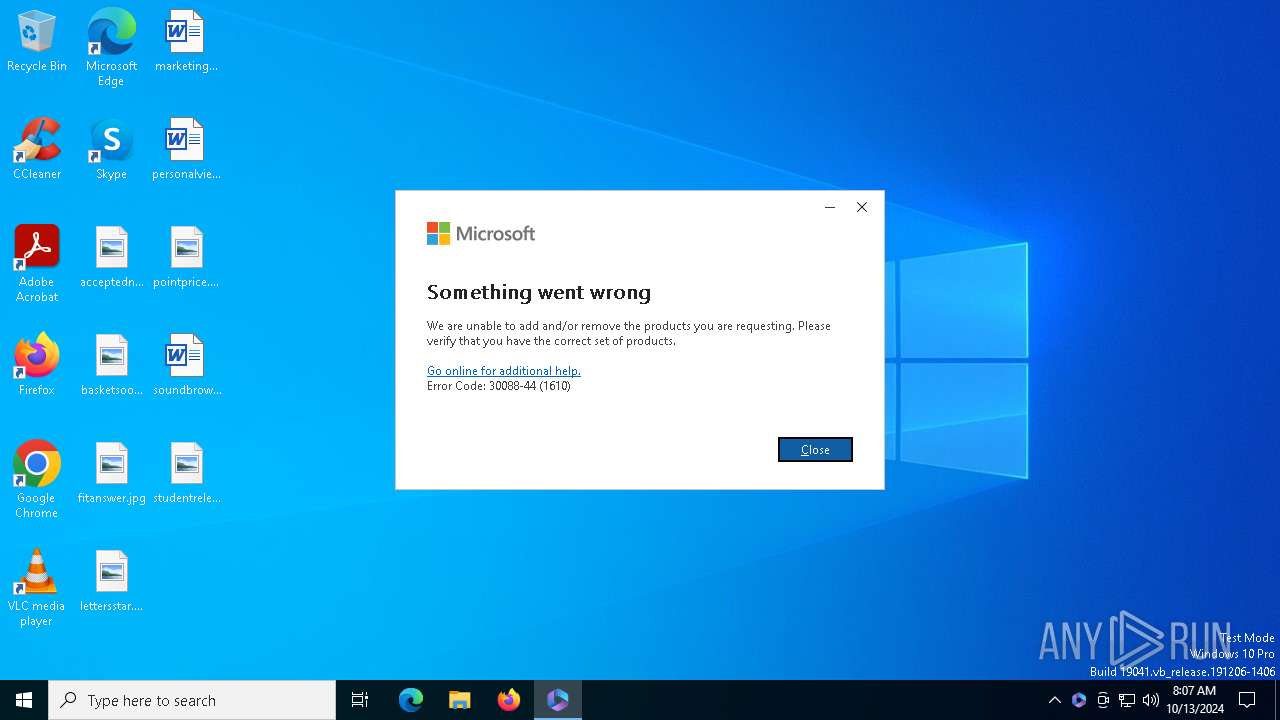
| File name: | OfficeSetup.exe |
| Full analysis: | https://app.any.run/tasks/e7d457c5-b50f-42fc-811f-814be476270b |
| Verdict: | Malicious activity |
| Analysis date: | October 13, 2024, 08:06:37 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 7AD1B4F05EBE11FEAEE40D37FE1A335C |
| SHA1: | C5BAA1B938155D7170DE7211904E4B96EF484C83 |
| SHA256: | 0130D8E24A40D46A5C694269FC247DE251793C13D0DFB0761A91A05D377DBB6B |
| SSDEEP: | 98304:H28/DYbp8XoJ0puZVXBKkV3wPHwAsFhZVJGtQZCIUcfShE0VRKdAGERtwTM6JGeL:YB57 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops legitimate windows executable
- OfficeSetup.exe (PID: 6100)
- OfficeClickToRun.exe (PID: 6760)
- OfficeClickToRun.exe (PID: 7924)
Application launched itself
- OfficeSetup.exe (PID: 6100)
- OfficeSetup.exe (PID: 6856)
Starts a Microsoft application from unusual location
- OfficeSetup.exe (PID: 6100)
- OfficeSetup.exe (PID: 6856)
- OfficeSetup.exe (PID: 4432)
Reads security settings of Internet Explorer
- OfficeSetup.exe (PID: 6856)
Executable content was dropped or overwritten
- OfficeClickToRun.exe (PID: 6760)
- OfficeClickToRun.exe (PID: 7924)
The process drops C-runtime libraries
- OfficeClickToRun.exe (PID: 6760)
INFO
Checks supported languages
- OfficeSetup.exe (PID: 6100)
- OfficeSetup.exe (PID: 6856)
Reads the machine GUID from the registry
- OfficeSetup.exe (PID: 6856)
Reads the computer name
- OfficeSetup.exe (PID: 6856)
Reads Microsoft Office registry keys
- OfficeSetup.exe (PID: 6856)
Process checks computer location settings
- OfficeSetup.exe (PID: 6856)
Process checks whether UAC notifications are on
- OfficeSetup.exe (PID: 6856)
Checks proxy server information
- OfficeSetup.exe (PID: 6856)
The process uses the downloaded file
- OfficeSetup.exe (PID: 6856)
Executes as Windows Service
- OfficeClickToRun.exe (PID: 7924)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:10:05 07:57:55+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit, Removable run from swap, Net run from swap |
| PEType: | PE32 |
| LinkerVersion: | 14.38 |
| CodeSize: | 4569600 |
| InitializedDataSize: | 2993664 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3e2f62 |
| OSVersion: | 5.2 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 16.0.18025.20140 |
| ProductVersionNumber: | 16.0.18025.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | Microsoft Corporation |
| FileDescription: | Microsoft 365 and Office |
| FileVersion: | 16.0.18025.20140 |
| InternalName: | Bootstrapper.exe |
| LegalTrademarks1: | Microsoft® is a registered trademark of Microsoft Corporation. |
| LegalTrademarks2: | Windows® is a registered trademark of Microsoft Corporation. |
| OriginalFileName: | Bootstrapper.exe |
| ProductName: | Microsoft Office |
| ProductVersion: | 16.0.18025.20140 |
Total processes
133
Monitored processes
7
Malicious processes
1
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4432 | "C:\Users\admin\AppData\Local\Temp\OfficeSetup.exe" ELEVATED sid=S-1-5-21-1693682860-607145093-2874071422-1001 RELAUNCHED | C:\Users\admin\AppData\Local\Temp\OfficeSetup.exe | OfficeSetup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft 365 and Office Version: 16.0.18025.20140 Modules
| |||||||||||||||
| 6100 | "C:\Users\admin\AppData\Local\Temp\OfficeSetup.exe" | C:\Users\admin\AppData\Local\Temp\OfficeSetup.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft 365 and Office Version: 16.0.18025.20140 Modules
| |||||||||||||||
| 6760 | OfficeClickToRun.exe platform=x64 culture=en-us productstoadd=O365ProPlusRetail.16_en-us_x-none cdnbaseurl=http://officecdn.microsoft.com/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60 baseurl=http://officecdn.microsoft.com/sg/492350f6-3a01-4f97-b9c0-c7c6ddf67d60 version=16.0.18025.20140 mediatype=CDN sourcetype=CDN O365ProPlusRetail.excludedapps=groove updatesenabled=False bitnessmigration=False deliverymechanism=492350f6-3a01-4f97-b9c0-c7c6ddf67d60 flt.useoutlookshareaddon=unknown flt.useofficehelperaddon=unknown flt.UseTeamsOnInstallConsumer=unknown flt.UseTeamsOnUpdateConsumer=unknown uninstallcentennial=True scenario=CLIENTUPDATE | C:\Program Files\Common Files\microsoft shared\ClickToRun\OfficeClickToRun.exe | OfficeSetup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Office Click-to-Run (SxS) Exit code: 0 Version: 16.0.16026.20140 Modules
| |||||||||||||||
| 6856 | OfficeSetup.exe RELAUNCHED | C:\Users\admin\AppData\Local\Temp\OfficeSetup.exe | OfficeSetup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft 365 and Office Version: 16.0.18025.20140 Modules
| |||||||||||||||
| 7244 | C:\WINDOWS\system32\DllHost.exe /Processid:{338B40F9-9D68-4B53-A793-6B9AA0C5F63B} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7924 | "C:\Program Files\Common Files\Microsoft Shared\ClickToRun\OfficeClickToRun.exe" /service | C:\Program Files\Common Files\microsoft shared\ClickToRun\OfficeClickToRun.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Office Click-to-Run (SxS) Version: 16.0.18025.20140 Modules
| |||||||||||||||
| 8108 | OfficeClickToRun.exe platform=x64 culture=en-us productstoadd=O365ProPlusRetail.16_en-us_x-none cdnbaseurl.16=http://officecdn.microsoft.com/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60 baseurl.16=http://officecdn.microsoft.com/sg/492350f6-3a01-4f97-b9c0-c7c6ddf67d60 version.16=16.0.18025.20140 mediatype.16=CDN sourcetype.16=CDN O365ProPlusRetail.excludedapps.16=groove updatesenabled.16=False bitnessmigration=False deliverymechanism=492350f6-3a01-4f97-b9c0-c7c6ddf67d60 flt.useoutlookshareaddon=unknown flt.useofficehelperaddon=unknown flt.UseTeamsOnInstallConsumer=unknown flt.UseTeamsOnUpdateConsumer=unknown uninstallcentennial=True | C:\Program Files\Common Files\microsoft shared\ClickToRun\OfficeClickToRun.exe | OfficeSetup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Office Click-to-Run (SxS) Version: 16.0.18025.20140 Modules
| |||||||||||||||
Total events
15 366
Read events
14 997
Write events
164
Delete events
205
Modification events
| (PID) Process: | (6856) OfficeSetup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (6856) OfficeSetup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (6856) OfficeSetup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (6856) OfficeSetup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (6856) OfficeSetup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
| (PID) Process: | (6856) OfficeSetup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 2 | |||
| (PID) Process: | (6856) OfficeSetup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 2 | |||
| (PID) Process: | (6856) OfficeSetup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | pt-br |
Value: 2 | |||
| (PID) Process: | (6856) OfficeSetup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ru-ru |
Value: 2 | |||
| (PID) Process: | (6856) OfficeSetup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | tr-tr |
Value: 2 | |||
Executable files
391
Suspicious files
18
Text files
166
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4432 | OfficeSetup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\A583E2A51BFBDC1E492A57B7C8325850 | binary | |
MD5:C7D1234376F3389D6C220F0DCF24341B | SHA256:F67F7E62B47D1C4D9059F9F01FF40D52044EE81F594C5B8C8925C254381061E5 | |||
| 4432 | OfficeSetup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\36AC0BE60E1243344AE145F746D881FE | binary | |
MD5:DDF4DE0DC1AC39C22F605957A1FE614B | SHA256:0ACF9791F2CBBF8330653DF8D90E760108DD7ED3B5DB03C4DE164BD5047E4D4A | |||
| 4432 | OfficeSetup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\0B8A20E1F3F4D73D52A19929F922C892 | binary | |
MD5:A7DC536583F3E01019D2054B33B4147F | SHA256:7C1E09E1CCD9A7E18969D47C7934E9D99FC7CB3E365EEF9E92F47FB0C522764B | |||
| 4432 | OfficeSetup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\0B8A20E1F3F4D73D52A19929F922C892 | binary | |
MD5:7B2D889AFA8558D921D5D96BBFFFF361 | SHA256:05023211964BF3AB5D2FA17D05E0B0EA36978DE2D1B6CC194DDF32437D40871C | |||
| 6856 | OfficeSetup.exe | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\F0032011-C65C-4BAB-AC93-230927974AE0 | xml | |
MD5:1C8E0BB5D82F71FC2A63792F10DD9C6D | SHA256:74913A14CDCAB436A9B505D578534AECD99F8B230A4743E5913C69A6C40934C4 | |||
| 6760 | OfficeClickToRun.exe | C:\Users\admin\AppData\Local\Temp\DESKTOP-JGLLJLD-20241013-0806a.log | text | |
MD5:417C8F0BE520DF140E541687C3879206 | SHA256:DA7106F2F655746EA0F35B77970F138B774793AFAD435DCF084C9776BD6E96A3 | |||
| 6760 | OfficeClickToRun.exe | C:\Program Files\Common Files\microsoft shared\ClickToRun\Updates\80EA3AE2-2610-473E-B165-22ECFE4D6AF4OfficeC2R736A50F6-52F5-49CA-8CDE-FC2626D859B9\api-ms-win-core-localization-l1-2-0.dll | executable | |
MD5:6B4F2CA3EFCEB2C21E93F92CDC150A9D | SHA256:B39A515B9E48FC6589703D45E14DCEA2273A02D7FA6F2E1D17985C0228D32564 | |||
| 4432 | OfficeSetup.exe | C:\Users\admin\AppData\Local\Temp\OfficeC2RB17E686D-7FD3-4DD7-BDC4-4B2E530C1587\v64.hash | text | |
MD5:762C96DF71D27FD2E998024C63D8412E | SHA256:355C109A417DF1E2200116679BC0AD5FEBCF13D4E61AFEF4959A7CB4CEC97938 | |||
| 4432 | OfficeSetup.exe | C:\Users\admin\AppData\Local\Temp\OfficeC2RB17E686D-7FD3-4DD7-BDC4-4B2E530C1587\VersionDescriptor.xml | xml | |
MD5:E23E9443A6B4288F6E5D0471991A1648 | SHA256:F2AC92A008D7BDA16E55A23D857FF6B8D9F3105AB5D554C657B7F95406A4DB45 | |||
| 6760 | OfficeClickToRun.exe | C:\Users\admin\AppData\Local\Temp\DESKTOP-JGLLJLD-20241013-0806.log | text | |
MD5:D6228FACD41AD97E3264E3F21F2A6A38 | SHA256:8B1FD7B9D0A0E20869D8A402F628B3A0FB1736046C3B2D0AA9D2A8DEDA9C8ADF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
58
TCP/UDP connections
65
DNS requests
33
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2076 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4128 | svchost.exe | HEAD | 200 | 23.48.23.35:80 | http://f.c2r.ts.cdn.office.net/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60/Office/Data/v64_16.0.18025.20140.cab | unknown | — | — | whitelisted |
4128 | svchost.exe | HEAD | 200 | 23.48.23.35:80 | http://f.c2r.ts.cdn.office.net/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60/Office/Data/v64_16.0.18025.20140.cab | unknown | — | — | whitelisted |
4128 | svchost.exe | GET | 200 | 23.48.23.35:80 | http://f.c2r.ts.cdn.office.net/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60/Office/Data/v64_16.0.18025.20140.cab | unknown | — | — | whitelisted |
4128 | svchost.exe | GET | 206 | 23.48.23.35:80 | http://f.c2r.ts.cdn.office.net/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60/Office/Data/v64_16.0.18025.20140.cab | unknown | — | — | whitelisted |
4432 | OfficeSetup.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
4432 | OfficeSetup.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Time-Stamp%20PCA%202010(1).crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6944 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5488 | MoUsoCoreWorker.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5488 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4020 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6856 | OfficeSetup.exe | 52.109.28.46:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
mrodevicemgr.officeapps.live.com |
| whitelisted |
f.c2r.ts.cdn.office.net |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |