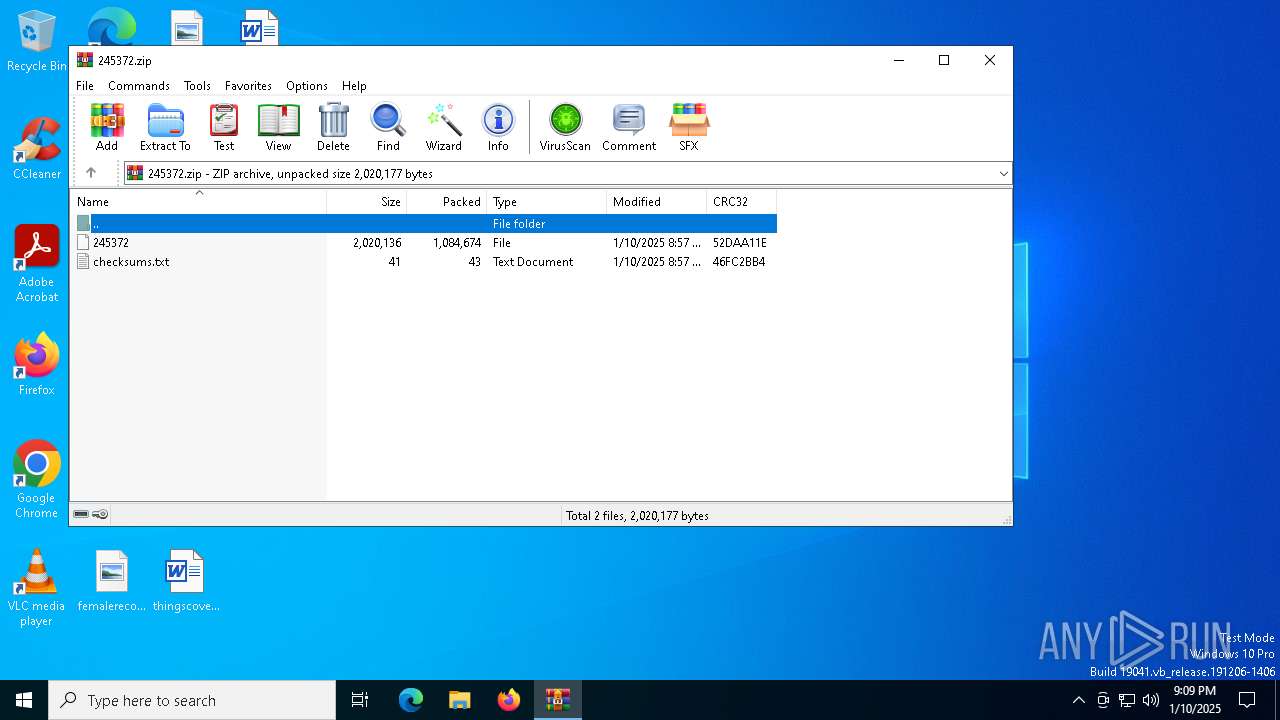
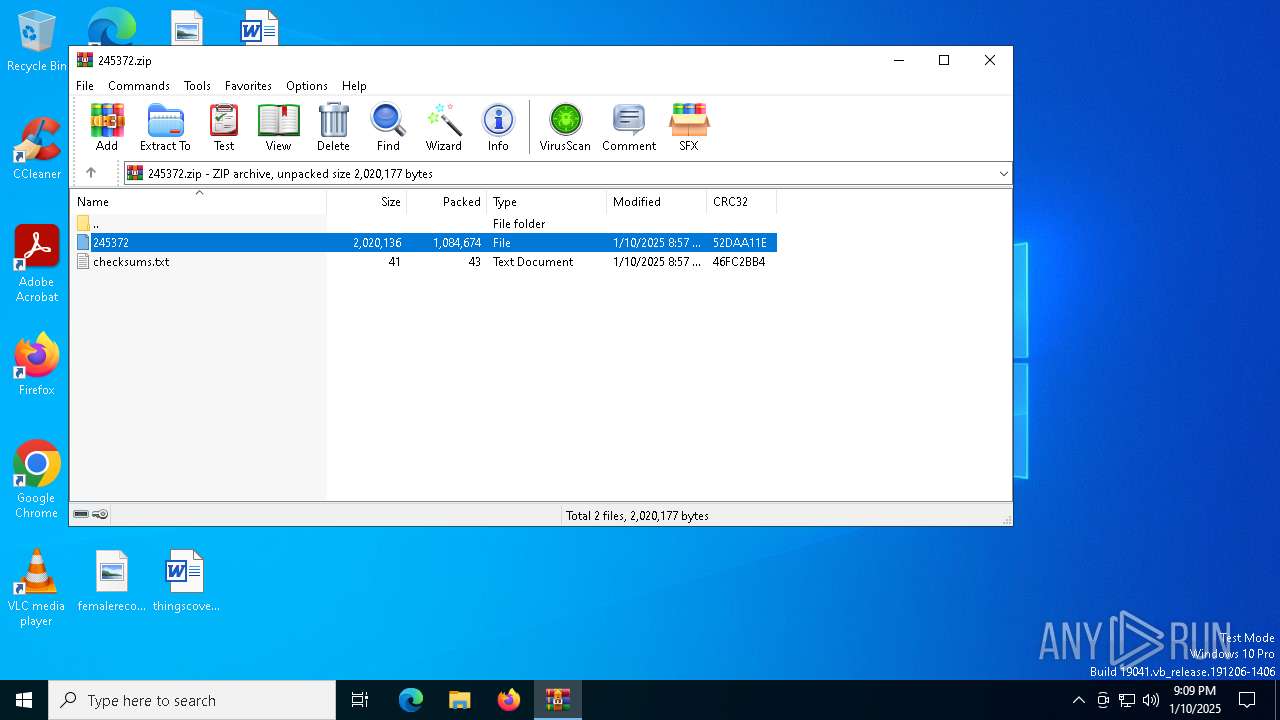
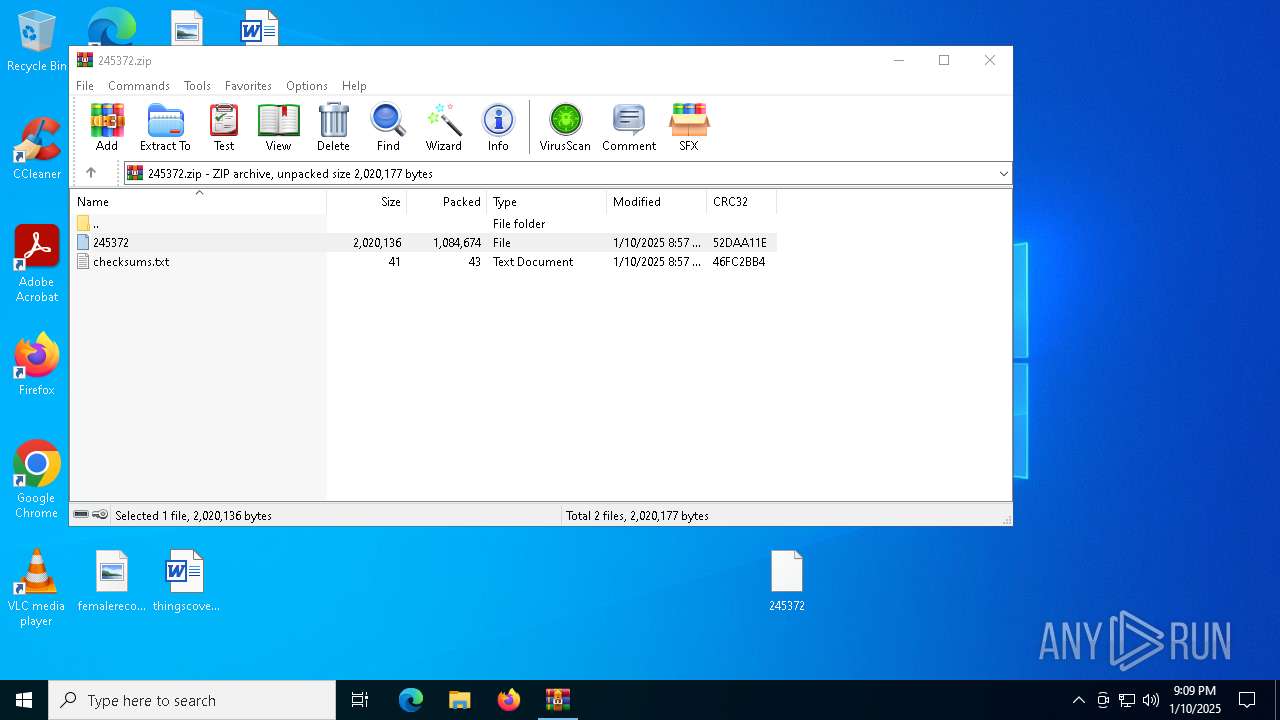
| File name: | 245372.zip |
| Full analysis: | https://app.any.run/tasks/5bc8ddcb-66f9-4942-8999-31d11ae56134 |
| Verdict: | Malicious activity |
| Analysis date: | January 10, 2025, 21:09:11 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 3EF420132F432FD92A8A568329408015 |
| SHA1: | 5AE2CF27A4340DC04EB915A95190D676E274FA0B |
| SHA256: | 010DC3ACE5821FC898D356C1AE185765F00C1A692A3FF5BC9D61E8F0C0289008 |
| SSDEEP: | 49152:GzQ+A9jqWkTejjzHmmwnn63J6ow/xZ/1RAkH8ezvyZfz97cCS5dCK7asYF7oGxVo:GzPABbkCjjzGmwnY6ow5ZtKkdeJYNn5j |
MALICIOUS
Executing a file with an untrusted certificate
- 245372.exe (PID: 3224)
- 245372.exe (PID: 3436)
- 245372.exe (PID: 6540)
SUSPICIOUS
Executes application which crashes
- 245372.exe (PID: 3436)
- 245372.exe (PID: 6540)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 2756)
- OpenWith.exe (PID: 6820)
The sample compiled with english language support
- WinRAR.exe (PID: 2756)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2756)
Reads security settings of Internet Explorer
- notepad.exe (PID: 7108)
Manual execution by a user
- 245372.exe (PID: 3436)
- 245372.exe (PID: 3224)
- 245372.exe (PID: 6540)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 6820)
Checks supported languages
- 245372.exe (PID: 3436)
- 245372.exe (PID: 6540)
Checks proxy server information
- WerFault.exe (PID: 4596)
- WerFault.exe (PID: 880)
Reads the computer name
- 245372.exe (PID: 3436)
Reads the software policy settings
- WerFault.exe (PID: 880)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:01:10 20:57:10 |
| ZipCRC: | 0x52daa11e |
| ZipCompressedSize: | 1084674 |
| ZipUncompressedSize: | 2020136 |
| ZipFileName: | 245372 |
Total processes
141
Monitored processes
8
Malicious processes
0
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 880 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 6540 -s 612 | C:\Windows\SysWOW64\WerFault.exe | 245372.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2756 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\245372.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 3224 | "C:\Users\admin\Desktop\245372.exe" | C:\Users\admin\Desktop\245372.exe | — | explorer.exe | |||||||||||
User: admin Company: Skype Technologies S.A. Integrity Level: MEDIUM Description: Skype Exit code: 3221226540 Version: 4.1.0.179 Modules
| |||||||||||||||
| 3436 | "C:\Users\admin\Desktop\245372.exe" | C:\Users\admin\Desktop\245372.exe | explorer.exe | ||||||||||||
User: admin Company: Skype Technologies S.A. Integrity Level: HIGH Description: Skype Exit code: 1 Version: 4.1.0.179 Modules
| |||||||||||||||
| 4596 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 3436 -s 620 | C:\Windows\SysWOW64\WerFault.exe | 245372.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6540 | "C:\Users\admin\Desktop\245372.exe" | C:\Users\admin\Desktop\245372.exe | explorer.exe | ||||||||||||
User: admin Company: Skype Technologies S.A. Integrity Level: HIGH Description: Skype Exit code: 1 Version: 4.1.0.179 Modules
| |||||||||||||||
| 6820 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7108 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\245372 | C:\Windows\System32\notepad.exe | — | OpenWith.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
8 927
Read events
8 899
Write events
22
Delete events
6
Modification events
| (PID) Process: | (2756) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2756) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2756) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2756) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\245372.zip | |||
| (PID) Process: | (2756) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2756) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2756) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2756) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4596) WerFault.exe | Key: | \REGISTRY\A\{5545ce67-80cf-7433-1d36-10eb856eee2f}\Root\InventoryApplicationFile |
| Operation: | write | Name: | WritePermissionsCheck |
Value: 1 | |||
| (PID) Process: | (4596) WerFault.exe | Key: | \REGISTRY\A\{5545ce67-80cf-7433-1d36-10eb856eee2f}\Root\InventoryApplicationFile\PermissionsCheckTestKey |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
1
Suspicious files
8
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4596 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_245372.exe_a15f195faac99f45888939e16a574214865f548_16a952e8_8426e67f-d495-4fa6-b138-cd719ec51412\Report.wer | — | |
MD5:— | SHA256:— | |||
| 880 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_245372.exe_a15f195faac99f45888939e16a574214865f548_16a952e8_39c7b24a-596f-4677-9871-3da9f49f6d96\Report.wer | — | |
MD5:— | SHA256:— | |||
| 4596 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERF1F6.tmp.WERInternalMetadata.xml | xml | |
MD5:710950535D034DBAB361FBEEF21129F6 | SHA256:4940C65AB7028EC5EC6BFE97F516067D04940D4B979DCA9A6FFE4B0C5BCEA3E5 | |||
| 2756 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2756.17203\245372 | executable | |
MD5:5A324597DED5FAA356A4B0A271940D09 | SHA256:175C3FD62C9BC800DA15199F9303C24AD8C27CB7CB5520A2037580FD0F2592DD | |||
| 4596 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERF245.tmp.xml | xml | |
MD5:95D910D1139A3E4D0AAE4AAE52728A4B | SHA256:4C2CAC1C1C55F59AA1F00AC5942F522678BA5F6A8E7E42C7C8A13A5FC5599239 | |||
| 4596 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERF158.tmp.dmp | binary | |
MD5:6C3B07DBB1B10CF052214D4402D7F8BC | SHA256:DE060C87E37AE7C93E32CDFDE318C53EF1EC3EAB56EE6C21A3B00D550B0E6A5D | |||
| 4596 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\245372.exe.3436.dmp | binary | |
MD5:15B85D7F731744D3A962838E4D815DDE | SHA256:8B08C7E013CCE126F8D6C7BCF682D691AE1C94061803480348AD74DCF35CCC0D | |||
| 4596 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\37C951188967C8EB88D99893D9D191FE | binary | |
MD5:FA84E4BCC92AA5DB735AB50711040CDE | SHA256:6D7205E794FDE4219A62D9692ECDDF612663A5CF20399E79BE87B851FCA4CA33 | |||
| 4596 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\37C951188967C8EB88D99893D9D191FE | binary | |
MD5:5D1B2377004ECD73CAD910EE1833EC4D | SHA256:564979114038C16EDA07D7A6266D07A63EAF330F773B26CC80F20A1915895864 | |||
| 4596 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\21253908F3CB05D51B1C2DA8B681A785 | binary | |
MD5:F6F53CD09A41E968C363419B279D3112 | SHA256:6D2BB01CC7A9BADE2113B219CAC1BDA86B2733196B7E1BD0C807CE1E396B1892 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
36
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.167:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6336 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5340 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5340 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4596 | WerFault.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4596 | WerFault.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5496 | RUXIMICS.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.167:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 104.126.37.153:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
904 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 40.126.32.140:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |