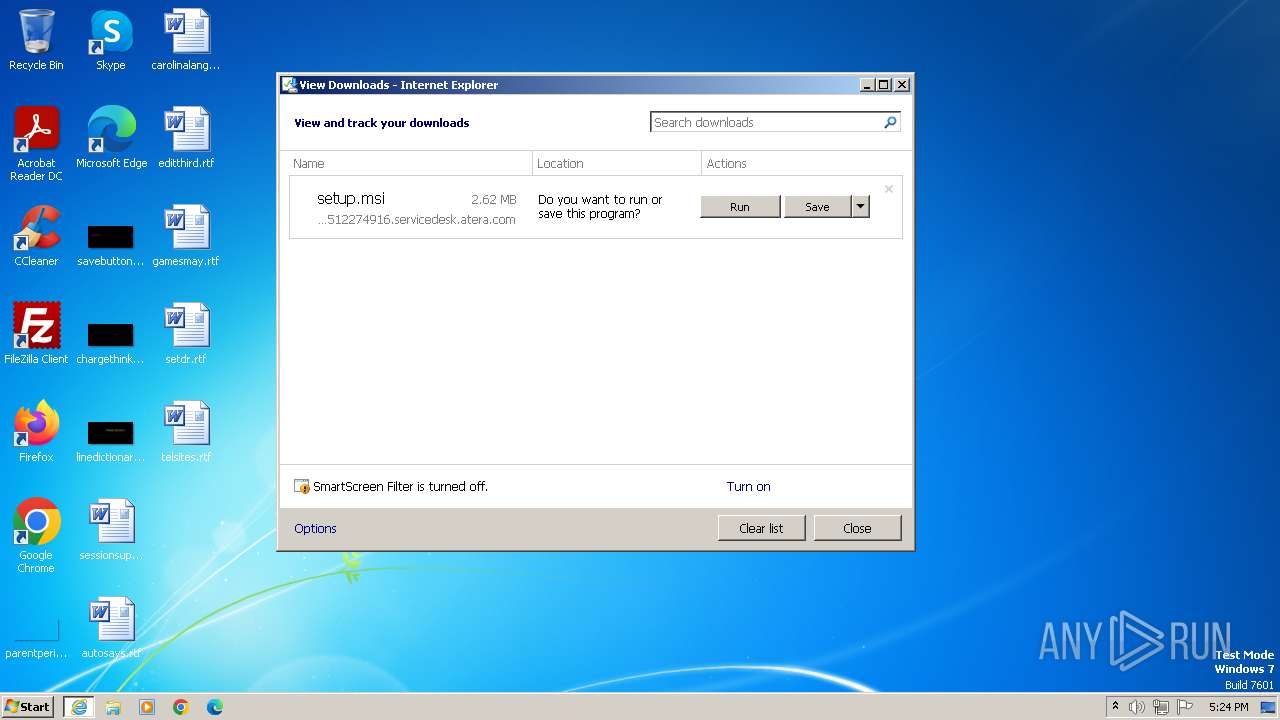
| URL: | https://HelpdeskSupport512274916.servicedesk.atera.com/GetAgent/Msi/?customerId=1&integratorLogin=hsinha%40fulcrumdigital.net&accountId=001Q3000001cyfLIAQ |
| Full analysis: | https://app.any.run/tasks/e73c0a88-6158-4ca4-9dac-f9e630da654b |
| Verdict: | Malicious activity |
| Analysis date: | October 19, 2023, 16:24:49 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| SHA1: | CAE3FCACE32C69D4AF17E155C0008B89EEFF5E16 |
| SHA256: | 011734BC9144F861035D7BFE41C205C04E84AFFB5B01D56DD30841C92BF3446C |
| SSDEEP: | 3:N8D46VVKmOXirAmJJUyG6lK1s9HACUl0RNp0GHM9e/a42VV3cD0n:2D3VgDij6yblKu9HALSH/HMA/QLn |
MALICIOUS
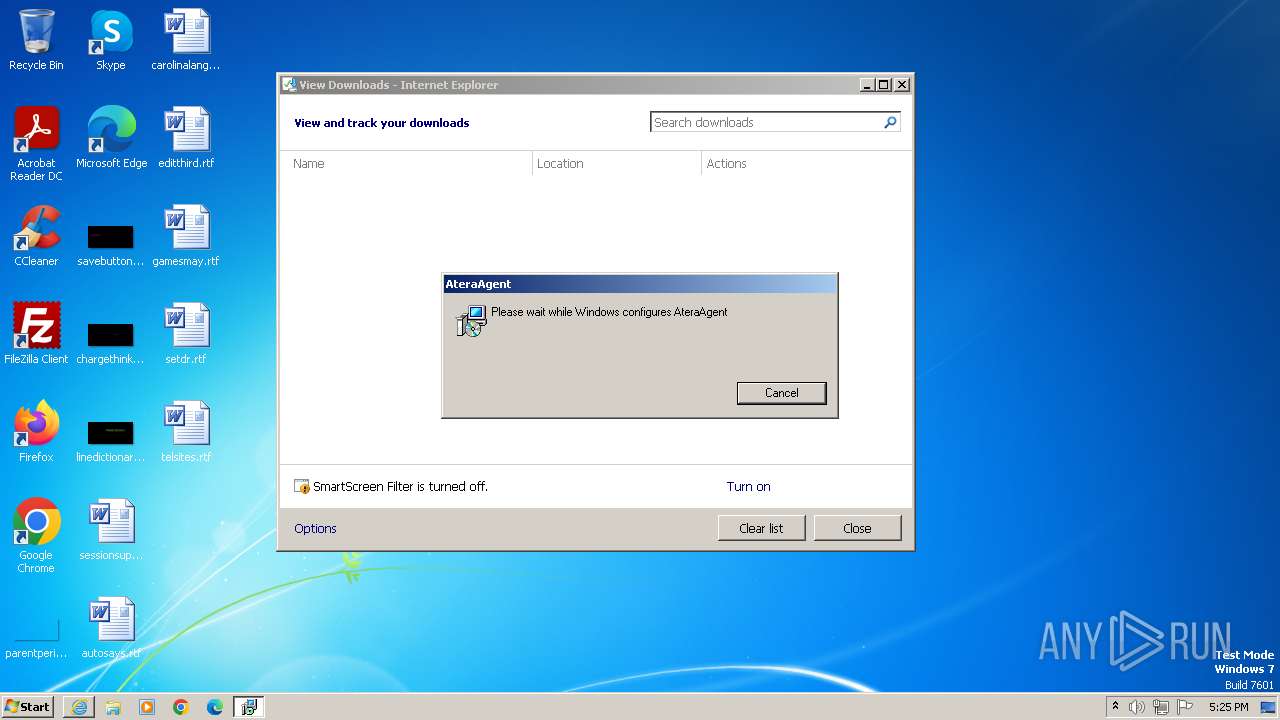
Drops the executable file immediately after the start
- msiexec.exe (PID: 3568)
- AteraAgent.exe (PID: 2812)
- AgentPackageTicketing.exe (PID: 1620)
Loads dropped or rewritten executable
- msiexec.exe (PID: 1764)
- rundll32.exe (PID: 3076)
- msiexec.exe (PID: 3084)
- AteraAgent.exe (PID: 2812)
- AteraAgent.exe (PID: 3672)
- AgentPackageADRemote.exe (PID: 3712)
- AgentPackageSTRemote.exe (PID: 3380)
Starts NET.EXE for service management
- msiexec.exe (PID: 3084)
- net.exe (PID: 3836)
Application was dropped or rewritten from another process
- AteraAgent.exe (PID: 3672)
- AgentPackageADRemote.exe (PID: 3712)
- AteraAgent.exe (PID: 2812)
- AgentPackageSTRemote.exe (PID: 3380)
- AgentPackageTicketing.exe (PID: 1620)
Creates a writable file the system directory
- AteraAgent.exe (PID: 3672)
- AteraAgent.exe (PID: 2812)
SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 3276)
- AteraAgent.exe (PID: 2812)
Checks Windows Trust Settings
- msiexec.exe (PID: 3568)
- AteraAgent.exe (PID: 3672)
Uses RUNDLL32.EXE to load library
- msiexec.exe (PID: 1764)
Process drops legitimate windows executable
- rundll32.exe (PID: 3076)
- msiexec.exe (PID: 3568)
- AteraAgent.exe (PID: 2812)
Uses TASKKILL.EXE to kill process
- msiexec.exe (PID: 3084)
Starts SC.EXE for service management
- AteraAgent.exe (PID: 2812)
The process creates files with name similar to system file names
- AteraAgent.exe (PID: 2812)
Starts CMD.EXE for commands execution
- AgentPackageAgentInformation.exe (PID: 3856)
The process executes VB scripts
- cmd.exe (PID: 2824)
Searches for installed software
- AgentPackageProgramManagement.exe (PID: 856)
- AgentPackageAgentInformation.exe (PID: 3856)
INFO
The process uses the downloaded file
- iexplore.exe (PID: 556)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 3540)
Application launched itself
- iexplore.exe (PID: 556)
- msiexec.exe (PID: 3568)
Checks supported languages
- msiexec.exe (PID: 3568)
- msiexec.exe (PID: 1764)
- msiexec.exe (PID: 3084)
- AteraAgent.exe (PID: 3672)
- AgentPackageADRemote.exe (PID: 3712)
- AgentPackageSTRemote.exe (PID: 3380)
- AteraAgent.exe (PID: 2812)
- AgentPackageTicketing.exe (PID: 1620)
- AgentPackageInternalPoller.exe (PID: 2604)
- AgentPackageProgramManagement.exe (PID: 856)
- AgentPackageAgentInformation.exe (PID: 3856)
Reads the computer name
- msiexec.exe (PID: 3568)
- msiexec.exe (PID: 1764)
- msiexec.exe (PID: 3084)
- AteraAgent.exe (PID: 3672)
- AgentPackageADRemote.exe (PID: 3712)
- AgentPackageSTRemote.exe (PID: 3380)
- AteraAgent.exe (PID: 2812)
- AgentPackageTicketing.exe (PID: 1620)
- AgentPackageInternalPoller.exe (PID: 2604)
- AgentPackageProgramManagement.exe (PID: 856)
- AgentPackageAgentInformation.exe (PID: 3856)
Reads the machine GUID from the registry
- msiexec.exe (PID: 3568)
- msiexec.exe (PID: 1764)
- msiexec.exe (PID: 3084)
- AteraAgent.exe (PID: 3672)
- AteraAgent.exe (PID: 2812)
- AgentPackageADRemote.exe (PID: 3712)
- AgentPackageSTRemote.exe (PID: 3380)
- AgentPackageTicketing.exe (PID: 1620)
- AgentPackageProgramManagement.exe (PID: 856)
- AgentPackageInternalPoller.exe (PID: 2604)
- AgentPackageAgentInformation.exe (PID: 3856)
Drops the executable file immediately after the start
- rundll32.exe (PID: 3076)
Create files in a temporary directory
- msiexec.exe (PID: 3568)
- rundll32.exe (PID: 3076)
Reads Environment values
- AteraAgent.exe (PID: 3672)
- AgentPackageADRemote.exe (PID: 3712)
- AteraAgent.exe (PID: 2812)
- AgentPackageSTRemote.exe (PID: 3380)
- AgentPackageTicketing.exe (PID: 1620)
- AgentPackageAgentInformation.exe (PID: 3856)
- AgentPackageProgramManagement.exe (PID: 856)
- AgentPackageInternalPoller.exe (PID: 2604)
Creates files in the program directory
- AteraAgent.exe (PID: 3672)
- AteraAgent.exe (PID: 2812)
- AgentPackageInternalPoller.exe (PID: 2604)
- AgentPackageTicketing.exe (PID: 1620)
Reads Microsoft Office registry keys
- AgentPackageAgentInformation.exe (PID: 3856)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
73
Monitored processes
22
Malicious processes
10
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 556 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://HelpdeskSupport512274916.servicedesk.atera.com/GetAgent/Msi/?customerId=1&integratorLogin=hsinha%40fulcrumdigital.net&accountId=001Q3000001cyfLIAQ" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 856 | "C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageProgramManagement\AgentPackageProgramManagement.exe" 757ba443-b799-438e-b826-1c7f832ecf60 "a447cabf-29d5-471c-9e41-f9bb97d66d17" agent-api.atera.com/Production 443 or8ixLi90Mf "syncinstalledapps" | C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageProgramManagement\AgentPackageProgramManagement.exe | AteraAgent.exe | ||||||||||||
User: SYSTEM Company: Atera Networks Integrity Level: SYSTEM Description: AgentPackageProgramManagement Exit code: 0 Version: 22.0.0.0 | |||||||||||||||
| 1620 | "C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageTicketing\AgentPackageTicketing.exe" 757ba443-b799-438e-b826-1c7f832ecf60 "b22bc30e-b206-419b-9a33-9ffb80ee00ba" agent-api.atera.com/Production 443 or8ixLi90Mf "maintain" | C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageTicketing\AgentPackageTicketing.exe | AteraAgent.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Description: AgentPackageTicketing Exit code: 0 Version: 24.10.0.0 Modules
| |||||||||||||||
| 1764 | C:\Windows\system32\MsiExec.exe -Embedding 5E71815415E92E76030E5C747E4699B6 | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2604 | "C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageInternalPoller\AgentPackageInternalPoller.exe" 757ba443-b799-438e-b826-1c7f832ecf60 "6e5c833c-862b-4fcb-b96b-00d705c06306" agent-api.atera.com/Production 443 or8ixLi90Mf "pollAll" | C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageInternalPoller\AgentPackageInternalPoller.exe | AteraAgent.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Description: AgentPackageInternalPoller Exit code: 0 Version: 23.1.0.0 Modules
| |||||||||||||||
| 2812 | "C:\Program Files\ATERA Networks\AteraAgent\AteraAgent.exe" | C:\Program Files\ATERA Networks\AteraAgent\AteraAgent.exe | services.exe | ||||||||||||
User: SYSTEM Company: ATERA Networks Ltd. Integrity Level: SYSTEM Description: AteraAgent Exit code: 0 Version: 1.8.6.7 Modules
| |||||||||||||||
| 2824 | "C:\Windows\System32\cmd.exe" /c cscript "C:\Program Files\Microsoft Office\Office14\ospp.vbs" /dstatus | C:\Windows\System32\cmd.exe | — | AgentPackageAgentInformation.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) | |||||||||||||||
| 3076 | rundll32.exe "C:\Windows\Installer\MSI1268.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_2036468 1 AlphaControlAgentInstallation!AlphaControlAgentInstallation.CustomActions.ShouldContinueInstallation | C:\Windows\System32\rundll32.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3084 | C:\Windows\system32\MsiExec.exe -Embedding E186B28CD04D5771A396DE5164D7EB9F E Global\MSI0000 | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3124 | "TaskKill.exe" /f /im AteraAgent.exe | C:\Windows\System32\taskkill.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
35 393
Read events
35 241
Write events
140
Delete events
12
Modification events
| (PID) Process: | (556) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (556) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (556) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (556) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (556) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (556) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (556) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (556) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (556) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (556) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
160
Suspicious files
36
Text files
34
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3568 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 3248 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 3076 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\MSI1268.tmp-\Microsoft.Deployment.WindowsInstaller.dll | executable | |
MD5:1A5CAEA6734FDD07CAA514C3F3FB75DA | SHA256:CF06D4ED4A8BAF88C82D6C9AE0EFC81C469DE6DA8788AB35F373B350A4B4CDCA | |||
| 3568 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{3c716f8b-f76a-421b-85c0-7f27a5b5418a}_OnDiskSnapshotProp | binary | |
MD5:6AE692CB3FCF8EAF5E9F7E4D1CA7EE71 | SHA256:37561335BEAD43515D8AA3A1B63BB763B4A0810E988FA38CAADCD91F8E3B7157 | |||
| 3076 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\MSI1268.tmp-\System.Management.dll | executable | |
MD5:878E361C41C05C0519BFC72C7D6E141C | SHA256:24DE61B5CAB2E3495FE8D817FB6E80094662846F976CF38997987270F8BBAE40 | |||
| 3568 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:6AE692CB3FCF8EAF5E9F7E4D1CA7EE71 | SHA256:37561335BEAD43515D8AA3A1B63BB763B4A0810E988FA38CAADCD91F8E3B7157 | |||
| 3568 | msiexec.exe | C:\Windows\Installer\1f0fe7.msi | executable | |
MD5:B534A54AF744D74BD5ADC08400260C54 | SHA256:C4565299B4CC8D0866A9B8ED58BD5FD52ADFE1FC6239868C63A805A4AC855BE4 | |||
| 3076 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\MSI1268.tmp-\AlphaControlAgentInstallation.dll | executable | |
MD5:4DB38E9E80632AF71E1842422D4B1873 | SHA256:4924AAD650FA0F88C6FC6CA77068D73F70F0D0866A98212B615290FFB0B04EFA | |||
| 3568 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\~DF959F7D09EC6913D8.TMP | binary | |
MD5:D41BAE431B6DBCAB3ED591FB39F0474C | SHA256:DE216E27B716215EAE3CCDDC9D6D1D3E29DB5CF58F8327D78D7854A82D9FBDE9 | |||
| 3076 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\MSI1268.tmp-\CustomAction.config | xml | |
MD5:1AF5819FDD9EB400A9A511D6AD0D2895 | SHA256:F864F1CF177C104EC6FC25520FE58DD502EA163C77219C4AD0C59BA929253797 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
26
DNS requests
17
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3248 | iexplore.exe | GET | 200 | 67.27.235.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?b40315f06fd1d4d8 | unknown | compressed | 4.66 Kb | unknown |
556 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
3248 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAz1vQYrVgL0erhQLCPM8GY%3D | unknown | binary | 471 b | unknown |
3672 | AteraAgent.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | binary | 727 b | unknown |
2812 | AteraAgent.exe | GET | 200 | 192.229.221.95:80 | http://cacerts.digicert.com/DigiCertTrustedG4CodeSigningRSA4096SHA3842021CA1.crt | unknown | binary | 1.68 Kb | unknown |
3672 | AteraAgent.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | binary | 471 b | unknown |
3672 | AteraAgent.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAZ%2FYEeVZiSnFZlhdD2BlJM%3D | unknown | binary | 727 b | unknown |
3248 | iexplore.exe | GET | 200 | 67.27.235.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?060020e49c501eb3 | unknown | compressed | 4.66 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3248 | iexplore.exe | 20.101.44.219:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
3248 | iexplore.exe | 67.27.235.254:80 | ctldl.windowsupdate.com | LEVEL3 | US | unknown |
3248 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
2656 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3672 | AteraAgent.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
2812 | AteraAgent.exe | 40.119.152.241:443 | agent-api.atera.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
2812 | AteraAgent.exe | 35.157.63.229:443 | ps.pndsn.com | AMAZON-02 | DE | unknown |
556 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
agent-api.atera.com |
| unknown |
ps.pndsn.com |
| unknown |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ps.atera.com |
| unknown |
cacerts.digicert.com |
| whitelisted |
api.nuget.org |
| whitelisted |
Threats
7 ETPRO signatures available at the full report