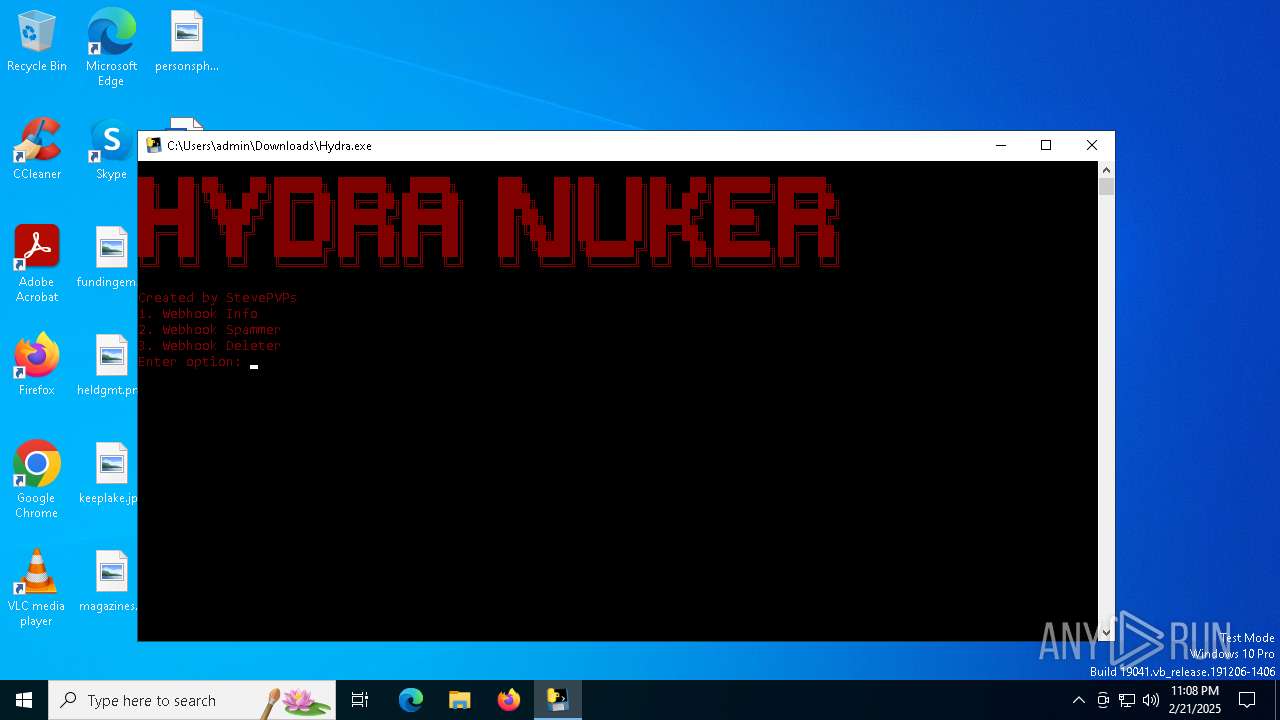
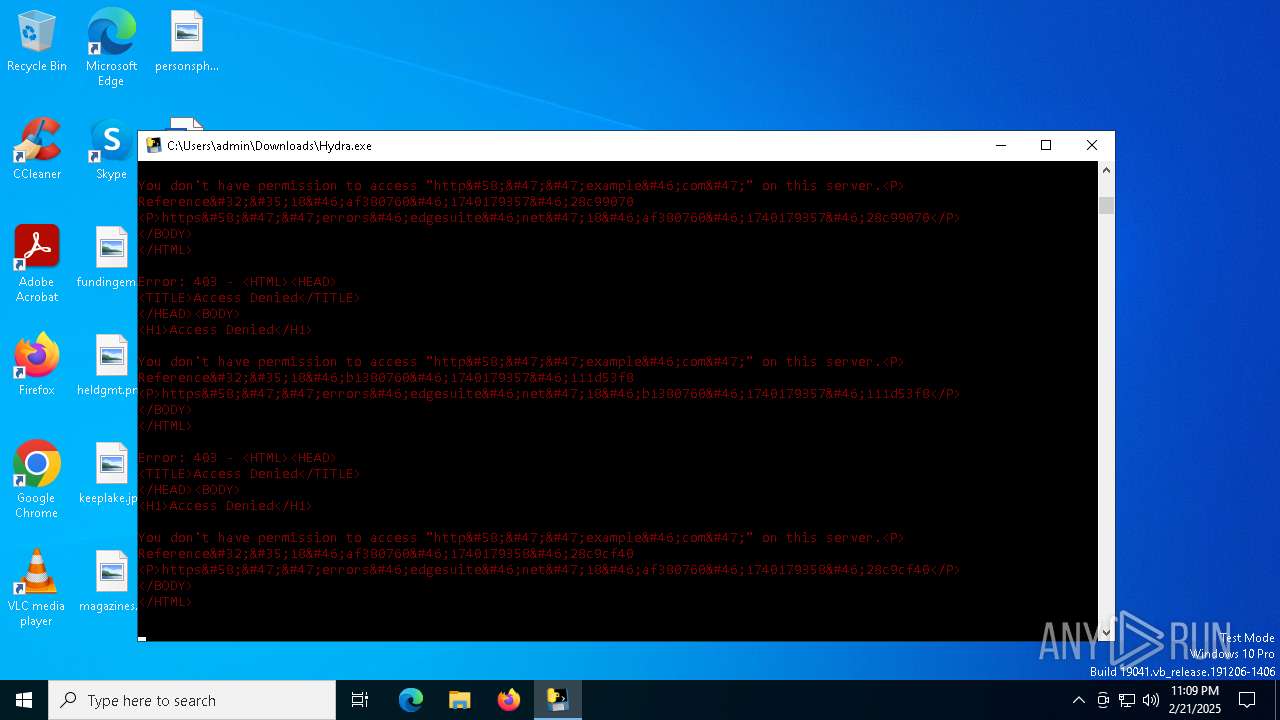
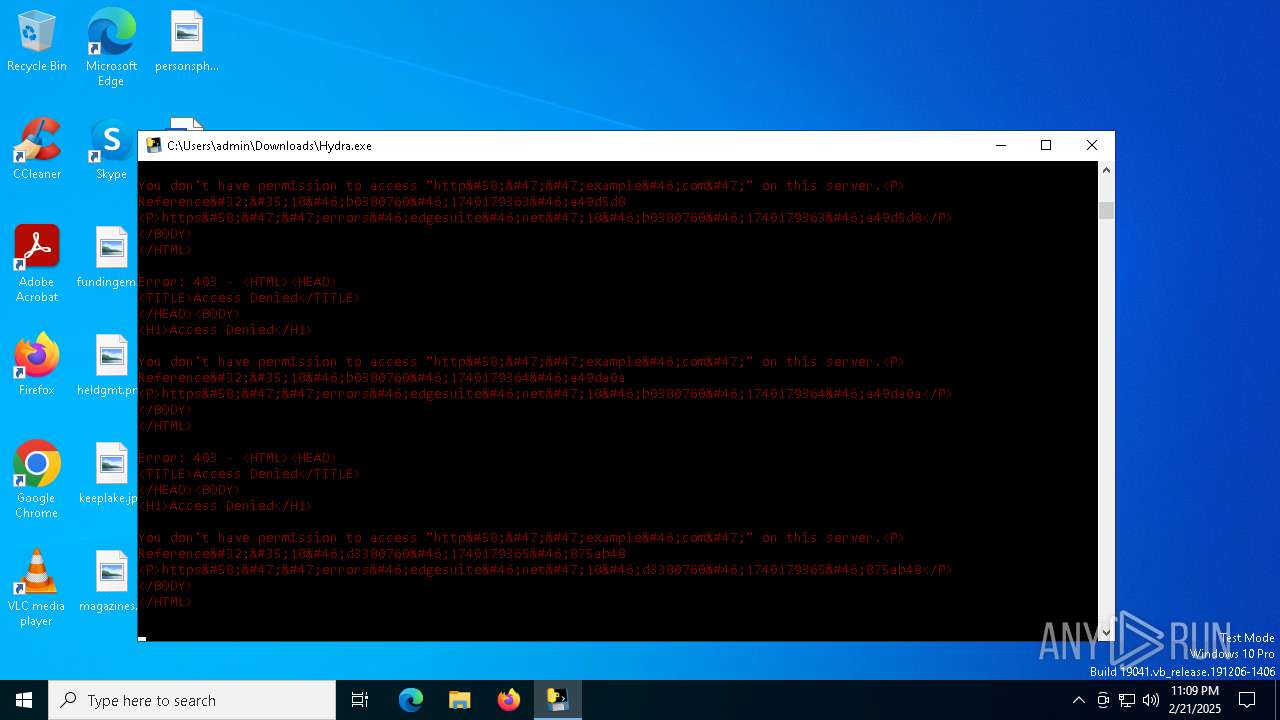
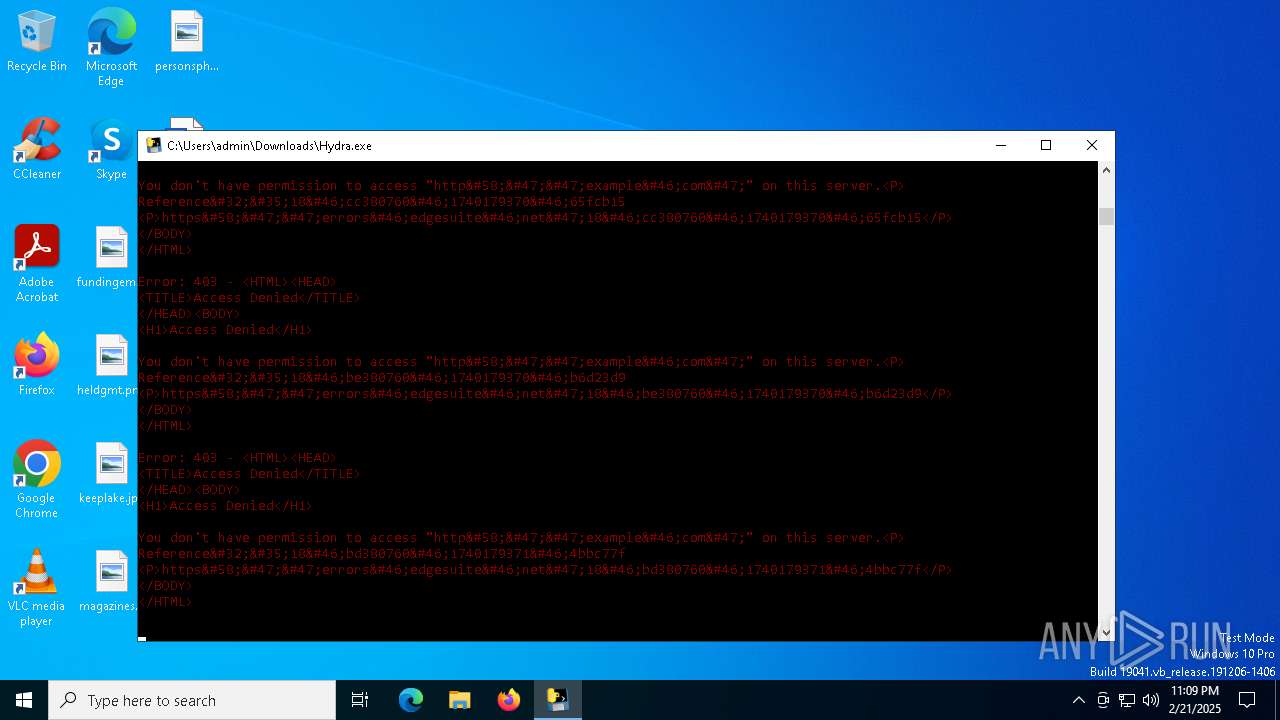
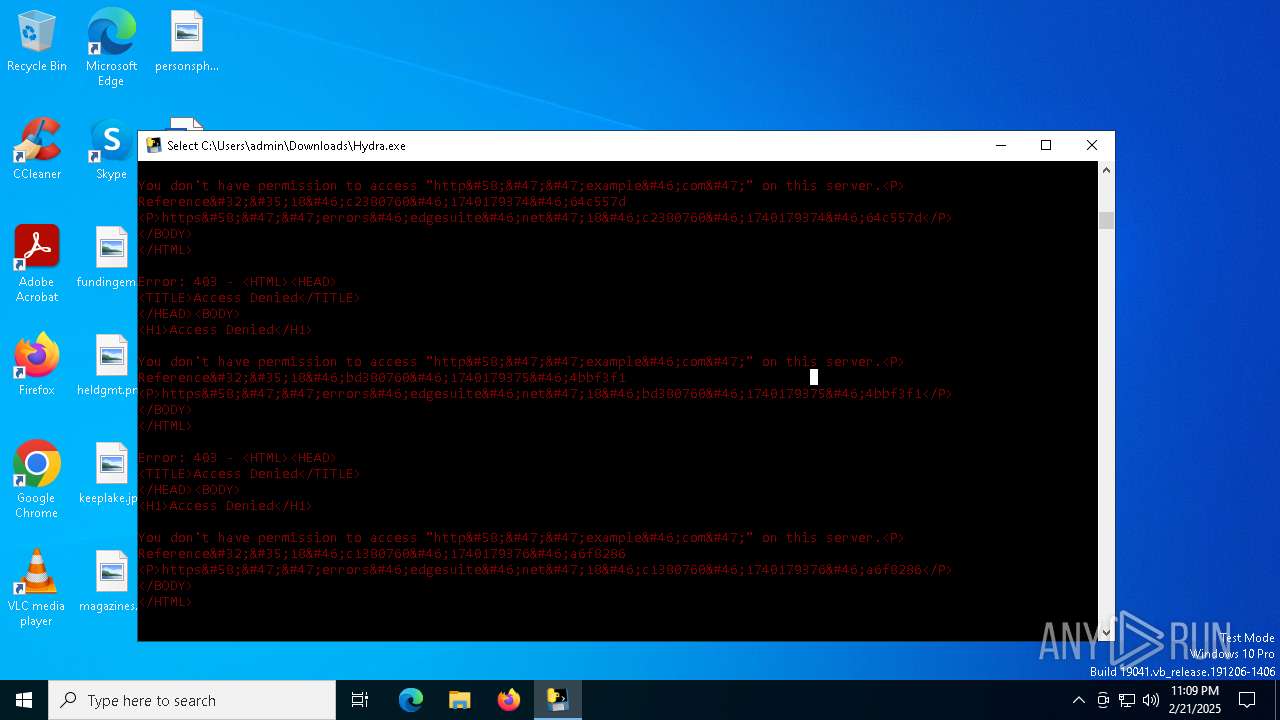
| download: | /STEVEPVPS69/Hydra-Nuker/raw/refs/heads/main/Hydra.exe |
| Full analysis: | https://app.any.run/tasks/4ed9f677-bb6f-4bb9-9efd-e2e32628dc48 |
| Verdict: | Malicious activity |
| Analysis date: | February 21, 2025, 23:08:21 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 6 sections |
| MD5: | D564AED79C7A8F6EECC310F9FCE08546 |
| SHA1: | 63A9C16AB76B688E097620608F8A48E4B1745FC7 |
| SHA256: | 014FECF9B75CD2365CF041B750AA5FEC9132EE265A9BA3C2AE9C1D7A27DCE148 |
| SSDEEP: | 98304:icdoBsyZkzKVfqvWj98WVeIg8S3kAE7t/qtHfktEzafhOsE+XZ0PJQ1knyuj/CKh:UfdrhUTbDGckQBObnTyY1r0Q6l |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops python dynamic module
- Hydra.exe (PID: 5572)
Executable content was dropped or overwritten
- Hydra.exe (PID: 5572)
The process drops C-runtime libraries
- Hydra.exe (PID: 5572)
Application launched itself
- Hydra.exe (PID: 5572)
Process drops legitimate windows executable
- Hydra.exe (PID: 5572)
Loads Python modules
- Hydra.exe (PID: 5236)
Starts CMD.EXE for commands execution
- Hydra.exe (PID: 5236)
INFO
Checks supported languages
- Hydra.exe (PID: 5572)
- Hydra.exe (PID: 5236)
Create files in a temporary directory
- Hydra.exe (PID: 5572)
The sample compiled with english language support
- Hydra.exe (PID: 5572)
Reads the computer name
- Hydra.exe (PID: 5572)
- Hydra.exe (PID: 5236)
Checks proxy server information
- Hydra.exe (PID: 5236)
PyInstaller has been detected (YARA)
- Hydra.exe (PID: 5572)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:02:12 21:09:13+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.41 |
| CodeSize: | 176640 |
| InitializedDataSize: | 152576 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xc380 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
119
Monitored processes
5
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1556 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Hydra.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4628 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | Hydra.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4876 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | Hydra.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5236 | "C:\Users\admin\Downloads\Hydra.exe" | C:\Users\admin\Downloads\Hydra.exe | Hydra.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225786 Modules
| |||||||||||||||
| 5572 | "C:\Users\admin\Downloads\Hydra.exe" | C:\Users\admin\Downloads\Hydra.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225786 Modules
| |||||||||||||||
Total events
698
Read events
698
Write events
0
Delete events
0
Modification events
Executable files
59
Suspicious files
1
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5572 | Hydra.exe | C:\Users\admin\AppData\Local\Temp\_MEI55722\_hashlib.pyd | executable | |
MD5:422E214CA76421E794B99F99A374B077 | SHA256:78223AEF72777EFC93C739F5308A3FC5DE28B7D10E6975B8947552A62592772B | |||
| 5572 | Hydra.exe | C:\Users\admin\AppData\Local\Temp\_MEI55722\_socket.pyd | executable | |
MD5:ABF998769F3CBA685E90FA06E0EC8326 | SHA256:62D0493CED6CA33E2FD8141649DD9889C23B2E9AFC5FDF56EDB4F888C88FB823 | |||
| 5572 | Hydra.exe | C:\Users\admin\AppData\Local\Temp\_MEI55722\VCRUNTIME140.dll | executable | |
MD5:862F820C3251E4CA6FC0AC00E4092239 | SHA256:36585912E5EAF83BA9FEA0631534F690CCDC2D7BA91537166FE53E56C221E153 | |||
| 5572 | Hydra.exe | C:\Users\admin\AppData\Local\Temp\_MEI55722\api-ms-win-core-debug-l1-1-0.dll | executable | |
MD5:33BBECE432F8DA57F17BF2E396EBAA58 | SHA256:7CF0944901F7F7E0D0B9AD62753FC2FE380461B1CCE8CDC7E9C9867C980E3B0E | |||
| 5572 | Hydra.exe | C:\Users\admin\AppData\Local\Temp\_MEI55722\_decimal.pyd | executable | |
MD5:AD4324E5CC794D626FFCCDA544A5A833 | SHA256:040F361F63204B55C17A100C260C7DDFADD00866CC055FBD641B83A6747547D5 | |||
| 5572 | Hydra.exe | C:\Users\admin\AppData\Local\Temp\_MEI55722\_cffi_backend.cp313-win_amd64.pyd | executable | |
MD5:5CBA92E7C00D09A55F5CBADC8D16CD26 | SHA256:0E3D149B91FC7DC3367AB94620A5E13AF6E419F423B31D4800C381468CB8AD85 | |||
| 5572 | Hydra.exe | C:\Users\admin\AppData\Local\Temp\_MEI55722\_ctypes.pyd | executable | |
MD5:2BD5DABBB35398A506E3406BC01EBA26 | SHA256:5C4C489AC052795C27AF063C96BC4DB5AB250144D4839050CFA9BB3836B87C32 | |||
| 5572 | Hydra.exe | C:\Users\admin\AppData\Local\Temp\_MEI55722\api-ms-win-core-datetime-l1-1-0.dll | executable | |
MD5:CFE0C1DFDE224EA5FED9BD5FF778A6E0 | SHA256:0D0F80CBF476AF5B1C9FD3775E086ED0DFDB510CD0CC208EC1CCB04572396E3E | |||
| 5572 | Hydra.exe | C:\Users\admin\AppData\Local\Temp\_MEI55722\_queue.pyd | executable | |
MD5:955B197C38EA5BD537CE9C7CB2109802 | SHA256:73CADE82EE139459FE5841E5631274FC9CAF7F579418B613F278125435653539 | |||
| 5572 | Hydra.exe | C:\Users\admin\AppData\Local\Temp\_MEI55722\_ssl.pyd | executable | |
MD5:CF541CC288AC0BEC9B682A2E0011D1FF | SHA256:E94F0195363C5C9BABFC4C17EC6FB1AA8BBABF59E377DB66CE6A79C4C58BBD07 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
102
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1616 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6032 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.159:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6092 | svchost.exe | GET | 200 | 23.48.23.159:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.159:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6092 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1616 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.159:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6092 | svchost.exe | 23.48.23.159:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.48.23.159:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6092 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 104.126.37.154:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
1176 | svchost.exe | 20.190.159.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
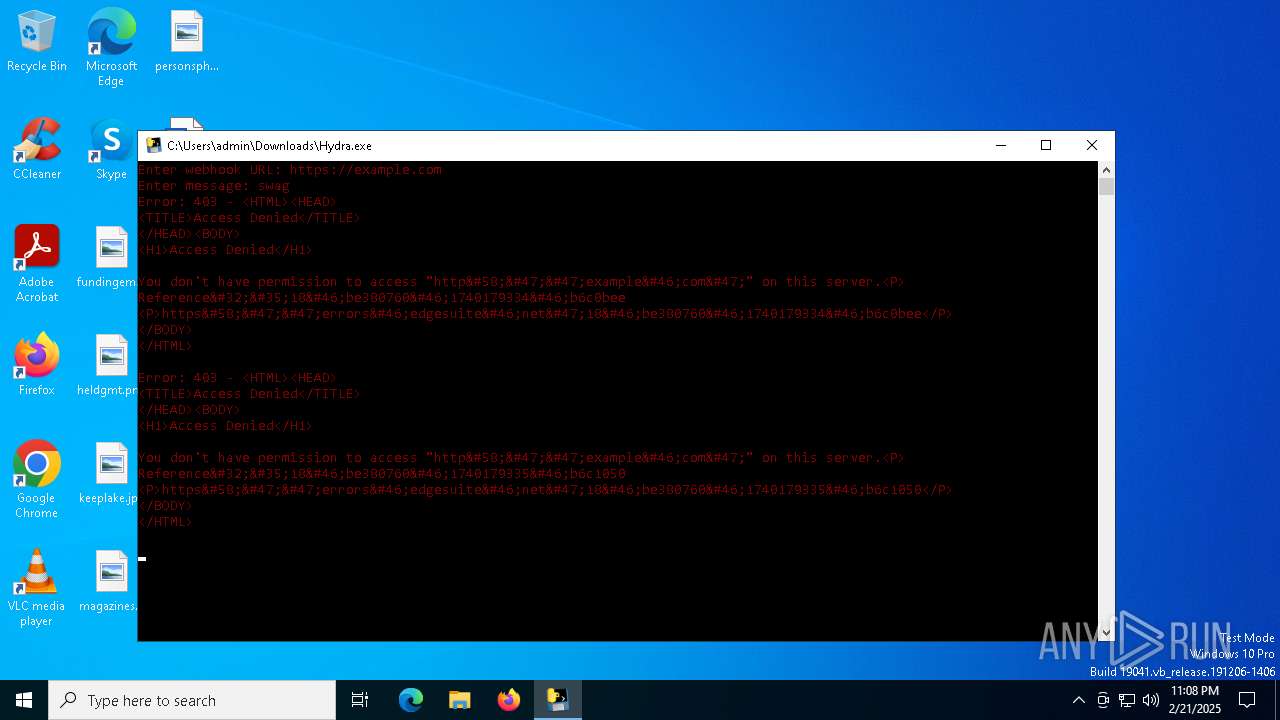
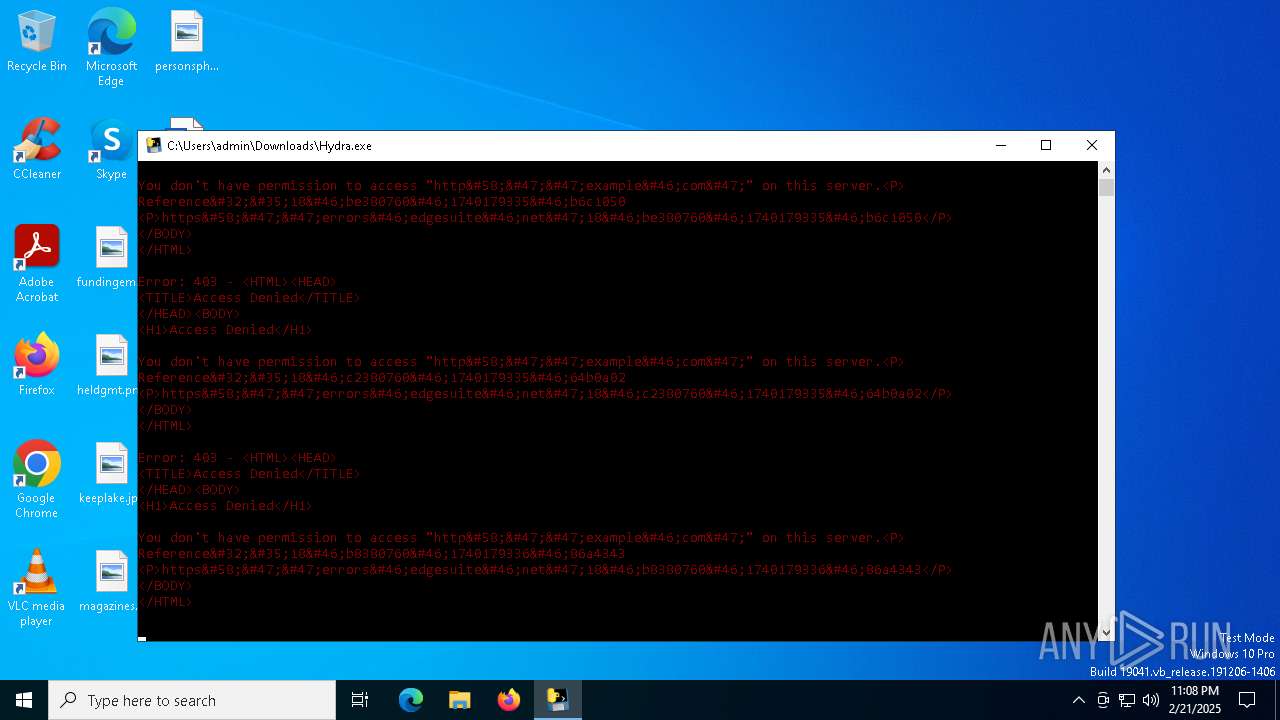
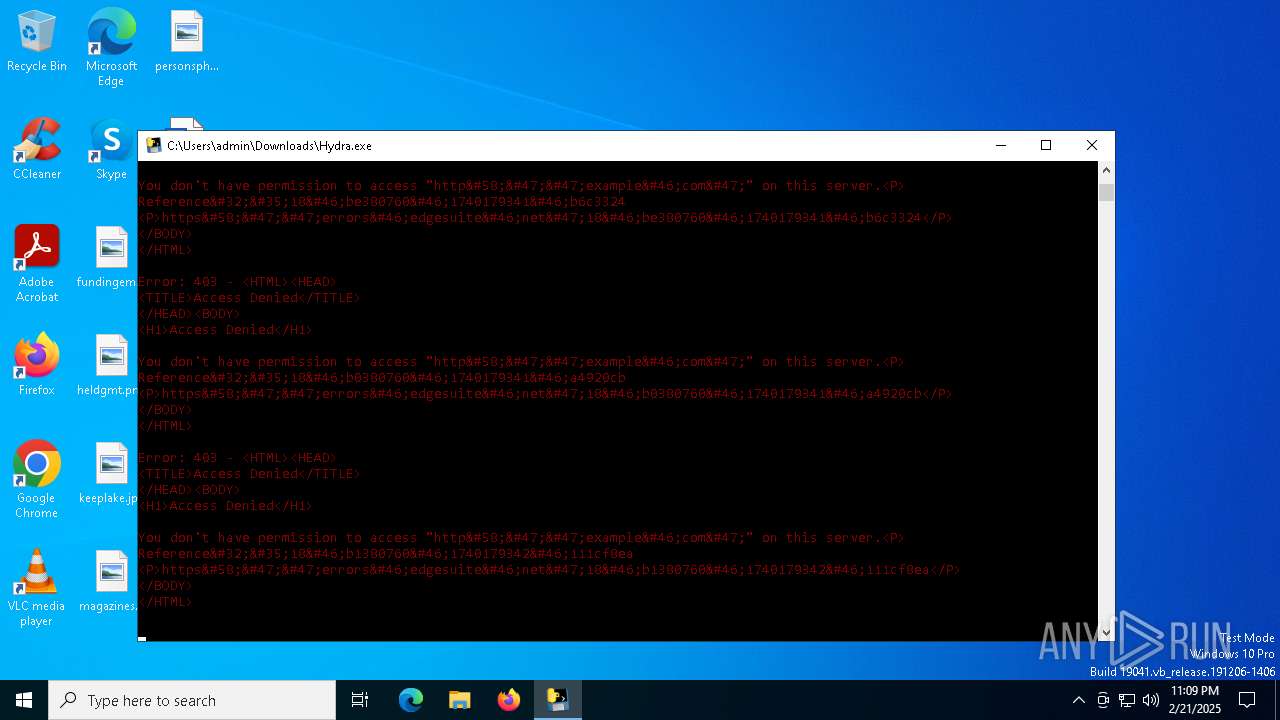
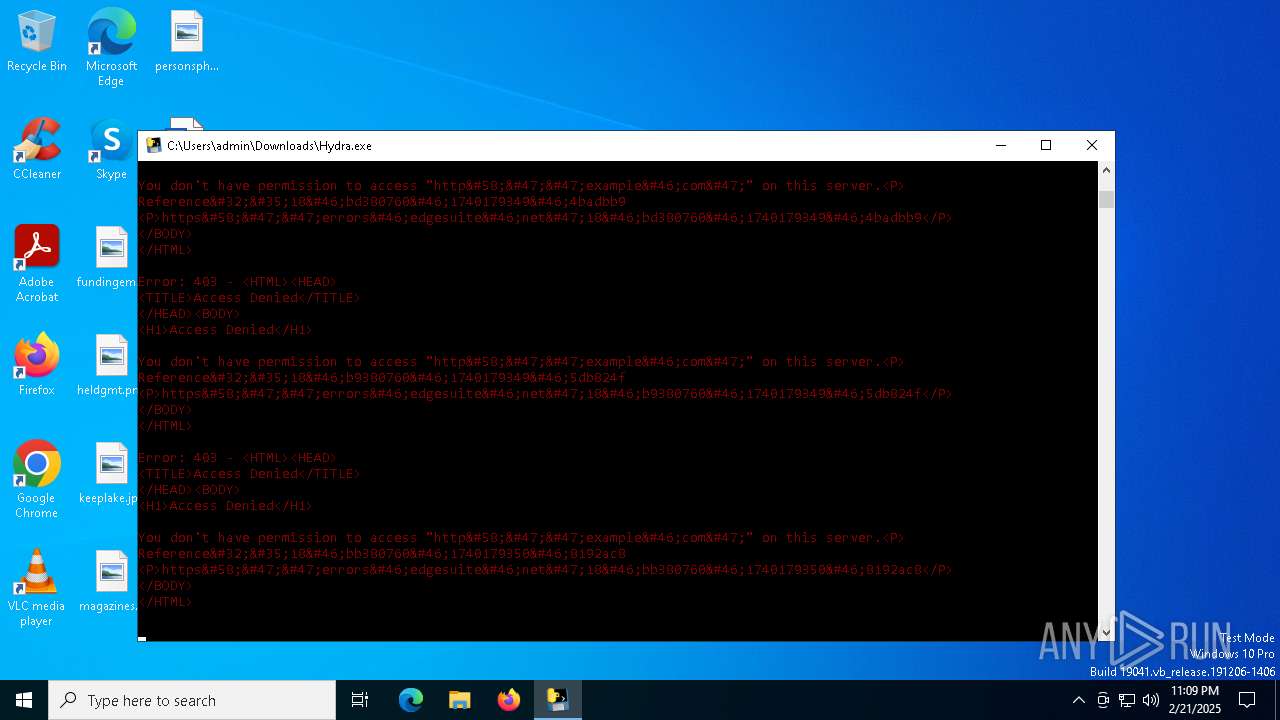
example.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |