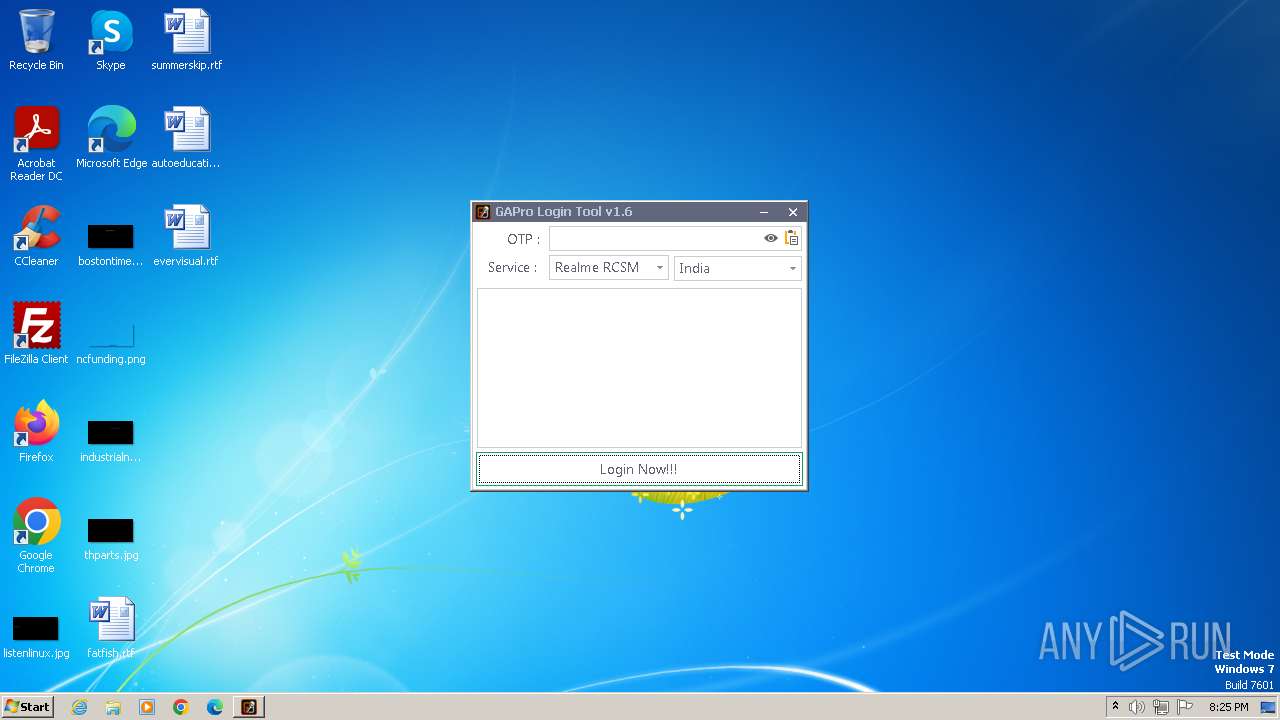
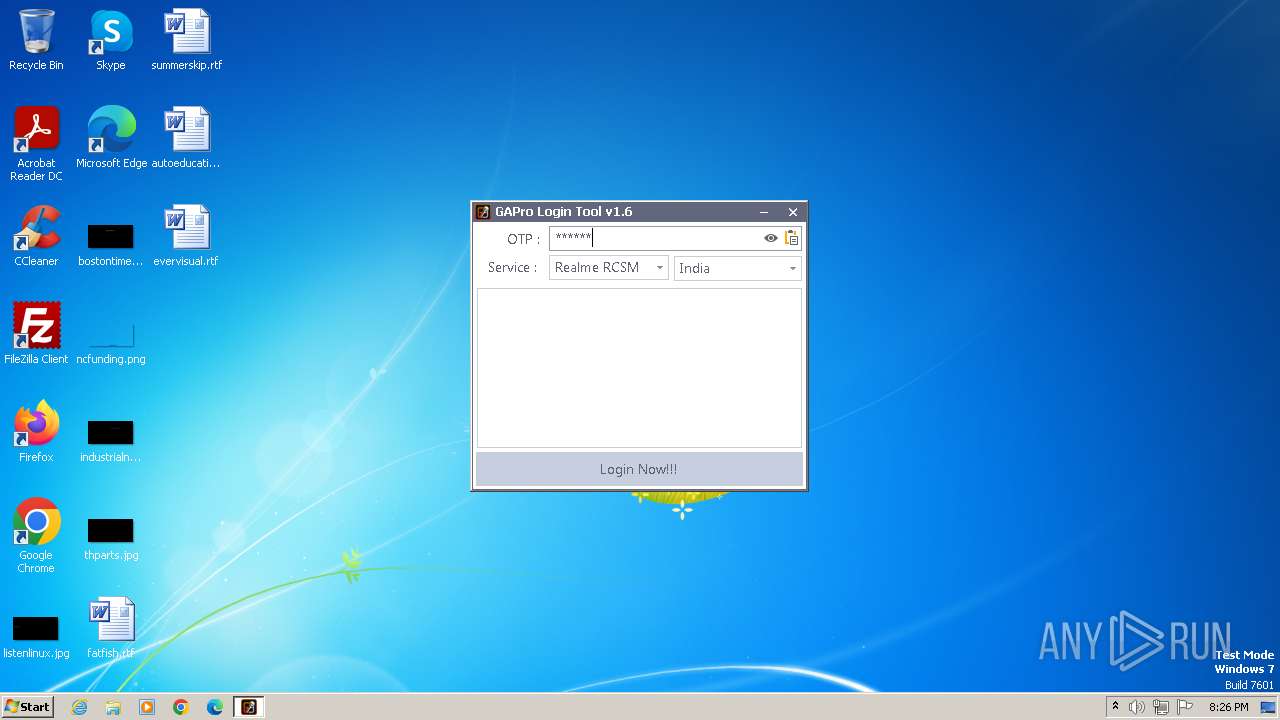
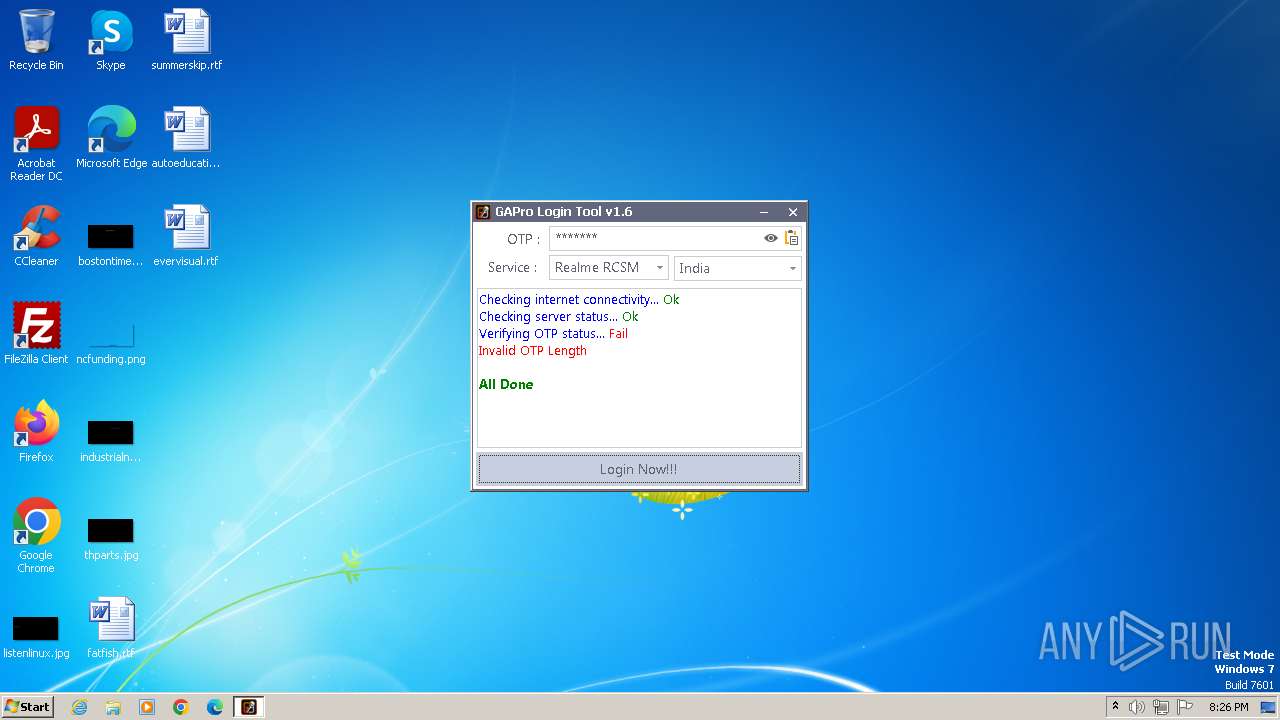
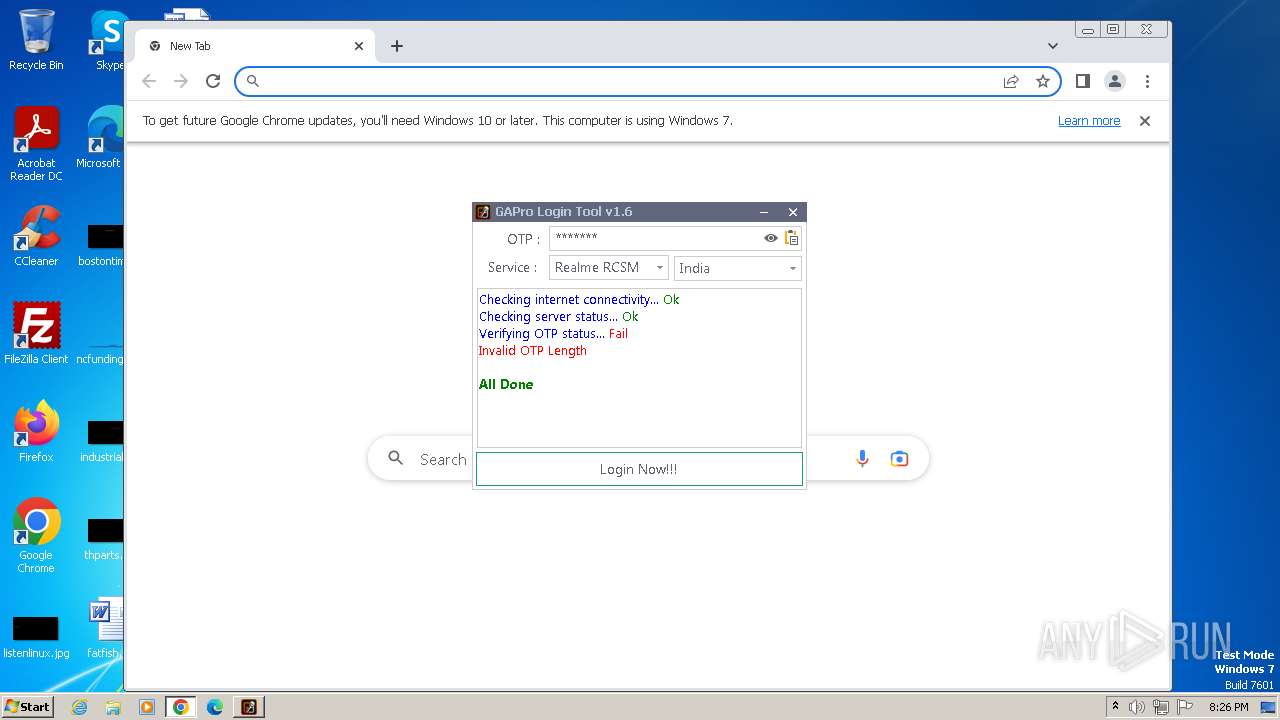
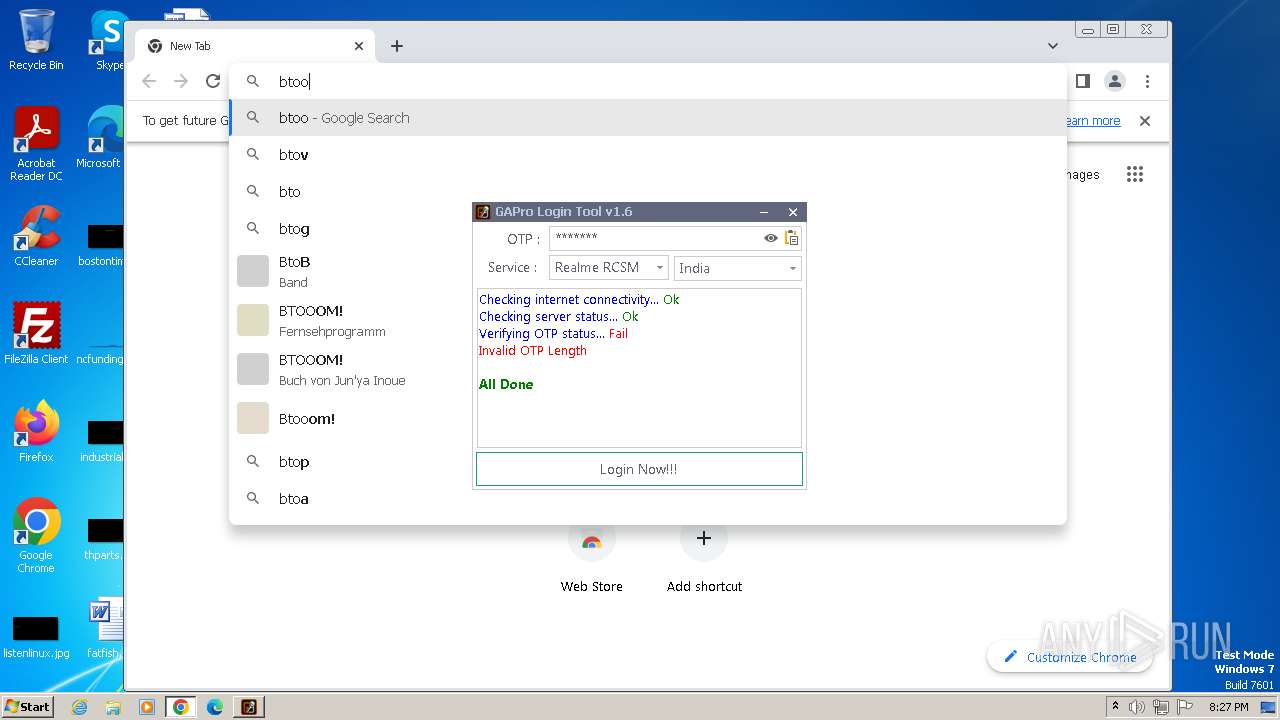
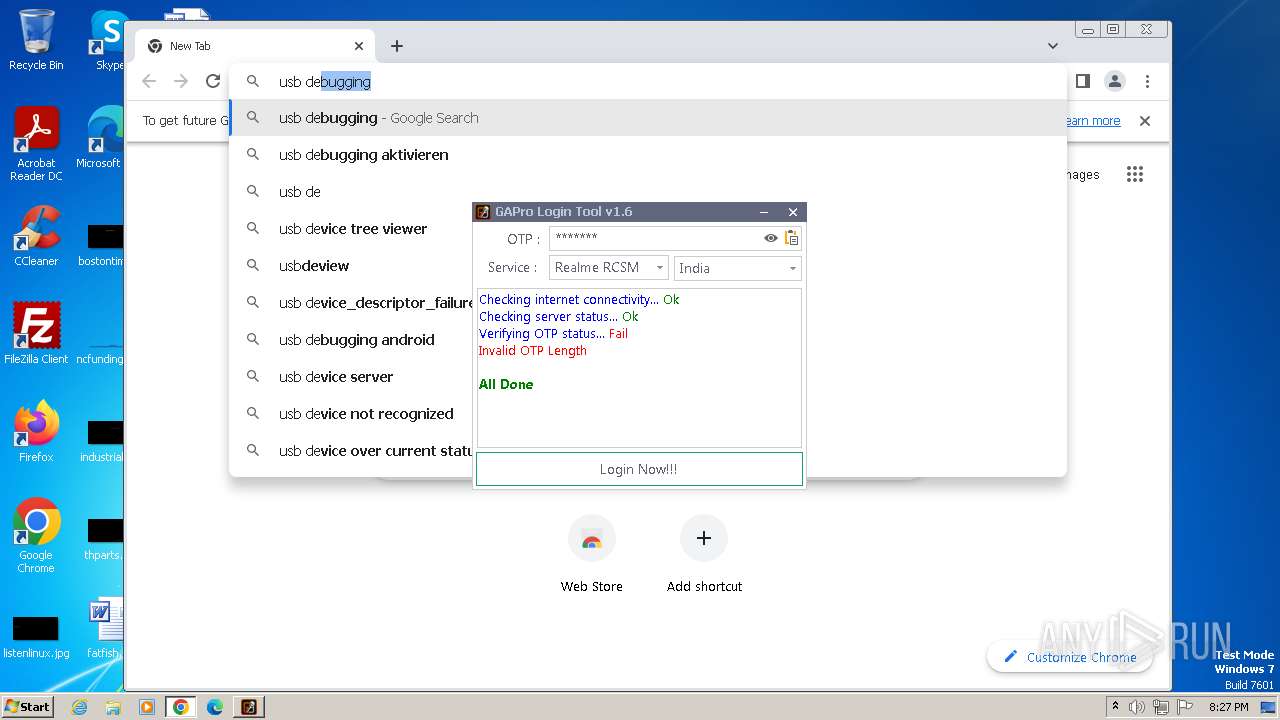
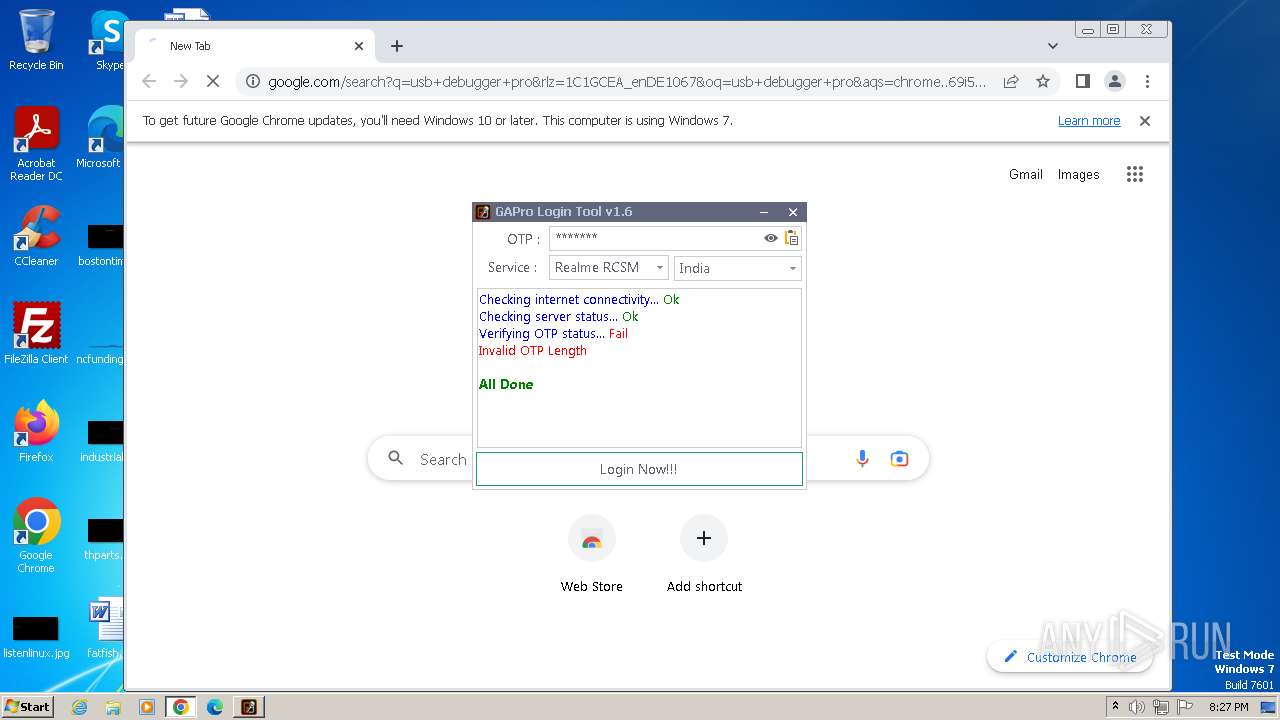
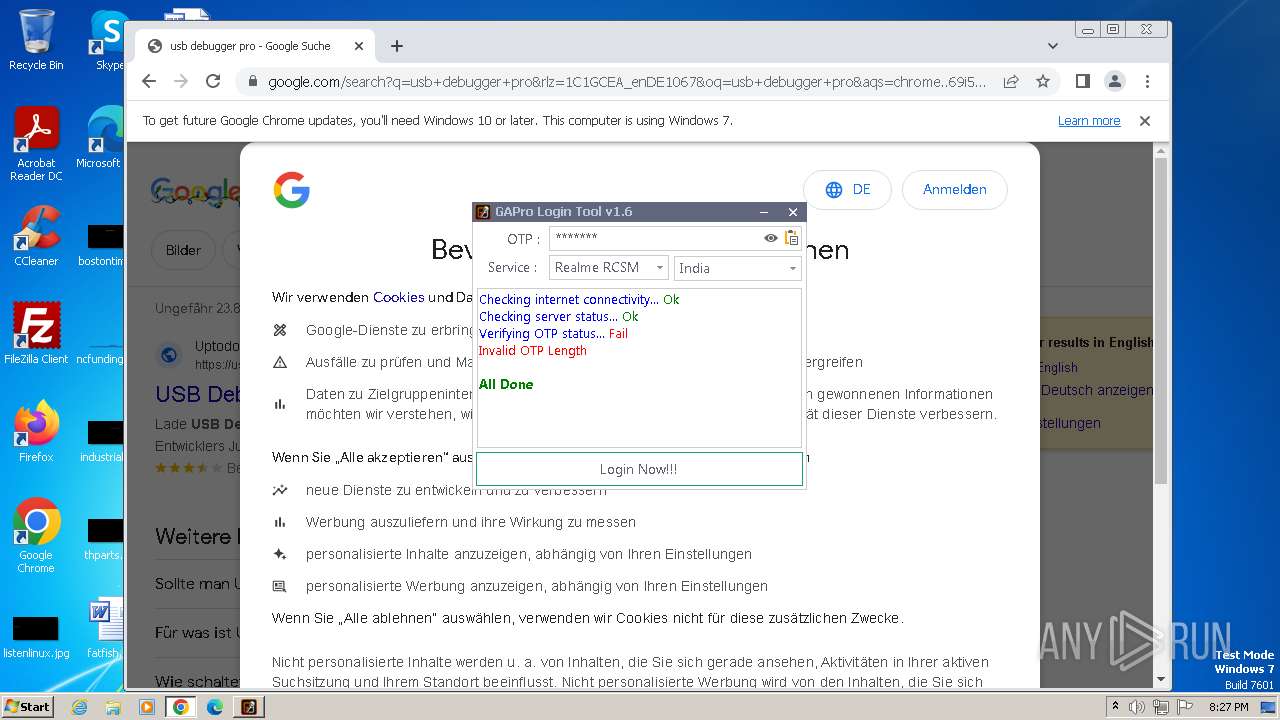
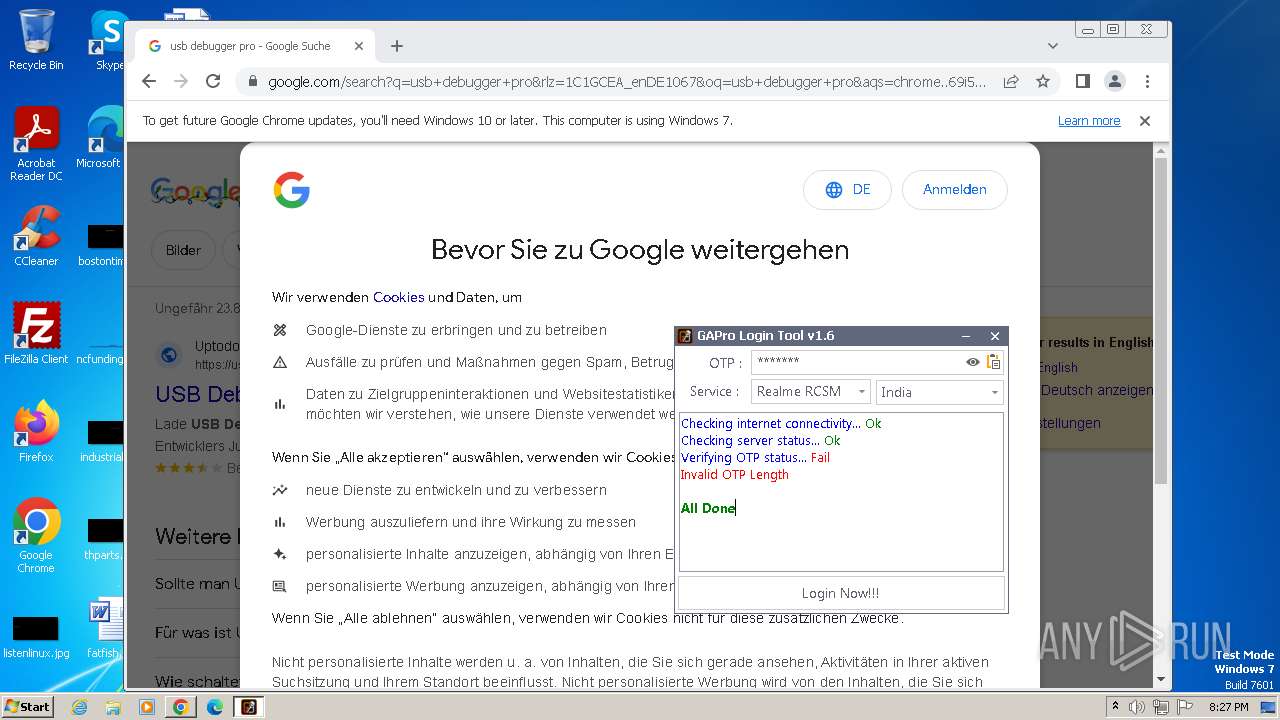
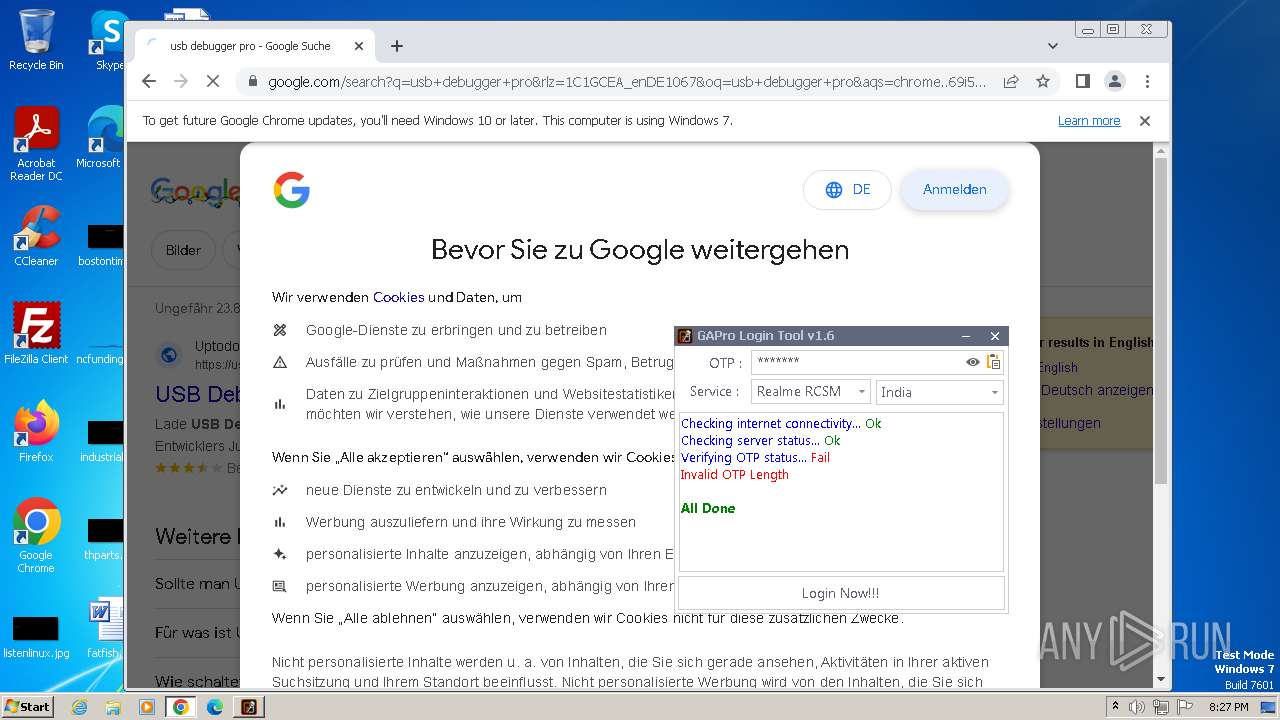
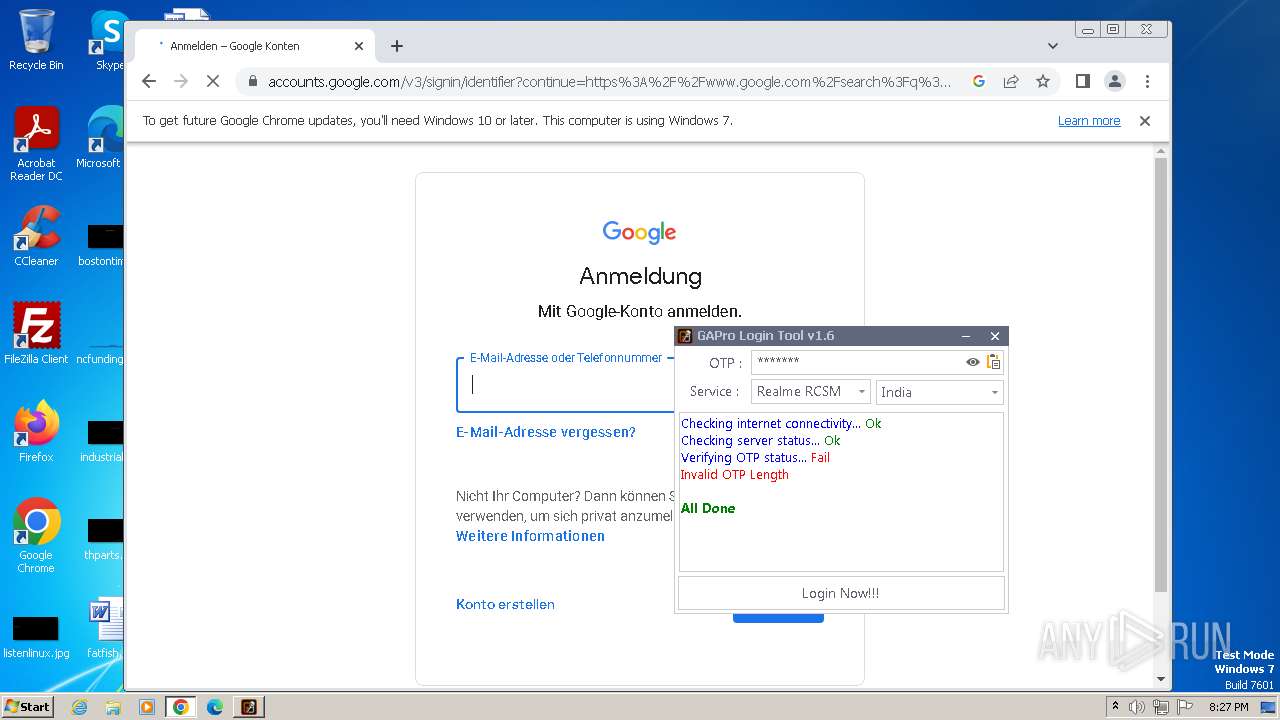
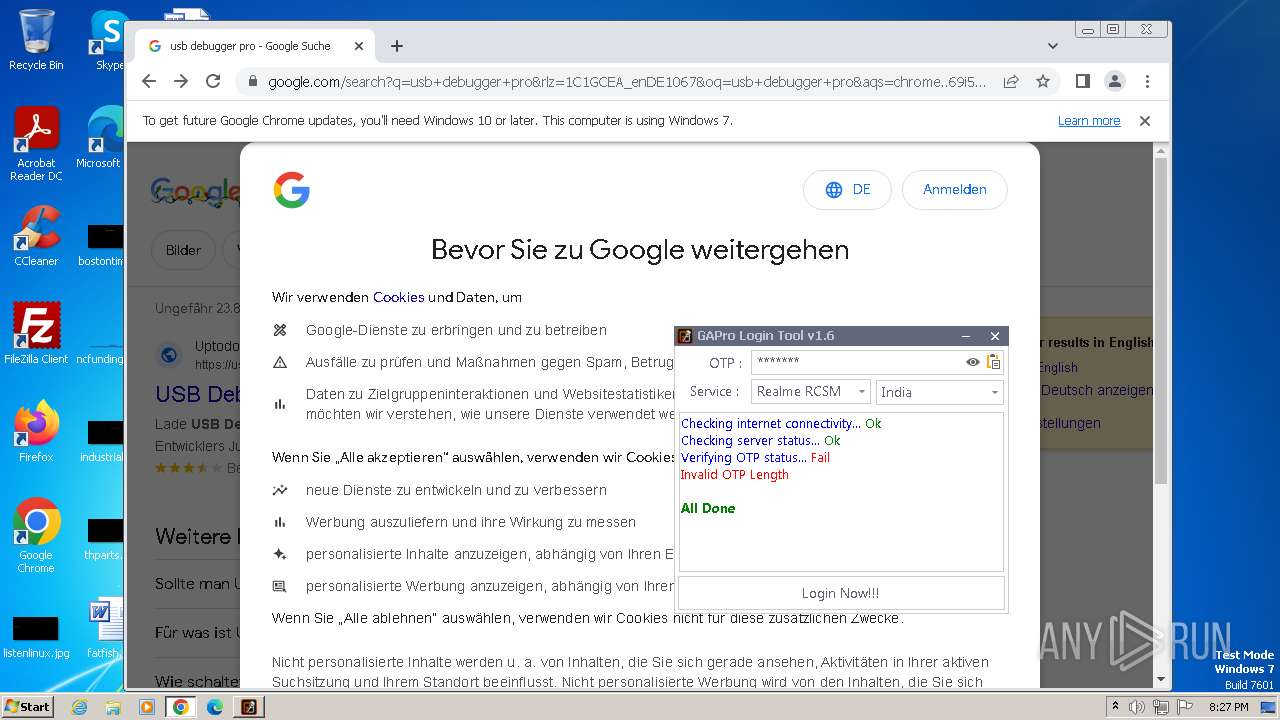
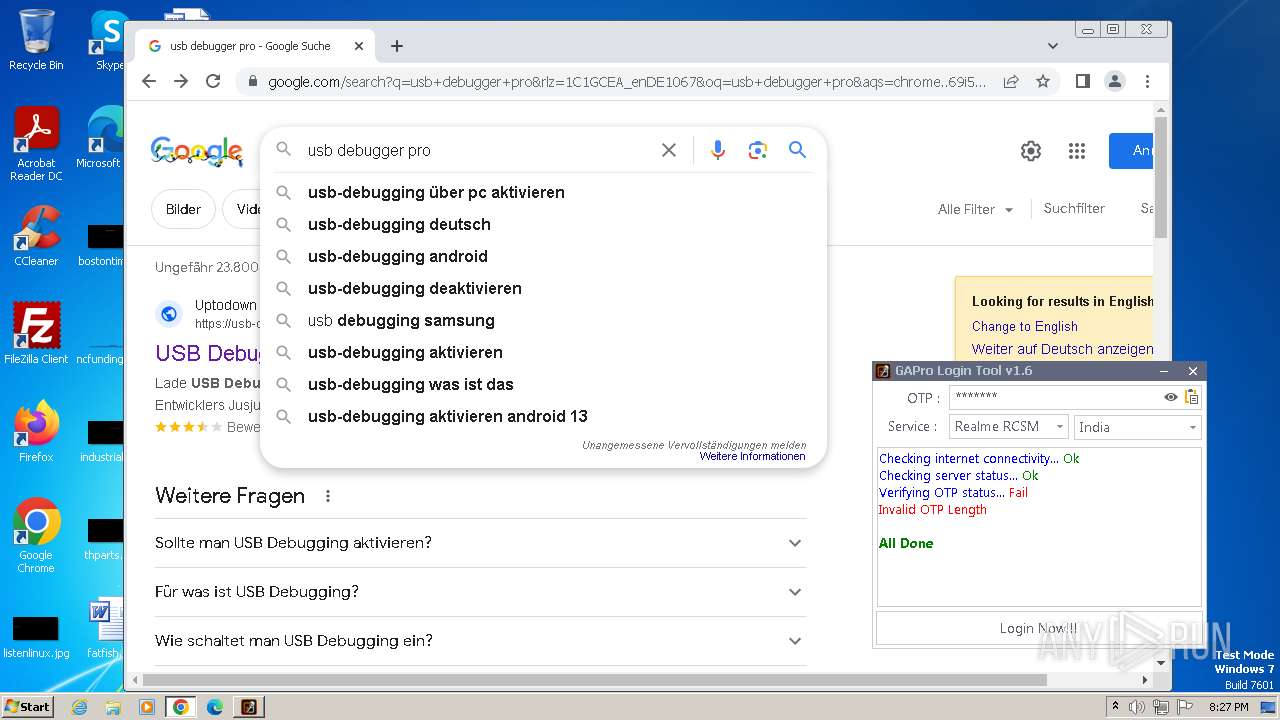
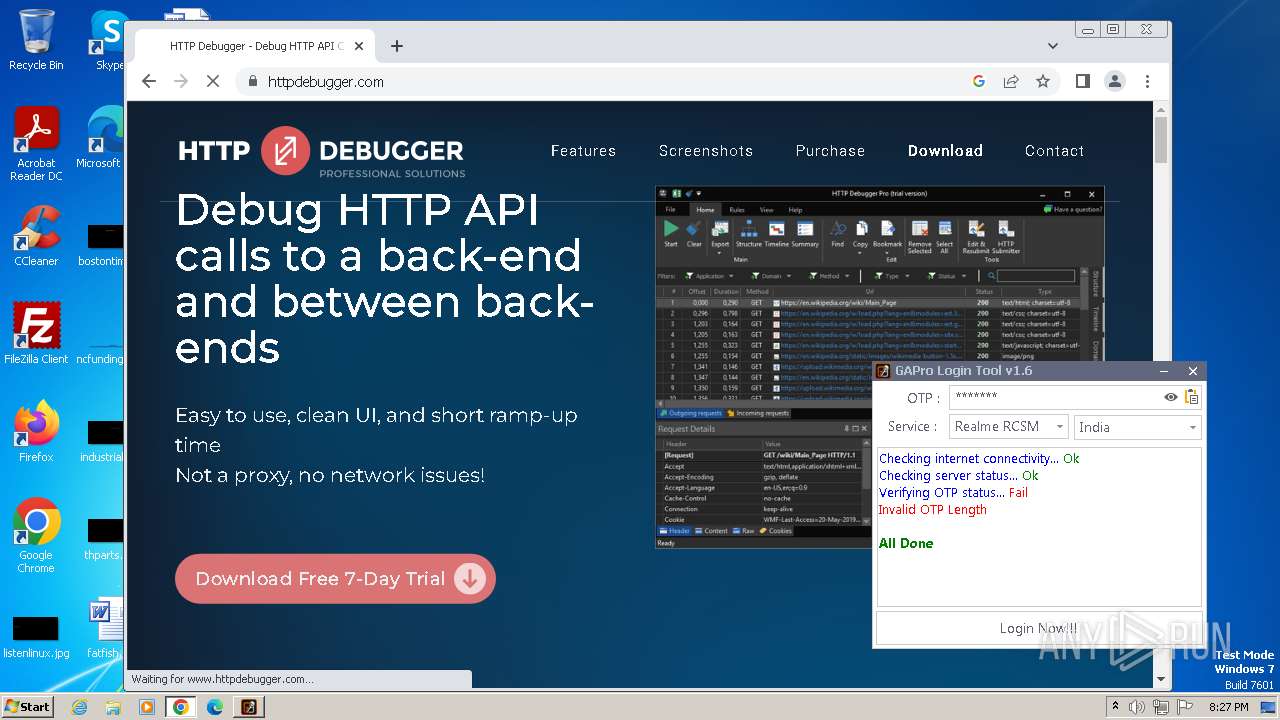
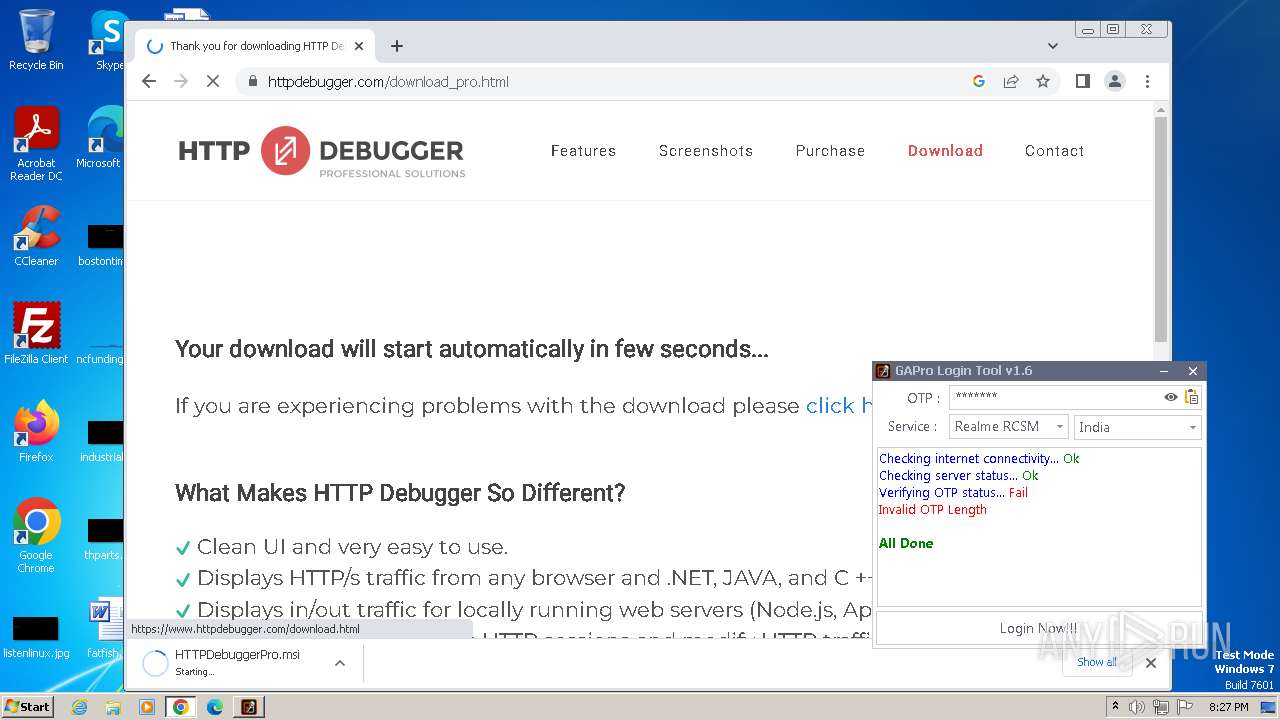
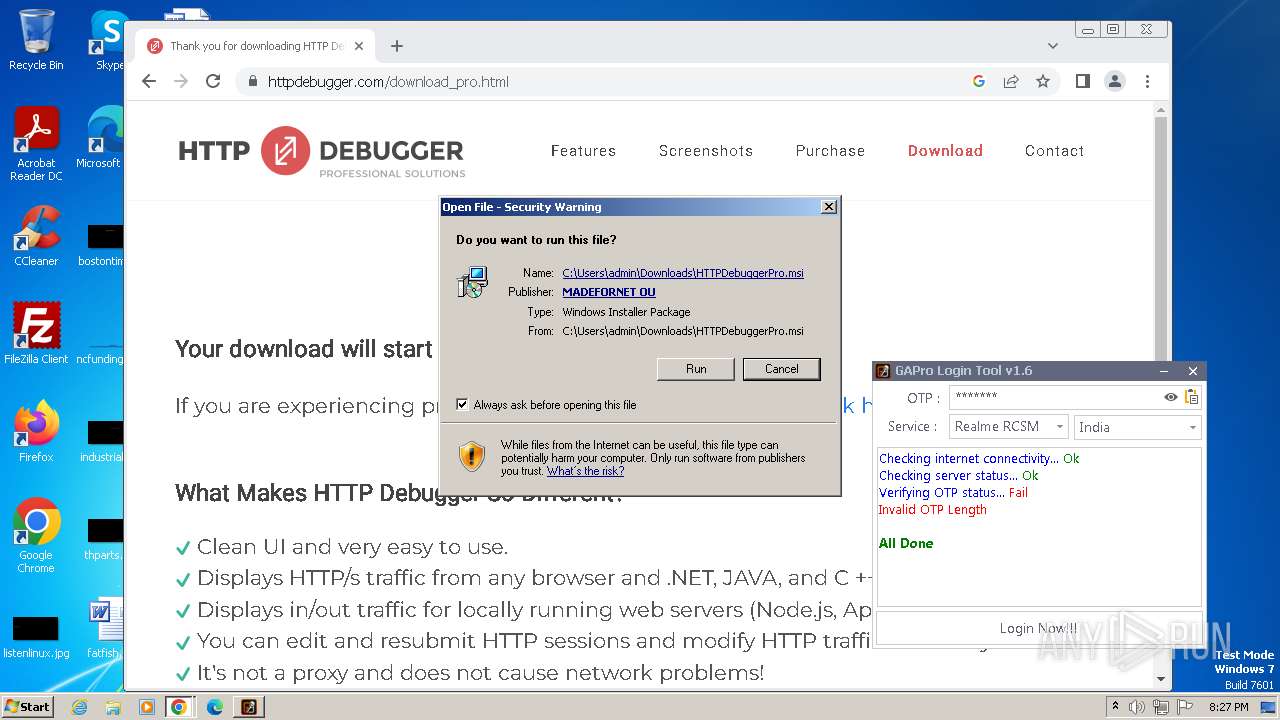
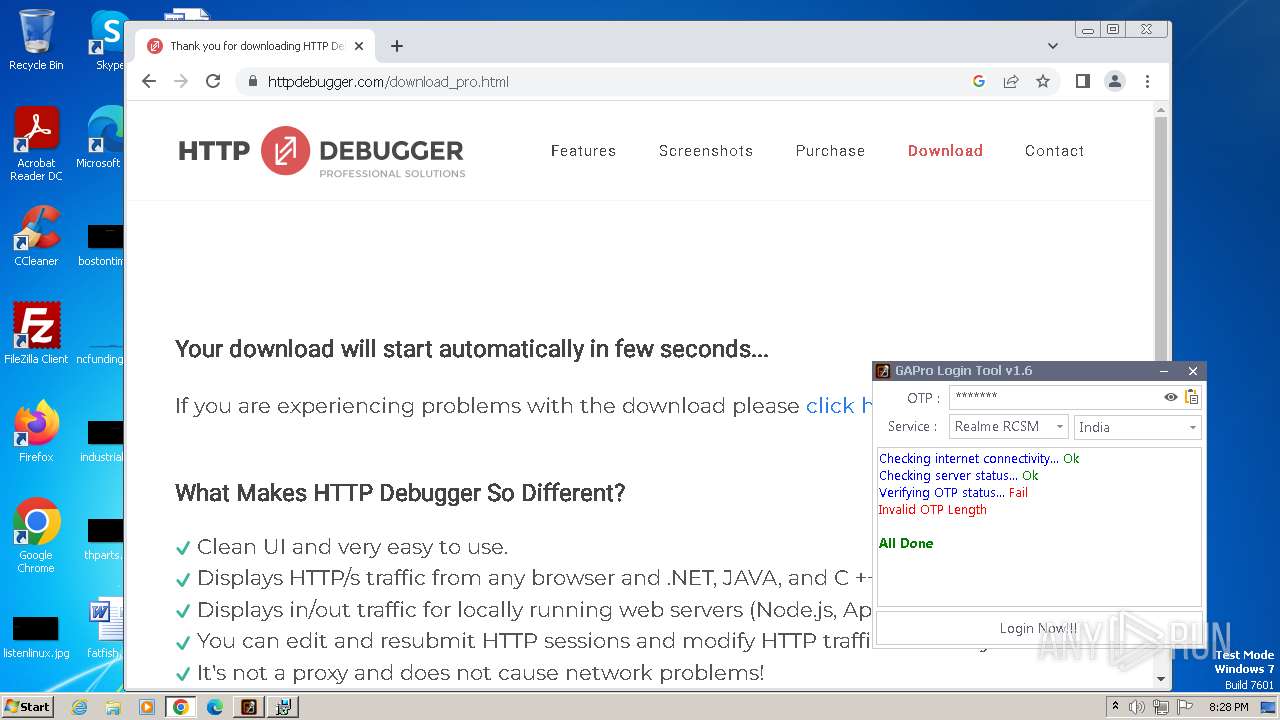
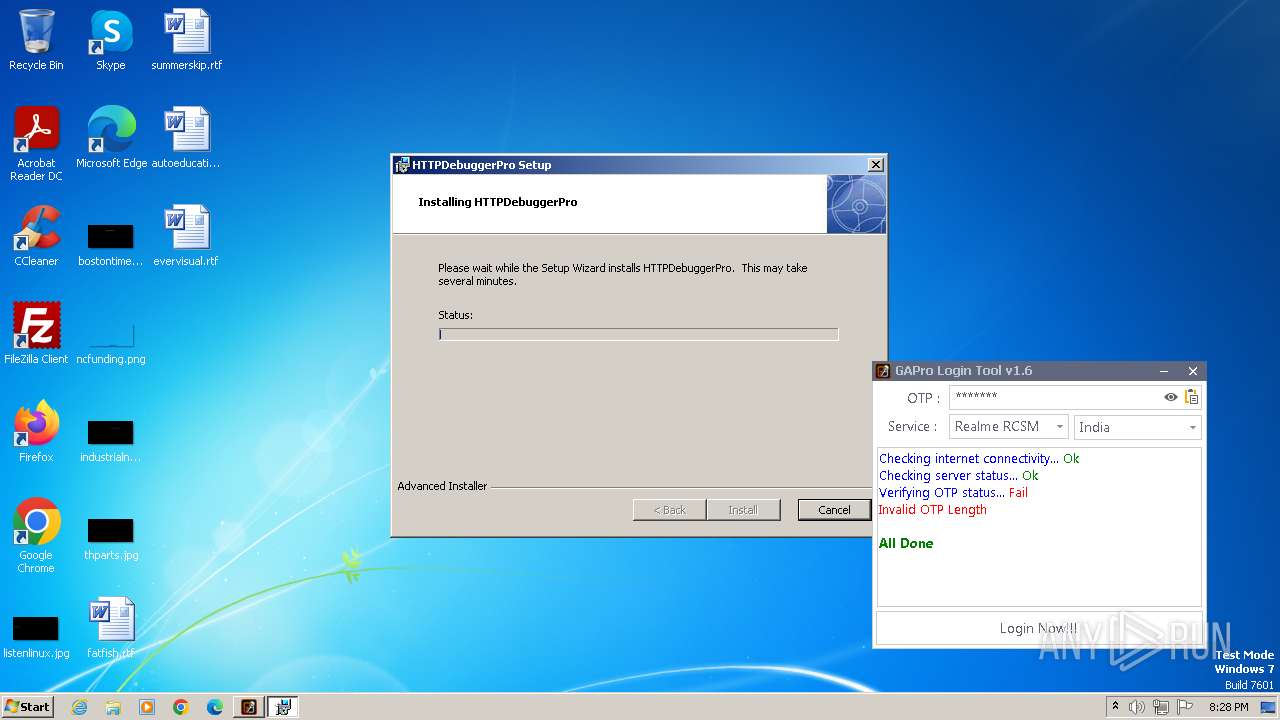
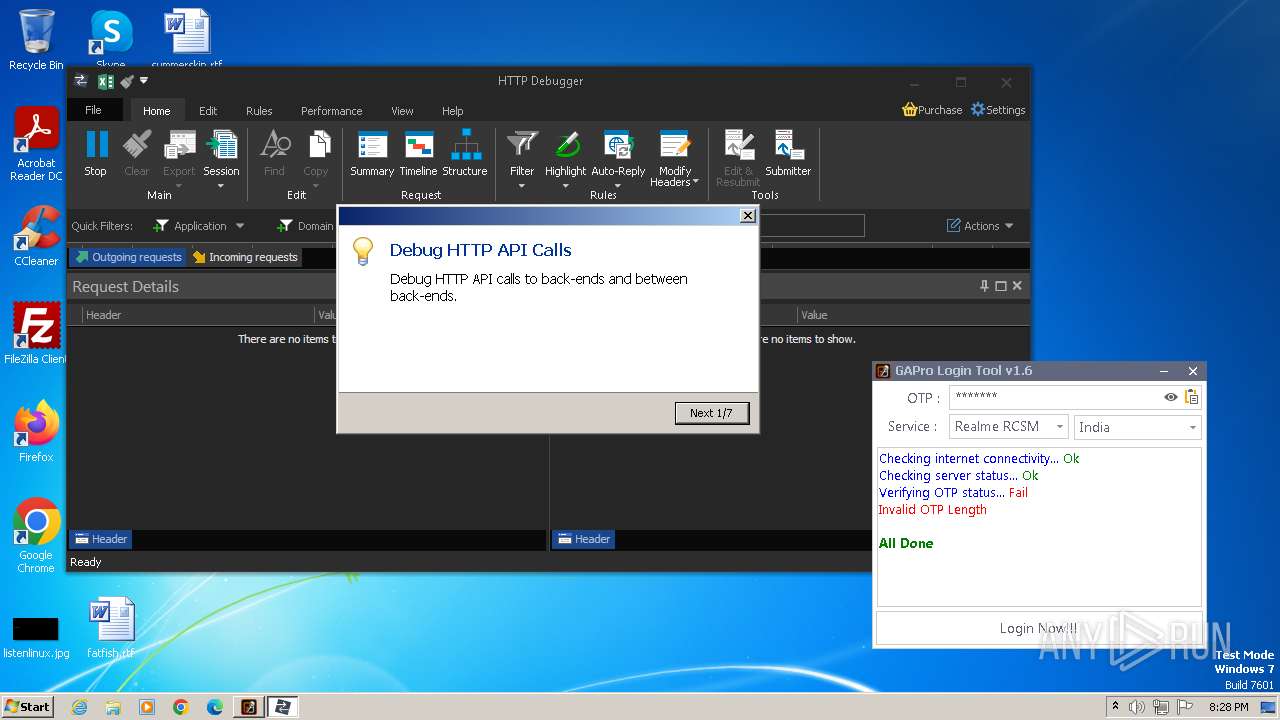
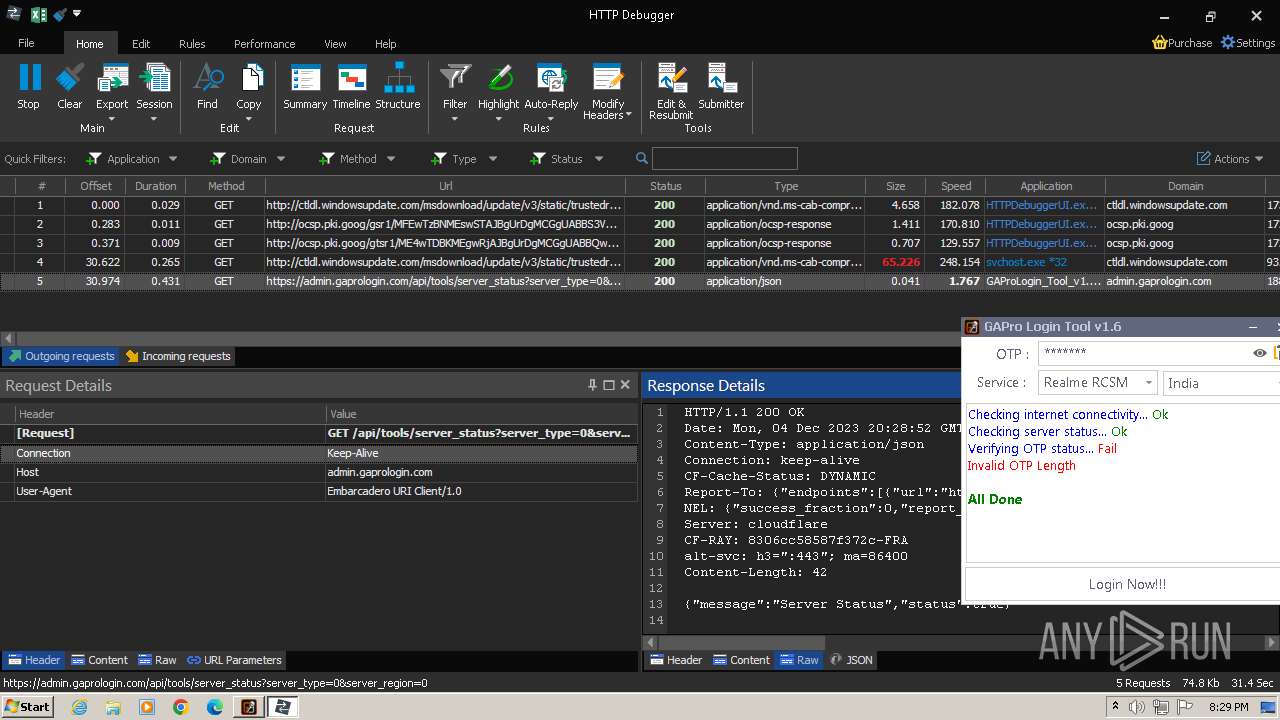
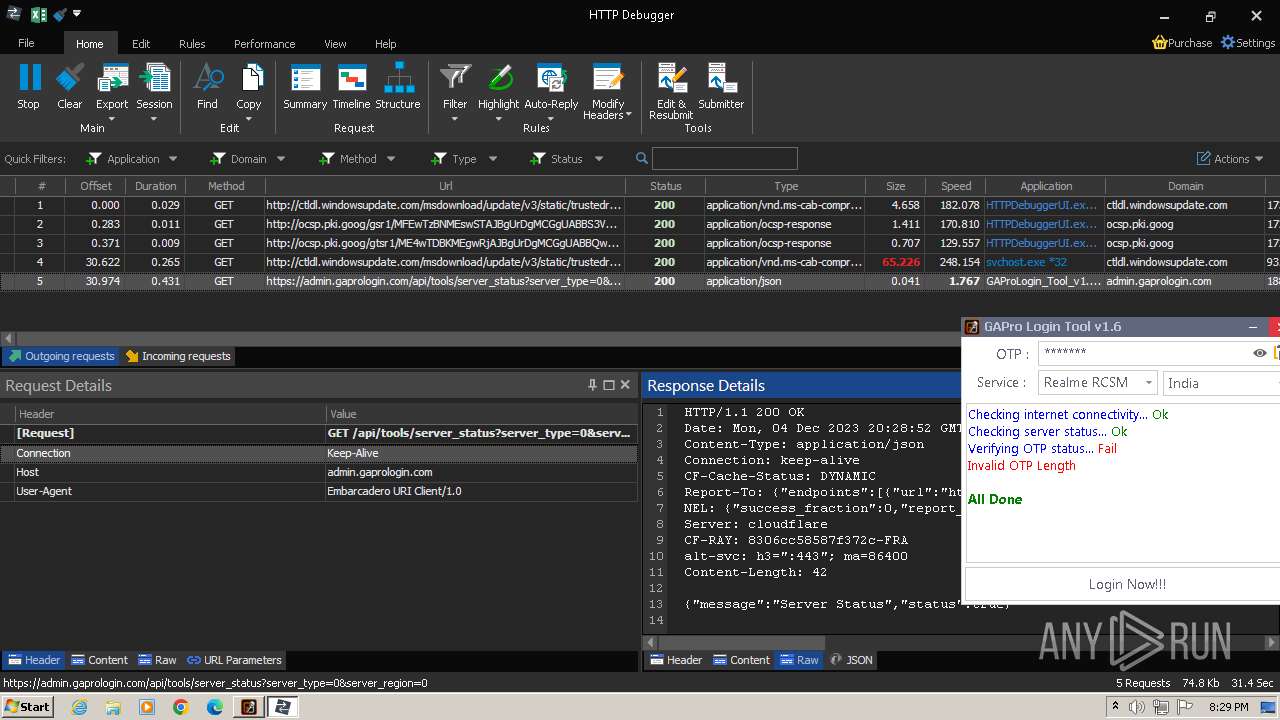
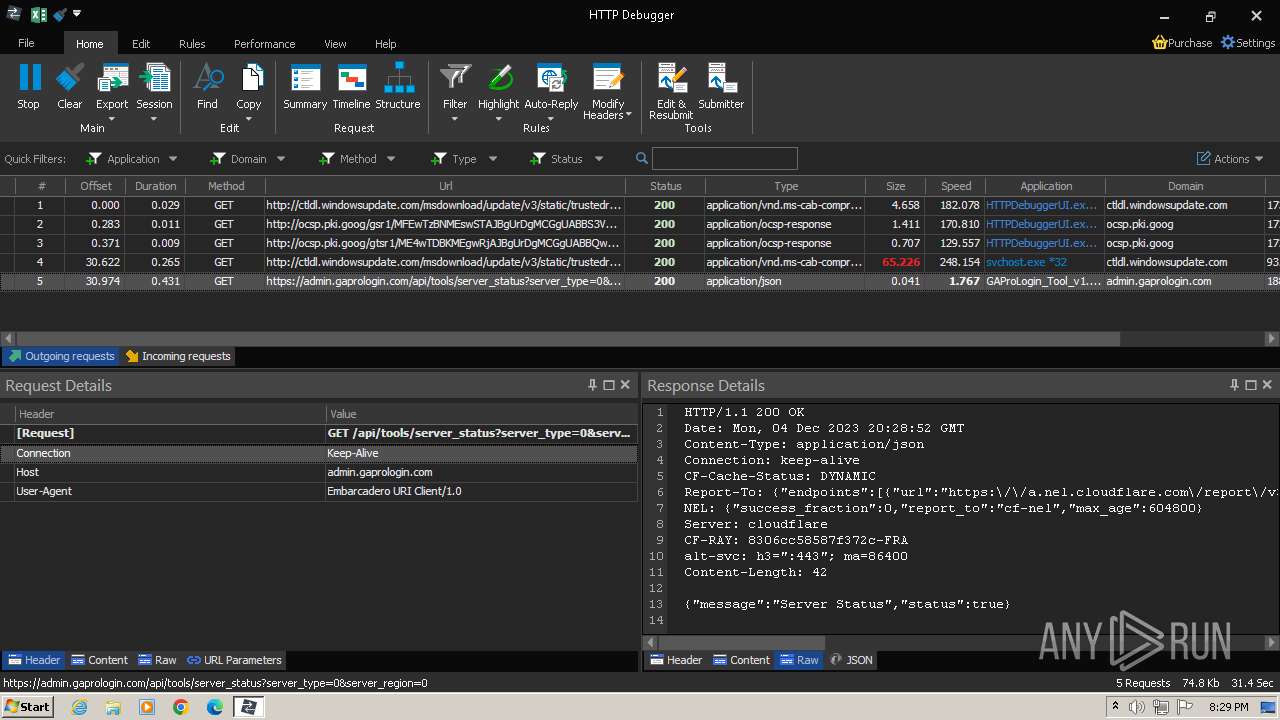
| File name: | GAProLogin_Tool_v1.6.exe |
| Full analysis: | https://app.any.run/tasks/9fbb4757-4cf5-4e12-9bac-076deb1bb07c |
| Verdict: | Malicious activity |
| Analysis date: | December 04, 2023, 20:24:52 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 58E0DC60B78D9DB53B90137EABECB648 |
| SHA1: | EBF5C641AA5AE68DAEA288DDB2E4F9A717F96B30 |
| SHA256: | 00FD5F9682F88B17714C8AE6717039E8042914A2574303EB419C0B79F9F1AD00 |
| SSDEEP: | 98304:O1KIFLtu0QXmUWGPg2+GJf+j15lUHlL3NPzNl/5OnJmOrrF66amhbx2RieMiysiZ:J+eXntkwphOezudwVabviqyJR |
MALICIOUS
Drops the executable file immediately after the start
- msiexec.exe (PID: 3100)
- HTTPDebuggerSvc.exe (PID: 2088)
Creates a writable file in the system directory
- HTTPDebuggerSvc.exe (PID: 2088)
Actions looks like stealing of personal data
- HTTPDebuggerSvc.exe (PID: 2088)
- certutil.exe (PID: 856)
SUSPICIOUS
Reads settings of System Certificates
- GAProLogin_Tool_v1.6.exe (PID: 2600)
- HTTPDebuggerUI.exe (PID: 3888)
Reads the Internet Settings
- GAProLogin_Tool_v1.6.exe (PID: 2600)
- msiexec.exe (PID: 2120)
- HTTPDebuggerUI.exe (PID: 3888)
Process drops legitimate windows executable
- chrome.exe (PID: 3636)
Executes as Windows Service
- VSSVC.exe (PID: 2140)
- HTTPDebuggerSvc.exe (PID: 2088)
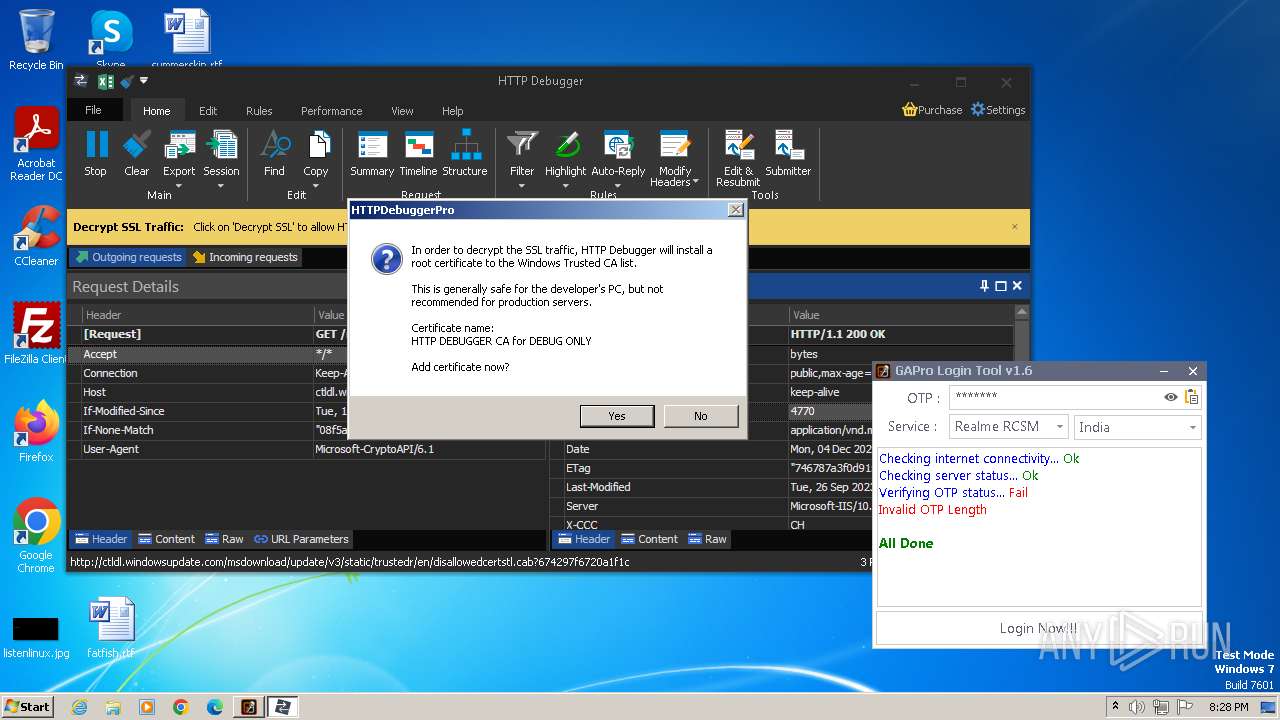
Checks Windows Trust Settings
- msiexec.exe (PID: 3100)
- HTTPDebuggerUI.exe (PID: 3888)
The process creates files with name similar to system file names
- msiexec.exe (PID: 3100)
Drops a system driver (possible attempt to evade defenses)
- msiexec.exe (PID: 3100)
- HTTPDebuggerSvc.exe (PID: 2088)
Creates files in the driver directory
- HTTPDebuggerSvc.exe (PID: 2088)
Reads Microsoft Outlook installation path
- HTTPDebuggerUI.exe (PID: 3888)
Reads Internet Explorer settings
- HTTPDebuggerUI.exe (PID: 3888)
Reads security settings of Internet Explorer
- HTTPDebuggerUI.exe (PID: 3888)
Adds/modifies Windows certificates
- GAProLogin_Tool_v1.6.exe (PID: 2600)
INFO
Manual execution by a user
- wmpnscfg.exe (PID: 2544)
- chrome.exe (PID: 3636)
- chrome.exe (PID: 1152)
Checks supported languages
- wmpnscfg.exe (PID: 2544)
- GAProLogin_Tool_v1.6.exe (PID: 2600)
- msiexec.exe (PID: 3100)
- msiexec.exe (PID: 2120)
- HTTPDebuggerSvc.exe (PID: 2088)
- HTTPDebuggerSvc.exe (PID: 3240)
- HTTPDebuggerUI.exe (PID: 3888)
- certutil.exe (PID: 856)
- msiexec.exe (PID: 276)
Reads the machine GUID from the registry
- GAProLogin_Tool_v1.6.exe (PID: 2600)
- msiexec.exe (PID: 3100)
- msiexec.exe (PID: 2120)
- HTTPDebuggerSvc.exe (PID: 2088)
- HTTPDebuggerUI.exe (PID: 3888)
- HTTPDebuggerSvc.exe (PID: 3240)
- msiexec.exe (PID: 276)
Reads the computer name
- wmpnscfg.exe (PID: 2544)
- msiexec.exe (PID: 3100)
- msiexec.exe (PID: 2120)
- msiexec.exe (PID: 276)
- HTTPDebuggerSvc.exe (PID: 2088)
- HTTPDebuggerSvc.exe (PID: 3240)
- HTTPDebuggerUI.exe (PID: 3888)
- GAProLogin_Tool_v1.6.exe (PID: 2600)
- certutil.exe (PID: 856)
Drops the executable file immediately after the start
- chrome.exe (PID: 3636)
- msiexec.exe (PID: 2168)
Application launched itself
- chrome.exe (PID: 3636)
- msiexec.exe (PID: 3100)
- chrome.exe (PID: 1152)
The process uses the downloaded file
- chrome.exe (PID: 604)
- chrome.exe (PID: 3636)
Checks proxy server information
- GAProLogin_Tool_v1.6.exe (PID: 2600)
- HTTPDebuggerUI.exe (PID: 3888)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 2168)
Create files in a temporary directory
- msiexec.exe (PID: 3100)
Reads product name
- HTTPDebuggerSvc.exe (PID: 2088)
- HTTPDebuggerSvc.exe (PID: 3240)
Reads Environment values
- HTTPDebuggerSvc.exe (PID: 2088)
- HTTPDebuggerSvc.exe (PID: 3240)
Creates files in the program directory
- HTTPDebuggerSvc.exe (PID: 2088)
Creates files or folders in the user directory
- HTTPDebuggerUI.exe (PID: 3888)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .dll | | | Win32 Dynamic Link Library (generic) (43.5) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (29.8) |
| .exe | | | Generic Win/DOS Executable (13.2) |
| .exe | | | DOS Executable Generic (13.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:07:06 11:52:29+02:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 6398976 |
| InitializedDataSize: | 2337280 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x12a3ef1 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.6.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| FileDescription: | GAProLogin |
| FileVersion: | 1.6.0.0 |
| ProgramID: | com.embarcadero.GAProLogin |
| ProductName: | GAProLogin |
| ProductVersion: | 1.0.0.0 |
Total processes
99
Monitored processes
53
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 276 | C:\Windows\system32\MsiExec.exe -Embedding D686F5AADE5AAE5C499F29DBA481FC00 | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 280 | "C:\Users\admin\AppData\Local\Temp\GAProLogin_Tool_v1.6.exe" | C:\Users\admin\AppData\Local\Temp\GAProLogin_Tool_v1.6.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: GAProLogin Exit code: 3221226540 Version: 1.6.0.0 Modules
| |||||||||||||||
| 604 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=4564 --field-trial-handle=1164,i,15756102692359306776,4345495189475140484,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 668 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1076 --field-trial-handle=1164,i,12724490328513335889,9940012662887319366,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 788 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --first-renderer-process --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=2188 --field-trial-handle=1164,i,12724490328513335889,9940012662887319366,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 856 | nss\certutil -A -t "TCu" -i "C:\ProgramData\HTTPDebuggerPro\Cert\SSL\HTTP DEBUGGER CA for DEBUG ONLY 2.cer" -n "HTTP DEBUGGER CA for DEBUG ONLY 2" -d sql:"C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\QLDYZ5~1.DEF"-f pwfile | C:\Program Files\HTTPDebuggerPro\nss\certutil.exe | HTTPDebuggerSvc.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 255 Modules
| |||||||||||||||
| 948 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=angle --use-angle=swiftshader-webgl --mojo-platform-channel-handle=1460 --field-trial-handle=1164,i,12724490328513335889,9940012662887319366,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 952 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=1396 --field-trial-handle=1164,i,12724490328513335889,9940012662887319366,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1116 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=4172 --field-trial-handle=1164,i,15756102692359306776,4345495189475140484,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1128 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=21 --mojo-platform-channel-handle=676 --field-trial-handle=1164,i,15756102692359306776,4345495189475140484,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
Total events
34 065
Read events
33 822
Write events
233
Delete events
10
Modification events
| (PID) Process: | (2600) GAProLogin_Tool_v1.6.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2600) GAProLogin_Tool_v1.6.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000005A010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2600) GAProLogin_Tool_v1.6.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3636) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3636) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3636) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3636) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3636) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3636) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 1 | |||
| (PID) Process: | (3636) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
Executable files
35
Suspicious files
252
Text files
67
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3636 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF22d3b5.TMP | — | |
MD5:— | SHA256:— | |||
| 3636 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3636 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Variations | binary | |
MD5:961E3604F228B0D10541EBF921500C86 | SHA256:F7B24F2EB3D5EB0550527490395D2F61C3D2FE74BB9CB345197DAD81B58B5FED | |||
| 3636 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF22d684.TMP | — | |
MD5:— | SHA256:— | |||
| 3636 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3636 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Platform Notifications\LOG.old | text | |
MD5:05387A3C4FCF1F3B992FF9FBF045AA1A | SHA256:B01E9451B8F6ABF03C9CD2E158C02D0A6BFDF771944F5D0B96DAD2DA6A7E3C8F | |||
| 3636 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\cb2ad675-101d-4f33-9c68-a80975b8c8e3.tmp | binary | |
MD5:5058F1AF8388633F609CADB75A75DC9D | SHA256:— | |||
| 3636 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Platform Notifications\LOG.old~RF22d4bf.TMP | text | |
MD5:65635E713D5CFC914717D1CC4CAC6989 | SHA256:4CB3EEB0369758290ABD7868DFD85D663C4AEF6C727FFF43BE693FDDBD0A6C28 | |||
| 3636 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Extension State\LOG.old | text | |
MD5:4F91C1E6BB20F7FF680A09754DC1139D | SHA256:48F675EFB86CCE216ED6DC02D7A05D91BFD3ACB402DF3617DF2E779D02264215 | |||
| 3636 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:8175FB7046E977DAAD01289080C116EF | SHA256:19E403B4BEF7D83DD425AB6A54DE943D244A16E5EA121DEC91C417608AEAACB7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
86
DNS requests
121
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
868 | svchost.exe | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/fzrp6xpdtqq2vakspwulwu2yae_62/khaoiebndkojlmppeemjhbpbandiljpe_62_win_n2jkzx33j3rlsltywormztyyby.crx3 | unknown | binary | 5.51 Kb | unknown |
868 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/fzrp6xpdtqq2vakspwulwu2yae_62/khaoiebndkojlmppeemjhbpbandiljpe_62_win_n2jkzx33j3rlsltywormztyyby.crx3 | unknown | — | — | unknown |
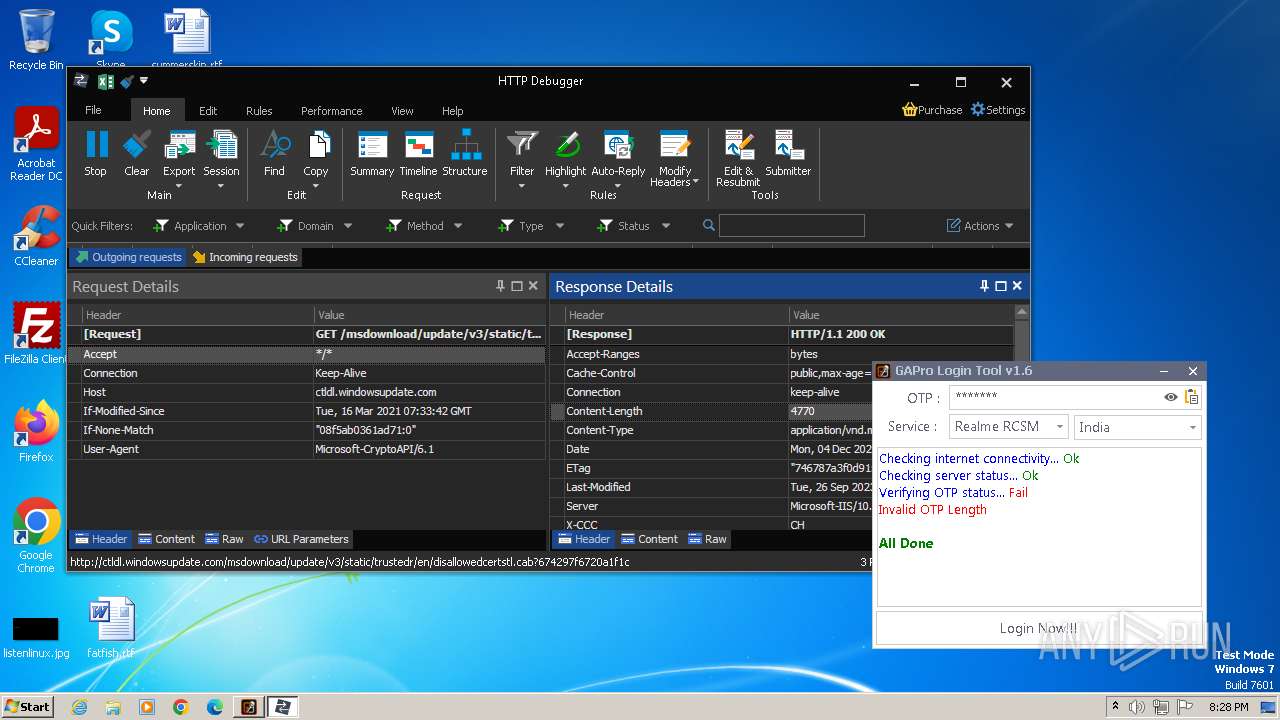
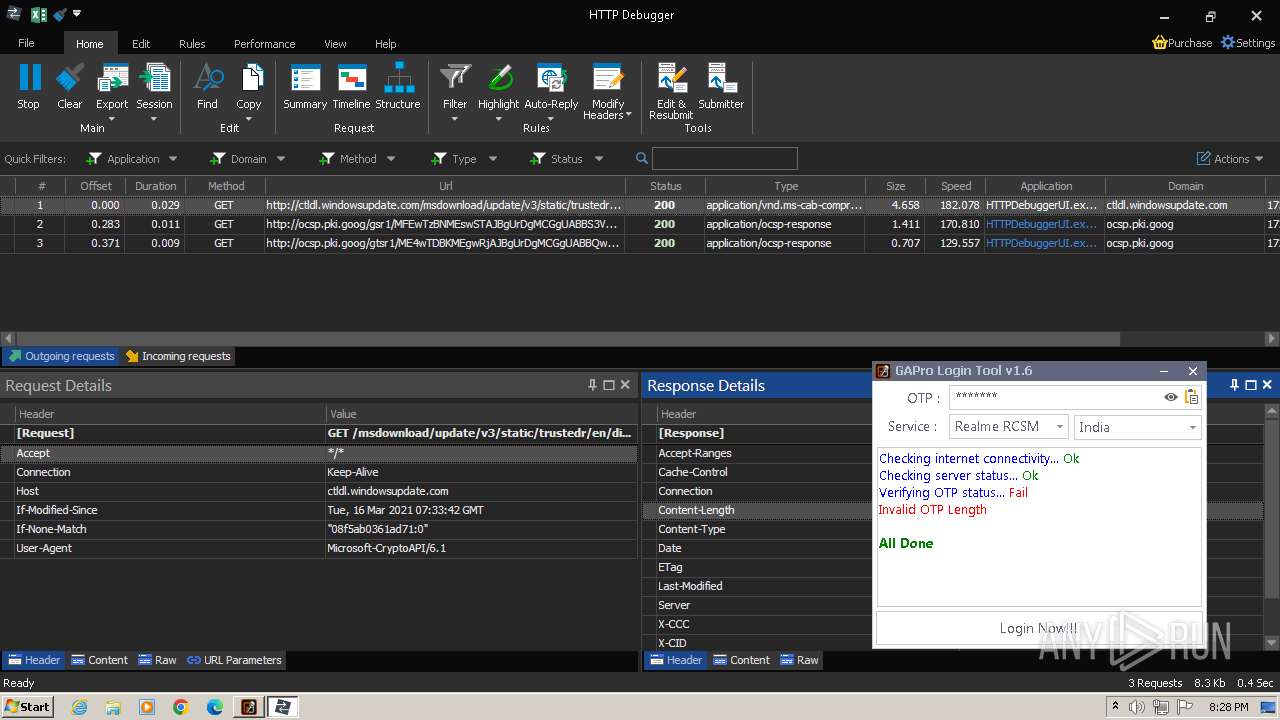
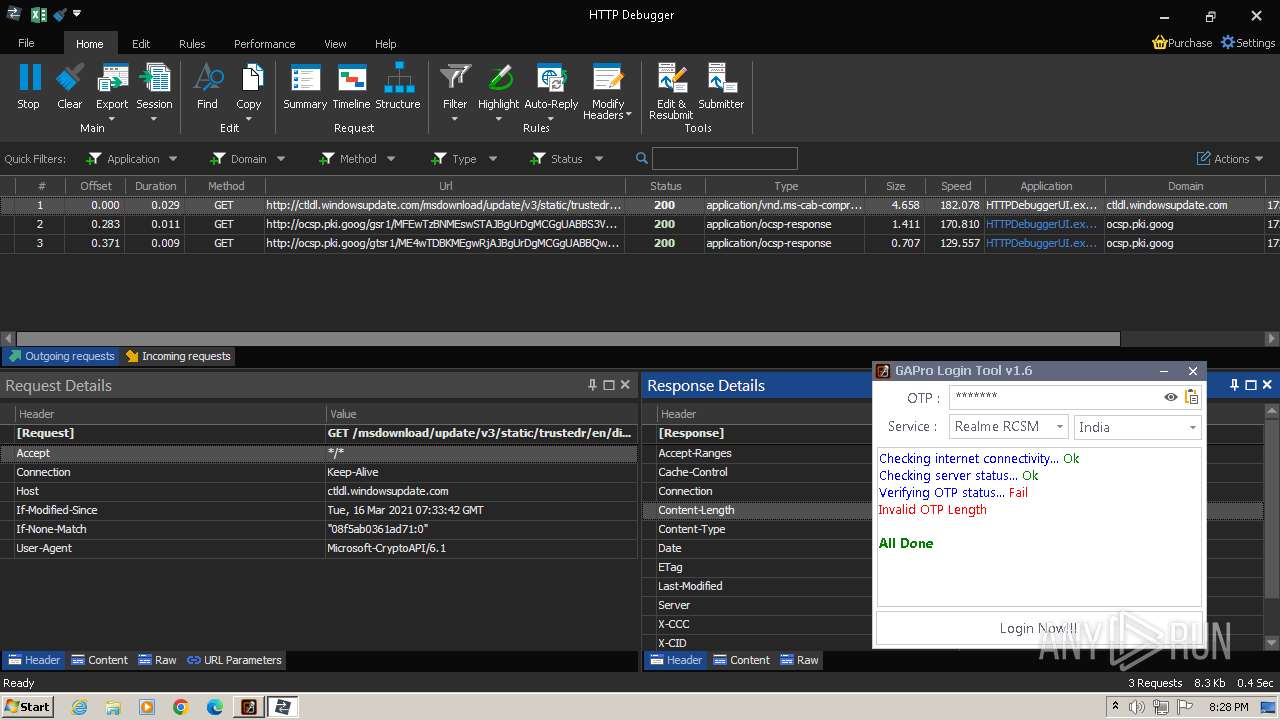
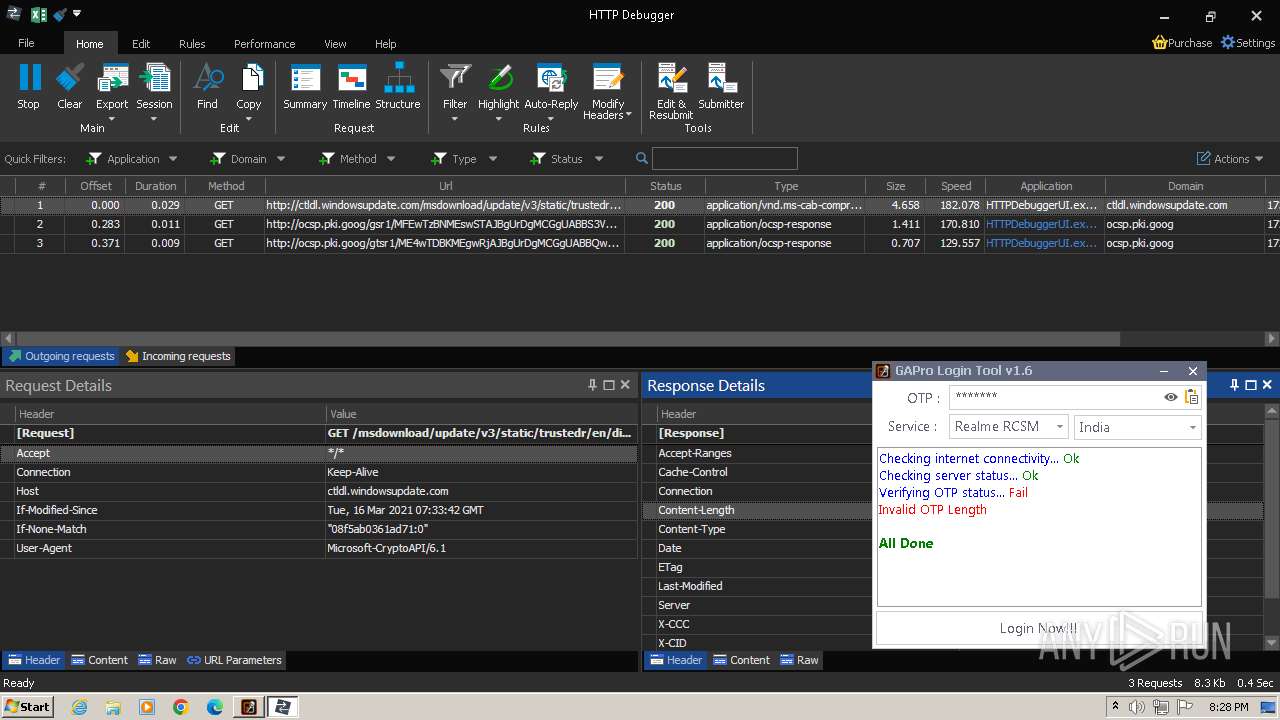
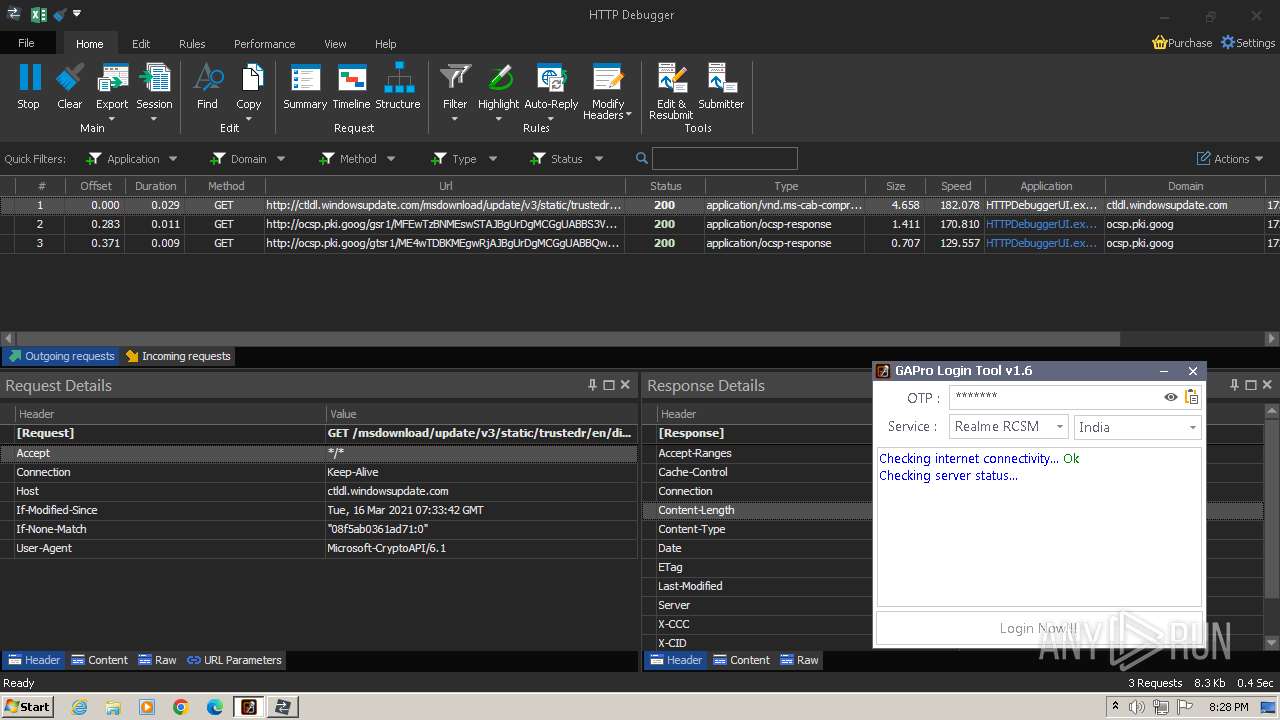
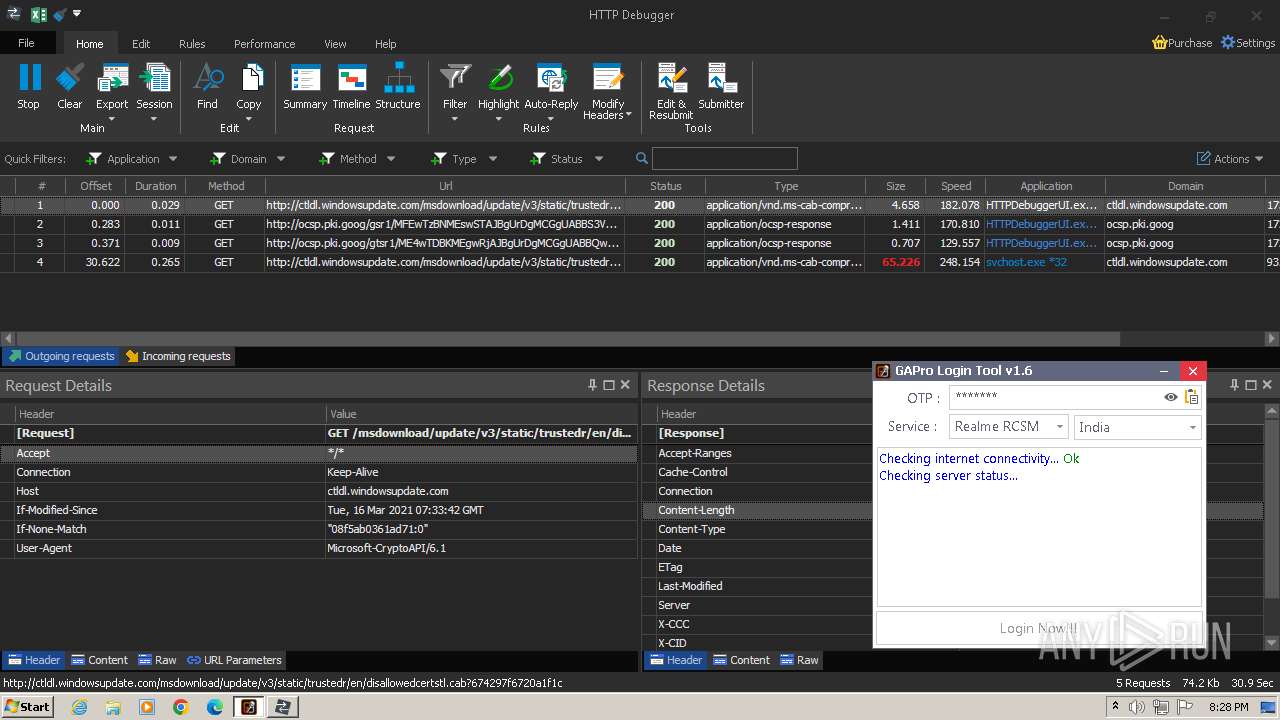
3888 | HTTPDebuggerUI.exe | GET | 200 | 173.222.108.219:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?674297f6720a1f1c | unknown | compressed | 4.66 Kb | unknown |
1080 | svchost.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?89542e423db2b091 | unknown | compressed | 65.2 Kb | unknown |
3888 | HTTPDebuggerUI.exe | GET | 200 | 172.217.18.99:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
3888 | HTTPDebuggerUI.exe | GET | 200 | 172.217.18.99:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFCjJ1PwkYAi7fE%3D | unknown | binary | 724 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
868 | svchost.exe | 184.30.20.134:80 | armmf.adobe.com | AKAMAI-AS | DE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
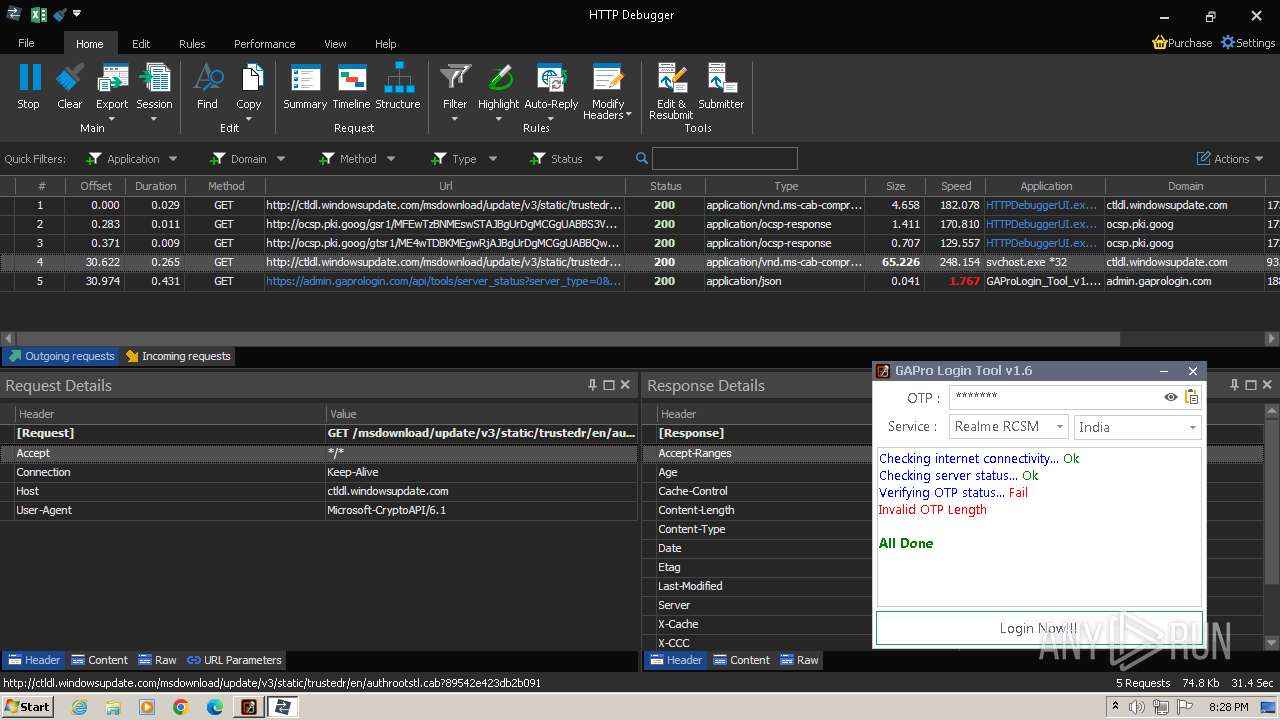
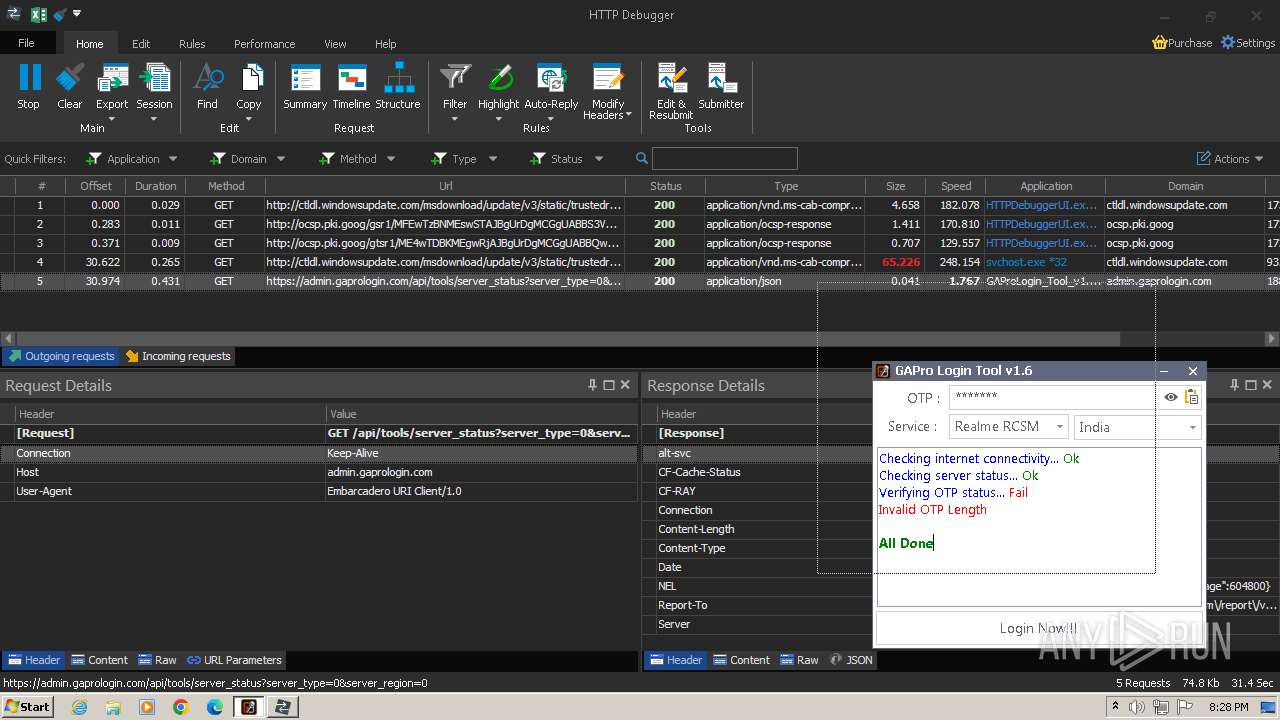
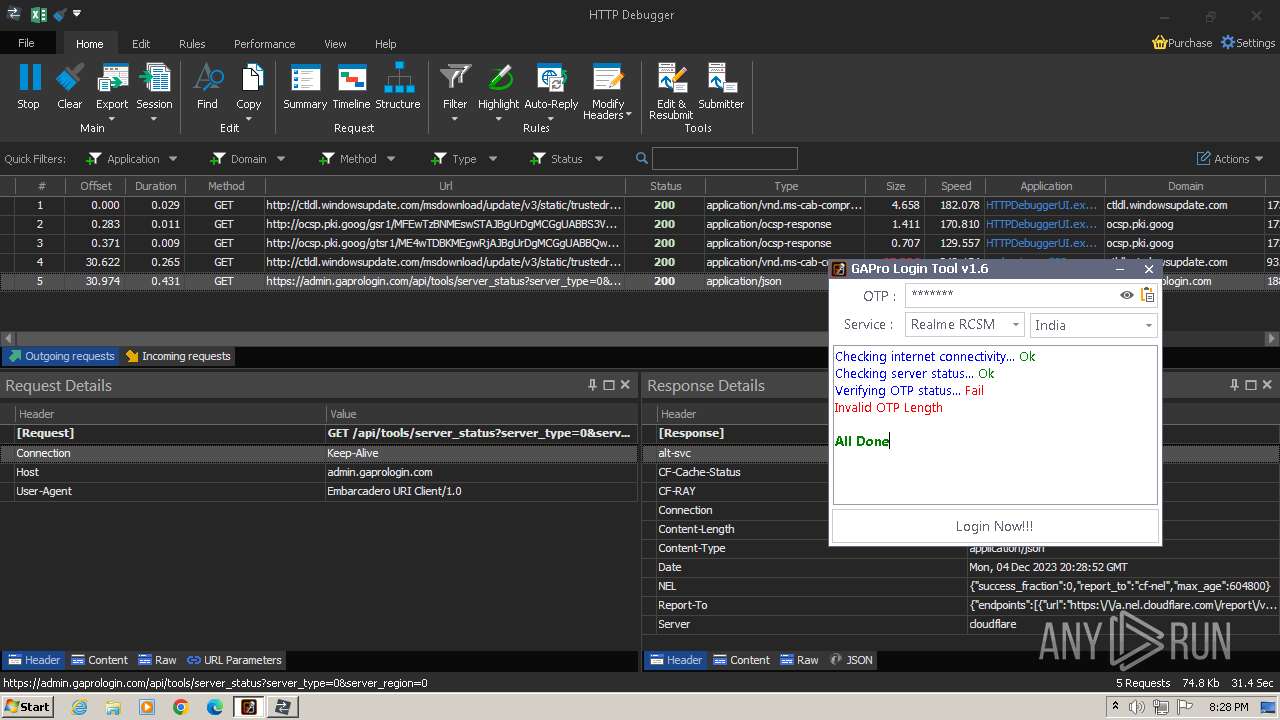
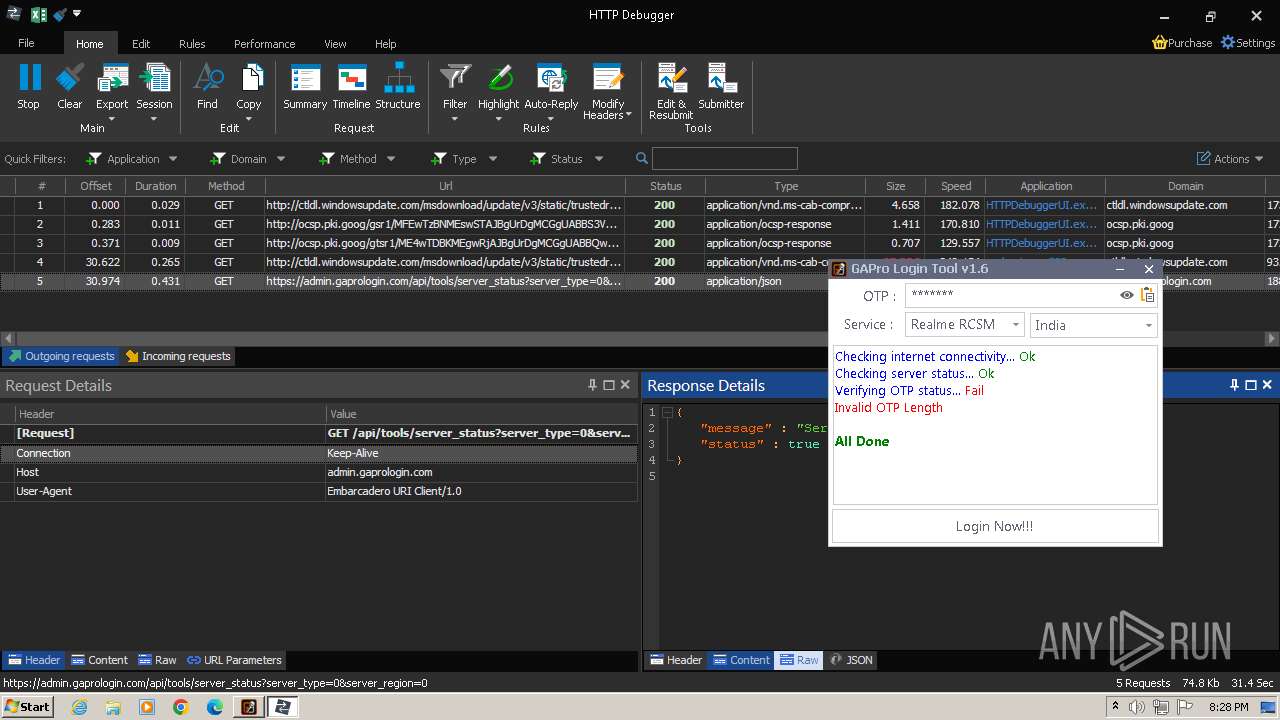
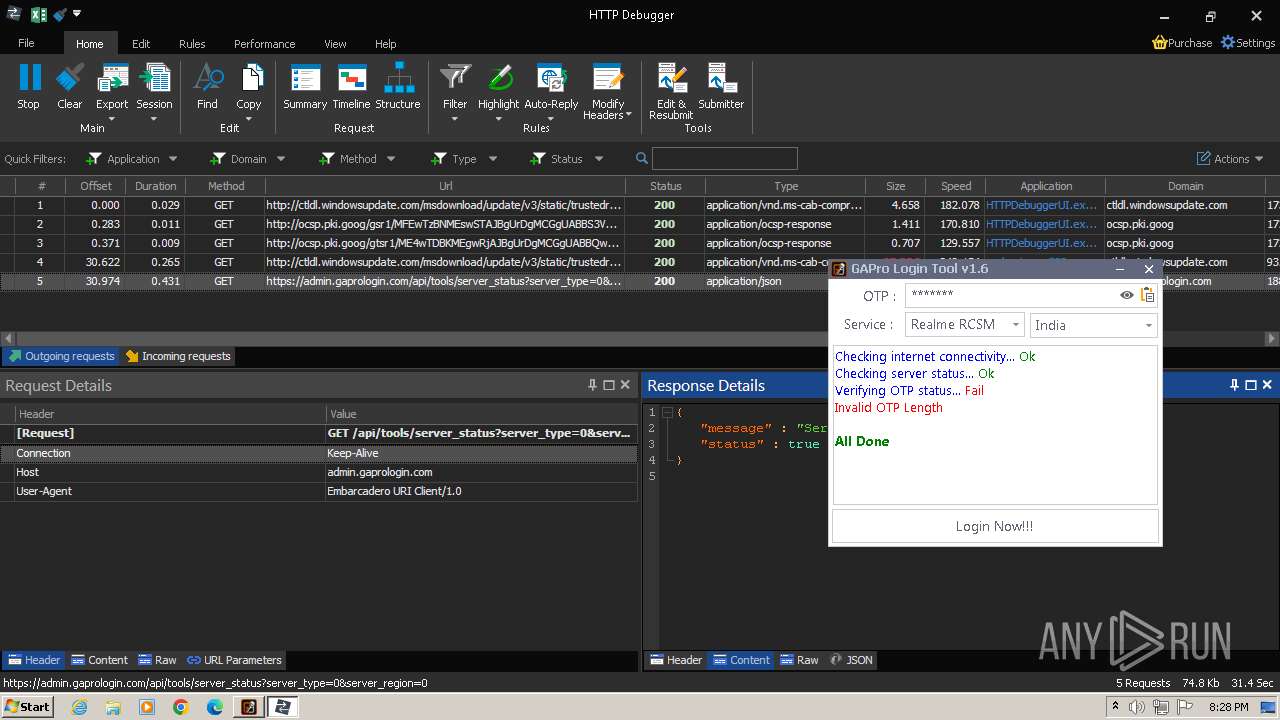
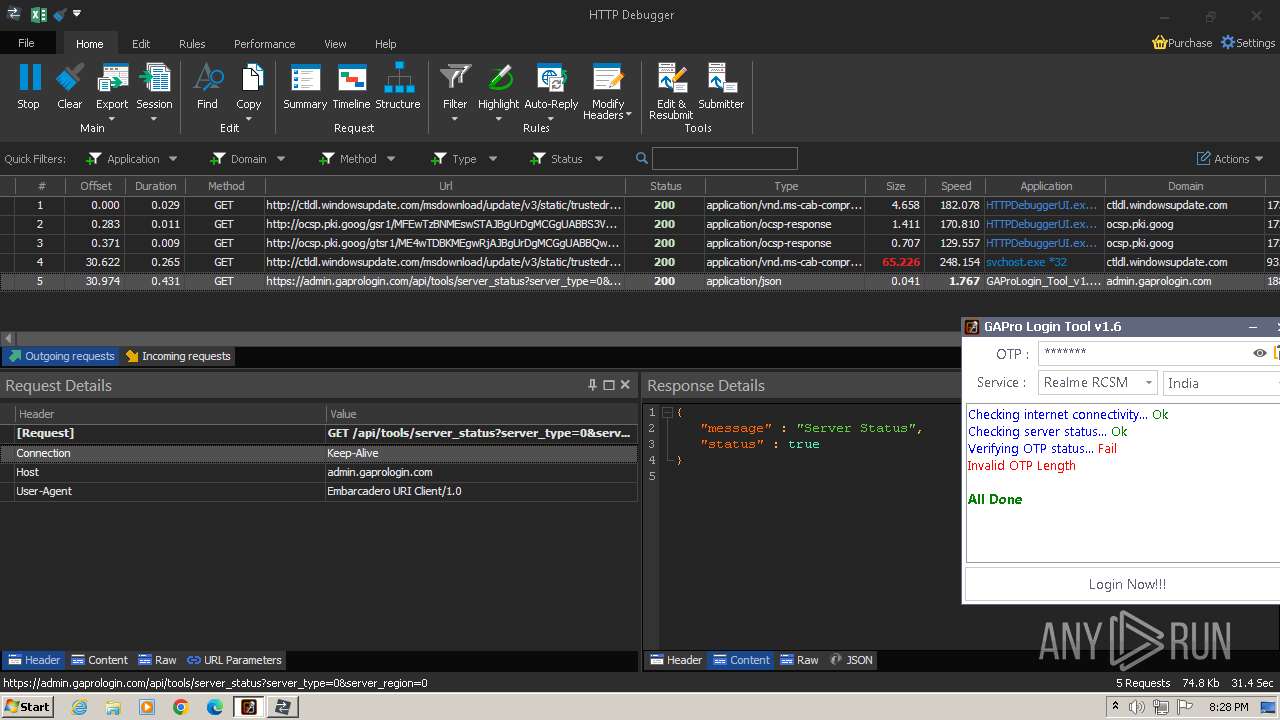
2600 | GAProLogin_Tool_v1.6.exe | 188.114.96.3:443 | admin.gaprologin.com | CLOUDFLARENET | NL | unknown |
2696 | chrome.exe | 142.250.185.131:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
3636 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2696 | chrome.exe | 108.177.15.84:443 | accounts.google.com | GOOGLE | US | unknown |
2696 | chrome.exe | 142.250.185.68:443 | www.google.com | GOOGLE | US | whitelisted |
2696 | chrome.exe | 142.250.186.131:443 | www.gstatic.com | GOOGLE | US | whitelisted |
3636 | chrome.exe | 224.0.0.251:5353 | — | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
armmf.adobe.com |
| whitelisted |
admin.gaprologin.com |
| unknown |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
update.googleapis.com |
| whitelisted |
apis.google.com |
| whitelisted |
encrypted-tbn0.gstatic.com |
| whitelisted |
lh5.googleusercontent.com |
| whitelisted |