| File name: | C4PROLoader.exe |
| Full analysis: | https://app.any.run/tasks/83d743be-8996-4181-b86e-0eb54f92df80 |
| Verdict: | Malicious activity |
| Analysis date: | March 10, 2024, 17:29:06 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 84533D18EB7E5AEA1DD0E022ACF81D8C |
| SHA1: | AC7EE8356BD60353D5A6C5DE9B540695216DEA55 |
| SHA256: | 0124803B8FA8822D637B2E0F233673C6CEBAEC63BCB980CCD6C2F842B25E10C6 |
| SSDEEP: | 98304:bDs7D8ruvCT8Or+sdQuhuHZVk0aucCARgKScGX4z/gW1vRwtlXoWMbGVBUM00Dhi:bk5U65SQ4/KxT7syKGzlOySh |
MALICIOUS
Drops the executable file immediately after the start
- C4PROLoader.exe (PID: 3864)
- fodhelper.exe (PID: 1740)
- C4PROLoader.exe (PID: 2908)
- C4PROLoader.exe (PID: 1040)
RACCOONCLIPPER has been detected (YARA)
- fodhelper.exe (PID: 3948)
SUSPICIOUS
Reads security settings of Internet Explorer
- C4PROLoader.exe (PID: 3864)
- C4PROLoader.exe (PID: 1040)
- C4PROLoader.exe (PID: 2908)
Starts CMD.EXE for commands execution
- C4PROLoader.exe (PID: 3864)
Reads the Internet Settings
- C4PROLoader.exe (PID: 3864)
- C4PROLoader.exe (PID: 1040)
- powershell.exe (PID: 3936)
- C4PROLoader.exe (PID: 2908)
- powershell.exe (PID: 3180)
- C4.exe (PID: 3164)
The executable file from the user directory is run by the CMD process
- C4PROLoader.exe (PID: 1040)
Base64-obfuscated command line is found
- C4PROLoader.exe (PID: 1040)
- C4PROLoader.exe (PID: 2908)
Starts POWERSHELL.EXE for commands execution
- C4PROLoader.exe (PID: 1040)
- C4PROLoader.exe (PID: 2908)
BASE64 encoded PowerShell command has been detected
- C4PROLoader.exe (PID: 1040)
- C4PROLoader.exe (PID: 2908)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 3936)
- powershell.exe (PID: 3180)
Executable content was dropped or overwritten
- C4PROLoader.exe (PID: 1040)
- C4PROLoader.exe (PID: 2908)
- fodhelper.exe (PID: 1740)
Application launched itself
- C4PROLoader.exe (PID: 1040)
The process executes via Task Scheduler
- fodhelper.exe (PID: 3948)
INFO
Reads the machine GUID from the registry
- C4PROLoader.exe (PID: 3864)
- C4PROLoader.exe (PID: 1040)
- C4.exe (PID: 3164)
Reads the computer name
- C4PROLoader.exe (PID: 3864)
- C4PROLoader.exe (PID: 1040)
- C4PROLoader.exe (PID: 2908)
- C4.exe (PID: 3164)
Checks supported languages
- C4PROLoader.exe (PID: 3864)
- C4PROLoader.exe (PID: 1040)
- C4PROLoader.exe (PID: 2908)
- C4.exe (PID: 3164)
- fodhelper.exe (PID: 1740)
- fodhelper.exe (PID: 3948)
Create files in a temporary directory
- C4PROLoader.exe (PID: 1040)
- C4PROLoader.exe (PID: 2908)
Creates files or folders in the user directory
- fodhelper.exe (PID: 1740)
Application launched itself
- msedge.exe (PID: 1236)
- msedge.exe (PID: 3980)
Manual execution by a user
- msedge.exe (PID: 3980)
Drops the executable file immediately after the start
- msedge.exe (PID: 3980)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
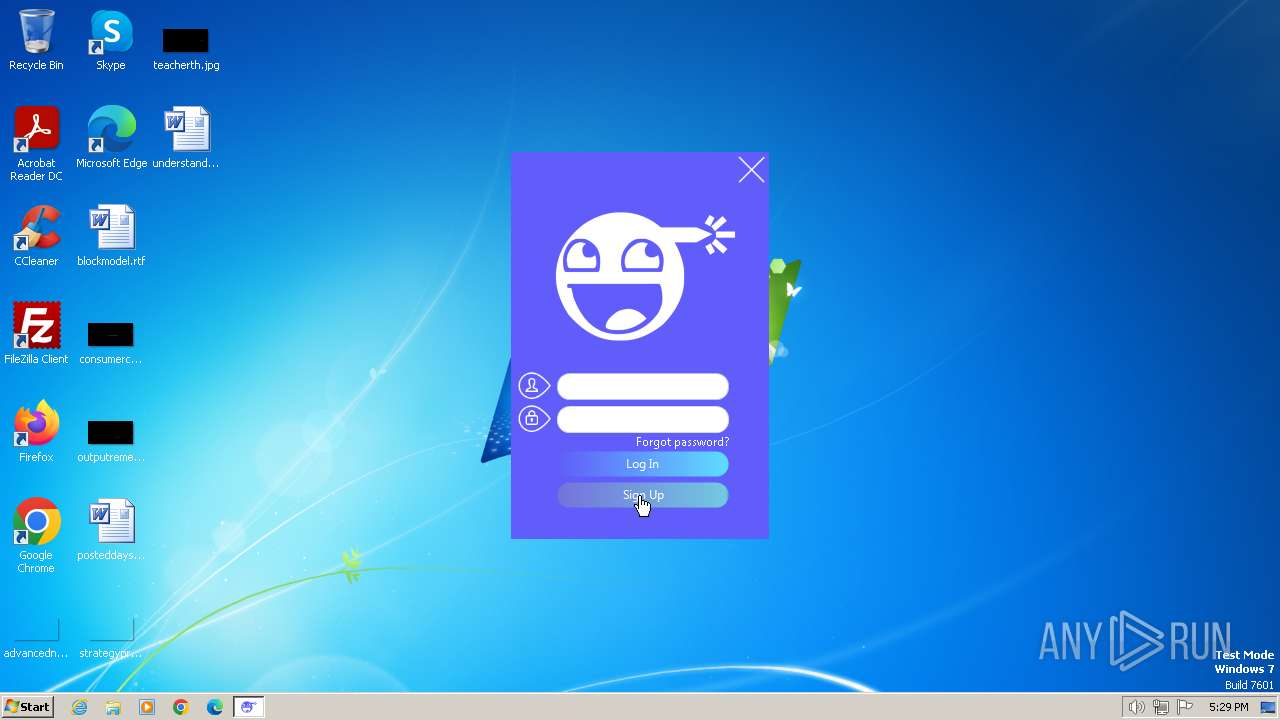
RaccoonClipper
(PID) Process(3948) fodhelper.exe
Wallets (18)ltc1qvfghx46z8v9fyawar6qgdhj5wtrslvvx2kn438
cosmos1k6y3w45ralwcaarlgt7zcgm5htk2rw9jq5jxce
addr1q90kzt7nhxjkhm5e40nadh5ym57p24aswumdy0aggyk8mmjlvyha8wd9d0hfn2l86m0gfhfuz4tmqaek6gl6ssfv0hhqe6akq0
LKTWnwuM4eZgXdUNh5RpV3ETxNRbbbPDFT
t1Upr9Q3VMFLC8sz6spautGumgDqdSvdgsq
bc1qnl5vwuzw57rtm98wg2jh6mu0p597892q0pss27
0xB78aD0c44964c978c763cCa142C8D3f30B711e3c
Ae2tdPwUPEZKFp3DNd7g57oc3vWeZ6N2fA1uA5KqJ9qyQTyC2D2YEaGEYzL
BXgs2AAWD7gF2WUNhva7byzkpR4QbvM3YHoCJzrGebnb
TXQXx2nJnd1PpUVkZvfh7LbffUisurwd43
YWAMDRGWA6TMDAVJV5XP6CQZZMO46NLC4TK555FRDCTPLUMST5YENA4VIE
Adu5K93Evg5jsQGdwMA69onB4dJ74L87GX
1BspfXbHj1R5RcShF31KNpBW79h9zBej5J
49XPrw6TrHAVvw2pPGhdifGdfYc3iHftvSwQvmy74drQMpU4bmE3syc6mV9uSKDhbQB54Egan4AL1NMzAvYRY3jHHZdYUcm
DB84kZEkPqBUVh1KvEcN7f3KSEEhPVMNPS
bnb1gjp5822en66dsh7k0v00q0hxzwuus3c0m2v74w
88ULP41eYUCWzYVGPXuBUEJR9j8Lu17zPKvkLqyXQMt3BjKZijVqiq6786u3bveEHnemGXR78uGj28ELXmDTURC2PJYRuTH
Z1BspfXbHj1R5RcShF31KNpBW79h9zBej5J
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (56.7) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (21.3) |
| .scr | | | Windows screen saver (10.1) |
| .dll | | | Win32 Dynamic Link Library (generic) (5) |
| .exe | | | Win32 Executable (generic) (3.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:03:10 17:08:35+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 8 |
| CodeSize: | 13948928 |
| InitializedDataSize: | 2048 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xd4f6fe |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | - |
| FileVersion: | 1.0.0.0 |
| InternalName: | Xgvltszua.exe |
| LegalCopyright: | - |
| LegalTrademarks: | - |
| OriginalFileName: | Xgvltszua.exe |
| ProductName: | - |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
81
Monitored processes
39
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 764 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1456 --field-trial-handle=1252,i,12365423113159659216,10431407775292495242,131072 /prefetch:3 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1020 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2316 --field-trial-handle=1252,i,12365423113159659216,10431407775292495242,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1036 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --first-renderer-process --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=2312 --field-trial-handle=1252,i,12365423113159659216,10431407775292495242,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1040 | "C:\Users\admin\AppData\Local\Temp\C4PROLoader.exe" | C:\Users\admin\AppData\Local\Temp\C4PROLoader.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
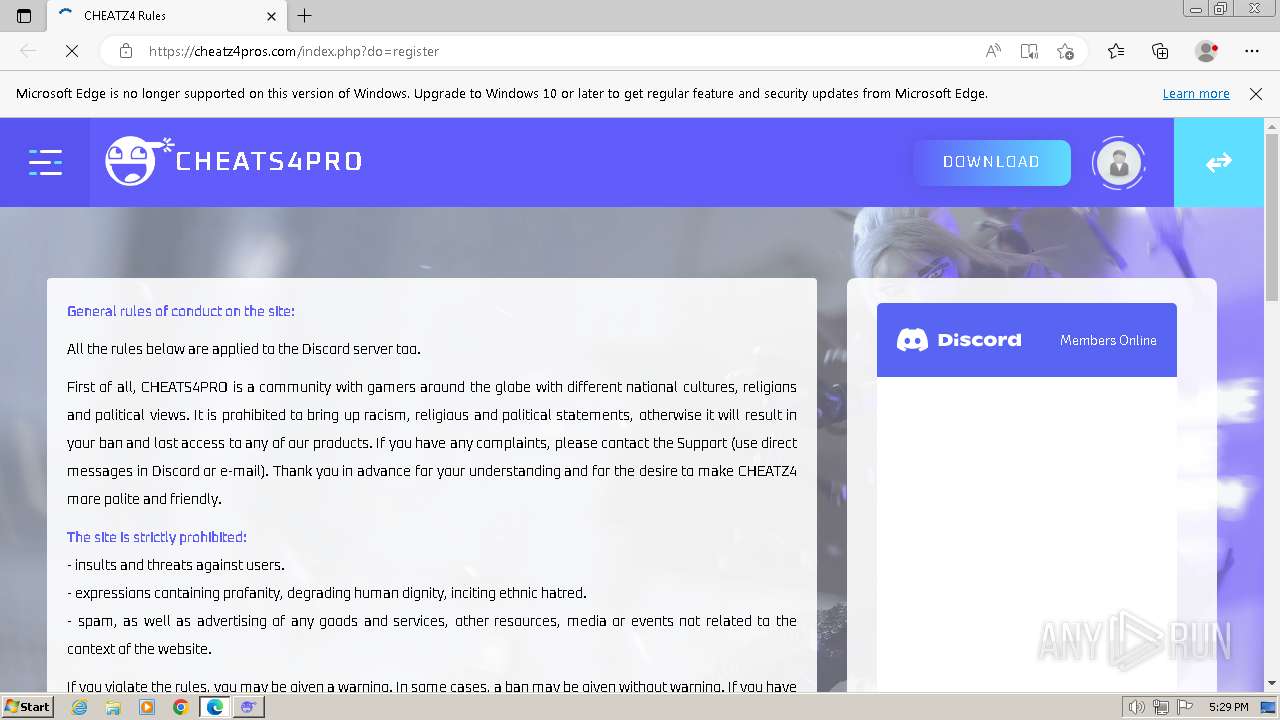
| 1236 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --single-argument https://cheatz4pros.com/index.php?do=register | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | C4.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1584 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1220 --field-trial-handle=1252,i,12365423113159659216,10431407775292495242,131072 /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1740 | "C:\Users\admin\AppData\Local\Temp\fodhelper.exe" | C:\Users\admin\AppData\Local\Temp\fodhelper.exe | C4PROLoader.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 4294967295 Modules
| |||||||||||||||
| 1816 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1516 --field-trial-handle=1340,i,17318050431573841471,17232529100045922616,131072 /prefetch:3 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1876 | "C:\Windows\System32\cmd.exe" /k START "" "C:\Users\admin\AppData\Local\Temp\C4PROLoader.exe" & EXIT | C:\Windows\System32\cmd.exe | C4PROLoader.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2032 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=3644 --field-trial-handle=1252,i,12365423113159659216,10431407775292495242,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
Total events
18 615
Read events
18 503
Write events
105
Delete events
7
Modification events
| (PID) Process: | (3864) C4PROLoader.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3864) C4PROLoader.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3864) C4PROLoader.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3864) C4PROLoader.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1040) C4PROLoader.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1040) C4PROLoader.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1040) C4PROLoader.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1040) C4PROLoader.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3936) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3936) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
7
Suspicious files
35
Text files
120
Unknown types
61
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2384 | msedge.exe | — | ||
MD5:— | SHA256:— | |||
| 3936 | powershell.exe | C:\Users\admin\AppData\Local\Temp\sahweijw.qf1.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 3980 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF1867cd.TMP | — | |
MD5:— | SHA256:— | |||
| 3936 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | dbf | |
MD5:446DD1CF97EABA21CF14D03AEBC79F27 | SHA256:A7DE5177C68A64BD48B36D49E2853799F4EBCFA8E4761F7CC472F333DC5F65CF | |||
| 3980 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1040 | C4PROLoader.exe | C:\Users\admin\AppData\Local\Temp\Ysccvlvjyy.exe | executable | |
MD5:2AA71925B72F427E18B0FA4D98E6DC9D | SHA256:C66DC9A14322ACD345544E98D9907E13A5F20783C66BA563B90D9D8D18D04C1A | |||
| 2908 | C4PROLoader.exe | C:\Users\admin\AppData\Local\Temp\C4.exe | executable | |
MD5:EEBAD7F8F7AD92BE4A9A12C46743D77B | SHA256:BCC5744B7F7265CB597420187C5448484BA5839AD9BB6E28C435CF452EF4470B | |||
| 3936 | powershell.exe | C:\Users\admin\AppData\Local\Temp\lp3s1ujn.3tv.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 3180 | powershell.exe | C:\Users\admin\AppData\Local\Temp\baj5whd0.gxf.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 3180 | powershell.exe | C:\Users\admin\AppData\Local\Temp\tj3pffkh.ekk.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
46
DNS requests
40
Threats
12
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | unknown |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
764 | msedge.exe | 13.107.21.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
3980 | msedge.exe | 239.255.255.250:1900 | — | — | — | unknown |
764 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
764 | msedge.exe | 188.114.97.3:443 | cheatz4pros.com | CLOUDFLARENET | NL | unknown |
764 | msedge.exe | 162.159.137.232:443 | discord.com | — | — | unknown |
764 | msedge.exe | 142.250.186.136:443 | www.googletagmanager.com | GOOGLE | US | unknown |
764 | msedge.exe | 172.217.18.10:443 | fonts.googleapis.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.edge.skype.com |
| whitelisted |
cheatz4pros.com |
| unknown |
edge.microsoft.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
discord.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
www.bing.com |
| whitelisted |
arc.msn.com |
| whitelisted |
region1.google-analytics.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
764 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
764 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
764 | msedge.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
764 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
764 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
764 | msedge.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
764 | msedge.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
764 | msedge.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
764 | msedge.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
764 | msedge.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |