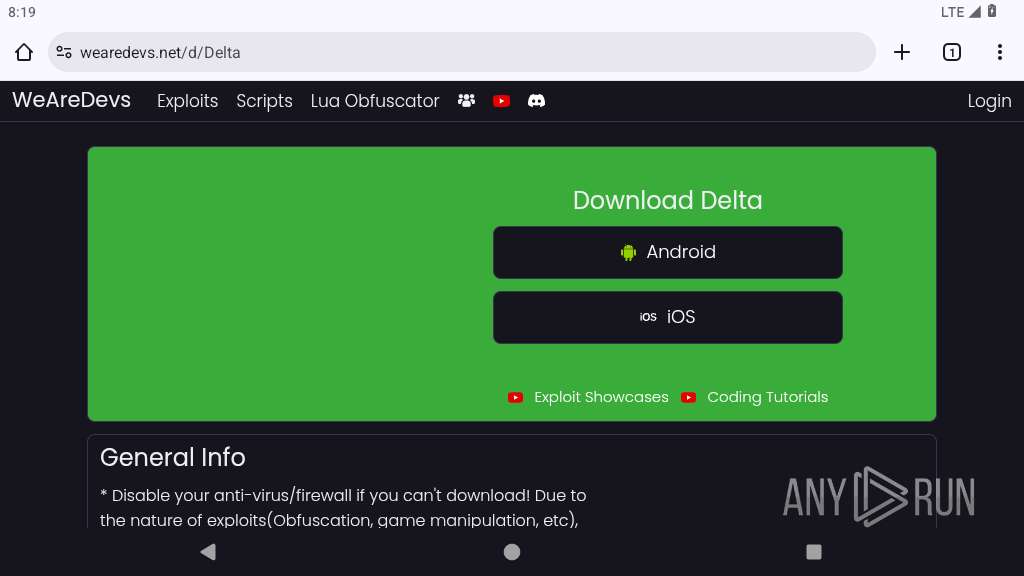
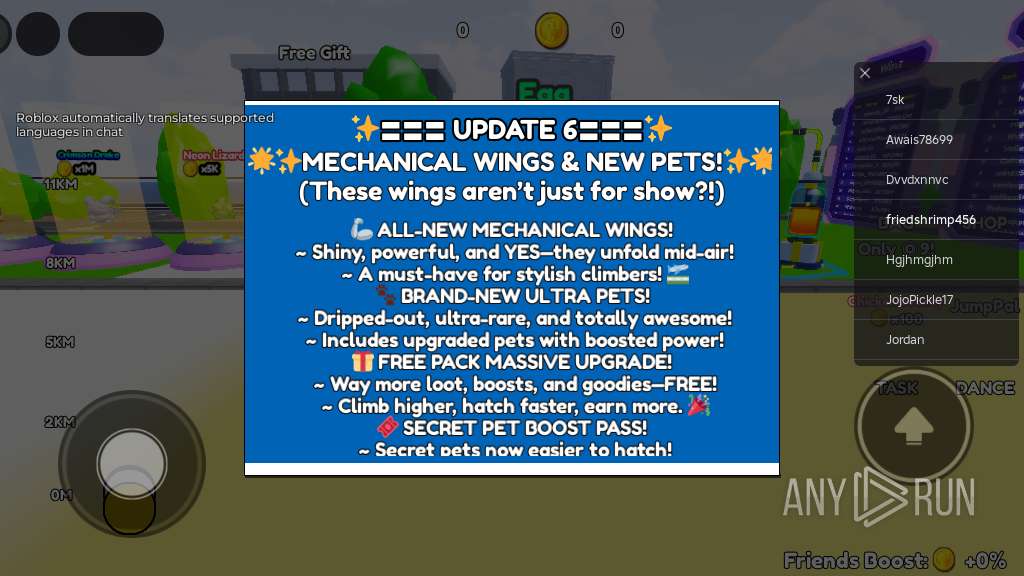
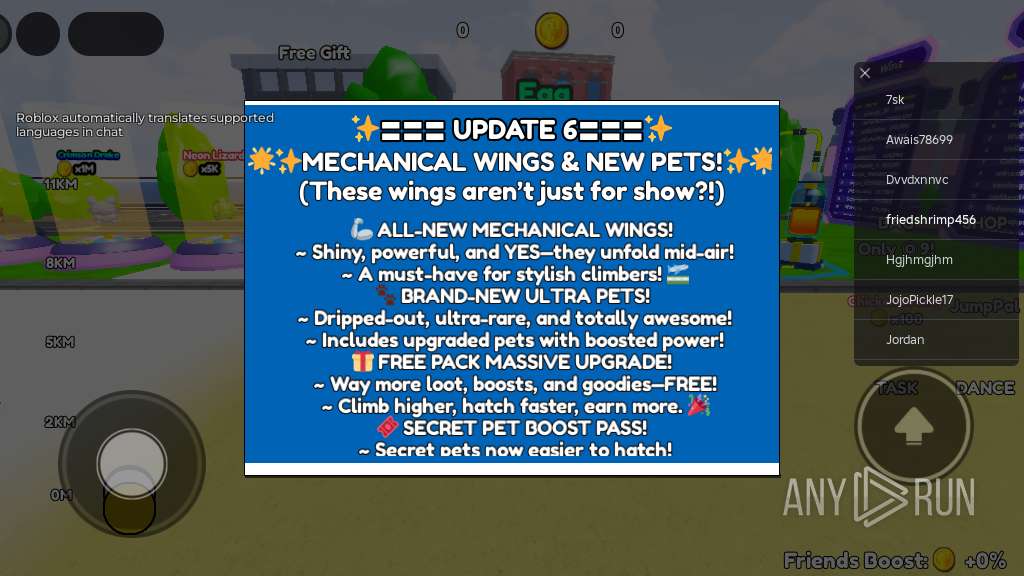
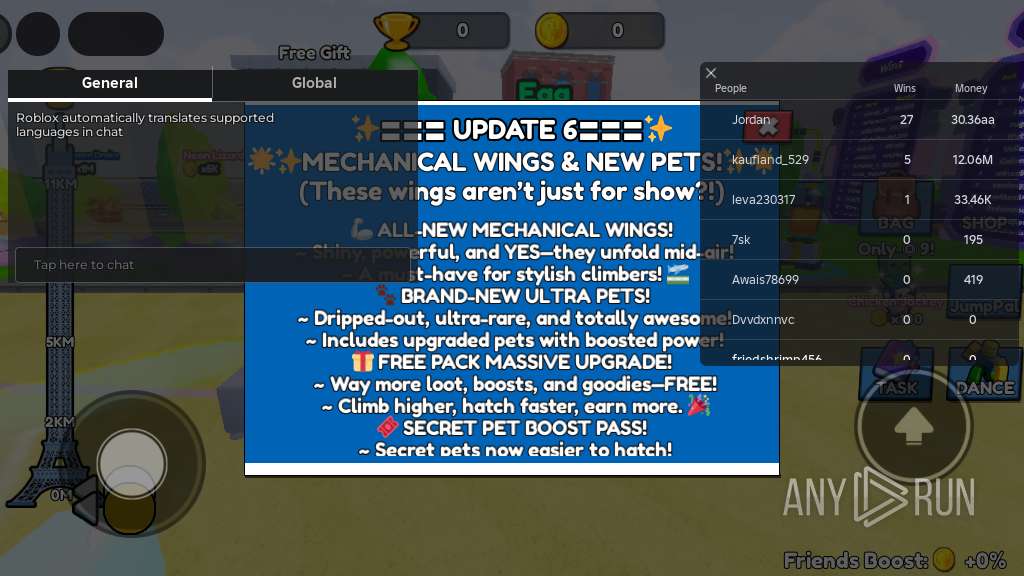
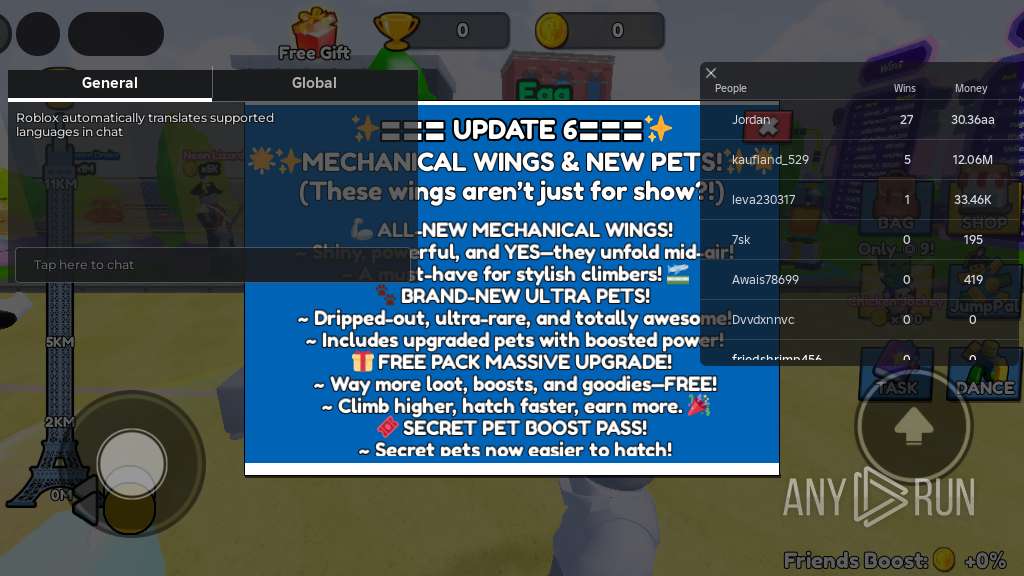
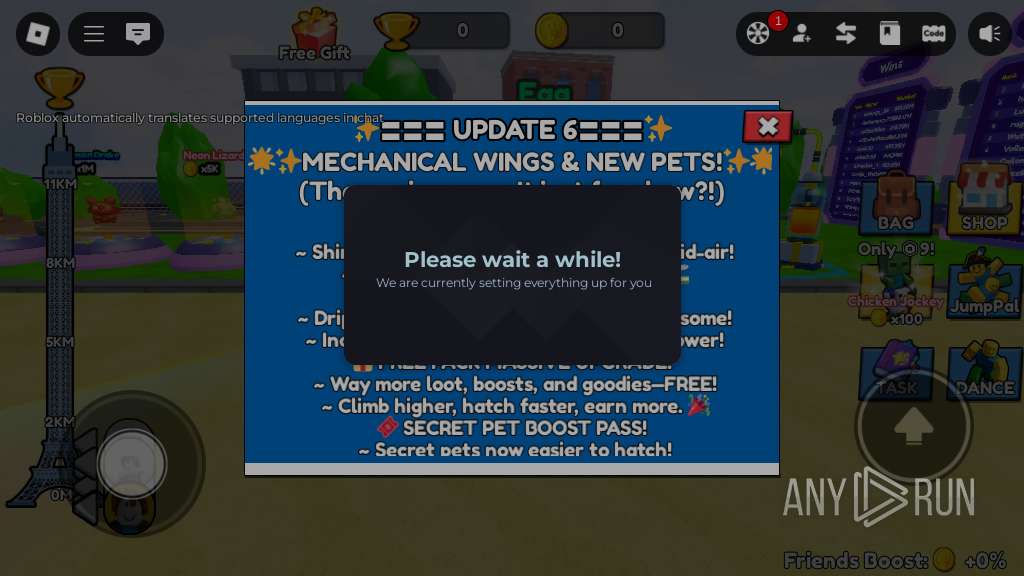
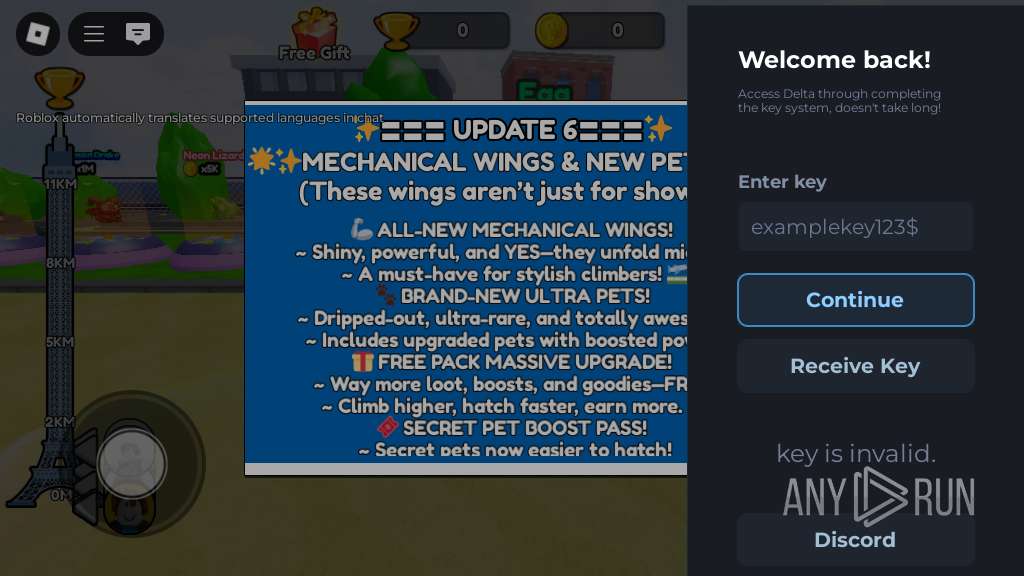
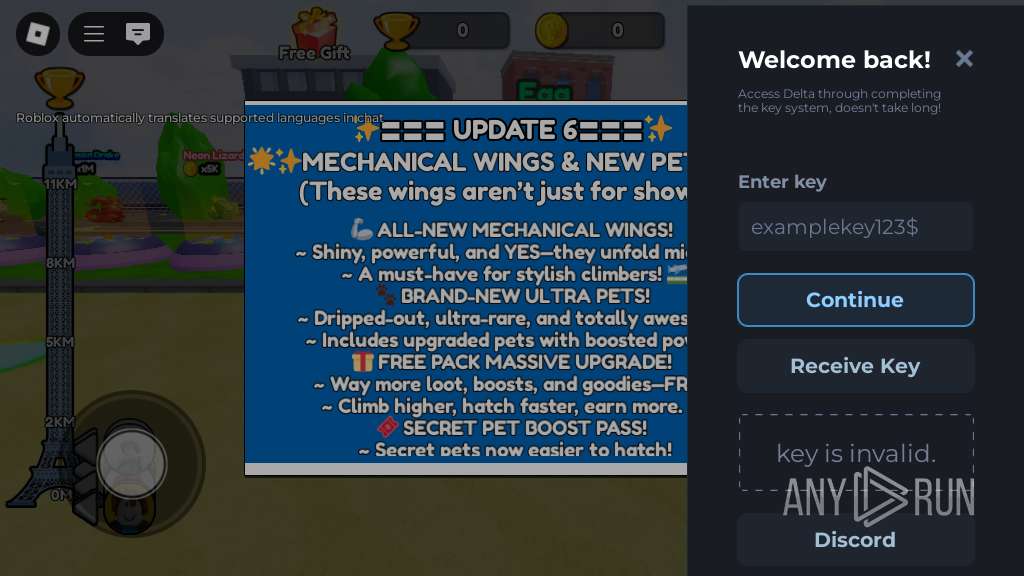
| URL: | https://wearedevs.net/d/Delta |
| Full analysis: | https://app.any.run/tasks/1b31e319-5c04-4fcc-bd1d-f74b39b997eb |
| Verdict: | Malicious activity |
| Analysis date: | June 12, 2025, 20:19:02 |
| OS: | Android 14 |
| Tags: | |
| Indicators: | |
| MD5: | 0CB7D0772652B9491B195075F0783617 |
| SHA1: | 5400C1AF637A15EEAD44A552B46C3FE0329016DF |
| SHA256: | 00DE8E94FCAE2354458E8E08E46158B8B4F57F288848FC56BA45EF303903D0B1 |
| SSDEEP: | 3:N8R/BApK8ORE:25BuBOi |
MALICIOUS
Executes system commands or scripts
- app_process64 (PID: 2801)
SUSPICIOUS
Collects data about the device's environment (JVM version)
- app_process64 (PID: 2801)
Accesses system-level resources
- app_process64 (PID: 2801)
Establishing a connection
- app_process64 (PID: 2801)
Updates data in the storage of application settings (SharedPreferences)
- app_process64 (PID: 2801)
Retrieves a list of running application processes
- app_process64 (PID: 2801)
Accesses memory information
- app_process64 (PID: 2801)
Checks Bluetooth audio routing status
- app_process64 (PID: 2801)
Launches a new activity
- app_process64 (PID: 2801)
Accesses external device storage files
- app_process64 (PID: 2801)
Reads device serial number identifier
- app_process64 (PID: 2801)
INFO
Dynamically inspects or modifies classes, methods, and fields at runtime
- app_process64 (PID: 2801)
Returns elapsed time since boot
- app_process64 (PID: 2801)
Loads a native library into the application
- app_process64 (PID: 2801)
Stores data using SQLite database
- app_process64 (PID: 2801)
Gets the display metrics associated with the device's screen
- app_process64 (PID: 2801)
Retrieves data from storage of application settings (SharedPreferences)
- app_process64 (PID: 2801)
Dynamically registers broadcast event listeners
- app_process64 (PID: 2801)
Retrieves the value of a secure system setting
- app_process64 (PID: 2801)
Verifies whether the device is connected to the internet
- app_process64 (PID: 2801)
Detects device power status
- app_process64 (PID: 2801)
Detects if debugger is connected
- app_process64 (PID: 2801)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
152
Monitored processes
30
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 1795 | com.android.statementservice | /system/bin/app_process64 | app_process64 | |
User: u0_a35 Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2232 | org.chromium.chrome | /system/bin/app_process64 | app_process64 | |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2285 | org.chromium.chrome_zygote | /system/bin/app_process64 | — | app_process64 |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2295 | org.chromium.chrome_zygote | /system/bin/app_process64 | — | app_process64 |
User: u0_a73 Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2324 | org.chromium.chrome:privileged_process0 | /system/bin/app_process64 | — | app_process64 |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2345 | com.android.adservices.api | /system/bin/app_process64 | — | app_process64 |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2386 | com.android.traceur | /system/bin/app_process64 | — | app_process64 |
User: u0_a54 Integrity Level: UNKNOWN Exit code: 512 | ||||
| 2416 | com.android.providers.partnerbookmarks | /system/bin/app_process64 | — | app_process64 |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2437 | org.chromium.chrome_zygote | /system/bin/app_process64 | — | app_process64 |
User: u0_a73 Integrity Level: UNKNOWN Exit code: 9 | ||||
| 2462 | /system/bin/dmesgd | /system/bin/dmesgd | — | init |
User: dmesgd Integrity Level: UNKNOWN Exit code: 0 | ||||
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
1 560
Text files
85
Unknown types
33
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2521 | app_process64 | /data/data/org.chromium.chrome/cache/.org.chromium.Chromium.ZQeDIX/manifest.json | binary | |
MD5:— | SHA256:— | |||
| 2521 | app_process64 | /data/data/org.chromium.chrome/cache/.org.chromium.Chromium.ZQeDIX/_metadata/verified_contents.json | ini | |
MD5:— | SHA256:— | |||
| 2541 | app_process64 | /data/data/org.chromium.chrome/cache/.org.chromium.Chromium.y4qkwX/list.pb | binary | |
MD5:— | SHA256:— | |||
| 2541 | app_process64 | /data/data/org.chromium.chrome/cache/.org.chromium.Chromium.y4qkwX/manifest.json | binary | |
MD5:— | SHA256:— | |||
| 2541 | app_process64 | /data/data/org.chromium.chrome/cache/.org.chromium.Chromium.y4qkwX/LICENSE | text | |
MD5:— | SHA256:— | |||
| 2541 | app_process64 | /data/data/org.chromium.chrome/cache/.org.chromium.Chromium.y4qkwX/_metadata/verified_contents.json | ini | |
MD5:— | SHA256:— | |||
| 2541 | app_process64 | /data/data/org.chromium.chrome/app_chrome/component_crx_cache/cab4d1f0a6a2a1afecae808a520f6690dd2b9d58bf54762877f2dc9715d55461 | binary | |
MD5:— | SHA256:— | |||
| 2582 | app_process64 | /data/data/org.chromium.chrome/cache/.org.chromium.Chromium.iUpOfz/privacy-sandbox-attestations.dat | binary | |
MD5:— | SHA256:— | |||
| 2582 | app_process64 | /data/data/org.chromium.chrome/cache/.org.chromium.Chromium.iUpOfz/manifest.json | binary | |
MD5:— | SHA256:— | |||
| 2582 | app_process64 | /data/data/org.chromium.chrome/cache/.org.chromium.Chromium.iUpOfz/_metadata/verified_contents.json | ini | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
330
DNS requests
228
Threats
132
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2232 | app_process64 | GET | — | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/diffgen-puffin/obedbbhbpmojnkanicioggnmelmoomoc/46aa4b4e34cfc311dbd61b35e64b658c48ee348f8763d0c15933e0d49c73305c | unknown | — | — | whitelisted |
— | — | GET | 204 | 142.250.186.67:80 | http://connectivitycheck.gstatic.com/generate_204 | unknown | — | — | whitelisted |
2232 | app_process64 | GET | 200 | 142.250.186.142:80 | http://clients2.google.com/time/1/current?cup2key=9:6fp4SeT36Dd9FB2OCCMSONJtYDt0oh3BZ5oc3Ya-ERs&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
2232 | app_process64 | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/diffgen-puffin/kgdbnmlfakkebekbaceapiaenjgmlhan/e41131c999e82c36dd1a380288d4af2f5decfed1ab6077c8c0aece3d05e1d0ea | unknown | — | — | whitelisted |
2232 | app_process64 | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acdvcifl2ztime6bsz3eijtcfeaq_2025.5.15.1/kiabhabjdbkjdpjbpigfodbdjmbglcoo_2025.05.15.01_all_ehum5zzx5qnqq3vyyhyi6ytrfq.crx3 | unknown | — | — | whitelisted |
2232 | app_process64 | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/pcbw6tyw7x3rtjiemkmpb6yn2m_2025.6.9.0/kgdbnmlfakkebekbaceapiaenjgmlhan_2025.06.09.0_all_bvkcqje4h2s3xof6azs7f4xfba.crx3 | unknown | — | — | whitelisted |
2232 | app_process64 | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/V3P1l2hLvLw_7/7_all_sslErrorAssistant.crx3 | unknown | — | — | whitelisted |
2232 | app_process64 | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/pmwjjzrzpgfwjodqqj542dn6kq_67/khaoiebndkojlmppeemjhbpbandiljpe_67_android_epp2f7wtecwsnk5eqcobxrqmyi.crx3 | unknown | — | — | whitelisted |
2232 | app_process64 | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/itevd7lf7x6ftnuj3eofyx22v4_9860/hfnkpimlhhgieaddgfemjhofmfblmnib_9860_all_acm32ncklefaevf77whpuuisda2a.crx3 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
451 | mdnsd | 224.0.0.251:5353 | — | — | — | unknown |
— | — | 216.239.35.12:123 | time.android.com | — | — | whitelisted |
— | — | 142.250.184.196:443 | www.google.com | GOOGLE | US | whitelisted |
— | — | 142.250.186.67:80 | connectivitycheck.gstatic.com | GOOGLE | US | whitelisted |
— | — | 74.125.133.81:443 | staging-remoteprovisioning.sandbox.googleapis.com | GOOGLE | US | whitelisted |
2232 | app_process64 | 142.250.186.142:80 | clients2.google.com | GOOGLE | US | whitelisted |
2232 | app_process64 | 104.26.6.147:443 | wearedevs.net | — | — | whitelisted |
2232 | app_process64 | 74.125.133.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
2232 | app_process64 | 142.250.186.100:443 | www.google.com | — | — | whitelisted |
2232 | app_process64 | 142.250.181.234:443 | fonts.googleapis.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.google.com |
| whitelisted |
connectivitycheck.gstatic.com |
| whitelisted |
time.android.com |
| whitelisted |
staging-remoteprovisioning.sandbox.googleapis.com |
| whitelisted |
google.com |
| whitelisted |
clients2.google.com |
| whitelisted |
wearedevs.net |
| whitelisted |
accounts.google.com |
| whitelisted |
cdn.wearedevs.net |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO Android Device Connectivity Check |
2232 | app_process64 | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
2232 | app_process64 | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
2232 | app_process64 | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
2232 | app_process64 | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
2232 | app_process64 | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
2232 | app_process64 | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
2232 | app_process64 | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
2232 | app_process64 | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
2232 | app_process64 | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |