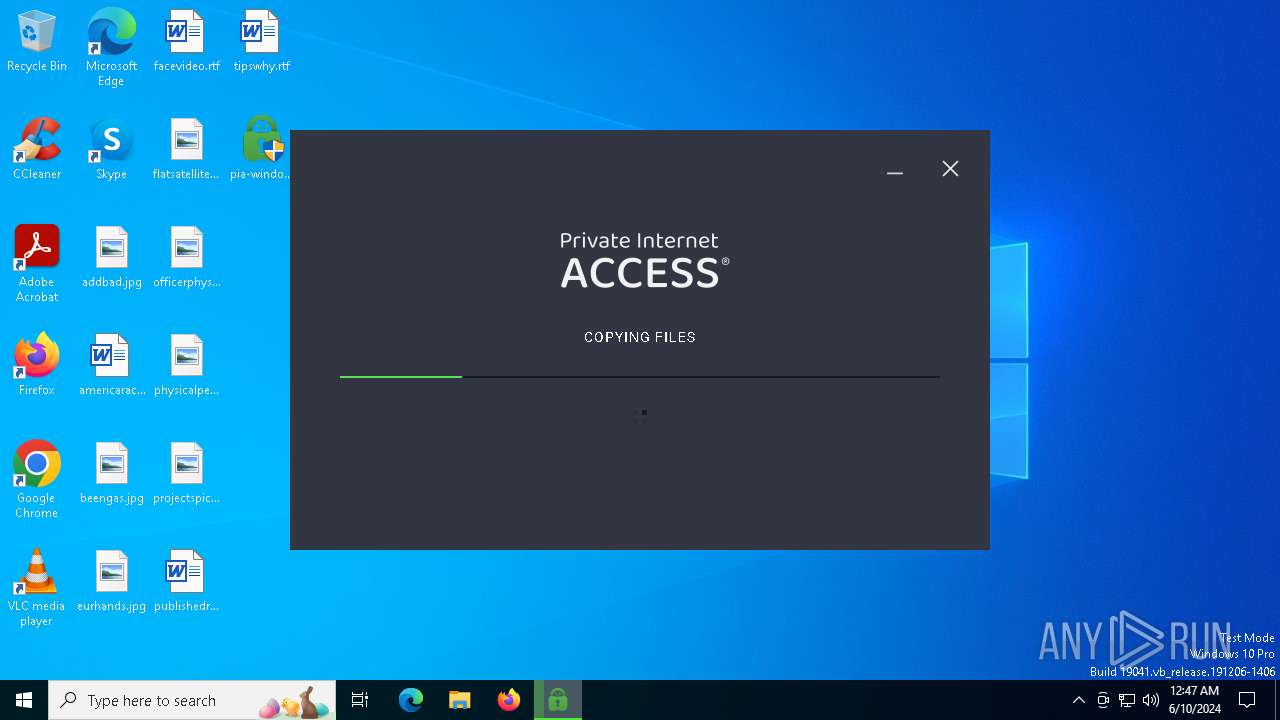
| File name: | pia-windows-x64-3.5.7-08120.exe |
| Full analysis: | https://app.any.run/tasks/c510e55a-760d-4714-bf87-581e1ade913b |
| Verdict: | Malicious activity |
| Analysis date: | June 10, 2024, 00:47:33 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows |
| MD5: | C5A4DAD9025BD2196874B395DB2093E7 |
| SHA1: | F38AC163E2064F249190A2CF7B3E50E1C66BEEF8 |
| SHA256: | 013A8235CB3126EA004C16A48671CB3045F81031864F2AF56BB9E50A6737EA28 |
| SSDEEP: | 393216:ltZJAGZxQBpPmXGawOgKoiOT+w57wghr:jZOB/CgkOFhr |
MALICIOUS
Creates a writable file in the system directory
- drvinst.exe (PID: 6776)
- drvinst.exe (PID: 6828)
- msiexec.exe (PID: 2680)
- drvinst.exe (PID: 1448)
Drops the executable file immediately after the start
- drvinst.exe (PID: 6776)
- drvinst.exe (PID: 6828)
- pia-windows-x64-3.5.7-08120.exe (PID: 6460)
- msiexec.exe (PID: 6976)
- msiexec.exe (PID: 2680)
- drvinst.exe (PID: 1448)
SUSPICIOUS
Drops a system driver (possible attempt to evade defenses)
- pia-windows-x64-3.5.7-08120.exe (PID: 6460)
- drvinst.exe (PID: 6776)
- drvinst.exe (PID: 6828)
- msiexec.exe (PID: 2680)
- drvinst.exe (PID: 1448)
The process drops C-runtime libraries
- pia-windows-x64-3.5.7-08120.exe (PID: 6460)
Reads security settings of Internet Explorer
- pia-windows-x64-3.5.7-08120.exe (PID: 6460)
Checks Windows Trust Settings
- pia-windows-x64-3.5.7-08120.exe (PID: 6460)
- drvinst.exe (PID: 6776)
- drvinst.exe (PID: 1448)
Creates files in the driver directory
- drvinst.exe (PID: 6776)
- drvinst.exe (PID: 6828)
- msiexec.exe (PID: 2680)
- drvinst.exe (PID: 1448)
Executable content was dropped or overwritten
- drvinst.exe (PID: 6776)
- drvinst.exe (PID: 6828)
- drvinst.exe (PID: 1448)
- pia-windows-x64-3.5.7-08120.exe (PID: 6460)
Creates or modifies Windows services
- drvinst.exe (PID: 6828)
Executes as Windows Service
- pia-service.exe (PID: 6908)
- VSSVC.exe (PID: 7040)
Creates a software uninstall entry
- pia-windows-x64-3.5.7-08120.exe (PID: 6460)
Detected use of alternative data streams (AltDS)
- pia-client.exe (PID: 7164)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 6976)
Process drops legitimate windows executable
- pia-windows-x64-3.5.7-08120.exe (PID: 6460)
INFO
Checks supported languages
- pia-windows-x64-3.5.7-08120.exe (PID: 6460)
- drvinst.exe (PID: 6776)
- drvinst.exe (PID: 6828)
- pia-service.exe (PID: 6908)
- msiexec.exe (PID: 6976)
- pia-client.exe (PID: 7164)
- msiexec.exe (PID: 2680)
- drvinst.exe (PID: 1448)
- pia-wgservice.exe (PID: 5656)
Reads the computer name
- pia-windows-x64-3.5.7-08120.exe (PID: 6460)
- drvinst.exe (PID: 6828)
- pia-service.exe (PID: 6908)
- msiexec.exe (PID: 6976)
- drvinst.exe (PID: 6776)
- pia-client.exe (PID: 7164)
- msiexec.exe (PID: 2680)
- drvinst.exe (PID: 1448)
- pia-wgservice.exe (PID: 5656)
Reads the software policy settings
- pia-windows-x64-3.5.7-08120.exe (PID: 6460)
- drvinst.exe (PID: 6776)
- drvinst.exe (PID: 1448)
Reads the machine GUID from the registry
- pia-windows-x64-3.5.7-08120.exe (PID: 6460)
- drvinst.exe (PID: 6776)
- pia-service.exe (PID: 6908)
- drvinst.exe (PID: 1448)
Create files in a temporary directory
- pia-windows-x64-3.5.7-08120.exe (PID: 6460)
Creates files in the program directory
- pia-windows-x64-3.5.7-08120.exe (PID: 6460)
- pia-service.exe (PID: 6908)
Creates files or folders in the user directory
- pia-client.exe (PID: 7164)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6976)
- msiexec.exe (PID: 2680)
Application launched itself
- msiexec.exe (PID: 6976)
Creates a software uninstall entry
- msiexec.exe (PID: 6976)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:03:27 12:04:13+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.29 |
| CodeSize: | 340992 |
| InitializedDataSize: | 21925376 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x2cd84 |
| OSVersion: | 6.1 |
| ImageVersion: | - |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
Total processes
133
Monitored processes
14
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1448 | DrvInst.exe "4" "9" "C:\WINDOWS\Temp\6c8506b80b12ca9f35baac96e6ddd0dd17f8ce6c71eb160df627fdf216db7a4a\wintun.inf" "9" "4a936323f" "00000000000001E0" "WinSta0\Default" "00000000000001F0" "208" "C:\WINDOWS\Temp\6c8506b80b12ca9f35baac96e6ddd0dd17f8ce6c71eb160df627fdf216db7a4a" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2680 | C:\Windows\System32\MsiExec.exe -Embedding 6BB1566589A4803C33EE9B3DDE36B5FB E Global\MSI0000 | C:\Windows\System32\msiexec.exe | msiexec.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5428 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5656 | "C:\Program Files\Private Internet Access\pia-wgservice.exe" /cleaninterface wgpia0 | C:\Program Files\Private Internet Access\pia-wgservice.exe | — | pia-service.exe | |||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 0 Modules
| |||||||||||||||
| 5920 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6036 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | pia-wgservice.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6340 | "C:\Users\admin\Desktop\pia-windows-x64-3.5.7-08120.exe" | C:\Users\admin\Desktop\pia-windows-x64-3.5.7-08120.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 6460 | "C:\Users\admin\Desktop\pia-windows-x64-3.5.7-08120.exe" | C:\Users\admin\Desktop\pia-windows-x64-3.5.7-08120.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 6776 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{80471874-1ec1-d74c-8a96-78644a394e15}\oemvista.inf" "9" "4913cc9cb" "00000000000001E0" "WinSta0\Default" "00000000000001F0" "208" "c:\program files\private internet access\tap\win10" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6828 | DrvInst.exe "2" "211" "ROOT\NET\0000" "C:\WINDOWS\INF\oem1.inf" "oem1.inf:3beb73aff103cc24:tap-pia-0901.ndi:9.24.2.601:tap-pia-0901," "4913cc9cb" "00000000000001EC" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
19 214
Read events
18 871
Write events
316
Delete events
27
Modification events
| (PID) Process: | (6460) pia-windows-x64-3.5.7-08120.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\piavpn |
| Operation: | write | Name: | URL Protocol |
Value: | |||
| (PID) Process: | (6460) pia-windows-x64-3.5.7-08120.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\Setup\SetupapiLogStatus |
| Operation: | write | Name: | setupapi.dev.log |
Value: 4096 | |||
| (PID) Process: | (6828) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\tap-pia-0901 |
| Operation: | write | Name: | Owners |
Value: oem1.inf | |||
| (PID) Process: | (6828) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Setup\PnpLockdownFiles\%SystemRoot%/System32/drivers/tap-pia-0901.sys |
| Operation: | write | Name: | Owners |
Value: oem1.inf | |||
| (PID) Process: | (6828) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\DRIVERS\DriverDatabase\DriverPackages\oemvista.inf_amd64_4c9c04020589fe8d\Descriptors\tap-pia-0901 |
| Operation: | write | Name: | Configuration |
Value: tap-pia-0901.ndi | |||
| (PID) Process: | (6828) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\DRIVERS\DriverDatabase\DriverPackages\oemvista.inf_amd64_4c9c04020589fe8d\Descriptors\tap-pia-0901 |
| Operation: | write | Name: | Manufacturer |
Value: %provider% | |||
| (PID) Process: | (6828) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\DRIVERS\DriverDatabase\DriverPackages\oemvista.inf_amd64_4c9c04020589fe8d\Descriptors\tap-pia-0901 |
| Operation: | write | Name: | Description |
Value: %devicedescription% | |||
| (PID) Process: | (6828) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\DRIVERS\DriverDatabase\DriverPackages\oemvista.inf_amd64_4c9c04020589fe8d\Configurations\tap-pia-0901.ndi |
| Operation: | write | Name: | Service |
Value: tap-pia-0901 | |||
| (PID) Process: | (6828) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\DRIVERS\DriverDatabase\DriverPackages\oemvista.inf_amd64_4c9c04020589fe8d\Configurations\tap-pia-0901.ndi |
| Operation: | write | Name: | ConfigScope |
Value: 5 | |||
| (PID) Process: | (6828) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\DRIVERS\DriverDatabase\DriverPackages\oemvista.inf_amd64_4c9c04020589fe8d\Configurations\tap-pia-0901.ndi\Driver\Ndi |
| Operation: | write | Name: | Service |
Value: tap-pia-0901 | |||
Executable files
152
Suspicious files
645
Text files
564
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6460 | pia-windows-x64-3.5.7-08120.exe | C:\Program Files\Private Internet Access\Qt\labs\folderlistmodel\plugins.qmltypes | text | |
MD5:3E72475117B4FCA01344C01E945D2E4E | SHA256:5F3888C687398413E1273BC7380FDFA50CBD3D502EB9FF3F63B40BD4D66F29BD | |||
| 6460 | pia-windows-x64-3.5.7-08120.exe | C:\Program Files\Private Internet Access\Qt\labs\settings\plugins.qmltypes | text | |
MD5:6669D4C46230AB0F3481099D627FFB99 | SHA256:79BF121D97758B4F7982BECB71D50A39C4EF65161857279CB5E53ABC84C4BFEB | |||
| 6460 | pia-windows-x64-3.5.7-08120.exe | C:\Program Files\Private Internet Access\architecture.txt | text | |
MD5:0027F42E1E5DFCB4FD5F8F9C6DB89AF3 | SHA256:7520B5A1B312EFDE4FD7E2793EF4BC0CF8F1C235F778D203AB7216A0E31B3880 | |||
| 6460 | pia-windows-x64-3.5.7-08120.exe | C:\Program Files\Private Internet Access\Qt\labs\settings\qmldir | text | |
MD5:B1F564E1CEC8D91FFA94C36EDE2A8F24 | SHA256:49522AF40488E52E8A1DEDA8B51F591DF1ACCA1605336784EB7D4299E5AF02EC | |||
| 6460 | pia-windows-x64-3.5.7-08120.exe | C:\Program Files\Private Internet Access\QtGraphicalEffects\Colorize.qml | text | |
MD5:911DF8B6D57C50176D64598BB623514E | SHA256:C97BCEA811DC59D480E9857196AC553D4863BA53783040BDFC7F5E339D429865 | |||
| 6460 | pia-windows-x64-3.5.7-08120.exe | C:\Program Files\Private Internet Access\QtGraphicalEffects\ColorOverlay.qml | text | |
MD5:CA164AC3D826D66663092DACF1346749 | SHA256:30D97360EFE13C029774513E6176BF68C8FAC7C87F8E03DDE458C8321784BA12 | |||
| 6460 | pia-windows-x64-3.5.7-08120.exe | C:\Program Files\Private Internet Access\QtGraphicalEffects\Blend.qml | text | |
MD5:46BDDF3E69B845AC1C59C7352906FE38 | SHA256:AEB67E09E08878484F0C1351A88F823D4A9D063C59EF33F56399747A2F058641 | |||
| 6460 | pia-windows-x64-3.5.7-08120.exe | C:\Program Files\Private Internet Access\Qt\labs\platform\plugins.qmltypes | text | |
MD5:4B1DAC5DD47A1928E4B1635968774D68 | SHA256:2E1A5C057B921CA6AA70BDD28E87F5BE907F6E8AD34B45DD8504E5FE6F92A632 | |||
| 6460 | pia-windows-x64-3.5.7-08120.exe | C:\Program Files\Private Internet Access\QtGraphicalEffects\DirectionalBlur.qml | text | |
MD5:D9AF0AAB657E1A2D4FB2AE18A8D5CA61 | SHA256:8E60BB7C92D977238D52808587BA0DCA664D6119278B54453BF07657C815C872 | |||
| 6460 | pia-windows-x64-3.5.7-08120.exe | C:\Program Files\Private Internet Access\QtGraphicalEffects\ConicalGradient.qml | text | |
MD5:BCFC5A243AC02C54BF7DCE968A917D53 | SHA256:F331E1CFA131C3838603948333A1726887817626E6D7569E9540E084DF0D6075 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
37
DNS requests
9
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5576 | svchost.exe | GET | 200 | 2.19.117.22:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
— | — | GET | 200 | 2.17.0.227:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
5140 | MoUsoCoreWorker.exe | GET | 200 | 2.17.0.227:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
5576 | svchost.exe | GET | 200 | 2.17.0.227:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
— | — | GET | 200 | 104.19.240.167:443 | https://serverlist.piaservers.net/vpninfo/servers/v6 | unknown | text | 114 Kb | unknown |
— | — | GET | 200 | 104.19.240.167:443 | https://serverlist.piaservers.net/shadow_socks | unknown | text | 1.50 Kb | unknown |
— | — | GET | 200 | 172.64.151.73:443 | https://api.privateinternetaccess.com/api/client/status | unknown | binary | 39 b | unknown |
— | — | POST | 204 | 104.110.240.59:443 | https://www.bing.com/threshold/xls.aspx | unknown | — | — | unknown |
— | — | GET | 200 | 104.110.240.131:443 | https://www.bing.com/rb/18/jnc,nj/6hU_LneafI_NFLeDvM367ebFaKQ.js?bu=DyIrb3t-gQF4cnWyAbUBK6UBK7gB&or=w | unknown | s | 21.3 Kb | unknown |
— | — | GET | 200 | 172.64.151.73:443 | https://www.privateinternetaccess.com/clients/desktop/release | unknown | binary | 1.14 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
5140 | MoUsoCoreWorker.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5576 | svchost.exe | 2.19.117.22:80 | crl.microsoft.com | Akamai International B.V. | GB | unknown |
5576 | svchost.exe | 2.17.0.227:80 | www.microsoft.com | AKAMAI-AS | DK | unknown |
— | — | 2.17.0.227:80 | www.microsoft.com | AKAMAI-AS | DK | unknown |
5140 | MoUsoCoreWorker.exe | 2.17.0.227:80 | www.microsoft.com | AKAMAI-AS | DK | unknown |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
5576 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5140 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
api.privateinternetaccess.com |
| unknown |
www.privateinternetaccess.com |
| unknown |
serverlist.piaservers.net |
| unknown |
r.bing.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Generic Protocol Command Decode | SURICATA HTTP Request abnormal Content-Encoding header |
5 ETPRO signatures available at the full report