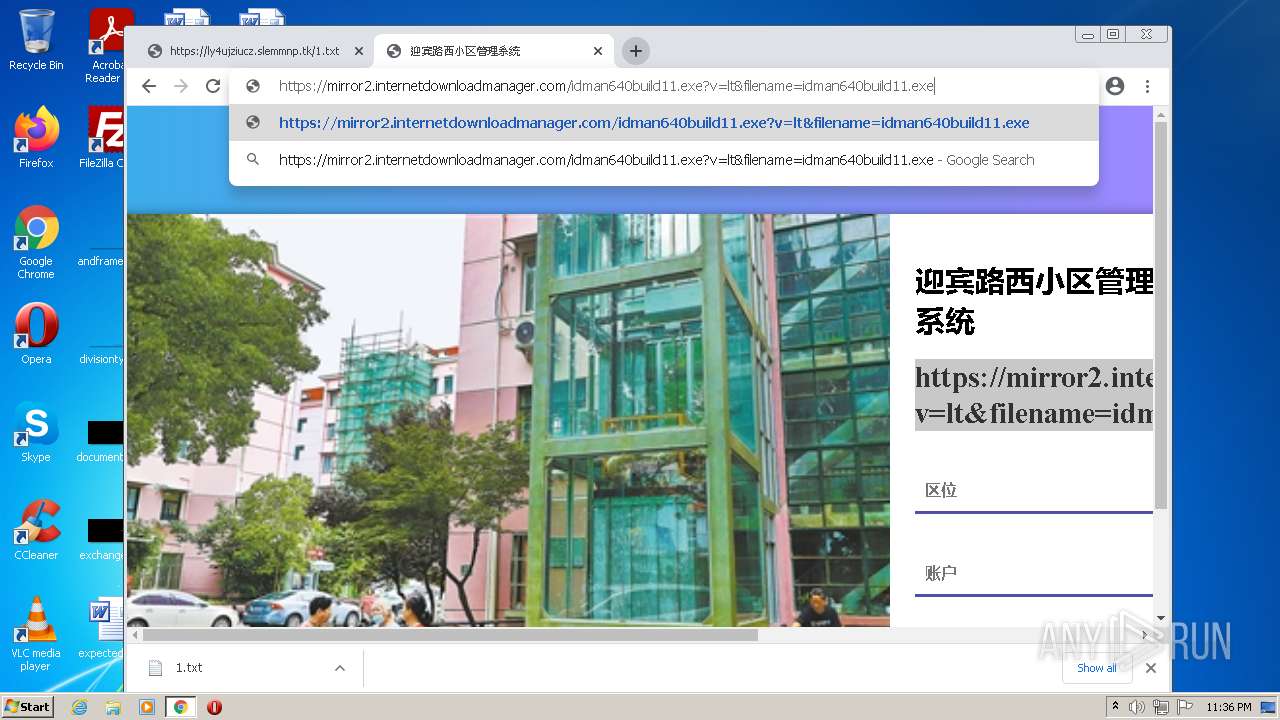
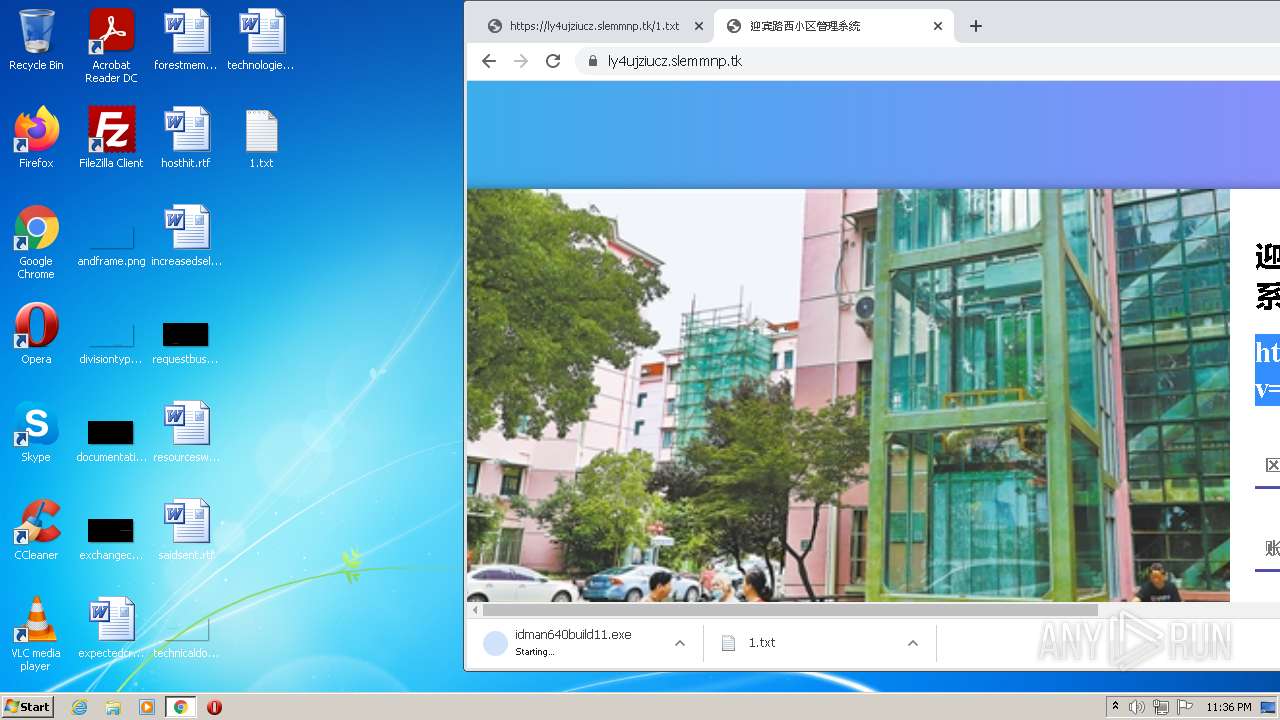
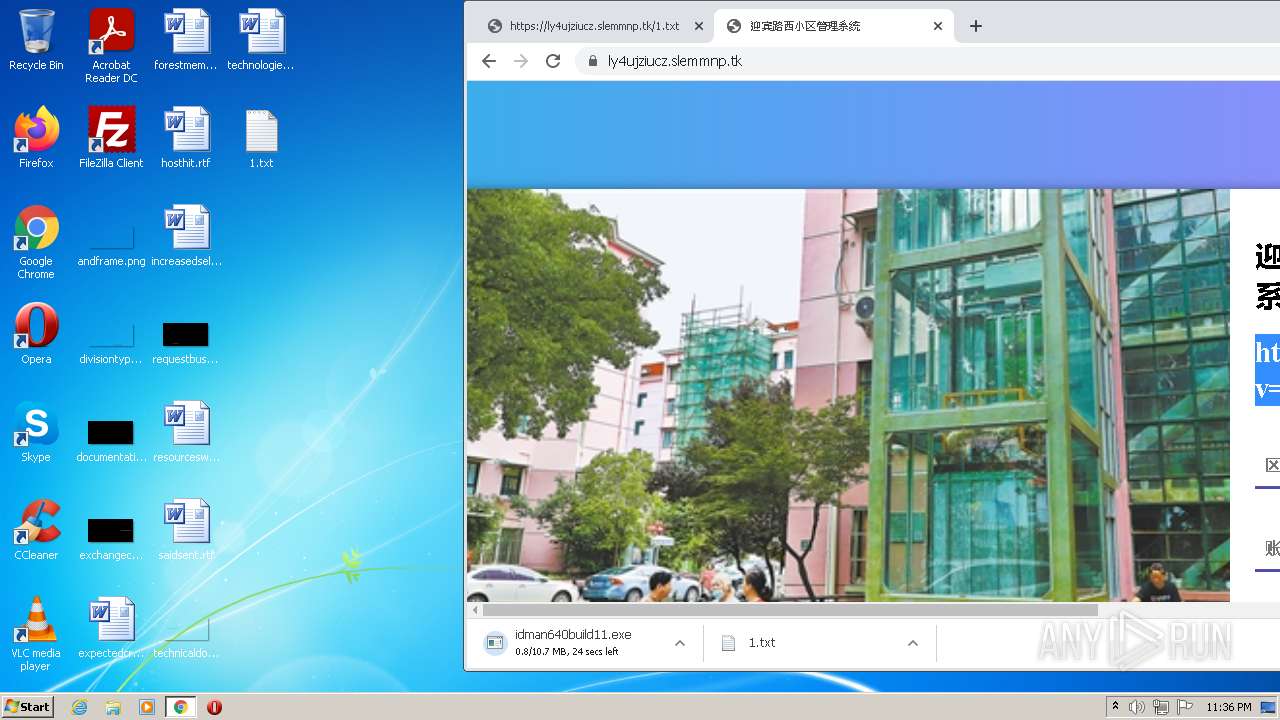
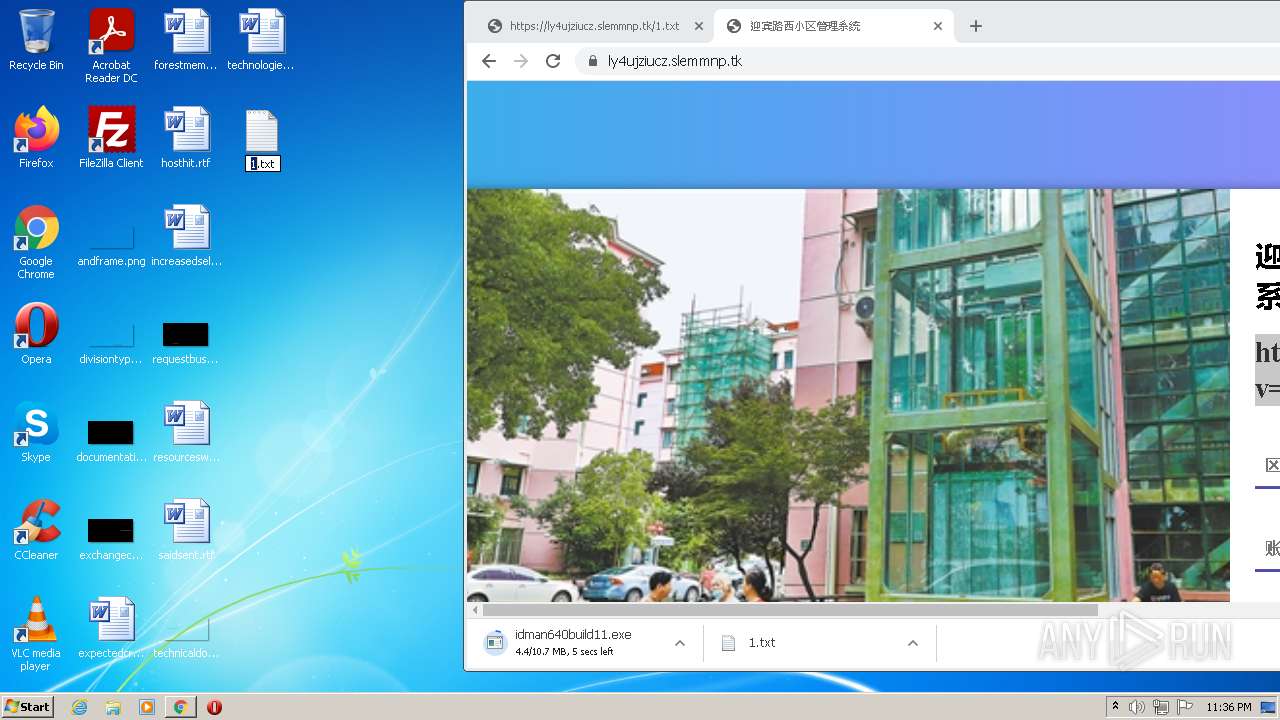
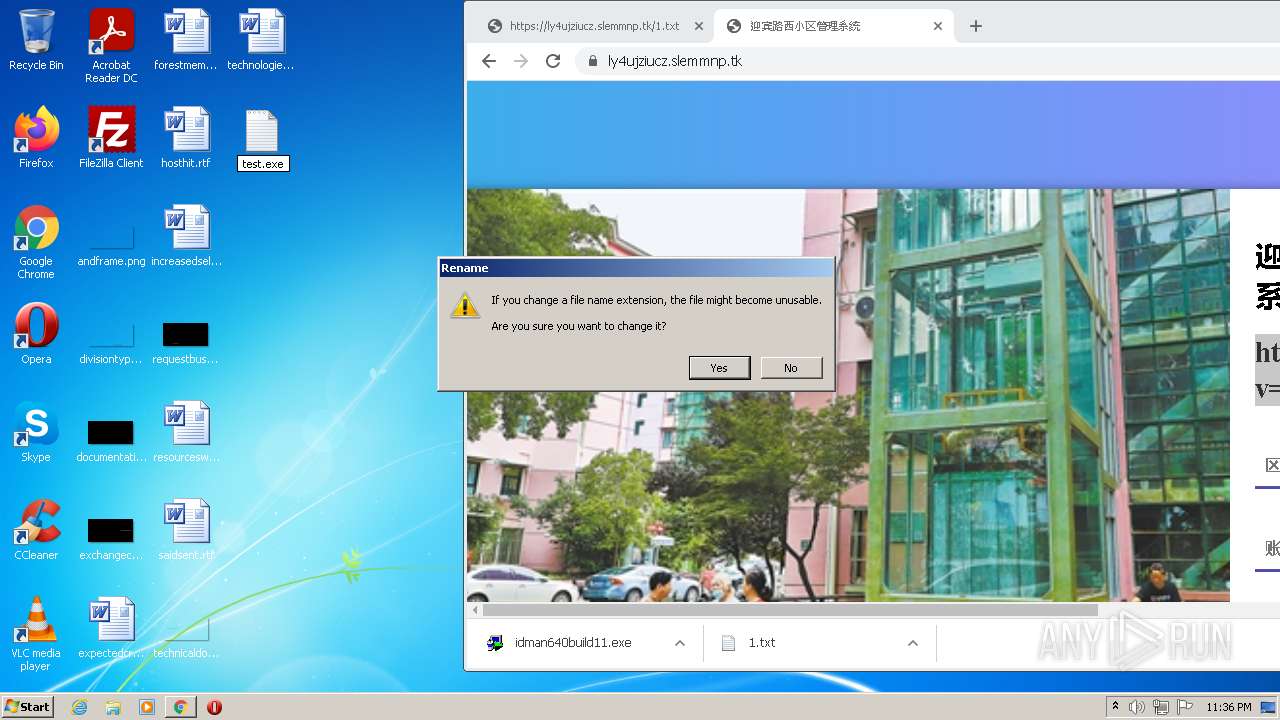
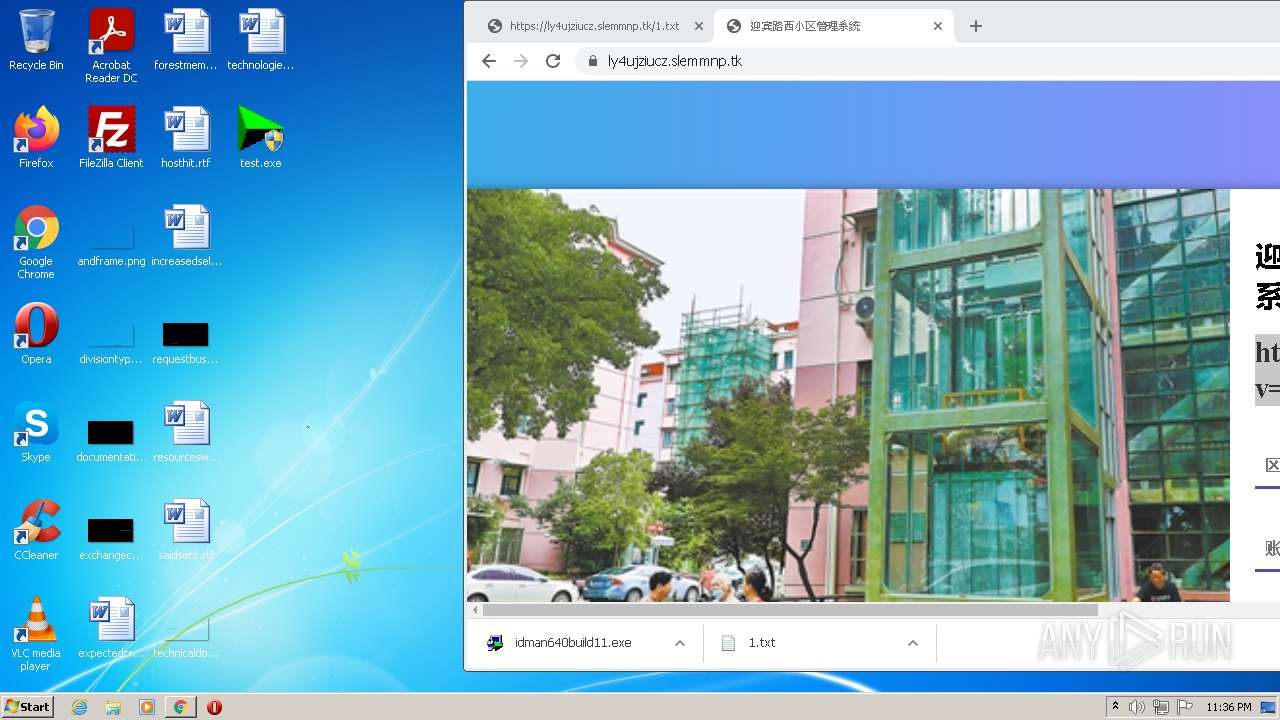
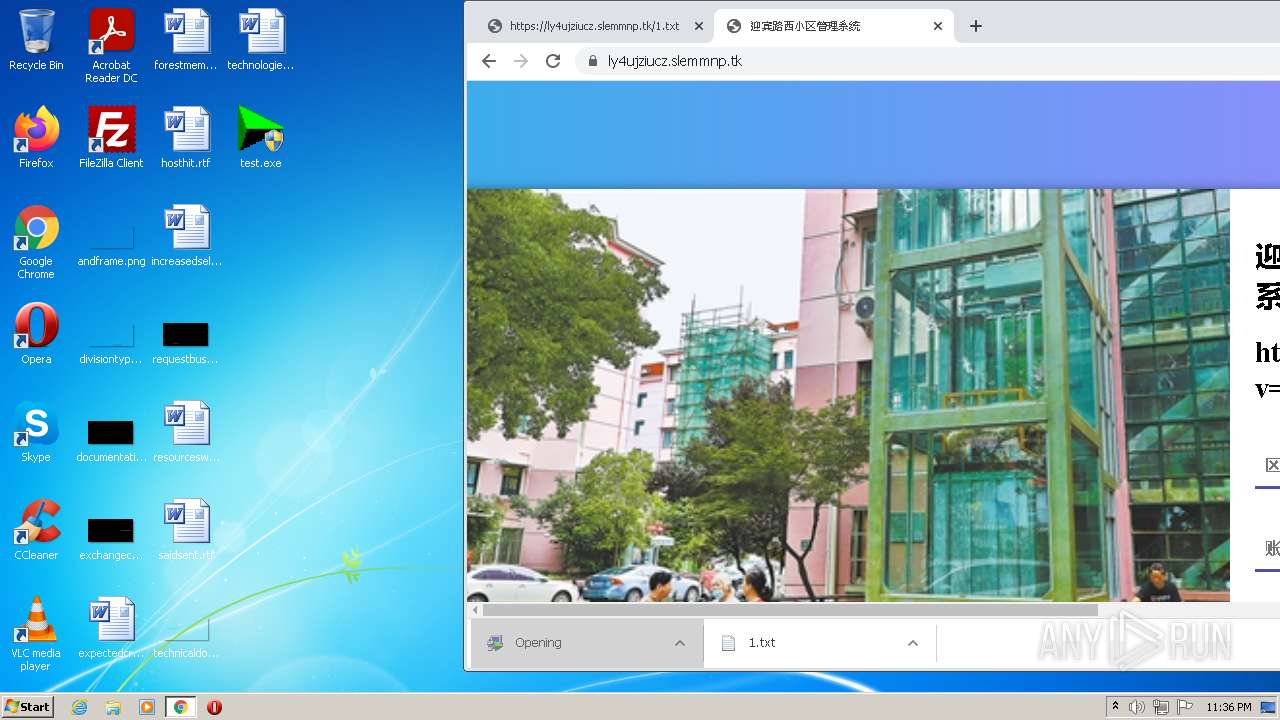
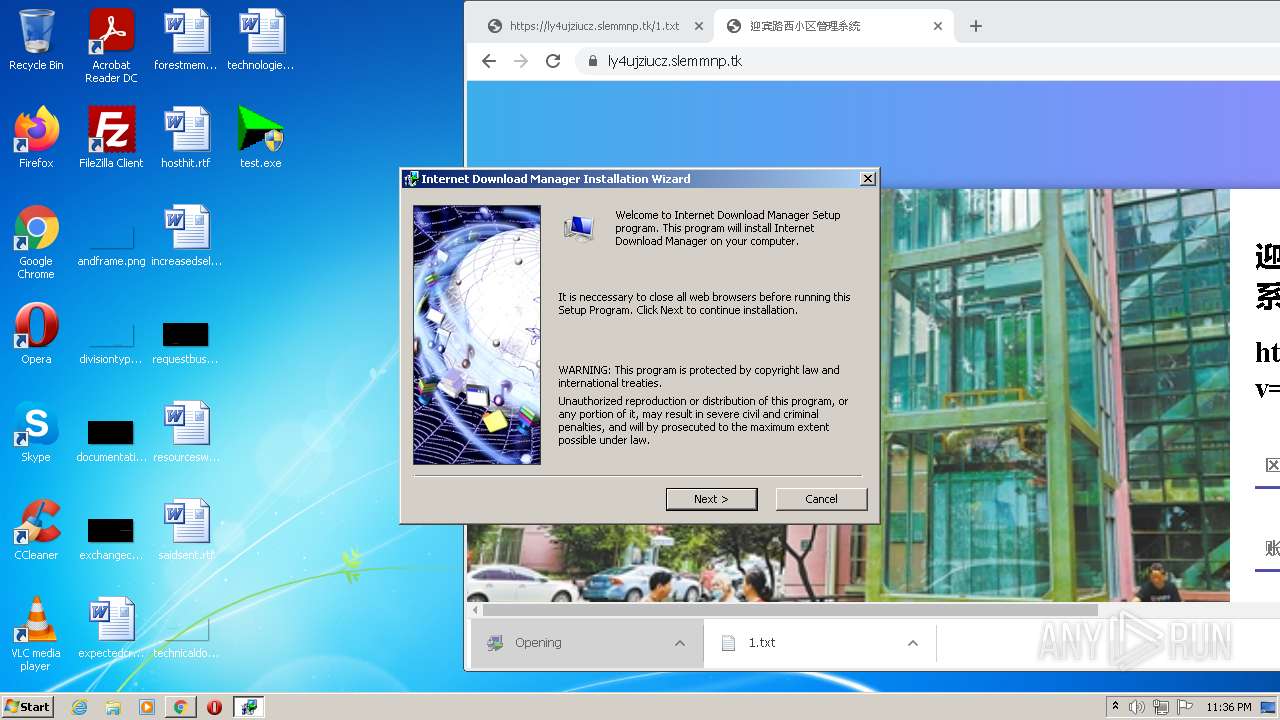
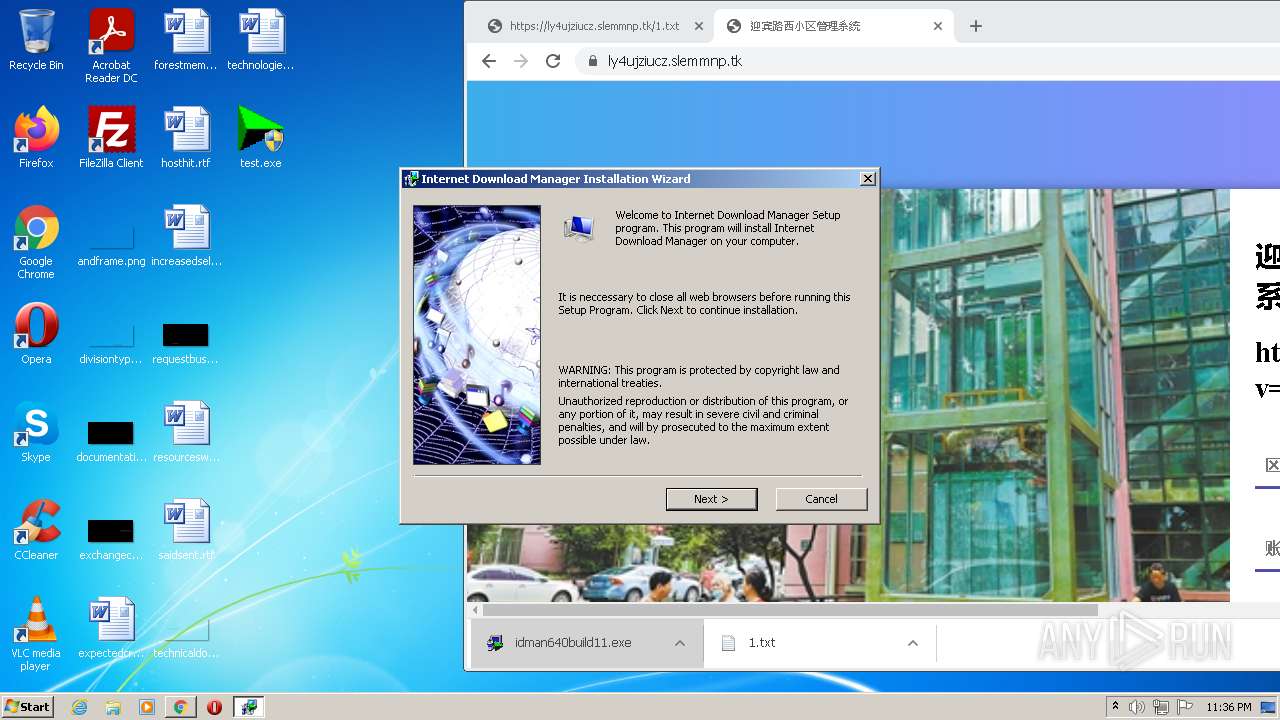
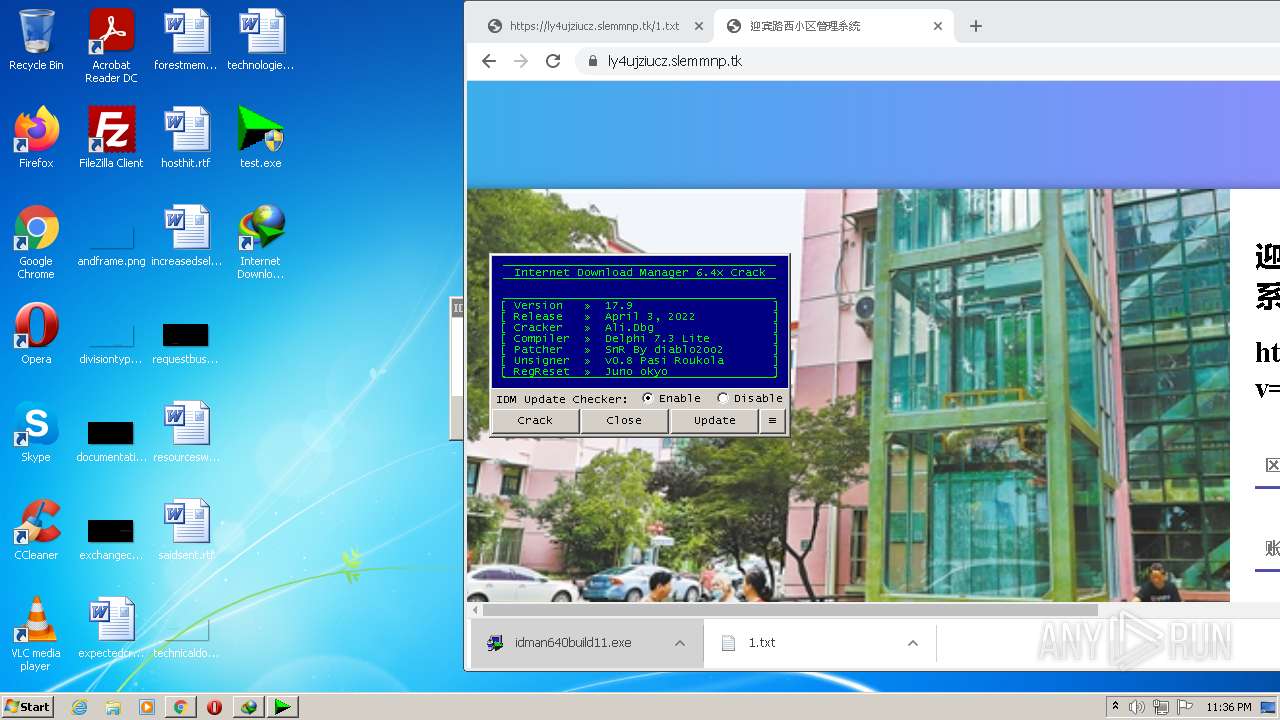
| URL: | https://ly4ujziucz.slemmnp.tk/1.txt |
| Full analysis: | https://app.any.run/tasks/033634f0-c87e-4306-8495-681342a2ac0e |
| Verdict: | Malicious activity |
| Analysis date: | May 20, 2022, 22:35:43 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 445E060BF0A549E76515C87B4C3AA59B |
| SHA1: | 34CF76FBF714AFD9E84D29E064ED4D84A512EDE3 |
| SHA256: | 011FE85A0C4FD44DB03F941DB85838CA48B06FD972D3F61ABCCA7B26576C5A1D |
| SSDEEP: | 3:N8cRtfLWniu:2cbjWnh |
MALICIOUS
Drops executable file immediately after starts
- chrome.exe (PID: 1272)
- chrome.exe (PID: 3212)
- wscript.exe (PID: 3588)
- test.exe (PID: 1304)
- UnSigner.exe (PID: 3112)
Application was dropped or rewritten from another process
- idman640build11.exe (PID: 3228)
- idman640build11.exe (PID: 2612)
- test.exe (PID: 2728)
- test.exe (PID: 1304)
- UnSigner.exe (PID: 3112)
- IDMan.exe (PID: 1964)
SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 1264)
Modifies files in Chrome extension folder
- chrome.exe (PID: 1272)
Executable content was dropped or overwritten
- chrome.exe (PID: 1272)
- chrome.exe (PID: 3212)
- test.exe (PID: 1304)
- wscript.exe (PID: 3588)
- UnSigner.exe (PID: 3112)
Drops a file with a compile date too recent
- chrome.exe (PID: 1272)
- chrome.exe (PID: 3212)
- test.exe (PID: 1304)
- wscript.exe (PID: 3588)
- UnSigner.exe (PID: 3112)
Checks supported languages
- idman640build11.exe (PID: 2612)
- IDM1.tmp (PID: 3640)
- idmBroker.exe (PID: 2364)
- IDMan.exe (PID: 1964)
- test.exe (PID: 1304)
- wscript.exe (PID: 3588)
- UnSigner.exe (PID: 3112)
Creates a directory in Program Files
- IDM1.tmp (PID: 3640)
Reads the computer name
- IDM1.tmp (PID: 3640)
- IDMan.exe (PID: 1964)
- wscript.exe (PID: 3588)
- test.exe (PID: 1304)
Creates a software uninstall entry
- IDM1.tmp (PID: 3640)
Creates files in the user directory
- IDM1.tmp (PID: 3640)
- IDMan.exe (PID: 1964)
Creates/Modifies COM task schedule object
- IDM1.tmp (PID: 3640)
- IDMan.exe (PID: 1964)
Starts application with an unusual extension
- idman640build11.exe (PID: 2612)
Searches for installed software
- test.exe (PID: 1304)
Creates files in the program directory
- wscript.exe (PID: 3588)
- IDM1.tmp (PID: 3640)
Executes scripts
- test.exe (PID: 1304)
Uses TASKKILL.EXE to kill process
- test.exe (PID: 1304)
Uses REG.EXE to modify Windows registry
- test.exe (PID: 1304)
INFO
Changes internet zones settings
- iexplore.exe (PID: 2944)
Reads the computer name
- iexplore.exe (PID: 1264)
- iexplore.exe (PID: 2944)
- chrome.exe (PID: 3212)
- chrome.exe (PID: 1272)
- chrome.exe (PID: 3320)
- chrome.exe (PID: 1036)
- chrome.exe (PID: 3860)
- chrome.exe (PID: 3972)
- chrome.exe (PID: 2584)
- chrome.exe (PID: 3332)
- chrome.exe (PID: 3204)
- chrome.exe (PID: 1132)
- taskkill.exe (PID: 3992)
Application launched itself
- iexplore.exe (PID: 2944)
- chrome.exe (PID: 1272)
Manual execution by user
- chrome.exe (PID: 1272)
- test.exe (PID: 2728)
- test.exe (PID: 1304)
Checks supported languages
- iexplore.exe (PID: 2944)
- iexplore.exe (PID: 1264)
- chrome.exe (PID: 1272)
- chrome.exe (PID: 2252)
- chrome.exe (PID: 3320)
- chrome.exe (PID: 3212)
- chrome.exe (PID: 3140)
- chrome.exe (PID: 3776)
- chrome.exe (PID: 1840)
- chrome.exe (PID: 3500)
- chrome.exe (PID: 1036)
- chrome.exe (PID: 3728)
- chrome.exe (PID: 1988)
- chrome.exe (PID: 2756)
- chrome.exe (PID: 3752)
- chrome.exe (PID: 352)
- chrome.exe (PID: 3528)
- chrome.exe (PID: 3972)
- chrome.exe (PID: 3860)
- chrome.exe (PID: 3204)
- chrome.exe (PID: 304)
- chrome.exe (PID: 3152)
- chrome.exe (PID: 968)
- chrome.exe (PID: 3332)
- chrome.exe (PID: 2584)
- chrome.exe (PID: 3860)
- chrome.exe (PID: 3860)
- chrome.exe (PID: 480)
- chrome.exe (PID: 3564)
- chrome.exe (PID: 1124)
- chrome.exe (PID: 1132)
- taskkill.exe (PID: 3992)
- reg.exe (PID: 3928)
Reads the date of Windows installation
- iexplore.exe (PID: 2944)
- chrome.exe (PID: 1132)
Reads the hosts file
- chrome.exe (PID: 1272)
- chrome.exe (PID: 3212)
Reads settings of System Certificates
- chrome.exe (PID: 3212)
- chrome.exe (PID: 1272)
- IDMan.exe (PID: 1964)
Checks Windows Trust Settings
- chrome.exe (PID: 1272)
- IDMan.exe (PID: 1964)
- wscript.exe (PID: 3588)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
89
Monitored processes
42
Malicious processes
5
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 304 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilReadIcon --field-trial-handle=1032,12838671286459521698,5126343874368471945,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=icon_reader --mojo-platform-channel-handle=3944 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 352 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1032,12838671286459521698,5126343874368471945,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3460 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 480 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilReadIcon --field-trial-handle=1032,12838671286459521698,5126343874368471945,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=icon_reader --mojo-platform-channel-handle=3704 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 968 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilReadIcon --field-trial-handle=1032,12838671286459521698,5126343874368471945,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=icon_reader --mojo-platform-channel-handle=3736 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1036 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1032,12838671286459521698,5126343874368471945,131072 --enable-features=PasswordImport --gpu-preferences=MAAAAAAAAADgAAAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --use-gl=swiftshader-webgl --mojo-platform-channel-handle=2980 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1124 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1032,12838671286459521698,5126343874368471945,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --extension-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=27 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=712 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1132 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1032,12838671286459521698,5126343874368471945,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3664 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1264 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2944 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1272 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | Explorer.EXE | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1304 | "C:\Users\admin\Desktop\test.exe" | C:\Users\admin\Desktop\test.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
29 841
Read events
28 982
Write events
784
Delete events
75
Modification events
| (PID) Process: | (2944) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (2944) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (2944) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30960793 | |||
| (PID) Process: | (2944) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 81023226 | |||
| (PID) Process: | (2944) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30960794 | |||
| (PID) Process: | (2944) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2944) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2944) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2944) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2944) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
9
Suspicious files
139
Text files
102
Unknown types
23
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1272 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-628817C9-4F8.pma | — | |
MD5:— | SHA256:— | |||
| 2944 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFC039EA9596CDCF3B.TMP | gmc | |
MD5:— | SHA256:— | |||
| 2944 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF1FF835E1FF2AF5AB.TMP | gmc | |
MD5:— | SHA256:— | |||
| 2944 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF6374EF7F38557DE9.TMP | gmc | |
MD5:— | SHA256:— | |||
| 2944 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\RecoveryStore.{3095B06D-D88D-11EC-BF60-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
| 2944 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Last Active\RecoveryStore.{42C873D0-1D90-11EB-BA2C-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
| 2944 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Last Active\{3095B070-D88D-11EC-BF60-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
| 2944 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{3095B06F-D88D-11EC-BF60-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
| 2944 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF8EBF876B4E5EE913.TMP | gmc | |
MD5:— | SHA256:— | |||
| 3212 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Cache\index | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
32
DNS requests
21
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3212 | chrome.exe | GET | 302 | 142.250.184.206:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvNzI0QUFXNV9zT2RvdUwyMERESEZGVmJnQQ/1.0.0.6_nmmhkkegccagdldgiimedpiccmgmieda.crx | US | html | 591 b | whitelisted |
3212 | chrome.exe | GET | 200 | 173.194.150.219:80 | http://r5---sn-5goeen7r.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvNzI0QUFXNV9zT2RvdUwyMERESEZGVmJnQQ/1.0.0.6_nmmhkkegccagdldgiimedpiccmgmieda.crx?cms_redirect=yes&mh=e_&mip=196.196.52.6&mm=28&mn=sn-5goeen7r&ms=nvh&mt=1653085939&mv=m&mvi=5&pl=24&rmhost=r6---sn-5goeen7r.gvt1.com&shardbypass=sd&smhost=r5---sn-5goeen7y.gvt1.com | US | crx | 242 Kb | whitelisted |
3212 | chrome.exe | GET | 200 | 23.216.77.80:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?d818397021ff8279 | US | compressed | 60.0 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1264 | iexplore.exe | 172.67.186.19:443 | ly4ujziucz.slemmnp.tk | — | US | malicious |
3212 | chrome.exe | 172.217.16.131:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
3212 | chrome.exe | 142.250.185.196:443 | www.google.com | Google Inc. | US | whitelisted |
3212 | chrome.exe | 142.250.185.174:443 | clients2.google.com | Google Inc. | US | whitelisted |
3212 | chrome.exe | 142.250.186.173:443 | accounts.google.com | Google Inc. | US | suspicious |
3212 | chrome.exe | 142.250.181.225:443 | clients2.googleusercontent.com | Google Inc. | US | whitelisted |
3212 | chrome.exe | 172.217.16.138:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
3212 | chrome.exe | 142.250.185.106:443 | content-autofill.googleapis.com | Google Inc. | US | whitelisted |
3212 | chrome.exe | 23.216.77.80:80 | ctldl.windowsupdate.com | NTT DOCOMO, INC. | US | suspicious |
3212 | chrome.exe | 142.250.184.227:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ly4ujziucz.slemmnp.tk |
| malicious |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
clients2.google.com |
| whitelisted |
www.google.com |
| malicious |
clients2.googleusercontent.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
a.nel.cloudflare.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET DNS Query to a .tk domain - Likely Hostile |
— | — | Potentially Bad Traffic | ET DNS Query to a .tk domain - Likely Hostile |