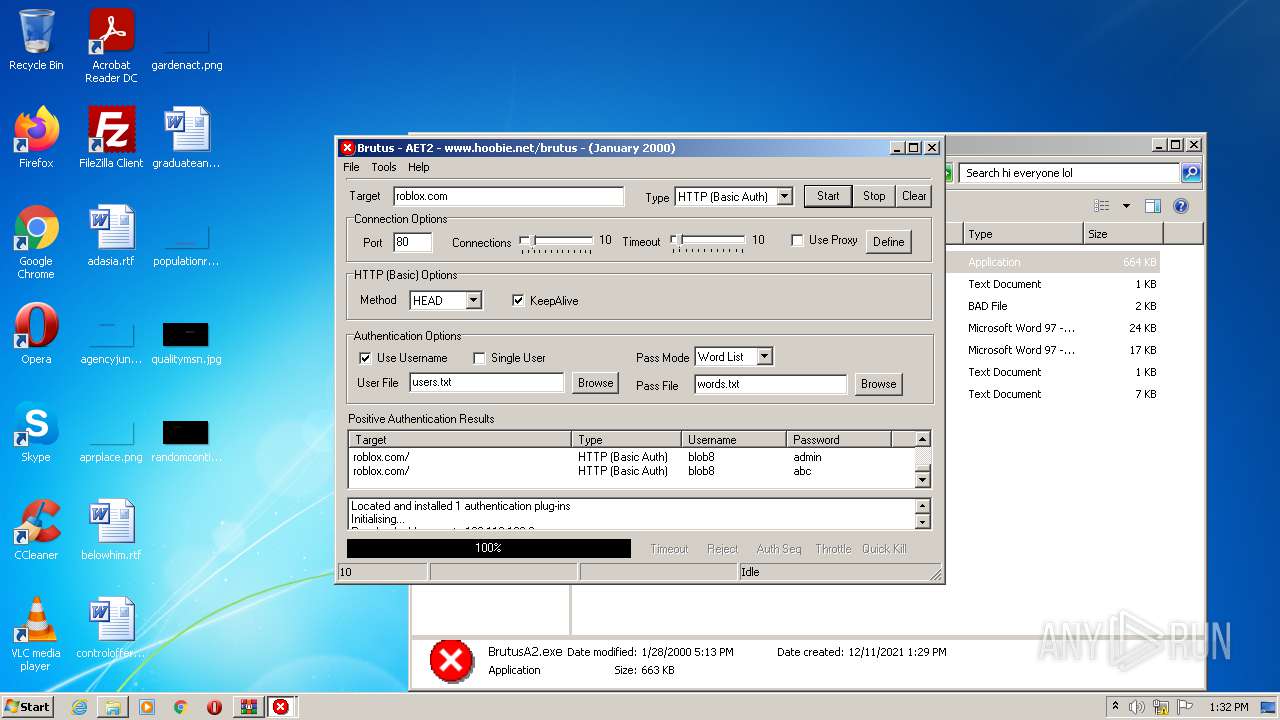
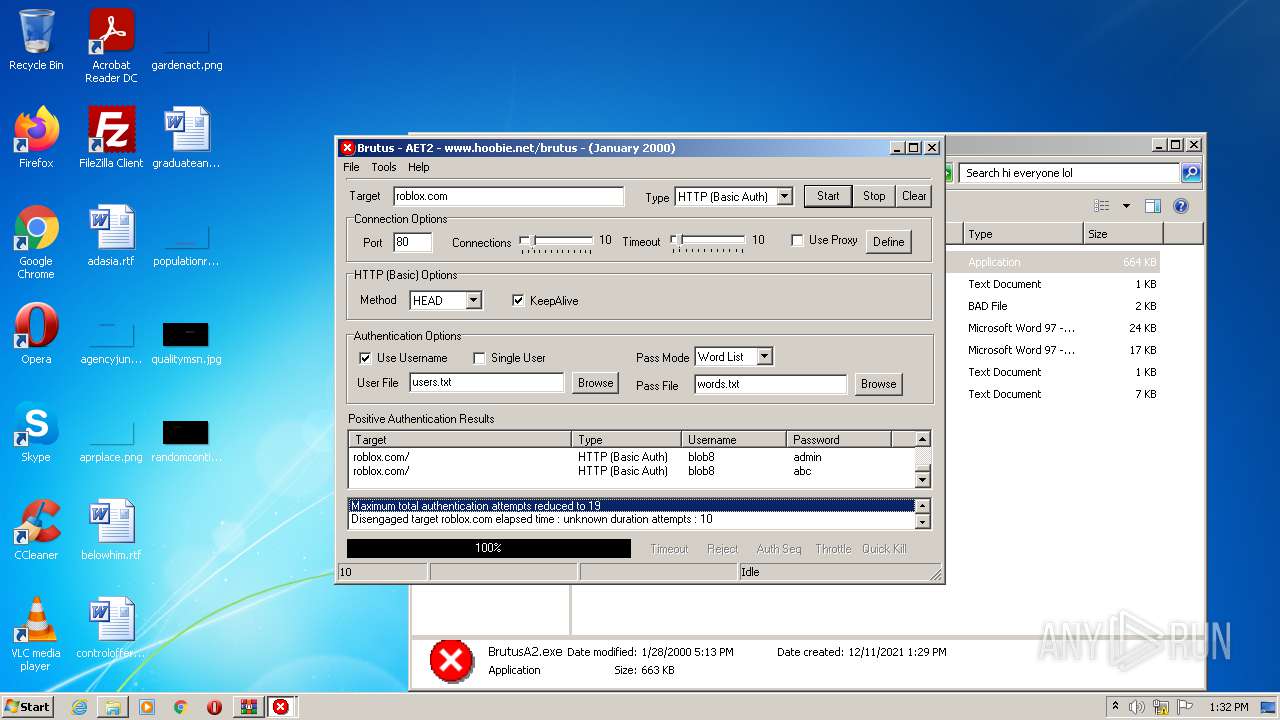
| File name: | brutus-aet2-darknet.zip |
| Full analysis: | https://app.any.run/tasks/6815f273-b4da-4388-9313-d983af1a9302 |
| Verdict: | Malicious activity |
| Analysis date: | December 11, 2021, 13:28:28 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 0663525EC99A1BCEBD9C8ABE398B6828 |
| SHA1: | E356D0FC6A920A010E990288ABC670B94FBBEB2A |
| SHA256: | 017E705BF6E5EBB4FDE25AF315DCC561813520F0C2687DB47E93D1DD5D6C099F |
| SSDEEP: | 6144:65B5F+q8+Q1qPtNpwi5E3c+Awo0GyRdlRH+pg4mexfdVn7iPw8aVCJ7QgY/:6Hn+F+QMpwi3+vJGy3lJlTeLi48YCVQf |
MALICIOUS
Application was dropped or rewritten from another process
- BrutusA2.exe (PID: 2236)
- BrutusA2.exe (PID: 760)
SUSPICIOUS
Reads default file associations for system extensions
- WinRAR.exe (PID: 1252)
- WINWORD.EXE (PID: 2492)
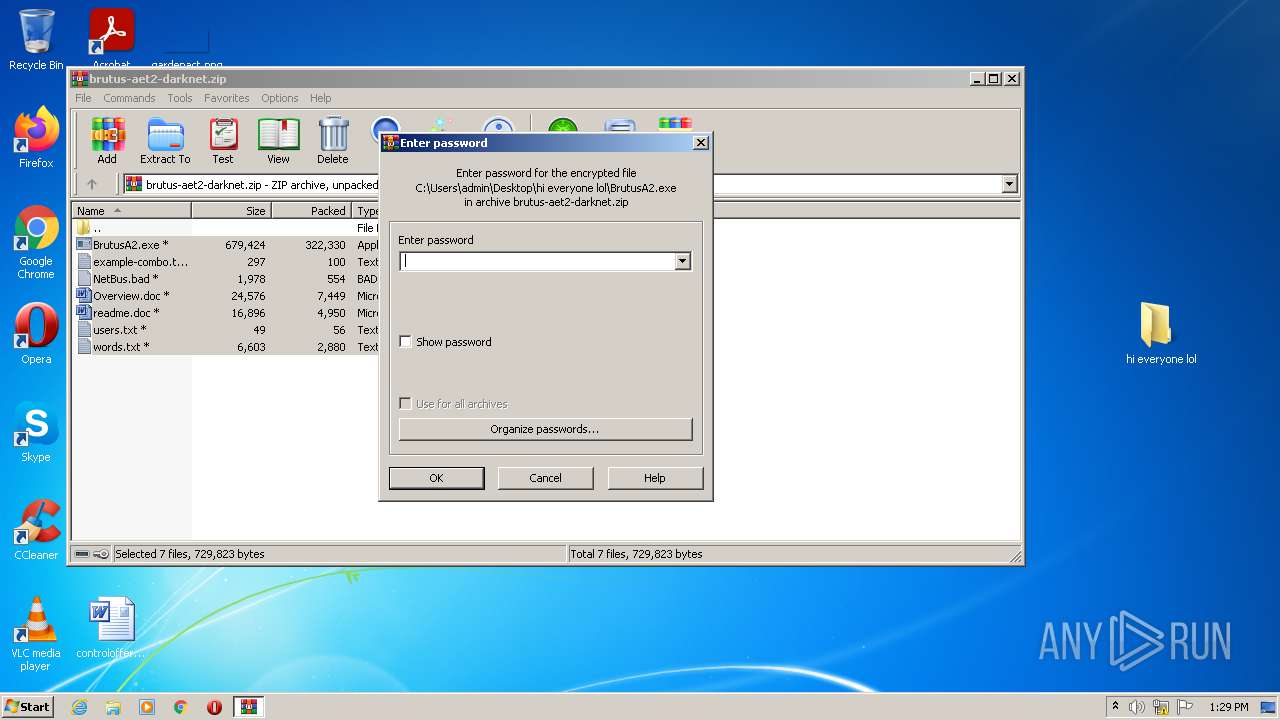
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1252)
Reads the computer name
- WinRAR.exe (PID: 1252)
- BrutusA2.exe (PID: 760)
Drops a file with too old compile date
- WinRAR.exe (PID: 1252)
Checks supported languages
- BrutusA2.exe (PID: 2236)
- WinRAR.exe (PID: 1252)
- BrutusA2.exe (PID: 760)
Starts Microsoft Office Application
- WINWORD.EXE (PID: 2492)
Application launched itself
- WINWORD.EXE (PID: 2492)
INFO
Manual execution by user
- NOTEPAD.EXE (PID: 3576)
- NOTEPAD.EXE (PID: 2044)
- BrutusA2.exe (PID: 2236)
- WINWORD.EXE (PID: 2492)
- NOTEPAD.EXE (PID: 1740)
- BrutusA2.exe (PID: 760)
Checks supported languages
- NOTEPAD.EXE (PID: 2044)
- WINWORD.EXE (PID: 2492)
- NOTEPAD.EXE (PID: 3576)
- WINWORD.EXE (PID: 1728)
- NOTEPAD.EXE (PID: 1740)
Creates files in the user directory
- WINWORD.EXE (PID: 2492)
Reads the computer name
- WINWORD.EXE (PID: 2492)
- WINWORD.EXE (PID: 1728)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 1728)
- WINWORD.EXE (PID: 2492)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | BrutusA2.exe |
|---|---|
| ZipUncompressedSize: | 679424 |
| ZipCompressedSize: | 322330 |
| ZipCRC: | 0xf7266f15 |
| ZipModifyDate: | 2000:01:28 17:13:17 |
| ZipCompression: | Deflated |
| ZipBitFlag: | 0x0001 |
| ZipRequiredVersion: | 20 |
Total processes
50
Monitored processes
8
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
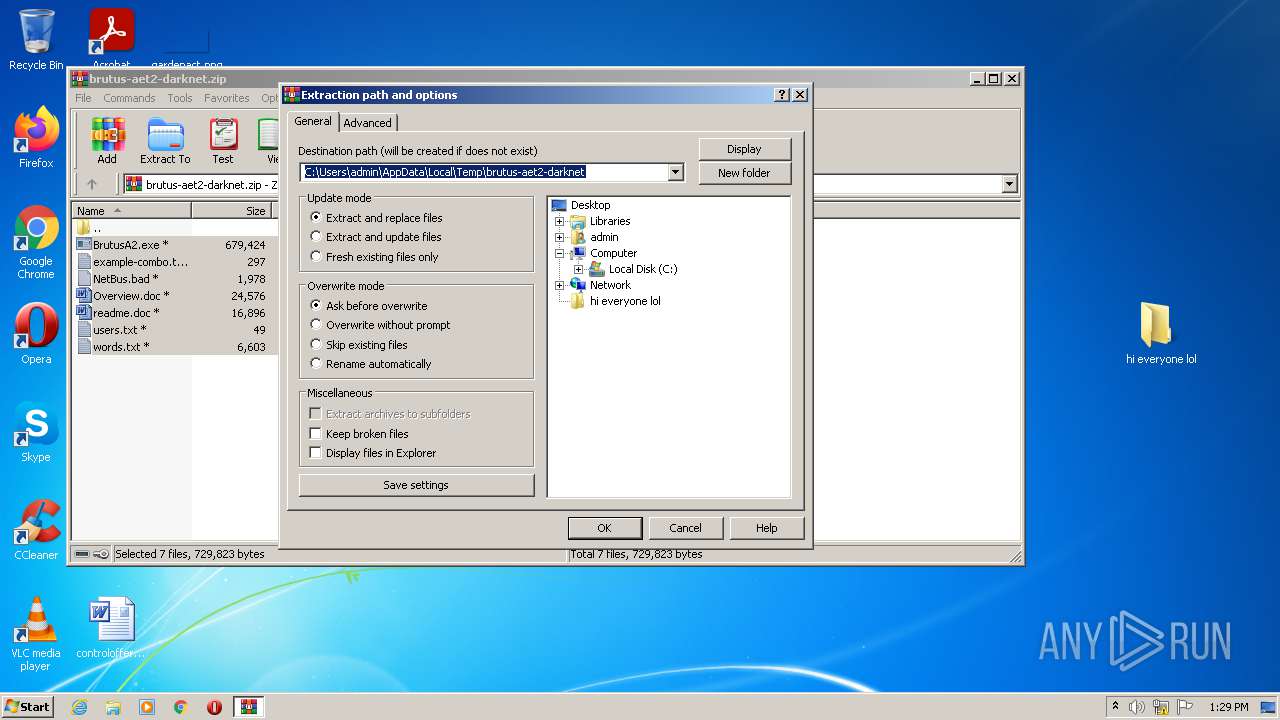
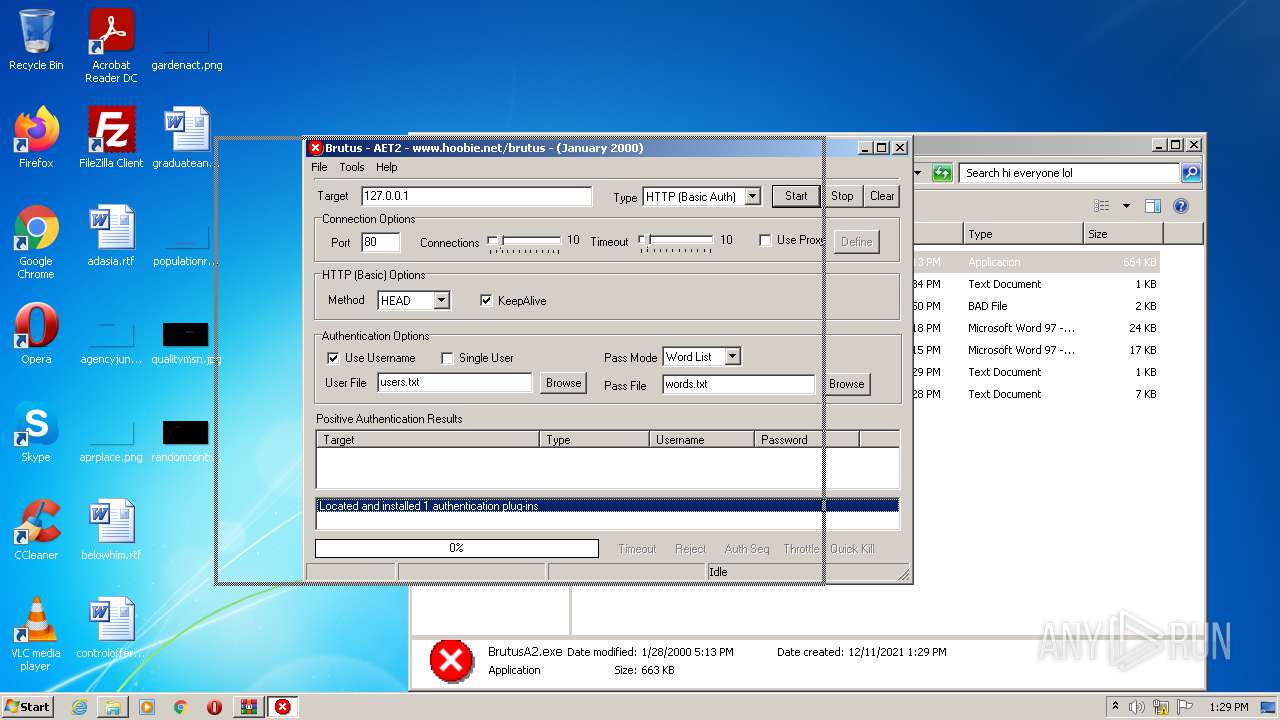
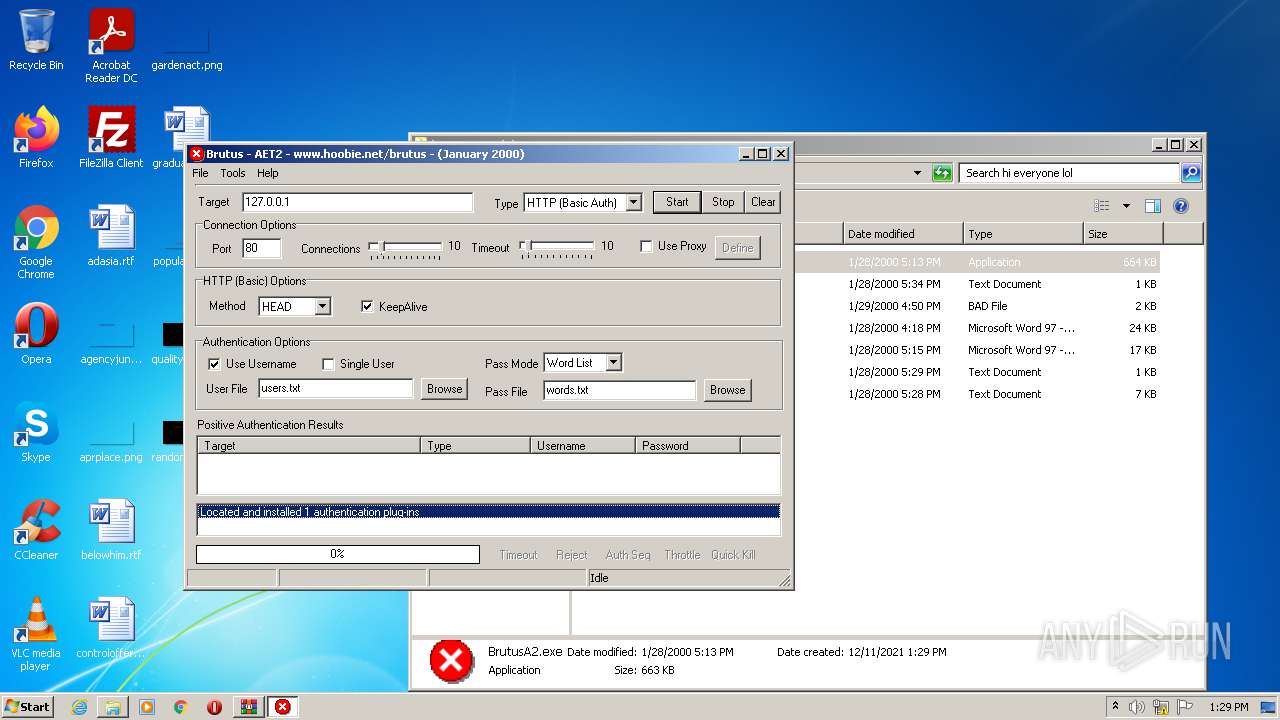
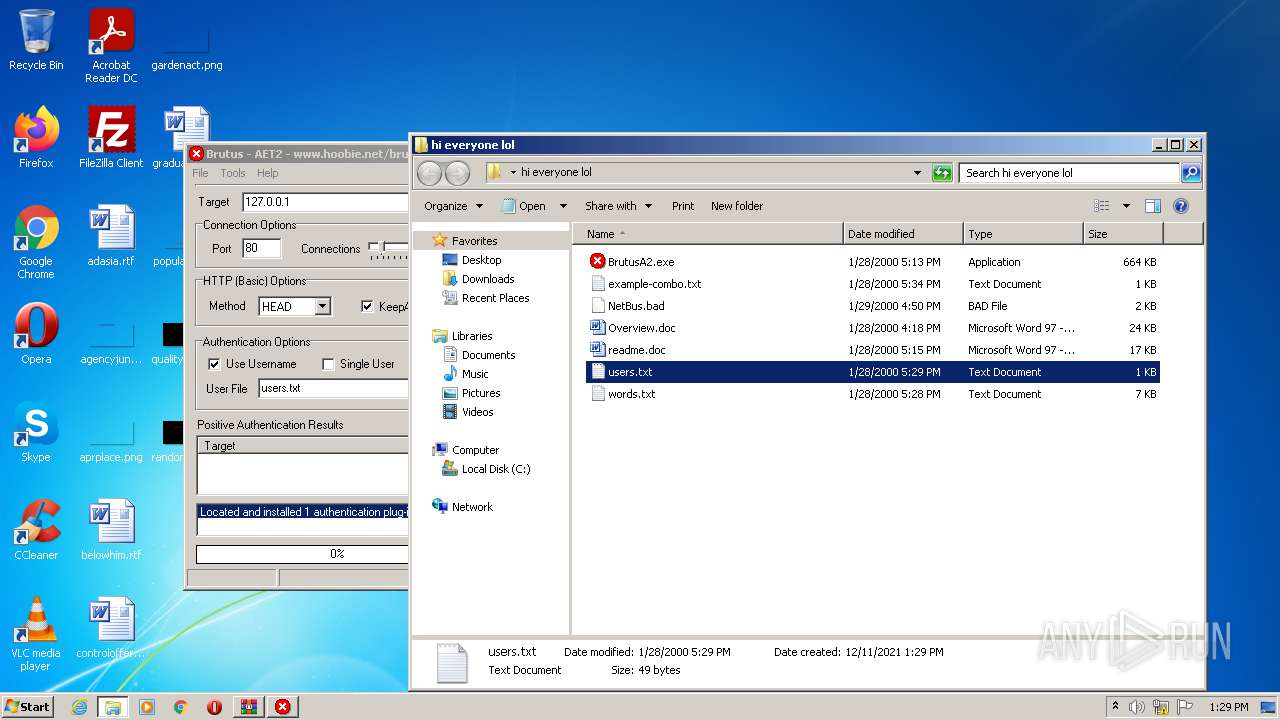
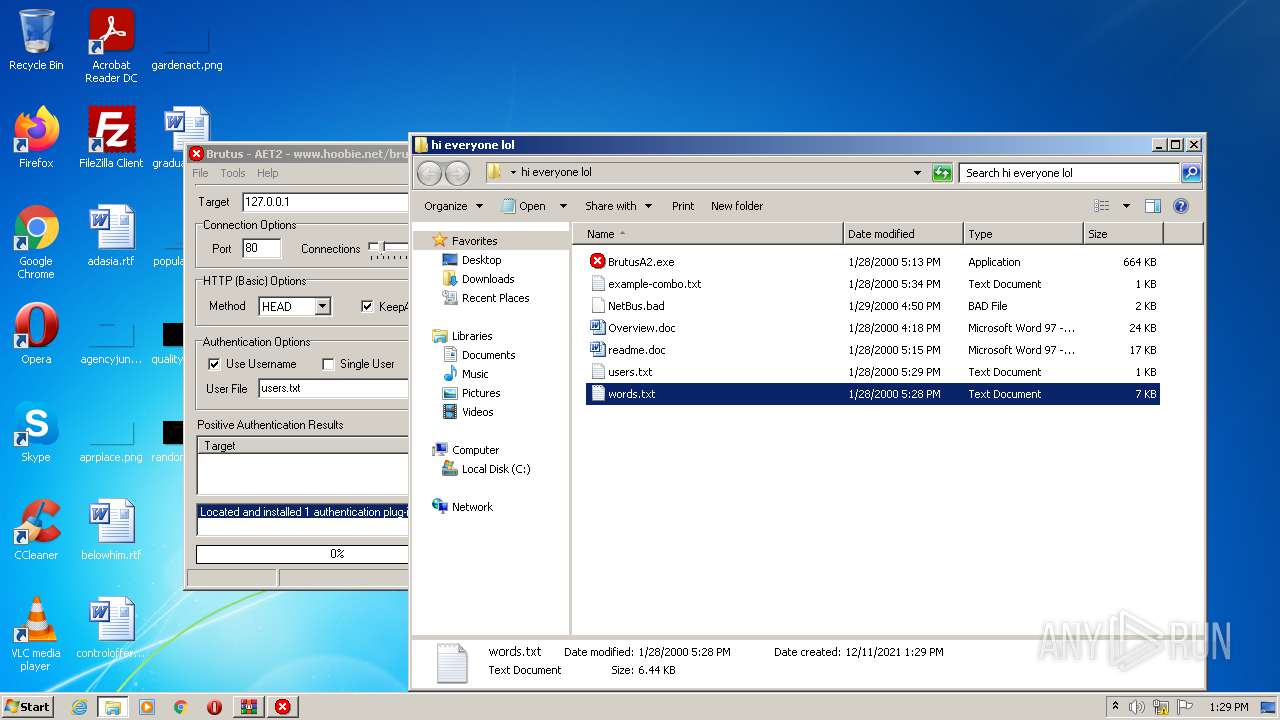
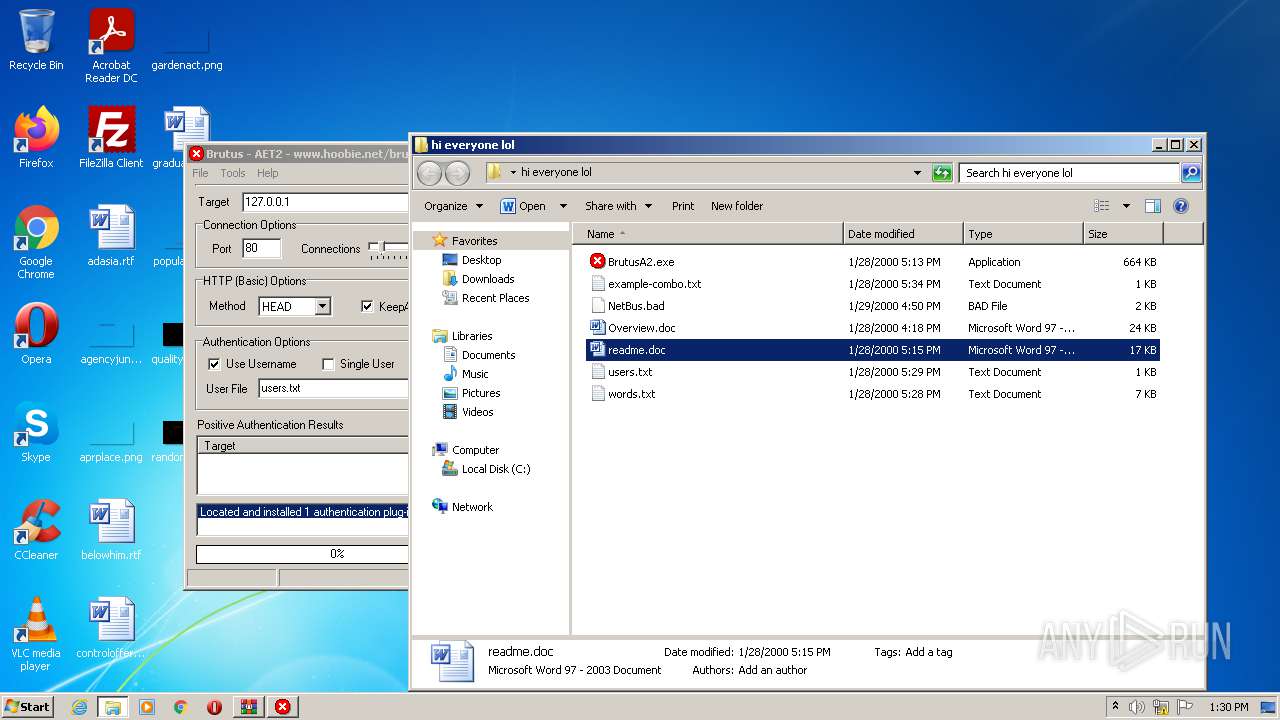
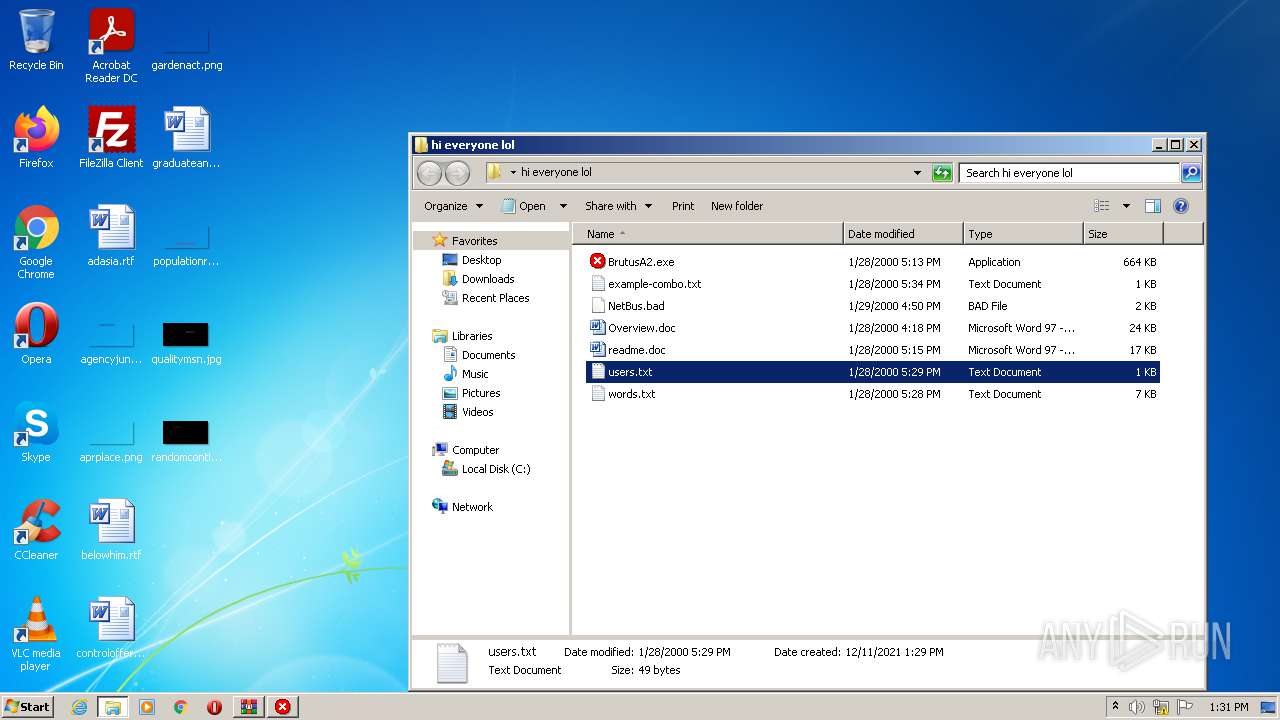
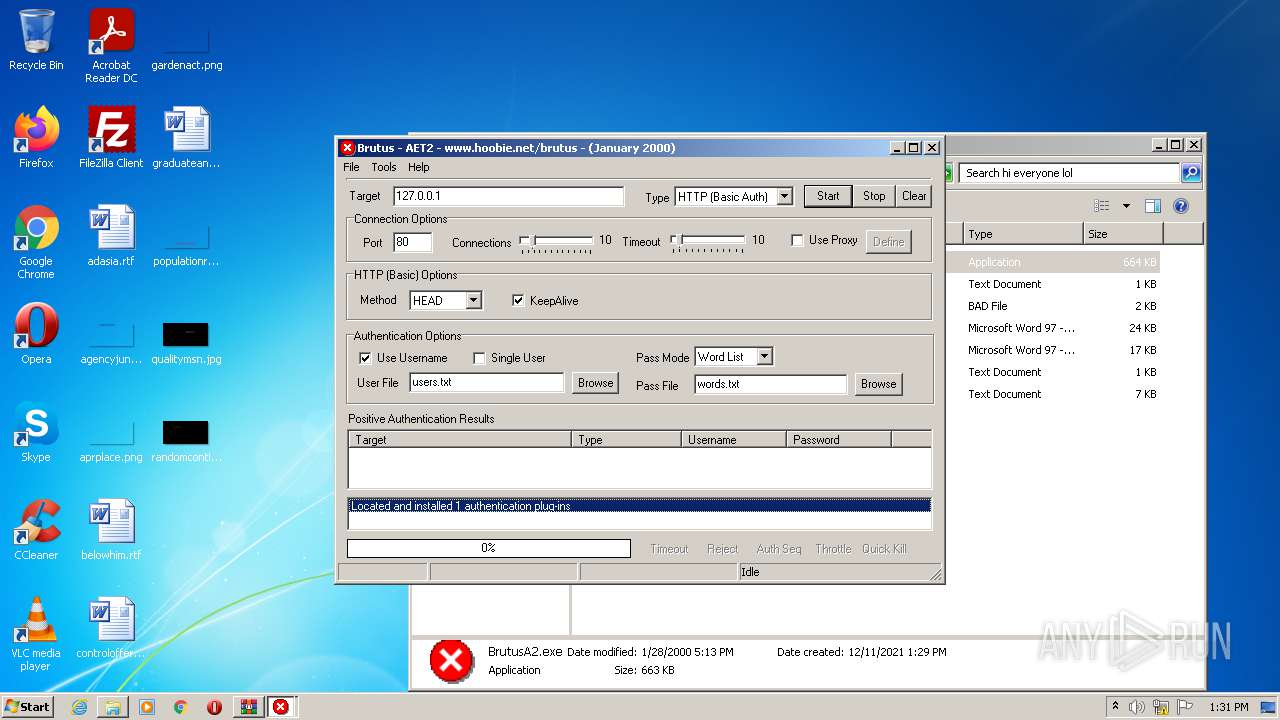
| 760 | "C:\Users\admin\Desktop\hi everyone lol\BrutusA2.exe" | C:\Users\admin\Desktop\hi everyone lol\BrutusA2.exe | Explorer.EXE | ||||||||||||
User: admin Company: HooBie Inc. Integrity Level: MEDIUM Description: Brutus AET 2 Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1252 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\brutus-aet2-darknet.zip" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1728 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /Embedding | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
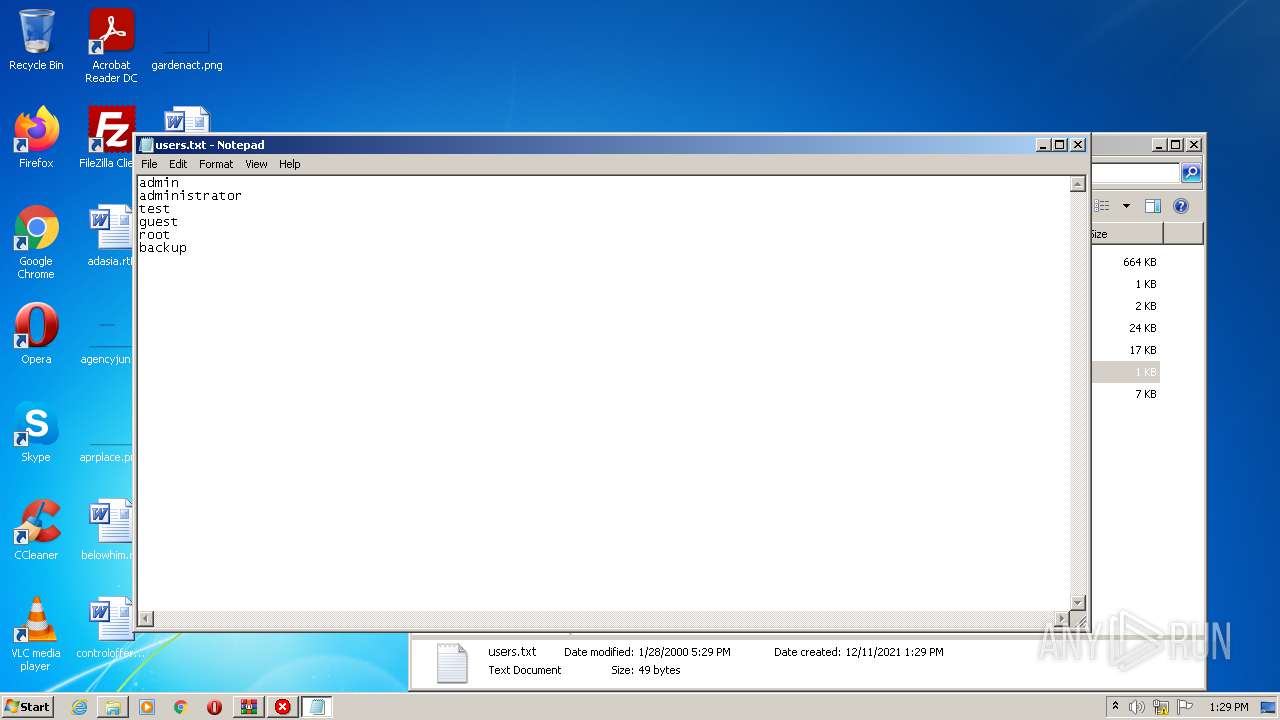
| 1740 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\hi everyone lol\users.txt | C:\Windows\system32\NOTEPAD.EXE | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2044 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\hi everyone lol\words.txt | C:\Windows\system32\NOTEPAD.EXE | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2236 | "C:\Users\admin\Desktop\hi everyone lol\BrutusA2.exe" | C:\Users\admin\Desktop\hi everyone lol\BrutusA2.exe | — | Explorer.EXE | |||||||||||
User: admin Company: HooBie Inc. Integrity Level: MEDIUM Description: Brutus AET 2 Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
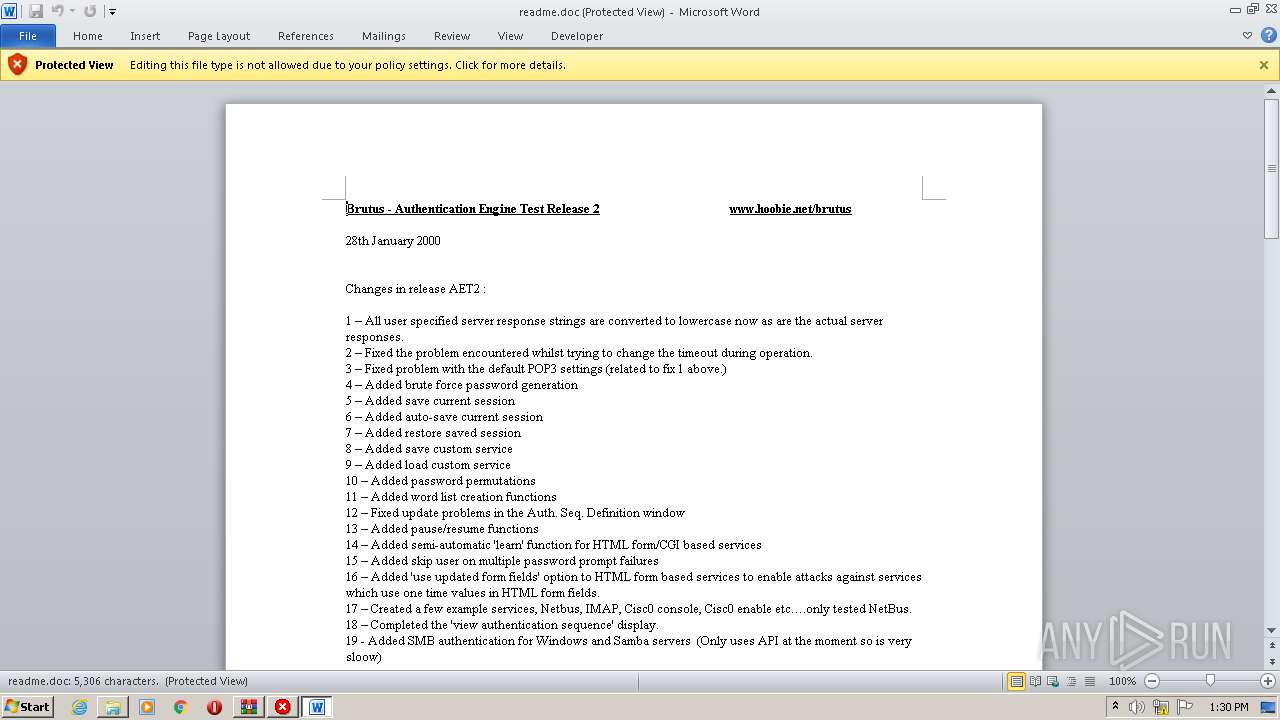
| 2492 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\hi everyone lol\readme.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3576 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\hi everyone lol\users.txt | C:\Windows\system32\NOTEPAD.EXE | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
5 582
Read events
5 408
Write events
134
Delete events
40
Modification events
| (PID) Process: | (1252) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1252) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1252) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1252) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (1252) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (1252) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\brutus-aet2-darknet.zip | |||
| (PID) Process: | (1252) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1252) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1252) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1252) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
1
Suspicious files
4
Text files
6
Unknown types
7
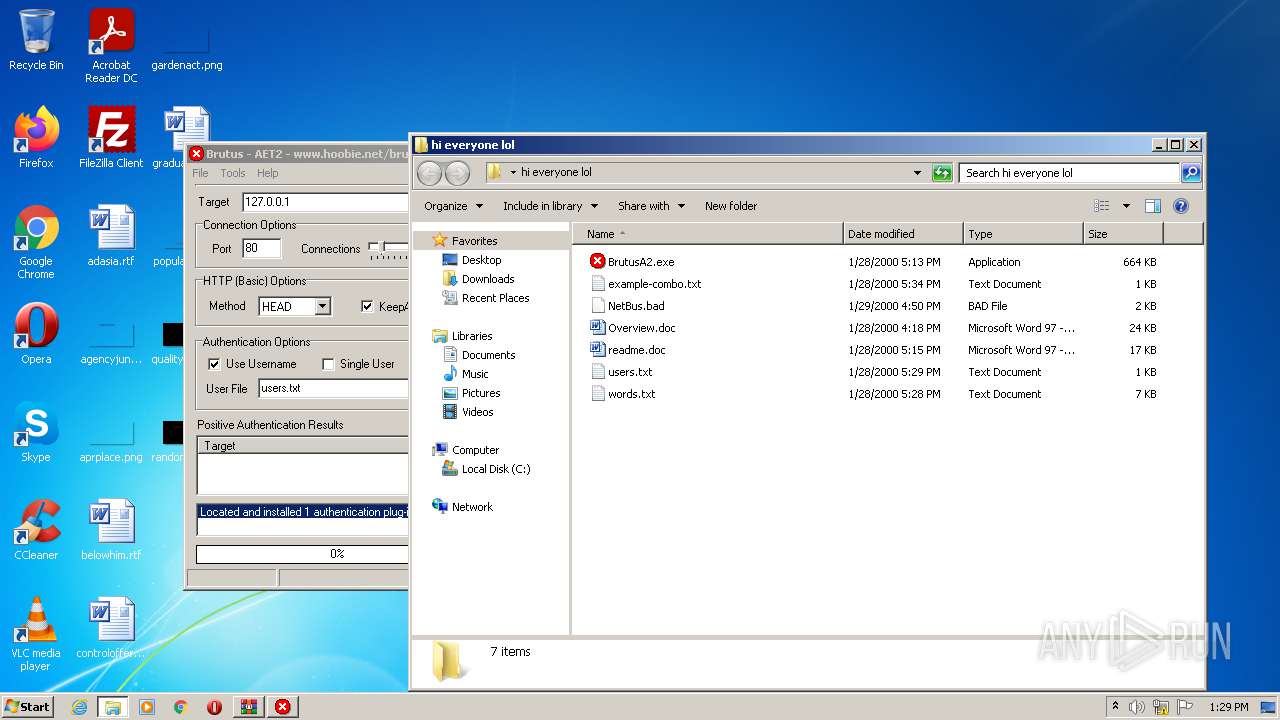
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2492 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR9EE9.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2492 | WINWORD.EXE | C:\Users\admin\Desktop\hi everyone lol\~$readme.doc | pgc | |
MD5:— | SHA256:— | |||
| 1252 | WinRAR.exe | C:\Users\admin\Desktop\hi everyone lol\Overview.doc | document | |
MD5:80E3161B23D2308C45C2F4CA1C30E1DF | SHA256:7CED891A776D4406985DB49402D3CFC3F954643892759101576E83C2A2212B3B | |||
| 2492 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2492 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\readme.doc.LNK | lnk | |
MD5:— | SHA256:— | |||
| 1252 | WinRAR.exe | C:\Users\admin\Desktop\hi everyone lol\BrutusA2.exe | executable | |
MD5:D6066D187BE09B56D917AD3AA63E4874 | SHA256:49A3E574080A63B1A24980B3A775A82B5A9F7C269318662F5BBEBCF21F8CEFE4 | |||
| 1252 | WinRAR.exe | C:\Users\admin\Desktop\hi everyone lol\NetBus.bad | text | |
MD5:190972127D2E2A813DC42166E2DC0F8E | SHA256:F779FE0C6BAE424075EF0A051C9E94151264F05597A2ED14D21197AC705854AC | |||
| 1728 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\OICE_1BFCFB6B-6661-4523-9612-4834AD0098B3.0\~DF025BD29551F17A0F.TMP | gmc | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
| 2492 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DFDC86CE3E382CBAAE.TMP | gmc | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
| 2492 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{3D29FFDB-870B-459F-BC0B-1A5CF86F488B}.tmp | smt | |
MD5:5D4D94EE7E06BBB0AF9584119797B23A | SHA256:4826C0D860AF884D3343CA6460B0006A7A2CE7DBCCC4D743208585D997CC5FD1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
20
TCP/UDP connections
23
DNS requests
2
Threats
22
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
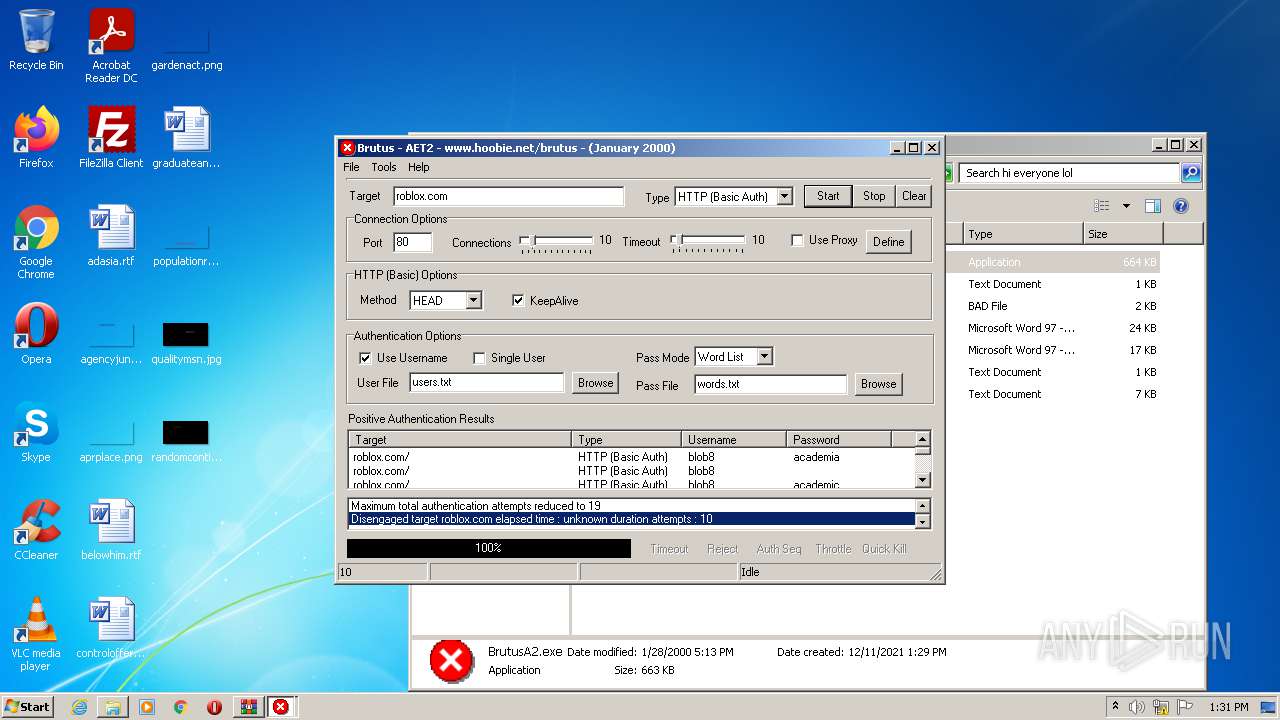
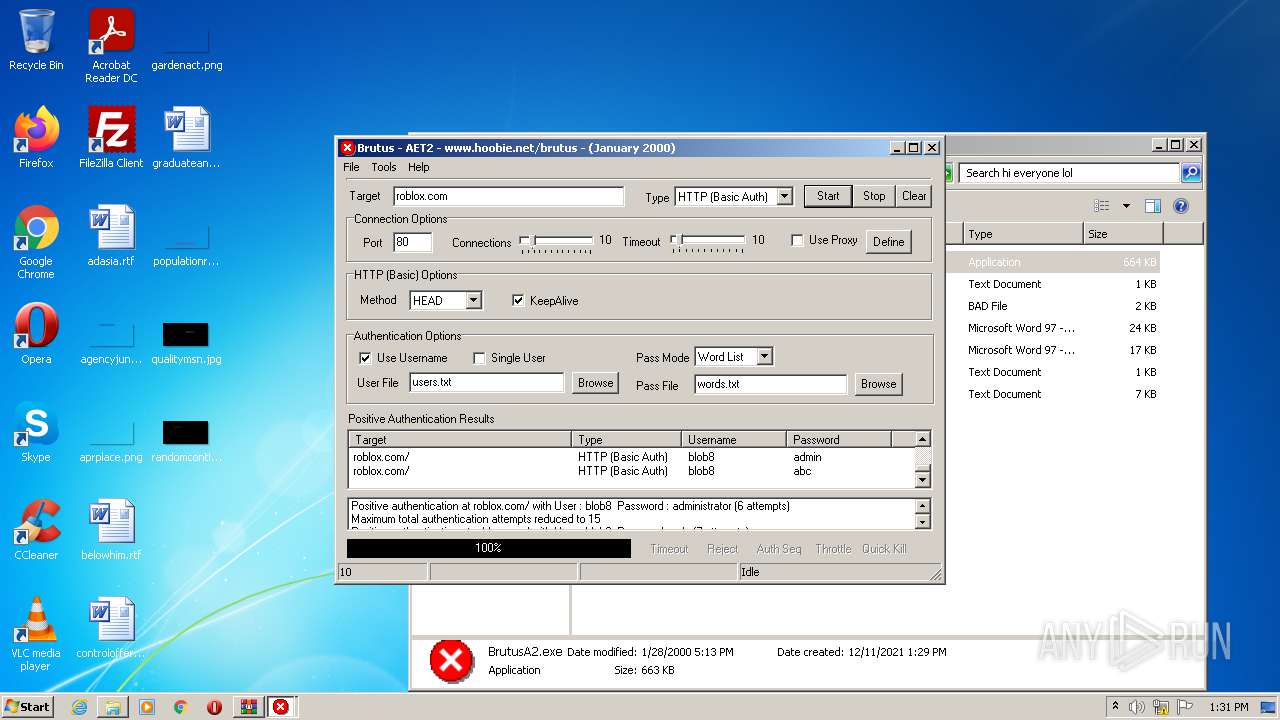
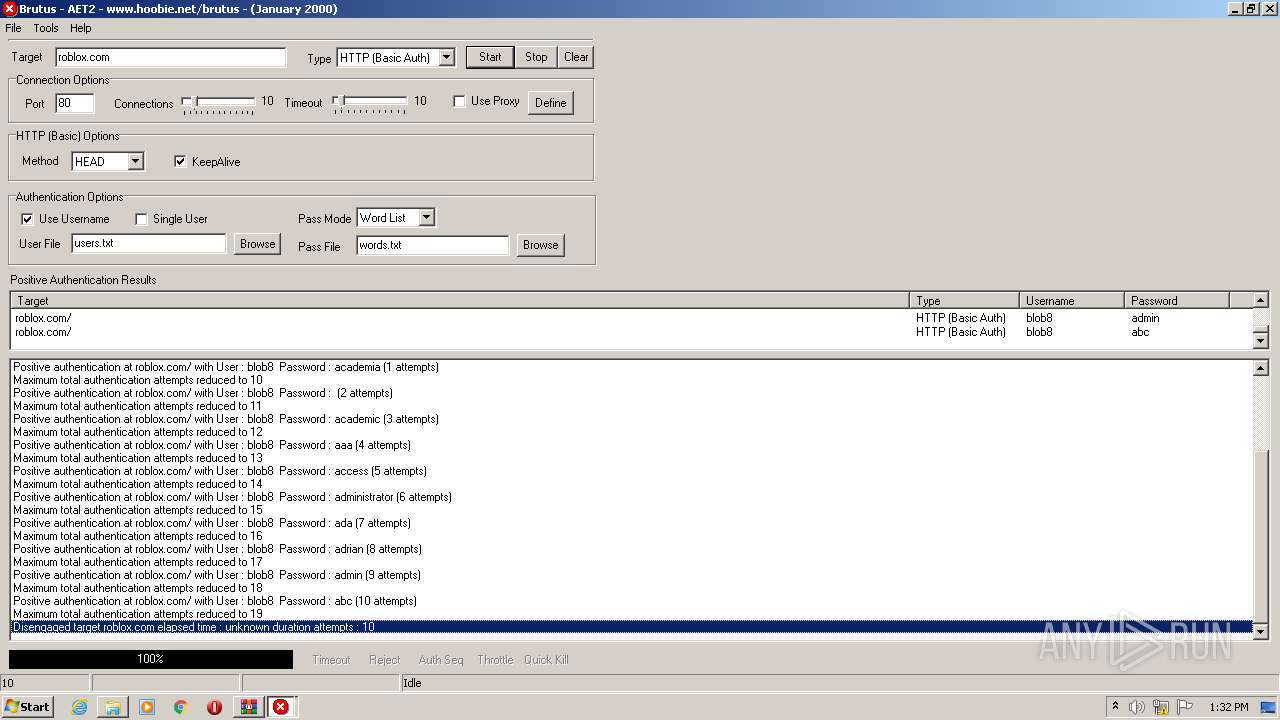
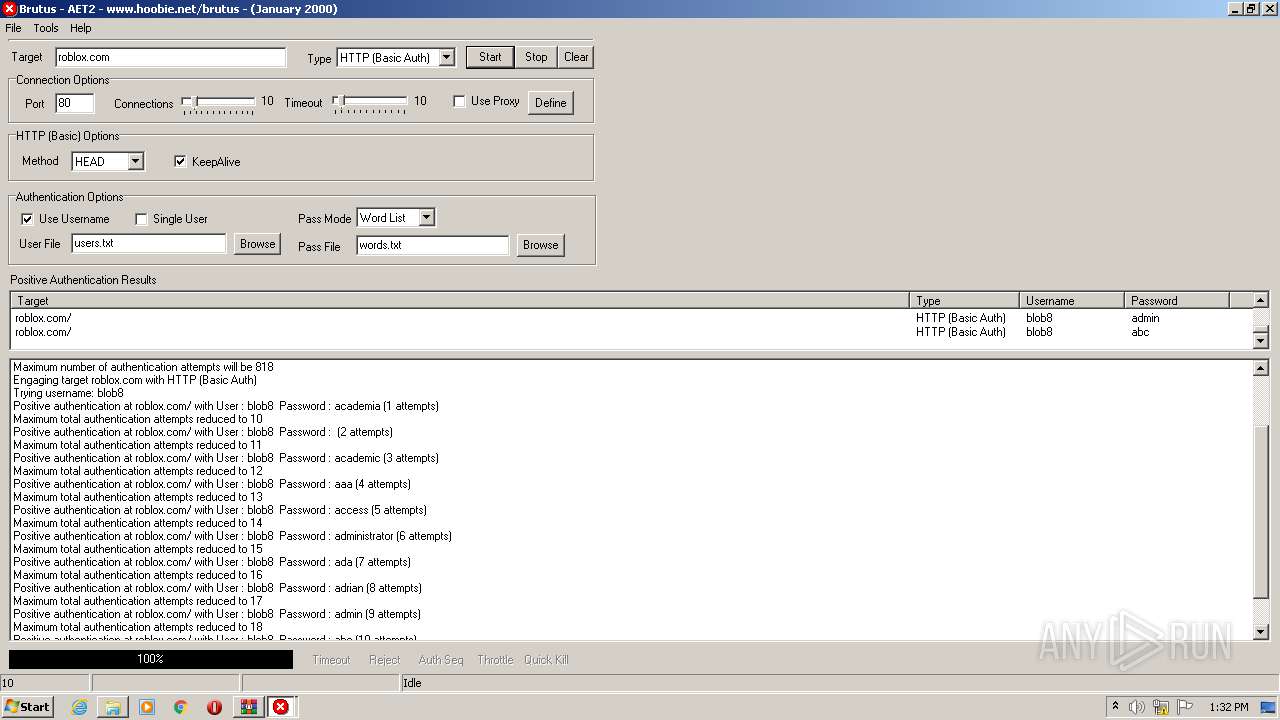
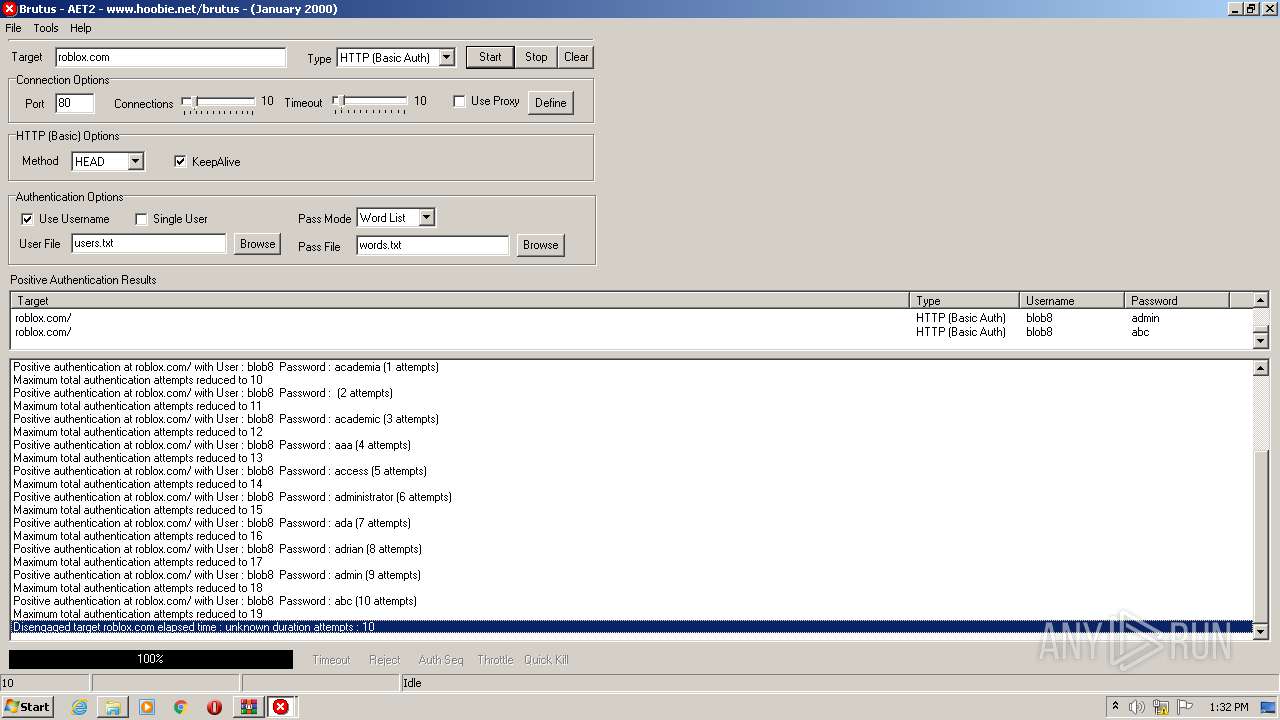
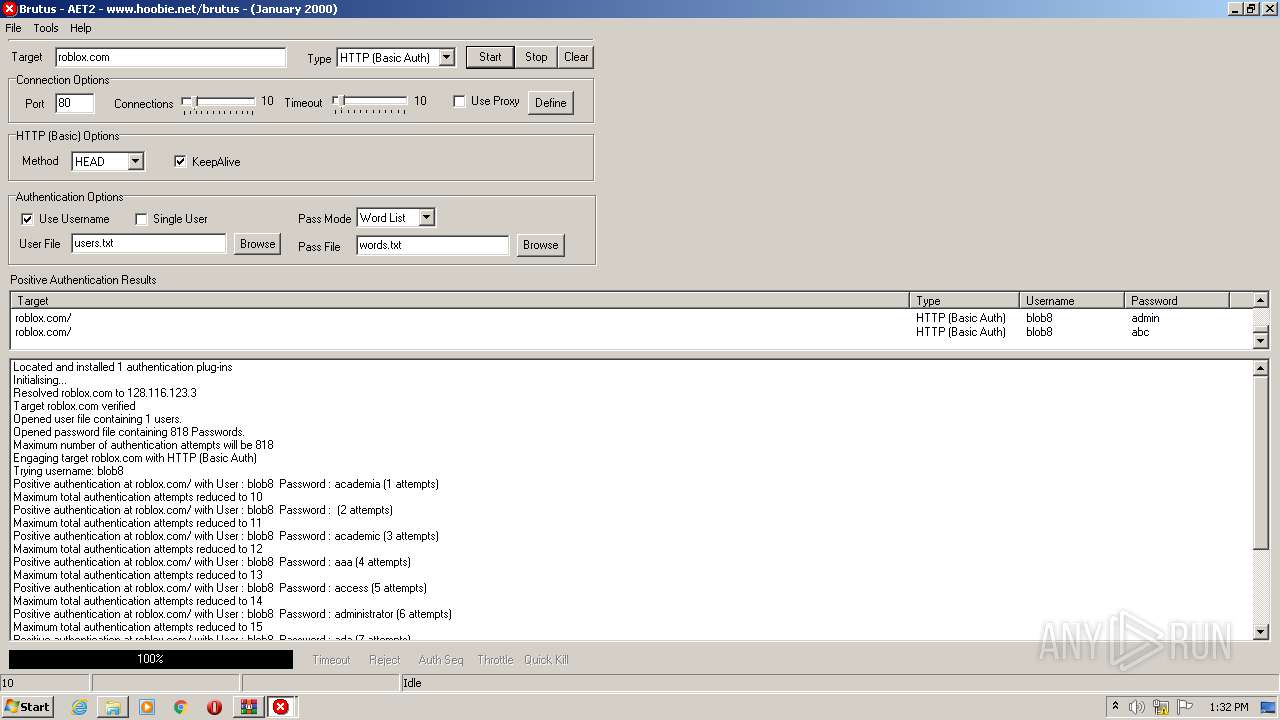
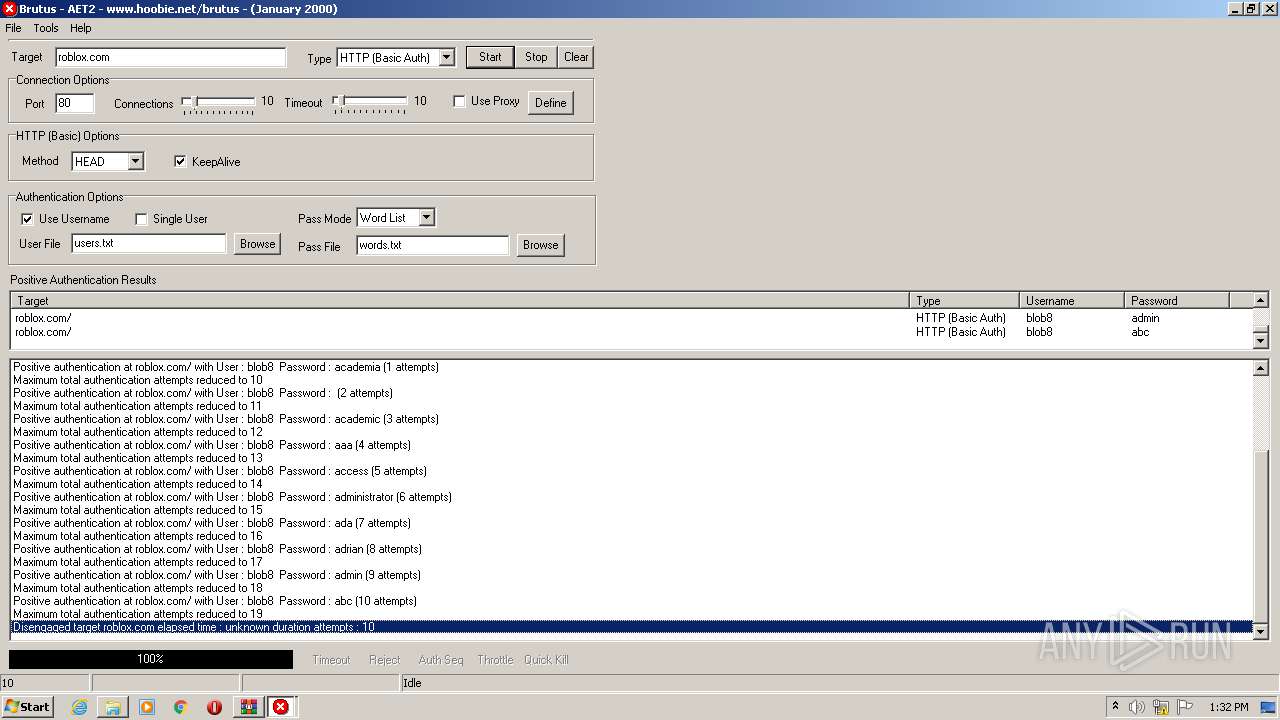
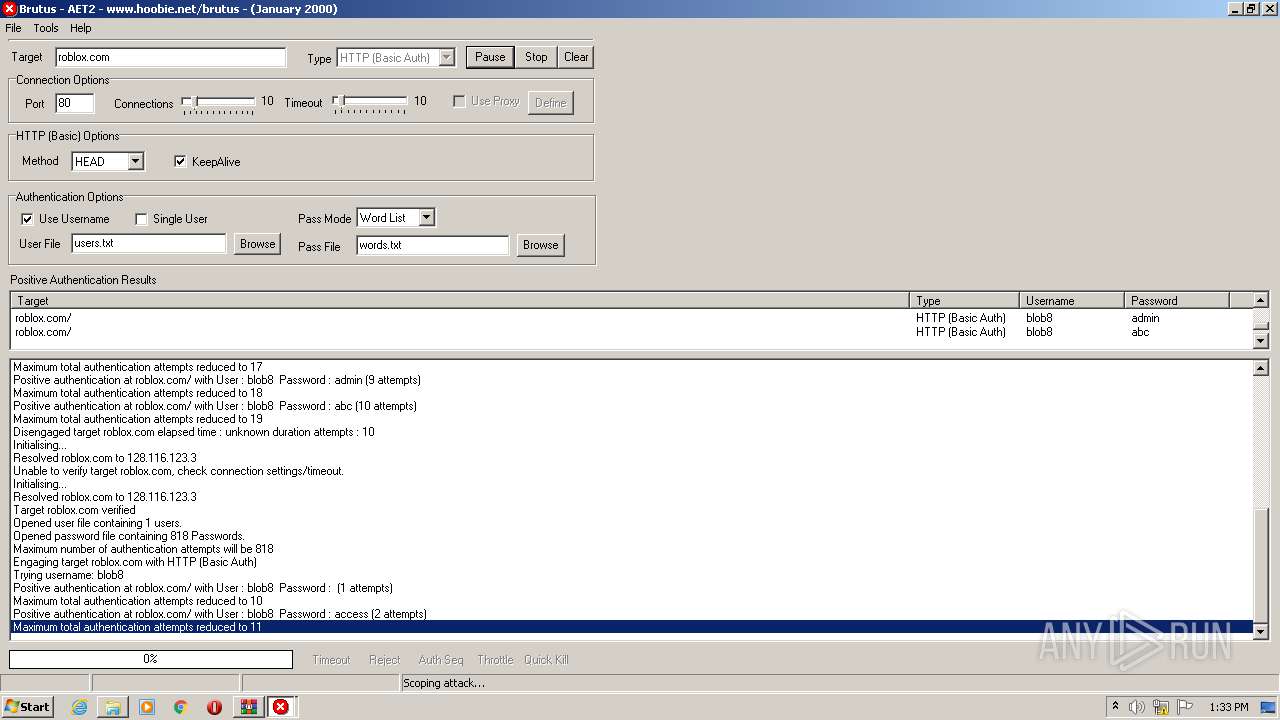
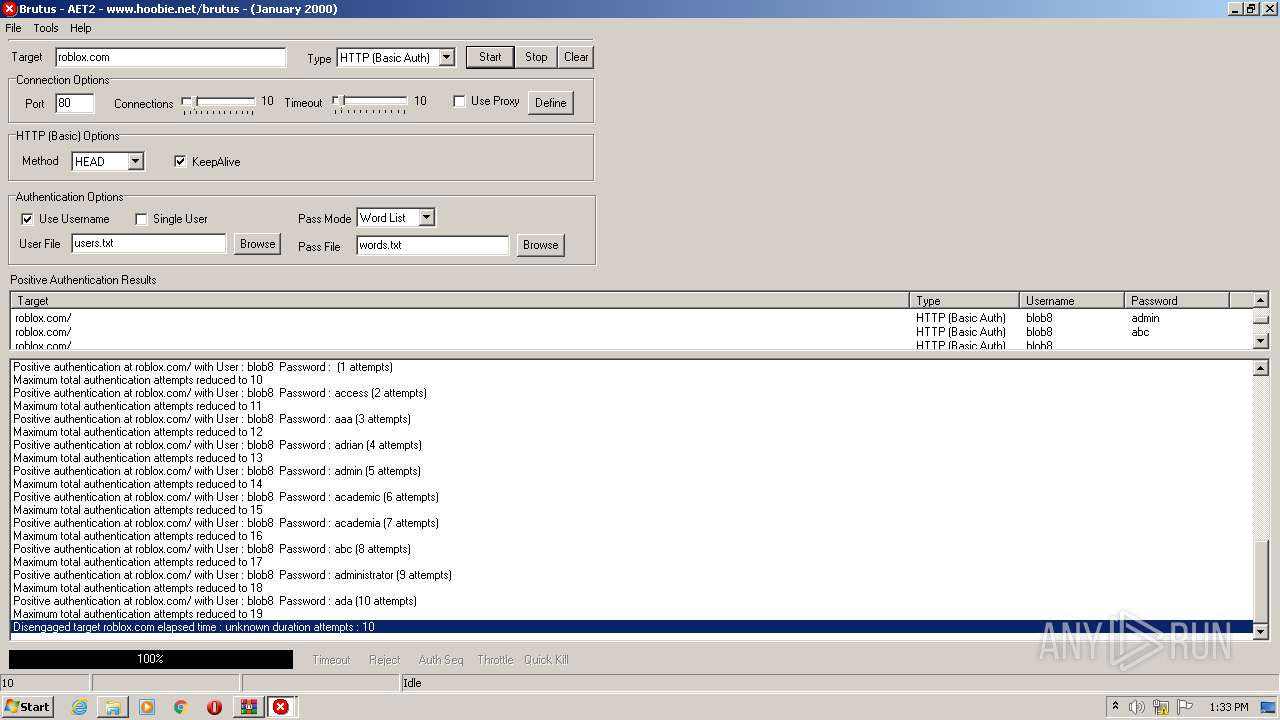
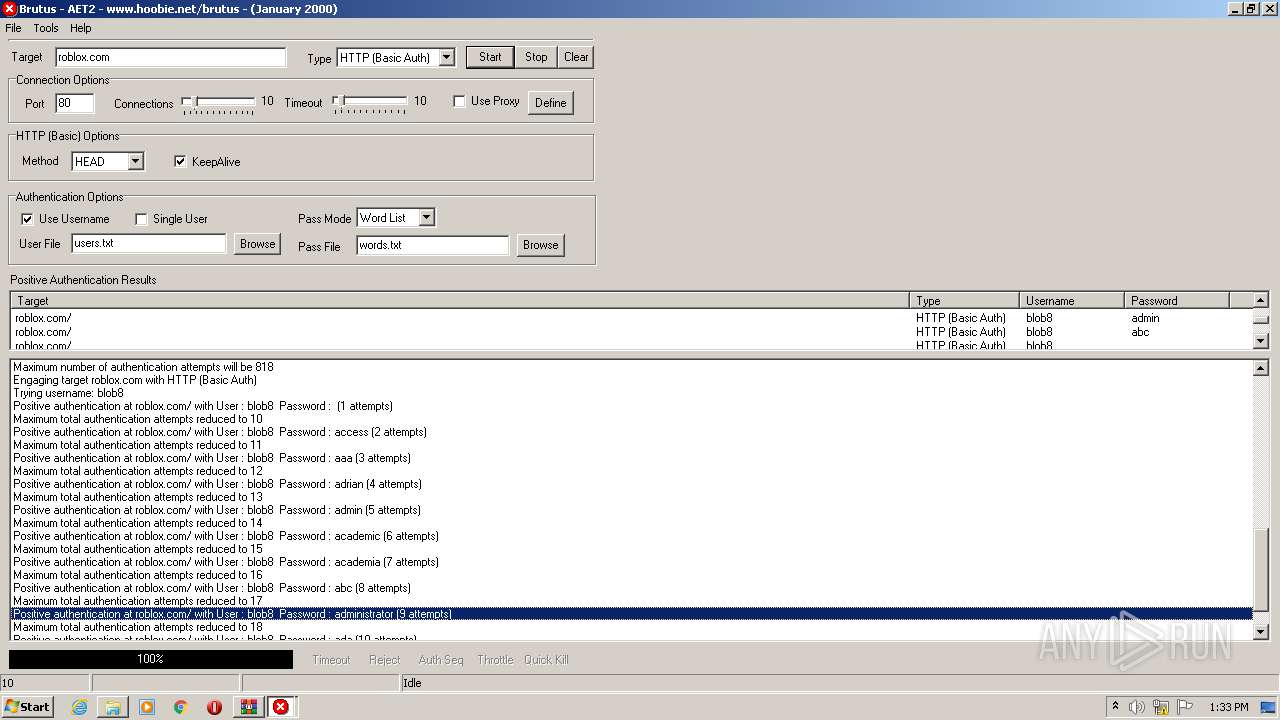
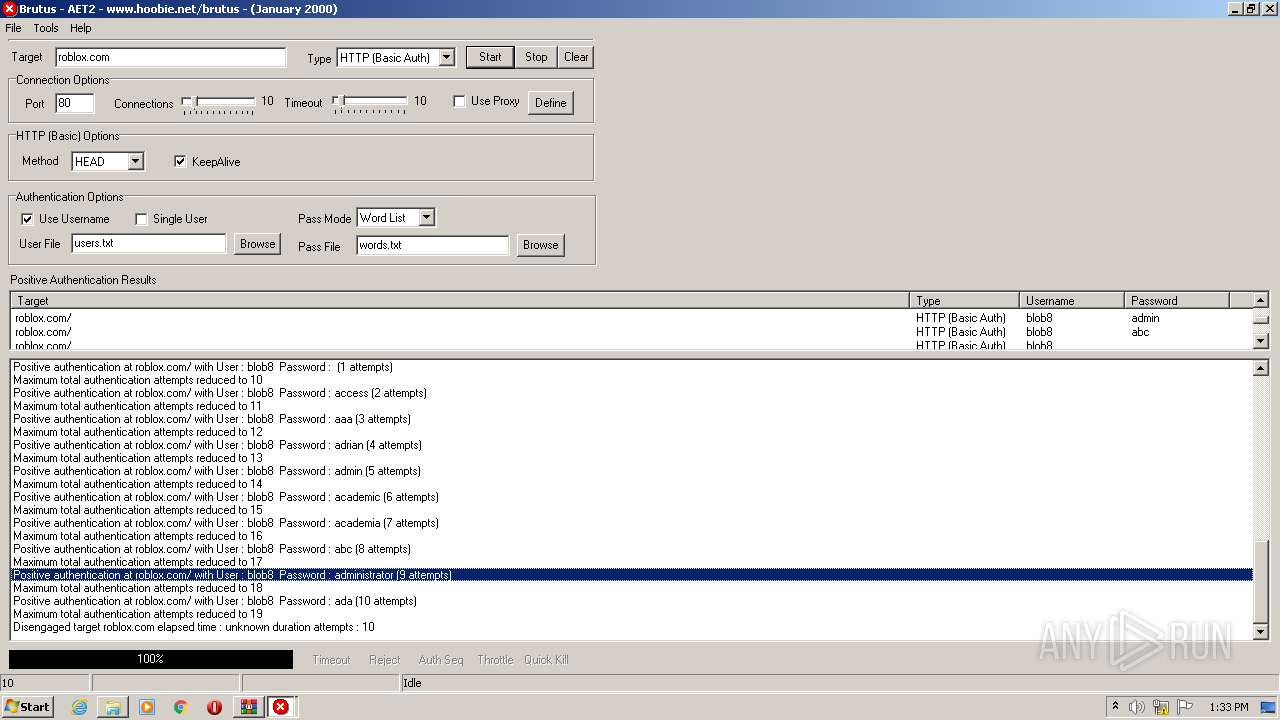
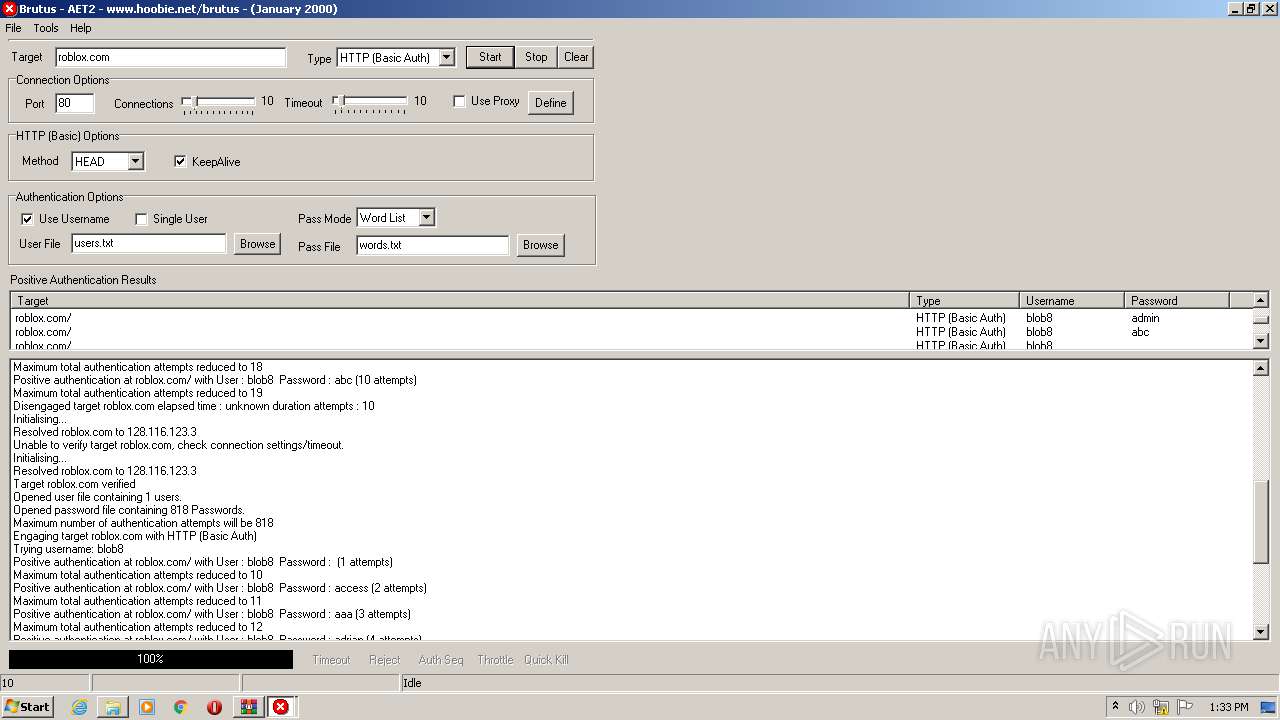
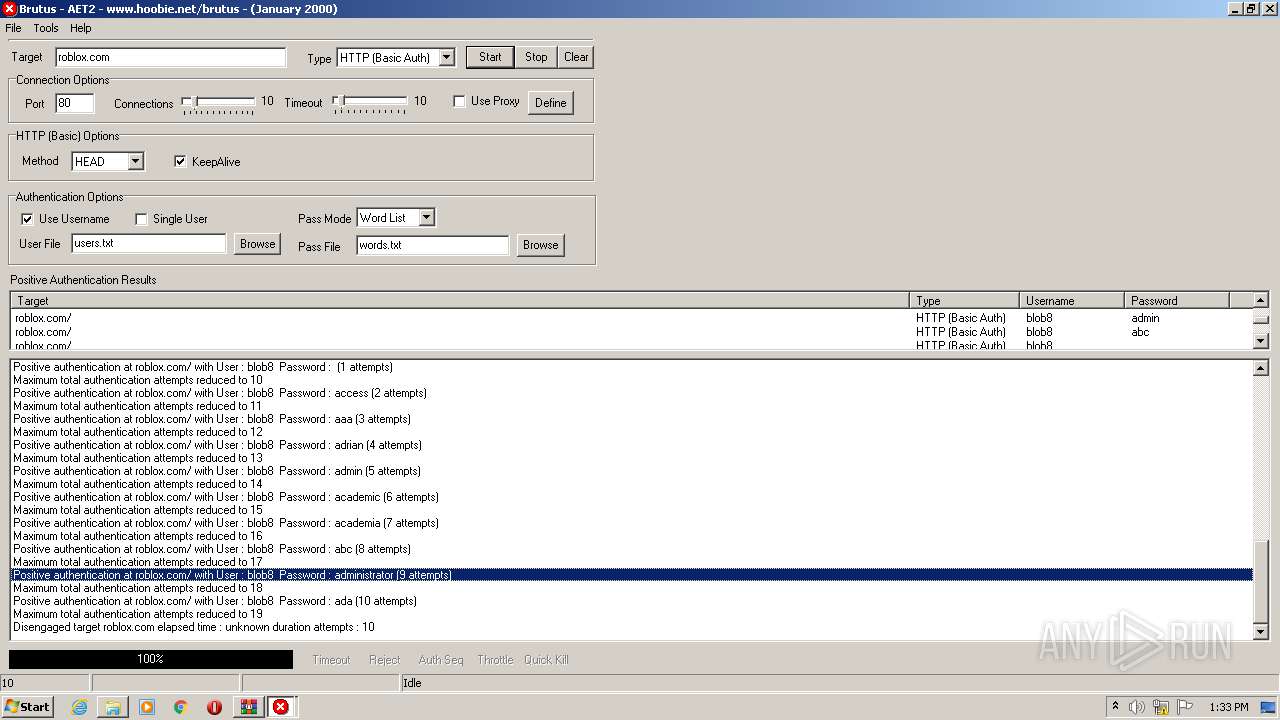
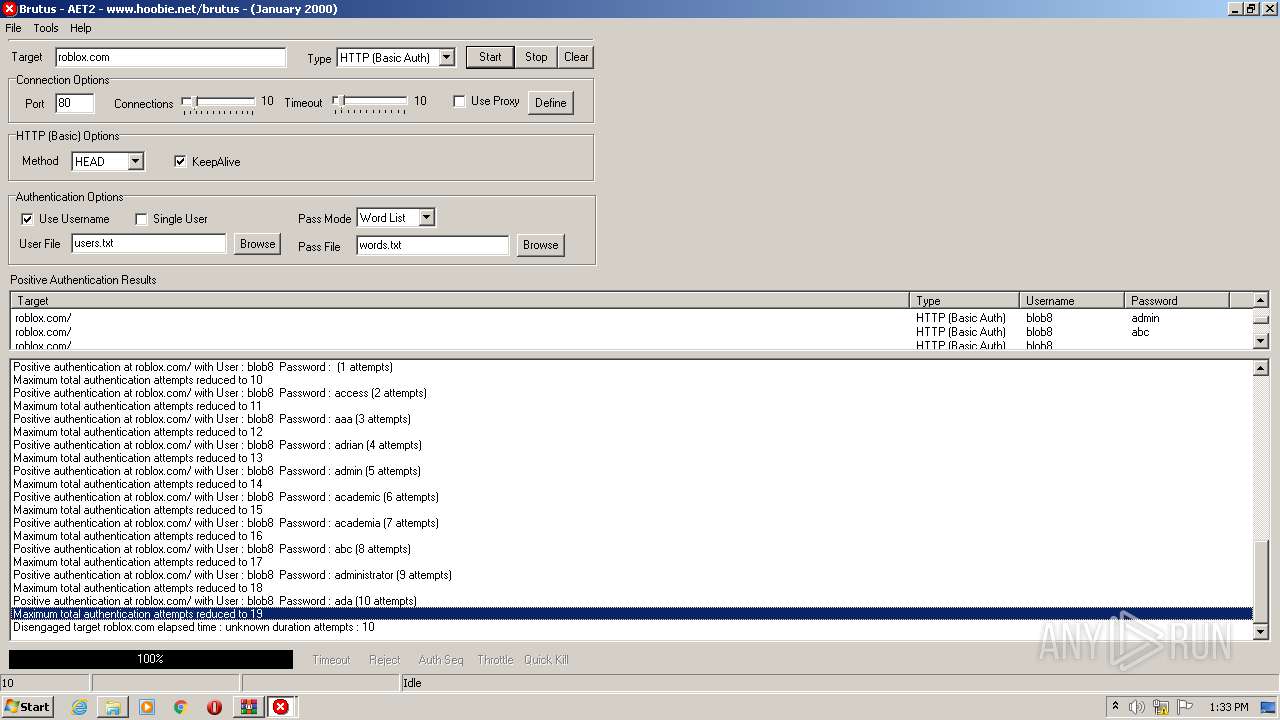
760 | BrutusA2.exe | HEAD | 308 | 128.116.123.3:80 | http://roblox.com/ | US | — | — | whitelisted |
760 | BrutusA2.exe | HEAD | 308 | 128.116.123.3:80 | http://roblox.com/ | US | — | — | whitelisted |
760 | BrutusA2.exe | HEAD | 308 | 128.116.123.3:80 | http://roblox.com/ | US | — | — | whitelisted |
760 | BrutusA2.exe | HEAD | 308 | 128.116.123.3:80 | http://roblox.com/ | US | — | — | whitelisted |
760 | BrutusA2.exe | HEAD | 308 | 128.116.123.3:80 | http://roblox.com/ | US | — | — | whitelisted |
760 | BrutusA2.exe | HEAD | 308 | 128.116.123.3:80 | http://roblox.com/ | US | — | — | whitelisted |
760 | BrutusA2.exe | HEAD | 308 | 128.116.123.3:80 | http://roblox.com/ | US | — | — | whitelisted |
760 | BrutusA2.exe | HEAD | 308 | 128.116.123.3:80 | http://roblox.com/ | US | — | — | whitelisted |
760 | BrutusA2.exe | HEAD | 308 | 128.116.123.3:80 | http://roblox.com/ | US | — | — | whitelisted |
760 | BrutusA2.exe | HEAD | 308 | 128.116.123.3:80 | http://roblox.com/ | US | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 128.116.123.3:80 | roblox.com | University Corporation for Atmospheric Research | US | suspicious |
760 | BrutusA2.exe | 128.116.123.3:80 | roblox.com | University Corporation for Atmospheric Research | US | suspicious |
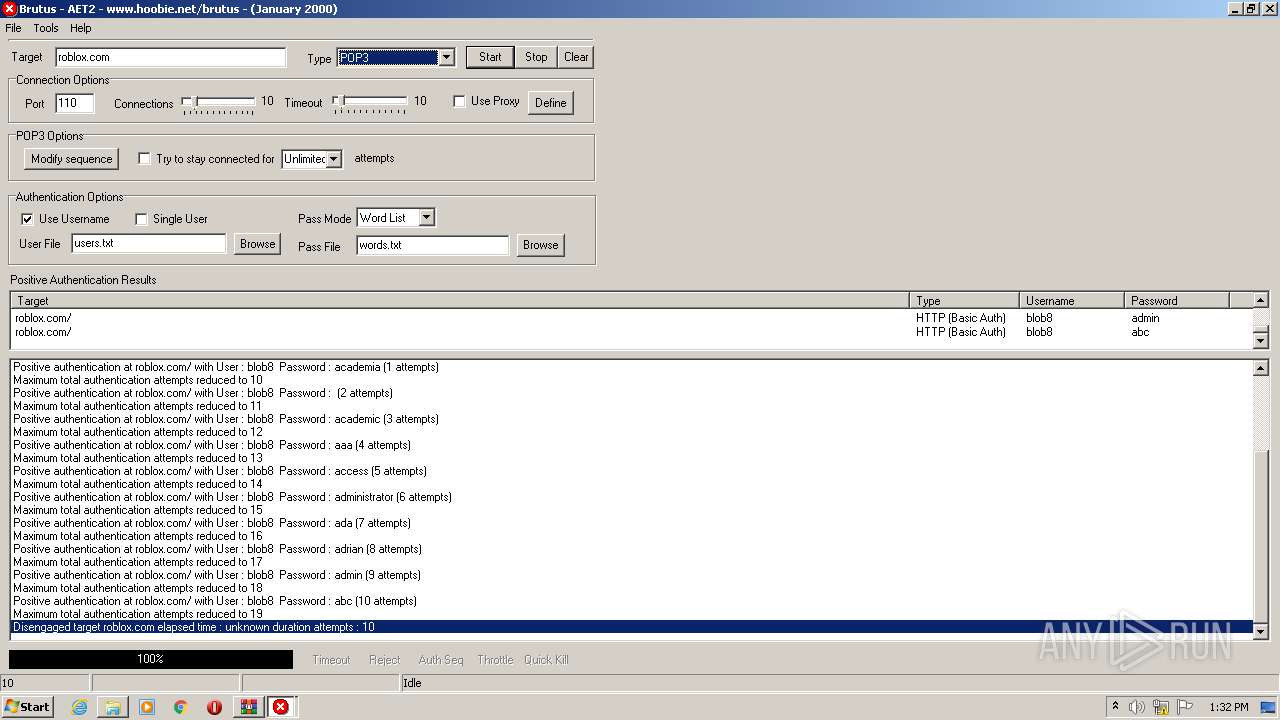
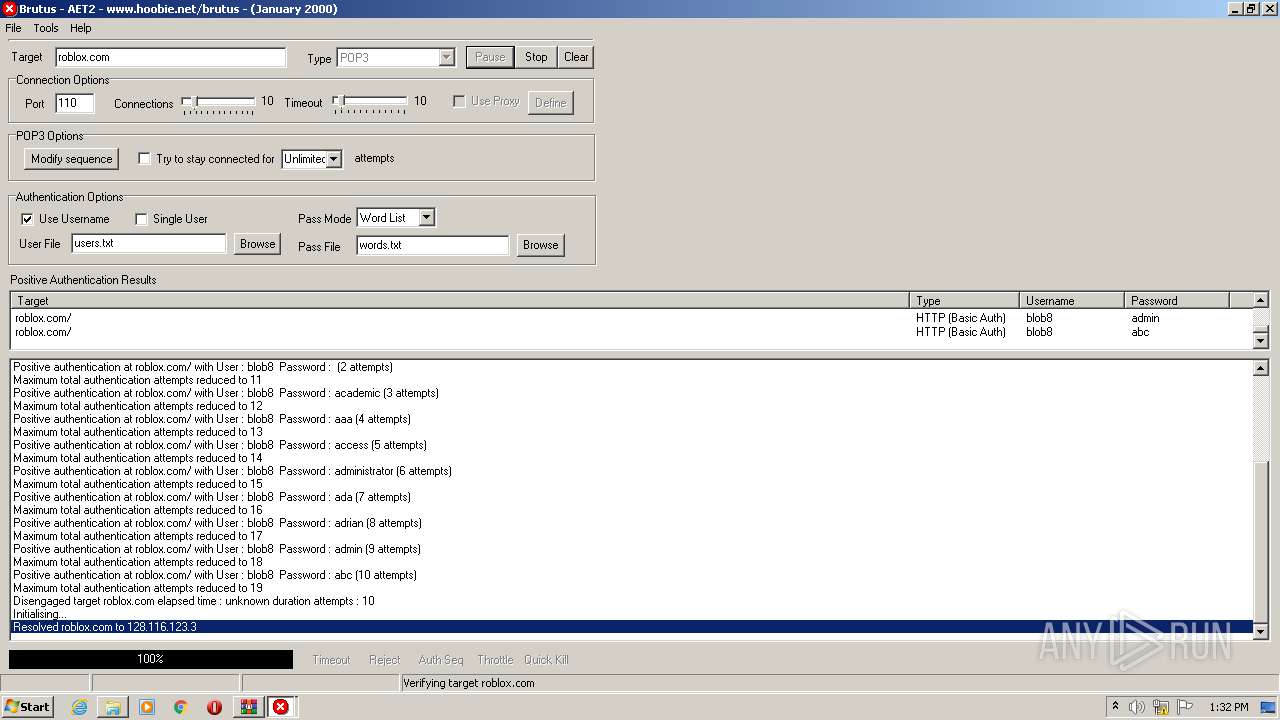
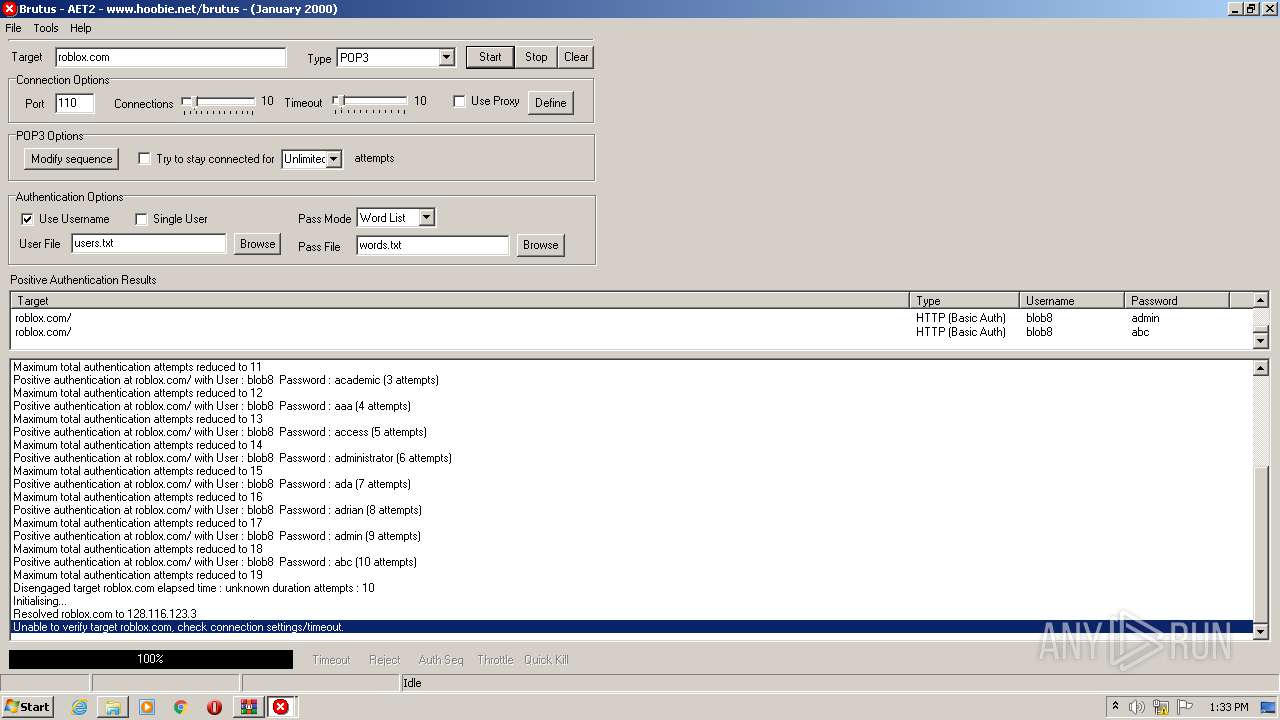
760 | BrutusA2.exe | 128.116.123.3:110 | roblox.com | University Corporation for Atmospheric Research | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
roblox.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
760 | BrutusA2.exe | Potential Corporate Privacy Violation | ET POLICY Outgoing Basic Auth Base64 HTTP Password detected unencrypted |
760 | BrutusA2.exe | Attempted Information Leak | ET SCAN Brutus Scan Outbound |
760 | BrutusA2.exe | Attempted Information Leak | ET SCAN Brutus Scan Outbound |
760 | BrutusA2.exe | Attempted Information Leak | ET SCAN Brutus Scan Outbound |
760 | BrutusA2.exe | Attempted Information Leak | ET SCAN Brutus Scan Outbound |
760 | BrutusA2.exe | Attempted Information Leak | ET SCAN Brutus Scan Outbound |
760 | BrutusA2.exe | Attempted Information Leak | ET SCAN Brutus Scan Outbound |
760 | BrutusA2.exe | Attempted Information Leak | ET SCAN Brutus Scan Outbound |
760 | BrutusA2.exe | Attempted Information Leak | ET SCAN Brutus Scan Outbound |
760 | BrutusA2.exe | Attempted Information Leak | ET SCAN Brutus Scan Outbound |