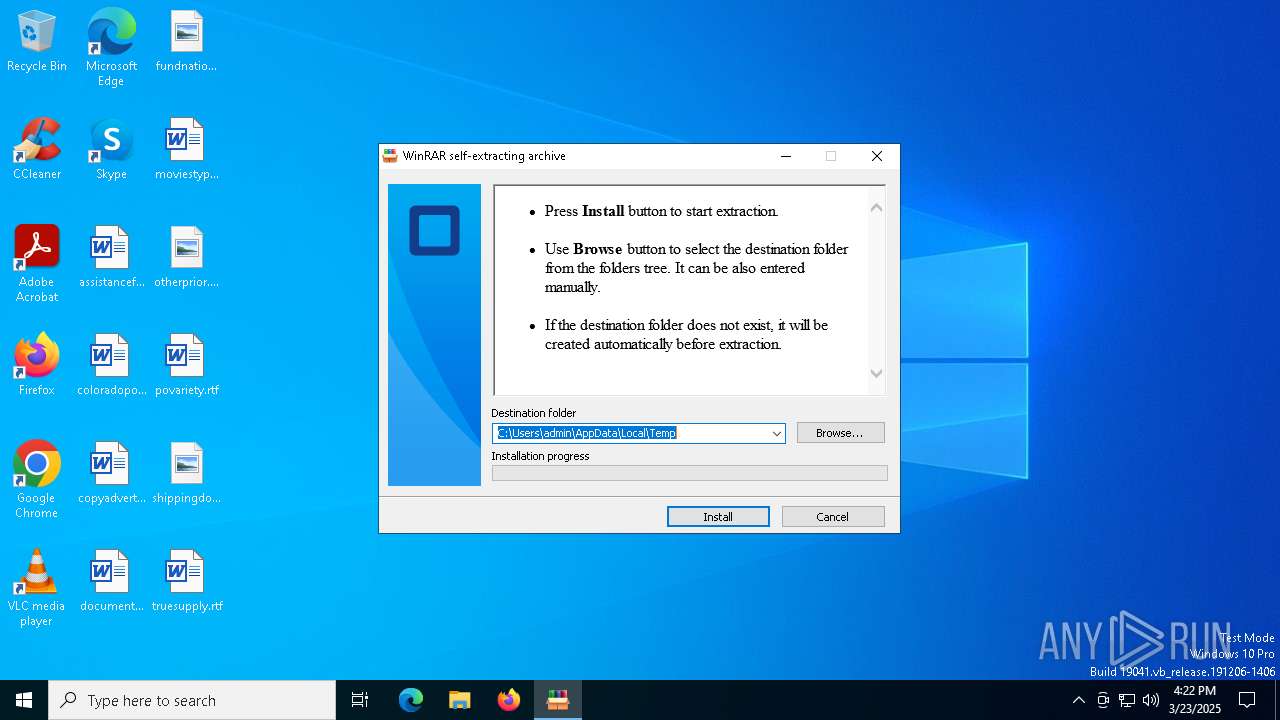
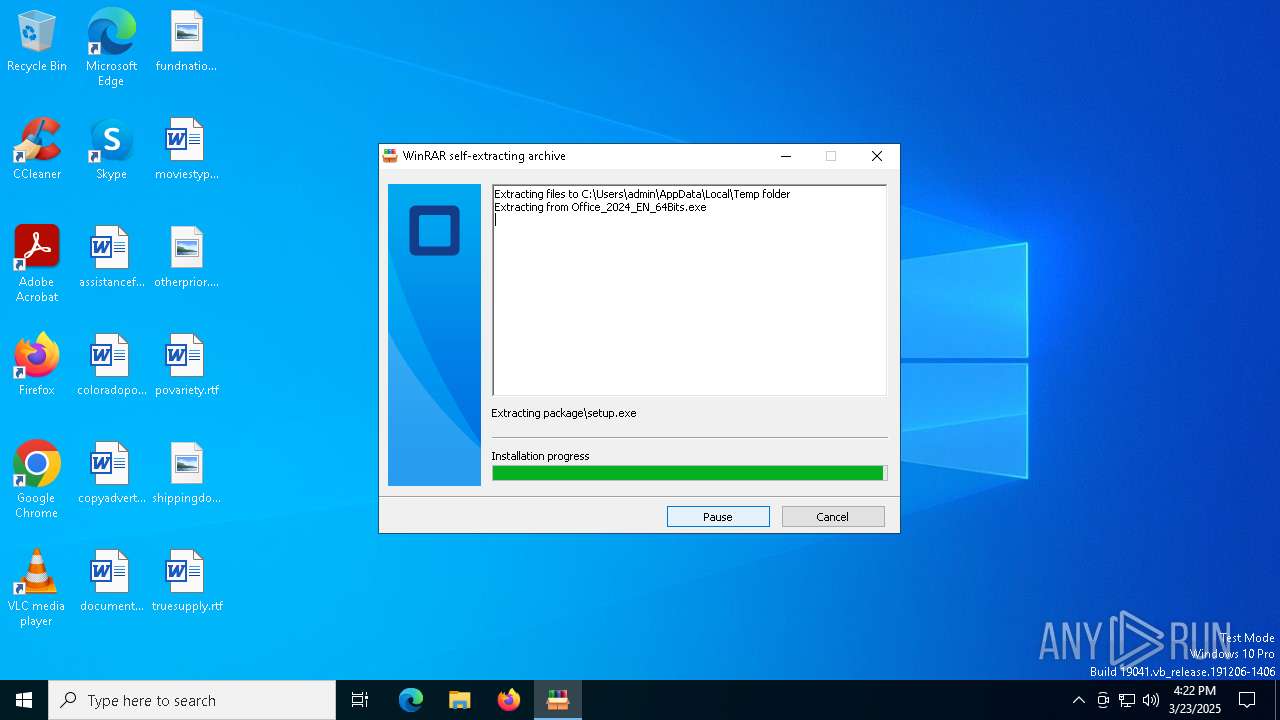
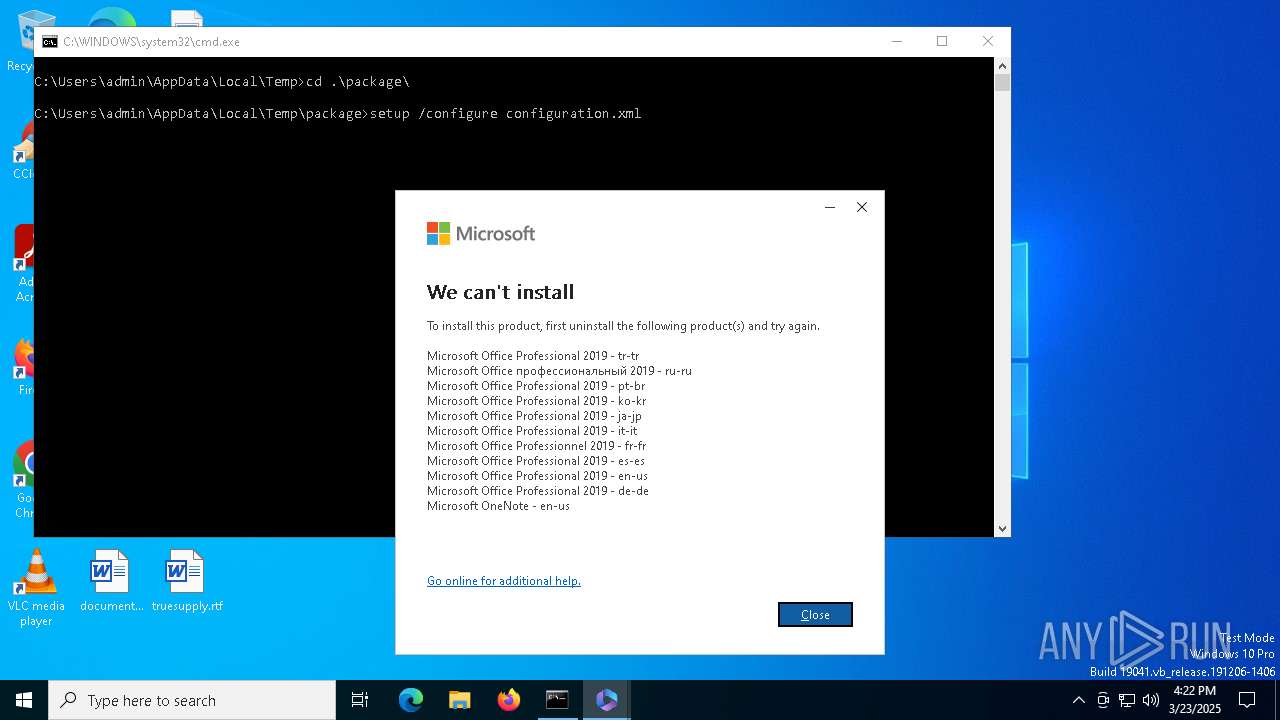
| File name: | Office_2024_EN_64Bits.exe |
| Full analysis: | https://app.any.run/tasks/cf4bed67-5544-4941-8b81-6995bb0366c5 |
| Verdict: | Malicious activity |
| Analysis date: | March 23, 2025, 16:21:55 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 6 sections |
| MD5: | 7408133E63AA3D775BEEDBA6EA6ED3E9 |
| SHA1: | C0C98105A43F1478E659CA675BE30AC56FE0BCB7 |
| SHA256: | 0157AFE7FBB8757A5F92BBB9D2DFBC2F06D9A1A8493B6D25E64A1735AC455811 |
| SSDEEP: | 98304:SfLIQ/3oou0LTVZOyCrFW+JdcIfrp41GzL6u4Ndl2etH7M5ozFhGW9rPhVGaiimE:8jaiqbNQ |
MALICIOUS
Scans artifacts that could help determine the target
- setup.exe (PID: 7580)
- setup.exe (PID: 7468)
SUSPICIOUS
Reads security settings of Internet Explorer
- Office_2024_EN_64Bits.exe (PID: 3332)
- setup.exe (PID: 7468)
- setup.exe (PID: 7580)
Executable content was dropped or overwritten
- Office_2024_EN_64Bits.exe (PID: 3332)
Reads Microsoft Outlook installation path
- Office_2024_EN_64Bits.exe (PID: 3332)
Process drops legitimate windows executable
- Office_2024_EN_64Bits.exe (PID: 3332)
Reads Internet Explorer settings
- Office_2024_EN_64Bits.exe (PID: 3332)
The executable file from the user directory is run by the CMD process
- setup.exe (PID: 7468)
Executing commands from a ".bat" file
- Office_2024_EN_64Bits.exe (PID: 3332)
Starts a Microsoft application from unusual location
- setup.exe (PID: 7468)
- setup.exe (PID: 7580)
There is functionality for taking screenshot (YARA)
- Office_2024_EN_64Bits.exe (PID: 3332)
Application launched itself
- setup.exe (PID: 7468)
Searches for installed software
- setup.exe (PID: 7580)
Starts CMD.EXE for commands execution
- Office_2024_EN_64Bits.exe (PID: 3332)
INFO
Checks proxy server information
- Office_2024_EN_64Bits.exe (PID: 3332)
- setup.exe (PID: 7468)
- setup.exe (PID: 7580)
Checks supported languages
- Office_2024_EN_64Bits.exe (PID: 3332)
- setup.exe (PID: 7468)
- setup.exe (PID: 7580)
Reads the computer name
- Office_2024_EN_64Bits.exe (PID: 3332)
- setup.exe (PID: 7468)
- setup.exe (PID: 7580)
Create files in a temporary directory
- Office_2024_EN_64Bits.exe (PID: 3332)
- setup.exe (PID: 7468)
- setup.exe (PID: 7580)
Process checks computer location settings
- Office_2024_EN_64Bits.exe (PID: 3332)
- setup.exe (PID: 7580)
- setup.exe (PID: 7468)
Reads the machine GUID from the registry
- setup.exe (PID: 7468)
- setup.exe (PID: 7580)
Reads Microsoft Office registry keys
- setup.exe (PID: 7468)
- setup.exe (PID: 7580)
Creates files or folders in the user directory
- setup.exe (PID: 7468)
- setup.exe (PID: 7580)
Reads the software policy settings
- setup.exe (PID: 7580)
- setup.exe (PID: 7468)
Reads Environment values
- setup.exe (PID: 7468)
- setup.exe (PID: 7580)
Process checks whether UAC notifications are on
- setup.exe (PID: 7468)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:10:03 07:51:19+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.33 |
| CodeSize: | 214528 |
| InitializedDataSize: | 263680 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x21d50 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
139
Monitored processes
8
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2692 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3332 | "C:\Users\admin\AppData\Local\Temp\Office_2024_EN_64Bits.exe" | C:\Users\admin\AppData\Local\Temp\Office_2024_EN_64Bits.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 4294967295 Modules
| |||||||||||||||
| 5504 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7404 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\start.bat" " | C:\Windows\SysWOW64\cmd.exe | — | Office_2024_EN_64Bits.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 4294967295 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7412 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
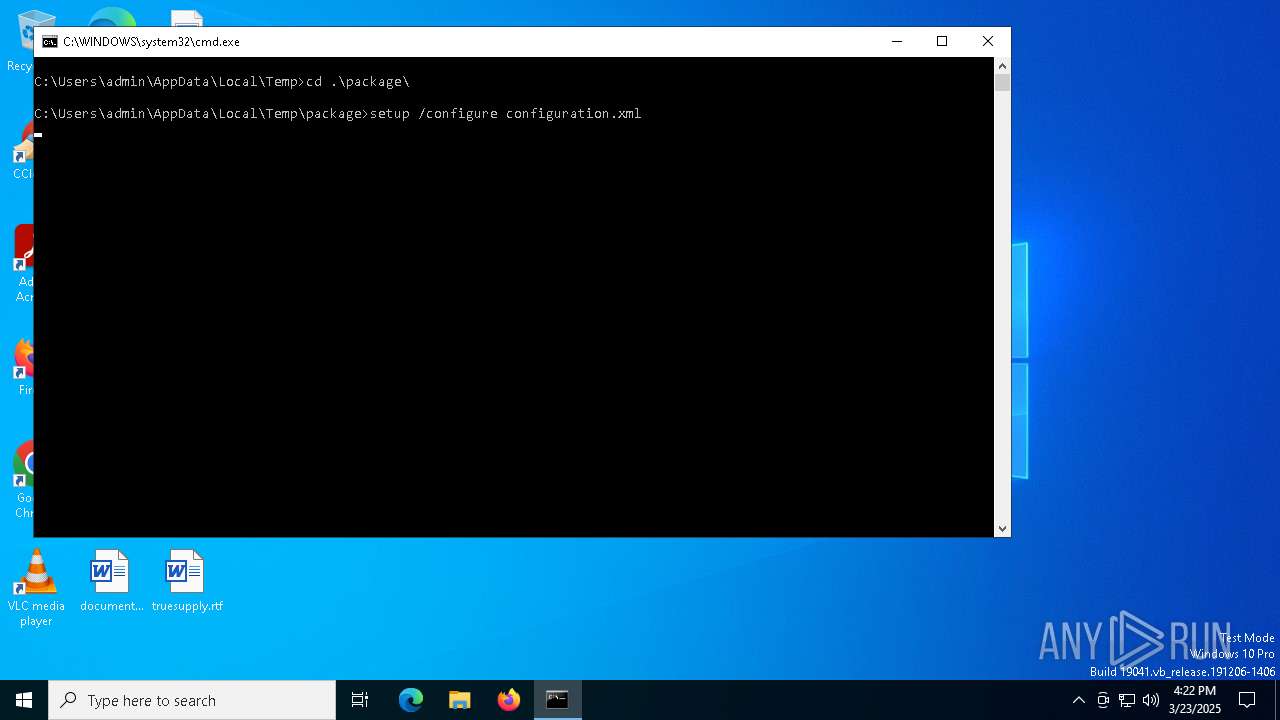
| 7468 | setup /configure configuration.xml | C:\Users\admin\AppData\Local\Temp\package\setup.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft 365 and Office Exit code: 4294967295 Version: 16.0.17531.20046 Modules
| |||||||||||||||
| 7580 | "C:\Users\admin\AppData\Local\Temp\package\setup.exe" ELEVATED sid=S-1-5-21-1693682860-607145093-2874071422-1001 /configure configuration.xml | C:\Users\admin\AppData\Local\Temp\package\setup.exe | setup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft 365 and Office Exit code: 4294967295 Version: 16.0.17531.20046 Modules
| |||||||||||||||
| 7600 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
5 206
Read events
5 074
Write events
126
Delete events
6
Modification events
| (PID) Process: | (3332) Office_2024_EN_64Bits.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3332) Office_2024_EN_64Bits.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3332) Office_2024_EN_64Bits.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (7468) setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 1 | |||
| (PID) Process: | (7468) setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common |
| Operation: | write | Name: | SessionId |
Value: FD749532204ECA48A793121021A36DB1 | |||
| (PID) Process: | (7468) setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\Internet\WebServiceCache\AllUsers\officeclient.microsoft.com\config16--syslcid=1033&build=16.0.17531&crev=3 |
| Operation: | write | Name: | Last |
Value: 0 | |||
| (PID) Process: | (7468) setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (7468) setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (7468) setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (7468) setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
Executable files
1
Suspicious files
9
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7580 | setup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | binary | |
MD5:E097A6D14E491F63DAC41A093C4CC230 | SHA256:9985B173D5485BD34E36C95F94AE721AABEBAA69D8BFFA0A2DDC46864C4D743E | |||
| 3332 | Office_2024_EN_64Bits.exe | C:\Users\admin\AppData\Local\Temp\package\Click To Run.bat | text | |
MD5:AD3ED1D41F9B51F7F203D56597C05958 | SHA256:413B8E555D8F42C56D22D6843708F7BFCB0BBEDB4F833BF3C89880665925BD14 | |||
| 7580 | setup.exe | C:\Users\admin\AppData\Local\Microsoft\Office\OTele\setup.exe.db-shm | binary | |
MD5:C4A28FCF9CA18CE2C1EB29C787B6307E | SHA256:A65A572A8074A56AD756BBE4258AB0E13AC04FDEEE6F07C39EC220EDAEE261FE | |||
| 7468 | setup.exe | C:\Users\admin\AppData\Local\Microsoft\Office\OTele\setup.exe.db-journal | binary | |
MD5:12595C071632F80E9DF72F565D197E96 | SHA256:59522A0A27384E9A98FF6885B295E9D094735DC0F10138362BD82703F159E12F | |||
| 3332 | Office_2024_EN_64Bits.exe | C:\Users\admin\AppData\Local\Temp\package\setup.exe | executable | |
MD5:7488D696F9A3D74E093B4C31EF7282C6 | SHA256:B03C4CC3C1377EE81B1F94DA126E58A30F484D4D935889538FAE1C650DD6828B | |||
| 7580 | setup.exe | C:\Users\admin\AppData\Local\Microsoft\Office\OTele\setup.exe.db | binary | |
MD5:D0DE7DB24F7B0C0FE636B34E253F1562 | SHA256:B6DC74E4A39FFA38ED8C93D58AADEB7E7A0674DAC1152AF413E9DA7313ADE6ED | |||
| 3332 | Office_2024_EN_64Bits.exe | C:\Users\admin\AppData\Local\Temp\start.bat | text | |
MD5:83EEA8C8BF2C4E394BD3D7B5E99B2EE3 | SHA256:D7D4B20EB7E17DCF3CE914AA1BC29A94427434CC67519CACFDE2C13419C70FB7 | |||
| 3332 | Office_2024_EN_64Bits.exe | C:\Users\admin\AppData\Local\Temp\package\configuration.xml | text | |
MD5:B8A2F53FD00F8AC78982A497E2472497 | SHA256:D30E4B5CBF1C373DE24CC2BA9A660BD5006DDE136ACDFE30CF194701C77C1F64 | |||
| 7580 | setup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | binary | |
MD5:AF701737237FEF0A70352C83D58E1831 | SHA256:5D3E037EC1F2DBEC73F11304B87DCE75DED3695FCE32810909AAB3645C246CBA | |||
| 7468 | setup.exe | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\543D14A4-A234-4C5E-A88C-41C59C51A1BE | xml | |
MD5:91BB8334D7B652D1F42407B012B160CC | SHA256:371F68642976C220136CCE536B4F1183D29BABE3B04BED518D344AD757A18274 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
28
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.169:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7580 | setup.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
1512 | backgroundTaskHost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7876 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7876 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.169:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
3216 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 40.126.32.74:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 23.54.109.203:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2112 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1512 | backgroundTaskHost.exe | 20.199.58.43:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
mobile.events.data.microsoft.com |
| whitelisted |